A Study of Delayed Competitive Influence Propagation Based on Shortest Path Calculation
Abstract
1. Introduction
1.1. Delayed Competition Propagation Overview
1.2. Delayed Competition Propagation Problem
1.3. Main Work of This Paper
2. Related Work
2.1. Delayed Competition Study Based on an Economic Model
2.2. Delayed Competition Study Based on the Disease Model
2.3. Delayed Competition Study Based on the Information Model
3. The Method Proposed in This Paper
3.1. Main Ideas
3.2. Variable Representation
3.3. Node Evaluation
3.3.1. Find the Nearest Propagation Region
3.3.2. Build the Shortest Path Snapshot
3.3.3. Evaluate Competitive Influence Factors
3.4. Algorithm Definition
3.4.1. Node Evaluation Method Based on Shortest Path Snapshot
3.4.2. Algorithm Input and Output Pseudo-Code
| Algorithm 1: HeuPFE, a heuristic finding algorithm based on propagation factor evaluation |
| Input: Graph: G, the number of negative seeds: kN Output: Top-kP vertices 1: initialize S = Ø, SG = Ø 2: select kN vertices as the negatives seeds 3: community partition and get z candidate communities which contain negative seed vertices: C1, C2, …, Cz 4: for i = 1 to z do 5: in current community Ci, Sv = 0 6: construct the vertex pair index of primitive topology, and add to the array AP 7: for j = 1 to r do 8: disturb randomly the sequence of primitive topology, and add to the array AS 9: generate the adjacency matrix of array AS, and add to the matrix M 10: find the shortest path snapshot from the vertex u, and add to the queue Q 11: assess the PFE of every v for negative vertex u based on the shortest path snapshot which is based on Formula (4) then Sv+ = PFE (v,u) 12: end for 13: compute average PFE for every vertex v except the negative vertices: PFE(v,u) = Sv/r 14: for j = 1 to t do 15: SP = SP ∪ {argmax v ϵ Ci\SP {PFE(v,u)}} 16: end for 17: end for 18: return SP |
3.4.3. Introduction of Each Function of the Algorithm
4. Experimental Analysis
4.1. Experimental Setup
4.1.1. Experimental Environment
4.1.2. Experimental Dataset
