Abstract
The Industrial Internet of Things (IIoT) is pivotal in advancing industrial automation, offering significant improvements in connectivity and efficiency. However, the integration of heterogeneous devices within IIoT systems presents substantial challenges, primarily due to the diversity in device hardware, protocols, and functionalities. In this paper, we propose a new pattern language specifically designed to enhance interoperability and operational efficiency across industrial settings. Drawing from a case study of the State Company for Automotive Industry (S.C.A.I.) in Iraq, this study details the development and integration of eleven interrelated patterns. These patterns were carefully combined based on identified relationships, forming a comprehensive pattern language that addresses key aspects of system heterogeneity, including device communication, data security, and system scalability. The pattern language was validated using the Delphi process theory, engaging industry experts to refine and optimize the framework for practical application. The implementation of this pattern language led to significant improvements in system integration, enabling seamless communication between diverse devices and enhancing operational workflows. The case study demonstrates the practical viability of the proposed pattern language in enhancing interoperability within real-world Industrial Internet of Things (IIoT) applications. Furthermore, the replicable nature of this framework makes it a valuable resource for other industrial environments seeking to harness the power of IIoT technologies.
1. Introduction
The Industrial Internet of Things (IIoT) refers to the interconnected network of physical devices, vehicles, buildings, and other items embedded with electronics, software, sensors, and network connectivity that enable these objects to collect and exchange data. An IIoT system, therefore, is an integrated platform that facilitates the management, processing, and analysis of data from heterogeneous devices within industrial settings, leading to improved decision-making, operational efficiency, and automation.
The IIoT represents a transformative leap in the landscape of industrial automation, enhancing connectivity, monitoring, and operations across a wide array of devices and systems [1]. As industries relentlessly push towards digitization, the challenges associated with managing diverse, heterogeneous devices become increasingly complex. One pivotal challenge is the heterogeneity in device technologies. Indeed, IIoT systems varied in terms of communication protocols, operating systems, and functionalities, which often impedes seamless integration and efficient operation [2]. Addressing heterogeneity issues is crucial because the diverse nature of device technologies can create integration and interoperability challenges. A structured approach, such as the application of a pattern language tailored for IIoT systems, can provide coherent solutions to these challenges, ensuring robust, scalable, and interoperable IIoT architectures [3].
The IIoT systems architecture typically consists of four layers: device layer, communication layer, data layer, and application layer. The device layer includes heterogeneous devices such as sensors, actuators, and controllers that collect data from the physical world. The communication layer facilitates the transfer of data between devices and the data layer, which stores and processes data. Finally, the application layer leverages the data to provide insights and value to end users [4,5].
Addressing these challenges necessitates innovative solutions that transcend conventional design and management approaches. This paper applies our pattern language, which is specifically tailored for designing IIoT systems, to incorporate heterogeneous problems for IIoT devices. Our primary objective is to develop a comprehensive pattern language tailored specifically to enhance interoperability within IIoT systems. Although we focus on interoperability, the concept of operational efficiency is inherently addressed through the systematic integration and application of these patterns.
A pattern language offers a structured method of describing good design practices within a field of expertise. Software patterns are solutions to common design problems. These patterns are used socially as pattern languages to resolve issues. Simply put, a pattern language is a group of related patterns that provide a step-by-step process to solve a specific problem within a given context [6]. This approach is exemplified by the application of modular language in industrial environments, as demonstrated in the case study of the State Company for Automotive Industry (S.C.A.I.) in Iraq.
The concept of heterogeneity in IIoT systems refers to the diversity and variance in device hardware, operating systems, protocols, and functionalities within a network. This diversity often introduces challenges in interoperability, scalability, and management. Heterogeneity can manifest in several forms, including but not limited to sensor diversity, communication protocols, and data formats [7]. Pattern languages, originally coined by architect Christopher Alexander [8], are applied within the IIoT to provide a structured and coherent collection of design patterns that systematically address specific problems. A pattern in this context is a proven solution to a common problem, encapsulating essential information about how to implement the solution effectively in various contexts. The use of a pattern language facilitates the design and integration of complex systems by offering a set of interconnected patterns that are both compatible and complementary [9].
The use of design patterns undoubtedly improves the quality of production and reduces software maintenance costs [10,11]. When applying patterns, it is important to consider their inter-relationships to create a more concise and cohesive design, rather than applying patterns in isolation [12,13]. The best practice for applying patterns to their inter-relationships is to use pattern languages to solve problems as a whole [14,15]. A pattern language is a collection of interrelated patterns that can be used to solve specific software development problems [13].
Eleven patterns were carefully selected for this work, as they form a comprehensive toolkit that addresses the main challenges of heterogeneity in IIoT systems. These patterns were chosen based on their seamless interconnectivity and ability to support each other, ensuring a robust and integrated design framework. The criteria for selecting and arranging these patterns included various factors, such as the following:
- Relevance: IIoT patterns are crucial for addressing security and privacy challenges, enhancing the adoption and implementation of IoT devices and services. Patterns encode solutions to common problems and facilitate secure and privacy-aware design in IoT environments [16].
- Complementarity: Patterns in software engineering, including those used in IIoT, promote reusability and interoperability among components, offering modular solutions that complement each other and enhance system functionality [17].
- Interoperability: Digital twins in IIoT systems enable significant interoperability and flexibility by facilitating the integration of diverse data sources and enhancing system responsiveness [18].
- Data Flow: The design of IIoT systems emphasizes robust data acquisition systems that support a wide range of data handling capabilities from collection to analytics, ensuring effective data flow throughout the system [19].
- System Functionality: IIoT design patterns significantly contribute to system architecture by enhancing connectivity and security, thereby supporting complex system functionalities and integration across varied industrial environments [20].
- Complexity: Patterns provide structured approaches to managing complexity in IIoT systems, from simple device communications to sophisticated analytics and fault tolerance mechanisms, making complex systems more manageable and efficient [21].
The rest of this paper is organized as follows. Section 2 discusses the related works in the field of IIoT systems, focusing on previous research and approaches that address heterogeneity and integration challenges. Section 3 elaborates on the proposed approach, detailing the development and application of the pattern language designed to enhance IIoT systems. Section 4 presents the case study of the State Company for Automotive Industry (S.C.A.I.) in Iraq, illustrating the practical implementation and effectiveness of the pattern language in a real-world industrial setting. Section 5 involves the validation of the pattern language using the Delphi process theory, providing insights from industry experts. Finally, Section 6 concludes the paper, summarizing the findings and discussing potential future research directions.
2. Related Work
The rapidly evolving field of the IIoT is marked by integrating heterogeneous systems and developing sophisticated pattern languages. This section explores pivotal research contributions addressing system heterogeneity and applying pattern languages to enhance IIoT systems. By examining these efforts, we gain insights into the diverse strategies employed to ensure seamless operation and efficiency in IIoT environments. ultimately paving the way for more resilient and adaptive industrial applications.
2.1. Heterogeneous Systems
In the domain of IIoT, significant progress has been made in addressing the challenges posed by heterogeneous systems. Song et al. [22] developed methodologies for matching events with patterns across diverse data types, enhancing the capability to derive meaningful insights from disparate data streams. Complementary to this, Hadj Kacem et al. [23] focused on enhancing the security and efficiency during the initial setup of IoT devices, a critical aspect for maintaining robustness from the onset of deployment. Further extending the versatility of IIoT applications beyond industrial settings, Jin [24] explored the integration of diverse educational resources, providing a template for data integration and real-time operational challenges. Xiong et al. [25] addressed the pivotal need for robust communication links by designing novel authentication protocols for heterogeneous IIoT systems, thereby enhancing security. Petroulakis et al. [26] introduced a comprehensive framework ensuring end-to-end security, connectivity, and interoperability within IIoT, aligning with structured design patterns to handle system heterogeneity.
Wang et al. [27] presented a distributed Q-learning algorithm aimed at enhancing network resource allocation in IIoT environments, optimizing energy efficiency and overall service quality through adaptive management of network conditions. Sengupta et al. [28] introduced a framework for community detection in heterogeneous networks using spectral clustering, primarily analytical in nature but offering valuable insights for managing operational systems in dynamic IIoT environments.
Narayanan et al. [29] proposed a probabilistic framework for protocol conversions across heterogeneous gateways, optimizing data transmission and reducing conversion overhead. Liu et al. [30] discussed managing and querying heterogeneous fuzzy XML databases using advanced tree pattern-matching techniques, improving data retrieval accuracy and efficiency.
2.2. Pattern Languages and IIoT Systems
This section reviews various pattern languages and their applications in IIoT, highlighting their benefits and limitations. Parallel to these technological advancements, the development of pattern languages has been instrumental in addressing the complexities of IIoT systems. Arcaini et al. [31] constructed MSL, a pattern language tailored for engineering self-adaptive systems, addressing the broader scope of system integration challenges. Jaloudi [32] evaluated communication protocols within IIoT environments, ensuring high reliability and low latency, further reinforcing these efforts.
Hamood et al. [33] introduced an innovative federated learning framework, aligning with the use of pattern languages to improve system operations and maintenance predictively. Chand et al. [34] evaluated machine learning models for design pattern recognition, mirroring the use of similar technologies to meet the unique operational demands of IIoT systems.
Yu et al. [35] proposed an efficient method for detecting structural design patterns in software systems, significantly reducing the search space and facilitating rapid identification of pattern instances. Orłowski et al. [36] developed a design pattern language ontology for Smart City systems, managing complex knowledge and data effectively through design patterns.
Elaasar et al. [37] introduced VPML, a unified approach for detecting design patterns in MOF-based modeling languages, enhancing model comprehension and maintenance. Rouhi et al. [6] developed a formal model for understanding and applying patterns and pattern languages, utilizing EBNF to graphically model patterns. Zamani et al. [38] introduced the Pattern Language Verifier, a tool designed to verify the application of pattern languages in model-driven design frameworks.
The presented works illustrate the significant strides made in both managing heterogeneity in IIoT systems and developing robust pattern languages. These advancements collectively contribute to the enhancement of IIoT systems’ functionality, security, and efficiency. By integrating diverse methodologies and innovative frameworks, researchers continue to pave the way for more resilient and adaptive IIoT environments, ensuring that these systems can meet the evolving demands of modern industrial applications.
Table 1 presents a comparative analysis of existing works in the field of IIoT systems, highlighting the focus areas of each study. The identified research gaps, particularly in addressing comprehensive interoperability and the integration of heterogeneous devices, underscore the need for a structured pattern language that can bridge these gaps. Unlike previous studies, which often address these challenges in isolation, our research proposes an integrated approach through a pattern language that systematically enhances both interoperability and operational efficiency.

