Optimization of the AODV-Based Packet Forwarding Mechanism for BLE Mesh Networks
Abstract
:1. Introduction
2. BLE Mesh Architecture and Message Routing Protocols
2.1. BLE Mesh Architecture
- Model layer:Models define operations based on use cases in the model layer. The Bluetooth mesh model specification or vendors specify these models. The models are identifiable by Bluetooth SIG and vendor-defined unique identifiers of 16 and 32 bit;
- Foundation layer:The states, messages, and models are defined in this layer that are needed to setup and maintain mesh networks in different contexts. The configuration client and server model and the health client and server model are the two types of models specified in the Bluetooth SIG specification;
- Access layer:The access layer specifies how the upper transport layer can be used by the upper layers. It is also responsible for defining the app’s data structure and implementing encryption/decryption operations. Finally, before passing data to the upper layers, it ensures that the network and application keys in the incoming data are correct;
- Upper transport layer:This layer is in charge of application data encryption, decryption, and authentication, as well as keeping the secrecy of access messages. It also specifies the control messages that are used to coordinate the transport layer functions between nodes;
- Lower transport layer:This layer specifies how messages in the top layers are segmented and reassembled in the lower-layer protocol into units of data. It is also in charge of controlling segmentation and reassembly;
- Network layer:Data transfer addressing, formatting, encryption, and authentication are all handled by the network layer. This layer is also in charge of handling message forwarding and dropping decisions.The BLE mesh network layer, on the other hand, lacks a routing mechanism and relies on a flooding-based approach;
- Bearer layer:The message transmission mechanism is defined by the bearer layer. In the newest BLE 5 mesh requirements, there are two types of bearers available: advertising bearer and GATT bearer;
- Bluetooth core specifications:The Bluetooth core specifications’ network stack supports the physical data transfer between the nodes/devices with the help of a layering architecture. The host, controller, and physical/radio layers are the three fundamental layers of the BLE network stack.The host layer, which sits just beneath the application layer, has many nonreal-time network and transport protocols that allow apps on different devices to communicate with one another. The Generic Access Profile (GAP), Generic Attribute Profile (GATT), Security Manager (SM), Attribute Protocol (ATT), and Logical Link Control and Adaptation Protocol (L2CAP) are among the modules found in this layer.The BLE Link Layer (LL) protocols (low-level and real-time) are implemented by the controller layer. It performs packet reception, schedules transmissions, and ensures data delivery to the destination, in addition to handling control operations and physical layer interfaces via the Host Control Interface (HCI);The physical layer is in charge of wireless signal transmission. BLE uses the 2.4 GHz Industrial, Scientific, and Medical (ISM) frequency spectrum, with 40 narrowband channels (2 MHz bandwidth) divided into three Advertising Channels (AC) (Ch. 37–39) and 37 Data Channels (DC) (Ch. 0–36). Device detection, connection establishment, and the transmission of broadcast messages are all handled by the ACs. DCs, on the other hand, allow two-way data flow between linked devices and rely on Adaptive Frequency Hopping (AFH) for subsequent communications.Moreover, the BLE communication profiles are discussed in Appendix A.
2.2. Message Routing Protocols
- Reactive (on-demand) protocolsMessages received by the reactive forwarding protocol provide information about the destination nodes. Every transmission table entry is only active for a limited amount of time. The item will be erased if no traffic is encountered for a certain destination within the specified time frame. A process for new route discovery will be launched upon receiving the request from the sender node. Examples of such protocols include ad hoc AODV [4] and Dynamic Source control Routing (DSR) [5];
- Proactive (table driven) protocolsFor all nodes, whether active or not, explicit forwarding table entries are maintained by proactive forwarding protocols. The Bellman–Ford algorithm is used to keep feasible pathways to important nodes, allowing data to be delivered to the destination as soon as possible. The examples of this kind of protocol include: Babel, Optimized Link State Routing (OLSR) [10], Destination Sequenced Distance Vector (DSDV) [11], and others;
- Cluster-based protocolsScatternet is a kind of cluster-based transmission protocol in BLE 4.1 to support multihop communications. The network nodes are divided into multiple overlapping disjoint clusters [12]. Each cluster is led by the cluster head, who maintains memberships in a cluster and is then utilized to find the path that connects the clusters. The clustering of nodes decreases the flood during the path discovery procedure. In addition, the protocol monitors any single directional links for transmission between clusters and intracluster. Protocols of this type include the Two-Tier Data Dissemination Protocol (TTDD) [13], ring routing [14], Energy-Efficient Secured Ring Routing (E2SR2) [15], and others.
