Derogation of Physical Layer Security Breaches in Maturing Heterogeneous Optical Networks
Abstract
:1. Introduction
1.1. Related Work
1.2. Organization and Notation of Paper
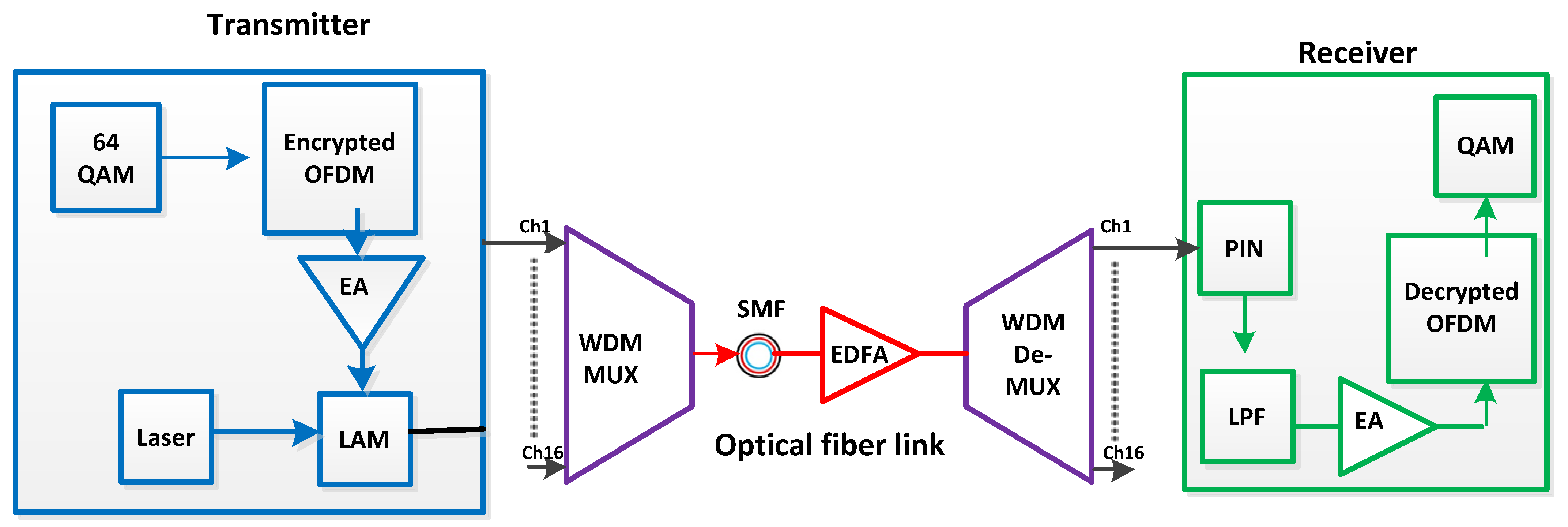
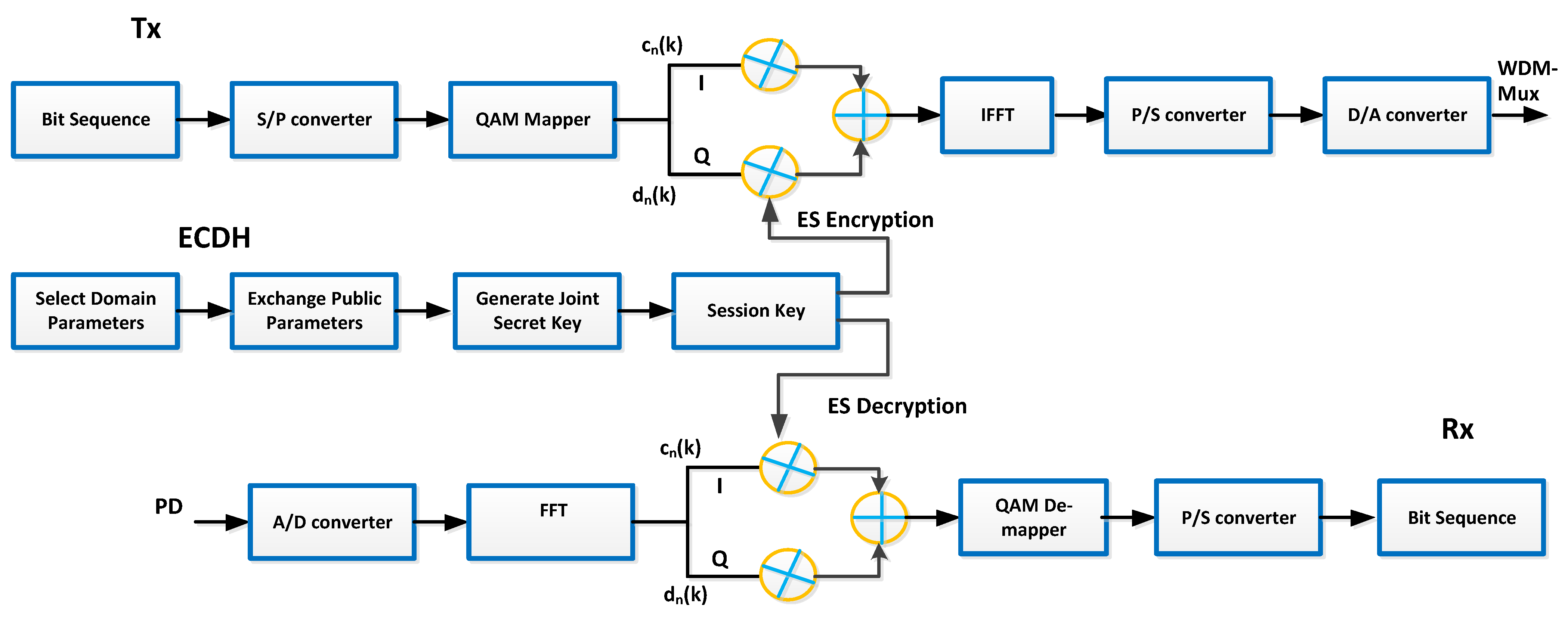
2. Proposed Layout
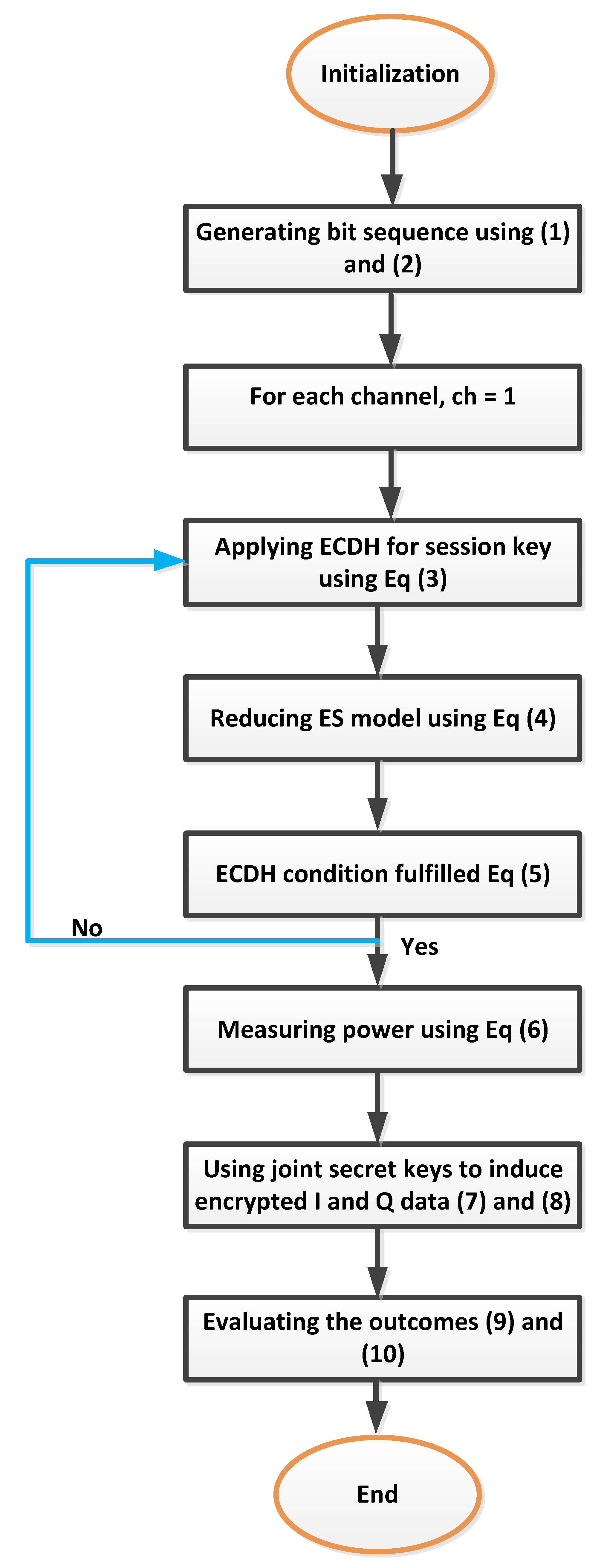
3. Analytical Modeling for Secure Communication
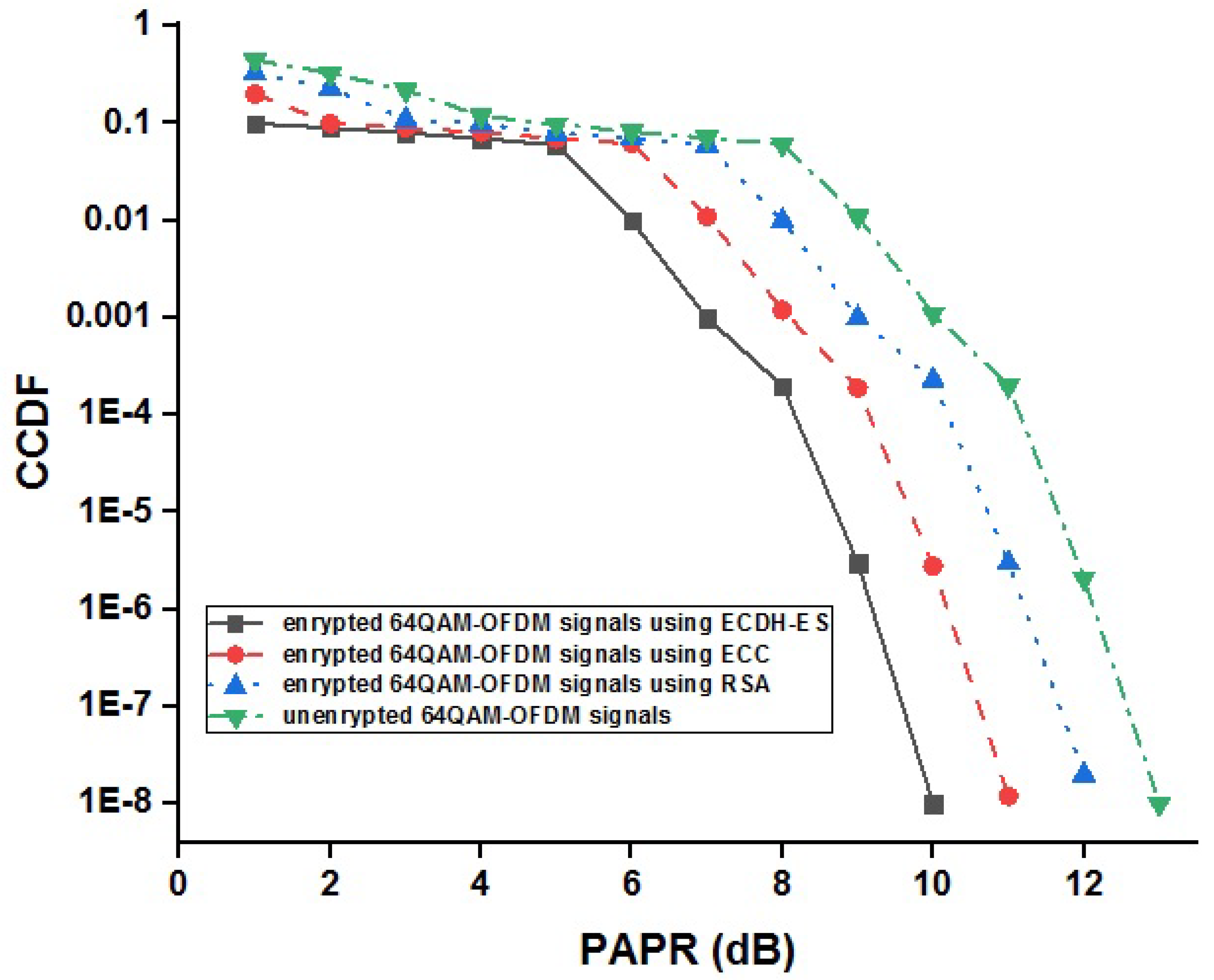
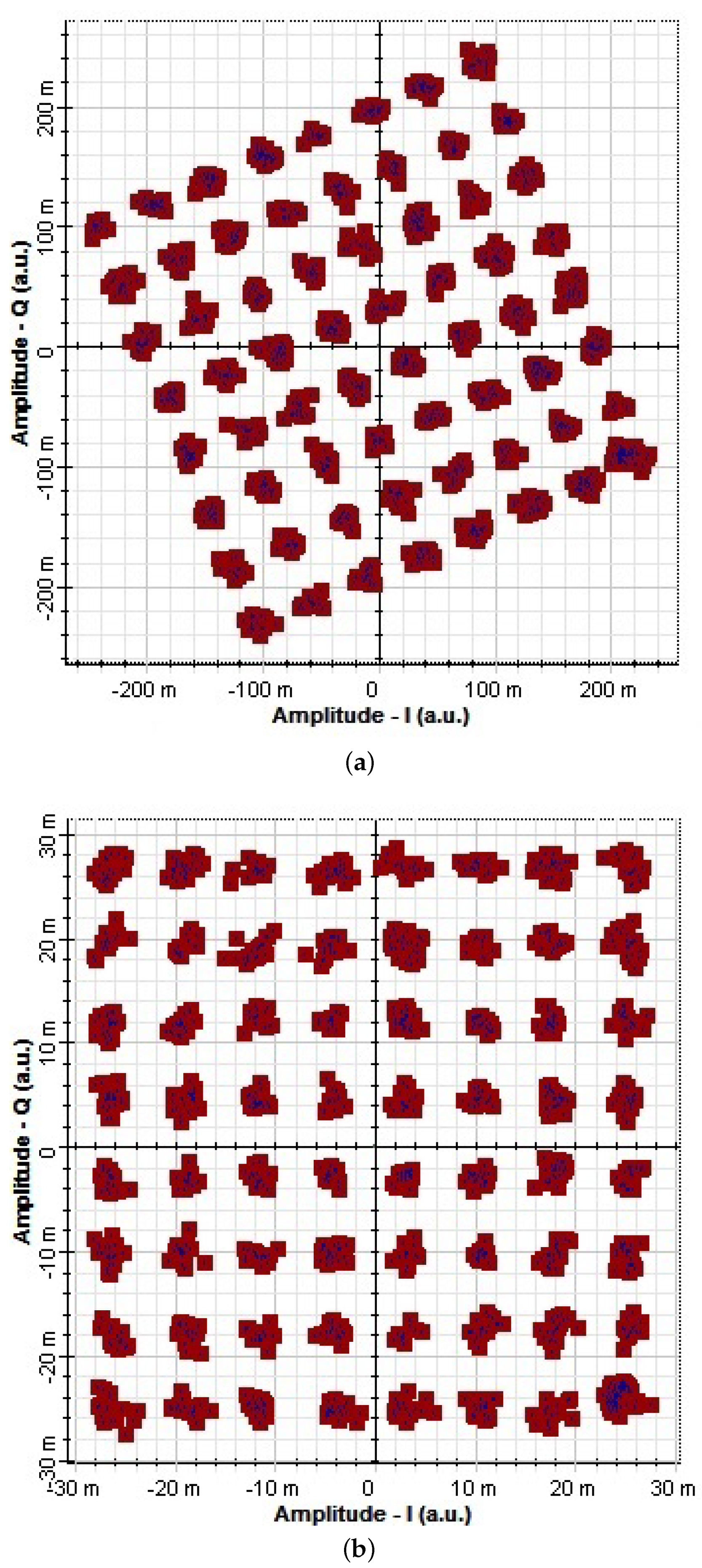
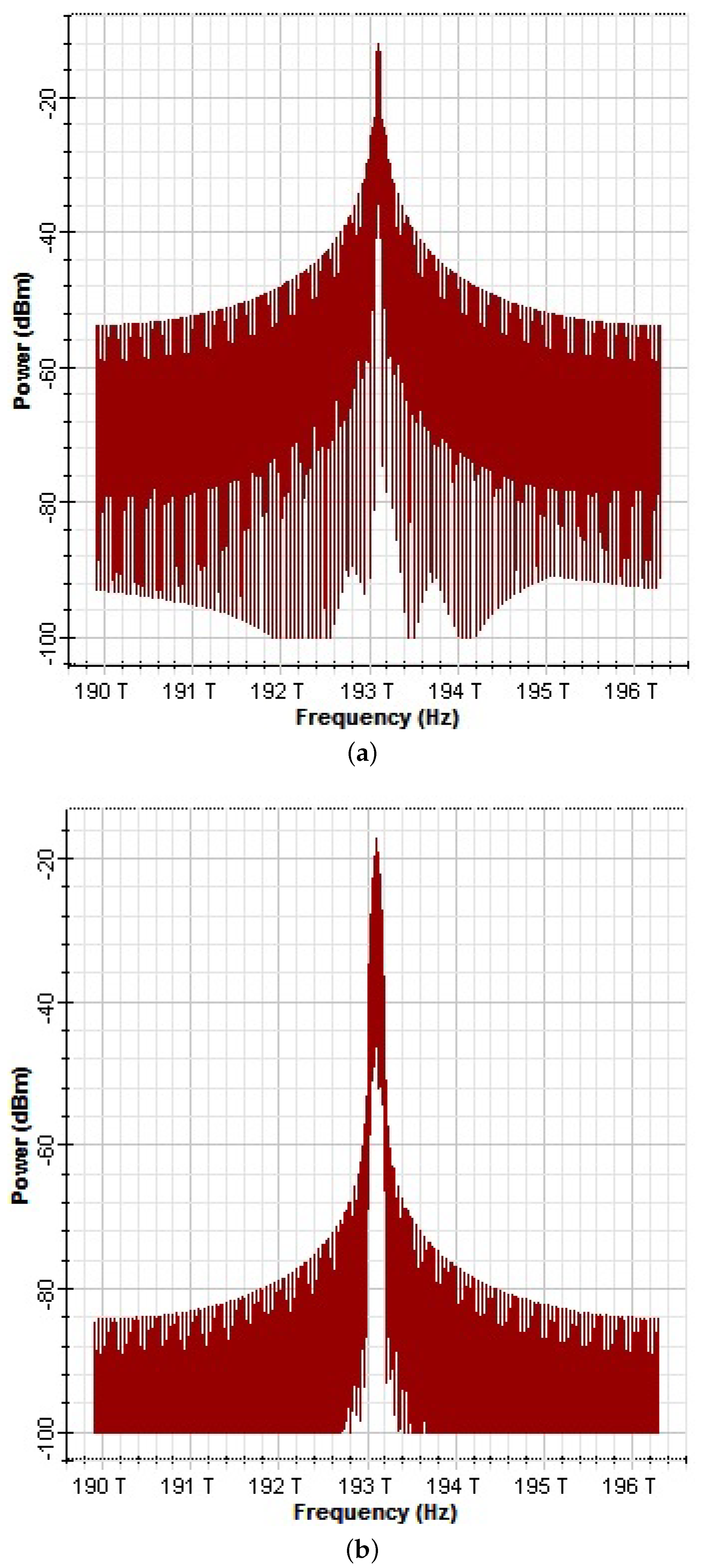
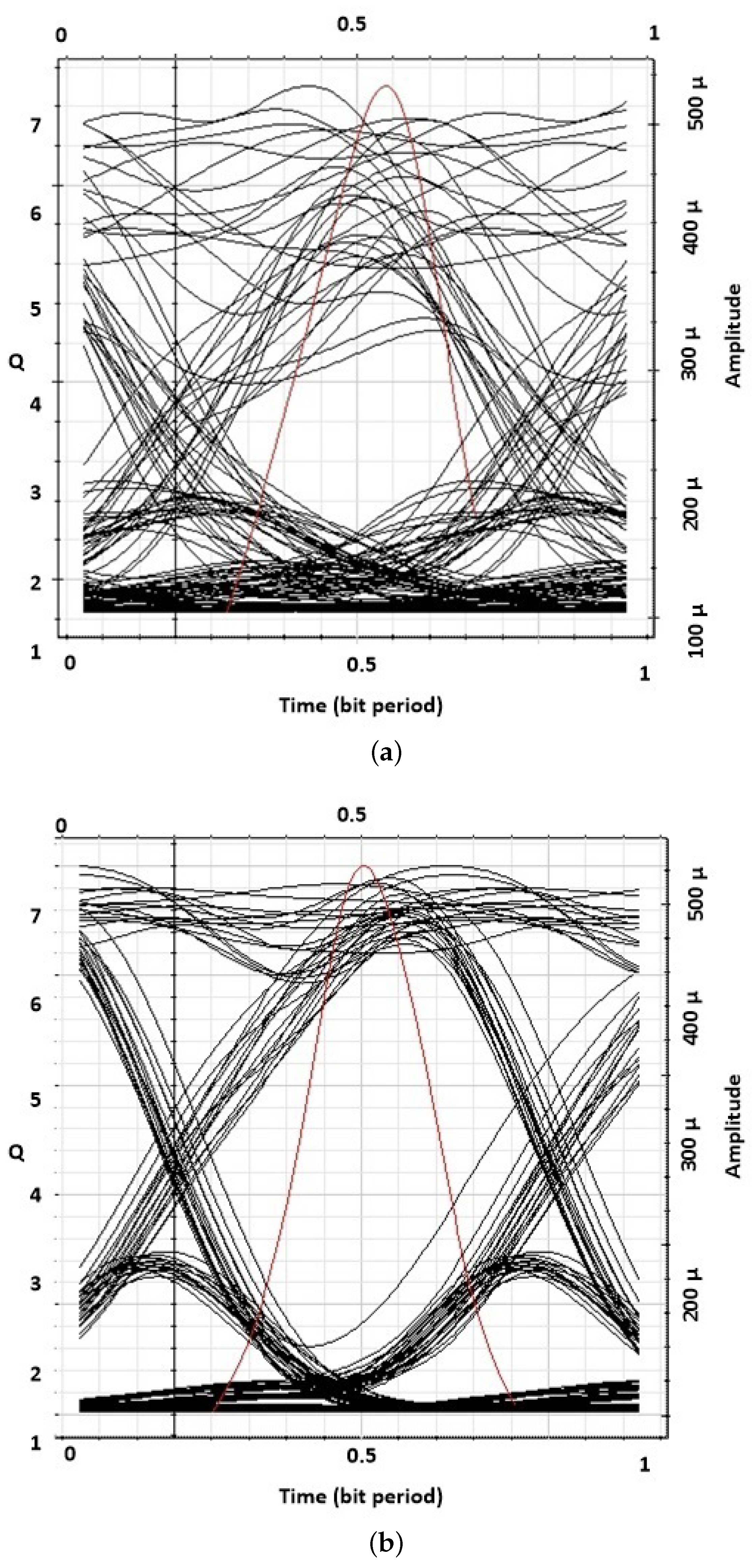
4. Results and Discussion
| Algorithm 1: Proposed ES-based ECDH algorithm for enhancing physical layer security in ONs |
| ine x and y private keys are selected, including primitive parameters using Equations (5) and (6): |
| = (, ), ECDH session key is computed for OLT, and ONU in ON. |
| : For key extension |
| : H = [], where |
| : Initialize |
| for k = n + 1 to 59. |
| temp = nbox() |
| v = temp⊕ recon( + 1) |
| = ⊕v |
| = ⊕ |
| = ⊕ |
| if key size = 256 bits |
| = nbox() |
| For 128, 192, and 256 bit key, estimate 3,5 and 7 sub-keys |
| k = k + n + 1 |
| is incremented |
| Modify H and go to (initialize ) |
| While encryption |
| generate I and Q data in 128, 192, and 256 blocks |
| initial phase = block(1 − input) ⊕ block(first − sub-key) |