Table 1.
A comparative analysis of existing works on IIoT system design.
3. Pattern Language Development
Based on the principles outlined earlier, the pattern language was developed to offer practical solutions and formal linkages for dealing with heterogeneity issues in IIoT. The sequence and specific application of these patterns are detailed as follows:
3.1. Overview of Patterns
The patterns have been thoughtfully chosen for this work, as they make up a complete toolkit that tackles the primary challenges of heterogeneity in IIoT systems. These patterns were selected for their smooth interconnectivity and their ability to complement each other, ensuring a strong and cohesive design framework.
- Publish/Subscribe [39]: Ensuring that heterogeneous devices can communicate with each other and with the IIoT system.
- Device Gateway [40]: Connecting devices with various communication protocols using gateways to provide data exchange and functionalities inside an IIoT system.
- Data Acquisition [41]: Collecting data from heterogeneous devices and integrating it into the IIoT system.
- Edge Computing [42]: Addresses the need for efficient data processing and analytics in IIoT systems.
- Device Management [43]: Managing the lifecycle of heterogeneous devices, including device discovery, configuration, provisioning, and maintenance.
- Security (Authentication) [44]: Ensuring the security of IIoT systems and devices. Includes strategies for the authentication of data.
- Scalability [45]: Designing IIoT systems that can scale up or down based on changing demands.
- Modular Architecture [46]: Design the IIoT system as a collection of modular components that can be easily assembled and disassembled.
- Analytics [47]: Analyzing data collected from heterogeneous devices to extract insights and derive actionable information.
- Predictive Maintenance [48]: Using analytics techniques to predict when devices are likely to fail allows for proactive maintenance and replacement.
- Fault Tolerance [49]: Discusses the difficulty of creating IIoT systems that can function even if a device fails or the network is disrupted.
The term ‘pattern’ is used to describe a set of repeatable solutions to recurring problems in IIoT system design, extending beyond traditional software patterns to include use cases and non-functional requirements. This broader interpretation aligns with the unique challenges of IIoT systems, where interoperability, scalability, and security must be addressed holistically. While traditional literature often limits ‘patterns’ to reusable design solutions, our approach expands this definition to encapsulate the full spectrum of elements necessary for effective IIoT integration. This expansion is supported by works such as Alexander’s Pattern Language [50], which advocates for a flexible understanding of patterns in complex system design.
The confusion between ‘pattern’ and ‘solution’ arises because traditional patterns are often seen as generic solutions that can be reused in various contexts. However, in the context of IIoT, we assert that patterns need to be context-aware and problem-specific to be effective. According to Rouhi and Zamani [6], patterns should not only provide a solution but also embody the context, the forces that drive the design decisions, and the relationships with other patterns. Thus, by extending patterns to include use cases and non-functional requirements, we are aligning with a more nuanced understanding that considers these elements as patterns in their own right, shaped by specific IIoT contexts.
Additionally, Schmidt and Cleeland [15] support the view that patterns must be adaptable to specific contexts and not just static solutions. They argue that patterns, especially in complex systems like middleware or IIoT, often need to encapsulate specific scenarios (akin to use cases) and address various non-functional concerns, such as performance, security, and scalability. This interpretation justifies our approach of including these elements as part of a comprehensive pattern language tailored for IIoT systems.
The patterns are carefully categorized into three main points: core design patterns, extended design patterns, and supporting elements. This classification helps to provide a clearer understanding of how different elements function within the pattern language designed for IIoT systems.
Core Design Patterns: Core design patterns are the traditional patterns used in software engineering and system design. These include foundational design solutions like publish/subscribe, device gateway, and edge computing, which are central to enabling interoperability and communication between heterogeneous devices in IIoT environments. As described by Gamma et al. [51], these patterns represent reusable solutions to common problems, such as ensuring secure communication (Schmidt and Cleeland [15]).
Extended Design Patterns: Extended design patterns encompass elements that extend beyond the traditional scope of patterns, such as use cases and non-functional requirements (e.g., security, scalability). This extension aligns with the expanded understanding of patterns as argued by Alexander [50], who suggested that patterns should address a wider range of challenges in complex systems. Similarly, Lytra et al. [3] emphasize that pattern languages should adapt to their specific domain and include broader system-level concerns to provide holistic solutions. By incorporating use cases and non-functional requirements, we ensure that our pattern language not only addresses core design concerns but also adapts to the unique operational context of IIoT systems.
Supporting Elements: Supporting elements include practical, context-driven solutions that enhance the applicability of the pattern language within specific IIoT scenarios, such as predictive maintenance and fault tolerance. These elements, while not considered traditional patterns, are essential for addressing the specific operational challenges within IIoT systems. According to Rouhi and Zamani [6], patterns should embody not only solutions but also the context and forces driving the design decisions. By considering these elements as part of the broader pattern language, we align with the notion that patterns must be context-aware and problem-specific, particularly in complex systems like IIoT [15].
The inclusion of use cases and non-functional requirements as patterns is an intentional and strategic decision, motivated by the need to provide a comprehensive framework for designing IIoT systems. While this approach diverges from traditional definitions, it is supported by literature that advocates for flexibility in the application of patterns to address the unique challenges of complex systems. For instance, Hadj Kacem et al. [23] demonstrate the applicability of non-traditional patterns in IoT environments, suggesting that the unique requirements of IIoT systems justify an expanded understanding of what constitutes a “pattern”.
The integration of these patterns into the broader IIoT system architecture is what ultimately justifies their classification as “design patterns”. Each pattern plays a role in solving specific design challenges while contributing to the overall system architecture. For example, the publish/subscribe pattern facilitates decentralized communication, which is crucial in a distributed IIoT environment, while the security pattern ensures that this communication remains secure. The predictive maintenance pattern leverages data analytics to optimize system reliability, which is directly tied to the system’s operational efficiency.
By structuring these patterns within a cohesive framework, they collectively contribute to the design, development, and deployment of robust, scalable, and secure IIoT systems. Therefore, classifying these patterns as “design patterns” is not only appropriate but essential to understanding their role in addressing the complex challenges inherent in IIoT system design. Arranging patterns within the architecture layers of an IIoT system is crucial for optimal functionality and efficiency, enabling seamless integration, effective data management, and streamlined operations in industrial settings. Here is an arrangement showcasing the patterns incorporated in the work as shown in Table 2.

Table 2.
Placement of patterns in IIoT architecture layers.
3.2. Importance of Pattern Interrelationships
The strength of a pattern language lies not just in the individual patterns but significantly in how these patterns interact. Understanding these relationships is vital to designing systems that are both robust and versatile. For instance, the “Device Gateway” pattern can enhance the effectiveness of the “Data Acquisition” pattern by ensuring that data from various devices are normalized and integrated smoothly. Similarly, the “Edge Computing” pattern works in tandem with “Analytics” to process data locally, which speeds up decision-making and reduces the need for extensive data transmission. These relationships are systematically detailed in the document’s Table 2 and Table 3, where the dependencies and interactions among patterns are explored. This comprehensive mapping is essential for architects and designers to visualize the complete landscape of the system and effectively apply the pattern language to real-world scenarios.

Table 3.
Notations for representing the relationship between patterns.
The relationship and interaction among these patterns are crucial, as they ensure that the application of one pattern can enhance or complement the effectiveness of others, forming a robust and integrated system.
IIoT solutions refer to the complete frameworks or systems deployed to address specific industrial challenges. Patterns, on the other hand, are the building blocks of these solutions—reusable templates that solve particular design problems. For instance, a security pattern contributes to an IIoT solution by ensuring data integrity and confidentiality, thereby supporting the broader goal of operational reliability. By interconnecting various patterns, a coherent and effective IIoT solution can be architected [57].
4. Research Methodology
The practical implementation of our pattern language is exemplified in the case study of the State Company for Automotive Industry (S.C.A.I.) in Iraq. This section outlines how each identified pattern was applied to solve specific challenges associated with the IIoT within the automotive factory setting.
4.1. Case Study “State Company for Automotive Industrial (S.C.A.I.)”
The State Company for Automotive Industry (S.C.A.I.), an automobile manufacturing plant established in 1976 and located in the Babylon Governorate, Iraq, will focus on its transition towards implementing IIoT technologies. This transition marks S.C.A.I.’s endeavor to modernize its production processes and enhance its product offerings, which range from trucks and buses to saloon cars and specialized vehicles, in collaboration with international partners like Savim, Scania, and Icarus [58,59].
4.2. Case Study Design
S.C.A.I. has embarked on integrating IIoT technologies into its manufacturing processes to increase efficiency, improve product quality, and reduce downtime. However, the factory is encountering several challenges that hinder its progress and ability to keep up with the rapid development of IIoT solutions. The heterogeneous nature of devices, varying protocols, and the complexity of managing a vast array of IIoT components are among the significant issues faced by the company.
The adoption of IIoT technologies in the automotive manufacturing sector offers unprecedented opportunities for innovation, efficiency, and customization. S.C.A.I.’s initiative to embrace these technologies represents a strategic move to enhance its competitiveness in the global market. However, the journey towards a fully integrated IIoT-enabled manufacturing environment is fraught with challenges, particularly in terms of device heterogeneity, data management, security, scalability, and system interoperability.