3. Related Works
4. Optimized-AODV Protocol Topologies and Testbed Design
4.1. O-AODV Topologies and Testbed Design
4.1.1. Initial Findings and Proposed Optimizations for O-AODV
4.1.2. Hardware and Software Utilized for the O-AODV Testbed
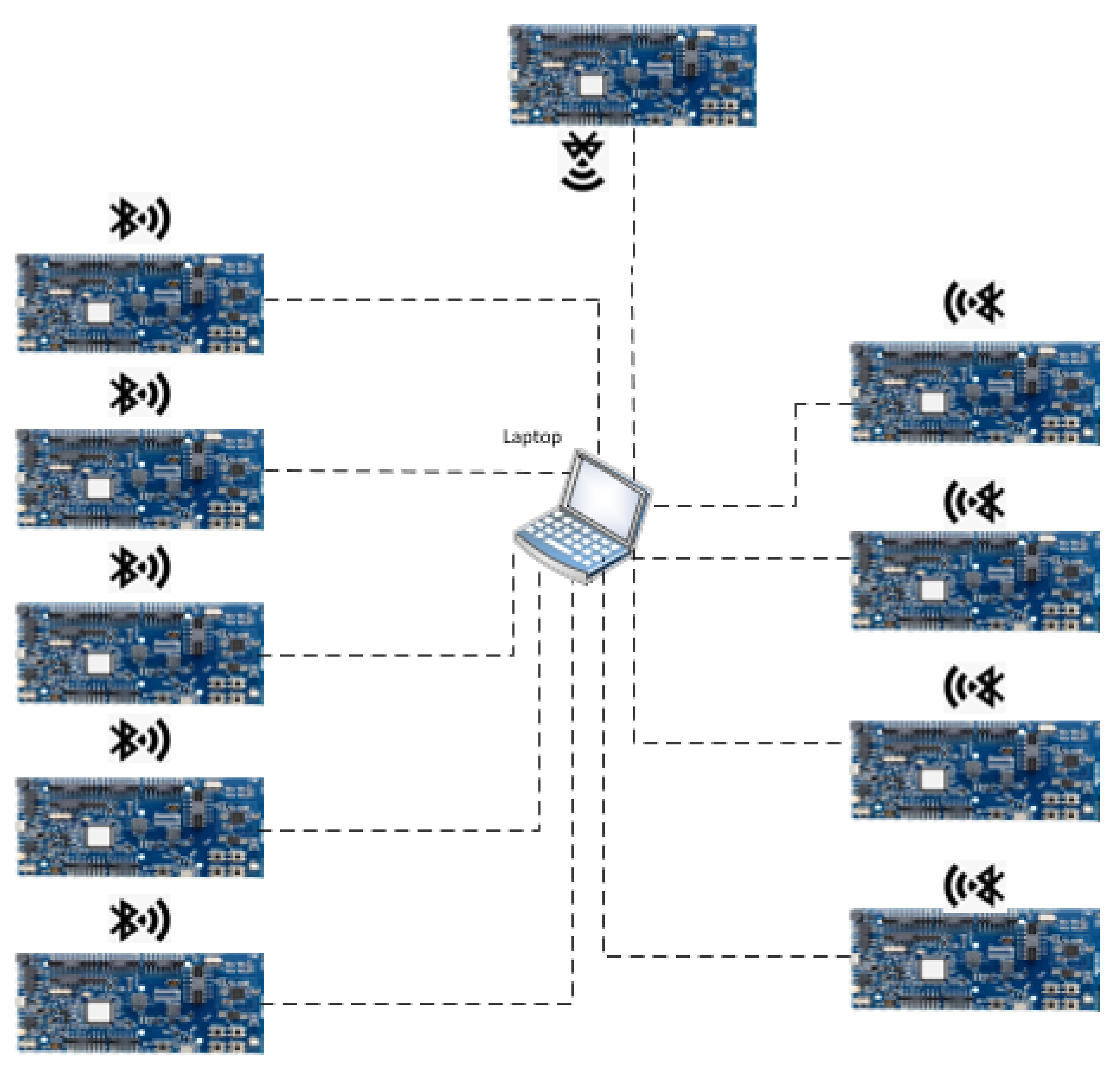
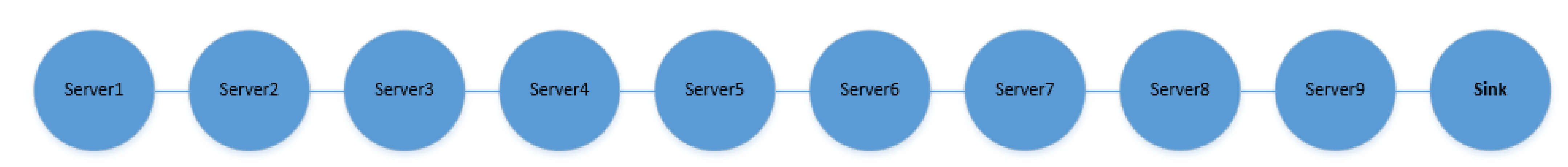
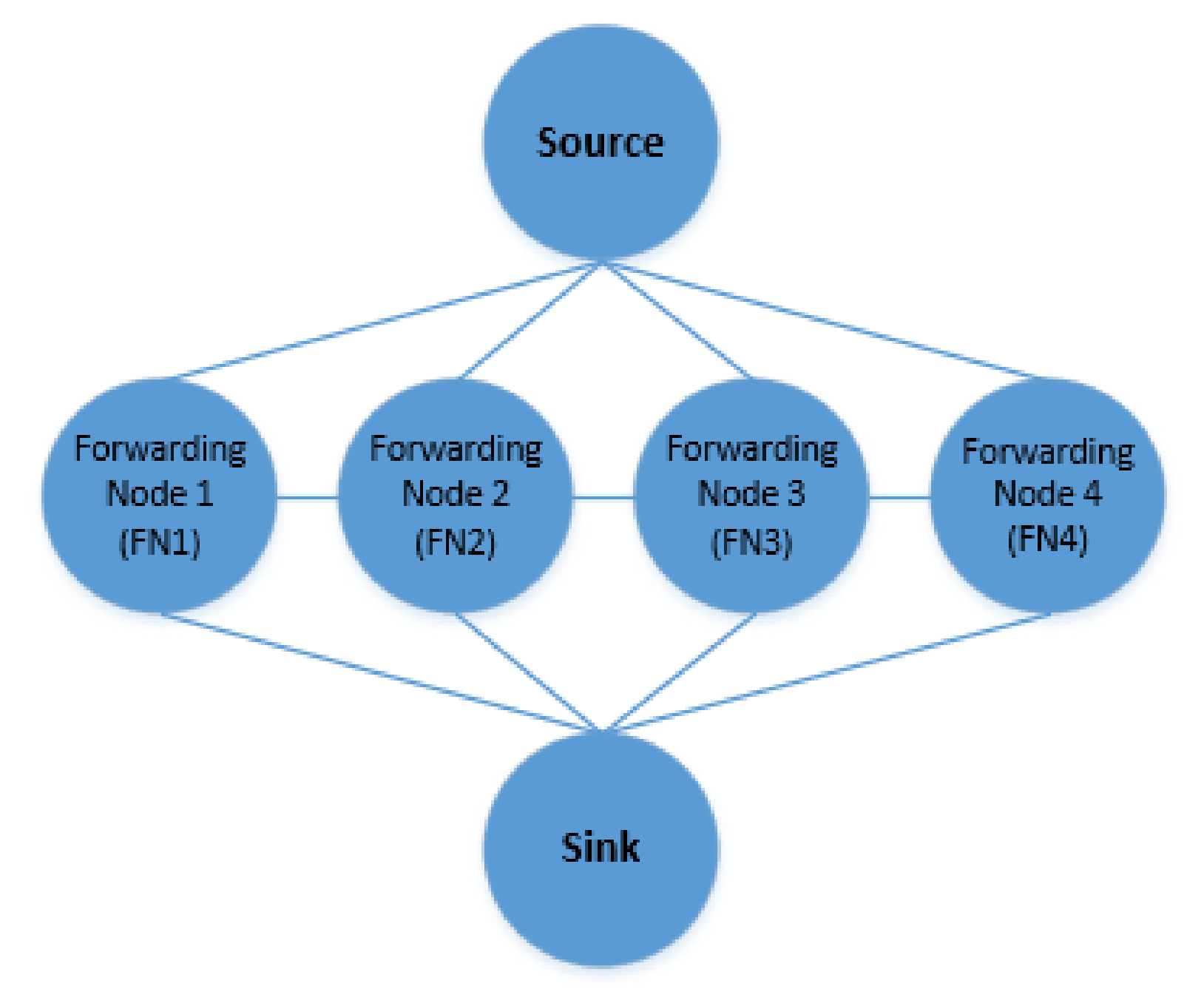
4.1.3. Experimental Topologies
5. Proposed Optimized-AODV Protocol Optimizations Achieved with the Experimental Results
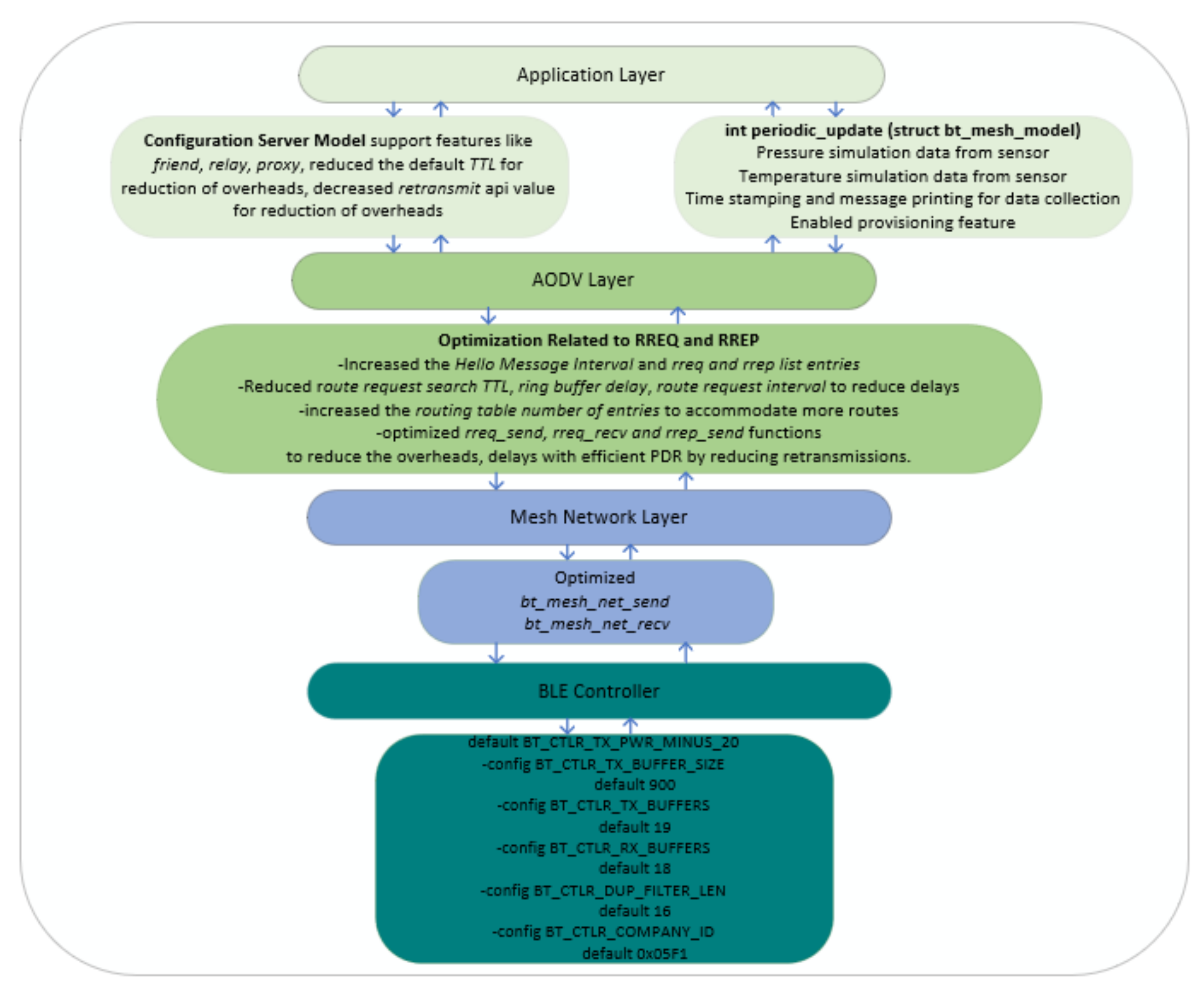
5.1. How the Optimizations Were Achieved
5.1.1. Route Request and Route Reply Optimization
5.1.2. Route Request Search and TTL Optimization
5.1.3. BLE Mesh Network and AODV Layer Optimization
5.1.4. Application Layer Optimization
5.1.5. Impact of Optimizations
5.2. Performance Measurement Metrics Used for the Experiments
Average End-to-End Delay
Average Per-Hop Delay
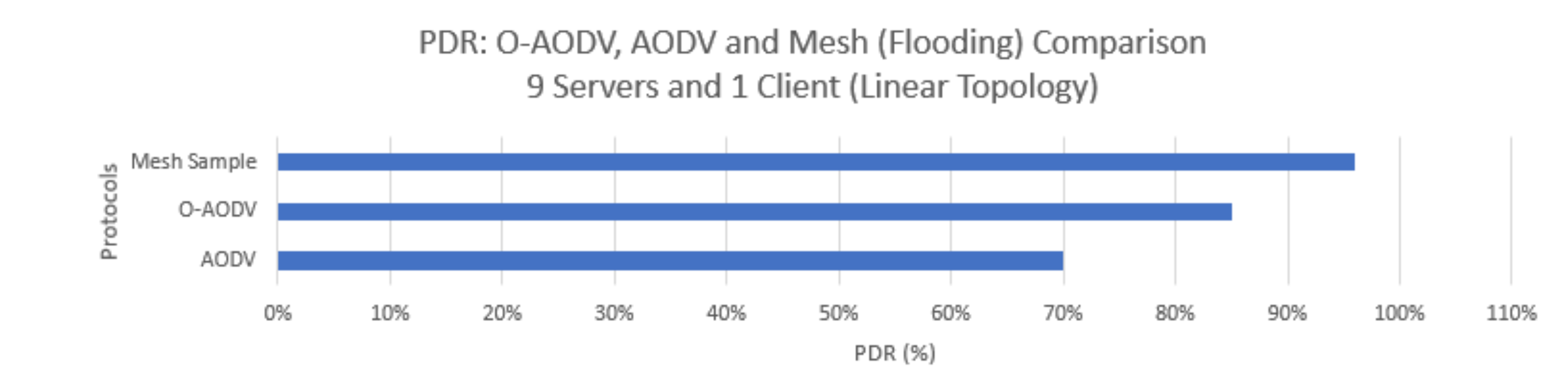
PDR
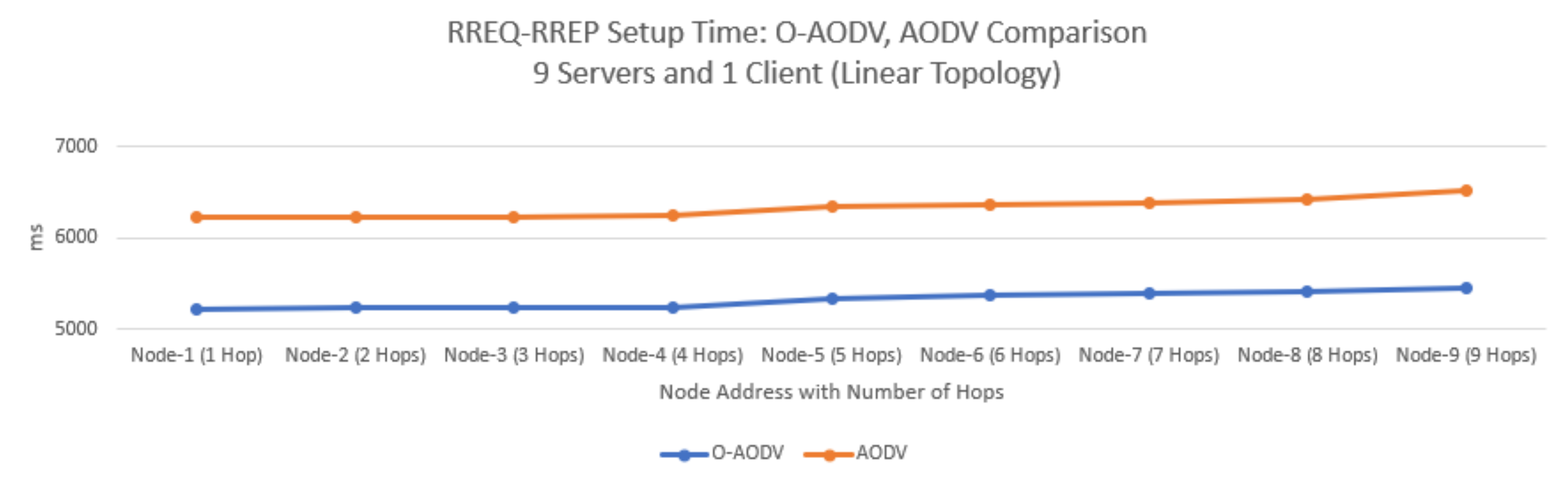
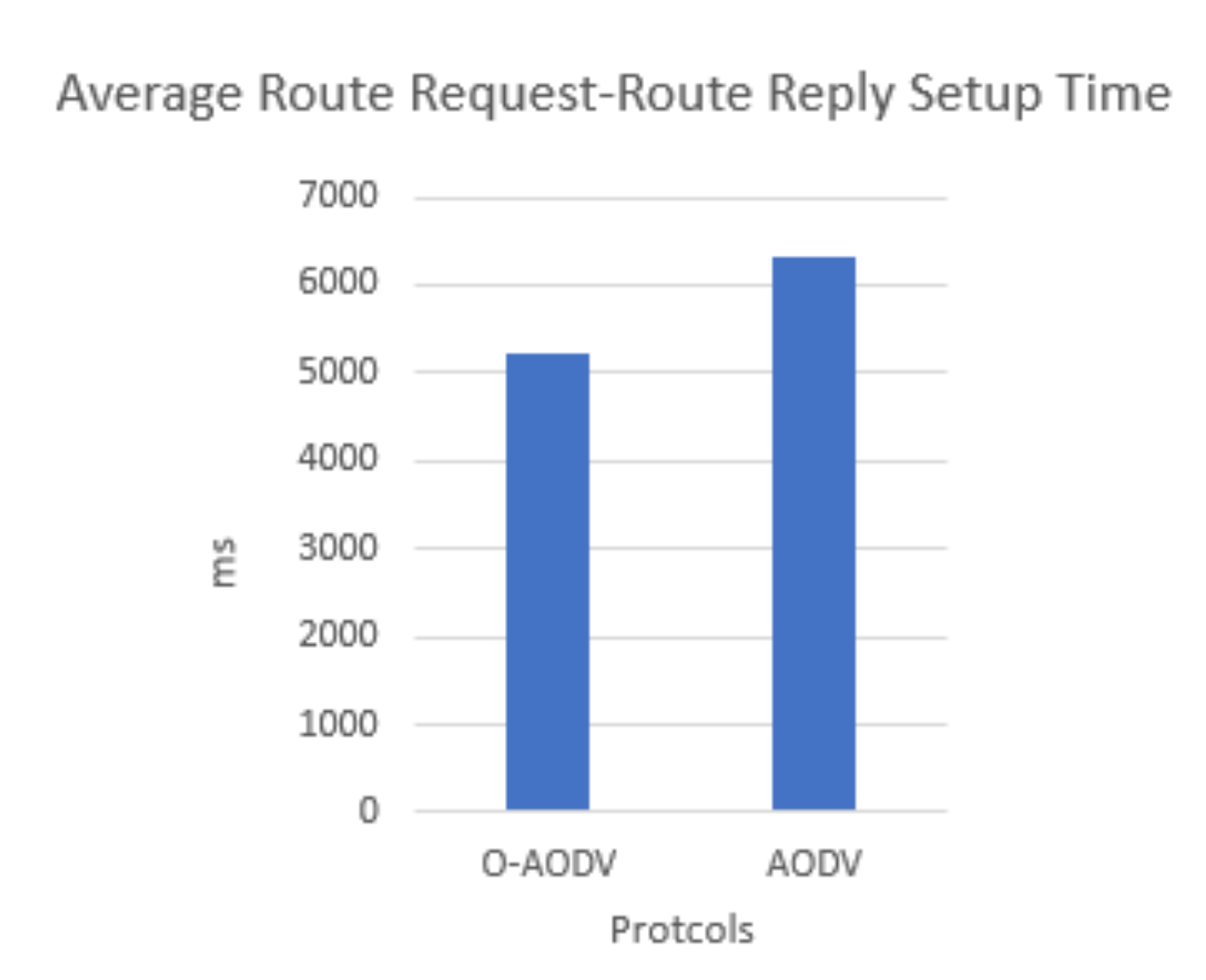
RREQ-RREP Setup Time
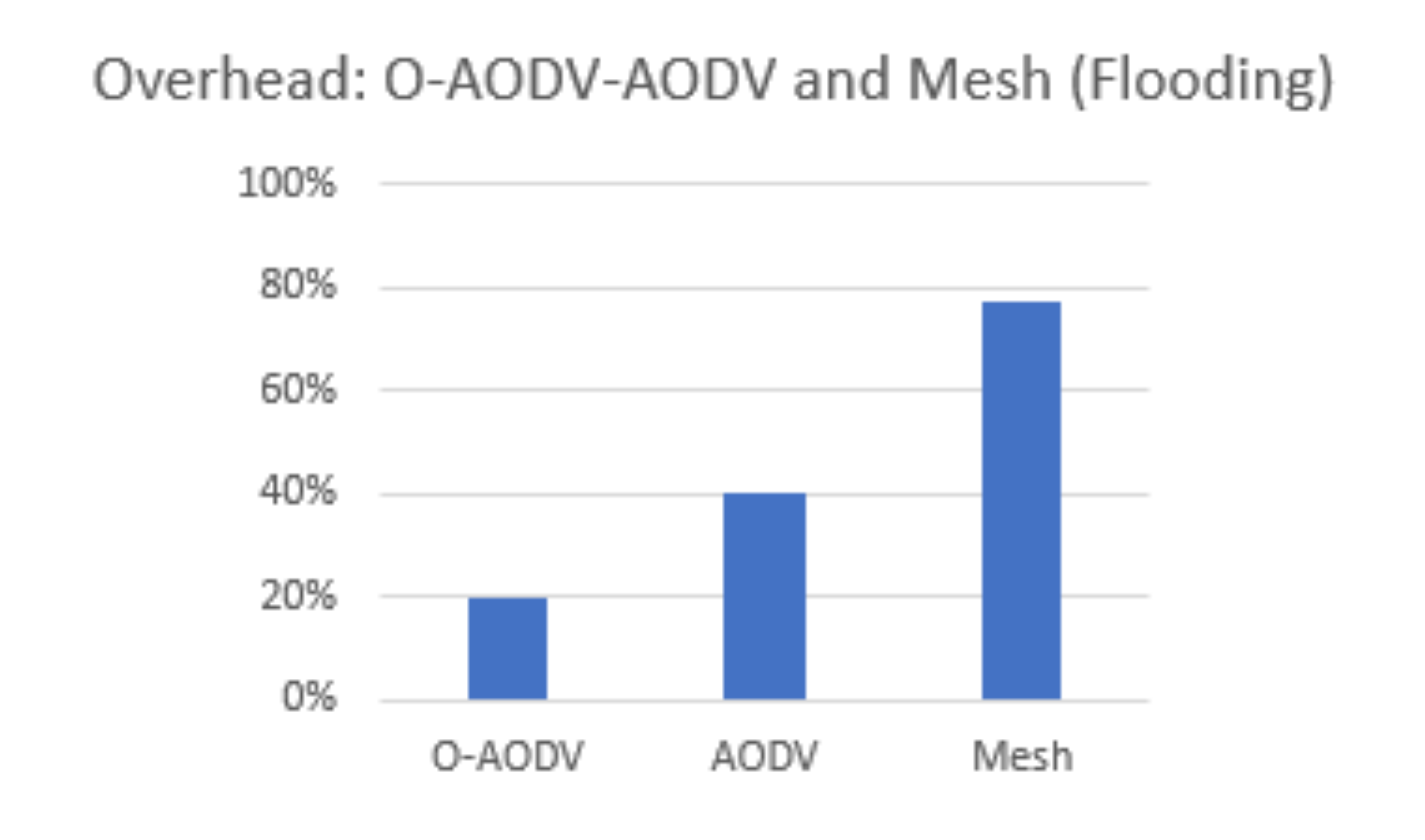
Overhead
5.3. Common Experiment Setup and Configurations
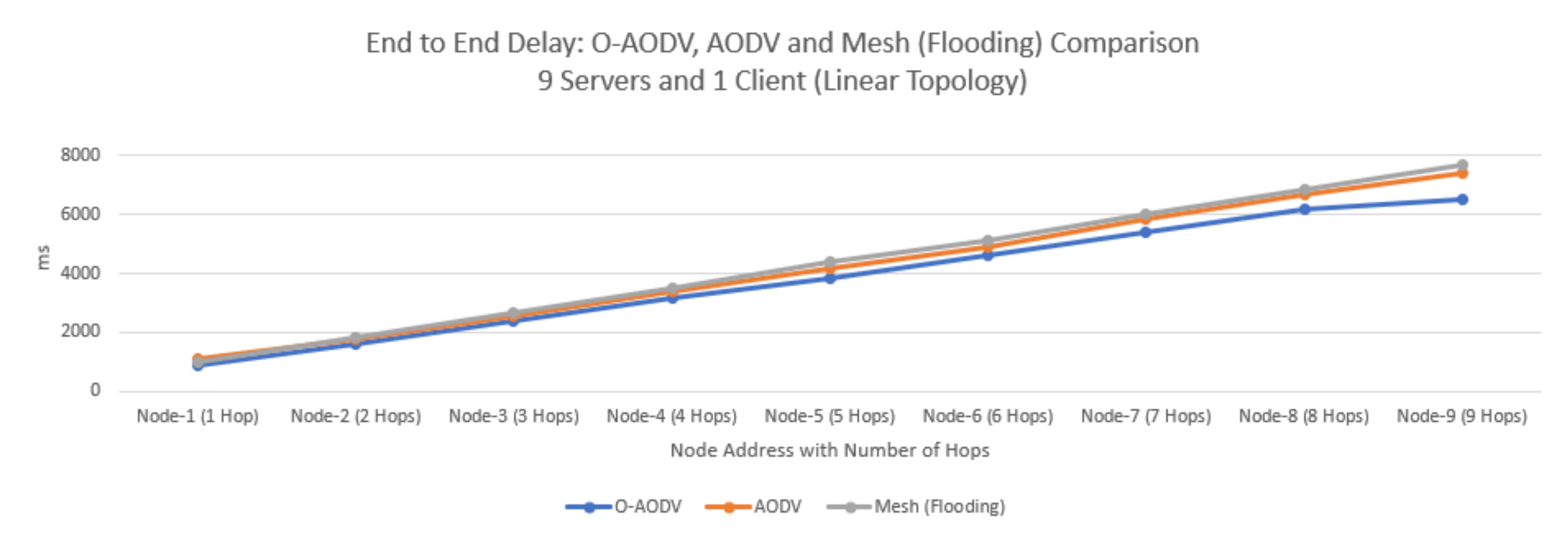
5.4. Experimental Results: O-AODV Linear Topology with 10 Nodes
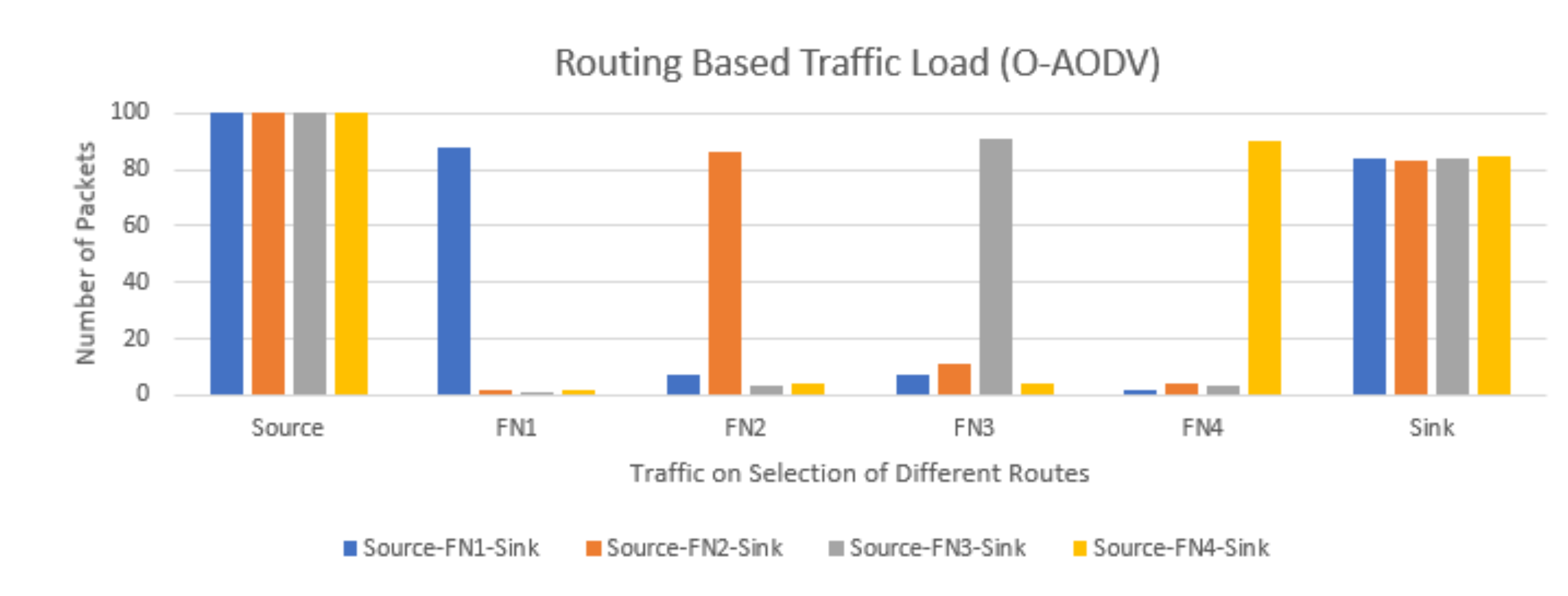
5.5. Experimental Results: O-AODV Multipath Topology with Six Nodes
5.6. Experimental Results: O-AODV Multipath Topology with 10 Nodes
5.7. Experimental Result Findings
5.8. Experiment Results, Discussion, and Research Contributions
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AC | Advertising Channel |
| AFH | Adaptive Frequency Hopping |
| AODV | Ad hoc On-demand Distance Vector |
| ATT | Attribute Protocol |
| BLE | Bluetooth Low-Energy |
| DC | Data Channel |
| DSDV | Destination-Sequenced Distance Vector |
| DSR | Dynamic Source Control Routing |
| E2SR2 | Energy-Efficient Secured Ring Routing |
| FM | FruityMesh |
| GAP | Generic Access Profile |
| GATT | Generic Attribute Profile |
| IETF | Internet Engineering Task Force |
| LL | Link Layer |
| LLP | Low-Energy Legacy Pairing |
| LESC | Low-Energy Secure Connection |
| L2CAP | Logical Link Control and Adaptation Protocol |
| MHTS | MultiHop Transfer Service |
| NDN | Named Data Networking |
| O-AODV | Optimized Ad hoc On-demand Distance Vector |
| OLSR | Optimized Link State Routing Protocol |
| PAN | Personal Area Network |
| PDR | Packet Delivery Ratio |
| PDU | Protocol Data Unit |
| SIG | Special Interest Group |
| TDMA | Time-Division Multiple Access |
| TTDD | Two-Tier Data Dissemination |
| WAHN | Wireless Ad Hoc Network |
List of Symbols