4.1.3. Experimental Model
4.1.4. Comparison Method
4.1.5. Evaluation Indicators
4.2. Analysis of Results
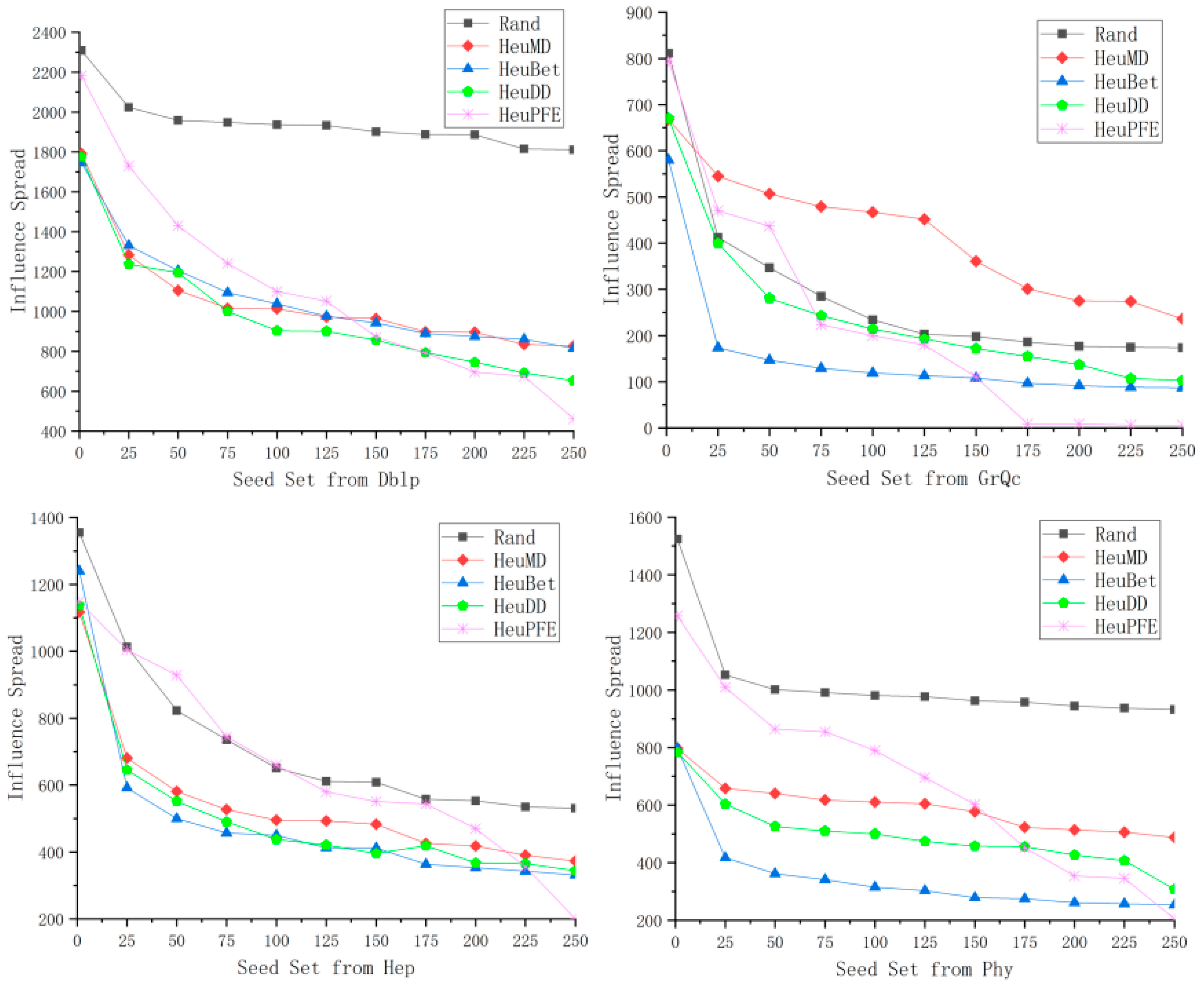
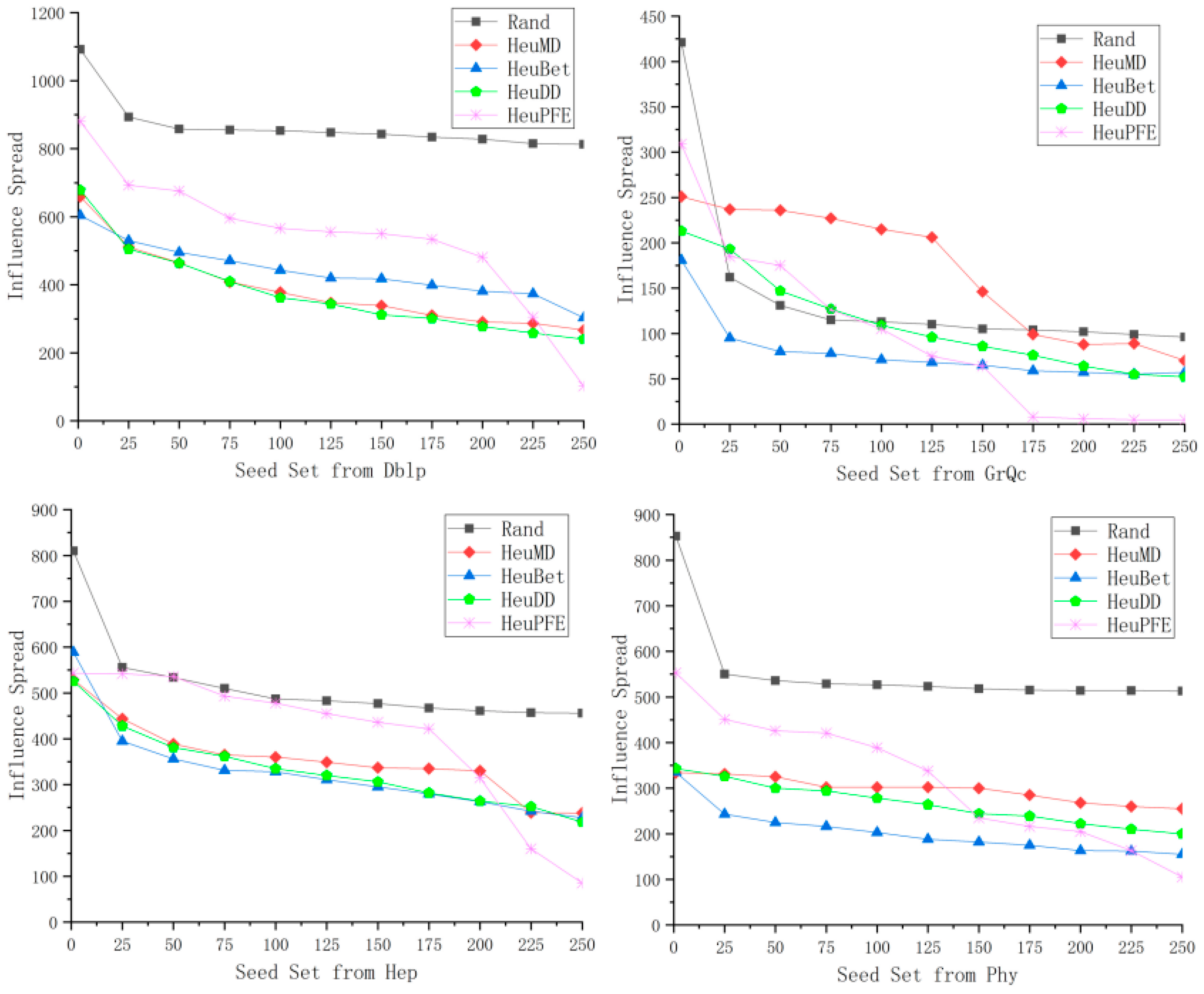
4.2.1. Experimental Results Demonstration
4.2.2. Analysis of Influence Scope
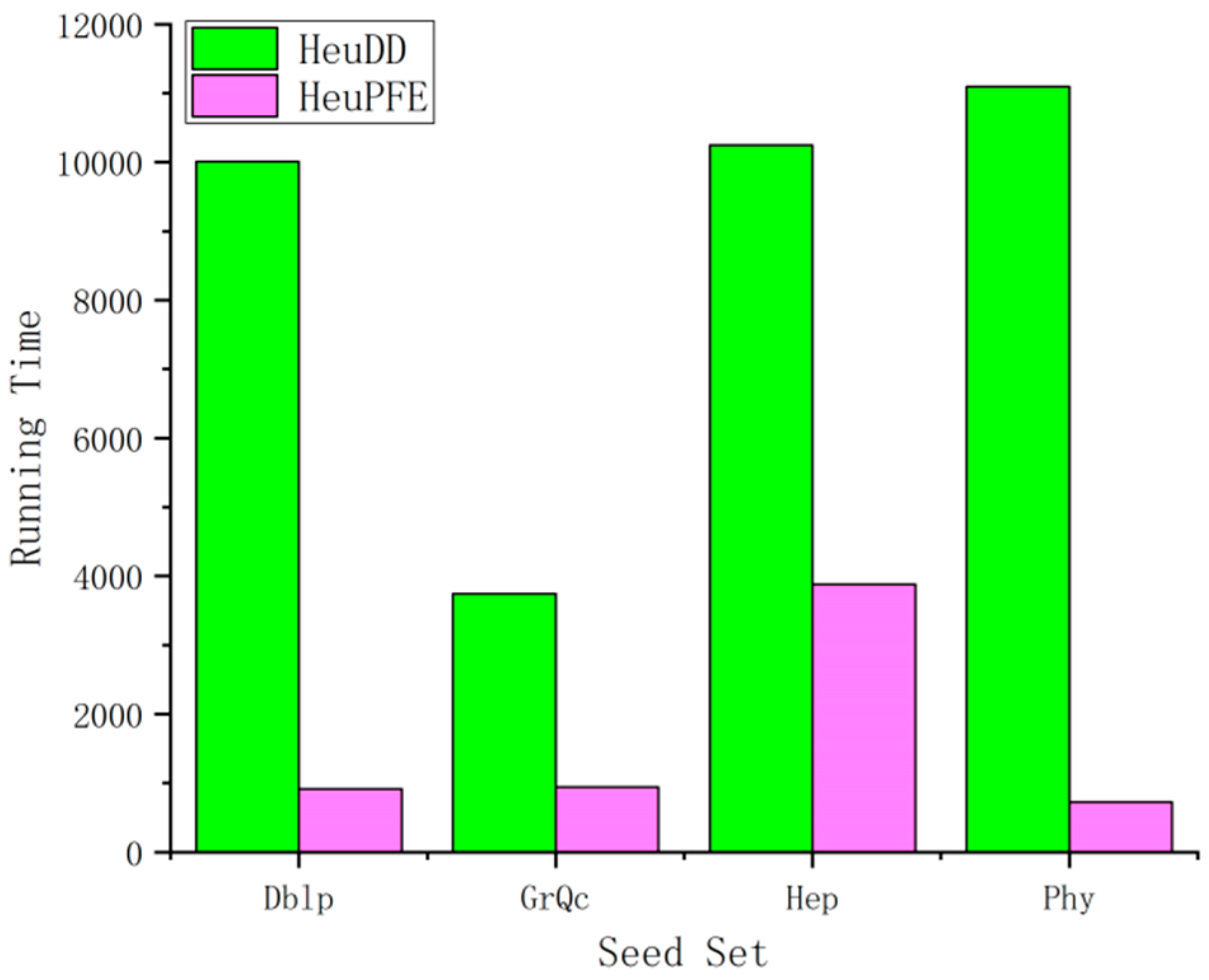
4.2.3. Running Time Analysis
5. Conclusions and Outlook
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Stackelberg Model [EB/OL]. 1934. Available online: https://wiki.mbalib.com/wiki/ (accessed on 30 August 2008).
- Higgins, R.S. An economic theory of leader choice in Stackelberg models. J. Econ. Stud. 1996, 23, 79–95. [Google Scholar] [CrossRef]
- Bharathi, S.; Kempe, D.; Salek, M. Competitive influence maximization in social networks. In International Workshop on Web and Internet Economics; Springer: Berlin/Heidelberg, Germany, 2007; pp. 306–311. [Google Scholar]
- Kostka, J.; Oswald, Y.A.; Wattenhofer, R. Word of mouth: Rumor dissemination in social networks. In International Colloquium on Structural Information and Communication Complexity; Springer: Berlin/Heidelberg, Germany, 2008; pp. 185–196. [Google Scholar]
- Clark, A.; Poovendran, R. Maximizing influence in competitive environments: A Gametheoretic Approach. In International Conference on Decision and Game Theory for Security; Springer: Berlin/Heidelberg, Germany, 2011; pp. 151–162. [Google Scholar]
- Hemmati, M.; Smith, J.C.; Thai, M.T. A cutting-plane algorithm for solving a weighted influence interdiction problem. Comput. Optim. Appl. 2014, 57, 71–104. [Google Scholar] [CrossRef]
- Taninmis, K.; Aras, N.; Altinel, I.K. Influence Maximization With Deactivation In Social Networks. Eur. J. Oper. Res. 2019, 278, 105–119. [Google Scholar] [CrossRef]
- Pastor-Satorras, R.; Vespignani, A. Immunization of complex networks. Phys. Rev. E 2002, 65, 036104. [Google Scholar] [CrossRef] [PubMed]
- Cohen, R.; Havlin, S.; Ben-Avraham, D. Efficient immunization strategies for computer networks and populations. Phys. Rev. Lett. 2003, 91, 247901. [Google Scholar] [CrossRef] [PubMed]
