A Tripartite Evolutionary Game Analysis of Enterprise Data Sharing Under Government Regulations
Abstract
:1. Introduction
2. Literature Review
2.1. Enterprise Data Sharing
2.2. Government Regulation and Enterprise Data Sharing
2.3. Evolutionary Game Theory and Its Applications in the Field of Data Sharing
3. Model Assumptions and Tripartite Evolutionary Game Model Construction
3.1. Model Assumptions
3.1.1. Subjects of the Game
3.1.2. Behavioral Strategies of Subjects
3.1.3. Probability of Behavioral Strategies
3.1.4. Game Diagram and Parameter Setting
3.2. Tripartite Evolutionary Game Model Construction
4. Stability Analysis of Tripartite Evolutionary Game Theory
4.1. The Jacobi Matrix of Replicator Dynamic System
4.2. Stability Analysis of Equilibrium Points
5. System Simulation
5.1. The Test of Evolutionary Stability Strategy
5.2. The Impact of the Changes in Initial Probability
5.3. The Influence of Key Variables on Subjects’ Evolutionary Strategies
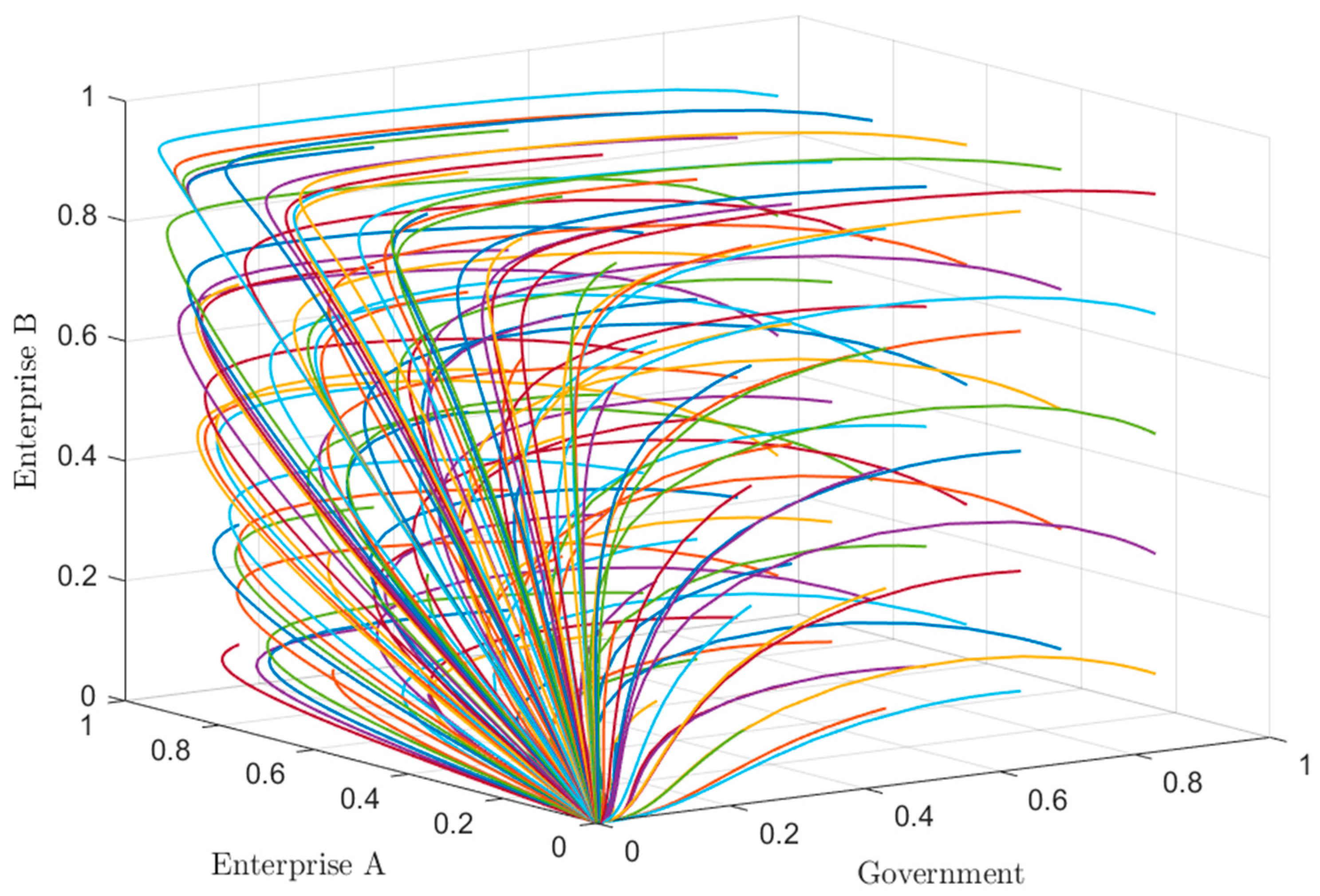
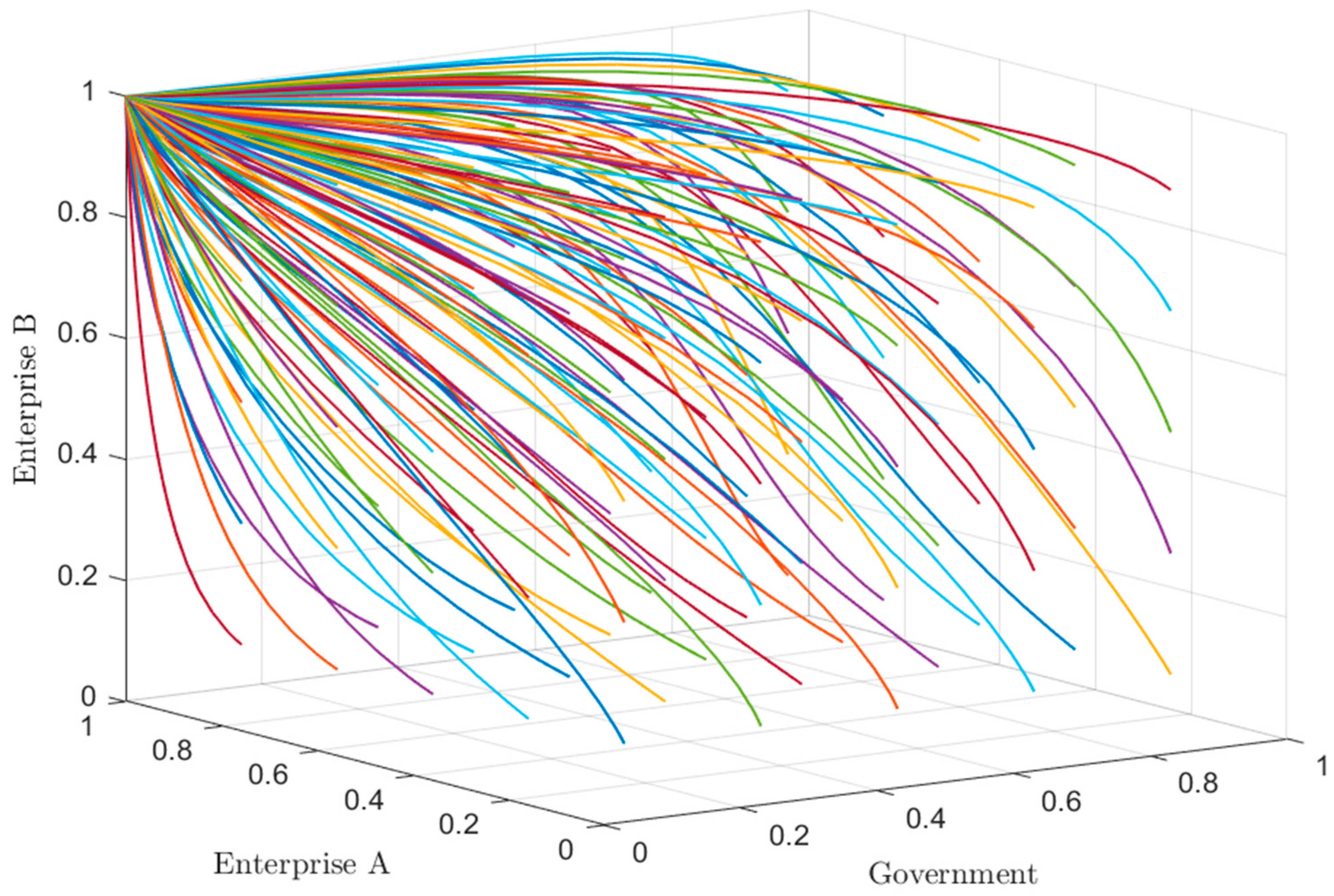
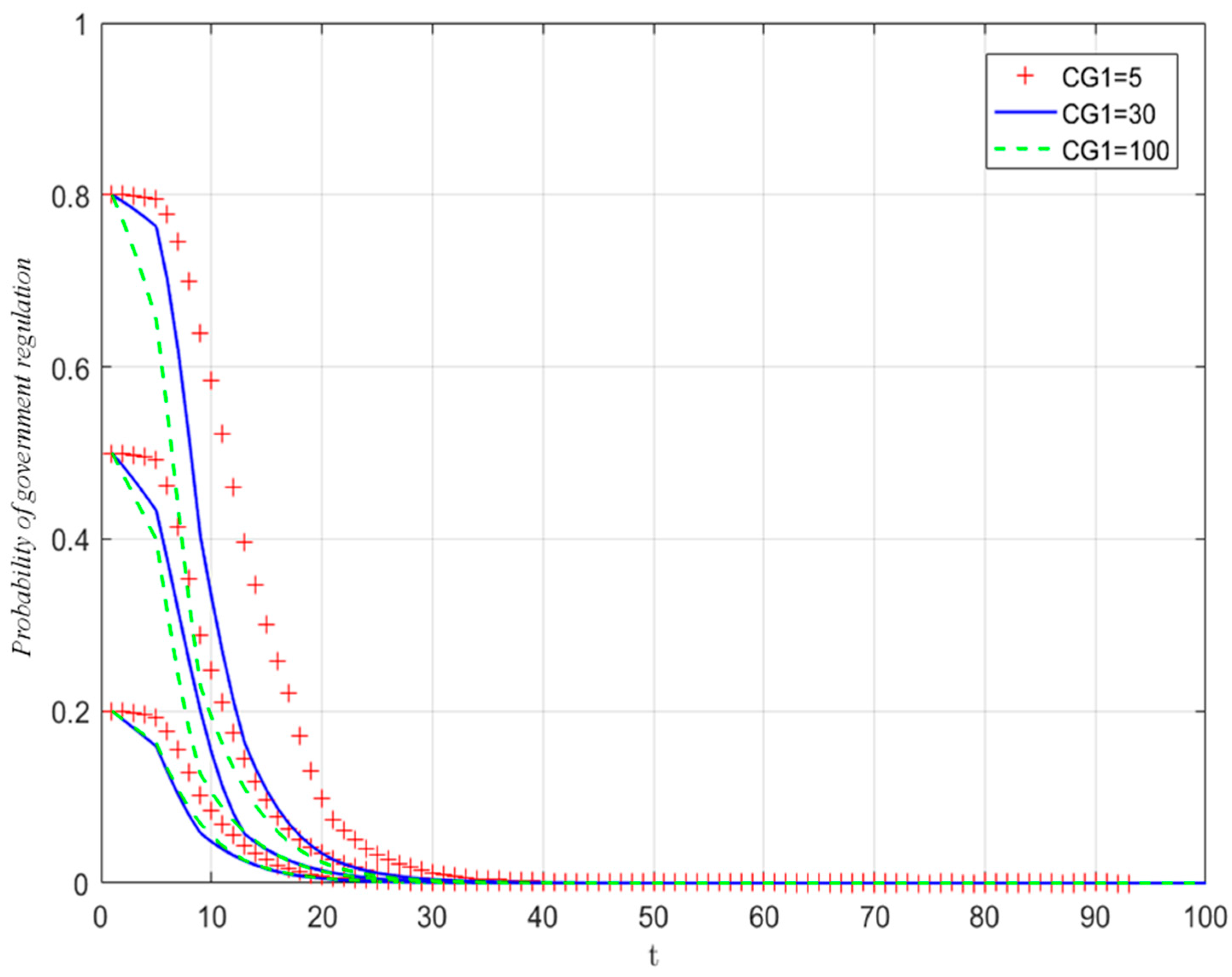
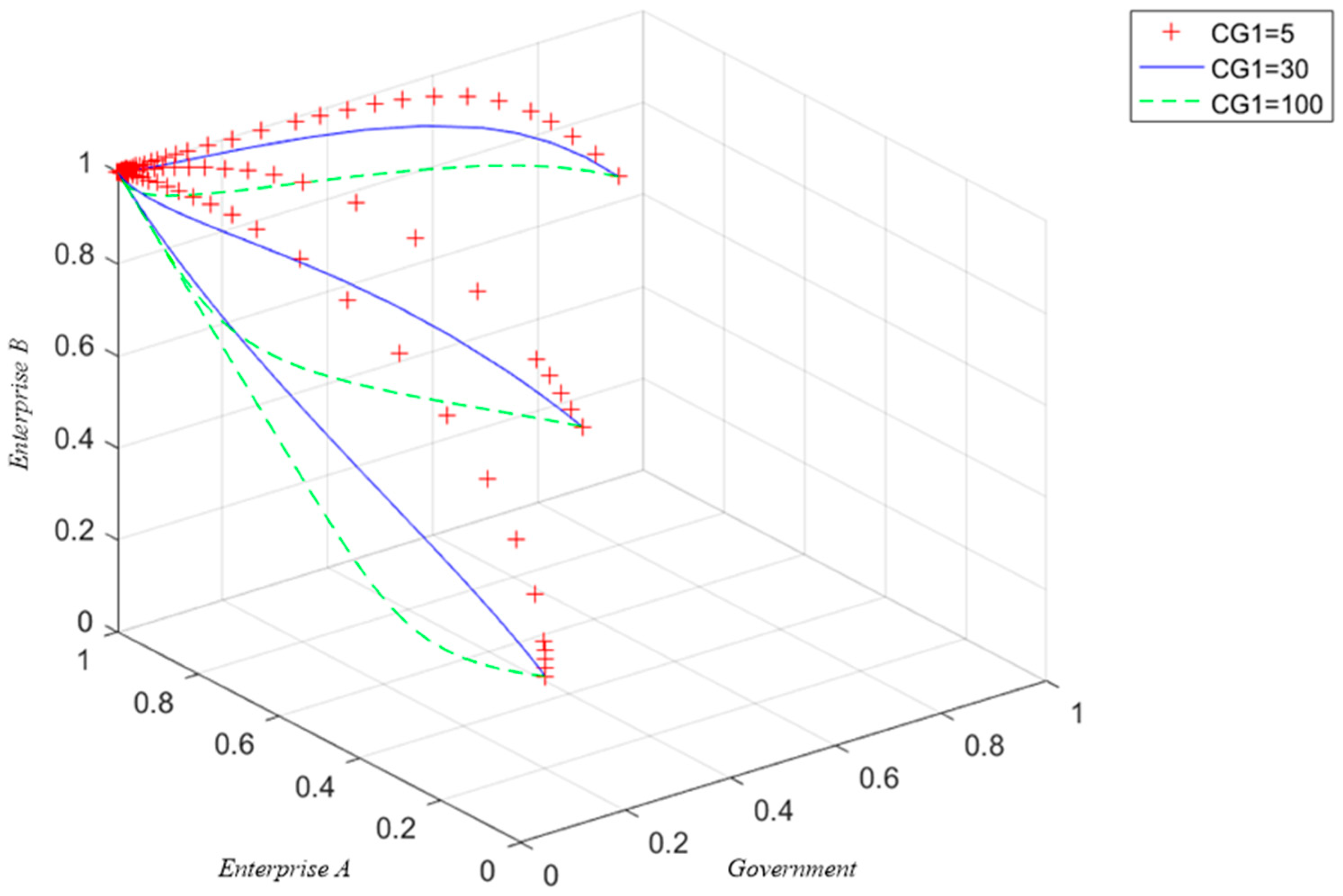
5.3.1. The Influence of Government Regulation Cost
5.3.2. The Influence of Government Penalties
5.3.3. The Influence of Government Incentives
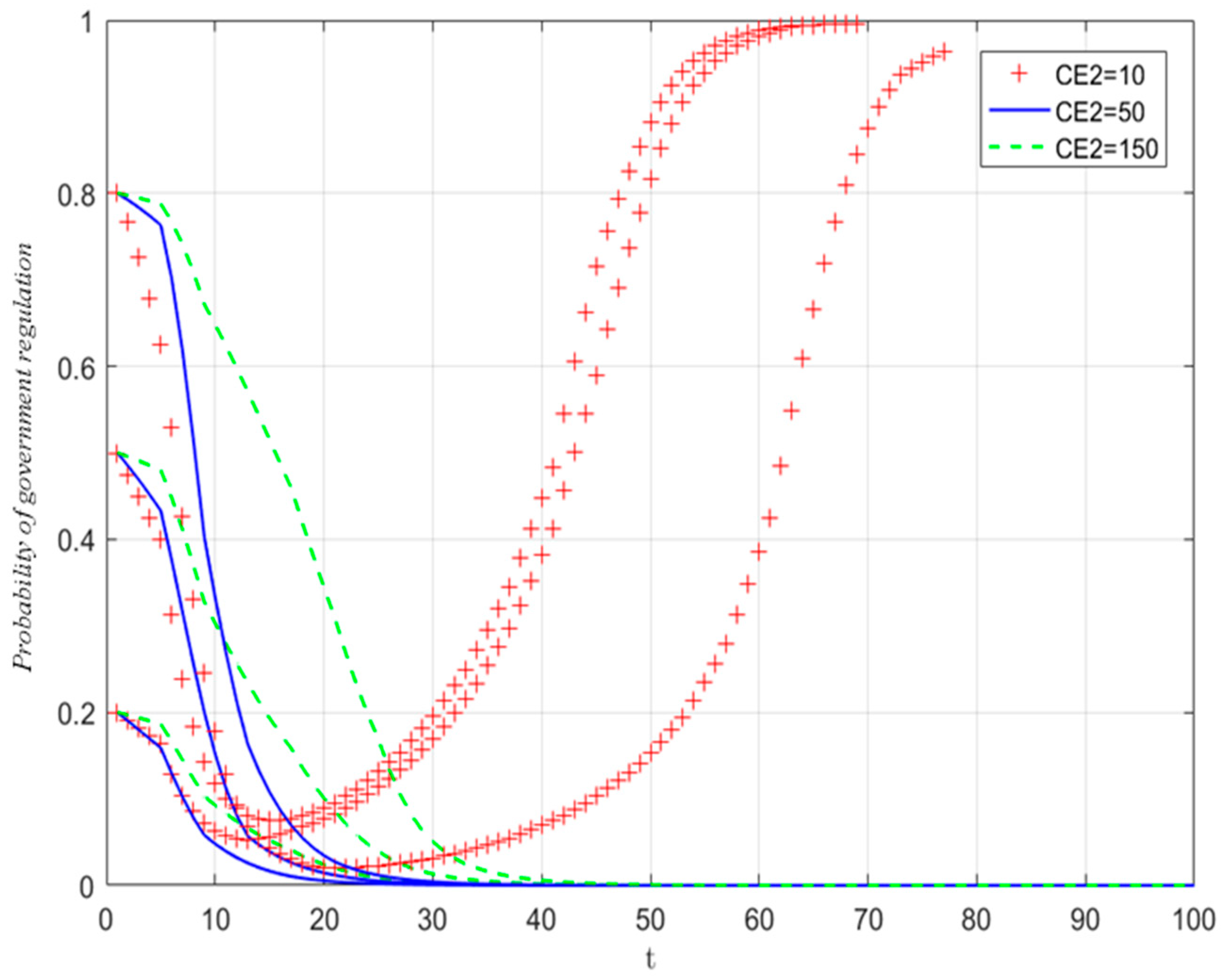
5.3.4. The Influence of Compensation Fees for Enterprises to Obtain Shared Data
6. Conclusions and Policy Implications
- (1)
- Precisely regulate the intensity of government regulation. In the context of the “no-regulation, data-sharing, data-sharing” combination strategy, where government-related factors primarily influence the evolutionary speed, the government must adopt a proactive and well-planned approach. In the initial phase, it is crucial to formulate rational and stringent control cost budgets, penalty regulations, and reward mechanisms. For regulatory costs, a meticulous accounting of the necessary human resources, material assets, and technological investments is essential. This precision ensures that costs are neither exorbitantly high, which could strain public finances, nor too low, which might compromise the effectiveness of supervision. Penalty standards should be scientifically calibrated according to the severity of enterprises’ violations and their tolerance thresholds. This scientific approach guarantees that the penalties have sufficient deterrence without being overly punitive. The reward mechanism, on the other hand, should be designed to be highly appealing. By offering substantial incentives, such as tax breaks, preferential policies, or financial subsidies, the government can encourage enterprises to actively engage in data sharing.
