Identity-Based Online/Offline Encryption Scheme from LWE
Abstract
:1. Introduction
1.1. Our Motivation and Contributions
- (1)
- We first investigate the coexistence of anti-quantum security and efficiency in the IBE system, and design an IBOOE scheme from the LWE problem.
- (2)
- We then construct our concrete IBOOE scheme from LWE and prove the CPA secure under the standard model.
- (3)
1.2. Paper Organization
2. Related Work
3. Preliminaries
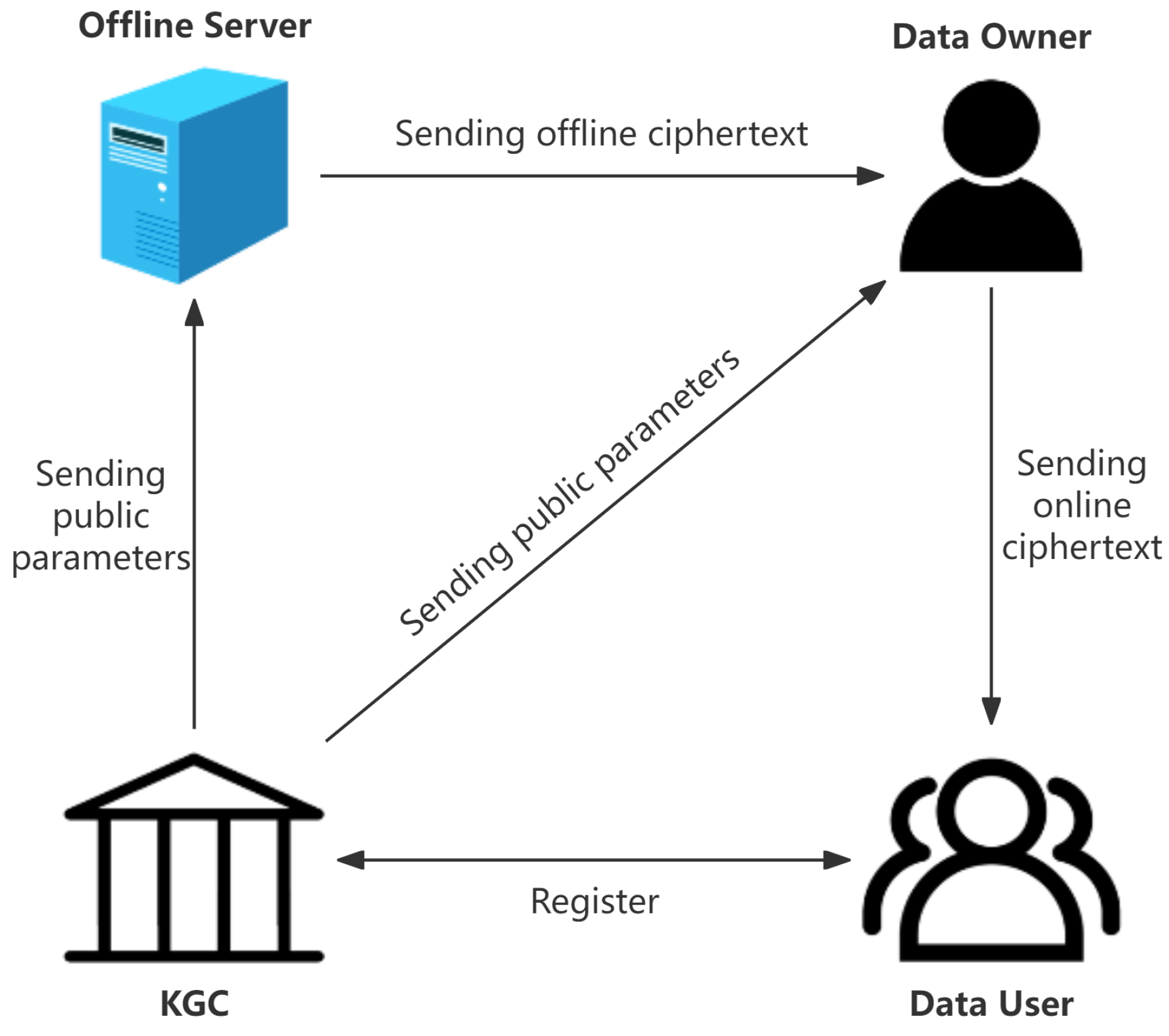
3.1. Framework and Security of IBOOE
- (1)
- For , challenger uses algorithm for setting challenge ciphertext as .