4.3. Areas of the S.C.A.I. Components and Defects
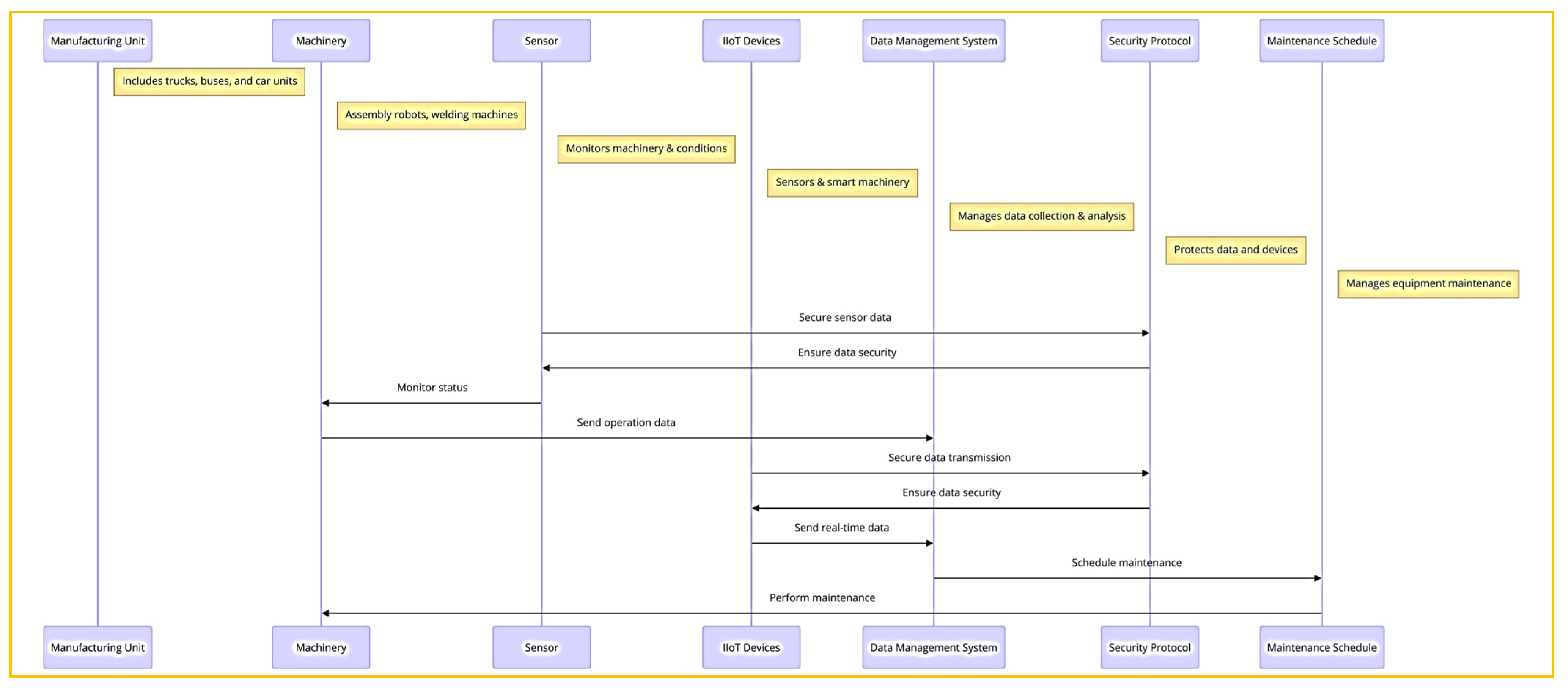
The S.C.A.I. is a complex structure that faces numerous challenges. It comprises several components, such as manufacturing units, machines, data management systems, and security protocols. The primary objective here is to create a structural overview that can identify potential defect areas and failure points while highlighting the relationships among the components [60]. Figure 1 shows a sequence diagram to specify the operation of the factory with its main components, which is described in the following.
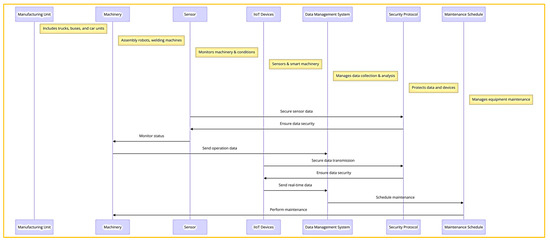
Figure 1.
The operation of the factory with its main components.
4.3.1. Main Components
- Manufacturing Unit: Represents the various production lines within the factory, such as trucks, buses, and saloon cars manufacturing units.
- Machinery: Includes all equipment used in production, from assembly robots to welding machines.
- Sensor: Devices that monitor machinery and environmental conditions.
- IIoT Device: A generalization for all IIoT-enabled devices, including sensors and smart machinery.
- Data Management System: Manages data collection, storage, and analysis.
- Security Protocol: Defines the security measures and protocols for protecting data and devices.
- Maintenance Schedule: Manages the maintenance activities for machinery and equipment.
Assembly robots and welding machines start assembling the car body, monitored by sensors. IIoT devices communicate real-time data to a central data management system, which analyzes the data and checks maintenance schedules. Security protocols ensure data safety while the assembly line continues through various stages, monitored by sensors. After assembly, quality checks are performed, and data are continuously fed back for real-time analysis and record-keeping, preparing for the next production cycle.
4.3.2. Defect Areas and Points of Failure
In the complex ecosystem of IIoT systems, identifying and understanding potential defect areas and points of failure across different components is critical to ensuring operational efficiency and system security. From the manufacturing unit to security protocols, each sector presents unique challenges and vulnerabilities that can significantly impact performance and reliability. This overview addresses the following main areas:
- Manufacturing Unit: Defect areas include overcapacity, underutilization, or outdated production techniques. Points of failure might involve the lack of flexibility in switching between product types or delays in production due to equipment failure.
- Machinery: Critical points of failure include machinery that is prone to frequent breakdowns due to lack of maintenance or obsolete technology. Defect areas cannot be identified in machinery that has a high energy consumption or low efficiency.
- Sensor and IIoT Device: Key defect areas involve inaccurate readings due to poor calibration or sensors that are not adequately rugged for the factory environment. A significant point of failure is the lack of secure firmware updates, risking cyber-attacks.
- Data Management System: Defects include insufficient data storage capacity or poor data analysis capabilities leading to inadequate decision-making. A failure point is a system overload due to excessive data inflow.
- Security Protocol: A major defect area is the lack of robust security measures, leading to vulnerabilities in data integrity and device safety. Points of failure include weak authentication mechanisms and insufficient encryption.
- Maintenance Schedule: Defects in scheduling result in delayed maintenance, causing unplanned downtime. A critical failure point is the lack of predictive maintenance capabilities, leading to equipment failures.
The identified defect areas provide a foundation for addressing challenges through targeted IIoT solutions, enhancing efficiency, security, and predictive maintenance capabilities.
4.4. Relationships and Associations
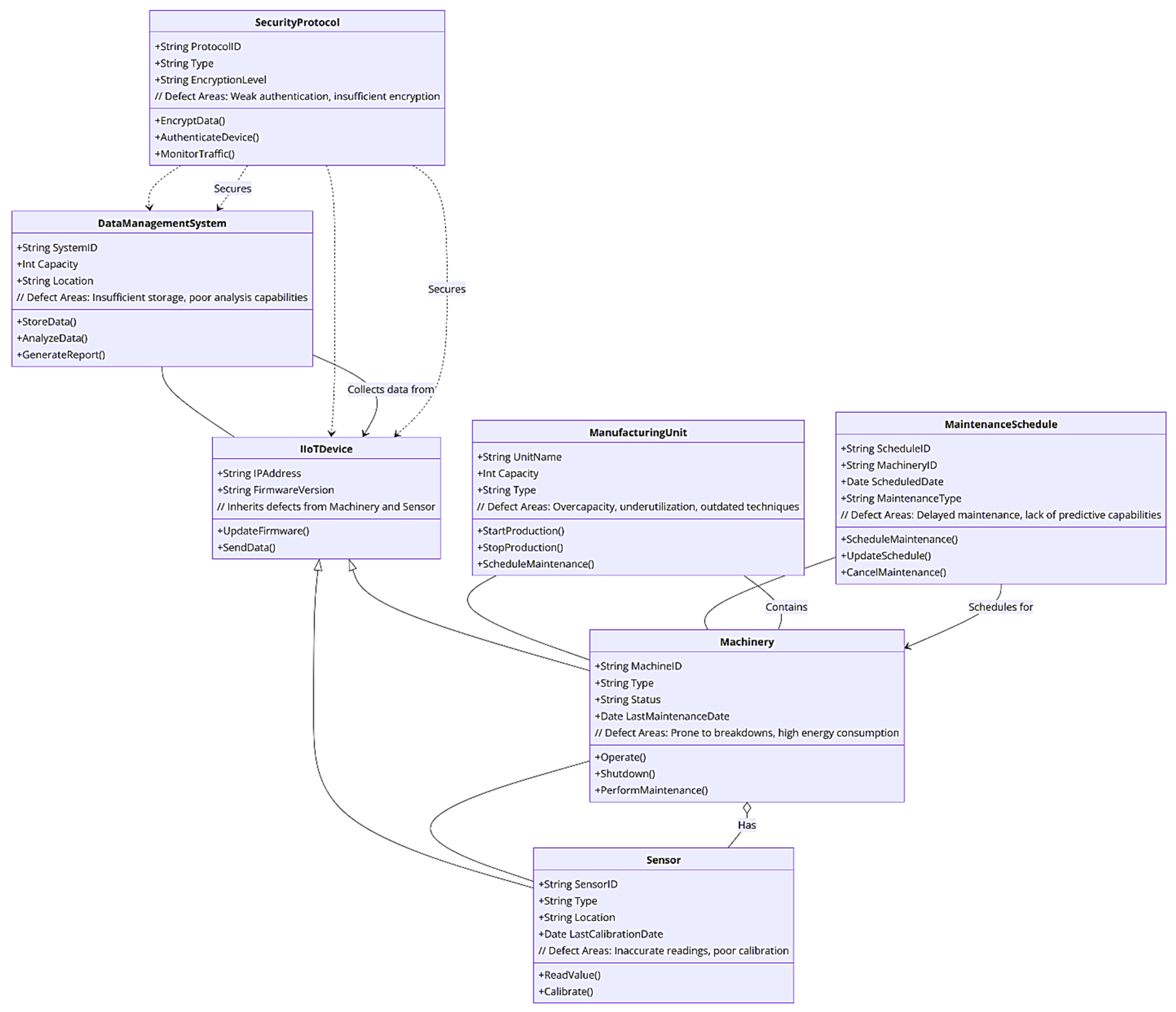
In the intricate domain of IIoT systems, understanding the relationships and associations among various components is pivotal for designing robust and efficient networks. These relationships, which include composition, aggregation, generalization, association, and dependency, serve as the foundation for how different elements within an IIoT system interact and function together. By exploring the relationships between manufacturing units and machinery, machinery and sensors, IIoT devices and their subclasses (sensors and machinery), data management systems, security protocols, and maintenance schedules, we uncover the structural and operational dynamics essential for the seamless integration of heterogeneous devices. Each relationship type conveys a specific mode of interaction, highlighting the dependencies, data flow, and hierarchical structures within the system, thereby guiding the development of a coherent and secure IIoT framework and shedding light on their significance in the context of IIoT system design [61].
- ManufacturingUnit to Machinery: A composition relationship, as each ManufacturingUnit contains multiple pieces of Machinery. This represents that if a ManufacturingUnit ceases to exist, its associated Machinery would no longer be relevant.
- Machinery to Sensor: An aggregation relationship, indicating that Machinery can have multiple Sensors attached to it, but these Sensors can exist independently of the Machinery.
- IIoTDevice to Sensor and Machinery: A generalization relationship, where IIoTDevice is a parent class and both Sensor and Machinery are child classes that inherit from IIoTDevice. This denotes that both Sensors and Machinery can be considered IIoTDevices with additional functionalities.
