Formal Verification of Authentication and Service Authorization Protocols in 5G-Enabled Device-to-Device Communications Using ProVerif
Abstract
:1. Introduction
- We explore how D2D communications can be used to offload traffic and push contents to the edge closer to the end user in 5G.
- We propose a D2D security solution for authentication, data caching and sharing authorization in network-assisted and non-network-assisted D2D communications scenarios. The solution consists of two security protocols for providing authentication and authorization to D2D users facilitated by Identity-based Encryption (IBE), Elliptic Curve Integrated Encryption Scheme (ECIES) and access control mechanisms.
- We model and formally analyze the proposed protocols using formal methods and automated protocol verifier ProVerif with applied pi calculus.
- We also analyze the protocols security properties conscientiously using two taxonomies.
2. Related Work
3. Service Delivery in 5G-Enabled D2D Communications Network
3.1. System Model
- C-RAN is adopted for the centralization of base stations, resources virtualization and edge service deployment.
- CCN is adopted for content distribution and caching.
- D2D communications is adopted for direct communication, content dissemination and data offloading.
- UE: Transmitter and receiver.
- Next generation NodeB (gNB): Base station connecting UE to the network.
- HN: UE registers to and receives services from it.
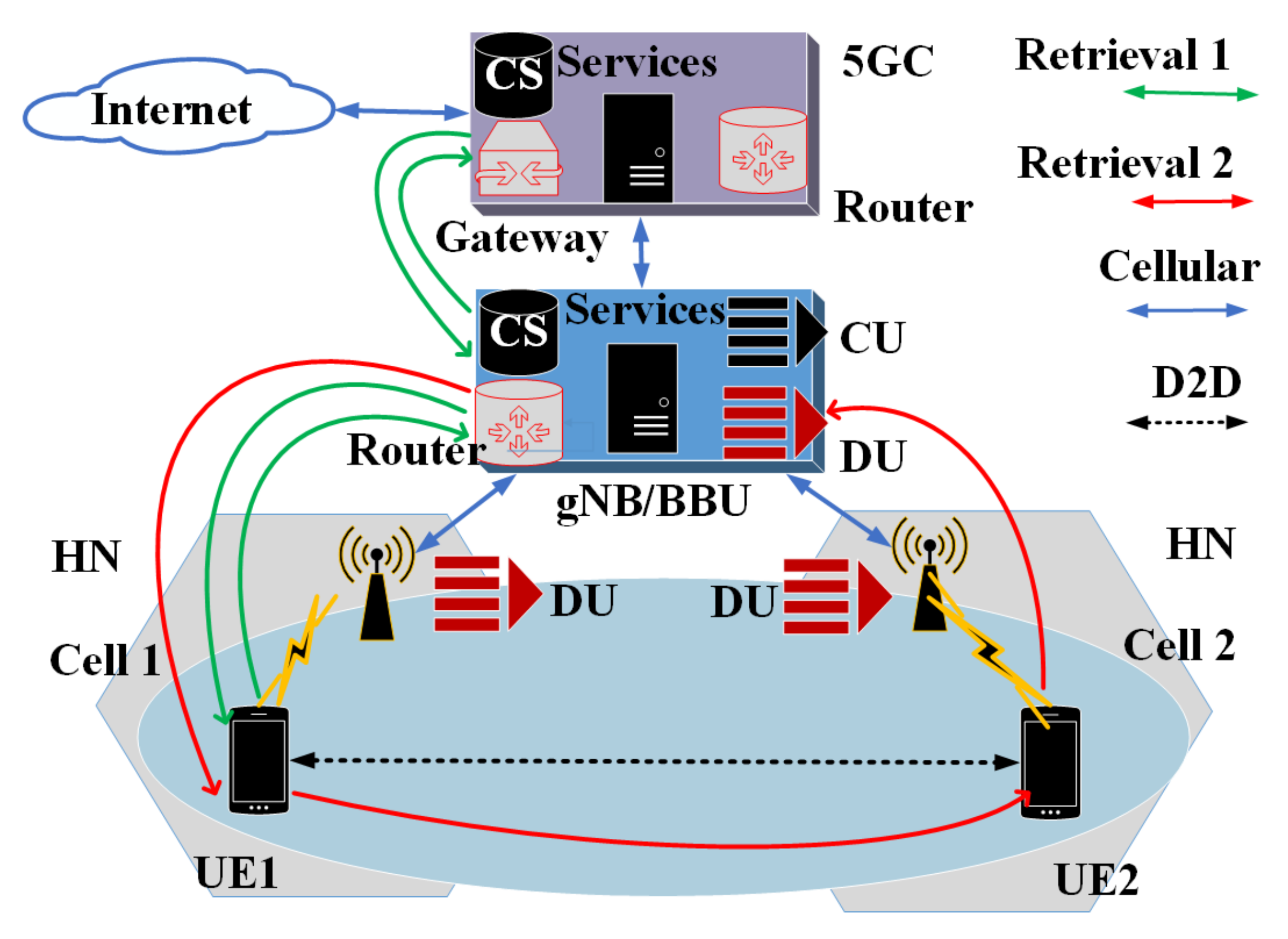
3.2. Service Access and Delivery
3.3. D2D Communications Process
3.3.1. D2D Communications Network Assisted
- When the SMF receives a session request message, it checks if the transmitter and receiver are within the same cell and the channel condition can support D2D communications. Then, it initiates the D2D connectivity with the help of gNB. The request messages include UE IDs and data name.