- (2)
- For , the challenger directly uses the challenge ciphertext chosen before and setsThe challenger then sends as the ciphertext for challenge to adversary .
3.2. Sampling Algorithms
- –
- For matrix and its -trapdoor , matrix , vector and parameter , the algorithm outputs a vector distributed statistically approaching to .
- –
- For matrix and its -trapdoor , matrix , uniformly random matrix from , vector , and parameter , the algorithm outputs a vector distributed statistically close to .
3.3. Encoding Identities as Matrices
4. New Lattice-Identity-Based Online/Offline Encryption
4.1. Construction
4.2. Parameters and Correctness
4.3. Security Proof
- : The Game 0 is between the adversary for our scheme and the INDr-sID-CPA challenger, it is just as described in Definition 3, namely the original game.
- :
- (1)
- For , the challenger uses algorithm for setting the challenge ciphertext as (,,M).
- (2)
- For , the challenger directly uses the ciphertext chosen before and sets
- :
- (1)
- For , the challenger uses algorithm for setting challenge ciphertext as (,,M).
- (2)
- For , the challenger directly uses the ciphertext chosen before and sets
- :
- (a)
- From n of the given LWE samples, it makes the random matrix and for all the i-th column of is the r-vector .
- (b)
- Specify the zeroth LWE sample as a publicly available random r-vector . The zeroth LWE sample has not been used yet.
- (c)
- Use and to create the remaining of public parameters as in Game 2.
- (d)
- Lastly, it sends public parameters to the adversary.
- (a)
- Set as the entries from the LWE instance and set from .
- (b)
- Letting for masking message bit.
- (c)
- Set .
- (d)
- Send to the adversary.
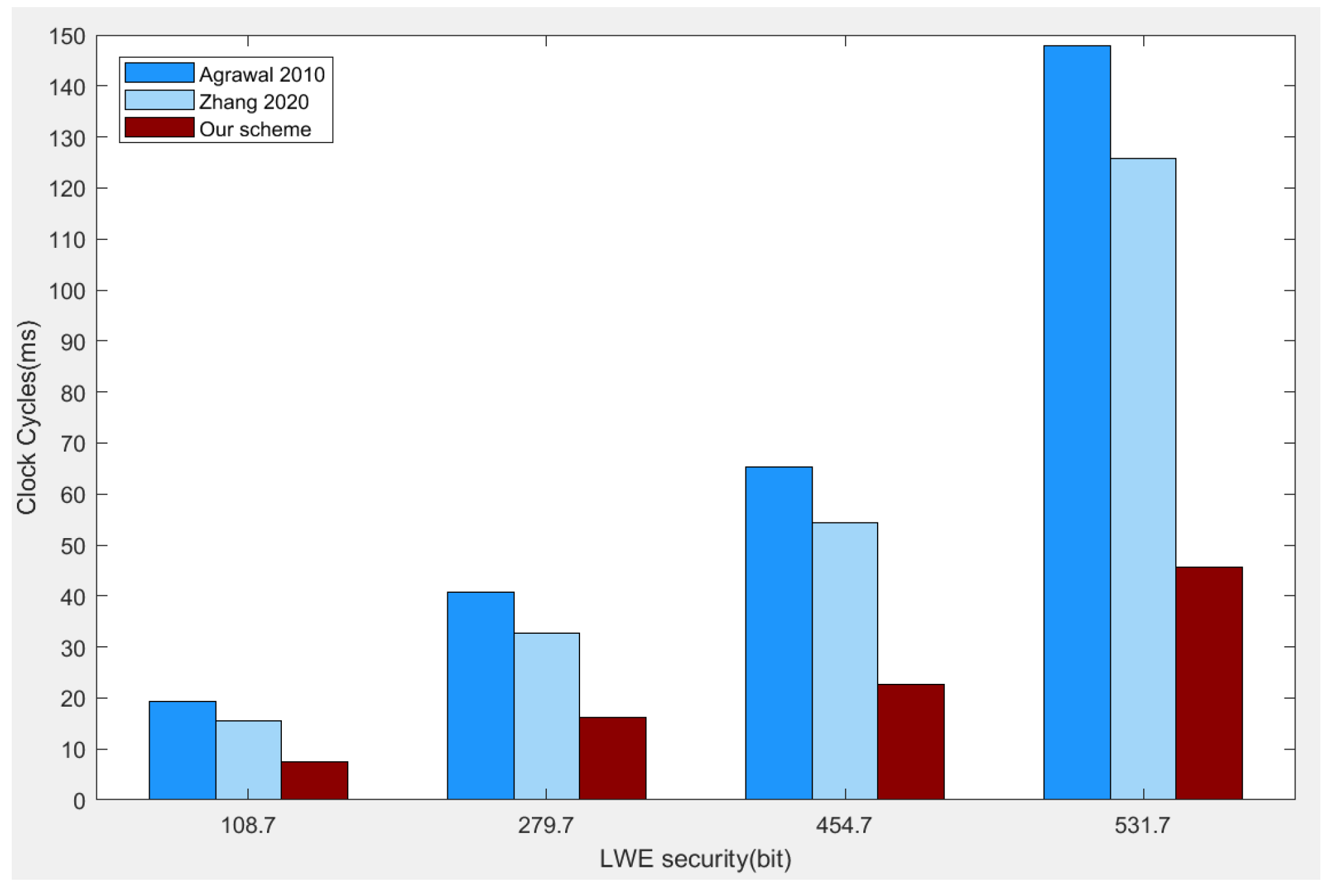
5. Comparison and Analysis
5.1. Theoretical Comparison
5.2. Experimental Simulation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for Hard Lattices and New Cryptographic Constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008. [Google Scholar]
- Cash, D.; Hofheinz, D.; Kiltz, E.; Peikert, C. Bonsai Trees, or How to Delegate a Lattice Basis. J. Cryptol. 2012, 25, 601–639. [Google Scholar] [CrossRef]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient Lattice (H)IBE in the Standard Model. In Advances in Cryptology–EUROCRYPT 2010, Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6110, pp. 553–572. [Google Scholar]
- Zhang, Y.; Liu, Y.; Guo, Y.; Zheng, S.; Wang, L. Adaptively Secure Efficient (H)IBE over Ideal Lattice with Short Parameters. Entropy 2020, 22, 1247. [Google Scholar] [CrossRef] [PubMed]
- Regev, O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography. J. ACM (JACM) 2009, 56, 1–40. [Google Scholar] [CrossRef]
- Zhandry, M. Secure Identity-based Encryption in the Quantum Random Oracle Model. Int. J. Quantum Inf. 2015, 13, 1550014. [Google Scholar] [CrossRef]
