Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case
Abstract
:1. Introduction
- Enhance Mobile Broadband (eMBB).
- Massive Machine-Type Communications (mMTC).
- Ultra-Reliable Low-Latency Communications (URLLC).
- Service layer.
- Infrastructure layer.
- Business function layer.
- Orchestration layer.
- Network function layer.
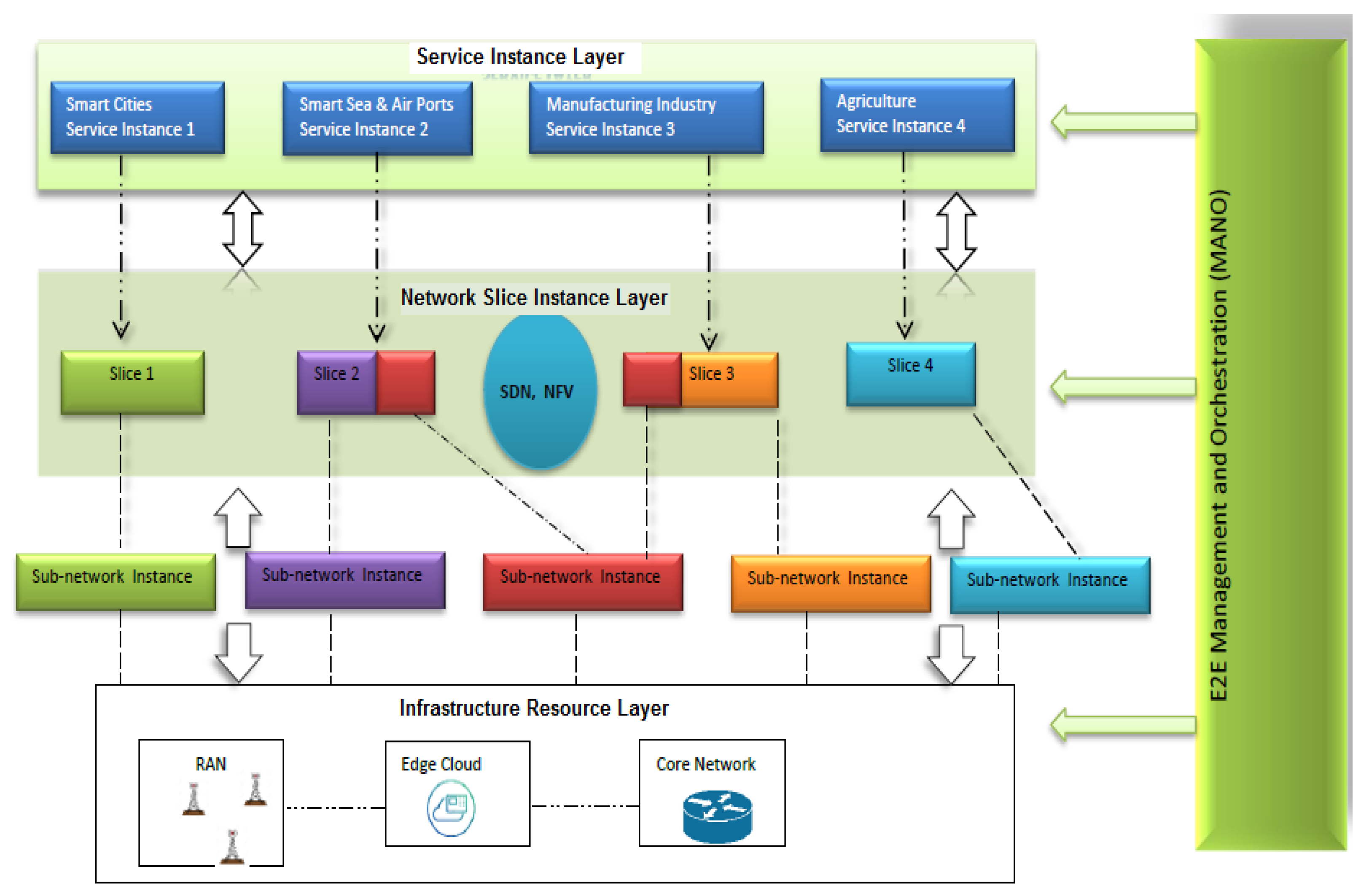
2. Network Slicing in 5G
- Service instance layer.
