Abstract
Succinct Non-interactive Arguments of Knowledge (SNARks) are receiving a lot of attention as a core privacy-enhancing technology for blockchain applications. Polynomial commitment schemes are important building blocks for the construction of SNARks. Polynomial commitment schemes enable the prover to commit to a secret polynomial of the prover and convince the verifier that the evaluation of the committed polynomial is correct at a public point later. Bünz et al. recently presented a novel polynomial commitment scheme with no trusted setup in Eurocrypt’20. To provide a transparent setup, their scheme is built over an ideal class group of imaginary quadratic fields (or briefly, class group). However, cryptographic assumptions on a class group are relatively new and have, thus far, not been well-analyzed. In this paper, we study an approach to transpose Bünz et al.’s techniques in the discrete log setting because the discrete log setting brings a significant improvement in efficiency and security compared to class groups. We show that the transposition to the discrete log setting can be obtained by employing a proof system for the equality of discrete logarithms over multiple bases. Theoretical analysis shows that the transposition preserves security requirements for a polynomial commitment scheme.
1. Introduction
Zero-Knowledge Succinct Non-interactive Arguments of Knowledge (zk-SNARKs) are non-interactive proof systems between the prover and the verifier. They provide a way for the prover to convince the verifier that the statement claimed by the prover is true without disclosing any other information except the validity of the statement while maintaining a short proof size and an efficient verification by the verifier. Since their adoption to cryptocurrency systems, such as Zcash [] and Ethereum [], zk-SNARKs are regarded as an essential technique for solving data privacy issues in blockchain-based applications. There have been numerous SNARK proposals in the literature. Some constructions present very efficient proof systems with the help of a trusted setup [,,]. Because the transparent property is desirable for applications, such as cryptocurrency, recent constructions [,,] have focused on a proof system with a transparent setting, i.e., they have no trusted setup.
The construction of SNARKs with no trusted setup heavily relies on a transparent and efficient polynomial commitment scheme. At a high level, transparent zk-SNARKs can be constructed using the framework from polynomial interactive oracle proofs (IOP) [,] as follows: (1) The prover expresses the required computation for proving a statement as a set of low-degree polynomials over a finite field , which is a representation of its witness. (2) The prover sends commitments to low degree polynomials to the verifier, and the verifier then checks the proof by querying evaluations of polynomials for points chosen uniformly at random from , where we crucially require a polynomial commitment scheme. (3) Finally, one can obtain the non-interactive version of the previous proof systems by applying the Fiat–Shamir heuristic [].
In this paper, we focus on polynomial commitment schemes. Let be the prover’s secret polynomial over a field with the degree at most d, i.e., . In polynomial commitment schemes, the prover sends the commitment to f to the verifier. Later, upon input of a public point , the prover convinces the verifier that the committed polynomial f holds with a proof. We call a polynomial commitment scheme transparent if it requires no trusted setup to generate public parameters for the scheme. Since the first construction was developed by Kate et al. [], a variety of polynomial commitment schemes have been proposed in the literature.
For polynomial commitment schemes, the main factors of efficiency consist of the computation complexities of the prover (prover complexity) and verifier (verifier complexity), and the communication complexity between them. Usually, constructions with a trusted setup provide higher efficiency than those with a transparent setting. Recently, Bünz et al. [] proposed an efficient polynomial commitment scheme with a transparent setting. Asymptotically, it achieves a logarithmic verifier complexity and proof size for evaluation (communication complexity). In brief, it improves efficiency by applying an evaluation protocol in a recursive manner. It reduces the degree of a polynomial f by half at each iteration; hence, iterations overall. Transparency in the scheme relies on the use of a group of unknown order whose concrete candidate is an ideal class group of imaginary quadratic fields.
The security of a group of unknown order stems from the infeasibility of computing the order of the group. Previous cryptographic constructions over a class group considered concrete group parameters, such as a 1665-bit negative fundamental discriminant for 128-bit security [,], which was used in Bünz et al.’s scheme []. However, recent works report that the above parameters for class groups provide less security than expected. Notably, Dobson and Galbraith estimate that class groups with a 1665-bit discriminant only offer 55-bit security []. They, therefore, claim that orders of a random class group should be at least for a 128-bit security level. Those parameters correspond to approximately a 6656-bit discriminant. This leads to a decreased efficiency for the cryptographic primitives based on class groups.
