1. Introduction
A networked control system (NCS) is a type of control system in which the control and feedback data packets are exchanged through communication channels between agents and the controller. NCS systems are used to enhance the efficiency and reliability of the control systems [
1,
2,
3,
4]. The simplicity and efficiency of NCSs for constructing networks among multi-agent systems have received significant attention over the past years. Although leveraging communication channels in an NCS can control and supervise the system more efficiently and reliably, NCSs are prone to cyber disruptions—either inherent or intentional ones, such as cyberattacks. The most known cyberattacks are denial of service (DoS), which disables access to the system information or a service [
5], false data injection (FDI), which intentionally manipulates the exchange of data [
6], replay attack, which maliciously repeats valid data transmissions [
7], and a newly found attack, the time-delay switch (TDS) [
3]. The number and intensity of these cyber manipulations have grown in recent years. One of these cyber attacks was the 2015 Ukraine Blackout event, in which about 225,000 customers lost their electricity for several hours. This cyber incident was a successful FDI on an actual power grid [
8]. The 2019 Venezuela blackout resulted from a cyberattack on energy supplies in eighteen states that affected two-thirds of the country [
9,
10]. These cyber disruptions determine the criticality of studying cyber attacks on NCSs, like power grids.
A TDS attack is made by inserting time delays into communication channels of NCSs [
11]. Since NCSs are time-sensitive and require updated measurement signals, a TDS can be highly destructive [
11,
12]. Time delays can occur purposefully or inherently in a wide range of engineering systems [
12,
13,
14]. In general, time delays are common in control systems and can influence the stability of control systems. Even worse delays can occur when an adversary injects random TDS attacks into NCSs, making the systems inefficient or even unstable. This circumstance stems from the fact that the controller needs to receive the measurement values in real time to be able to generate the control signals. NCSs transmit the sensor measurements from agents to a centralized control unit through communication channels, and injecting TDS attacks will result in instability in NCSs. Therefore, it is crucial to design a secure NCS that is robust to both natural delays and TDS attacks [
3,
15].
Even though it has been shown in the literature that TDS attacks can cause instability in NCSs [
11], only a few studies have focused on detecting TDS attacks in real time, and none have investigated the compensation of TDS attacks by designing a secure controller. A neural network (NN) approach was developed in [
16] as a tool for estimating a time delay in industrial communication systems with nonlinear dynamics, but the stability of this controller has not been investigated. Another NN-based approach was introduced in [
17] to estimate the state of the system in real time. The aforementioned proposed algorithms require offline training and cannot detect TDS attacks in real time. Although machine learning techniques have been utilized for cyber attack detection in NCSs [
18], various susceptible and erroneous detection results have been reported in the literature [
19,
20]. These machine learning methods are prone to maliciously altering the training or test data and cause disastrous operation issues and system instability [
20]. A robust controller was introduced in [
21] for systems with nonlinear dynamics. The proposed approach can compensate for the effects of TDS attacks in real time without detecting them. However, the proposed controller can only mitigate small amounts of TDS attacks. The approach proposed in [
22] uses a neural-network-based detection algorithm to detect and estimate the TDS attack in real time. However, the proposed approach can estimate the TDS attacks accurately, but it cannot mitigate the effects of TDS attacks in real time. To mitigate the effect of a TDS attack, Ref. [
12] proposed an adaptive control algorithm that estimates TDS attacks introduced into measurement signals. This work was able to detect and mitigate TDS attacks in real time. However, the stability of the proposed method was not investigated due to the nature of the controller design. Furthermore, the convergence of attack detection and estimation requires further investigation.
Table 1 summarizes the advantages and disadvantages of approaches in the literature.
The contributions of this papers are as follows:
It develops a novel secure control strategy to estimate and compensate TDS attacks in real time for NCSs with linear dynamics to address the current barriers in the detection and compensation of TDS attacks in the literature.
It designs a secure controller that is able to mitigate the effects of TDS attacks using the proposed model-based algorithm.
The controller and estimator in this paper are designed based on the Lyapunov theory to guarantee the stability of an NCS under a TDS attack. The proposed method is compared with an NN-based method [
22] to show the efficacy of the proposed technique in the presence of the TDS attack.