| for round 9, 11, and 13 down to 1 |
| bytesubs = nbox (first phase) |
| for shift row |
| circular shift row 1, 2, 3, and 4 left |
| for each row and column, mcol = constant × shift row, addrv = mcol ⊕ block(round-subkey) |
| for final step, out = repeat (bytesub to circular shift) |
| ciphertext = out |
| go to (generated I and Q step) |
5. Conclusions
Funding
Conflicts of Interest
References
- Ali, F.; Muhammad, F.; Habib, U.; Khan, Y.; Usman, M. Modeling and minimization of FWM effects in DWDM-based long-haul optical communication systems. Photon Netw. Commun. 2020, 41, 36–46. [Google Scholar] [CrossRef]
- Kani, J.; Bourgart, F.; Cui, A.; Rafel, A.; Rodrigues, S. Next generation PON-part I: Technology roadmap and general requirements. IEEE Commun. Mag. 2009, 47, 43–49. [Google Scholar] [CrossRef]
- Ali, F.; Khan, Y.; Muhammad, F.; Habib, U.; Abbas, Z.H.; Khan, M.A.; Ali, A. Extenuation of phase shift influenced nonlinear impairments in fiber optics network. Trans. Emerg. Telecommun. Technol. 2020, 31, e3930. [Google Scholar] [CrossRef]
- Mesaritakis, C.; Akriotou, M.; Kapsalis, A.; Grivas, E.; Chaintoutis, C.; Nikas, T.; Syvridis, D. Physical unclonable function based on a multi-mode optical waveguide. Sci. Rep. 2018, 8, 1–12. [Google Scholar] [CrossRef]
