DEFS—Data Exchange with Free Sample Protocol
Abstract
:1. Introduction
2. Background
2.1. Distributed Ledger Technologies
2.2. Smart Contracts
2.3. Merkle Hash Trees
3. State of the Art
4. Data Exchange Protocol
4.1. Protocol Overview
- Protocol preparation. In this initial phase, the provider prepares not only the data to be exchanged but also all the parameters and cryptographic material necessary to demonstrate that the data exchange is secure and private. More specifically, the provider:
- Divides the complete dataset in portions. These portions are chosen randomly (not consecutively) from the dataset.
- Generates a seed to generate symmetric cryptographic keys.
- Uses these keys to create a MHT, whose root can be used to check the correctness of this cryptographic material.
- Encrypts a random permutation of the data portions with the keys, obtaining an encrypted and randomised version of the whole dataset.
- Creates another MHT using the hashes of these cryptograms as leaves, whose root can be used to verify the correctness of the cryptograms generated.
- Deploys a smart contract in the blockchain that includes among other information, the roots of the previous trees.
If a consumer has interest in obtaining the dataset, the protocol continues as follows:- The consumer receives the whole dataset encrypted but it cannot be decrypted at that very moment.
- The consumer queries the smart contract to obtain the root of the tree of cryptograms and verifies that all the cryptograms belong to this tree.
As previously stated, this is only a brief summary of the steps to follow in this phase. A more exhaustive explanation of the protocol preparation phase can be found in Section 4.3.3. At this point, all entities (consumer, provider, and smart contract) are ready to start the protocol execution phase, in which the consumer will have access to the complete dataset and will perform the payment. - Protocol execution. In this phase, the consumer gets some samples of the dataset (for free) to evaluate if it is worth to pay for the whole set, and if so, he will obtain the dataset and the provider will get paid:
- The consumer chooses at random some sample portions to be revealed. Note that the provider committed the shuffled encrypted data at the very beginning of the protocol. Since the consumer requests random samples, neither consumers nor providers have control over the samples that will be revealed.
- The provider discloses the keys for those samples so the consumer can evaluate the quality of the dataset.
- If the consumer is not convinced, the protocol ends here. However, if they decides that it is worth paying for the dataset, they commit the payment to the smart contract.
- The provider is asked to publish the seed (that will disclose all the encryption keys) in the smart contract.
- If the consumer is able to properly decrypt the dataset, after a timeout, the provider gets paid and the protocol ends.
- If the consumer is able to prove that there were problems with the previous procedure, he starts a conflict resolution phase to obtain a refund.
A more exhaustive explanation of the protocol execution phase can be found in Section 4.3.4.The following phase will only be needed in case the consumer considers that he has been cheated on. - Conflict resolution. This phase is optional and only takes place if the consumer detects provider misbehaviour. The conflict resolution can end with a refund if the consumer is able to demonstrate one of the following misbehaviours:
- A key is not properly generated.
- A cryptogram does not have the proper format when decrypted.
A more exhaustive explanation can be found in Section 4.3.5.
4.2. Protocol Properties
- Data sample evaluation. The consumer gets a free set of fair samples of the data being traded before paying. The protocol ensures that neither the consumer nor the provider are able to manipulate the chosen data or select specific samples.
- Payment guarantees. The provider gets paid if and only if the consumer has access to the whole set of data. That is, the consumer cannot get the data without paying for it and the provider does not get paid without disclosing the data.
- The solution is cost-efficient. Due to high fees on public ledgers, DEFS minimises the amount of data stored on the ledger, which is also independent of the quantity of data traded. This way, both the amount of data stored and the number of interactions with the distributed ledger are constant.
- Non-repudiation. The DEFS protocol ensures that any party involved in the exchange is not able to cancel and/or deny the data exchange once an agreement is made.
- Liveness. The different timeouts guarantee that the protocol reaches a final state, even when one of the parties quits in advance.
4.3. The DEFS Protocol
4.3.1. Requirements
- Secure off-chain channel between provider and consumer: It is assumed that the off-chain channel between consumer and provider is end-to-end protected. This requirement can be easily met by using the widely supported TLS protocol—e.g., with HTTPS. TLS only requires the server to hold a valid certificate (and its complementary private key) in order to create the secure channel. That is to say, consumers just need a valid TLS client, which is implemented by default in most programming languages, application frameworks, and/or web browsers.
- Validation of data blocks’ format: It is assumed that consumers can verify received data blocks according to a previously agreed schema. The process that verifies that a data portion meets a predefined format is usually called a validator. Validators are used by many technologies to check received responses before processing them. In object-oriented programming, this process is usually done by trying to parse the response as a given type of object, which will produce an error if it does not. There are also specific standards with well-known implementations, such as JSON-LD [24], that help define and validate specific data schemas.