- DataManagementSystem to IIoTDevice: A direct association, indicating that the DataManagementSystem collects and processes data from multiple IIoTDevices. This relationship signifies data flow from IIoTDevices to the DataManagementSystem.
- SecurityProtocol to IIoTDevice and DataManagementSystem: A dependency relationship, as both IIoTDevices and the DataManagementSystem rely on SecurityProtocol for secure operation. This relationship highlights the importance of security measures for the integrity and safety of the system.
- MaintenanceSchedule to Machinery: Another direct association, where the MaintenanceSchedule manages maintenance activities for Machinery. This indicates that each piece of Machinery has a corresponding set of maintenance schedules.
Figure 2 depicts the structure, relationships, and identified weaknesses within S.C.A.I.’s manufacturing environment, including the relationships between categories using a UML class diagram. This diagram displays the relationships between various categories such as composition, aggregation, and dependency. It also includes annotations describing the nature of these relationships, for instance, “Contains”, “Has”, “Collects data from”, “Secures”, and “Schedules for”. This diagram aims to clarify how different components of the manufacturing environment are interconnected and dependent on each other. By doing so, it highlights potential areas for improving and strengthening security and efficiency within the system.
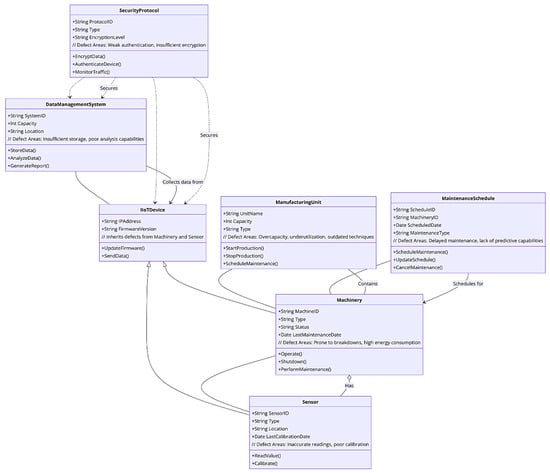
Figure 2.
The S.C.A.I. manufacturing environment.
4.5. Challenges
- Heterogeneity of Devices: The factory utilizes a wide range of machines and sensors from different manufacturers, each with its own set of protocols and interfaces. This diversity complicates the integration of a cohesive IIoT system [53]. For example, integration efforts can consume up to 30% of the total project time due to incompatibility issues between devices. In a typical IIoT project costing USD 500,000, this translates to an additional USD 150,000 in expenses solely for integration efforts.
- Data Management and Analysis: Capturing, processing, and analyzing data from numerous sources in real-time demand robust and scalable data management solutions [54]. For instance, an automotive manufacturing plant generates approximately 2 terabytes of data daily from various sensors and machines. Without efficient data management, up to 20% of this data could be lost or go unanalyzed, leading to missed insights and potential operational inefficiencies. This data loss could equate to a financial impact of USD 200,000 annually due to suboptimal decision-making.
- Security and Authentication: Ensuring the security of IIoT devices and safeguarding sensitive data from cyber threats is paramount [55]. A single cyberattack can result in downtime costing up to USD 100,000 per hour in a manufacturing setting. In 2020, the average cost of a data breach was USD 3.86 million, which underscores the importance of robust authentication mechanisms to prevent unauthorized access and protect sensitive data.
- Scalability: As the factory expands its IIoT infrastructure, the system must be scalable to accommodate new devices and technologies without compromising performance [56]. A lack of scalability can lead to performance bottlenecks, where system efficiency drops by 15–20% as new devices are added. This inefficiency can cause production delays, potentially costing the factory USD 50,000 daily in lost productivity during peak scaling periods.
- Interoperability: Ensuring seamless communication and interoperability between diverse systems and technologies is critical for achieving operational efficiency and flexibility [57]. For example, a project has a budget of USD 1 million but faces significant delays due to interoperability issues. These delays could extend project timelines by 6 to 12 months. As a result, there can be cost overruns of up to USD 400,000, which will have a significant impact on the project’s return on investment.
4.6. Solutions
To address these challenges, the following patterns and technologies could be implemented:
- Device Gateway Pattern: Acts as an intermediary that simplifies communication between heterogeneous devices and the IIoT platform. It can translate different protocols and manage connections efficiently [62].
- Data Acquisition and Edge Computing: By processing data at the edge, closer to where it is generated, S.C.A.I. can reduce latency, decrease bandwidth usage, and improve response times. Edge computing devices can pre-process data before sending it to the cloud for further analysis [63].
- Scalability with Modular Architecture: Adopting a modular architecture for the IIoT system allows for easier scalability. This approach enables the factory to add, remove, or upgrade modules without disrupting the entire system [64].
- Security with Authentication: Implementing robust authentication protocols and encryption standards ensures secure communication between devices and protects against unauthorized access [65].
- Predictive Maintenance with Analytics: Utilizing advanced analytics and machine learning algorithms for predictive maintenance can significantly reduce downtime and maintenance costs by forecasting equipment failures before they occur [66].
By systematically addressing these challenges with targeted solutions, S.C.A.I. can enhance its IIoT capabilities, streamline its operations, and secure a competitive advantage in the rapidly evolving automotive industry.
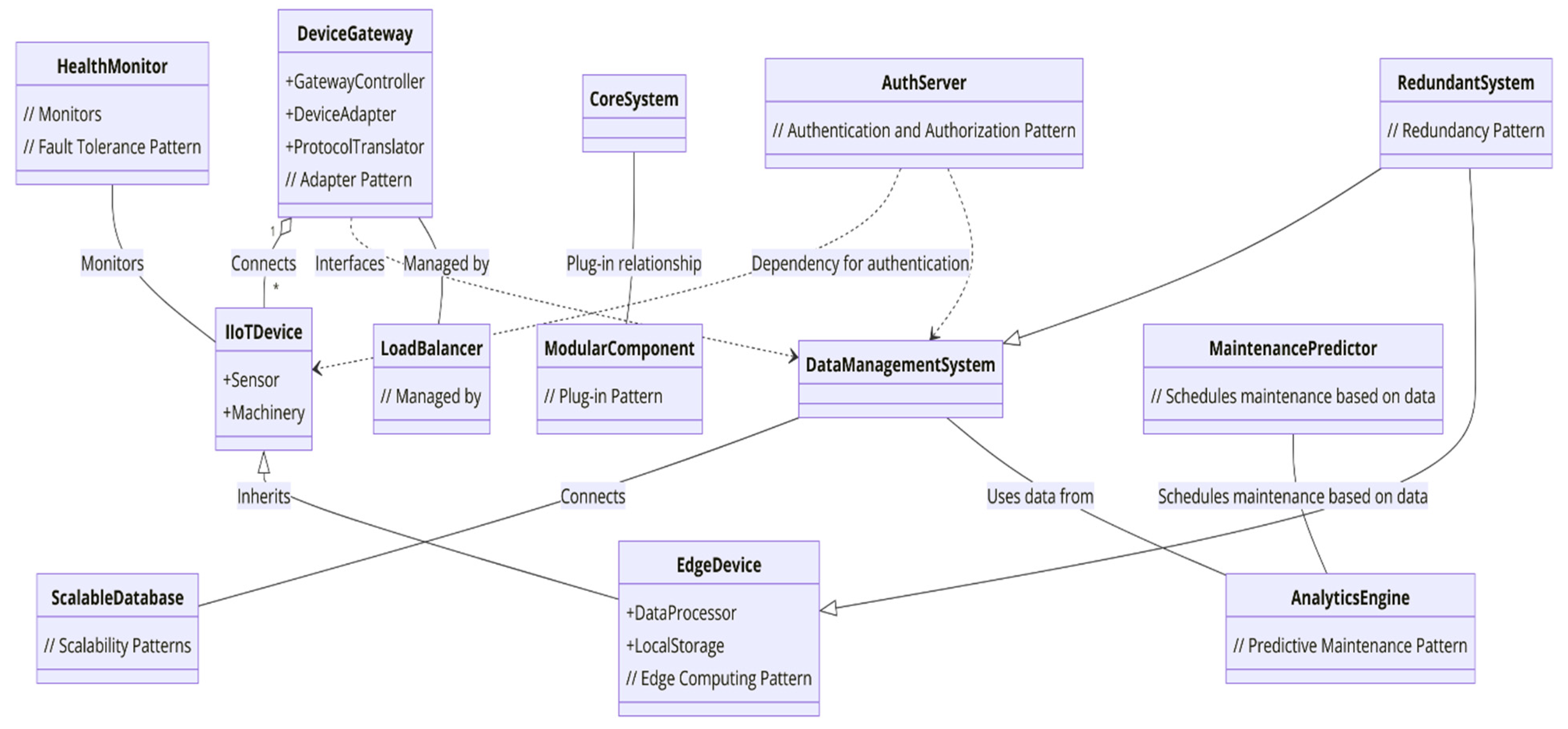
4.7. Developing a Comprehensive UML Conceptual Diagram for IIoT Solutions to Overcome the Challenges in S.C.A.I.
4.7.1. Components and Patterns
- Device Gateway:Role: Facilitates communication between heterogeneous devices and the central IIoT system.Components: GatewayController, DeviceAdapter, ProtocolTranslator.Relationships: Connects directly to IIoTDevices (Sensor, Machinery) and interfaces with the DataManagementSystem. Use aggregation between GatewayController and DeviceAdapter to indicate that multiple adapters can be managed by a single controller.
- Data Acquisition and Edge Computing:Role: Processes data at the source to reduce latency and bandwidth usage.Components: EdgeDevice (inherits IIoTDevices), DataProcessor, LocalStorage.Relationships: EdgeDevice connects to Sensors and Machinery, sending processed data to the DataManagementSystem. Composition between EdgeDevice and DataProcessor to represent that each EdgeDevice contains a DataProcessor.
- Modular Architecture:Role: Ensures system scalability and flexibility.Components: CoreSystem, ModularComponent.Relationships: Use a plug-in relationship between CoreSystem and ModularComponent to represent the dynamic addition/removal of modules.
- Security—Authentication:Role: Protects data and devices from unauthorized access.Components: AuthServer, SecurityProtocol (updated to include AuthenticationMechanism).Relationships: Dependency from IIoTDevices and DataManagementSystem on AuthServer to signify the need for authentication before access.
- Scalability:Role: Allows the system to handle growth in data and devices.Components: ScalableDatabase, LoadBalancer.Relationships: ScalableDatabase is connected to DataManagementSystem, indicating data storage solutions that can expand. LoadBalancer shows association with GatewayController to manage incoming device connections.