| ∑ | Summation sign |
| % | Percentage |
| = | Equals symbol |
| / | Division symbol |
| − | Subtraction (if used with a mathematical equation or formula) |
| D | Average end-to-end delay or average one-way delay |
| i | Packet identifier |
| Mega bits per second | |
| Millisecond | |
| n | Number of packets successfully delivered |
| Reception time | |
| Send time |
Appendix A. BLE Communication Profiles
Appendix A.1. Generic Access Profile
Appendix A.2. Generic Attribute Profile
Appendix A.3. Security Manager
Appendix A.4. Attribute Protocol
Appendix A.5. L2CAP
Appendix B. Zephyr RTOS
Appendix B.1. Bluetooth Support
Appendix B.2. BLE and BLE Mesh Security Features
References
- Ghori, M.R.; Wan, T.C.; Sodhy, G.C. Bluetooth Low Energy 5 Mesh Based Hospital Communication Network (B5MBHCN). In Advances in Cyber Security; Springer: Singapore, 2020; Volume 1132, pp. 247–261. [Google Scholar] [CrossRef]
- Ghori, M.R.; Wan, T.-C.; Sodhy, G.C. Bluetooth Low Energy Mesh Networks: Survey of Communication and Security Protocols. Sensors 2020, 20, 3590. [Google Scholar] [CrossRef] [PubMed]
- Bluetooth. Available online: https://www.Bluetooth.com (accessed on 21 July 2021).
- Perkins, C.; Das, S. Ad Hoc On-Demand Distance Vector (AODV) Routing; Tech. Memo.; University of California: Santa Barbara, CA, USA; University of Cincinnati: Cincinnati, OH, USA, 2003; Available online: https://tools.ietf.org/html/rfc3561 (accessed on 10 June 2021).
- Johnson, D.; Hu, Y. The Dynamic Source Routing Protocol (DSR) for Mobile Ad Hoc Networks for IPv4; Rice University: Houston, TX, USA, 2007; Available online: https://tools.ietf.org/html/rfc4728 (accessed on 5 June 2021).
- Hussein, A.; Tarek, R.; Osama, H.; Fawzy, R.; Elsayed, K.; Taha, M. An AODV-Based Routing Scheme for Large-Scale Bluetooth Low-Energy Mesh Networks. In Proceedings of the 8th International Japan-Africa Conference on Electronics, Communications, and Computations (JAC-ECC), Alexandria, Egypt, 14–15 December 2020; pp. 7–10. [Google Scholar] [CrossRef]
- Zhang, J.; Sun, Z. Assessing multihop performance of reactive routing protocols in wireless sensor networks. In Proceedings of the IEEE International Conference on Communication Software and Networks (ICCSN), Beijing, China, 4–6 June 2016; pp. 444–449. [Google Scholar] [CrossRef]
- Bhargava, N.; Bhargava, R.; Mathuria, M.; Kumawat, A. Performance Evaluation of Reactive and Proactive Routing Protocols over MANET. Int. J. Comput. Appl. 2013, 73, 3. [Google Scholar] [CrossRef]
- Murillo, Y.; Reynders, B.; Chiumento, A.; Pollin, S. A Multiprotocol Low-Cost Automated Testbed for BLE Mesh. IEEE Commun. Mag. 2019, 57, 76–83. [Google Scholar] [CrossRef]