In this paper, we put forward a study to overcome the efficiency degradation of Bünz et al.’s construction caused by the use of class groups. To do this, we focus on transposing their techniques in the discrete log setting, preserving a no-trust setup. This approach brings about two advantages. First, the (elliptic curve) discrete log problem is one of the standard cryptographic assumptions as opposed to the order assumption of class groups. To date, its security has been well-understood. Second, the group operation in the discrete log setting (e.g., elliptic curve groups) is much more efficient than that in the class groups, which significantly reduces the actual computation cost for both the prover and the verifier. In addition, a group element in the discrete log setting is shorter than that in class groups. This advantage cuts the cost of bandwidth spent by the prover and the verifier when applying the evaluation protocol of a polynomial commitment scheme.
Our approach is built on an information-theoretic abstraction given in [] to construct a polynomial commitment scheme. The abstraction requires two properties, a linear homomorphism and a monomial homomorphism, which the underlying commitment scheme should provide. These two properties enable the verifier to apply the computations among polynomials over their committed forms, such as a linear combination (a linear homomorphism) and a degree-shift operation (a monomial homomorphism) of polynomials. The two properties are necessary for an evaluation protocol using a recursive call, which is critical in achieving a logarithmic verifier and communication complexities. To realize these properties in a discrete log setting, we utilize a polynomial encoding method devised by Bootle et al. []. This method uses a variant of the Pedersen commitment scheme [], which naturally provides a linear homomorphism. Unfortunately, however, the Pedersen commitment scheme is not a monomial homomorphism, which is easily obtained in a class group-based scheme []. Thus, we focus our attention on the study of a discrete log-based proof system to prove that a monomial homomorphism is verifiably computed in the discrete log setting. The contribution of this work is as follows.
- We clarify a proof system that proves the correct computation of a monomorphism in the discrete log setting. Specifically, we show it suffices to have a proof system to check the equality of a discrete logarithm over multiple bases, say . Given two subsets and of a group , allows the prover to convince the verifier that and have equal exponents, i.e., for , without disclosing raw exponents. A number of studies on have been carried out independently of the construction of polynomial commitment schemes. This work bridges two rather independent proof systems and provides a blueprint to combine these proof systems for the construction of an efficient, transparent polynomial commitment scheme in the discrete log setting.
- We propose a recursive argument to show the correct polynomial evaluation by employing . Our approach is to transpose a recursive argument from a class group in [] to that from the discrete log setting. We present a security analysis to demonstrate the completeness and soundness of the proposed protocol. In addition, We present a zero-knowledge version of the obtained polynomial commitment scheme. A zero-knowledge version ensures that no information of the prover’s secret polynomial is leaked while the prover convinces the verifier that holds for a point .
The remainder of this paper is organized as follows. In Section 2, we review related works. In Section 3, we provide the background on the hardness assumption and building blocks for polynomial commitment schemes. In Section 4, we present our approach to transpose Bünz et al.’s techniques in the discrete log setting and investigate a sub-routine protocol as a sufficient condition for our approach. In Section 5, we discuss the performance and security of our approach. In Section 6, we extend the polynomial commitment scheme in the previous section to the version with a zero-knowledge evaluation protocol. Finally, we provide some concluding remarks in Section 7.
2. Related Work
A lot of recent research on polynomial commitment schemes have been carried out in the context of Succinct Non-interactive ARguments of Knowledge (SNARKs). In particular, a polynomial commitment scheme provides a key tool to generate a zk-SNARK from a polynomial interactive oracle proof (IOP) [,].
Kate et al. first constructed efficient and succinct polynomial commitment schemes for univariate polynomials []. The construction is based on bilinear pairings over elliptic curves and requires a trusted setup. Its extension to multivariate polynomials has been proposed by Papamanthou et al. [] and Zhang et al. []. Zhang et al. [] also presented the zero-knowledge version of their work []. These schemes all use bilinear pairings and require a trusted setup.