- Then, gNB starts a strategy list of communication patterns, push uplink shared channel, physical uplink control channel, power indicator, scan spectrum and time. After analyzing the request messages from SMF, it sends the message to .
- , hoping to make D2D connectivity with , sends regular information in the physical radio access channel with binary code, UE ID, data name and the UE can also detect received information from other UEs.
- After matching the targeted , the initiating sends the D2D connectivity request to gNB.
- Then, gNB analyzes the D2D connectivity request and chooses the best communication pattern for the D2D pair based on the conditions of the channel and cell resource utilization.
- Sometimes the D2D connectivity request fails; the normal cellular communication mode is adapted and the communication between the UEs goes back to the conventional cellular mode.
- Conversely, if the D2D mode request including orthogonal or reused pattern is permitted, gNB establishes a strategy list including communication patterns, power indicator, scan spectrum and scan time and sends it to .
- After completing the channel measurement such as normalized interference intervals, provides an update to gNB.
- gNB allocates spectrum resource to and lets recognize the same channel. Training sequences at the allocated channel are sent by the to help to get the link quality. Then, sends a confirmation message back to after checking that the link quality is suitable and confirms it to gNB.

3.3.2. D2D Communications Non-Network Assisted
- , hoping to make direct communication, transmits beacon signals with low frame rate to reduce signaling overhead.
- , in proximity, responds by sending acknowledgement messages.
- The received messages are evaluated based on metrics, such as Signal-to-Interference-plus-Noise Ratio (SINR).
- The UEs can start direct communication with each other, when a received signal is above the predetermined metrics threshold with a good quality of service.
4. Security in 5G-Enabled D2D Communications Network
4.1. Problem Definition
4.2. Proposed D2D Security Solution
- Scenario A: Intra-operator, non-roaming and same cell, both UEs are in cellular coverage of gNB, same HN and subscribed to the same MNO.
- Scenario B: Intra-operator, non-roaming and different cells, both in HN coverage, subscribed and served by the same operator but in different cells.
- Scenario C: Inter-operators and roaming, one UE is in HN, while the other UE is roaming in visited network, and both users subscribe to different operators.
- Scenario D: Inter-operators and out of coverage, both UEs are out of coverage and can share content without involving their HNs. It also applies to emergency situations. Both UEs subscribed to different operators.

4.3. Security Requirement
4.4. Authentication and Authorization
- : DataName.
- DA: Dataset delegation (true), label , data owner ID , data owner’s public key , token owner ID , scope (offline access, cache, share, any).
- hKd1: Nonce key ID signed by data owner’s private key
- Exp: Token expiry date.
5. Modeling of the Proposed Protocols
5.1. DDSec Protocol
DDSec Protocol Message Exchange and Execution
- Msg1 UEA→gNB:({AdvMsg},{KgNBa})
- Msg2 UEB→gNB:({IntMsg},{KgNBb})
- Msg3.gNB→UEA:({DiscMsg},{KgNBa})
- Msg4.gNB→UEB:({LinkUpMsg},{KgNBb})
- Msg5.UEA→UEB:({PublMsg},{PKUEB})
- Msg6.UEB→UEA:({LookUp},{PKUEA})
- Msg7.UEA→UEB:({SendData},{PKUEB})
5.2. DDACap Protocol
DDACap Protocol Message Exchange and Execution
- Msg1 UEB→UEC:({AdvMsg})
- Msg2 UEC→UEB:({IntMsg},{PKUEB})
- Msg3.UEB→UEC:({PublMsg},{PKUEC})
- Msg4.UEC→UEB:({LookUp},{PKUEB})
- Msg5.UEB→UEC:({SendData},{PKUEC})
6. Verification of the Proposed Protocols
6.1. Formal Methods
6.2. Formal Verification Using Proverif
- functions: fun encrypt(bitstring, pkey): bitstring., key: type key., private and public names: free rand_a: bitstring[private] free pubChannel : channel.