- Identification system: The DEFS protocol releases random samples of the dataset to potential consumers before they commit paying for the entire dataset. However, there is a risk of an attacker using multiple identities to retrieve a representative portion of the dataset for free. In this context, DEFS assumes that there are off-chain solutions run by the providers which could effectively limit the amount of identities an attacker could take. A known example is binding the identity to an e-mail account or a mobile phone. The provider should decide the most suitable authentication method depending on the price of the traded data and the type of consumers. For example, in some cases, authenticating with an e-mail can be enough. In other scenarios, e-mail might not be enough because it is not hard to generate multiple “identities” based on different e-mail accounts. In the latter case, providers might require authenticating with a mobile phone or even with both factors. In some specific cases, authentication could involve more factors, such as physical key generators, smart cards, etc.
4.3.2. Notation
4.3.3. Protocol Preparation
- Consumer→Provider: Request .The protocol starts with the consumer’s interest in a dataset. Through the marketplace, the consumer requests some offered to the provider. Note that each time the consumer desires a dataset, a new instance of the DEFS protocol is required.
- Provider: Set .In this step the provider has to decide the main parameters associated to the dataset. These parameters are the identifier of the data exchange (); the price of the dataset (p); the number of portions in which the dataset will be divided (n); the number of sample portions to be revealed before the payment (v); and, finally, the associated amount of cryptocurrency to ensure a complete refund in case a conflict resolution ends in favour of the consumer ().How to choose v depends on the identification system in use (see Section 4.3.1) and the resilience from providing, for free, a representative part of the dataset to one or multiple attackers. The analysis in Section 5.3 shows how to properly choose v based on the size of the dataset and the estimated amount of identities an attacker can hold.
- Provider: Generate s.The provider should generate the symmetric encryption keys in such a way that in the case of disclosing some of them, the consumer will not be able to derive any other key (or the whole set). In addition, the consumer must be able to easily derive all the keys when they agree to buy the dataset. A simple way to achieve these features is by generating an initially private seed and to use a cryptographic hash function to compute the whole set of keys. For that reason, the seed s is calculated using a random number generator.
- Provider: Compute ] | ∀i ∈{0…n − 1}.The provider has to compute a set of n symmetric encryption keys (). In DEFS, we compute each key as the hash function, for instance Keccak256, of the sum of the seed s and the index i using the following formula:This construction has the expected properties: without the seed s the consumer cannot derive any other key, but once the seed is known, it is easy for the consumer to calculate the whole sequence of keys.
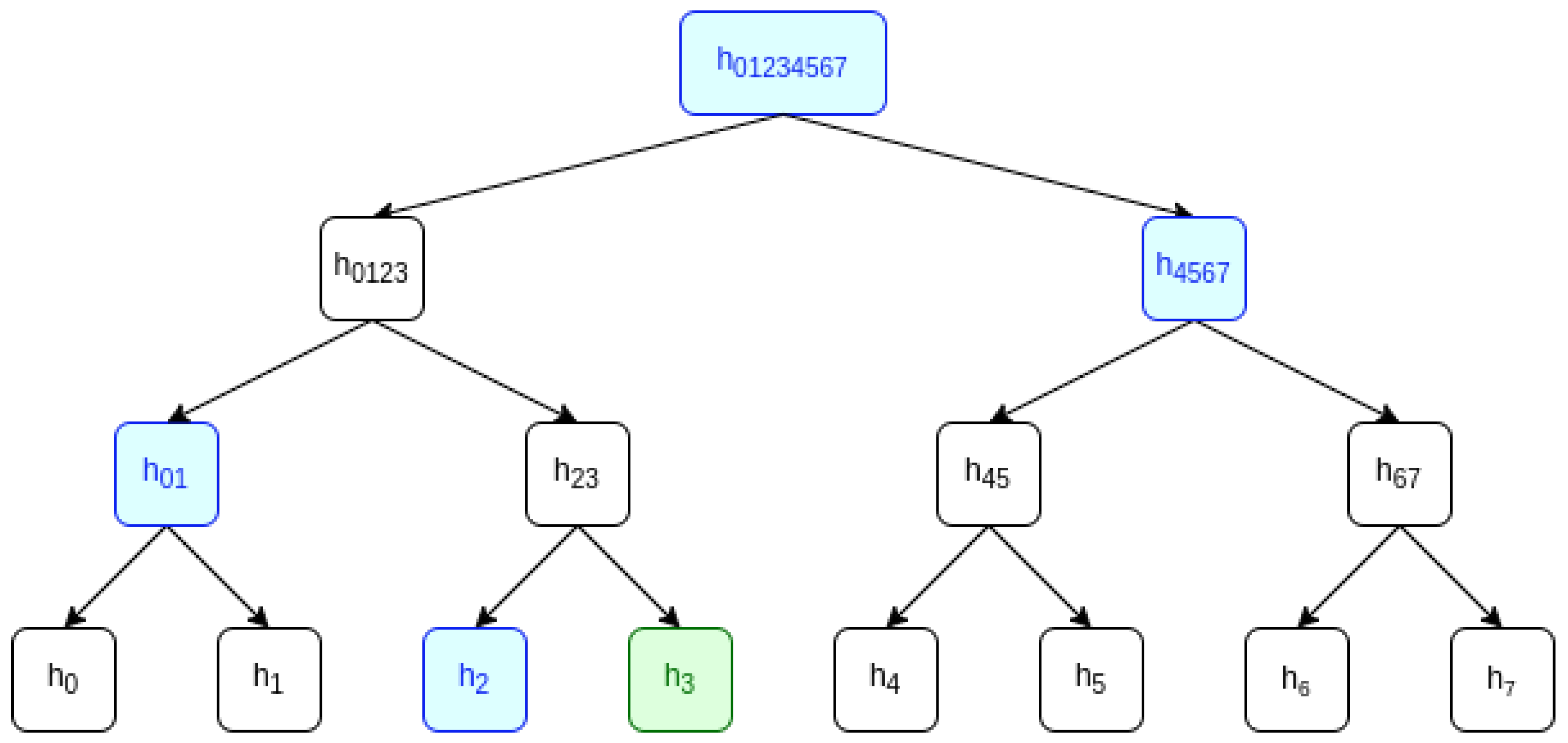