- Kitsak, M.; Gallos, L.K.; Havlin, S.; Liljeros, F.; Muchnik, L.; Stanley, H.E.; Makse, H.A. Identification of influential spreaders in complex networks. Nat. Phys. 2010, 6, 888–893. [Google Scholar] [CrossRef]
- Hou, B.; Yao, Y.; Liao, D. Identifying all-around nodes for spreading dynamics in complex networks. Phys. A Stat. Mech. Its Appl. 2012, 391, 4012–4017. [Google Scholar] [CrossRef]
- Liu, J.G.; Ren, Z.M.; Guo, Q. Ranking the spreading influence incomplex networks. Phys. A Stat. Mech. Its Appl. 2013, 392, 4154–4159. [Google Scholar] [CrossRef]
- Zhang, Y.; Prakash, B.A. Dava: Distributing vaccines over networks under prior information. In Proceedings of the 2014 SIAM International Conference on Data Mining, Philadelphia, PA, USA, 24–26 June 2014; pp. 46–54. [Google Scholar]
- Zhang, Y.; Adiga, A.; Saha, S.; Vullikanti, A.; Prakash, B.A. Near-optimal algorithms for controlling propagation at group scale on networks. IEEE Trans. Knowl. Data Eng. 2016, 28, 3339–3352. [Google Scholar] [CrossRef]
- Chen, L.D.; Ren, X.L.; Zhang, Q.M.; Zhang, Y.C.; Zhou, T. Vital nodes identification in complex networks. Phys. Rep. 2016, 650, 1–63. [Google Scholar] [CrossRef]
- Kimura, M.; Saito, K.; Motoda, H. Minimizing the spread of contamination by blocking links in a network. AAAI 2008, 8, 1175–1180. [Google Scholar]
- Kimura, M.; Saito, K.; Motoda, H. Blocking links to minimize contamination spread in a social network. ACM Trans. Knowl. Discov. Data (TKDD) 2009, 3, 9. [Google Scholar] [CrossRef]
- Tong, H.; Prakash, B.A.; Eliassi-Rad, T.; Faloutsos, M.; Faloutsos, C. Gelling and melting, large graphs by edge manipulation. In Proceedings of the 21st ACM International Conference on Information and Knowledge Management, Maui, HI, USA, 29 October–2 November 2012; pp. 245–254. [Google Scholar]
- Kuhlman, C.J.; Tuli, G.; Swarup, S.; Marathe, M.V.; Ravi, S.S. Blocking simple and comple contagion by edge removal. In Proceedings of the 2013 IEEE 13th International Conference on Data Mining, Dallas, TX, USA, 7–10 December 2013; pp. 399–408. [Google Scholar]