To summarize, the contribution of the paper is its proposal of a novel TDS attack detection technique along with its design of a secure Lyapunov-based controller for NCSs with linear dynamics under TDS attacks. The proposed algorithm is a model-based method that is able to detect and compensate for TDS attacks in real time with low computational complexity compared with learning-based methods.
The rest of the paper is organized as follows.
Section 2 presents a general model for an NCS under a TDS attack. The proposed controller with a Luenberger observer is described in
Section 3.
Section 4 verifies the controller’s stability. The case study is described in
Section 5. Simulations and results are demonstrated in
Section 6, and the conclusion is presented in
Section 7.
2. Networked Control Systems
Despite all of the benefits of NCSs, including that they are fast, reliable, and have remote capability, NCSs are vulnerable to cyber disruptions and threats, since NCSs are highly dependent on information, communication, and cyber interfaces [
1,
2,
3]. NCSs are used in critical infrastructures, and their security is categorized as one of the important concerns in the nation. Therefore, the vulnerability to external interruptions and attacks must be prevented. Since these systems heavily rely on networked communications, this dependency introduces delays, data packet drops, bandwidth allocations, and other cybersecurity issues in the data transfer process [
11,
23,
24].
Specifically, delays can cause catastrophic failures in the systems that are under control. Measured data and control commands must be transferred within a limited period; otherwise, introducing delays to these signals makes the system unable to trace its operating conditions and causes an undesired response [
3,
25].
2.1. Dynamic Model of an NCS
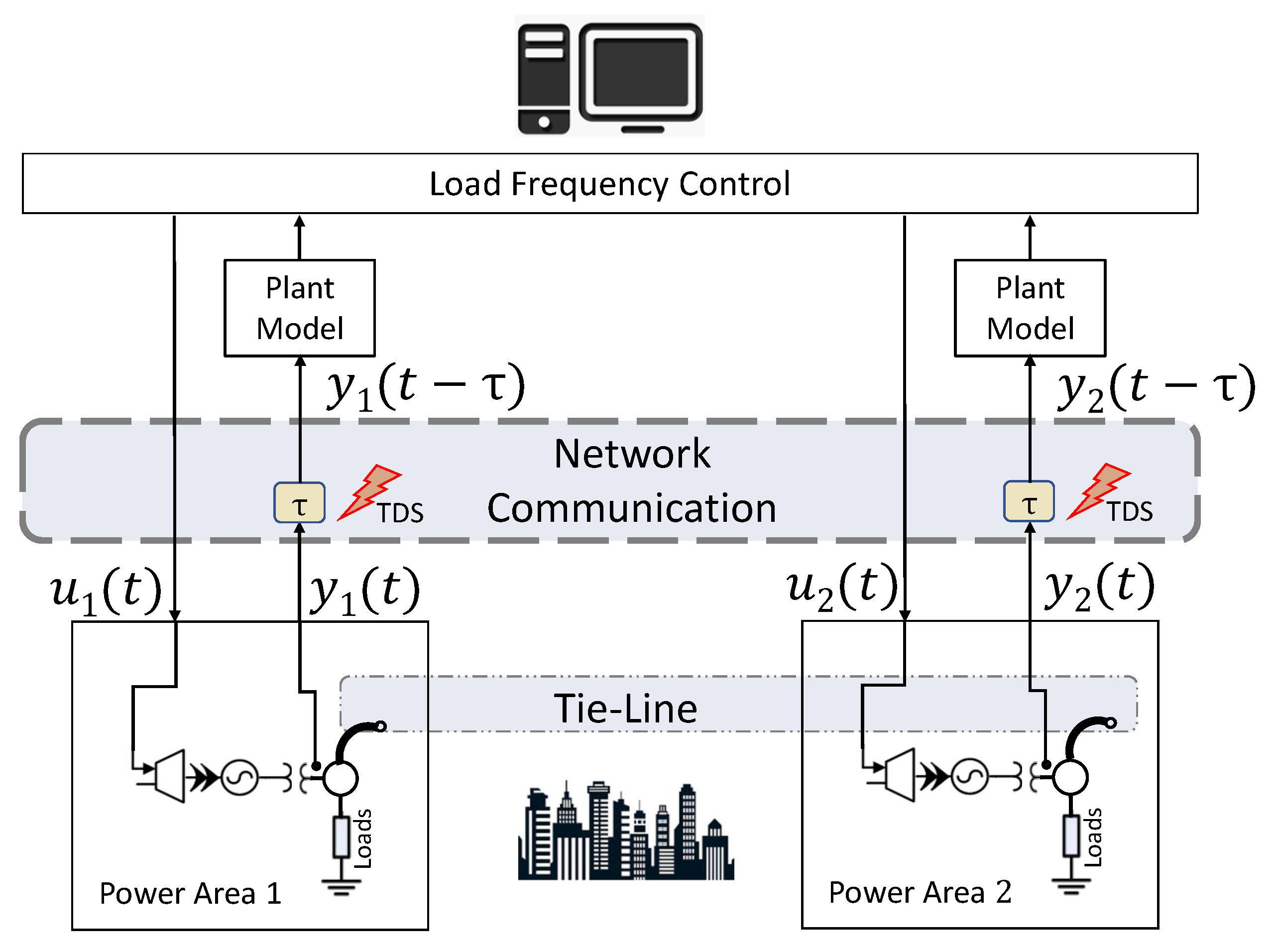
A general diagram of an NCS system is presented in
Figure 1. The communication between the plant and the controller takes place through a networked communication channel. Commands from the controller to the actuators and sensing signals from measurement sensors, which are vulnerable points of NCSs, must flow through the network. The NCS is mathematically represented by the following state-space model, assuming that the NCS has
J agents:
where
indicates the states of NCS and can be described as
and
is the state-space vector of the
agent of the NCS.
In a similar manner,
is the vector of inputs and
is the output, the aggregated state measurements of the system, which are described as
Each agent in the NCS can have a different number of inputs
, outputs
, and states
. This means that each vector in
and
has its own dimension.
where
,
, and
are the dimensions of each vector of the state-space, inputs, and outputs, respectively, for the
agent.
The matrix
A is described as:
Here, each sub-conjunct has the dimension of the agent in the system. represents the mutual dependency between agents.
If all the agents are independent of each other, the matrix changes to the following:
In the same way, the matrix