- Queries: On secrecy, reachability and authentication. A secrecy property is specified as a query of the attacker’s knowledge attacker(M). When the fact attacker(M) is derivable, the attacker may have the knowledge of M, but, if it is not derived, there is no way that the attacker can gain the knowledge of M. With reachability, the query attacker(K) is also used to debug the model of the protocol to check a particular branch is reachable or not, query k: bitstring; event(endServer(k)). The authentication properties are specified as correspondence assertions in the form of event(e1(M)) event(e2(M)) which have to be proven. In the case of the DDSec and DDACap protocols, the following is queried to test the secrecy of message attributes such as query attacker (rand_a) for a nonce, query attacker (ua) for id and query attacker (skuea) for key. query C:host,B:host,K:pkey, rand_rc:nonce; event(endUEB(B,C,K,rand_rc)) ==> event(beginUEA(B, C, K, rand_rc)) is used to test the events’ relationship.
- Events: Querying events to test their relationship. (i) Event correspondence tested query is a basic correspondence assertion, query x1:t1 . . , xn:tn; event(e(M1, ..,Mj)) ==> event (e’(N1,..,Nk)), for the non-injective correspondence there is at least one earlier occurrence of e’. (ii) Injective correspondence assertions capture the one-to-one relationship, query x1:t1, . ., xn:tn; inj-event(e(M1, . . , Mj)) ==> inj-event(e’(N1,..,Nk)). The correspondence asserts that, for each occurrence of event e(M1, . . ,Mj), there is a distinct earlier occurrence of event e’(N1, . . ,Nk).
- Process: The protocol is encoded using main process and process macros for the participating entities to allow sub-process being defined as (!process). The main process also starts off several copies of the system entities (UEs and gNB) with the relevant parameters representing several sessions of the roles as explained in the message exchange in Section 5.1 and Section 5.2.
6.3. Formal Analysis of DDSec Protocol
6.3.1. The Attack on DDSec Protocol
| UEA -> gNB: {AdvMsg}, {KgNBa} |
| UEB -> gNB: {IntMsg}, {KgNBb} |
| gNB -> UEA: {DiscMsg}, {KgNBa} |
| gNB -> UEA: {LinkUpMsg}, {KgNBb} |
| UEA -> I_UEB: {PublMsg}, {PKI} |
| I_UEA -> UEB: {PublMsg, {PKUEB} |
| UEB -> I_UEA: {LookUp}, {PKI} |
| I_UEB -> UEA: {LookUp}, {PKUEA} |
| UEA -> I_UEB: {SenData}, {PKI} |
| I_UEA -> UEB: {SenData}, {PKUEB} |
6.3.2. Attack Derivation and Trace
| TRACE 1 |
| -- Query not attacker(rand_a[]) |
| Completing... |
| Starting query not attacker(rand_a[]) |
| goal reachable: attacker(rand_a[]) |
| 1 new skuea_36: skey creating skuea_2040 at {1} |
| 2 new skua: sskey creating skua_2041 at {2} |
| 3 new skueb_37: skey creating skueb_2042 at {3} |
| 4 new skub: sskey creating skub_2043 at {4} |
| 5 new kgnba: key creating kgnba_2044 at {5} |
| 6 new kgnbb: key creating kgnbb_2045 at {6} |
| 7 out(c, M) with M = pk(skuea_2040) at {8} |
| 8 out(c, M_2190) with M_2190 = spk(skua_2041) at {10} |
| 9 out(c, M_2262) with M_2262 = pk(skueb_2042) at {12} |
| 10 out(c, M_2333) with M_2333 = spk(skub_2043) at {14} |
| 11 insert keys(A,pk(skuea_2040)) at {15} |
| 12 insert keys(B,pk(skueb_2042)) at {16} |
| 13 The attacker has the message rand_a. |
| 14 A trace has been found. |
| 15 RESULT not attacker(rand_a[]) is false. |
| TRACE 2 |
| 16 new ua_66: id creating ua_7831 at {57} in copy a_7503 |
| 17 new ub_67: id creating ub_7832 at {58} in copy a_7503 |
| 18 new dataname_68: bitstring creating dataname_7833 at {59} in copy |
| a_7503 |
| 19 out(c, M_7890) with M_7890 = sencrypt((ub_7832,dataname_7833, |
| pk(skueb_7504)),kgnbb_7509) at {62} in copy a_7503 |
| 20 in(c, (PublMsg,a,a_7502)) at {63} in copy a_7503 |
| 21 event endUEB(A,B,pk(skueb_7504),rand_a,rand_b) at {64} in copy a_7503 |
| (goal) |