- Analytics and Predictive Maintenance:Role: Uses data analysis for forecasting and decision-making.Components: AnalyticsEngine, MaintenancePredictor.Relationships: AnalyticsEngine connects to DataManagementSystem for data analysis. MaintenancePredictor uses data from AnalyticsEngine to schedule maintenance (MaintenanceSchedule).
- Fault Tolerance:Role: Ensures system reliability and continuous operation.Components: RedundantSystem, HealthMonitor.Relationships: RedundantSystem mirrors critical components like DataManagementSystem and EdgeDevice. HealthMonitor is associated with all IIoTDevices and critical system components to monitor system health.
4.7.2. Integration with Pre-Solution State
Figure 3 shows a UML class diagram illustrating the integration of IIoT solutions into a S.C.A.I. manufacturing environment. Before IIoT integration, we have components like manufacturing unit, machinery, and basic sensors as existing elements without advanced IIoT capabilities. But after IIoT integration, the system consists of the addition of IIoT solutions and their connections to pre-existing components. This demonstrates the transformation towards a more efficient, secure, and scalable system. This structured approach to creating a UML diagram with IIoT integration will clearly show the transformation of S.C.A.I.’s manufacturing processes, highlighting the strategic implementation of various patterns to solve the outlined challenges. In Figure 3, the diagram illustrates the role of each component within the IIoT integration framework, highlighting how the pattern addresses the challenges identified using specific design patterns. We provide a clear view of the strategic approaches used to enhance efficiency, safety, and scalability in manufacturing.
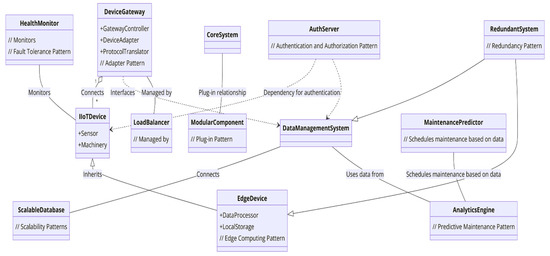
Figure 3.
Integration of IIoT solutions into the S.C.A.I. manufacturing environment.
This UML diagram outlines the transition of the State Company for Automotive Industry (S.C.A.I.) towards integrating IIoT technologies into its manufacturing processes. It identifies challenges such as device heterogeneity, data management, security, scalability, and interoperability. To overcome these, it suggests solutions like the device gateway pattern, data acquisition and edge computing, modular architecture, security with authentication, and predictive maintenance with analytics. The conclusion emphasizes the strategic implementation of these IIoT solutions to enhance efficiency, security, and scalability in S.C.A.I.’s manufacturing operations, showcasing a transformation towards a more modern, efficient, and competitive manufacturing environment.
The application of this pattern language at S.C.A.I. demonstrates its effectiveness in tackling the diverse challenges of integrating IIoT technologies in an industrial setting. The case study not only shows the practical benefits of each pattern but also highlights the cohesive operation of the system when these patterns are applied in concert.
5. Validation of the Pattern Language Using the Delphi Process Theory
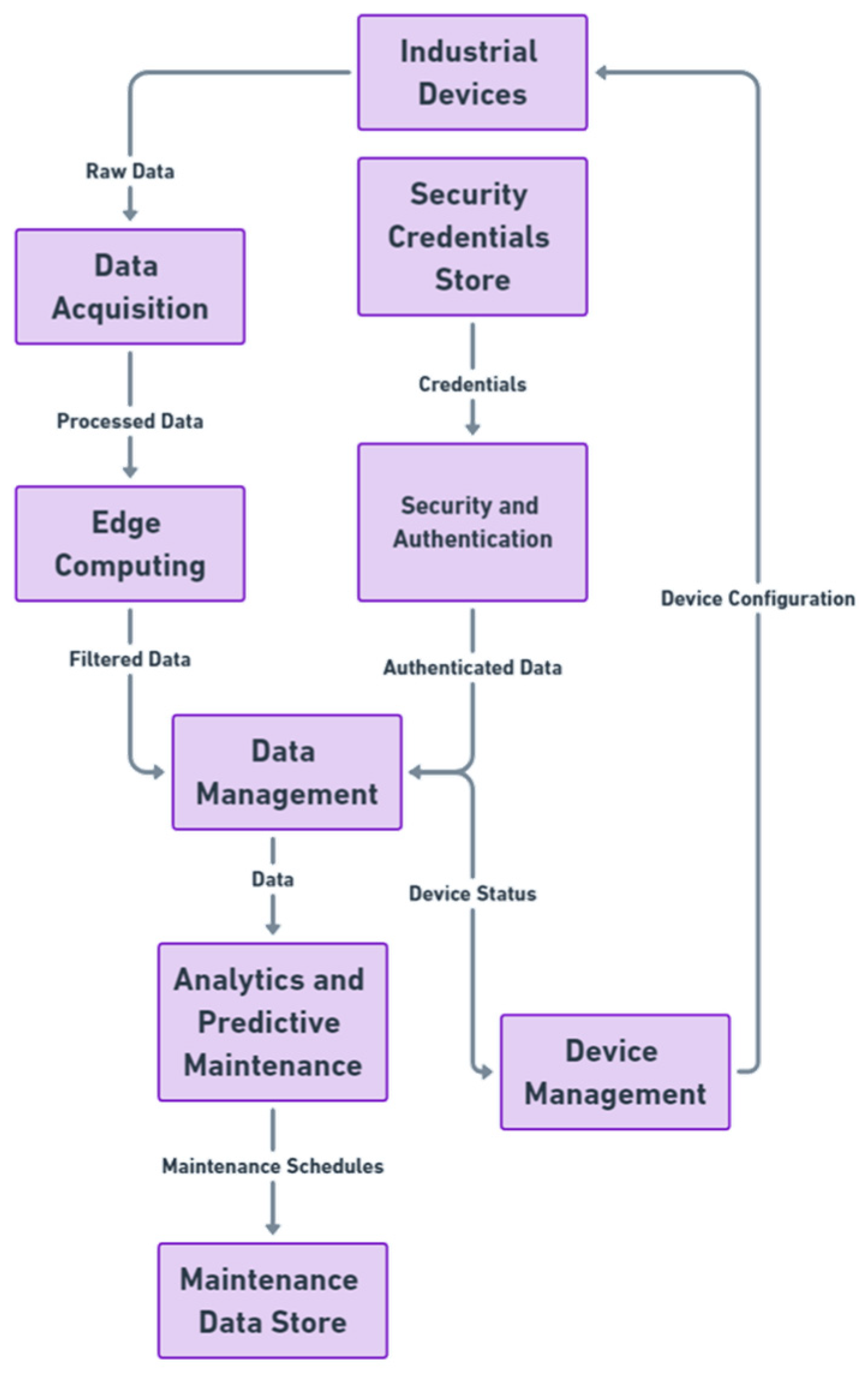
The validation of the developed pattern language was performed using the Delphi process theory, a structured communication technique originally developed as a systematic, interactive forecasting method that relies on a panel of experts. The experts answer questionnaires in two or more rounds. After each round, a facilitator provides an anonymous summary of the experts’ forecasts from the previous round as well as the reasons they provided for their judgments. Thus, experts are encouraged to revise their earlier answers in light of the replies of other members of their panel. It is believed that during this process the range of the answers will decrease and the group will converge towards the “correct” answer. Figure 4 shows a data flow diagram (DFD) summarizing the key components and processes of IIoT in S.C.A.I.
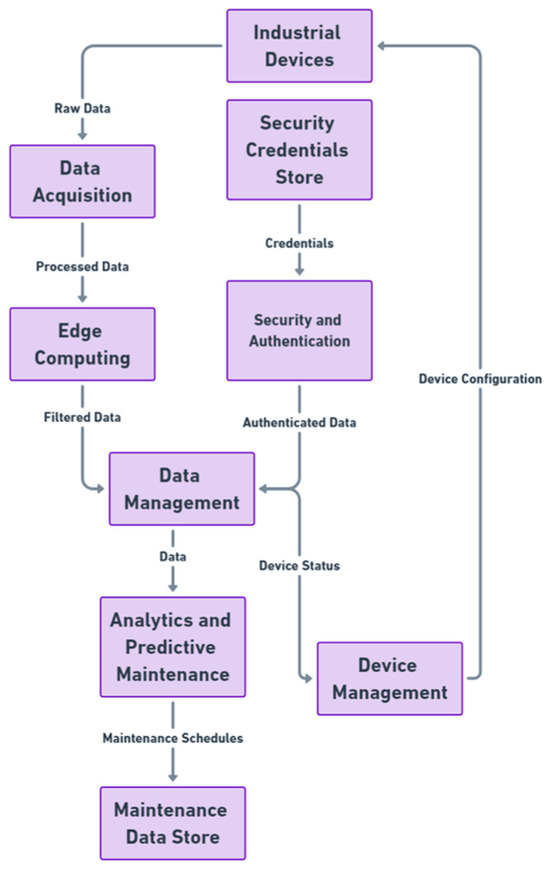
Figure 4.
The processes of IIoT in S.C.A.I.
5.1. Implementation of Delphi Process
- Expert Selection: A panel of experts in IIoT, industrial systems design, and pattern language development was assembled. These experts were selected based on their knowledge, experience, and contribution to the fields relevant to the project. The study limited the number of experts to nine due to communication limitations, access to information, scheduling problems, confidentiality issues, and time constraints. The Delphi approach is enhanced by the idea of comparison with a single participant; “n + 1” participants achieve more effective results [67]. Data analysis involves using computer-based qualitative analysis programs or manual analysis. According to John W. Creswell [68], analyzing qualitative data from a few pages can be performed manually instead of utilizing computer programs. Therefore, we manually analyzed the qualitative data obtained from nine interviewees to determine their perception of the study model’s suitability. Table 4 shows the summary of interviewees’ profiles.
 Table 4. IIoT design patterns and relationships.
Table 4. IIoT design patterns and relationships. - First Round: The initial questionnaire was distributed to the experts, detailing the pattern language and its application in the S.C.A.I. case study. Experts were asked to evaluate the adequacy, relevance, and potential effectiveness of each pattern in addressing the identified challenges.
- Feedback Compilation: Responses were collected and summarized to identify common agreements and disagreements. Key points of contention or uncertainty were highlighted for further exploration.
- Second Round: The summary and specific feedback from the first round were sent back to the experts, along with additional questions that aimed to delve deeper into the issues raised. Experts were encouraged to reconsider their initial assessments and provide further insights based on the collective feedback.
- Final Analysis: The responses from the second round were analyzed to assess the consensus among the experts. Adjustments to the pattern language were proposed based on areas where significant agreement or insightful suggestions were noted.