- Uppu, R.; Wolterink, T.A.; Goorden, S.A.; Chen, B.; Škorić, B.; Mosk, A.P.; Pinkse, P.W. Asymmetric cryptography with physical unclonable keys. Quantum Sci. Technol. 2019, 4, 045011. [Google Scholar] [CrossRef] [Green Version]
- Ji, J.; Zhang, G.; Wang, K.; Xu, M. Improvement of physical-layer security and reliability in coherent time-spreading OCDMA wiretap channel. Opt. Quant. Electron. 2018, 50, 215. [Google Scholar] [CrossRef]
- Skorin-Kapov, N.; Furdek, M.; Zsigmond, S.; Wosinska, L. Physical-layer security in evolving optical networks. IEEE Commun. Mag. 2016, 54, 110–117. [Google Scholar] [CrossRef]
- Wang, Z.; Xiao, Y.; Wang, S.; Yan, Y.; Wang, B.; Chen, Y.; Zhou, Z.; He, J.; Yang, L. Probabilistic shaping based constellation encryption for physical layer security in OFDM RoF system. Opt. Express 2021, 29, 17890–17901. [Google Scholar] [CrossRef]
- Ji, J.; Zhang, G.; Li, W.; Sun, L.; Wang, K.; Xu, M. Performance analysis of physical-layer security in OCDMA-based wiretap channel. J. Opt. Commun. Netw. 2017, 9, 813–818. [Google Scholar] [CrossRef]
- Javidi, B.; Carnicer, A.; Yamaguchi, M.; Nomura, T.; Pérez-Cabré, E.; Millán, M.S.; Nishchal, N.K.; Torroba, R.; Barrera, J.F.; He, W.; et al. Roadmap on optical security. J. Opt. 2016, 18, 083001. [Google Scholar] [CrossRef]