- Network slice instance layer.
- Resource layer.
2.1. Service Layer
2.2. Network Instance Layer
2.3. Resource or Infrastructure Layer
3. Enabling Technologies
3.1. Software Defined Networking (SDN)
3.2. ONF SDN Architecture
3.3. Network Function Virtualization (NFV)
3.4. Management and Orchestration
- Management and Orchestration (MANO): Manages and coordinates the virtualization in the architecture. It consists of the following three entities:
- (1).
- Virtualized infrastructure manager (VIM): Helps to manage the network functions virtualization infrastructure (NFVI) resources.
- (2).
- VNF manager (VNFM): Helps to provide connectivity and to configure the VNFs.
- (3).
- Orchestrator: Helps to manage the life cycle of network infrastructure resources and ensures the integrity of process-to-process service.
- Network Functions Virtualization Infrastructure (NFVI): It is connected to the VNFs.
- Network Management System (NMS): It consists of element management (EM) and operation/business support system (OSS/ BSS). Collectively, it helps to provide general management by communicating with MANO functions.
- Infrastructure SDN Controller (ISDNC): Dynamically manages the infrastructure resources, which enables them to communicate with the VNFs [22].
- Tenant SDN Controller (TSDNC): Operate and dynamically manages the underlying data plane resources via interface.
4. Machine Learning and AI for Network Slicing Beyond 5G Systems
4.1. Supervised Learning for Network Slicing
4.1.1. Support Vector Machine (SVM)
4.1.2. k-Nearest Neighbor (KNN)
4.1.3. Deep Learning
4.2. Unsupervised Learning for Network Slicing
K-means Clustering
4.3. Reinforcement Learning
5. ML for Mobility Prediction
6. ML for Resource Management
7. RAN Slicing in 5G
8. Performance Evaluation of Network Slicing
9. Smart Port Use Case
- Intelligent automation (IA).
- Virtual reality (VR).
- Smart guided vehicle (SGV).
9.1. Intelligent Automation (IA) (mMTC)
9.2. Virtual Reality (VR) (eMBB)
9.3. Smart Guided Vehicles (SGV) (URLLC)
9.4. Design Overview
9.5. Methodology
9.5.1. Data Processing
9.5.2. Feature Extraction
9.5.3. Clustering
9.5.4. Core Network
10. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Tomtsis, D.; Kokkonis, G.; Kontogiannis, S. Evaluating existing wireless technologies for IoT data transferring. In Proceedings of the 2017 South Eastern European Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM), Kastoria, Greece, 23–25 September 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Alreshidi, A.; Ahmad, A. Architecting. Software for the Internet of Thing Based Systems. Future Internet 2019, 10, 153. [Google Scholar] [CrossRef] [Green Version]
- Network Slicing Use Case Requirements. Available online: https://www.gsma.com/futurenetworks/wp-content/uploads/2018/07/Network-Slicing-Use-Case-Requirements-fixed.pdf (accessed on 12 December 2020).
- 3GPP, TR 23.711. Enhancements of Dedicated Core Networks Selection Mechanism (Release 14). 2016. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=2962 (accessed on 26 September 2016).
- Kaloxylos, A. A survey and an analysis of network slicing in 5G networks. IEEE Commun. Stand. Mag. 2018, 2, 60–65. [Google Scholar] [CrossRef]
- View on 5G Architecture—5G PPP Architecture Working Group. Available online: https://www.trust-itservices.com/sites/default/files/View%20on%205G%20Architecture%20-%205G%20PPP%20Architecture%20Working%20Group.pdf (accessed on 19 June 2019).
