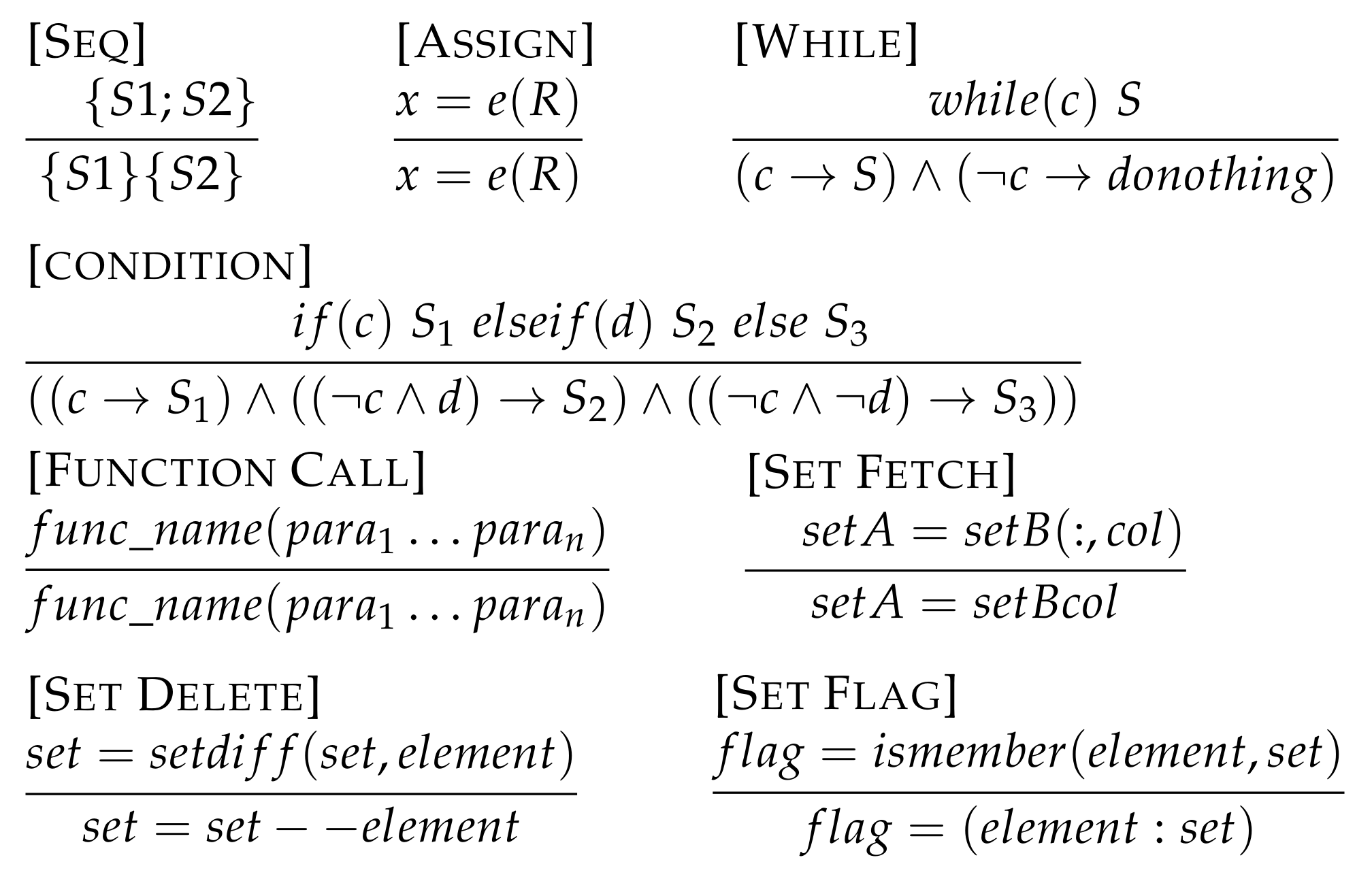
5.1. Operational Context
In montague pragmatics [
22,
23], context is composed of tuples of function variables and context. For different contexts, the same variable can have different semantics. The operational context is a set of key-value pairs composed of the constraint relationship between the variable value and the corresponding variable value. The context
can be expressed as:
Among them, to represents several variable names, and to represent the constraint relationship on the value of the corresponding variable. The uniqueness of the collection element is determined by the variable name.