- Clausen, T.; Jacquet, P. Optimized Link State Routing Protocol (OLSR); Project Hipercom; INRIA: Paris, France, 2003; Available online: https://tools.ietf.org/html/rfc3626 (accessed on 5 June 2021).
- Perkins, C.; Bhagwat, P. Highly Dynamic Destination-Sequenced Distance-Vector Routing (DSDV) for Mobile Computers. ACM SIGCOMM Comput. Commun. Rev. 1999, 24, 234–244. [Google Scholar] [CrossRef]
- Jiang, M.; Li, J.; Hu, Y. Cluster Based Routing Protocol (CBRP) Functional Specification; National University of Singapore (NUS): Singapore, 1999. [Google Scholar]
- Luo, H.; Ye, F.; Cheng, J.; Lu, S.; Zhang, L. TTDD: Two-Tier Data Dissemination in Large-Scale Wireless Sensor Networks. Wirel. Netw. 2005, 11, 161–175. [Google Scholar] [CrossRef]
- Tunca, C.; Isik, S.; Donmez, M.Y.; Ersoy, C. Ring Routing: An Energy-Efficient Routing Protocol for Wireless Sensor Networks with a Mobile Sink. IEEE Trans. Mob. Comput. 2015, 14, 1947–1960. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. E2SR2: An acknowledgement-based mobile sink routing protocol with rechargeable sensors for wireless sensor networks. Wirel. Netw. 2019, 25, 2697–2721. [Google Scholar] [CrossRef]
- Mikhaylov, K.; Tervonen, J. Multihop data transfer service for Bluetooth Low Energy. In Proceedings of the 13th International Conference on ITS Telecommunications (ITST), Tampere, Finland, 5–7 November 2013; pp. 319–324. [Google Scholar] [CrossRef]
- Martinez, C.; Eras, L.; Dominguez, F. The Smart Doorbell: A proof-of-concept Implementation of a Bluetooth Mesh Network. In Proceedings of the IEEE Third Ecuador Technical Chapters Meeting (ETCM), Cuenca, Ecuador, 15–19 October 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Balogh, A.; Imre, S.; Lendvai, K.; Szabo, S. Service Mediation in multihop Bluetooth Low Energy networks based on NDN approach. In Proceedings of the 23rd International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 16–18 September 2015; pp. 285–289. [Google Scholar] [CrossRef]
- Guo, Z.; Harris, I.G.; Tsaur, L.; Chen, X. An on-demand scatternet formation and multihop routing protocol for BLE-based wireless sensor networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 1590–1595. [Google Scholar] [CrossRef]
- Tanaka, K.; Murase, M.; Naito, K. Prototype implementation of BLE based automated data collection scheme in agricultural measurement system. In Proceedings of the 15th IEEE Annual Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–2. [Google Scholar] [CrossRef]
- Bardoutsos, A.; Filios, G.; Katsidimas, I.; Nikoletseas, S. Energy Efficient Algorithm for Multihop BLE Networks on Resource-Constrained Devices. In Proceedings of the 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 400–407. [Google Scholar] [CrossRef]