- Provider: Generate .The provider builds a binary MHT for the set of keys, which is going to be used to generate the proof of the correctness of the keys used to encrypt the data portions. We denote the MHT of encryption keys as , its root , and we refer to a membership proof of a leaf i as . Figure 4 shows an example of a . An exhaustive explanation about the algorithm to construct these trees can be found in [25]. Here, we will simply include a brief summary of this algorithm. To construct the , keys must be sorted by using their indexes, from 0 to . The leaves of the tree are calculated by hashing the keys in their respective position (hashed keys). The rest of the intermediate nodes in upper levels are just calculated by hashing the concatenation of the lower left and right nodes of the same branch. The tree construction continues until reaching the top level, in which we obtain the . Notice that the is the digest of the complete key set K, and it can be used as a proof of its correctness. It is also important to remark that the algorithm to construct this tree should be public, and all the entities have to use the same algorithm because any change in the keys or in the order of constructing it will cause an avalanche effect that will result in the root being completely different.
- Provider: Generate ] | ∀i .Now, using the pre-existing data to be exchanged, the provider has to build an array () with the portions where each has the corresponding data and the index as a header ). This format is going to allow the smart contract to determine if the cryptograms have been properly generated. It is also important to note that each data portion contains a group of random registries, not consecutive ones. To do that, registries are sorted using an external random generator tool provided by the marketplace, which should be open source and auditable to avoid duplicated entries in the same portion. This will avoid a potential attack where the consumer replicates several data requests to obtain free samples without committing any payment. More details about potential attacks can be found in Section 5.3.
- Provider: Encrypt data. ] | = ()∀i .Now the provider is able to encrypt all the portions of the dataset , and obtain the set of cryptograms C.
- Provider: Generate .The provider builds a binary MHT for the set of cryptograms, which is going to be the proof of their correctness. We denote the MHT of cryptograms as , its root , and we refer to a membership proof of a leaf i as . Figure 5 shows an example of an . The algorithm of the is the same as the , but just changing the information used to construct it. Cryptograms are sorted by using their indexes, from 0 to . The leaves of the tree are calculated by hashing the cryptograms in their respective position (hashed encrypted data). The rest of the intermediate nodes in upper levels are just calculated by hashing the concatenation of the lower left and right nodes of the same branch. The tree construction continues until reaching the top level, in which we obtain the root of the Merkle hash tree of cryptograms (). Note that the is the digest of the complete set C, and it can be used as a proof of its correctness.
- Provider→SC: Deploy smart contract with parameters (, n, p, v, , , ).Next, the provider deploys a smart contract in a ledger that stores the data-exchange identifier (), the total number of portions (n), the number of sample portions to be revealed before the payment, the price (p) of the dataset, and the amount of cryptocurrency to assure the fairness from the provider on the conflict resolution process (), and the root of both Merkle hash trees (,). These roots will allow proving whether an element is or is not a cryptogram or a key and its position in the MHT. Using this, the system is able to efficiently assure the consumer that the provider cannot alter the committed dataset.