| 22 The event endUEB(A,B,pk(skueb_7504),rand_a,rand_b) is executed. |
| 23 A trace has been found. |
| 24 RESULT event(endUEB(A_107,B_108,K,rand_a_109,rand_b_110)) ==> |
| event(beginUEA(A_107,B_108,K,rand_a_109,rand_b_110)) is false. |
- The first trace, by eavesdropping the attacker knows rand_a, line 1–6 at inputs {1}–{6} corresponds to the creation of keys. Lines 7–10 at outputs {8}, {10}, {12}, {14} correspond to the public keys; they are stored in fresh variables M, M_2190, M_2262, M_2333, respectively, by the attacker for later reuse. Lines 11–12 at inputs {15}, {16} show the public keys are inserted in the key table in the main process for and . Then, the attacker gets rand_a[].
- The second and third traces, Lines 1–12 at {1}–{16}, are the same as in Trace 1 while in Traces 2 and 3 the steps are the same but in different sessions a_7503 and a_9678, respectively. With Lines 16–17 at inputs {57} and {58} corresponding to creations of ua, ub, the attacker creates ua_7831, ub_7832 and stores them in a_7503. Thus, Line 19 at output {62} corresponds to a session copy a_7503 has with the attacker, sending its ID ub_7832 and data name data name_7833, which the attacker stores in a new variable M_7890 for later use. In the same session, the attacker receives (PublMsg,a,a_7502) at input {63}. Line 21 shows the attacker receiving his goal at {64} when event endUEB(A,B,pk(skueb_7504),rand_a,rand_b) is executed in a_7503 with as ends the protocol believing it was communicating with , but in fact it was communicating with the attacker. Trace 2 shows an attack on non-injective agreement, while Trace 3 shows an attack on injective agreement executed in session a_9678.

6.4. Improved Version of DDSec Protocol
6.5. Formal Analysis of DDACap Protocol
7. Security Analysis
7.1. Protocol Security Analysis
7.1.1. The Analysis Using Security Properties of Set 1
- Secrecy: This is achieved since rand_a and rand_b are never revealed to the attacker. It also covers confidentiality and privacy of the protocol’s data.
- Aliveness: and obtain the aliveness of each other during and messages exchange. gets non-injective agreement on rand_a with and with on rand_b.
- Weak Agreement: This is achieved when both entities obtain non-injective agreement on rand_a, rand_b, respectively, as ends running the protocol with guaranteed that has been talking to .
- Non-injective Agreement: obtains non-injective agreement on and with , respectively, and holds in ProVerif with event(endUEB(A_107, B_108, K, rand_a_109, rand_b_110)) ==> event(beginUEA(A_107, B_108, K, rand_a_109, rand_b_110)).
- Injective Agreement: It is central to the protocol’s purpose; injective agreement between and on and assures each other that they are known. to and to holds with inj-event (endUEB(A_116, B_117, K_118, rand_a_119, rand_b_120)) ==> inj-event (beginUEA(A_116, B_117, K_118, rand_a_119, rand_b_120)).
7.1.2. The Analysis Using Security Properties of Set 2
- Mutual Entity Authentication: and authenticated each other with A, B, pkuea, rand_a, rand_b when they proved to hold, hence enforcing this requirement.
- Mutual Key Authentication: The public keys and are self-certified, used as identifiers and hashed. This implicitly authenticates the public keys.
- Mutual Key Confirmation: This requirement does not apply to this protocol as the UEs generate their own public and private keys. However, since they both use ECIES that partly enforces this agreement, the successful authentication of to and to implicitly enforces this requirement.
- Key Freshness: ProVerif has no function to check key freshness, however the messages exchange includes nonces and timestamps, hence checking the freshness of messages which includes the keys. Since the secrecy of these keys are not violated, it implies keys are fresh.