Associated with transparent SNARKs, polynomial commitment schemes with a transparent setting have received significant attention and, along with the previously mentioned constructions, many schemes can be found in the literature. Bootle et al. [] constructed a transparent polynomial commitment scheme in the discrete log setting. They represent a polynomial of degree d as a matrix with rows and columns and then write a polynomial evaluation as matrix multiplications. This leads to a commitment size, verifier complexity, and communication complexity. Wahby et al. presented a transparent polynomial commitment scheme [] for multilinear polynomials under the discrete log assumption. The scheme is built on the ideas of a matrix commitment of Bootle et al. [] and the inner-product argument of Bünz et al. []. For a polynomial of degree d, the commitment size, verifier complexity, and communication complexity are required. Ben-Sasson et al. [] introduced the Fast Reed Solomon IOP of Proximity (FRI), which implicitly yields a transparent polynomial commitment scheme. Kattis et al. [] and Zhang et al. [] independently presented a method for obtaining polynomial commitment schemes from FRI. Their construction has size commitments for the security parameter and communication complexity and supports quantum resistance. In addition, Lee [] proposed a multivariate polynomial commitment scheme with a transparent setting using pairing-based commitments. The scheme builds on inner product arguments given in Bootle et al. [] and Bünz et al. []. Recently, Boneh et al. [] studied additive polynomial commitment schemes, where commitments form an additive group [,,,,]. They showed that the additive property yields a batch evaluation of polynomial commitments, which can be used for the efficient construction of SNARKs.
Groups of unknown order provide a mathematical structure for interesting cryptographic applications, such as delay functions [], accumulators [], and polynomial commitment schemes []. Most cryptographic applications consider two candidate groups of unknown order, i.e., RSA groups [] and ideal class groups of imaginary quadratic fields []. RSA groups assume a trusted setup in generating the RSA modulus and hence do not meet our current interest. By contrast, class groups do not require a trusted setup and thus have been used in recent constructions with a transparent setting [,,]. Dobson and Galbraith [] analyzed the security of the candidate parameters for class groups proposed in [,]. They argued that the parameters in [,] do not meet the desired security level and present much larger parameters, which lead to an extremely large size-up for commitments in previous constructions. In this line of research, Belabas et al. [] recently reported that the order assumption in class groups of imaginary quadratic fields does not hold in certain special classes of prime numbers. Some studies have explored alternative source groups of unknown order with a transparent setting. As an example, Dobson and Galbraith [] suggested the Jacobian of hyperelliptic curves of genus 3, whereas Lee [] pointed out that the order of the Jacobian of a hyperelliptic curve can be efficiently computed.
3. Preliminaries
Throughout the paper, denotes the security parameter written in unary. The function denotes a negligible function, i.e., . For a set S, we use to denote that an element e is sampled uniformly at random from S. For a probabilistic algorithm A, we write to denote that y is returned as the result of A on input x together with a randomness r picked internally.
3.1. The Discrete Logarithm Assumptions
Let be an algorithm that takes on input and returns a -bit prime number p, cyclic group of order p, and a generator g of .
Definition 1
(Discrete Logarithm Assumption). The discrete logarithm assumption holds relative to if for any polynomial-time adversary ,
Definition 2
(Discrete Logarithm Relation Assumption). The discrete logarithm relation assumption holds relative to if for any polynomial-time adversary ,
In the above definition, for some is called a non-trivial discrete logarithm relation. It is well-known that the discrete logarithm relation assumption is equivalent to the discrete logarithm assumption [].
3.2. Zero-Knowledge Arguments of Knowledge
Let be a polynomial-time-decidable binary relation. and are called a statement and a witness, respectively. We define as the set , which is called the language of . We consider an argument system for a relation consisting of three probabilistic polynomial-time algorithms . A non-interactive algorithm takes the security parameter as an input and returns a common reference string (crs) . and are called a prover and a verifier, respectively, and both are interactive algorithms. In addition, takes as input a triple of , a statement , and a witness . Moreover, takes as input a pair of and a statement and outputs 0 or 1. We denote the transcript produced by and for an interaction by and write , where if accepts and if rejects.
Definition 3
(Argument of Knowledge). We call the triple an argument of knowledge for relation if it has completeness and witness-extended emulation, as defined below.
Definition 4
(Perfect Completeness). has perfect completeness if for all non-uniform polynomial-time adversaries ,
Definition 5
(Witness-Extended Emulation [,]). has witness-extended emulation if for every deterministic polynomial-time prover there exists an expected polynomial-time emulator such that for all non-uniform polynomial-time adversaries , the difference between the following two probabilities is less than or equal to :
where the oracle called by permits rewinding to any round and running again on fresh verifier randomness, and is the initial state of .
Definition 6
(Public Coin). An argument system is called public coin if the verifier chooses its messages uniformly at random, and independently of the messages sent by the prover, i.e., the challenges correspond to the verifier’s randomness.