- Khalil, E.B.; Dilkina, B.; Song, L. Scalable diffusion-aware optimization of network topology. In Proceedings of the 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, New York, NY, USA, 24–27 August 2014; pp. 1226–1235. [Google Scholar]
- Liu, X. Research on Efficient Processing Techniques for Influence Maximization Problems in Large-Scale Social Networks. Ph.D. Thesis, National University of Defense Technology, Changsha, China, 2013; pp. 25–26. [Google Scholar]
- Zhang, J.; Wang, S.; Zhan, Q.; Yu, P.S. Interwined viral marketing in social networks. In Proceedings of the IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, San Francisco, CA, USA, 18–21 August 2016; pp. 239–246. [Google Scholar]
- Carnes, T.; Nagarajan, C.; Wild, S.M.; van Zuylen, A. Maximizing influence in a competitive social network: A follower’s perspective. In Proceedings of the Ninth International Conference on Electronic Commerce, Chicago, IL, USA, 8–12 July 2007; pp. 351–360. [Google Scholar]
- Chen, W.; Wei, L.; Zhang, N. Time-critical influence maximization in social networks with time-delayed diffusion process. In Proceedings of the 26th AAAI Conference on Artificial Intelligence, Melbourne, Australia, 19–25 August 2012. [Google Scholar]
- Lin, S.-C.; Lin, S.-D.; Che, M.-S.N. A learning-based framework to handle multi-round multi-party influence maximization on social networks. In Proceedings of the 21th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Sydney, Australia, 10–13 August 2015; pp. 695–704. [Google Scholar]
- Bozorgi, A.; Samet, S.; Kwisthout, J.; Wareham, T. Community-based influence maximization in social networks under a competitive linear threshold model. Knowl.-Based Syst. 2017, 134, 149–158. [Google Scholar] [CrossRef]
- Li, H.; Pan, L.; Wu, P. Dominated competitive influence maximization with time-critical and timedelayed diffusion in social networks. J. Comput. Sci. 2018, 28, 318–327. [Google Scholar] [CrossRef]