- Sirur, S.; Juturu, P.; Gupta, H.P.; Serikar, P.R.; Reddy, Y.K.; Barak, S.; Kim, B. A mesh network for mobile devices using Bluetooth low energy. In Proceedings of the IEEE Sensors, Busan, Korea, 1–4 November 2015. [Google Scholar] [CrossRef]
- Ng, P.C.; She, J. A Novel Overlay Mesh with Bluetooth Low EnergyNetwork. In Proceedings of the WCNC, Marrakesh, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Dvinge, R.T.E.; Stalmach, A.; Nalpantidis, L. Connection-Based Bluetooth Mesh Network as a Low Energy Solution for Off-Grid Data Networks. In Proceedings of the 8th International Conference on Modern Circuits and Systems Technologies (MOCAST), Thessaloniki, Greece, 13–15 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Li, R.; Li, X. Directional Multi-path Routing Algorithm Based on BLE Mesh. In Proceedings of the CSQRWC, Taiyuan, China, 18–21 July 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Leonardi, L.; Patti, G.; Lo Bello, L. Multi-Hop Real-Time Communications Over Bluetooth Low Energy Industrial Wireless Mesh Networks. IEEE Access 2018, 6, 26505–26519. [Google Scholar] [CrossRef]
- Patti, G.; Leonardi, L.; Lo Bello, L. A Bluetooth Low Energy real-time protocol for Industrial Wireless mesh Networks. In Proceedings of the IECON 2016-42nd Annual Conference of the IEEE Industrial Electronics Society, Florence, Italy, 23–26 October 2016; pp. 4627–4632. [Google Scholar] [CrossRef]
- Jung, C.; Kim, K.; Seo, J.; Silva, B.; Han, K. Topology Configuration and Multihop Routing Protocol for Bluetooth Low Energy Networks. IEEE Access 2017, 5, 9587–9598. [Google Scholar] [CrossRef]
- Seymer, P.; Wijesekera, D.; Kan, C. Secure Outdoor Smart Parking Using Dual Mode Bluetooth Mesh Networks. In Proceedings of the VTC2019-Spring, Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Hansen, E.A.; Nielsen, M.H.; Serup, D.E.; Williams, R.J.; Madsen, T.K.; Abildgren, R. On Relay Selection Approaches in Bluetooth Mesh Networks. In Proceedings of the 10th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Moscow, Russia, 5–9 November 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Wang, S.; Chiang, K. BLE Tree Networks for Sensor Devices in Internet of Thing. In Proceedings of the DASC, PiCom, DataCom, CyberSciTech, Orlando, FL, USA, 6–10 November 2017; pp. 1304–1309. [Google Scholar] [CrossRef]
- Chiumento, A.; Reynders, B.; Murillo, Y.; Pollin, S. Building a connected BLE mesh: A network inference study. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Barcelona, Spain, 15–18 April 2018. [Google Scholar] [CrossRef]
- Darroudi, S.M.; Gomez, C. Modeling the Connectivity of Data-Channel-Based Bluetooth Low Energy Mesh Networks. IEEE Commun. Lett. 2018, 22, 2124–2127. [Google Scholar] [CrossRef]