- Katsumata, S.; Yamada, S.; Yamakawa, T. Tighter Security Proofs for GPV-IBE in the Quantum Random Oracle Model. J. Cryptol. 2021, 34, 5. [Google Scholar] [CrossRef]
- Gao, W.; Yang, L.; Zhang, D.; Liu, X. Quantum Identity-based Encryption from the Learning with Errors Problem. Cryptography 2022, 6, 9. [Google Scholar] [CrossRef]
- Dutta, P.; Susilo, W.; Duong, D.H.; Baek, J.; Roy, P.S. Lattice-based Unidirectional IBPRE Secure in Standard Model. arXiv 2020, arXiv:2005.06741. [Google Scholar]
- Wu, L.; Yang, X.; Zhang, M.; Wang, X. IB-VPRE: Adaptively Secure Identity-based Proxy Re-encryption Scheme from LWE with Re-encryption Verifiability. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 469–482. [Google Scholar]
- Liu, Y.; Sun, Y. Generic Construction of Server-aided Revocable Hierarchical Identity-based Encryption. Int. Conf. Inf. Secur. Cryptol. 2020, 12612, 73–82. [Google Scholar]
- Li, J.; Teng, M.; Zhang, Y.; Yu, Q. A Leakage-Resilient CCA-Secure Identity-Based Encryption Scheme. Comput. J. 2016, 59, 1066–1075. [Google Scholar] [CrossRef]
- Li, J.; Guo, Y.; Yu, Q.; Lu, Y.; Zhang, Y. Provably Secure Identity-based Encryption Resilient to Post-challenge Continuous Auxiliary Input Leakage. Secur. Commun. Netw. 2016, 9, 1016–1024. [Google Scholar]
- Li, J.; Yu, Q.; Zhang, Y. Identity-based Broadcast Encryption with Continuous Leakage Resilience. Inf. Sci. 2018, 429, 177–193. [Google Scholar] [CrossRef]
- Yu, Q.; Li, J.; Ji, S. Hierarchical Identity-Based Online/Offline Encryption Scheme with Leakage Resilience. Secur. Commun. Netw. 2022, 2022, 6849761. [Google Scholar]
- Abla, P.; Liu, F.H.; Wang, H.; Wang, Z. Ring-based Identity Based Encryption–Asymptotically Shorter MPK and Tighter Security. In Theory of Cryptography: 19th International Conference, TCC, Raleigh, NC, USA, 8–11 November 2021; Springer: Cham, Switzerland, 2021; Volume 13044, pp. 157–187. [Google Scholar]
- Fan, J.; Lu, X.; Au, M.H. Adaptively Secure Identity-Based Encryption from Middle-Product Learning with Errors. In Proceedings of the Australasian Conference on Information Security and Privacy, Brisbane, QLD, Australia, 5–7 July 2023; Volume 13915, pp. 320–340. [Google Scholar]
- Lai, Q.; Liu, F.H.; Wang, Z. New Lattice Two-Stage Sampling Technique and Its Applications to Functional Encryption – Stronger Security and Smaller Ciphertexts. In Advances in Cryptology—EUROCRYPT 2021, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 17–21 October 2021; Springer: Cham, Switzerland, 2021; Volume 12696, pp. 498–527. [Google Scholar]
- Weiden, P.; Hülsing, A.; Cabarcas, D.; Buchmann, J. Instantiating Treeless Signature Schemes. Cryptol. ePrint Arch. 2013, 2013, 65. [Google Scholar]