- Provider→Consumer: Send and the complete set of cryptograms (C).Finally, the provider delivers the smart contract address, the data-exchange identifier , and the complete set of cryptograms C to the consumer. Obviously, it would be totally impractical to exchange that amount of data using the ledger as storage. Instead, the exchange of cryptograms between the provider and consumer is done off-blockchain. Notice also that since the seed will be public at the end of the process, all the off-blockchain traffic must have been exchanged using a secure channel.
- Consumer→SC: Request data from .At this point, the consumer has the which is related to the deployed smart contract and can read the values set by the provider in step 9.
- SC→Consumer: Reply with values n, p, v, , .Now the consumer has the total number of portions (n), the number of samples they can obtain before committing the payment (v), the price of the data (p), the Merkle roots of both trees (,), and the complete set of cryptograms (C).
- Consumer: Compute and verify .As the consumer has the complete set of cryptograms C, he has the capability and responsibility to re-generate to verify that the root calculated is coherent with the one at the smart contract. If so, the consumer knows that all cryptograms ∀i were properly generated and match the . The consumer is responsible for verifying the at this very moment, and if he continues with the protocol, tacitly accepts the correctness of the generation of the cryptograms. This means that in the case of later conflict resolution, the consumer cannot argue that the cryptograms were wrongly generated to get a refund.
4.3.4. Protocol Execution
- Consumer: Generate R = [] | ∀ ∈{}.The consumer selects, at random, the set of indexes R which correspond to the sample portions to be revealed (for free). We consider that the provider should not decide on its own which data samples will be revealed because they could decide to use a biased (not fair) set of samples. The consumer is also not able to purposely choose particular registries because the dataset was previously randomly sorted by the provider. Therefore, the consumer will choose an array of v values, at random, within the range 0 to , corresponding to the indexes of the sample portions. As none of the entities control which registries are going to be disclosed, the fairness of this process is assured.
- Consumer→Provider: Request R which contains v indexes to be revealed.The consumer informs the provider of the v indexes of the sample portions to be revealed (R).
- Provider→Consumer: Return and ∀i∈{R}.The provider discloses the keys associated with the v indexes and the Merkle proofs to verify them in the . This process is done totally off-blockchain. Note that allowing the consumer to choose v sample portions with no cost could result in attacks as the consumer could try to get a large amount of free data by repeating the process of getting small samples. We do not consider this attack especially dangerous because the consumer cannot choose particular registries of the dataset. In addition, the provider can decide how many times consumers are allowed to get a sample set without making a final deal, and they can use the marketplace to blacklist abusive consumers. Nonetheless, a comprehensive analysis of potential attacks is made in Section 5.3. As shown in the analysis, the provider should carefully choose v and n to minimise the impact of such attacks.
- Consumer: Verify each proof. ∀i ∈{R}.The customer should verify that the proofs sent by the provider match the . To provide a partial example, consider the case of Figure 4, in which . Let us consider the case of one single sample portion , and the consumer has chosen index 3 to disclose. In this case, is sent to the consumer, and the proofs of the correctness are = (,). The consumer should verify if the following expression matches:Note that the expression is just calculating the root of , and comparing it with the value published in the smart contract. If the values match, the key can be considered valid as it matches the proofs, and the consumer will continue with the protocol. If not, that means that the provider did not send the proper proofs and that the key is not verifiable. In this case, the consumer can abandon the protocol.
- Consumer: Decrypt and verify each data sample.Now that the consumer is sure that the v keys are valid, he can decrypt the sample portions with the received keys:Once this is done, the consumer has to verify that the resulting data portions have the expected format:If not, the data samples are invalid, and the consumer can end the protocol at this moment. If the format is valid, the consumer will evaluate the data samples ∀i ∈ R. If the samples do not convince the consumer to pay for the whole dataset, the protocol ends here, but if they do, they will continue with the following steps.
- Consumer→SC: Transaction committing payment.If the samples convinced the consumer, he will send a transaction to the smart contract with the payment (p) to buy the dataset.
- Consumer→SC: Subscription to seed revelation.The consumer also subscribes to the ‘seedReleased’ event, expecting to receive a notification when the provider publishes the seed to allow complete data decryption.
- (Timeout 1) Consumer→SC: Seed not released and the consumer is refunded.If the provider has not released the seed in time, a first timeout (Timeout 1) will expire, and after that, the smart contract will allow the consumer to refund the payment. This is an unhappy path in the protocol.
- Provider→SC: Transaction publishing the seed.The provider discloses the seed value s via a blockchain transaction before Timeout 1 expires. This is the happy path of the protocol.