- (2)
- Reasonably intervene in the compensation fees for enterprise data sharing. The compensation fees for enterprises to obtain shared data have a profound impact on the ultimate evolutionary direction of all three parties involved. When these fees are low, enterprises tend to be reluctant to share data. To address this issue, the government can play a guiding role. The government can introduce clear guidelines on reasonable price ranges for data-sharing compensation. By doing so, it can effectively regulate the compensation-fee market, preventing situations where enterprises abandon data sharing due to unjust or unreasonable fee structures. Additionally, the government should encourage industry associations to take the lead in constructing data-sharing cost assessment platforms, which can help enterprises calculate compensation costs accurately and fairly.
- (3)
- Improve the market mechanism for data sharing. The government should strengthen the institutional construction of the data-sharing market, formulate fair and transparent data-sharing rules, and prevent unfair competition among enterprises. It should prohibit dominant enterprises from monopolizing key data resources, restrict opportunities for other enterprises to access data, avoid uneven distribution of data resources, and hinder market innovation vitality. At the same time, the government should crack down severely on malicious tampering of data, false labeling of data, and other behaviors, create a good atmosphere for data sharing, enhance the willingness and confidence of enterprises in data sharing, and promote the healthy development of the entire industry’s data-sharing ecosystem.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Magalhaes, G.; Roseira, C. Open Government Data and the Private Sector: An Empirical View on Business Models and Value Creation. Gov. Inf. Q. 2020, 37, 101248. [Google Scholar] [CrossRef]
- Zech, H. Building a European Data Economy. IIC 2017, 48, 501–503. [Google Scholar] [CrossRef]
- Alexander, V.Y. Recalibrating the Data Economy: Towards a System of Access and Benefit Sharing. Eur. Data Prot. Law Rev. 2023, 9, 333–344. [Google Scholar]
- Ma, X.; Jiao, H.; Zhao, Y.; Huang, S.; Yang, B. Does Open Data have the Potential to Improve the Response of Science to Public Health Emergencies? J. Informetr. 2024, 18, 101505. [Google Scholar] [CrossRef]
- Joseph, H. The Evolving U.S. Policy Environment for Open Research Data. Inf. Serv. Use 2016, 36, 45–48. [Google Scholar] [CrossRef]
- Latvakoski, J.; Umer, A.; Nykänen, T.; Tihinen, J.; Talman, A. A Simulation-Based Study on Securing Data Sharing for Situational Awareness in a Port Accident Case. Systems 2024, 12, 389. [Google Scholar] [CrossRef]
- Huang, A.; Triebe, M.; Li, Z.T.; Wu, H.; Joung, B.G.; Sutherland, J.W. A Review of Research on Smart Manufacturing in Support of Environmental Sustainability. Int. J. Sustain. Manuf. 2022, 5, 132–163. [Google Scholar] [CrossRef]
- Abbas, A.E.; Agahari, W.; Van de Ven, M.; Zuiderwijk, A.; De Reuver, M. Business Data Sharing through Data Marketplaces: A Systematic Literature Review. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 3321–3339. [Google Scholar] [CrossRef]