We recall special honest verifier zero-knowledge, which states that the view of the verifier can be simulated if the verifier follows the protocol honestly and if challenges made by the verifier are known in advance.
Definition 7
(Perfect SHVZK). A public coin argument system is called a perfect special honest verifier zero-knowledge (SHVZK) argument for relation if there exists a probabilistic polynomial-time simulator such that for all interactive non-uniform polynomial-time adversaries ,
where ρ is the public coin randomness used by the verifier.
The general forking lemma [,] is useful for proving that an argument system has witness-extended emulation. Consider a public coin interactive argument system with r rounds. We view distinct accepting transcripts as having a tree format with depth r and leaves, which we call an -tree. For , let be the i-th round challenge chosen among exactly values. The root node is labeled with a statement s and has exactly children labeled with a distinct value for , where each edge from the root to a child is labeled with a message from the prover to the verifier on . Similarly, each node in depth is labeled with a distinct value for and has children labeled with a distinct value for , where each edge from to is labeled with a message from the prover to the verifier on . Note that each path from the root to a leaf then corresponds to an accepting transcript.
Lemma 1
(General Forking Lemma [,]). Let be a public coin argument system for relation with r rounds. Let χ be a witness extraction algorithm that succeeds with overwhelming probability in extracting a witness from an -tree of accepting transcripts in probabilistic polynomial time. If is bounded above by a polynomial in the security parameter λ, has witness-extended emulation.
3.3. Commitment Schemes
We review the definitions and security properties regarding the polynomial commitment schemes. In the following, we use a tuple for arguments or a returned tuple of the prover and the verifier . In a tuple, before the semicolon and after it denotes public variables known to both and , and secret variables known to only , respectively.
Definition 8
(Commitment Scheme). A commitment scheme is a triple of probabilistic polynomial-time algorithms defined as follows:
- takes the security parameter λ on input, and outputs the public parameter, which specifies a message space, a randomness space, and a commitment space;
- takes a secret message m and an optional random r chosen uniformly at random on input and returns a commitment c and (optionally) a secret opening hint r;
- verifies the commitment c to the message m provided with the opening hint r. It outputsif the commitment is valid andotherwise.
A commitment scheme is binding if for all non-uniform polynomial-time adversaries,
A commitment scheme is hiding if for all non-uniform polynomial-time adversaries,
In a polynomial commitment scheme, additionally checks whether the evaluation at any point is correct with respect to the committed polynomial given by . The below definition of polynomial commitment schemes is given by Bünz et al. [], which extends that of Kate et al. [].
Definition 9
(Polynomial Commitment Scheme [,]). Let be a commitment scheme for a message space over a ring R. A polynomial commitment scheme additionally consists of a protocol as follows:
- is an interactive public coin protocol betweenand. Bothandhave as input a commitment c, points, and a degree d. In addition, knows the opening of c to a secret polynomialwithand a secret opening hint r. convincesthatby applying the protocol.
3.4. Privacy-Preserving Blockchain with SNARKs
Recently, SNARKs have been receiving a lot of attention from the blockchain industry as a solution for balancing privacy and publicly-verifiable integrity. For instance, Zcash employs SNARKs to provide Bitcoin with user anonymity and privacy of transaction data with anonymous coins []. SNARKs are also used to verify Ethereum smart contracts over private input [].
Figure 1 presents a high-level architecture of privacy-preserving blockchains with SNARKs. A typical way that SNARKs are used in blockchains is as follows. The real data is stored in off-chain storage. The data posted to the on-chain blockchain (blockchain ledger) consist of the commitment to the transaction and its proof that the target transaction is valid. Cryptographic commitment schemes ensure that it is very difficult to obtain the original input value from the committed value, and the proof generated using SNARKs can be verifiable by any node in the blockchain network. Therefore, the privacy problem is solved because the data is hidden in the public on-chain blockchain. In addition, since zero-knowledge techniques provide fast verification, they are being used in various ways to improve the performance and minimize the size of the blockchain. It is worth noting that a polynomial commitment scheme is a key building block to compile a polynomial IOP system, which is a formal representation of a proving statement, into a SNARK [,].