- SC→Consumer: Event to consumer about seed revelation.As result of executing the transaction, the smart contract generates an event, and the consumer will be notified that the seed value s has been revealed. The smart contract stops Timeout 1 (due to seed revelation), and starts Timeout 2, allowing the consumer to start conflict resolution. Once that the consumer has the seed, they can derive all the keys:Now the consumer has all the cryptographic material to decrypt the cryptograms C but, previously, they had to verify that all the keys are correct. The procedure is similar to the one performed in Step 4, but with the difference that now the consumer has the capacity of re-generating the whole . If the consumer detects that (one or several) keys were not properly generated, they can start the optional phase of conflict resolution to obtain a refund. On the contrary, if all the keys were properly generated, the consumer can decrypt the previously received cryptograms C and access the whole dataset:The consumer also has to verify that the have the proper format, in the same manner that was done in Step 5 but for all the cryptograms. If the consumer detects that one or more cryptograms were not properly generated (they do not have the proper format), they can start the optional phase of conflict resolution to obtain a refund. Note that at this point, the consumer cannot argue that the cryptograms do not match the because this should have been verified in the protocol preparation phase. On the contrary, if all the cryptograms (once decrypted) have the proper format, the consumer has the complete dataset and can consider the protocol ended.
- (Timeout 2) Provider→SC: Withdraw and protocol end.If Timeout 2 expires, it means that the consumer considers that the keys were properly generated and the cryptograms have the proper format (because if not, they would have previously started the conflict resolution). In this case, the provider can send a transaction to the smart contract to withdraw the payment and end the protocol.
4.3.5. Conflict Resolution
- A key is not properly generated:When consumers obtain the seed s in Step 9 of the protocol execution phase, they are able to generate the whole set of keys K. The way to check if the set of keys is compliant or not is by generating the whole set K with the formula and also re-constructing the whole and verifying that the calculated root matches the one published in the smart contract. At this moment, a consumer can know that the registered MRK is incorrect. However, in general, he cannot detect which keys were not properly generated. Although not possible in general, there are particular cases in which the consumer can do the detection of wrong keys. The detection is possible when the wrong keys are either one of the keys used for encrypting the samples, or a sibling key of them. In both cases, the consumer has got an MPK from the provider that matches the registered MRK. Then, if one of those keys does not follow the agreed format hash (i + s), the consumer can send the hash of the wrong key, its MPK, and the index in conflict to prove to the smart contract that the provider committed an incorrect MRK. For simplicity, we will assume that the consumer detects one single not-compliant key , but this discussion is completely valid in the case of having multiple not compliant keys (DEFS does not distinguish between one or several not compliant keys, and in the case where it is demonstrated that one single key is not properly generated, the entire payment will be refunded to the consumer). The following are the steps that the consumer, smart contract, and provider have to follow during conflict resolution about a specific key . The associated sequence diagram is detailed in Figure 7:
- (1)
- Consumer→SC: tx: conflictKThis conflict resolution is performed with a transaction from the consumer to the smart contract calling the function ‘conflictK’. In this transaction, the consumer sends as parameters the problematic index (e), the hash of the invalid key (), and its associated proof ().
- (2)
- SC: Verify with theThe smart contract verifies that and match the MRK from Step 9.
- (3)
- SC: Verify !=The smart contract verifies whether matches or not. If there is a match, it means that the provider did not cheat, while if the check does not match, then it means that the provider cheated.
- (4)
- SC: Provider cheatingIf the provider cheated, the smart contract refunds the consumer. In this case, the consumer receives the price of the data (p) and also the cost of the transactions he sent. The cost of the transactions is taken from the provider’s .
- (5)
- SC: Provider not cheatingIf the provider did not cheat, the smart contract automatically transfers the payment (p) to the provider.
- Cryptograms do not have the proper format:This situation happens when there is a conflict in D, and so one or several data portions do not have the proper format. Just a remark that there was a previous checking of this type in Step 5 of the protocol execution phase, in which v of the possible sample portions were tested to see if they had the proper format:However, not all the data portions were tested (only v of n). For simplicity, we will assume that there is one single not-compliant portion , but this discussion is completely valid in case of having multiple not compliant portions.This scenario implies that the decryption of a results in a that does not correspond with the expected format . Specifically, the decrypted cryptogram does not start with the expected index (e). In this case, the consumer can start the conflict resolution about the format of data. Figure 8 shows the sequence diagram about this scenario.
- (1)
- tx: conflictD:The conflict resolution about a starts with a transaction from the consumer to the smart contract. To do that, the transaction calls the smart contract function ‘conflictD’ and sends as parameters the problematic index (e), the cryptogram involved , and the proofs of the validity of this particular cryptogram. The intention of the consumer is to show that the cryptogram was properly generated by the provider, but that after decrypting it with , the resulting data portion has a bad format.In this case, the protocol can be resolved in a single transaction from the consumer, because the smart contract can compute . Note that there is no need for an extra timeout because the provider does not need to send anything, and all the proofs are available for the smart contract to compute.