- Pham, C.V.; Duong, H.V.; Hoang, H.X. Competitive Influence Maximization within Time and Budget Constraints in Online Social Networks: An Algorithmic Approach. Appl. Sci. 2019, 9, 2274. [Google Scholar] [CrossRef]
- Chen, B.-L.; Sheng, Y.-Y.; Ji, M.; Liu, J.-W.; Yu, Y.-T.; Zhang, Y. Competitive Influence Maximization on Online Social Networks under Cost Constraint. KSII Trans. Internet Inf. Syst. 2021, 15, 1263–1274. [Google Scholar] [CrossRef]
- Budak, C.; Agrawal, D.; EL Abbadi, A. Limiting the spread of misinformation in social networks. In Proceedings of the 20th International Conference on World Wide Web, Hyderabad, India, 28 March–1 April 2011; ACM: New York, NY, USA, 2011; pp. 665–674. [Google Scholar]
- Nguyen, N.P.; Yan, G.; Thai, M.T.; Eidenbenz, S. Containment of misinformation spread in online social networks. In Proceedings of the 4th ACM Web Science (WebSci’ 12), Evanston, IL, USA, 22–24 June 2012; ACM: New York, NY, USA, 2012. [Google Scholar]
- Wang, B.; Chen, G.; Fu, L.; Song, L.; Wang, X. Drimux: Dynamic rumor influence minimization with user experience in social networks. IEEE Trans. Knowl. Data Eng. 2016, 29, 2168–2181. [Google Scholar] [CrossRef]
- Rawale, S.; Birkure, S.; Hiray, K.; Deshmukh, D. Detection and Minimization Influence of Rumor in Social Network. Int. Res. J. Eng. Technol. (IRJET) 2017, 4, 757–761. [Google Scholar]
- Yan, R.; Zhu, Y.; Li, D.; Ye, Z. Minimum cost seed set for threshold influence problem under competitive models. World Wide Web 2018, 22, 2977–2996. [Google Scholar] [CrossRef]
- Gu, H.; Xi, J.; Wu, J. Community division algorithm based on association coefficient. Microcomput. Appl. 2015, 34, 17–19. [Google Scholar]
- Raghavan, U.N.; Albert, R.; Kumara, S. Near linear time algorithm to detec community structures in large-scale networks. Phys. Rev. E 2007, 76, 036106. [Google Scholar] [CrossRef] [PubMed]
- High Energy Physics [EB/OL]. 2003. Available online: http://www.arxiv.org/archive/hep (accessed on 5 June 2003).