B is defined as
Therefore, any single has the dimension based on the number of terms in the state vector () and the number of terms in the input vector () of the agent in the NCS.
Matrix
C is composed of
for each agent in the system. The dimension of each
is
. Matrix
C is defined as:
2.2. NCS under a TDS Attack
The controller of an NCS is considered to be an optimal controller, which is described as
where
z is the signal measured by the centralized controller.
Since delays are introduced to the communication channel, the signals received by the controller from each agent in the NCS are not the
originally observed from the system output. This paper assumes that an adversary cannot access control signals and only injects the TDS attacks into the measurement signals. The measured signal under a TDS attack can be described as
where
is the delay of the
element of the NCS.
4. Proposed Delay Detection Method
In this section, and are designed using the Lyapunov approach. Furthermore, this section illustrates how TDS attacks are estimated in real time.
Consider the Lyapunov function described as
where
is a positive gain,
is the state estimation error, and
is the delay estimation error.
In (
21), the derivative of the Lyapunov function is taken to obtain the required parameters and design a controller that is resilient against TDS attacks. It should be noted that time-delay attacks here target the input signals
and
. The output data
y from the plant also have the delay attack shift in this model.
Substituting
and
into (
21), we obtain:
Then,
and
are substituted according to (
1) and (
14), respectively. The equation changes into:
Substituting the signals
u and
from (
18) and (
19), the equation becomes the following:
Considering a constant delay in the channel, even if it happens over short periods of time, the derivative of the delay is going to be null (
). Using a Taylor series, the delayed signal is modeled approximately up to the first derivative term as
.
Assuming that the second and third terms in (
25) can cancel out each other,
can be obtained as follows:
After this, the derivative of the Lyapunov function is simplified as in (
27).
Applying the distributive property, Equation (
27) is extended to (E:dem4):
Simplifying (
27), we obtain the following equations, which will be used to find the estimated delay
:
The element is a parameter for characterizing the system to make it possible to run the computation of the estimated delay value. Unfortunately, there is not a previous relation between the physical parameters of the system and the value of . The moment when the attack is deployed and the amount of delay injected have different effects on the system. The method used to get is based on the peak value observed when tracking the error signal—the difference between the plant response and the observer response—and defining the value. Then, some series of tests must be performed under known TDS attack conditions to validate the definition of . An offset may be applied according to the essay results to guarantee more precise estimates.