- (2)
- Verify:The smart contract has to verify that the cryptogram provided by the consumer is valid, that is to say, that calculating for the problematic cryptogram from is coherent with the root stored in the smart contract. To provide some piece of example, consider the case of Figure 5, in which . Let us consider the case of demonstrating that is properly generated. In this case, the proofs of the correctness of are = (,). The smart contract should verify if this expression matches:Notice that the expression is just calculating the root of , and comparing it with the value published in the smart contract. If these values match, the cryptogram can be considered valid as it matches the proofs, and the protocol continues with the following step. If not, the consumer did not send the proper proofs to demonstrate that the provider was cheating and that the withdrawal of the money is automatically received as shown in Step (7).
- (3)
- Compute :Now the smart contract knows that the cryptogram is valid. Next, the smart contract computes the associated key . Remember that s was published by means of the transaction sent in Step 9 of the protocol execution phase.
- (4)
- Decrypt :The smart contract has the valid key and the valid cryptogram, so it is able to decrypt and obtain =().
- (5)
- Verify format:The smart contract can verify if the data portion has the correct format.
- (6)
- refund:If the data portion does not start with the index e, the provider was cheating, so the transaction ends transferring the costs (p+) to the consumer.
- (7)
- withdraw:If the data portion start with the index e, the provider was not cheating, and the transaction ends transferring the payment (p) and the to the provider.
- Cryptograms are not properly generated:This case happens when there is a conflict in C and one or several cryptograms do not match the root of the tree . As previously stated, the consumer receives all the cryptograms C in Step 10 of the protocol preparation and verifies the correctness of the whole set of cryptograms in Step 13. The consumer was responsible for verifying the at this very moment, and if any problem during this checking was found, the protocol will simply be aborted before committing any payment. However, if the consumer continued with the protocol, they were tacitly accepting the correctness of the generation of the cryptograms and the corresponding and . In case the consumer detects a cryptogram () not matching the at the protocol execution or protocol resolution phases, they cannot try to get a refund, and for this reason, the conflict resolution is not considering that case.
- Dataset is of bad quality:This case happens when the consumer obtains a valid data portion (with the correct format , but the content does not have the quality expected by the consumer. In this particular case, the DEFS protocol is not able to consider the quality of the dataset (most probably, assessing the goodness of a dataset requires human interaction and cannot be made automatically by the smart contract), so this case is out of its scope of discussion and no refund can be requested from the consumer’s side. The v sample portions that were disclosed in Step 5 of the protocol execution (for free, prior to any payment) alleviate this possibility. In any case, the marketplace can consider having a reputation tool to value data providers and try to avoid this kind of behaviour.
4.3.6. State Diagram
5. Security Analysis
5.1. Protection against Channel Attacks
5.2. Consumer’s Protection against Provider Attacks
5.3. Provider’s Protection against Consumer Attacks
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| API | application programming interface |
| DEFS | data exchange with free sample |
| DLT | distributed ledger technology |
| IPFS | interplanetary file system |
| MHT | Merkle hash tree |
| MR | Merkle hash root |
| MP | Merkle proof |
| MPC | Merkle proof of cryptograms |
| MPK | Merkle proof of encryption keys |
| MRK | root of the Merkle hash tree of keys |
| MRC | root of the Merkle hash tree of cryptograms |
| TTP | trusted third party |
| SC | smart contract |
| SDTE | secure data trading ecosystem |
References
- Gopalkrishnan, V.; Steier, D.; Lewis, H.; Guszcza, J. Big Data, Big Business: Bridging the Gap. In Proceedings of the 1st International Workshop on Big Data, Streams and Heterogeneous Source Mining: Algorithms, Systems, Programming Models and Applications, Beijing, China, 12 August 2012; BigMine ’12. Association for Computing Machinery: New York, NY, USA, 2012; pp. 7–11. [Google Scholar] [CrossRef]
- Thomas, L.D.W.; Leiponen, A. Big data commercialization. IEEE Eng. Manag. Rev. 2016, 44, 74–90. [Google Scholar] [CrossRef]
- Ravi, N.; Sunitha, N.R. Introduction of Blockchain to Mitigate The Trusted Third Party Auditing for Cloud Security: An Overview. In Proceedings of the 2017 2nd International Conference On Emerging Computation and Information Technologies (ICECIT), Tumakuru, India, 15–16 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Bashir, I. Mastering Blockchain; Packt Publishing Ltd.: Birmingham, UK, 2017. [Google Scholar]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain Technology Overview. 2019. Available online: https://arxiv.org/abs/1906.11078 (accessed on 10 May 2021).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. White Pap. 2014, 151, 1–32. [Google Scholar]
- Haider, F. Compact Sparse Merkle Trees. Cryptology ePrint Archive, Report 2018/955. 2018. Available online: https://eprint.iacr.org/2018/955 (accessed on 1 June 2021).