- Rost, P.; Breitbach, M.; Roreger, H.; Erman, B.; Mannweiler, C.; Miller, R.; Viering, I. Customized Industrial Networks: Network Slicing Trial at Hamburg Seaport. IEEE Wirel. Commun. 2018, 25, 48–55. [Google Scholar] [CrossRef]
- Sgambelluri, A.; Tusa, F.; Gharbaoui, M.; Maini, E.; Toka, L.; Perez, J.M.; Paolucci, F.; Martini, B.; Poe, W.Y.; Hernandes, J.M.; et al. Orchestration of network services across multiple operators: The 5G exchange prototype. In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Finland, 12–15 June 2017; pp. 1–5. [Google Scholar]
- Gramaglia, M.; Digon, I.; Friderikos, V.; von Hugo, D.; Mannweiler, C.; Puente, M.A.; Samdanis, K.; Sayadi, B. Flexible connectivity and QoE/QoS management for 5G Networks: The 5G NORMA view. In Proceedings of the 2016 IEEE International Conference on Communications Workshops (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 373–379. [Google Scholar]
- Rizou, S.; Athanasoulis, P.; Andriani, P.; Iadanza, F.; Carrozzo, G.; Breitgand, D.; Weit, A.; Griffin, D.; Jimenez, D.; Acar, U.; et al. A service platform architecture enabling programmable edge-to-cloud virtualization for the 5G Media industry. In Proceedings of the 2018 IEEE International Symposium on Broadband Multimedia Systems and Broadcasting (BMSB), Valencia, Spain, 6–8 June 2018; pp. 1–6. [Google Scholar]
- Tzanakaki, A.; Anastasopoulos, M.; Simeonidou, D.; Berberana, I.; Syrivelis, D.; Korakis, T.; Flegkas, P.; Mur, D.C.; Demirkol, I.; Gutiérrez, J.; et al. 5G infrastructures supporting end-user and operational services: The 5G-XHaul architectural perspective. In Proceedings of the 2016 IEEE International Conference on Communications Workshops (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 57–62. [Google Scholar]
- NGMN Alliance. Description of Network Slicing Concept. White Paper. 2016. Available online: https://www.ngmn.org/publications/description-of-network-slicing-concept.html (accessed on 2 January 2021).
- NGMN 5G Project Requirements and Architecture–Work Stream E2E Architecture (Version 1.0). Available online: https://www.ngmn.org/wp-content/uploads/160113_NGMN_Network_Slicing_v1_0.pdf (accessed on 13 January 2016).
- McKeown, N.; Balakrishnan, H.; Peterson, L.L.; Shenker, S.; Turner, J.S.; Anderson, T.; Parulkar, G.; Rexford, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- ONF TR-526, Applying SDN Architecture to 5G Slicing. April 2016. Available online: https://opennetworking.org/wp-content/uploads/2014/10/Applying_SDN_Architecture_to_5G_Slicing_TR-526.pdf (accessed on 2 January 2021).
- ONF TR-521, SDN Architecture. February 2016. Available online: https://opennetworking.org/wp-content/uploads/2014/10/TR-521_SDN_Architecture_issue_1.1.pdf (accessed on 2 January 2021).
- Zhu, S.; Bi, J.; Sun, C.; Wu, C.; Hu, H. Sdpa: Enhancing stateful forwarding for software-defined networking. In Proceedings of the 2015 IEEE 23rd International Conference on Network Protocols (ICNP), San Francisco, CA, USA, 10–13 November 2015; 2015; pp. 323–333. [Google Scholar]
- Ordonez-Lucena, J.; Ameigeiras, P.; Lopez, D.; Ramos-Munoz, J.; Lorca, J.; Folgueira, J. Network slicing for 5G with SDN/NFV: Concepts, architectures, and challenges. IEEE Commun. Mag. 2017, 55, 80–87. [Google Scholar] [CrossRef] [Green Version]
- ETSI, Network Functions Virtualisation (NFV); Management and Orchestration 1 (2014): V1. Available online: https://www.etsi.org/deliver/etsi_gs/nfv-man/001_099/001/01.01.01_60/gs_nfv-man001v010101p.pdf (accessed on 5 January 2021).
- Taylor, M. The Myth of the Carrier-Grade Cloud. 2015. Available online: http://www.metaswitch.com/the-switch/the-myth-of-thecarrier-grade-cloud (accessed on 5 January 2021).
- ETSI GS NFV-EVE 005. Network Functions Virtualisation (NFV); Ecosystem; Report on SDN Usage in NFV Architectural Framework, v. 1.1.1, December 2015. Available online: https://www.etsi.org/deliver/etsi_gs/NFV-EVE/001_099/005/01.01.01_60/gs_nfv-eve005v010101p.pdf (accessed on 7 January 2021).