- Dabbous, A.; Tarhini, A. Does Sharing Economy Promote Sustainable Economic Development and Energy Efficiency? Evidence from OECD Countries. J. Innov. Knowl. 2020, 6, 58–68. [Google Scholar] [CrossRef]
- Janssen, M.; Charalabidis, Y.; Zuiderwijk, A. Benefits, Adoption Barriers and Myths of Open Data and Open Government. J. Inf. Syst. Manag. 2012, 29, 258–268. [Google Scholar] [CrossRef]
- Gil-Garcia, J.R.; Sayogo, D.S. Government Interorganizational Information Sharing Initiatives: Understanding the Main Determinants of Success. Gov. Inf. Q. 2016, 33, 572–582. [Google Scholar] [CrossRef]
- Bigdeli, A.A.Z.; Kamal, B.M.M.; Cesare, C.S.D. Electronic Information Sharing in Local Government Authorities: Factors Influencing the Decision-making Process. Int. J. Inf. Manag. 2013, 33, 816–830. [Google Scholar] [CrossRef]
- Kowalczyk, S.; Shankar, K. Data-sharing in the Sciences. Annu. Rev. Inf. Sci. Technol. 2010, 45, 247–294. [Google Scholar] [CrossRef]
- Borgman, C.L. The Conundrum of Sharing Research Data. J. Am. Soc. Inf. Technol. 2012, 63, 1059–1078. [Google Scholar] [CrossRef]
- Wessels, B.; Finn, R.L.; Linde, P.; Mazzetti, P.; Nativi, S.; Riley, S.; Smallwood, R.; Taylor, M.J.; Tsoukala, V.; Wadhwa, K.; et al. Issues in the Development of Open Access to Research Data. Prometheus 2014, 32, 49–66. [Google Scholar] [CrossRef]
- Elvas, L.B.; Ferreira, J.C.; Dias, M.S.; Rosário, L.B. Health Data Sharing towards Knowledge Creation. Systems 2023, 11, 435. [Google Scholar] [CrossRef]
- Henriksen-Bulmer, J.; Faily, S.; Jeary, S. Privacy Risk Assessment in Context: A Meta-model Based on Contextual Integrity. Comput. Secur. 2019, 82, 270–283. [Google Scholar] [CrossRef]
- Lee, J.S.; Jun, S.P. Privacy-preserving Data Mining for Open Government Data from Heterogeneous Sources. Gov. Inf. Q. 2021, 38, e101544. [Google Scholar] [CrossRef]
- Cheng, X. Personal Data Rights in the Era of Big Data. Soc. Sci. China 2019, 40, 174–188. [Google Scholar]
- Schopfel, J.; Chaudiron, S.; Jacquemin, B.; Prost, H.; Severo, M.; Thiault, F. Open Access to Research Data in Electronic Theses and Dissertations: An Overview. Libr. Hi Tech 2014, 32, 612–627. [Google Scholar] [CrossRef]
- Lips, A.M.B.; O’neill, R.R.; Eppel, E.A. Cross-Agency Collaboration in New Zealand: An Empirical Study of Information Sharing Practices, Enablers and Barriers in Managing for Shared Social Outcomes. Int. J. Publ. Adm. 2011, 34, 255–266. [Google Scholar] [CrossRef]
- Fan, J.; Zhang, P.; Yen, D.C. G2G Information Sharing among Government Agencies. Inf. Manag. 2014, 51, 120–128. [Google Scholar] [CrossRef]
- Dawes, S. Interagency Information Sharing: Expected Benefits, Manageable Risks. J. Policy Anal. Mgmt. 1996, 15, 377–394. [Google Scholar] [CrossRef]
- Lim, D.S.K.; Morse, E.A.; Mitchell, R.K.; Seawright, K.K. Institutional Environment and Entrepreneurial Cognitions: A Comparative Business Systems Perspective. Entrep. Theory Pract. 2010, 34, 491–516. [Google Scholar] [CrossRef]