- Unknown-Key Share: Since the entities use their own unique key pair and private keys are not violated, it enforces this requirement. The entities’ ID and generated hashes prevent this attack. The inclusion of and in the authentication process also proves this requirement.
- Key Compromise Impersonation Resilience: Since the entities use their own unique public/private keys using ECIES, it enforces this requirement. Therefore, knowing one key in a session is not enough to deduce another. Backward and forward secrecy of keys are possible; no entity or adversary is capable of computing keys in past session or predict feature keys, which is due to ECC. Obviously, the public keys are globally known but the private keys are only known to the owners. However, to compromise the keys, ECIES, and would have to be compromised at the same time. It should be noted that compromising the HN during the primary authentication does not necessarily mean that D2D authentication will be compromised.
7.2. Security Consideration
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- 3GPP. Security architecture, procedures for 5G system. In Technical Specification (TS) 3GPP TS 33.501 V17.0.0 (2020–2012); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2020. [Google Scholar]
- Edris, E.K.K.; Aiash, M.; Loo, J. Investigating Network Services Abstraction in 5G enabled Device-to-Device (D2D) Communications. In 2019 IEEE SmartWorld, Ubiquitous Intelligence Computing, Advanced Trusted Computing, Scalable Computing Communications, Cloud Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI); IEEE: Leicester, UK, 2019; pp. 1660–1665. [Google Scholar] [CrossRef]
- Yu, H.; Afzal, M.K.; Zikria, Y.B.; Rachedi, A.; Fitzek, F.H.P. Tactile Internet: Technologies, test platforms, trials, and applications. Future Gener. Comput. Syst. 2020, 106, 685–688. [Google Scholar] [CrossRef]
- Feng, D.; Lai, L.; Luo, J.; Zhong, Y.; Zheng, C.; Ying, K. Ultra-reliable and low-latency communications: Applications, opportunities and challenges. Sci. China Inf. Sci. 2021, 64, 1–12. [Google Scholar] [CrossRef]
- Singh, K.; Ku, M.L.; Flanagan, M.F. Energy-Efficient Precoder Design for Downlink Multi-User MISO Networks With Finite Blocklength Codes. IEEE Trans. Green Commun. Netw. 2021, 5, 160–173. [Google Scholar] [CrossRef]
- Liu, L.; Yu, W. A D2D-based Protocol for Ultra-Reliable Wireless Communications for Industrial Automation. IEEE Trans. Wirel. Commun. 2018, 17, 5045–5058. [Google Scholar] [CrossRef]
- 3GPP. Study on architecture enhancements to support Proximity-based Services (ProSe). In Technical Specification (TS) 3GPP TR 23.703 V12.0.0 (2014-02); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2014. [Google Scholar]
- Gupta, A.; Jha, R.K. A Survey of 5G Network: Architecture and Emerging Technologies. IEEE Access 2015, 3, 1206–1232. [Google Scholar] [CrossRef]
- Chandrasekaran, G.; Wang, N.; Hassanpour, M.; Xu, M.; Tafazolli, R. Mobility as a Service (MaaS): A D2D-Based Information Centric Network Architecture for Edge-Controlled Content Distribution. IEEE Access 2018, 6, 2110–2129. [Google Scholar] [CrossRef] [Green Version]
- Edris, E.K.K.; Aiash, M.; Loo, J. The Case for Federated Identity Management in 5G Communications. In Proceedings of the 5th IEEE International Conference on Fog and Mobile Edge Computing (FMEC 2020), Paris, France, 20–23 April 2020; IEEE: Paris, France, 2020. [Google Scholar]
- 5GPPP. Deliverable D2.7 Security Architecture (Final); Technical Report, 5G Enablers for Network; 5GPPP: Heidelberg, Germany, 2017. [Google Scholar]
- 3GPP. 5G system stage 2 Rel-17. In Technical Report 3GPP TSG Rel-17 (2021); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2021. [Google Scholar]
- 3GPP. Proximity-based services (ProSe) Stage 2. In Technical Specification (TS) 3GPP TS 23.303 V16.0.0 (2020-07); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2020. [Google Scholar]
- Qiao, J.; Shen, X.; Mark, J.; Shen, Q.; He, Y.; Lei, L. Enabling device-to-device communications in millimeter-wave 5G cellular networks. IEEE Commun. Mag. 2015, 53, 209–215. [Google Scholar] [CrossRef]