- Situ, G.; Gopinathan, U.; Monaghan, D.S.; Sheridan, J.T. Cryptanalysis of optical security systems with significant output images. Appl. Opt. 2017, 46, 5257–5262. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Guan, K.; Tulino, A.M.; Winzer, P.J.; Soljanin, E. Secrecy capacities in space-division multiplexed fiber optic communication systems. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1325–1335. [Google Scholar] [CrossRef]
- Furdek, M.; Skorin-Kapov, N.; Wosinska, L. Attack-Aware Dedicated Path Protection in Optical Networks. J. Light. Technol. 2016, 34, 1050–1061. [Google Scholar] [CrossRef]
- Furdek, M.; Natalino, C.; Giglio, A.D.; Schiano, M. Optical network security management: Requirements, architecture, and efficient machine learning models for detection of evolving threats. IEEE/Osa J. Opt. Commun. Netw. 2021, 13, A144–A155. [Google Scholar] [CrossRef]
- Bai, W.; Yang, H.; Zhao, Y.; Zhang, J.; Tan, Y.; Zhu, X.; Ding, H. Security strategy against multipoint eavesdropping in Elastic Optical Networks. In Proceedings of the 2016 21st OptoElectronics and Communications Conference (OECC) Held Jointly with 2016 International Conference on Photonics in Switching (PS), Niigata, Japan, 3–7 July 2016; pp. 1–3. [Google Scholar]