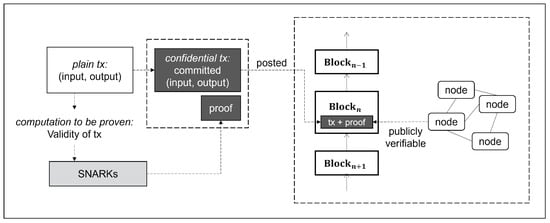
Figure 1.
Overview of blockchain with SNARKs.
4. Our Approach
In this section, we present our approach to transpose Bünz et al.’s techniques in the discrete log setting. We investigate and identify a sufficient condition for a transposition. Specifically, we show how to employ a proof system for the equality of discrete logarithms. For the rest of this paper, we encode a polynomial over a field into a vector . For a group let be a vector for some positive integer ℓ. For we denote the multi-exponentiation by . When it is clear from the context, we write the commitment to a polynomial as instead of for the sake of convenience. We also take a finite field as for a prime p. Table 1 presents frequently-used notations in the paper.

Table 1.
Notations.
4.1. Bünz et al.’s Abstraction
Bünz et al. [] presented a polynomial commitment scheme for their construction of SNARKs. The proposed scheme operates in a recursive way by reducing the degree of polynomial f by half during each iteration, and hence, there are iterations overall. More precisely, given an odd degree d polynomial , the prover splits it into two polynomials
which both polynomials have a degree of roughly satisfying
The prover then sends the verifier the commitments and to and , respectively. At the end of each iteration, the prover takes the next input polynomial as
for a random received from the verifier.
Because the verifier needs to check if from committed polynomials, the verifier should be able to homomorphically compute a committed form of the current and the next from and to see whether (1) holds. The verifier also needs to compute a commitment to a polynomial in (2) for the next iteration from and .
To support the computation of the committed form, Bünz et al. [] define the following two abstract properties.
- linear homomorphismfor polynomials f and g, and scalars a and b (a linear homomorphism);
- monomial homomorphismfor some bounded positive integer d.
Figure 2 illustrates Bünz et al.’s abstraction for a polynomial commitment scheme with a recursive argument from the above two properties.
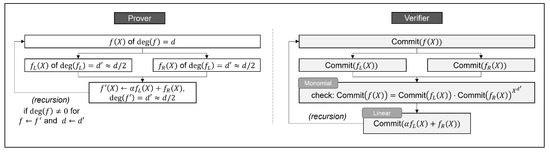
Figure 2.
Bünz et al.’s approach for the recursive argument. The prover recursively reduces the degree of f at each iteration over a plain f. The verifier recursively reduces the degree of f at each iteration over a committed form of f using monomial and linear homomorphic properties.
4.2. Base Commitment Scheme to Polynomial
We construct a polynomial commitment scheme based on a generalization of the Pedersen commitment scheme []. In the generalized Pedersen commitment, consists of a group of a prime order p, and group elements . For a secret message vector the prover chooses and computes
It is well-known that the generalized Pedersen commitment is perfectly hiding and computationally binding under the discrete logarithm relation assumption []. It is also important to note that the generalized Pedersen commitment scheme is homomorphic, i.e.,
We consider a commitment scheme, which does not use the randomness in the generalized Pedersen commitment scheme, as follows:
- : On input of the security parameter , it first samples of a prime order p of length . It then chooses and returns where .
- : For a secret polynomial with, it computes and outputs .
- : On input c and , the verifier computes and checks if in .
Because the generalized Pedersen commitment scheme is computationally binding under the discrete logarithm relation assumption, so is the commitment scheme above.
4.3. Evaluation Protocol
As presented in Section 4.1, Bünz et al.’s approach considers two properties (a linear homomorphism and a monomial homomorphism) for the underlying commitment schemes, which is crucial for the verifier to compute (1) from the commitments to the polynomials and on the right-hand side. However, our base commitment scheme does not provide monomial homomorphism, while it immediately holds the linear homomorphic property. A monomial homomorphic commitment scheme is not known thus far in the discrete log setting with no trusted setup. This is because a monomial homomorphic property may require some special structures for base elements in the group, which is impossible to generate without a trusted setup.
Thus, our approach focuses on providing a way to check the integrity of and , i.e., using the linear homomorphic property only. The idea behind our approach is presented in Figure 3. To avoid monomial homomorphism, our approach simply lets the prover send one additional commitment to besides two commitments to and so that can be verified using the linear homomorphic property.