- Renode. Available online: https://renode.io/ (accessed on 29 June 2021).
- Zephyr Project. Available online: https://www.zephyrproject.org/ (accessed on 29 June 2021).
- Silva, L.A.; Leithardt, V.R.Q.; Rolim, C.O.; González, G.V.; Geyer, C.F.R.; Silva, J.S. PRISER: Managing Notification in Multiples Devices with Data Privacy Support. Sensors 2019, 19, 3098. [Google Scholar] [CrossRef] [PubMed] [Green Version]





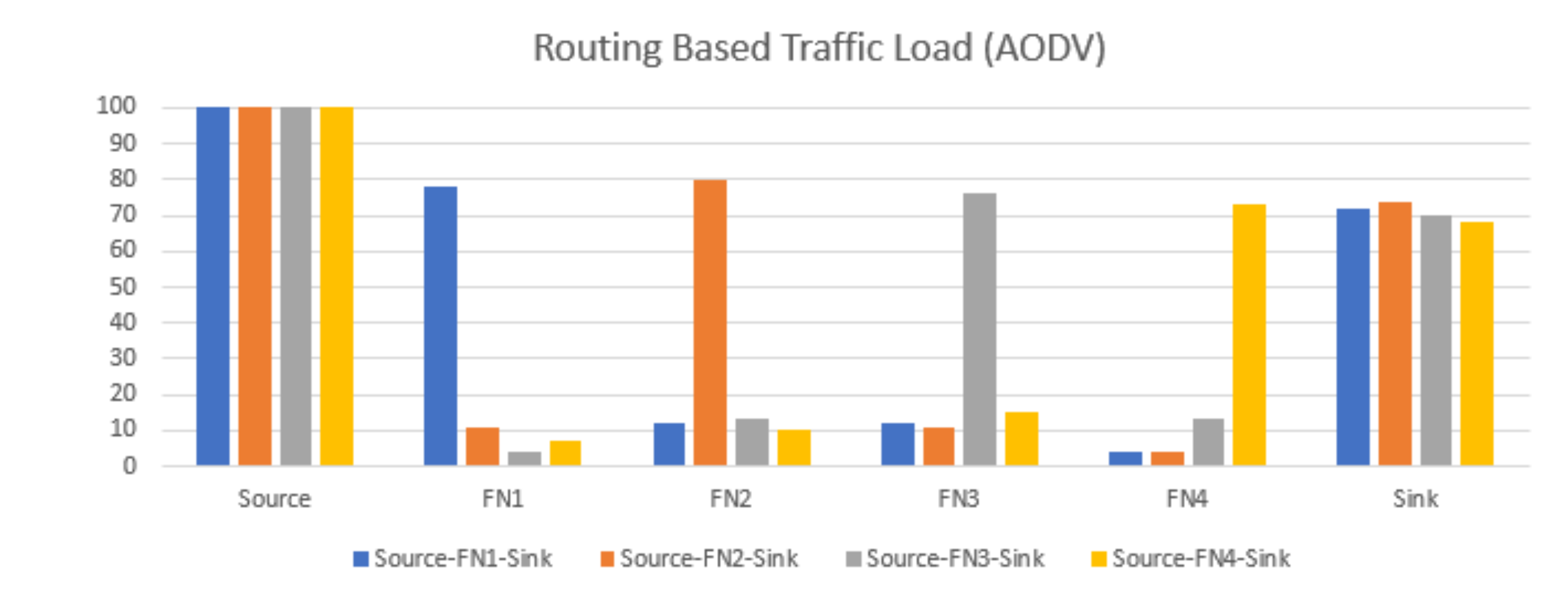
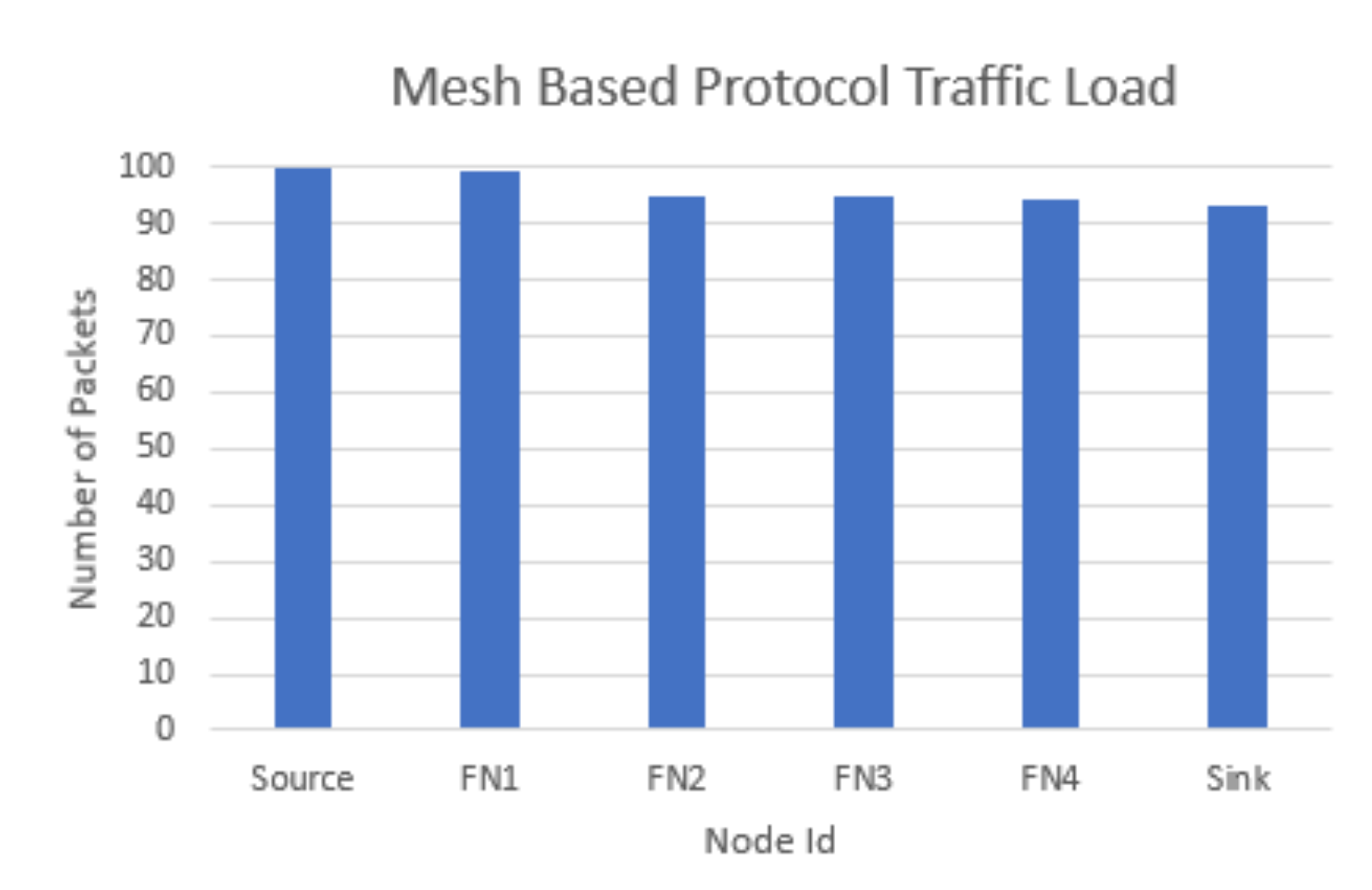

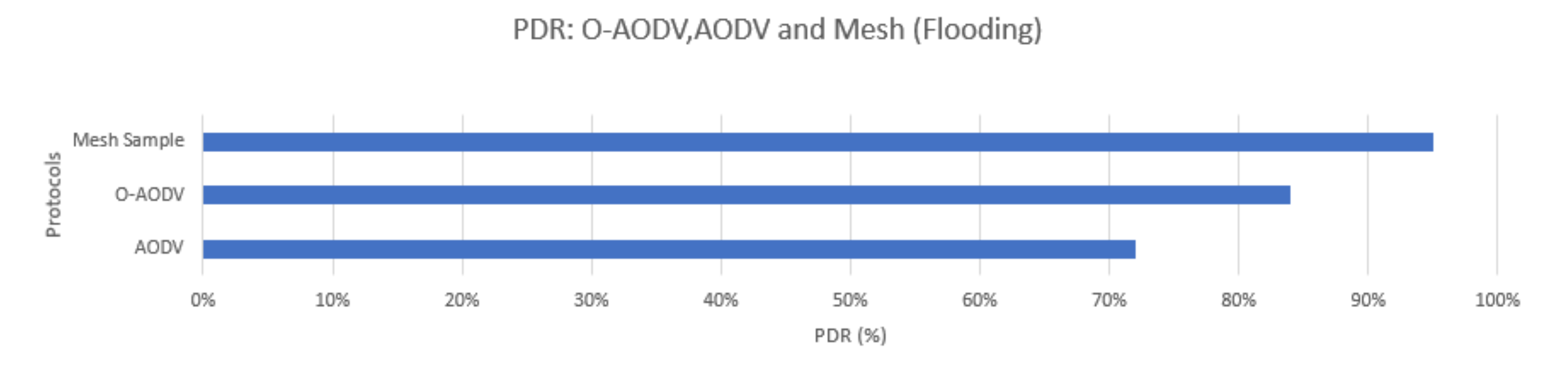


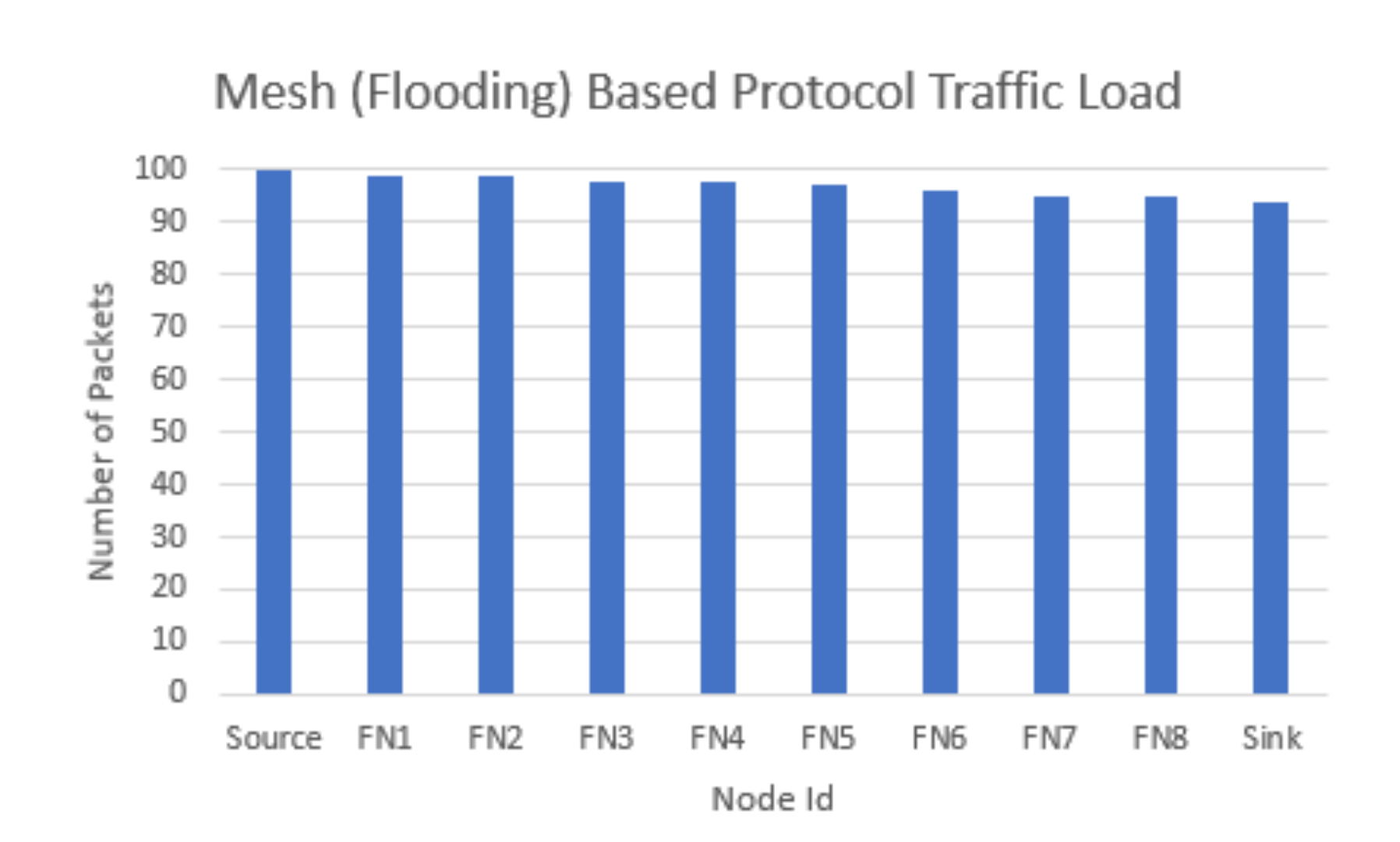
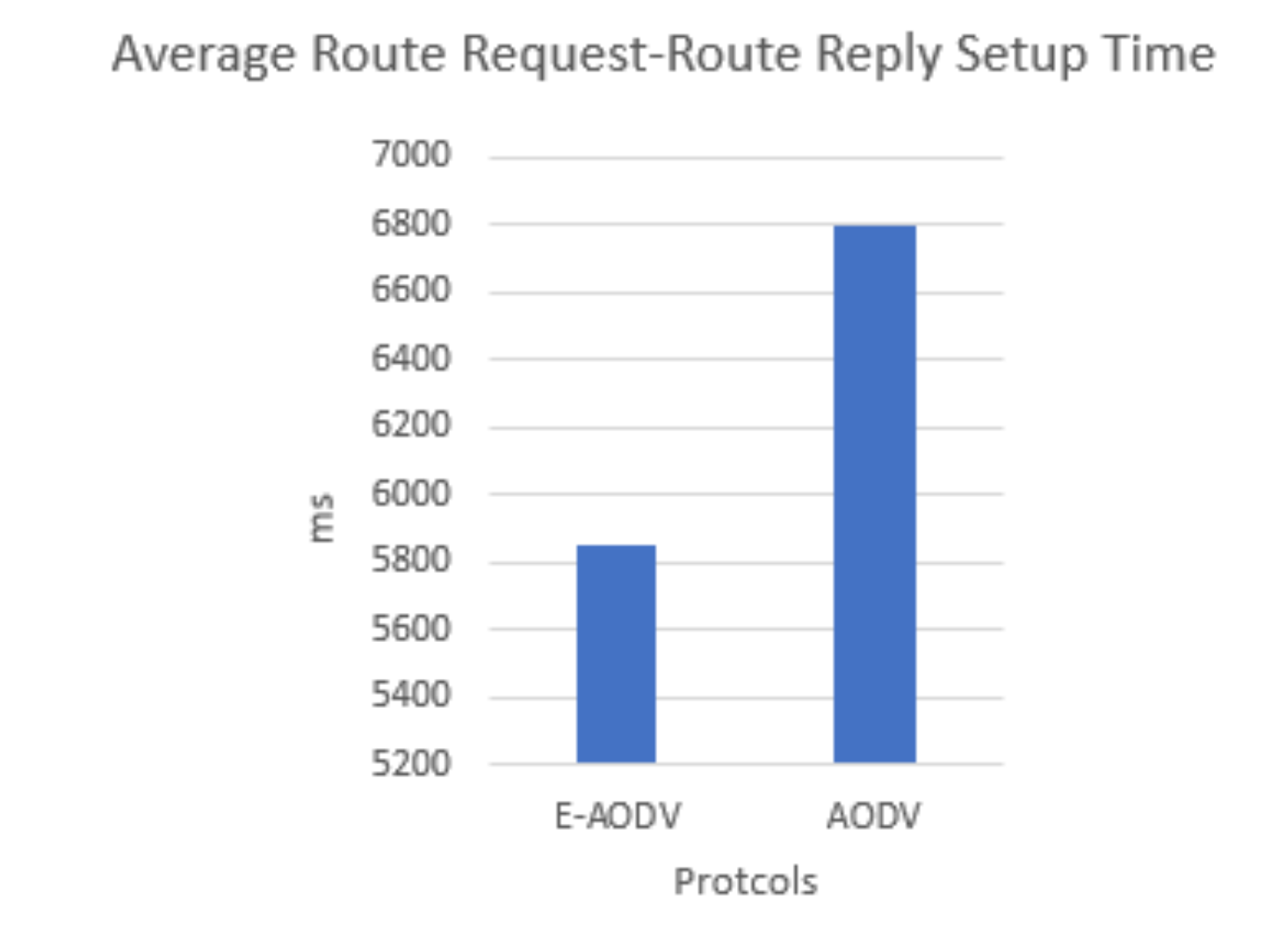



| Ref. | –Protocol | -Connection-Oriented (C) /Routing (R) -Flooding (F)/(R) | Testbed (T)/ Simulation (S) | PDR | End-to-End Delay | Overheads | Power Consumption | Nodes Other Measurements (OM) Throughput |
|---|---|---|---|---|---|---|---|---|
| [9] | –FruityMesh and Trickle | C (FM)/ R-Reactive F-TR | T-nRF52 (BLE 5) -Five Hardkernel Odroid-C2 -Netgear GS108T 8-port switch | -FM: 100%, 90%, 40% with 1, 5, 10 p/s resp -TR: 100%, 80%, 38% with 1, 5, 10 p/s resp | -FM: 0.3, 3.7, 3.9 s with 1, 5, 10 p/s resp -TR: 0.4, 0.3, 0.3 s with 1, 5, 10 p/s | × | FM: 9 mW TR: 28 mW | 37 Nodes |
| [24] | –FruityMesh | C (FruityMesh (FM)) /R-Reactive | T-Nordic Thingy: 52 IOT sensor kit -nRF52DK -nRF6707 | × | × | × | Note: Connection Interval (CI) (7.5–400 ms) (a) 0.65–0.1 mA (Adv Interval 100 ms with CI) (b) 0.6–0.03 mA (Adv Interval 600 ms with CI) (c) Network Life 10–250 d with CI | 1 to 3 Nodes OM with CI from 7.5–400 ms and advertising interval (100 and 600) the current drain is 0–0.65 mA Throughput Approximately from 8–0.5 kB/s for CI 5–400 ms and max 3 packets/interval -with CI > 400 ms is 150 b/s |
| [25] | –D-AOMDV | F | S-MATLAB | Approximately 75–88% with number of nodes 10–40 | × | × | × | 40 Nodes |
| [26] | –MRT-BLE | C (Static Routing Configure Offline to obtain bounded delays) | T-(BLE) X-NUCLEO-IDB05A1 | 1 Hop => 100% 5 Hops => 97% | 1 Hop => 120 ms 5 Hops => 1400 ms | × | × | 8 Nodes |
| [27] | –RT-BLE | C (Static Routing Configure Offline to obtain bounded delays) | T-(BLE) X-NUCLEO-IDB05A1 | × | 20 ms | × | × | 4 Nodes |
| [28] | –CbODRP | C/R-Reactive | S | × | -Route discovery delay 40–100 ms with 50–90 nodes | -Control Packet Overhead 12–88 with Route Discovery interval 1–10 s | Approximately 250–500 mA with 50–90 nodes | 50 to 90 Nodes |
| [30] | –K2 Pruning Greedy Connect and Dominator | F-(Greedy Connect (GC) K2 Pruning (KP) Dominator(D)) | S-MATLAB | -Area (330 × 330 msq) K2: Approximately 80–8% with packets 5–200 p/s GC: 65–8% with packets 5–200 p/s | × | × | × | 1000 Nodes |