- Sturges, P.; Bamkin, M.; Anders, J.H.S.; Hubbard, B.; Hussain, A.; Heeley, M. Research Data Sharing: Developing a Stakeholder-Driven Model for Journal Policies. J. Assoc. Inf. Sci. Technol. 2015, 66, 2445–2455. [Google Scholar] [CrossRef]
- Dong, C.; Liu, J.; Mi, J. How to Enhance Data Sharing in Digital Government Construction: A Tripartite Stochastic Evolutionary Game Approach. Systems 2023, 11, 212. [Google Scholar] [CrossRef]
- Chawinga, W.D.; Zinn, S. Global Perspectives of Research Data Sharing, a Systematic Literature Review. Libr. Inf. Sci. Res. 2019, 41, 109–122. [Google Scholar] [CrossRef]
- Ghorashi, S.R.; Zia, T.; Bewong, M.; Jiang, Y. An Analytical Review of Industrial Privacy Frameworks and Regulations for Organisational Data Sharing. Appl. Sci. 2023, 13, 12727. [Google Scholar] [CrossRef]
- Joyce, A.; Javidroozi, V. Smart City Development, Data Sharing Vs. Data Protection Legislations. Cities 2024, 148, 104859. [Google Scholar] [CrossRef]
- Borycz, J.; Olendorf, R.; Specht, A.; Grant, B.; Crowston, K.; Tenopir, C.; Allard, S.; Rice, N.M.; Hu, R.; Sandusky, R.J. Perceived Benefits of Open Data Are Improving but Scientists Still Lack Resources, Skills, and Rewards. Humanit. Soc. Sci. Commun. 2023, 10, 1–12. [Google Scholar] [CrossRef]
- Loenen, B.; Kulk, S.; Ploeger, H. Data Protection Legislation: A Very Hungry Caterpillar: The Case of Mapping Data in the European Union. Gov. Inf. Q. 2016, 33, 338–345. [Google Scholar] [CrossRef]
- Nugroho, R.P.; Zuiderwijk, A.; Janssen, M.; de Jong, M. A Comparison of National Open Data Policies: Lessons Learned. Transform. Gov. People Process Policy 2015, 9, 286–308. [Google Scholar] [CrossRef]
- Tenopir, C.; Allard, S.; Douglass, K.; Aydinoglu, A.U.; Wu, L.; Read, E.; Manoff, M.; Frame, M. Data Sharing by Scientists: Practices and Perceptions. PLoS ONE 2017, 6, 21101. [Google Scholar] [CrossRef]
- Kim, Y.; Zhang, P. Understanding Data Sharing Behaviors of STEM Researchers: The Roles of Attitudes, Norms, and Data Repositories. Libr. Inf. Sci. Res. 2015, 37, 189–200. [Google Scholar] [CrossRef]
- Fecher, B.; Friesike, S.; Hebing, M. What Drives Academic Data Sharing? PLoS ONE 2015, 10, 0118053. [Google Scholar] [CrossRef]
- Sun, L.L.; Zhao, N.X. Identifying Key Influence Factors of the Scientific Data Sharing: Based on Meta- ethnography. Inf. Stud. Theory Appl. 2020, 43, 91–97+52. [Google Scholar]
- Berberi, I.; Roche, D.G. Reply to: Recognizing and Marshalling the Pre-Publication Error Correction Potential of Open Data for More Reproducible Science. Nat. Ecol. Evol. 2023, 7, 1595–1596. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Y.Z.; Cao, F.F. Gaming Analysis of Government Data Opening and Sharing in the Big Data Era Based on Incomplete Information Dynamic Model. Inf. Sci. 2018, 36, 17–22+87. [Google Scholar]
- Xu, X.K.; Li, Y.M.; Pang, Q.H. Evolutionary Game Analysis of Government Open Data Sharing in the Digital Economy. J. Intell. 2020, 39, 119–125,87. [Google Scholar]
- Wei, Y.H.; Chen, X.L.; Zou, X.F. Data Sharing, Corporate Strategy and Government Regulatory Incentives Based on Evolutionary Game. Financ. Econ. 2020, 64, 107–120. [Google Scholar]