- Lyubashevsky, V. Lattice Signatures without Trapdoors. In Advances in Cryptology—EUROCRYPT 2012, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7237, pp. 738–755. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller. In Advances in Cryptology—EUROCRYPT 2012, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7237, pp. 700–718. [Google Scholar]
- Micciancio, D.; Walter, M. Gaussian Sampling over the Integers: Efficient, Generic, Constant-Time. In Advances in Cryptology–CRYPTO 2017, Proceedings of the 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Cham, Switzerland, 2017; Volume 10402, pp. 455–485. [Google Scholar]
- Sun, S.; Zhou, Y.; Ji, Y.; Zhang, R.; Tao, Y. Generic, Efficient and Isochronous Gaussian Sampling over the Integers. Cybersecurity 2022, 5, 10. [Google Scholar]
- Guo, F.; Mu, Y.; Chen, Z. Identity-based Online/Offline Encryption. Financ. Cryptogr. Data Secur. 2008, 5143, 247–261. [Google Scholar]
- Cramer, R.; Damgård, I. On the Amortized Complexity of Zero-Knowledge Protocols. In Advances in Cryptology, Proceedings of the Annual International Cryptology Conference 2009, Santa Barbara, CA, USA, 16–20 August 2009; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5677, p. 177. [Google Scholar]
- Karney, C.F.F. Sampling Exactly from the Normal Distribution. Acm Trans. Math. Softw. (TOMS) 2016, 42, 1–14. [Google Scholar] [CrossRef]
- Chen, Y.; Genise, N.; Mukherjee, P. Approximate Trapdoors for Lattices and Smaller Hash-and-sign Signatures. In Advances in Cryptology–ASIACRYPT 2019, Proceedings of the 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, 8–12 December 2019; Springer: Cham, Switzerland, 2019; Volume 11923, pp. 3–32. [Google Scholar]
- Chen, S.; Li, J.; Zhang, Y.; Han, J. Efficient Revocable Attribute-based Encryption with Verifiable Data Integrity. IEEE Internet Things J. 2024, 11, 10441–10451. [Google Scholar]
- Chen, N.; Li, J.; Zhang, Y.; Guo, Y. Efficient CP-ABE Scheme with Shared Decryption in Cloud Storage. IEEE Trans. Comput. 2022, 71, 175–184. [Google Scholar]
- Li, J.; Zhang, Y.; Ning, J.; Huang, X.; Poh, G.S.; Wang, D. Attribute Based Encryption with Privacy Protection and Accountability for CloudIoT. IEEE Trans. Cloud Comput. 2022, 10, 762–773. [Google Scholar] [CrossRef]
- Zhang, R.; Li, J.; Lu, Y.; Han, J.; Zhang, Y. Key Escrow-free Attribute Based Encryption with User Revocation. Inf. Sci. 2022, 600, 59–72. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zuo, B.; Li, J.; Zhang, Y.; Shen, J. Identity-Based Online/Offline Encryption Scheme from LWE. Information 2024, 15, 539. https://doi.org/10.3390/info15090539
Zuo B, Li J, Zhang Y, Shen J. Identity-Based Online/Offline Encryption Scheme from LWE. Information. 2024; 15(9):539. https://doi.org/10.3390/info15090539
Chicago/Turabian StyleZuo, Binger, Jiguo Li, Yichen Zhang, and Jian Shen. 2024. "Identity-Based Online/Offline Encryption Scheme from LWE" Information 15, no. 9: 539. https://doi.org/10.3390/info15090539