The Lyapunov theory is applied to guarantee that the system remains stable at different operating points. The Luenberger gain
L must satisfy the following equation:
The derivative can be taken from the observer. However, the error signal and its derivative must be deduced—because it is not possible to measure data at the plant output before the delayed channel—by checking the error .
The Taylor series approximation must be considered; neglecting the higher-order terms, the delayed signal is represented by the following:
Similarly, the estimated states are obtained below:
Subtracting Equations (
33) from (
34) will result in (
36):
The term
can be neglected because it is expected to go to zero due to the proper function of the proposed estimator. In this case, the Equation (
36) becomes:
Considering that the system must be stable because the chosen value of
L must guarantee the Lyapunov stability criteria, the Luenberger observer must bring estimation error signals in the form of
. Then,
. Taking
(the effects of this
k can be absorbed by
) to simplify the calculations, Equation (
37) becomes
This way, it is possible to deduce
and its derivative
used in Equations (
30) and (
31). They are obtained with the difference between consecutive samples in the digital readings.
5. NCS Case Study: Load Frequency Control Design for Power Grids
Load variation may create frequency oscillations and ultimately cause power grid instability. When the the grid load increases, the frequency decreases, and vice versa. Once a rapid load change is sensed, the electrical torque output is changed, which leads to a mismatch between the electrical and mechanical torques. This torque mismatch results in turbine speed changes that, in turn, cause frequency oscillations in the grid [
27].
The load frequency control (LFC) of power systems is crucial in sustaining the grid frequency within a predefined range. LFC guarantees that the grid generators can properly maintain a balance between load and energy supply using the regulation of generators’ set-points [
27].
The mathematical model for an NCS applied to the power grid with several agents was developed in [
12]. The mathematical model presented in Equation (
1) with the
vector is defined as the following:
where
is the frequency deviation,
is the generated power deviation,
is the turbine position,
is the tie-line power flow, and
is the control error given by
.
Therefore, the equations are going to have , , and , where is the control input vector, is the state vector, and is the output of the agent in the system.
In this study, multiple grids are connected to the same tie-line within the same NCS. This means that agents can communicate with each other and exchange power among themselves through the grid. The matrix
A will be similar to that presented in (
8) with the following elements: Each
will be
and
will be
The parameters presented in (
41) and (
42) are described as follows:
Similarly to (
10), the matrix
B is defined below:
Since vectors
and
are the same as those shown in Equation (
1), the matrix
C presented in Equation (
1) is an identity matrix, and finally, the matrix
D is considered null in this study.
6. Simulation Results
This section illustrates the performance of the proposed secure control design along with the TDS attack detection technique through the case study that was introduced in
Section 5. On top of the simulation, the method was implemented in a hardware-in-the-loop (HIL) environment to show that the proposed method is practical. For the HIL testing, we used a DS1104 Controller Board in connection with the MATLAB Simulink software. The LFC model was implemented via MATLAB Simulink 2019a, and it was converted into a C program to be loaded into the Dspace board. The results were observed using the Dspace console in real time. To show that the proposed method can perform well under measurement noise, we added zero-mean Gaussian noise during the HIL performance testing. As shown in
Figure 3, the NCS, including two agents, was subjected to TDS attacks.
Table 2 illustrates the parameter values that were used in the simulation.
The delay attacks were simulated based on the following assumptions:
Assumption 1.1. The TDS attack takes place at a certain moment and remains constant.
Assumption 1.2. The TDS attack affects all the states. The starting moment and the delay period are the same for all the states.
Assumption 1.3. From the moment the attack is launched, it persists until the end of the simulation.
6.1. Vulnerability Analysis
When running the NCS in an optimal control situation, with no compensation algorithm to correct the delays, it can be observed that the system becomes unstable for attacks of
ms or higher.
Figure 4 and
Figure 5 show the response of the system under a TDS attack. Both attacks were started at
s, but the intensity of the attack is different. In the first case,
s, and in the other one,
s. It can be observed that the delay of
s had an aggressive effect on the system, leading the response to a divergent behavior with a highly increasing rate.
Figure 4 represents a threshold condition, where the system started facing unstable responses due to the delay. It is possible to observe that the instability started around the instant at 30 s and the oscillations grew at a low rate. However, it was an unstable condition, and the system could not work under this attack. To detect and mitigate the effects of an attack, a resilient controller must be applied.