| [31] | –BLE-Tree Network | C and R (Reactive) | T Raspberry Pi 3 Model B (BLE 4.1) S | 100% (for 2 p/s) 97.5% (for 5 p/s) 82% (for 10 p/s) | Round-Trip Time: For 1 to 6 Hops = 100 ms to 530 ms | × | × | 40 Nodes |
| [32] | –BLE Mesh | C/R-Reactive | T- nRF52 (BLE 5) | High | Low | × | × | 12 Nodes |
| [33] | –DC-BMN | C | S-MATLAB | × | × | × | × | 100 Nodes OM For N Slot 10 |
| [6] | –AODV Based BLE Mesh Network | R-Reactive | T- nRF52840DK | 69% | 6200 ms | 42% | × | 6 Nodes OM: Average RREQ to RREP Setup Time: 6800 ms Traffic Load: Lower Than Mesh and Higher Than This Paper |
| O-AODV (Ghori, M.R. et al.) | –Optimized AODV Based BLE Mesh Network | R-Reactive | T- nRF52840DK | 82% | 5300 ms | 22% | × | 10 Nodes OM: Average RREQ to RREP Setup Time: 5800 ms Traffic Load: Lower Than Mesh and by [6] |
| Experiment Parameters | Scenario 1 | Scenario 2 | Scenario 3 |
|---|---|---|---|
| No of Experiments | 7 | 7 | 7 |
| Topology | Linear Topology with 10 Nodes | Multipath Topology with 6 Nodes | Multipath Topology with 10 Nodes |
| Link Speed | 2 Mbps | 2 Mbps | 2 Mbps |
| Offered Data Rate | 10 PDUs per Second | 10 PDUs per Second | 10 PDUs per Second |
| Packet Size | 15 Byte | 15 Byte | 15 Byte |
| No. of Packets Transmitted from the Source | 100 | 100 | 100 |
| Number of Sources and Sinks | 9 Sources, 1 Sink | 1 Source, 1 Sink | 1 Source, 1 Sink |
| Transmission Power | −40 dBm | −40 dBm | −40 dBm |
| Transmission Range | Approximately: 2–2.5 m | Approximately: 2–2.5 m | Approximately: 2–2.5 m |
| Relay Configuration | Enabled | Enabled | Enabled |
| Provisioning | Enabled but Given Hardcoded Network, Application, and Device Keys | Enabled but Given Hardcoded Network, Application and Device Keys | Enabled but Given Hardcoded Network, Application, and Device Keys |
| Packet Duplication Factor | 3 Transmissions with a 20 ms interval | 3 Transmissions with a 20 ms interval | 3 Transmissions with a 20 ms interval |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghori, M.R.; Wan, T.-C.; Sodhy, G.C.; Rizwan, A. Optimization of the AODV-Based Packet Forwarding Mechanism for BLE Mesh Networks. Electronics 2021, 10, 2274. https://doi.org/10.3390/electronics10182274
Ghori MR, Wan T-C, Sodhy GC, Rizwan A. Optimization of the AODV-Based Packet Forwarding Mechanism for BLE Mesh Networks. Electronics. 2021; 10(18):2274. https://doi.org/10.3390/electronics10182274
Chicago/Turabian StyleGhori, Muhammad Rizwan, Tat-Chee Wan, Gian Chand Sodhy, and Amna Rizwan. 2021. "Optimization of the AODV-Based Packet Forwarding Mechanism for BLE Mesh Networks" Electronics 10, no. 18: 2274. https://doi.org/10.3390/electronics10182274