- Zhang, T.; Fang, X.; Liu, Y.; Nallanathan, A. Content-centric mobile edge caching. IEEE Access 2019, 8, 11722–11731. [Google Scholar] [CrossRef]
- Zhang, A.; Chen, J.; Hu, R.Q.; Qian, Y. SeDS: Secure Data Sharing Strategy for D2D Communication in LTE-Advanced Networks. IEEE Trans. Veh. Technol. 2016, 65, 2659–2672. [Google Scholar] [CrossRef]
- Zhang, A.; Lin, X. Security-Aware and Privacy-Preserving D2D Communications in 5G. Netw. IEEE 2017, 31, 70–77. [Google Scholar] [CrossRef]
- Melki, R.; Noura, H.N.; Chehab, A. Lightweight and Secure D2D Authentication & Key Management Based on PLS. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Cao, M.; Chen, D.; Yuan, Z.; Qin, Z.; Lou, C. A lightweight key distribution scheme for secure D2D communication. In Proceedings of the 2018 International Conference on Selected Topics in Mobile and Wireless Networking (MoWNeT), Tangier, Morocco, 20–22 June 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Wang, M.; Yan, Z.; Niemi, V. UAKA-D2D: Universal Authentication and Key Agreement Protocol in D2D Communications. Mob. Netw. Appl. 2017, 22, 510. [Google Scholar] [CrossRef]
- Wang, M.; Yan, Z.; Song, B.; Atiquzzaman, M. AAKA-D2D: Anonymous Authentication and Key Agreement Protocol in D2D Communications. In Proceedings of the 2019 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Leicester, UK, 19–23 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1356–1362. [Google Scholar] [CrossRef]
- Gope, P. LAAP: Lightweight anonymous authentication protocol for D2D-Aided fog computing paradigm. Comput. Secur. 2019, 86, 223–237. [Google Scholar] [CrossRef]
- Seok, B.; Sicato, J.C.S.; Erzhena, T.; Xuan, C.; Pan, Y.; Park, J.H. Secure D2D communication for 5G IoT network based on lightweight cryptography. Appl. Sci. 2020, 10, 217. [Google Scholar] [CrossRef] [Green Version]
- Wang, P.; Chen, C.M.; Kumari, S.; Shojafar, M.; Tafazolli, R.; Liu, Y.N. HDMA: Hybrid D2D message authentication scheme for 5G-enabled vanets. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Lopes, A.P.G.; Gondim, P.R. Mutual authentication protocol for D2D communications in a cloud-based e-health system. Sensors 2020, 20, 2072. [Google Scholar] [CrossRef] [Green Version]
- Wang, L.; Tian, Y.; Zhang, D.; Lu, Y. Constant-round authenticated and dynamic group key agreement protocol for D2D group communications. Inf. Sci. 2019, 503, 61–71. [Google Scholar] [CrossRef]
- Wang, L.; Liu, J.; Chen, M.; Gui, G.; Sari, H. Optimization-based access assignment scheme for physical-layer security in D2D communications underlaying a cellular network. IEEE Trans. Veh. Technol. 2018, 67, 5766–5777. [Google Scholar] [CrossRef]
- Li, Z.; Hu, H.; Hu, H.; Huang, B.; Ge, J.; Chang, V. Security and Energy-aware Collaborative Task Offloading in D2D communication. Future Gener. Comput. Syst. 2021, 118, 358–373. [Google Scholar] [CrossRef]
- Yan, Z.; Xie, H.; Zhang, P.; Gupta, B.B. Flexible data access control in D2D communications. Future Gener. Comput. Syst. Future Gener. Comput. Syst. 2018, 82, 738–751. [Google Scholar] [CrossRef]
- Li, Q.; Huang, L.; Mo, R.; Huang, H.; Zhu, H. Robust and scalable data access control in D2D communications. IEEE Access 2018, 6, 58858–58867. [Google Scholar] [CrossRef]
- Kang, H.J.; Kang, C.G. Mobile device-to-device (D2D) content delivery networking: A design and optimization framework. J. Commun. Netw. 2014, 16, 568–577. [Google Scholar] [CrossRef]
- Golrezaei, N.; Molisch, A.F.; Dimakis, A.G.; Caire, G. Femtocaching and device-to-device collaboration: A new architecture for wireless video distribution. Commun. Mag. IEEE 2013, 51, 142–149. [Google Scholar] [CrossRef] [Green Version]
- Bastug, E.; Bennis, M.; Debbah, M. Living on the edge: The role of proactive caching in 5G wireless networks. Commun. Mag. IEEE 2014, 52, 82–89. [Google Scholar] [CrossRef] [Green Version]
- Jacobson, V. A Description of Content-Centric Networking (CCN). In Future Internet Summer School (FISS); 2009; Volume 2018, Available online: https://named-data.net/wp-content/uploads/2014/04/van-ccn-bremen-description.pdf (accessed on 2 July 2021).