The model of program execution can be expressed by the following formula:
It means that starting from a certain context , after the running of a program, the state of variables and data has changed and a new context is formed. For the context , we abstract it as an operational context . Therefore, the process of running the entire program can be abstracted as starting from a certain context , the execution of program, the state of variables and data has changed, thus forming a new context .
5.2. Formal Proof Method of Context-Based for Program Correctness
In software engineering, the development of a program starts from the system requirements to determine its high-level requirements, to verify the correctness of low-level requirements, and then to system integration and testing. The high-level requirements describe what a program does and output the corresponding result in the case of certain input. Based on such high-level requirements, in the verification process of this article, first-order logic expressions can be used to express high-level requirements in the form of pre-and post-conditions, that is, under a certain pre-condition. After the program runs, the corresponding post-conditions are expected to be obtained set conditions. We assume it is correct for the high-level requirements of manual confirmation. Concerning how to prove the consistency of the low-level requirements and the high-level requirements and correctness of the modeling procedure, we make the following reasoning, where
is the context concept proposed in the previous section,
is the precondition, and
is the postcondition, and
denotes the program to be proven.
The meaning of this formula is starting from the initial context
of the
program, after a series of statements in the f program, the final context
is obtained. This process can deduce the high-level requirement preconditions
containing high-level requirements. The post-condition
proves that the implementation of program meets high-level requirements, that is, low-level requirements are consistent with high-level requirements. Since there are multiple initial contexts in the
program, and the initial context is determined by high-level requirement preconditions, the high-level requirement preconditions are substituted into the context-based program execution process for subtraction, and the above deduction formula is modified, get the following formula:
The meaning of deformed formula is program takes the high-level requirement precondition as the constraint condition of its initial context , and the final context is obtained through the execution of the program. If the final context can deduce the post-conditions of high-level requirements, then it can be proved that the program fragment is consistent with the high-level requirements, so that the program is correct.
Above we have defined the core process of formal proof of program correctness, but it is impossible for us to directly prove a complete abstract language program. We need to decompose the program in order to prove and verify it sentence by sentence, and continuously update the value of the variable in the context and its constraint conditions, until all the sentences are executed, and the final context is obtained. Therefore, we can decompose the abstract language program
into a sequence of n sentences, namely
The
here represents different types of statements, such as assignment statements, conditional statements, loop statements, etc. The sequence of
constitutes a complete
program. Each
sentence has the previous context
as the initial context, and after the execution of
, the next context
is obtained. According to this execution process, the running process of the entire
program can be further abstracted into the following formula:
Then the consistency verification of high-level requirements and low-level requirements can be reduced to the following formula:
If it is proved one by one that the decomposed program can deduce the step a, then the proof of the entire program can be transformed into the following formula:
Substituting the high-level requirements precondition
into the execution process of each step
program for subtraction, the formula is transformed as follows:
Perform the reduction process according to this formula to obtain the post-conditions of the low-level requirements. Compare the post-conditions of the low-level requirements with the post-conditions of the high-level requirements. If the post-conditions of the high-level requirements are a subset of the post-conditions of the low-level requirements, it means that the program has realized the function of the high-level requirements. At the same time, the program as a low-level requirement is consistent with the high-level requirement. What we mean here is that a program will have multiple high-level requirements pre- and post-condition pairs. Only when the program completes all high-level requirements pre- and post-condition pairs, can the program be proved correct. Although the program has multiple high-level requirements and preconditions, the number is far less than the number of test cases using the test method. Therefore, the formal proof method of the program correctness in this paper is effective and reduces the verification workload.
As mentioned above, we present how to formally prove the correctness of the program, and the process to verify the consistency of high-level and low-level requirements is completely provided.