5.2. Results of the Delphi Process
The Delphi process led to several refinements in the pattern language, enhancing clarity, applicability, and the robust integration of the patterns within IIoT systems. Experts largely concurred on the strategic alignment of the patterns with the operational goals of IIoT systems, particularly in heterogeneous environments like S.C.A.I. The iterative rounds of the Delphi process ensured that the final pattern language was not only theoretically sound but also practically viable and tailored to the nuances of real-world industrial applications. Table 5 and Table 6 depict the opinions of nine experts on key factors that drive the Iraqi industry organizations for IoT systems.

Table 5.
The summary of interviewees’ profiles.

Table 6.
Results of the interviews.
5.2.1. System Validation
The validation process demonstrated the strength and flexibility of the pattern language in addressing diverse and complex challenges in IIoT systems. The comprehensive evaluation result revealed a high level of agreement among experts. For the proposed model, the approval rate was 87.11%. This rate indicates very good consistency among the nine experts. The table shows that we found that 87.87% of experts agreed about the individual factors and elements and how they can affect the adoption of IoT systems in Iraqi industrial providers. By looking at each item, it was found that 90.90% of them were in agreement regarding the items related to technology and how it affects the adoption of IoT systems. The involvement of a panel of domain experts ensured that the pattern language was robust, with comprehensive industry insights driving its development—the successful application and validation at S.C.A.I. provide a strong foundation for recommending this pattern language as a best practice model in similar industrial contexts.
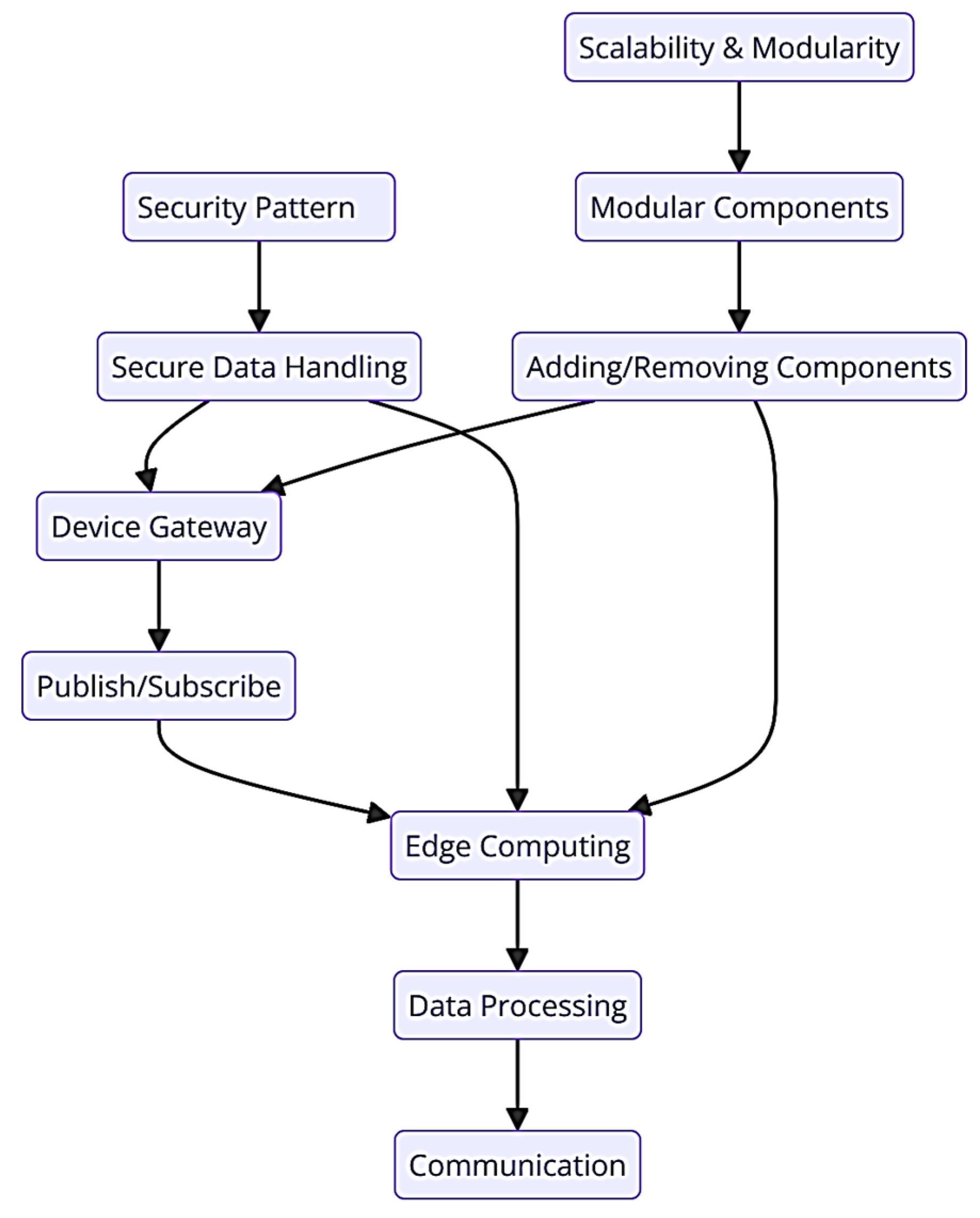
The Delphi process provided a structured approach to expert validation, ensuring that the pattern language was rigorously evaluated through iterative rounds of feedback. The process confirmed that the patterns were aligned with industry needs and were robust enough to address the complex challenges of IIoT system design. The development of a comprehensive system map further supported this validation, offering a detailed representation of how the patterns functioned within the S.C.A.I. environment. Figure 5 shows the used system map in the Delphi process.
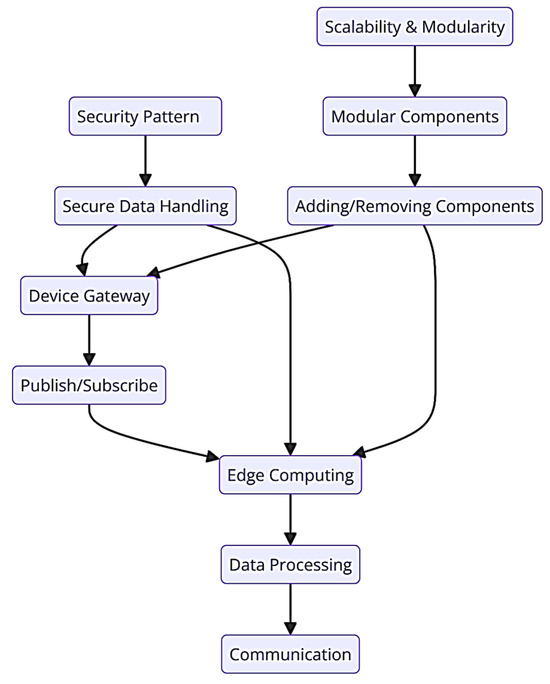
Figure 5.
The system map.
The system map illustrates the following:
- Interaction of Patterns: Shows how the device gateway, publish/subscribe, and edge computing patterns interconnect and facilitate seamless communication and data processing across the system.
- Security Integration: Highlights the implementation of the security pattern across various layers of the IIoT system, ensuring data protection and secure device interaction.
- Scalability and Modularity: Demonstrates how the system can be scaled and modified by adding or removing components within the modular architecture without disrupting operations.
The validation process, supported by the system map, provides a robust framework for understanding the practical application and benefits of the pattern language. It ensures that the patterns are not only theoretically sound but also effectively address the real-world challenges faced by IIoT systems.
The pattern language presented for S.C.A.I. stands out due to its practical applicability and detailed approach to addressing specific IIoT challenges. When compared to broader frameworks like RAMI 4.0 (Reference Architectural Model Industry 4.0) [69,70] and IIRA (Industrial Internet Reference Architecture) [58], this pattern language offers concrete solutions that can be mapped onto these frameworks to enhance specific aspects of IIoT implementations. This integration ensures that the theoretical benefits of RAMI 4.0 and IIRA are realized through practical, pattern-based solutions, making the pattern language a valuable tool in the IIoT landscape [71].
5.2.2. Results and Discussion
This section systematically presents the results of applying the developed pattern language in the context of the State Company for Automotive Industry (S.C.A.I.) and discusses their implications for IIoT system design.
- ▪
- Enhanced System Interoperability
The application of the device gateway and publish/subscribe patterns demonstrated a significant improvement in system interoperability. Specifically, the device gateway pattern facilitated seamless communication between devices operating on different protocols, thereby resolving one of the most critical challenges in IIoT systems—heterogeneous device integration. The publish/subscribe pattern further enhanced this by enabling asynchronous communication between devices, reducing direct dependencies, and allowing for more scalable and flexible system architecture.
The increased interoperability not only allowed for more efficient data exchange between devices but also improved overall system responsiveness. This finding underscores the importance of communication patterns in enhancing the interoperability of IIoT systems, which is essential for real-time data processing and decision-making.
- ▪
- Improved Operational Efficiency
Operational efficiency was markedly improved through the implementation of edge computing and predictive maintenance patterns. By processing data closer to the source, the edge computing pattern reduced latency and bandwidth usage, leading to faster decision-making processes. The predictive maintenance pattern, which employed advanced analytics to anticipate equipment failures, significantly reduced unplanned downtime by enabling proactive maintenance scheduling.
The reduction in downtime and the ability to process data locally resulted in a more efficient production process, demonstrating the critical role of edge computing in IIoT environments. This efficiency gain also highlights the practical benefits of integrating predictive maintenance within industrial settings, emphasizing the value of real-time analytics in maintaining operational continuity.
- ▪
- Robust System Security
The security (authentication) pattern was crucial in ensuring the protection of the IIoT system from cyber threats. This pattern introduced robust authentication mechanisms and encryption standards, which safeguarded data integrity and system operations against unauthorized access. As a result, there was a noticeable decrease in security breaches, contributing to a more secure operational environment.
The successful implementation of the security pattern highlights the necessity of incorporating strong security measures in IIoT systems. As IIoT environments are inherently vulnerable due to their connected nature, robust security protocols are indispensable in preventing potential disruptions and ensuring data confidentiality and system reliability.
- ▪
- Scalable and Flexible System Architecture
The adoption of the scalability and modular architecture patterns facilitated the system’s ability to adapt to varying operational demands without requiring extensive reconfiguration. These patterns ensured that as new devices and data streams were added, the system could scale accordingly while maintaining performance. The modular approach allowed for the independent development, testing, and deployment of system components, which streamlined the integration process.
This scalable and modular design approach proves to be vital in ensuring the longevity and adaptability of IIoT systems. As industrial environments continue to evolve, the ability to scale and modify system components without disrupting ongoing operations is crucial for maintaining competitive advantage.