- ETSI GS NFV-INF 001. Network Functions Virtualisation (NFV); Infrastructure Overview, v. 1.1.1, January 2015. Available online: https://www.etsi.org/deliver/etsi_gs/NFV-INF/001_099/001/01.01.01_60/gs_NFV-INF001v010101p.pdf (accessed on 7 January 2021).
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.J.A. The roadmap to 6G: AI empowered wireless networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef] [Green Version]
- Janakiram, D.; Reddy, V.; Kumar, P.A. Outlier detection in wireless sensor networks using Bayesian belief networks. In Proceedings of the International Conference on Communication System Software and Middleware, New Delhi, India, 8–12 January 2006; pp. 1–6. [Google Scholar]
- Moustapha, A.; Selmic, R. Wireless sensor network modeling using modified recurrent neural networks: Application to fault detection. IEEE Trans. Instrum. Meas. 2008, 57, 981–988. [Google Scholar] [CrossRef]
- Morelande, M.; Moran, B.; Brazil, M. Bayesian node localisation in wireless sensor networks. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, Las Vegas, NV, USA, 31 March–4 April 2008; pp. 2545–2548. [Google Scholar]
- Azmat, F.; Chen, Y.; Stocks, N. Analysis of Spectrum Occupancy Using Machine Learning Algorithms. IEEE Trans. Veh. Technol. 2016, 65, 6853–6860. [Google Scholar] [CrossRef]
- Singh, S.K.; Salim, M.M.; Cha, J.; Pan, Y.; Park, J.H. Machine Learning-Based Network Sub-Slicing Framework in a Sustainable 5G Environment. Sustainability 2020, 12, 6250. [Google Scholar] [CrossRef]
- Rezwan, S.; Choi, W. Priority-Based Joint Resource Allocation With Deep Q-Learning for Heterogeneous NOMA Systems. IEEE Access 2021, 9, 41468–41481. [Google Scholar] [CrossRef]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H. Machine Learning in Wireless Sensor Networks: Algorithms, Strategies, and Applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef] [Green Version]
- Kalyoncu, F.; Zeydan, E.; Yigit, I.O. A data analysis methodology for obtaining network slices towards 5g cellular networks. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018; pp. 1–5. [Google Scholar]
- Yajnanarayana, V.; Rydén, H.; Hévizi, L. 5G handover using reinforcement learning. In Proceedings of the 2020 IEEE 3rd 5G World Forum (5GWF), Bangalore, India, 10–12 September 2020. [Google Scholar]
- Ali, Z.; Baldo, N.; Mangues-Bafalluy, J.; Giupponi, L. Machine learning based handover management for improved QoE in LTE. In Proceedings of the NOMS 2016–2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 794–798. [Google Scholar]
- Ulvan, A.; Bestak, R.; Ulvan, M. Handover procedure and decision strategy in LTE-based femtocell network. Telecommun. Syst. 2013, 52, 2733–2748. [Google Scholar] [CrossRef]
- Mohamed, A.; Onireti, O.; Imran, M.A.; Imran, A.; Tafazolli, R. Predictive and Core-Network Efficient RRC Signalling for Active State Handover in RANs With Control/Data Separation. IEEE Trans. Wirel. Commun. 2017, 16, 1423–1436. [Google Scholar] [CrossRef] [Green Version]
- Capone, A.; Dos Santos, A.F.; Filippini, I.; Gloss, B. Looking beyond green cellular networks. In Proceedings of the 2012 9th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Courmayeur, Italy, 9–11 January 2012; pp. 127–130. [Google Scholar]
- Akoush, S.; Sameh, A. Mobile user movement prediction using bayesian learning for neural networks. In Proceedings of the 2007 International Conference on Wireless Communications and Mobile Computing, Honolulu, HI, USA, 12–16 August 2007; pp. 191–196. [Google Scholar]