- Checko, A.; Christiansen, H.; Yan, Y.; Scolari, L.; Kardaras, G.; Berger, M.; Dittmann, L. Cloud RAN for Mobile Networks-A Technology Overview. IEEE Commun. Surv. Tutor. 2015, 17, 405–426. [Google Scholar] [CrossRef] [Green Version]
- 3GPP. Study on Architecture for Next Generation System. In Technical Specification (TS) 3GPP TR 23.799 V14.0.0 (2016-12); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2016. [Google Scholar]
- Ravindran, R. Enabling ICN in 3GPP’s 5G NextGen Core Architecture. In Memo ICNRG; IETF: Fremont, CA, USA, 2019; Volume 2019. [Google Scholar]
- Edris, E.K.K.; Aiash, M.; Loo, J.; Alhakeem, M.S. Formal Verification of Secondary Authentication Protocol for 5G Secondary Authentication. Int. J. Secur. Netw. 2020, in press. [Google Scholar]
- Edris, E.K.K.; Aiash, M.; Loo, J. Network Service Federated Identity (NS-FId) Protocol for Service Authorization in 5G Network. In Proceedings of the 5th IEEE International Conference on Fog and Mobile Edge Computing (FMEC 2020), Paris, France, 20–23 April 2020; IEEE: Piscataway, NJ, USA, 2020. [Google Scholar]
- Altmann, V.; Skodzik, J.; Danielis, P.; Mueller, J.; Golatowski, F.; Timmermann, D. A DHT-Based Scalable Approach for Device and Service Discovery. In Proceedings of the 12th IEEE International Conference on Embedded and Ubiquitous Computing, Milan, Italy, 26–28 August 2014; pp. 97–103. [Google Scholar] [CrossRef]
- 3GPP. Feasibility study on the security aspects of remote provisioning, change of subscription for Machine to Machine (M2M) equipment. In Technical Specification (TS) 3GPP TR 33.812 V9.2.0 (2010-06); Third Generation Partnership Project; 3GPP: Sophia Antipolis, France, 2010. [Google Scholar]
- Wang, K.; Yu, F.R.; Li, H.; Li, Z. Information-Centric Wireless Networks with Virtualization and D2D Communications. IEEE Wirel. Commun. 2017, 24, 104–111. [Google Scholar] [CrossRef]
- Gandotra, P.; Jha, R.K.; Jain, S. A survey on device-to-device (D2D) communication: Architecture and security issues. J. Netw. Comput. Appl. 2017, 78, 9–29. [Google Scholar] [CrossRef]
- Haus, M.; Waqas, M.; Ding, A.Y.; Li, Y.; Tarkoma, S.; Ott, J. Security and Privacy in Device-to-Device (D2D) Communication: A Review. IEEE Commun. Surv. Tutor. 2017, 19, 1054–1079. [Google Scholar] [CrossRef]
- Nunes, I.O.; Tsudik, G. Lightweight Authentication & Access Control for Private Content-Centric Networks. In Proceedings of the International Conference on Applied Cryptography and Network Security, Leuven, Belgium, 2–4 July 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 598–615. [Google Scholar]
- Tourani, R.; Misra, S.; Mick, T.; Panwar, G. Security, Privacy, and Access Control in Information-Centric Networking: A Survey. IEEE Commun. Surv. Tutor. 2018, 20, 566–600. [Google Scholar] [CrossRef]
- Alliance, N. 5G security recommendations Package #2: Network Slicing. In White Paper; NGMN: Frankfurt am Main, Germany, 2016; pp. 1–12. [Google Scholar]
- Aamir, M.; Zaidi, S.M.A. Denial-of-service in content centric (named data) networking: A tutorial and state-of-the-art survey. Secur. Commun. Netw. 2015, 8, 2037–2059. [Google Scholar] [CrossRef]
- Lichtman, M.; Rao, R.; Marojevic, V.; Reed, J.; Jover, R.P. 5G NR Jamming, Spoofing, and Sniffing: Threat Assessment and Mitigation. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Edris, E.K.K.; Aiash, M.; Loo, J. Formal Verification and Analysis of Primary Authentication based on 5G-AKA Protocol. In The Third International Symposium on 5G Emerging Technologies (5GET 2020); IEEE: Paris, France, 2020. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef] [Green Version]
- SECG. SEC 1: Recommended Elliptic Curve Cryptography; SECG: Guangzhou, China, 2009. [Google Scholar]