- Yang, X.; Shen, Z.; Hu, X.; Hu, W. Physical layer encryption algorithm for chaotic optical OFDM transmission against chosen-plaintext attacks. In Proceedings of the 2016 18th International Conference on Transparent Optical Networks (ICTON), Trento, Italy, 10–14 July 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Abbade, M.L.F.; Lessa, L.S.; Santos, M.d.O.; Prado, A.J.d.; Aldaya, I. A New DSP-Based Physical Layer Encryption Technique Applied to Passive Optical Networks. In Proceedings of the 2018 20th International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 1–5 July 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Dahan, D.; Mahlab, U. Security threats and protection procedures for optical networks. IET Optoelectron. 2017, 11, 186–200. [Google Scholar] [CrossRef]
- Abbade, M.L.; Cvijetic, M.; Messani, C.A.; Alves, C.J.; Tenenbaum, S. All-optical cryptography of M-QAM formats by using two-dimensional spectrally sliced keys. Appl. Opt. 2015, 54, 4359–4365. [Google Scholar] [CrossRef]
- Savva, G.; Manousakis, K.; Rak, J.; Tomkos, I.; Ellinas, G. High-Power Jamming Attack Mitigation Techniques in Spectrally-Spatially Flexible Optical Networks. Access IEEE 2021, 9, 28558–28572. [Google Scholar] [CrossRef]
- Xiao, Y.; Wang, Z.; Cao, J.; Deng, R.; Liu, Y.; He, J.; Chen, L. Time-frequency domain encryption with SLM scheme for physical-layer security in an OFDM-PON system. IEEE/OSA J. Opt. Commun. Netw. 2018, 10, 46–51. [Google Scholar] [CrossRef]