- Thainesh, J.S.; Wang, N.; Tafazolli, R. Reduction of core network signalling overhead in cluster based LTE small cell networks. In Proceedings of the 2015 IEEE 20th International Workshop on Computer Aided Modelling and Design of Communication Links and Networks (CAMAD), Guildford, UK, 7–9 September 2015; pp. 226–230. [Google Scholar] [CrossRef]
- Mohamed, A.; Onireti, O.; Hoseinitabatabaei, S.A.; Imran, M.; Imran, A.; Tafazolli, R. Mobility prediction for handover management in cellular networks with control/data separation. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 3939–3944. [Google Scholar] [CrossRef] [Green Version]
- Sciancalepore, V.; Cirillo, F.; Xavier, C.P. Slice as a service (SlaaS) optimal IoT slice resources orchestration. In Proceedings of the GLOBECOM 2017–2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Bega, D.; Gramaglia, M.; Banchs, A.; Sciancalepore, V.; Samdanis, K.; Costa-Perez, X. Optimising 5G infrastructure markets: The business of network slicing. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Bega, D.; Gramaglia, M.; Fiore, M.; Banchs, A.; Costa-Perez, X. DeepCog: Cognitive network management in sliced 5G networks with deep learning. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 280–288. [Google Scholar]
- Yan, M.; Feng, G.; Zhou, J.; Sun, Y.; Liang, Y.C. Intelligent resource scheduling for 5G radio access network slicing. IEEE Trans. Veh. Technol. 2019, 68, 7691–7703. [Google Scholar] [CrossRef]
- Sallent, O.; Perez-Romero, J.; Ferrus, R.; Agusti, R. On radio access network slicing from a radio resource management perspective. IEEE Wirel. Commun. 2017, 24, 166–174. [Google Scholar] [CrossRef]
- Marsch, P.; Da Silva, I.; Bulakci, O.; Tesanovic, M.; El Ayoubi, S.E.; Rosowski, T.; Kaloxylos, A.; Boldi, M. 5G radio access network architecture: Design guidelines and key considerations. IEEE Commun. Mag. 2016, 54, 24–32. [Google Scholar] [CrossRef]
- Elayoubi, S.E.; Jemaa, S.B.; Altman, Z.; Galindo-Serrano, A. 5G RAN slicing for verticals: Enablers and challenges. IEEE Commun. Mag. 2019, 57, 28–34. [Google Scholar] [CrossRef] [Green Version]
- Lin, Y.B.; Tseng, C.C.; Wang, M.H. Effects of Transport Network Slicing on 5G Applications. Future Internet 2021, 13, 69. [Google Scholar] [CrossRef]
- Yang, J.; Feng, L.; Jin, T.; Liang, H.; Xu, F.; Tian, L. Enabling Sector Scheduling for 5G-CPE Dense Networks. Secur. Commun. Netw. 2020, 2020, 6684681. [Google Scholar] [CrossRef]
- Azhar, M.; Ke, S.; Shaheen, K.; Mi, X. Data mining techniques for wireless sensor networks: A survey. Int. J. Distrib. Sens. Netw. 2013, 9, 1–24. [Google Scholar]







| SDN Controllers | Throughput (millions/sec) | Latency s | Architecture |
|---|---|---|---|
| Floodlight | 0.2 | 25 | Centralized |
| Onix | 2.2 | 15 | Centralized |
| ONOS | 1.2 | 50 | Distributed |
| OpenDaylight (ODL) | 0.1 | 10 | Centralized |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sohaib, R.M.; Onireti, O.; Sambo, Y.; Imran, M.A. Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case. Electronics 2021, 10, 1090. https://doi.org/10.3390/electronics10091090
Sohaib RM, Onireti O, Sambo Y, Imran MA. Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case. Electronics. 2021; 10(9):1090. https://doi.org/10.3390/electronics10091090
Chicago/Turabian StyleSohaib, Rana Muhammad, Oluwakayode Onireti, Yusuf Sambo, and Muhammad Ali Imran. 2021. "Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case" Electronics 10, no. 9: 1090. https://doi.org/10.3390/electronics10091090
APA StyleSohaib, R. M., Onireti, O., Sambo, Y., & Imran, M. A. (2021). Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case. Electronics, 10(9), 1090. https://doi.org/10.3390/electronics10091090