- Girault, M. Self-certified public keys. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1991; pp. 490–497. [Google Scholar] [CrossRef]
- Lowe, G. A hierarchy of authentication specifications. In Proceedings of the 10th Computer Security Foundations Workshop, Rockport, MA, USA, 10–12 June 1997; IEEE: Piscataway, NJ, USA, 1997; pp. 31–43. [Google Scholar] [CrossRef] [Green Version]
- Menezes, A.J.; Oorschot, P.C.V.; Vanstone, S.A. Handbook of Applied Cryptography; Includes Bibliographical References and Index, ID: alma991001301199704781; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Aiash, M.; Loo, J. A formally verified access control mechanism for information centric networks. In Proceedings of the 12th International Joint Conference on e-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; IEEE: Piscataway, NJ, USA, 2015; Volume 4, pp. 377–383. [Google Scholar]
- Armando, A.; Basin, D.A.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.R.; Drielsma, P.H.; Heam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of Internet security protocols and applications. Comput. Aided Verif. Proc. 2005, 3576, 281–285. [Google Scholar]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 2.01: Automatic Cryptographic Protocol Verifier, User Manual and Tutorial. 2020. Available online: https://opam.ocaml.org/packages/proverif/ (accessed on 2 July 2021).
- Dolev, D.; Yao, A.C.C. On the Security of Public Key Protocols. IEEE Trans. Inf. Theory 1983, 30, 198–208. [Google Scholar] [CrossRef]
- Ryan, M.D.; Smyth, B. Applied pi calculus. Form. Model. Tech. Anal. Secur. Protoc. 2011, 5, 112–142. [Google Scholar]





| Notation | Description |
|---|---|
| // | UE |
| gNB | new generation NodeB |
| Rand_a/Rand_b/Rand_rb/Rand_rc | Nonce |
| PK(X) | public key |
| SK(X) | private Key |
| Exp | expiry date |
| URI | DataName |
| Ts | time stamp |
| Acap | security token |
| logical/node address | |
| D1 | hash (DataName) |
| session key (UE and gNB) | |
| hKd1 | nonce key ID |
| UA/UB/UC | pseudonym ID hash(X)UEID)) |
| DOID | data owner’s ID |
| hDOID | hash(DOID) |
| h(x) | hash value of message x |
| {x}{k} | message encrypted with key K |
| Term | Grammar |
|---|---|
| M, N ::= | term |
| a, b, c, k, s | name |
| x, y, z | variable |
| h(M1, … ,Mn) | constructor/destructor application |
| D ::= | expressions |
| fail | failure |
| P, Q ::= | processes |
| out(N,M); P | output |
| in(N, x : T); P | input |
| !P replication | |
| 0 | nil |
| P ∣ Q | parallel composition |
| new a : T; P | restriction |
| let x : T = D in P else Q | expression evaluation |
| if M then P else Q | conditional |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Edris, E.K.K.; Aiash, M.; Loo, J. Formal Verification of Authentication and Service Authorization Protocols in 5G-Enabled Device-to-Device Communications Using ProVerif. Electronics 2021, 10, 1608. https://doi.org/10.3390/electronics10131608
Edris EKK, Aiash M, Loo J. Formal Verification of Authentication and Service Authorization Protocols in 5G-Enabled Device-to-Device Communications Using ProVerif. Electronics. 2021; 10(13):1608. https://doi.org/10.3390/electronics10131608
Chicago/Turabian StyleEdris, Ed Kamya Kiyemba, Mahdi Aiash, and Jonathan Loo. 2021. "Formal Verification of Authentication and Service Authorization Protocols in 5G-Enabled Device-to-Device Communications Using ProVerif" Electronics 10, no. 13: 1608. https://doi.org/10.3390/electronics10131608
APA StyleEdris, E. K. K., Aiash, M., & Loo, J. (2021). Formal Verification of Authentication and Service Authorization Protocols in 5G-Enabled Device-to-Device Communications Using ProVerif. Electronics, 10(13), 1608. https://doi.org/10.3390/electronics10131608