- Xiao, Y.; Xu, W.; Zeng, S.; Peng, Q. Online User Information Sharing and Government Pandemic Prevention and Control Strategies-Based on Evolutionary Game Model. Front. Public Health 2021, 9, 747239. [Google Scholar] [CrossRef] [PubMed]
- Deng, W.B.; Dai, L.; Zhang, Z.C.; Fan, Z.F. Coordination Mechanism of Government Data Sharing Based on Evolutionary Game. Inf. Sci. 2023, 41, 10–19. [Google Scholar]
- Xu, H.; Zhou, Y.; Chen, H.K.Y. Evolutionary Game Analysis of Inter-Organizational Trust and Technology Sharing Behavior in Enterprise Collaborative Innovation. J. Intell. Fuzzy Syst. 2023, 45, 5723–5738. [Google Scholar] [CrossRef]
- Feng, Z.H.; Pei, X. Evolution of Data Sharing Behaviors between Platform Firms and the Government: Game Mechanism, Path Analysis and Policy Formation. Manag. Rev. 2023, 35, 175–187. [Google Scholar]
- Sun, G.Q.; Xie, Y.F. Blockchain Technology, Supply Chain Networks and Data Sharing: Based on the Perspective of Evolutionary Game. Chin. J. Manag. Sci. 2023, 31, 149–162. [Google Scholar]






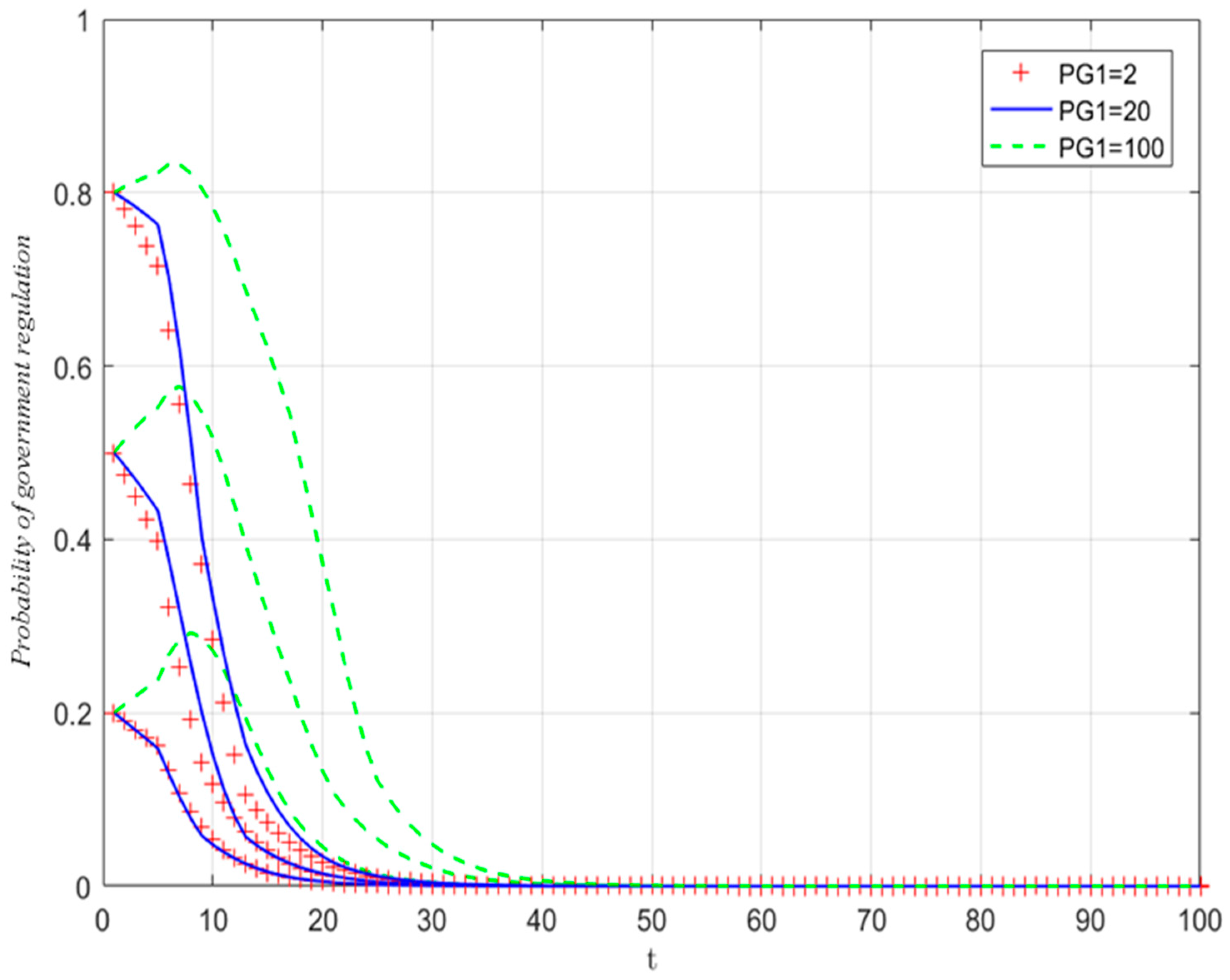
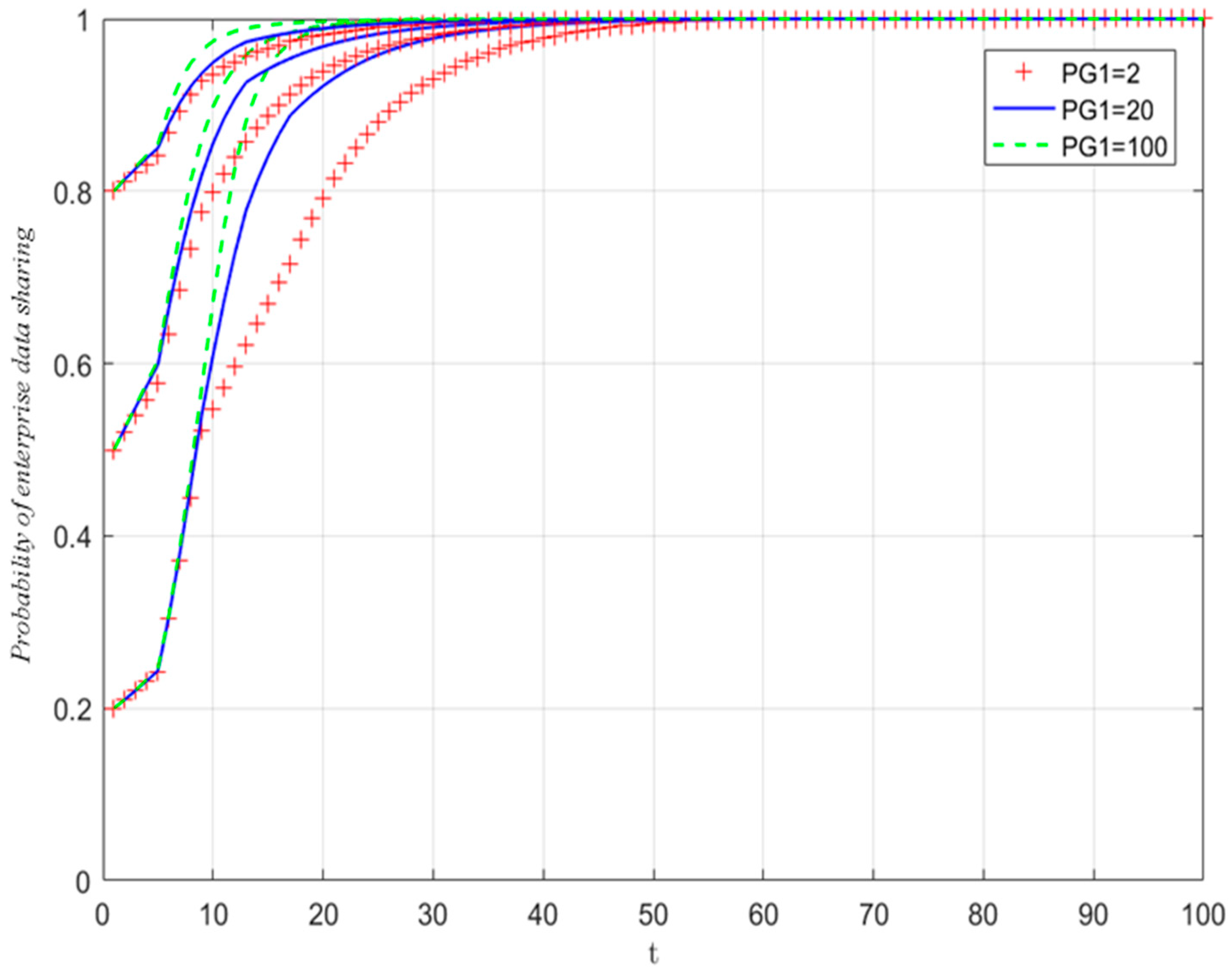


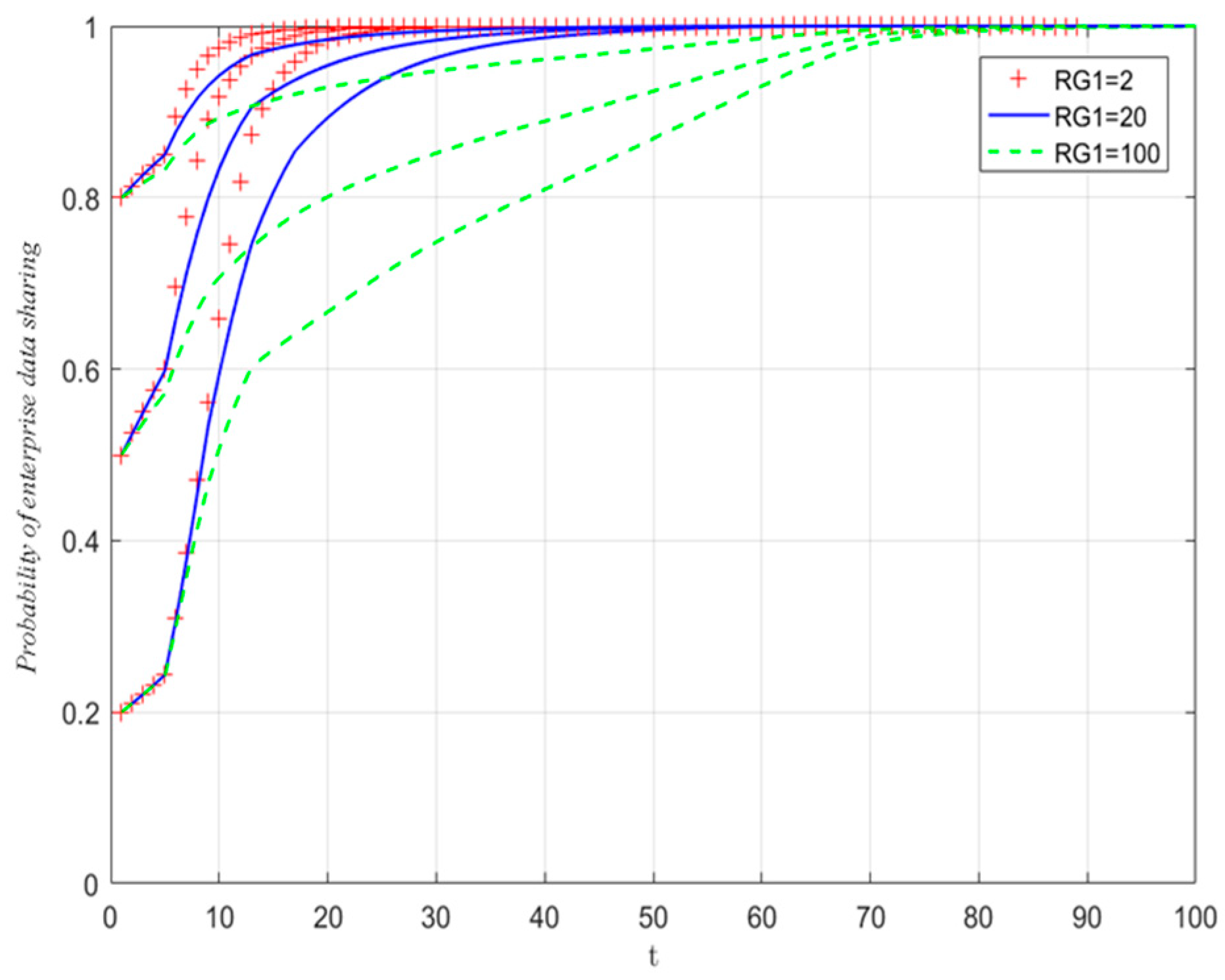
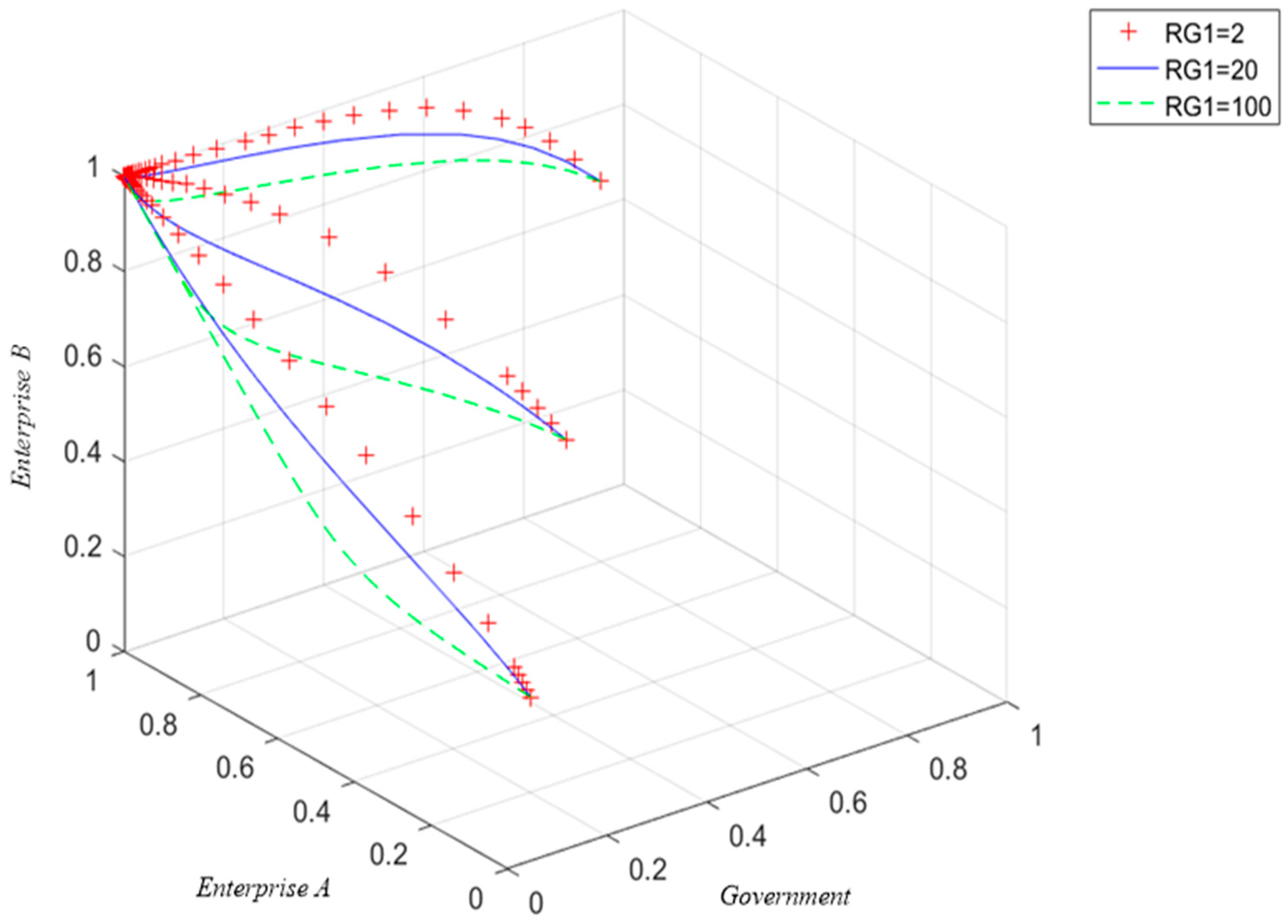


| Subjects | Parameter | Hidden Meaning |
|---|---|---|
| Government | CG1 | The cost to the government of choosing a regulation strategy |
| PG1 | Penalties for enterprises not sharing data during government regulation | |
| RG1 | Incentives for enterprises to respond positively to data sharing during government regulation | |
| BG1 | Macro benefits to the government when both enterprises engage in data sharing | |
| BG2 | Macro benefits to the government when one enterprise shares data and the other does not | |
| LG1 | Macro-governance losses suffered by the government when neither enterprise engages in data sharing | |
| Enterprise | CE1 | Data openness cost caused by enterprises choosing a data-sharing strategy |
| BE1 | Data retention benefits obtained by enterprises choosing no-data-sharing strategies | |
| CE2 | Compensation fees for the cost paid by an enterprise to obtain shared data from another enterprise | |
| RE1 | Data cooperation benefits from data sharing by another enterprise when this enterprise shares data | |
| LE1 | Data exchange imbalance loss suffered by one enterprise when it shares data, while the other enterprise does not share data | |
| RE2 | Data acquisition benefits from data sharing by another enterprise when this enterprise does not share data | |
| LE2 | Data closure loss suffered by one enterprise when it does not share data, and the other enterprise also does not share data |
| Behavior Strategy | Governments | Enterprise A | Enterprise B |
|---|---|---|---|
| (G1, A1, B1) | Regulation | Data-sharing | Data-sharing |
| (G1, A1, B2) | Regulation | Data-sharing | No-data-sharing |
| (G1, A2, B1) | Regulation | No-data-sharing | Data-sharing |
| (G1, A2, B2) | Regulation | No-data-sharing | No-data-sharing |
| (G2, A1, B1) | No-regulation | Data-sharing | Data-sharing |
| (G2, A1, B2) | No-regulation | Data-sharing | No-data-sharing |