- ▪
- Comprehensive System Validation
To reinforce the findings, the validation of the pattern language was carried out using the Delphi process (detailed in Section 5.2.1). This method ensured that the proposed patterns were not only theoretically sound but also practically viable. A system map (Figure 3) was developed to visually represent the integration and interaction of the patterns within the S.C.A.I. environment, providing a clear and comprehensive overview of the system’s architecture post-implementation.
The use of a system map to validate the pattern language in a real-world scenario strengthens the argument for its applicability and effectiveness. This visual representation also aids in understanding how the patterns interact and support each other, contributing to a cohesive and well-integrated IIoT system.
6. Conclusions
This research presented a comprehensive pattern language designed to tackle the complexities of integrating heterogeneous devices within IIoT systems. The structured approach of using interrelated patterns not only addressed the operational challenges but also enhanced the overall system architecture to be more robust, scalable, and secure. We conducted the Delphi process to validate the proposed pattern language and engage industry experts to refine and optimize the framework for practical application. While the Delphi process provided valuable insights and consensus from experts, it is not without limitations. The reliance on a small, specialized group of experts may introduce biases, and the iterative nature of the process, while thorough, can be time-consuming. Additionally, the development of the pattern language, although comprehensive, may require further adaptation when applied to different industrial sectors. Future research should focus on expanding the expert panel and exploring the application of the pattern language in diverse environments to enhance its generalizability and robustness.
The successful implementation and validation at the State Company for Automotive Industry (S.C.A.I.) underscore the pattern language’s relevance and effectiveness. The Delphi method facilitated the collection of diverse expert opinions, leading to the optimization of the framework for practical application in a real-world industrial setting. This rigorous validation process ensured that the pattern language was not only theoretically sound but also tailored to the specific needs and challenges of IIoT environments like S.C.A.I.
Future research could explore the extension of this pattern language to other industrial sectors and consider the integration of emerging technologies like artificial intelligence and machine learning to enhance the predictive capabilities and automation within IIoT systems. Continual refinement and adaptation of the pattern language to accommodate new challenges and technologies will be crucial to maintaining its applicability and effectiveness in the dynamic landscape of industrial IoT. This study provides a valuable framework for industrial entities looking to harness the power of IIoT while mitigating the inherent challenges of technological heterogeneity and system integration.
Author Contributions
Conceptualization, M.S.; methodology, M.S. and B.Z.; validation, H.H.A.; formal analysis, H.H.A.; investigation, H.H.A.; data curation, H.H.A.; writing—original draft, H.H.A.; writing—review & editing, M.S.; visualization, H.H.A.; supervision, B.Z. and S.K.-R.; project administration, M.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jain, S.; Chandrasekaran, K. Industrial Automation Using Internet of Things. In Advances in Information Security, Privacy, and Ethics; IGI Global: Hershey, PA, USA, 2020; pp. 28–64. [Google Scholar] [CrossRef]
- Peeples, M.M.; Iyer, A.K.; Cohen, J.L. Integration of a Mobile-Integrated Therapy with Electronic Health Records: Lessons Learned. J. Diabetes Sci. Technol. 2013, 7, 602–611. [Google Scholar] [CrossRef]
- Lytra, L.; Sobernig, S.; Tran, H.; Zdun, U. A pattern language for service-based platform integration and adaptation. In Proceedings of the EuroPLoP 201217th European Conference on Pattern Languages of Programs; Irsee, Germany, 11–15 July 2012, ACM: New York, NY, USA, 2012. [Google Scholar] [CrossRef]
- Yi, K.J.; Jeong, Y.-S. Smart factory: Security issues, challenges, and solutions. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 4625–4638. [Google Scholar] [CrossRef]
- Sen, S.; Song, L. An IIoT-Based Networked Industrial Control System Architecture to Secure Industrial Applications. In Proceedings of the 2021 IEEE Industrial Electronics and Applications Conference (IEACon), Penang, Malaysia, 22–23 November 2021; pp. 280–285. [Google Scholar] [CrossRef]
- Rouhi, A.; Zamani, B. Towards a formal model of patterns and pattern languages. Inf. Softw. Technol. 2016, 79, 1–16. [Google Scholar] [CrossRef]
- Noaman, M.; Khan, M.S.; Abrar, M.F.; Ali, S.; Alvi, A.; Saleem, M.A. Challenges in Integration of Heterogeneous Internet of Things. Sci. Program. 2022, 2022, 8626882. [Google Scholar] [CrossRef]
- Price, J. Christopher Alexander’s pattern language. IEEE Trans. Prof. Commun. 1999, 42, 117–122. [Google Scholar] [CrossRef]
- Wiles, J.; Watson, J. Patterns in Complex Systems Modeling. In Intelligent Data Engineering and Automated Learning—IDEAL 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 532–539. [Google Scholar] [CrossRef]
- Hegedűs, P.; Bán, D.; Ferenc, R.; Gyimóthy, T. Myth or Reality? Analyzing the Effect of Design Patterns on Software Maintainability. In Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2012; pp. 138–145. [Google Scholar] [CrossRef]
- Huston, B. The effects of design pattern application on metric scores. J. Syst. Softw. 2001, 58, 261–269. [Google Scholar] [CrossRef]
- Bayley, I.; Zhu, H. Formal specification of the variants and behavioural features of design patterns. J. Syst. Softw. 2010, 83, 209–221. [Google Scholar] [CrossRef]
- Liu, Y.; Lu, Q.; Yu, G.; Paik, H.-Y.; Zhu, L. A Pattern-Oriented Reference Architecture for Governance-Driven Blockchain Systems. In Proceedings of the 2023 IEEE 20th International Conference on Software Architecture (ICSA), L’Aquila, Italy, 13–17 March 2023. [Google Scholar]
- Rouhi, A.; Zamani, B. A model-based framework for automatic generation of a pattern language verifier. Softw. Pract. Exp. 2017, 47, 1945–1980. [Google Scholar] [CrossRef]
- Schmidt, D.C.; Cleeland, C. Applying patterns to develop extensible ORB middleware. IEEE Commun. Mag. 1999, 37, 54–63. [Google Scholar] [CrossRef]
- Papoutsakis, M.; Fysarakis, K.; Spanoudakis, G.; Ioannidis, S.; Koloutsou, K. Towards a Collection of Security and Privacy Patterns. Appl. Sci. 2021, 11, 1396. [Google Scholar] [CrossRef]
- Zhang, C.; Budgen, D. What Do We Know about the Effectiveness of Software Design Patterns? IEEE Trans. Softw. Eng. 2012, 38, 1213–1231. [Google Scholar] [CrossRef]
- Malakuti, S.; Grüner, S. Architectural aspects of digital twins in IIoT systems. In Proceedings of the ECSA ’18: 12th European Conference on Software Architecture: Companion Proceedings, Madrid, Spain, 24–28 September 2018; ACM: New York, NY, USA, 2018. [Google Scholar] [CrossRef]
- Zhou, J.; He, P. Research on Data Acquistion System of Flow Workshop Based on IIoT. In Proceedings of the 2020 IEEE 3rd International Conference of Safe Production and Informatization (IICSPI), Chongqing, China, 28–30 November 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar] [CrossRef]
- Pivoto, D.G.S.; de Almeida, L.F.F.; da Rosa Righi, R.; Rodrigues, J.J.P.C.; Lugli, A.B.; Alberti, A.M. Cyber-physical systems architectures for industrial internet of things applications in Industry 4.0: A literature review. J. Manuf. Syst. 2021, 58, 176–192. [Google Scholar] [CrossRef]
- Dobaj, J.; Schuss, M.; Krisper, M.; Boano, C.A.; Macher, G. Dependable mesh networking patterns. In Proceedings of the EuroPLoP ’19: 24th European Conference on Pattern Languages of Programs, Irsee, Germany, 3–7 July 2019; ACM: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Song, S.; Gao, Y.; Wang, C.; Zhu, X.; Wang, J.; Philip, S.Y. Matching Heterogeneous Events with Patterns. IEEE Trans. Knowl. Data Eng. 2017, 29, 1695–1708. [Google Scholar] [CrossRef]
- Kacem, M.H.; Tounsi, I.; Khalfi, N. Modeling and Specification of Bootstrapping and Registration Design Patterns for IoT Applications. In The Impact of Digital Technologies on Public Health in Developed and Developing Countries; Springer International Publishing: Cham, Switzerland, 2020; pp. 55–66. [Google Scholar] [CrossRef]
- Jin, H. Integration Mechanism of Heterogeneous Foreign Language Education Resources Based on Time Series Analysis in IIoT. Mob. Inf. Syst. 2022, 2022, 5309556. [Google Scholar] [CrossRef]
- Xiong, H.; Wu, Y.; Jin, C.; Kumari, S. Efficient and Privacy-Preserving Authentication Protocol for Heterogeneous Systems in IIoT. IEEE Internet Things J. 2020, 7, 11713–11724. [Google Scholar] [CrossRef]
- Petroulakis, N.E.; Lakka, E.; Sakic, E.; Kulkarni, V.; Fysarakis, K.; Somarakis, I.; Serra, J.; Sanabria-Russo, L.; Pau, D.; Falchetto, M.; et al. SEMIoTICS Architectural Framework: End-to-end Security, Connectivity and Interoperability for Industrial IoT. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; IEEE: Piscataway, NJ, USA, 2019. [Google Scholar] [CrossRef]
- Wang, J.; Jiang, C.; Zhang, K.; Hou, X.; Ren, Y.; Qian, Y. Distributed Q-Learning Aided Heterogeneous Network Association for Energy-Efficient IIoT. IEEE Trans. Ind. Inform. 2020, 16, 2756–2764. [Google Scholar] [CrossRef]