- Wu, Y.; Yu, Y.; Hu, Y.; Sun, Y.; Wang, T.; Zhang, Q. Channel-Based Dynamic Key Generation for Physical Layer Security in OFDM-PON Systems. IEEE Photonics J. 2021, 13, 1–9. [Google Scholar] [CrossRef]
- Liu, B.; Zhang, L.; Xin, X.; Liu, N. Piecewise Chaotic Permutation Method for Physical Layer Security in OFDM-PON. IEEE Photonics Technol. Lett. 2016, 28, 2359–2362. [Google Scholar] [CrossRef]
- Zhang, W.; Zhang, C.; Chen, C.; Zhang, H.; Jin, W.; Qiu, K. Hybrid Chaotic Confusion and Diffusion for Physical Layer Security in OFDM-PON. IEEE Photonics J. 2017, 9, 1–10. [Google Scholar] [CrossRef]
- Cvijetic, N. OFDM for next-generation optical access networks. J. Lightw. Technol. 2012, 30, 384–398. [Google Scholar] [CrossRef]
- Zhang, W.; Zhang, C.; Jin, W.; Chen, C.; Jiang, N.; Qiu, K. Chaos coding-based QAM IQ-encryption for improved security in OFDMA-PON. IEEE Photon. Technol. Lett. 2014, 26, 1964–1967. [Google Scholar] [CrossRef]
- Chang, J.; Cvijetic, N.; Wang, T.; Prucnal, P. Adaptive Photonic Beamforming for Physical Layer Security of Mobile Signals in Optical Fronthaul Networks. In Frontiers in Optics; OSA Technical Digest (Online); Paper FTh1B.5; Optical Society of America: Tucson, AZ, USA, 2014. [Google Scholar]