| (G2, A2, B1) | No-regulation | No-data-sharing | Data-sharing |
| (G2, A2, B2) | No-regulation | No-data-sharing | No-data-sharing |
| Strategic Combination | Governments | Enterprise A | Enterprise B |
|---|---|---|---|
| (G1, A1, B1) | BG1 − 2RG1 − CG1 | RE1 + RG1 − CE1 | RE1 + RG1 − CE1 |
| (G1, A1, B2) | BG2 + PG1 − RG1 − CG1 | RG1 + CE2 − CE1 − LE1 | BE1 + RE2 − CE2 − PG1 |
| (G1, A2, B1) | BG2 + PG1 − RG1 − CG1 | BE1 + RE2 − CE2 − PG1 | RG1 + CE2 − CE1 − LE1 |
| (G1, A2, B2) | 2PG1 − LG1 − CG1 | BE1 − LE2 − PG1 | BE1 − LE2 − PG1 |
| (G2, A1, B1) | BG1 | RE1 − CE1 | RE1 − CE1 |
| (G2, A1, B2) | BG2 | CE2 − LE1 − CE1 | BE1 + RE2 − CE2 |
| (G2, A2, B1) | BG2 | BE1 + RE2 − CE2 | CE2 − LE1 − CE1 |
| (G2, A2, B2) | −LG1 | BE1 − LE2 | BE1 − LE2 |
| Equilibrium Point | λ1 | λ2 | λ3 |
|---|---|---|---|
| E1 (0, 0, 0) | 2PG1 − CG1 | CE2 − CE1 − BE1 − LE1 + LE2 | CE2 − CE1 − BE1 − LE1 + LE2 |
| E2 (1, 0, 0) | CG1 − 2PG1 | CE2 − CE1 − BE1 − LE1 + LE2 + PG1 + RG1 | CE2 − CE1 − BE1 − LE1 + LE2 + PG1 + RG1 |
| E3 (0, 1, 0) | PG1 − CG1 − RG1 | BE1 + CE1 − CE2 + LE1 − LE2 | CE2 − CE1 − BE1 + RE1 − RE2 |
| E4 (0, 0, 1) | PG1 − CG1 − RG1 | CE2 − CE1 − BE1 + RE1 − RE2 | BE1 + CE1 − CE2 + LE1 − LE2 |
| E5 (1, 1, 0) | CG1 − PG1 + RG1 | BE1 + CE1 − CE2 + LE1 − LE2 − PG1 − RG1 | CE2 − CE1 − BE1 + PG1 + RE1 − RE2 + RG1 |
| E6 (1, 0, 1) | CG1 − PG1 + RG1 | CE2 − CE1 − BE1 + PG1 + RE1 − RE2 + RG1 | BE1 + CE1 − CE2 + LE1 − LE2 − PG1 − RG1 |
| E7 (0, 1, 1) | −CG1 − 2RG1 | BE1 + CE1 − CE2 − RE1 + RE2 | BE1 + CE1 − CE2 − RE1 + RE2 |
| E8 (1, 1, 1) | CG1 + 2RG1 | BE1 + CE1 − CE2 − PG1 − RE1 + RE2 − RG1 | BE1 + CE1 − CE2 − PG1 − RE1 + RE2 − RG1 |
| Equilibrium Point | λ1 | λ2 | λ3 | Stability | Stable Condition |
|---|---|---|---|---|---|
| E1 (0, 0, 0) | ± | ± | ± | ESS | 2PG1 < CG1,CE2 + LE2 < CE1 + BE1 + LE1 |
| E2 (1, 0, 0) | ± | ± | ± | ESS | CG1 < 2PG1,CE2 + LE2 + PG1 + RG1 < CE1 + BE1 + LE1 |
| E3 (0, 1, 0) | ± | +/− | −/+ | Instability | / |
| E4 (0, 0, 1) | ± | +/− | −/+ | Instability | / |
| E5 (1, 1, 0) | ± | +/− | −/+ | Instability | / |
| E6 (1, 0, 1) | ± | +/− | −/+ | Instability | / |
| E7 (0, 1, 1) | − | ± | ± | ESS | BE1 + CE1 + RE2 < CE2 + RE1 |
| E8 (1, 1, 1) | + | ± | ± | Instability | / |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, Y.; Sun, Z.; Qiu, L. A Tripartite Evolutionary Game Analysis of Enterprise Data Sharing Under Government Regulations. Systems 2025, 13, 151. https://doi.org/10.3390/systems13030151
Dong Y, Sun Z, Qiu L. A Tripartite Evolutionary Game Analysis of Enterprise Data Sharing Under Government Regulations. Systems. 2025; 13(3):151. https://doi.org/10.3390/systems13030151
Chicago/Turabian StyleDong, Ying, Zhongyuan Sun, and Luyi Qiu. 2025. "A Tripartite Evolutionary Game Analysis of Enterprise Data Sharing Under Government Regulations" Systems 13, no. 3: 151. https://doi.org/10.3390/systems13030151
APA StyleDong, Y., Sun, Z., & Qiu, L. (2025). A Tripartite Evolutionary Game Analysis of Enterprise Data Sharing Under Government Regulations. Systems, 13(3), 151. https://doi.org/10.3390/systems13030151