- Sengupta, S.; Chen, Y. Spectral clustering in heterogeneous networks. Stat. Sin. 2015, 25, 1081–1106. [Google Scholar] [CrossRef]
- Narayanan, R.; Murthy, C.S.R. A Probabilistic Framework for Protocol Conversions in IIoT Networks with Heterogeneous Gateways. IEEE Commun. Lett. 2017, 21, 2456–2459. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, X.X.; Zhang, L. Tree pattern matching in heterogeneous fuzzy XML databases. Knowl.-Based Syst. 2017, 122, 119–130. [Google Scholar] [CrossRef]
- Arcaini, P.; Mirandola, R.; Riccobene, E.; Scandurra, P. MSL: A pattern language for engineering self-adaptive systems. J. Syst. Softw. 2020, 164, 110558. [Google Scholar] [CrossRef]
- Jaloudi, S. Communication Protocols of an Industrial Internet of Things Environment: A Comparative Study. Future Internet 2019, 11, 66. [Google Scholar] [CrossRef]
- Hamood, M.; Albaseer, A.; Abdallah, M.; Al-Fuqaha, A. Clustered and Multi-Tasked Federated Distillation for Heterogeneous and Resource Constrained Industrial IoT Applications. IEEE Internet Things Mag. 2023, 6, 64–69. [Google Scholar] [CrossRef]
- Chand, S.; Pandey, S.K.; Horkoff, J.; Staron, M.; Ochodek, M.; Durisic, D. Comparing Word-Based and AST-Based Models for Design Pattern Recognition. In Proceedings of the PROMISE ’23: 19th International Conference on Predictive Models and Data Analytics in Software Engineering, San Francisco, CA, USA, 8 December 2023; ACM: New York, NY, USA, 2023. [Google Scholar] [CrossRef]
- Yu, D.; Zhang, P.; Yang, J.; Chen, Z.; Liu, C.; Chen, J. Efficiently detecting structural design pattern instances based on ordered sequences. J. Syst. Softw. 2018, 142, 35–56. [Google Scholar] [CrossRef]
- Orłowski, C.; Ziółkowski, A.; Orłowski, A.; Kapłański, P.; Sitek, T.; Pokrzywnicki, W. Ontology of the Design Pattern Language for Smart Cities Systems. In Transactions on Computational Collective Intelligence XXV; Springer: Berlin/Heidelberg, Germany, 2016; pp. 76–100. [Google Scholar] [CrossRef]
- Elaasar, M.; Briand, L.C.; Labiche, Y. VPML: An approach to detect design patterns of MOF-based modeling languages. Softw. Syst. Model. 2013, 14, 735–764. [Google Scholar] [CrossRef]
- Zamani, B.; Butler, G. Pattern Language Verification in Model Driven Design. Inf. Sci. 2013, 237, 343–355. [Google Scholar] [CrossRef]
- Rana, B.; Singh, Y.; Singh, P.K. A systematic survey on internet of things: Energy efficiency and interoperability perspective. Trans. Emerg. Telecommun. Technol. 2020, 32, e4166. [Google Scholar] [CrossRef]
- Iqbal, M.A.; Hussain, S.; Xing, H.; Imran, M. Enabling the Internet of Things: Fundamentals, Design, and Applications; Wiley: Hoboken, NJ, USA, 2020. [Google Scholar] [CrossRef]
- Perera, C.; Liu, C.H.; Jayawardena, S. The Emerging Internet of Things Marketplace From an Industrial Perspective: A Survey. IEEE Trans. Emerg. Top. Comput. 2015, 3, 585–598. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Fortino, G.; Trunfio, P. Internet of Things Based on Smart Objects; Springer International Publishing: Cham, Switzerland, 2014. [Google Scholar] [CrossRef]
- Reinfurt, L.; Breitenbücher, U.; Falkenthal, M.; Leymann, F.; Riegg, A. Internet of Things Patterns for Device Bootstrapping and Registration. In Proceedings of the EuroPLoP ’17: 22nd European Conference on Pattern Languages of Programs, Irsee, Germany, 12–16 July 2017; ACM: New York, NY, USA, 2017. [Google Scholar] [CrossRef]
- Li, F.; Voegler, M.; Claessens, M.; Dustdar, S. Efficient and Scalable IoT Service Delivery on Cloud. In Proceedings of the 2013 IEEE Sixth International Conference on Cloud Computing, Santa Clara, CA, USA, 28 June–3 July 2013; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar] [CrossRef]
- Sethi, P.; Sarangi, S.R. Internet of Things: Architectures, Protocols, and Applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef]
- Khan, A.R.; Kashif, M.; Jhaveri, R.H.; Raut, R.; Saba, T.; Bahaj, S.A. Deep Learning for Intrusion Detection and Security of Internet of Things (IoT): Current Analysis, Challenges, and Possible Solutions. Secur. Commun. Netw. 2022, 2022, 4016073. [Google Scholar] [CrossRef]
- Cao, Q.; Zanni-Merk, C.; Samet, A.; Reich, C.; De Beuvron FD, B.; Beckmann, A.; Giannetti, C. KSPMI: A Knowledge-based System for Predictive Maintenance in Industry 4.0. Robot. Comput.-Integr. Manuf. 2022, 74, 102281. [Google Scholar] [CrossRef]
- Smaali, S.; Benbessem, R.; Touati, H.M.N. A Fault Tolerance and Recovery Formal Model for IoT Systems. Int. J. Organ. Collect. Intell. 2022, 12, 1–24. [Google Scholar] [CrossRef]
- Alexander, C.; Ishikawa, S.; Silverstein, M. A Pattern Language: Towns, Buildings, Construction; Center for Environmental Structure Series; Center for Environmental Structure: Berkeley, CA, USA, 1977. [Google Scholar]
- Gamma, E.; Helm, R.; Johnson, R.; Vlissides, J. Design Patterns: Elements of Reusable Object-Oriented Software; Pearson Deutschland GmbH: München, Germany, 1995. [Google Scholar]
- Caiza, J.C.; Martín, Y.-S.; Del Alamo, J.M.; Guamán, D.S. Organizing Design Patterns for Privacy: A Taxonomy of Types of Relationships. In Proceedings of the EuroPLoP ’17: 22nd European Conference on Pattern Languages of Programs, Irsee, Germany, 12–16 July 2017; ACM: New York, NY, USA, 2017. [Google Scholar] [CrossRef]
- Noble, J. Classifying relationships between object-oriented design patterns. In Proceedings of the 1998 Australian Software Engineering Conference (Cat. No.98EX233), ASWEC-98, Adelaide, SA, Australia, 9–13 November 1998; IEEE Computer Society: Washington, DC, USA, 1998. [Google Scholar] [CrossRef]
- Zimmer, W. Relationships between design patterns. Pattern Lang. Program Des. 1995, 1, 345–364. [Google Scholar]
- Hamdan, S.; Ayyash, M.; Almajali, S. Edge-Computing Architectures for Internet of Things Applications: A Survey. Sensors 2020, 20, 6441. [Google Scholar] [CrossRef] [PubMed]
- Xu, X.; Bandara, H.M.N.D.; Lu, Q.; Weber, I.; Bass, L.; Zhu, L. A Decision Model for Choosing Patterns in Blockchain-Based Applications. In Proceedings of the 2021 IEEE 18th International Conference on Software Architecture (ICSA), Stuttgart, Germany, 22–26 March 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Ungurean, I.; Gaitan, N. A Dynamic IIoT Framework Based on the Publish–Subscribe Paradigm. Sensors 2023, 23, 9829. [Google Scholar] [CrossRef] [PubMed]
- AL-Munim, M.A.H.; Abdul Hameed, M.M. Investment Trends for Iraqi Industries in Terms of Clean Production (selected model). J. Econ. Adm. Sci. 2021, 27, 155–169. [Google Scholar] [CrossRef]
- Iraqi Ministry of Industry and Minerals. Automotive Industry. Available online: https://scai.industry.gov.iq/CMS.php?CMS_P=2 (accessed on 26 February 2024).
- Lu, X.; Baraldi, P.; Zio, E. A data-driven framework for identifying important components in complex systems. Reliab. Eng. Syst. Saf. 2020, 204, 107197. [Google Scholar] [CrossRef]
- Chi, Y.; Dong, Y.; Wang, Z.J.; Yu, F.R.; Leung, V.C.M. Knowledge-Based Fault Diagnosis in Industrial Internet of Things: A Survey. IEEE Internet Things J. 2022, 9, 12886–12900. [Google Scholar] [CrossRef]
- Dafare, M.; Waghmare, S.; Bhoyar, A.; Titarmare, A.S.; Chandankhede, P. LoRa-Enabled Smart RS485 Data Logger and MQTT Gateway for Industrial IoT Applications Using ESP32. In Proceedings of the 2023 International Conference on Circuit Power and Computing Technologies (ICCPCT), Kollam, India, 10–11 August 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar] [CrossRef]
- Padmavathy, T.; Muralidharan, C.; Sirajudeen, Y.M. Cloud-based industrial IoT infrastructure to facilitate efficient data analytics. In Cloud Analytics for Industry 4.0; De Gruyter: Berlin, Germany, 2022; pp. 31–52. [Google Scholar] [CrossRef]
- Bartolomucci, M. Automating Safety Mechanisms Insertion Providing Standard SIL Compliance in Digital Circuits. Ph.D. Thesis, Politecnico di Torino, Torino, Italy, 2023. [Google Scholar]
- Sun, P.; Shen, S.; Wan, Y.; Wu, Z.; Fang, Z.; Gao, X. A Survey of IoT Privacy Security: Architecture, Technology, Challenges, and Trends. IEEE Internet Things J. 2024; early access. [Google Scholar] [CrossRef]
- Farooq, B.; Bao, J.; Li, J.; Liu, T.; Yin, S. Data-Driven Predictive Maintenance Approach for Spinning Cyber-Physical Production System. J. Shanghai Jiaotong Univ. Sci. 2020, 25, 453–462. [Google Scholar] [CrossRef]
- Crisp, J.; Pelletier, D.; Duffield, C.; Adams, A.; Nagy, S. The Delphi Method? Nurs. Res. 1997, 46, 116–118. [Google Scholar] [CrossRef]
- Guetterman, T.; Creswell, J.W.; Kuckartz, U. Using joint displays and MAXQDA software to represent the results of mixed methods research. In Use of Visual Displays in Research and Testing: Coding, Interpreting, and Reporting Data; Information Age Publishing, Inc.: Charlotte, NC, USA, 2015; pp. 145–175. [Google Scholar]
- Melo, P.F.S.; Godoy, E.P.; Ferrari, P.; Sisinni, E. Open source control device for industry 4.0 based on RAMI 4.0. Electronics 2021, 10, 869. [Google Scholar] [CrossRef]
- Adolphs, P.; Bedenbender, H.; Dirzus, D.; Ehlich, M.; Epple, U.; Hankel, M.; Heidel, R.; Hoffmeister, M.; Huhle, H.; Kärcher, B.; et al. Status Report—Reference Architecture Model Industrie 4.0 (RAMI4.0); Technical Report; VDI—Verein Deutscher Ingenieure eV: Düsseldorf, Germany; ZVEI—German Electrical and Electronic Manufacturers Association: Frankfurt am Main, Germany, 2015. [Google Scholar]
- Nakagawa, E.Y.; Antonino, P.O.; Schnicke, F.; Capilla, R.; Kuhn, T.; Liggesmeyer, P. Industry 4.0 reference architectures: State of the art and future trends. Comput. Ind. Eng. 2021, 156, 107241. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).