- Dahlberg, R.; Pulls, T.; Peeters, R. Efficient Sparse Merkle Trees: Caching Strategies and Secure (Non-)Membership Proofs. Cryptology ePrint Archive, Report 2016/683. 2016. Available online: https://eprint.iacr.org/2016/683 (accessed on 1 June 2021).
- Al-Kuwari, S.; Davenport, J.H.; Bradford, R.J. Cryptographic Hash Functions: Recent Design Trends and Security Notions. Cryptology ePrint Archive, Report 2011/565. 2011. Available online: https://eprint.iacr.org/2011/565 (accessed on 1 June 2021).
- Yoo, H.; Ko, N. Blockchain based Data Marketplace System. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 21–23 October 2020; pp. 1255–1257. [Google Scholar] [CrossRef]
- Mikkelsen, L.; Mortensen, K.; Rasmussen, H.; Schwefel, H.P.; Madsen, T. Realization and Evaluation of Marketplace Functionalities Using Ethereum Blockchain. In Proceedings of the 2018 International Conference on Internet of Things, Embedded Systems and Communications (IINTEC), Hammamet, Tunisia, 20–22 December 2018; pp. 47–52. [Google Scholar] [CrossRef]
- Ranganthan, V.P.; Dantu, R.; Paul, A.; Mears, P.; Morozov, K. A Decentralized Marketplace Application on the Ethereum Blockchain. In Proceedings of the 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018; pp. 90–97. [Google Scholar] [CrossRef]
- Braud, A.; Fromentoux, G.; Radier, B.; Le Grand, O. The Road to European Digital Sovereignty with Gaia-X and IDSA. IEEE Netw. 2021, 35, 4–5. [Google Scholar] [CrossRef]
- Özyilmaz, K.R.; Doğan, M.; Yurdakul, A. IDMoB: IoT Data Marketplace on Blockchain. In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 11–19. [Google Scholar] [CrossRef] [Green Version]
- Nguyen, D.D.; Ali, M.I. Enabling On-Demand Decentralized IoT Collectability Marketplace using Blockchain and Crowdsensing. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Tzianos, P.; Pipelidis, G.; Tsiamitros, N. Hermes: An Open and Transparent Marketplace for IoT Sensor Data over Distributed Ledgers. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 167–170. [Google Scholar] [CrossRef]
- Arya, V.; Sen, S.; Kodeswaran, P. Blockchain Enabled Trustless API Marketplace. In Proceedings of the 2020 International Conference on COMmunication Systems NETworkS (COMSNETS), Bengaluru, India, 7–11 January 2020; pp. 731–735. [Google Scholar] [CrossRef] [Green Version]
- Musso, S.; Perboli, G.; Rosano, M.; Manfredi, A. A Decentralized Marketplace for M2M Economy for Smart Cities. In Proceedings of the 2019 IEEE 28th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Napoli, Italy, 12–14 June 2019; pp. 27–30. [Google Scholar] [CrossRef]
- Ramachandran, G.S.; Radhakrishnan, R.; Krishnamachari, B. Towards a Decentralized Data Marketplace for Smart Cities. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MI, USA, 16–19 September 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Jeong, B.G.; Youn, T.Y.; Jho, N.S.; Shin, S.U. Blockchain-Based Data Sharing and Trading Model for the Connected Car. Sensors 2020, 20, 3141. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.N.; Feng, X.; Xie, J.; Feng, H.; Guan, Z.; Wu, Q. A decentralized and secure blockchain platform for open fair data trading. Concurr. Comput. Pract. Exp. 2020, 32, e5578. [Google Scholar] [CrossRef]
- Ma, S.; Mu, Y.; Susilo, W. A Generic Scheme of plaintext-checkable database encryption. Inf. Sci. 2018, 429, 88–101. [Google Scholar] [CrossRef]
- Dai, W.; Dai, C.; Choo, K.K.R.; Cui, C.; Zou, D.; Jin, H. SDTE: A Secure Blockchain-Based Data Trading Ecosystem. IEEE Trans. Inf. Forensics Secur. 2020, 15, 725–737. [Google Scholar] [CrossRef]
- Standardization Initiativ, P. JSON for Linking Data. 2021. Available online: https://json-ld.org/ (accessed on 1 June 2021).