- Hu, X.; Yang, X.; Shen, Z.; He, H.; Hu, W.; Bai, C. Chaos-Based Partial Transmit Sequence Technique for Physical Layer Security in OFDM-PON. IEEE Photonics Technol. Lett. 2015, 27, 2429–2432. [Google Scholar] [CrossRef]
- Rothe, S.; Koukourakis, N.; Radner, H.; Lonnstrom, A.; Jorswieck, E.; Czarske, J.W. Physical Layer Security in Multimode Fiber Optical Networks. Sci. Rep. 2020, 10, 2740. [Google Scholar] [CrossRef]
- Mehibel, N.; Hamadouche, M. Authenticated secret session key using elliptic curve digital signature algorithm. Secur. Priv. 2021, 4, e148. [Google Scholar]
- Biswas, G.P. Establishment of authenticated secret session keys using digital signature standard. Inform Secur J. 2011, 20, 9–16. [Google Scholar] [CrossRef]


| Name | Description |
|---|---|
| Lorentzian laser | 1540.4 nm, 256 samples |
| Subcarrier | 1200 |
| Length | 200 km |
| Launch power | −10 to 4 dBm |
| Data rate | 100 Gbps |
| No FFT point | 1200 |
| Line width | 0.15 MHz |
| Symbol rate | 2.5 × 10 |
| Noise figure | 4 dB |
| Gain | 30 dB |
| Used Methodology | [28] | [29] | Presented Model |
|---|---|---|---|
| Modulation Format | 16QAM-OFDM | 16QAM-OFDM | 64QAM-OFDM |
| Encryption Technique | 3- level chaotic encryption | Quantum Key Distribution (QKD) | ECDH-ES |