- Chen, W.; Wang, Y.; Yang, S. Efficient influence maximization in social networks. In Proceedings of the 15th ACM SIGKDD conference on Knowledge Discovery and Data Mining, New York, NY, USA, 28 June–1 July 2009; pp. 199–208. [Google Scholar]
- Barthelemy, M. Betweenness centrality in large complex networks. Eur. Phys. J. B 2004, 38, 163–168. [Google Scholar] [CrossRef]

| Variables | Descriptions |
|---|---|
| N | The number of vertices |
| M | The number of edges |
| SN | The set of negative seed |
| kN | The number of negative seeds |
| kP | The number of positive seeds |
| R | The simulation times of propagation in algorithm |
| R | The simulation times of matrix in algorithm |
| SimCas(S) | The spread process of set S |
| S | The set of selected seed |
| SG | The candidate vertices set for algorithm |
| MGv | The marginal gain of vertex v which is added to set S |
| PFEv | The propagation factor evaluation of vertex v |
| Z | The number of communities |
| NC | The number of vertices in community |
| MC | The number of edges in community |
| Nsd | The shortest distance from the negative vertex u to v |
| Spf | The shortest path frequency through vertex v |
| Adm | The adjacency degree measure of vertex v |
| DataSet | #Vertices | #Edges |
|---|---|---|
| Dblp | 14,485 | 37,026 |
| GrQc | 5242 | 14,485 |
| Hep | 15,233 | 31,380 |
| Phy | 14,997 | 57,866 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Wang, Z. A Study of Delayed Competitive Influence Propagation Based on Shortest Path Calculation. Information 2024, 15, 370. https://doi.org/10.3390/info15070370
Li Y, Wang Z. A Study of Delayed Competitive Influence Propagation Based on Shortest Path Calculation. Information. 2024; 15(7):370. https://doi.org/10.3390/info15070370
Chicago/Turabian StyleLi, Yang, and Zhiqiang Wang. 2024. "A Study of Delayed Competitive Influence Propagation Based on Shortest Path Calculation" Information 15, no. 7: 370. https://doi.org/10.3390/info15070370
APA StyleLi, Y., & Wang, Z. (2024). A Study of Delayed Competitive Influence Propagation Based on Shortest Path Calculation. Information, 15(7), 370. https://doi.org/10.3390/info15070370