- Muñoz, J.; Forne, J.; Esparza, O. Certificate revocation system implementation based on the Merkle hash tree. Int. J. Inf. Secur. 2004, 2, 110–124. [Google Scholar] [CrossRef] [Green Version]
- Mansour, T.; Schork, M. Commutation Relations, Normal Ordering, and Stirling Numbers; Discrete Mathematics and Its Applications; Chapman and Hall/CRC: Boca Raton, FL, USA, 2015. [Google Scholar]
Short Biography of Authors
 | Rafael Genés-Durán is currently a PhD candidate of the Information Security Group (ISG) doing research in distributed ledger technologies and zero-knowledge proofs at Universitat Politècnica de Catalunya. He holds a B.S. degree in Telecommunications Engineering (2017) and a Master in Informatics Engineering (2019). Contact him at [email protected]. |
 | Juan Hernández-Serrano is an associate professor of the Department of Network Engineering of the Universitat Politècnica de Catalunya in Spain, and a researcher of the Information Security Group (ISG). He holds an M.S. in Network Engineering (2002) and a Ph.D. in the field of information security (2008). His research interests has been focused on different aspects of networks security and privacy, including IoT, distributed ledgers, cognitive radio networks, M2M, smart grids, eVoting and digital forensics. Contact him at [email protected]. |
 | Oscar Esparza is working as associate professor of the Department of Network Engineering of the Universitat Politècnica de Catalunya. He holds an M.S. in Telecommunications Engineering (1999) and a PhD in Security Engineering (2004). His expertise areas are related to network security and applied cryptography. Since 2017 he leads the Information Security Group (ISG) of the UPC. Contact him at [email protected]. |
 | Marta Bellés-Muñoz received her B.S. degree in Mathematics at Universitat Autònoma de Barcelona and continued her Master studies at Aarhus Universitet, where she focused on the study of elliptic curves and isogeny-based cryptography. She is currently a PhD student doing research on security and efficiency of arithmetic circuits for zero-knowledge proofs at Universitat Pompeu Fabra in collaboration with Dusk Network. Contact her at [email protected]. |
 | Jose L. Muñoz-Tapia is a researcher of the Information Security Group (ISG) and an associate professor of the Department of Network Engineering of the Universitat Politècnica de Catalunya. He holds an M.S. in Telecommunications Engineering (1999) and a PhD in Security Engineering (2003). He has worked in applied cryptography, network security and game theory models applied to networks and simulators. His research focus has now tuned to distributed ledger technologies, and he is the director of the Master program in Blockchain technologies at UPC School. Contact him at [email protected]. |










| Notation | Description |
|---|---|
| Price that the provider must pay in order to ensure fairness. | |
| Encrypted data portions (cryptograms) such that . | |
| Data portions. | |
| e | Index of an invalid cryptogram. |
| Data-exchange identifier. | |
| Encryption keys for data portions, such that . | |
| Merkle hash tree of cryptograms. | |
| Merkle hash tree of keys. | |
| Root of the Merkle hash tree of cryptograms. | |
| Root of the Merkle hash tree of keys. | |
| Merkle proof of a cryptogram with index i. | |
| Merkle proof of an encryption key with index i. | |
| n | Number of data portions. |
| p | Price of the dataset. |
| Set of indexes of the sample portions to be revealed. | |
| s | Seed. Random number for key generation. |
| v | Number of sample portions to be revealed. |
| n | v | Probability of Getting the Whole Dataset | |
|---|---|---|---|
| 10 | 1 | 10 | |
| 100 | 10 | 10 | |
| 1000 | 100 | 10 | |
| 10,000 | 1000 | 10 | ∼ |
| 100,000 | 10,000 | 10 | ∼ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Genés-Durán, R.; Hernández-Serrano, J.; Esparza, O.; Bellés-Muñoz, M.; Muñoz-Tapia, J.L. DEFS—Data Exchange with Free Sample Protocol. Electronics 2021, 10, 1455. https://doi.org/10.3390/electronics10121455
Genés-Durán R, Hernández-Serrano J, Esparza O, Bellés-Muñoz M, Muñoz-Tapia JL. DEFS—Data Exchange with Free Sample Protocol. Electronics. 2021; 10(12):1455. https://doi.org/10.3390/electronics10121455
Chicago/Turabian StyleGenés-Durán, Rafael, Juan Hernández-Serrano, Oscar Esparza, Marta Bellés-Muñoz, and José Luis Muñoz-Tapia. 2021. "DEFS—Data Exchange with Free Sample Protocol" Electronics 10, no. 12: 1455. https://doi.org/10.3390/electronics10121455