| Data Rate | 10 Gbps | 40 Gbps | 100 Gbps |
| Sumbol Rate | 10 | 10 | 2.5 × 10 |
| Fiber length | 20 km | 100 km | 200 km |
| Parameter | ECDH [30] | Biswas Approach [31] | Presented ECDH-ES |
|---|---|---|---|
| Session Key | - | yes | yes |
| Mutual Encryption | Exist | Exist | Exist |
| Joint Secret Key | - | - | yes |
| Impersonation security breach | Not Secure | Not Secure | Secure |
| No of I and Q Generated Blocks | 128 | 128 | 128, 192, and 256 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Armghan, A. Derogation of Physical Layer Security Breaches in Maturing Heterogeneous Optical Networks. Electronics 2021, 10, 2021. https://doi.org/10.3390/electronics10162021
Armghan A. Derogation of Physical Layer Security Breaches in Maturing Heterogeneous Optical Networks. Electronics. 2021; 10(16):2021. https://doi.org/10.3390/electronics10162021
Chicago/Turabian StyleArmghan, Ammar. 2021. "Derogation of Physical Layer Security Breaches in Maturing Heterogeneous Optical Networks" Electronics 10, no. 16: 2021. https://doi.org/10.3390/electronics10162021
APA StyleArmghan, A. (2021). Derogation of Physical Layer Security Breaches in Maturing Heterogeneous Optical Networks. Electronics, 10(16), 2021. https://doi.org/10.3390/electronics10162021