6.2. TDS Attack Detection and State Estimation
The observer compensation technique discussed in
Section 4 made the system operate correctly, even with TDS attacks of around
ms. The same TDS attack as that shown in
Figure 5 was simulated, but the system was equipped with the proposed secure controller. As
Figure 6 shows, the adverse effect of the TDS attack was improved by the proposed state estimation mechanism.
The simulation was repeated with different time delays inserted by the TDS attack into the NCS at different starting instants (
seconds).
Table 3 shows the results for three different time delays
. The results show an Mean Square Error (MSE) around 5%.
The estimation of the delay depends on the parameter
mentioned in (
30). The definition of
is a result of a complex set of essays running under known conditions to evaluate how the system responds to an injected delay depending on the amount of delay and the time instant at which was deployed. When an attack takes place, the error between the actual and the estimated states from the observer increases, and this is also reflected in the variations in
. Using the second derivative of
, the time instant of the TDS attack is detected (as shown in
Figure 7). Thus, it is deployed, and the error is used to define the value to be chosen for
. The solution for computing
was created by using a constant value for alpha and then comparing the results with the offset that should be needed to get the correct values of
. A polynomial approximation was created by taking the instant values of
; then, it was incorporated in the
computation.
6.3. Performance Evaluation
The performance of the method proposed in this paper is compared with the performance of the control method presented in [
22], which works based on an adaptive NN technique to estimate the time delay to which the NCS is exposed. The simulations were performed based on the following assumptions:
Assumption 2.1. The delay attack takes place in a certain moment and remains constant.
Assumption 2.2. The delay attack targets only the state of .
Assumption 2.3. The attack persists from the moment it is launched until the end of the simulation.
A delay
s was inserted from
s. The state estimation errors are shown in
Figure 8. The results show that the observer was able to accurately estimate measurement signals, even when the NCS was under TDS attacks. The results associated with the proposed method are presented in
Figure 9. As shown in the figure, it is clear that the proposed TDS attack detection technique is more accurate than the NN-based (traditional) detection technique.
The NN approach allows consecutive computations in order to correct the estimation error and compensate frequency discrepancies in the LFC. The proposed method based on the Lyapunov theory presented in (
20) depends on the parameter
, which is a characteristic quantity of the system, but it also depends on the instant the attack takes place. A study using the values of
,
, and
was used to calculate this parameter. So, the final value of
was reached more quickly, but a steady-state error can happen. The better the adjustment of the
parameter, the lower the steady-state error.
Another experiment to validate the Lyapunov method for avoiding TDS attack effects was made in a hardware-in-the-loop environment using external hardware equipment, the dSPACE CP1104 platform. A feedback loop was made for the
state through the connection on the board. A time delay of
s affected the LFC, and the resilient performance of the proposed controller was seen in the results. The signal response on
is shown in
Figure 10. This test is important because it shows the effectiveness of the solution in a real-life system, demonstrating how the correction takes place to keep the system working properly, even when it is subjected to a TDS attack.
7. Conclusions
This paper presented an approach to providing adjustments to the input signal in an NCS structure in order to keep a plant working properly, even under a TDS attack. The compensation signal is defined based on the Lyapunov theory and a Luenberger observer. The proposed approach was evaluated through a case study in which a two-agent LFC system was monitored and controlled. The performance of the controller was validated in a hardware-in-the-loop simulation using the dSPACE platform to emulate the feedback loop of the NCS under TDS attacks. It should be noted that the proposed method can be applied to any NCSs, such as cooperative driving systems.
During the transient response of the system, the proposed delay estimation is more precise compared with other techniques in the literature. Furthermore, the controller and estimator were designed based on Lyapunov stability analysis, unlike other traditional techniques. When the most significant variations take place, it is possible to detect the peaks caused by the attack. The final portion of the transient response already has lower variation, and it brings uncertainties to the estimation of . If the attack is deployed at an instant close to the starting point, the estimation is also affected because the observer will get the actual values from the plant. The variation in a delay over time is also a strong challenge for estimations, but this paper considered only constant delay attacks. Future work will enhance the proposed method to investigate time-variable TDS attacks. Although this paper focused on an NCS with dependent agents, the proposed method is general and can be used for a multi-agent system with independent dynamics.