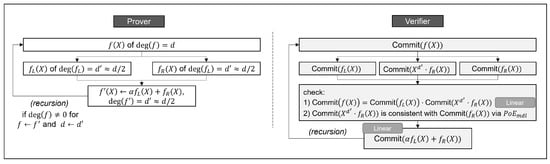
Figure 3.
Our approach for recursive argument. Aside from two commitments, and , the verifier additionally receives to confirm they properly come from the input polynomial f using linear homomorphic property only.
We present the evaluation protocol in Algorithm 1, which is a transposition of Bünz et al.’s construction [] in the discrete log setting. In Line 13 of the protocol, the prover sends one additional commitment . The verifier is then able to compute using a linear homomorphic property of the underlying commitment scheme (Line 13). However, because the polynomial is committed to and independently, it is required for the prover to prove that and are generated from the same polynomial . More precisely, given public parameter and two target instances and , the prover needs to convince the verifier that and have the same exponents. Thus, we require a proof for equality of discrete logarithms, which is invoked as a sub-protocol in the protocol (Line 12). takes , , , and on input and returns 1 if and have the same exponents and 0 otherwise. If the returned value is 0, aborts the protocol because is a cheating prover. We remark that several cryptographic protocols on have been proposed [,]. The works for have been developed independently from the construction of polynomial commitment schemes.
| Algorithm 1 | |
| |
| 1: if then | |
| 2: sends to | // is a constant |
| 3: checks that in | |
| 4: checks that in | |
| 5: returns 1 if all checks pass, 0 otherwise | |
| 6: else | |
| 7: and compute | |
| 8: sets and | //If d is even, then |
| 9: computes , , and in | |
| 10: computes and in | |
| 11: sends to | |
| 12: and run | //Checking that |
| 13: checks that in and returns 0 if the equation does not hold | |
| 14: checks that in and returns 0 if the equation does not hold | |
| 15: chooses and sends it to | |
| 16: and compute in and in | |
| 17: computes in | // |
| 18: and run | |
5. Discussion: Performance & Security Analysis
Let be the polynomial commitment scheme described in Section 4. In this section, we analyze the performance and security of the protocol.
5.1. Performance
We analyze the efficiency of our approach in comparison with the recently proposed schemes with a transparent setting found in the literature. For a concrete performance analysis, we borrow the examples of groups and parameters at the 128-bit security level given by Lee [], which is presented in Table 2. In Table 2, denotes a cyclic group of known order, which is implemented by curve25519-dalek []. An imaginary class group [] is taken as an example group of unknown order. The discriminant of is fixed as , which is estimated to offer the 128-bit security level []. This is implemented by ANTIC []. For a pairing-based construction, , , and denote the two source groups and the target group of a pairing P. The groups of pairing are implemented by RELIC [] over the curve BLS12-381 [].

Table 2.
Efficiency comparison between groups. The time is measured for operations to multiply a random point (element) of a group by a 256-bit scalar.
We analyze the efficiency of our approach. Let and be the size of an element in G and the communication complexity of , respectively. Let , , and be the computation cost in , the prover’s computation cost for , and the verifier’s computation cost for , respectively. Below we focus on the dominated terms for each complexity comprising the transmission and operations of the group elements, i.e., we neglect operations over a field . The protocol makes recursive calls roughly times. The messages between the prover and the verifier consist of times of three elements in , and , respectively. Thus, the communication complexity is equal to . The prover applies times of three multi-exponentiations [] of roughly size and one operation over , and on the prover’s side. This leads to computation complexity for the prover. The verifier applies times of one exponentiation and two operations over , and on the verifier’s side, which leads to computation complexity overall. The size of public parameter is .
We now provide a comparison for polynomial commitment schemes [,] with a transparent setting, which achieves a logarithmic verifier complexity in Table 3. The table focuses on the dominated terms for each complexity comprising the transmission and operations of the group elements. As mentioned above, We apply multi-exponentiation techniques [] to both our approach and Bünz et al.’s construction to reduce the prover complexity by a factor of . In the case of Bünz et al.’s construction, it is possible to reduce the size of public parameter to a single element of when multi-exponentiation techniques are not applied. Table 3 summarizes the efficiency analysis on communication and computation complexities, and the size of the public parameter for recent polynomial commitment schemes with transparent setting and our approach.

Table 3.
Comparison between polynomial commitment schemes with a transparent setting. and denote the size of an element and the computation cost of a group operation in the corresponding group, respectively. We express communication complexity in the number of group elements and computation complexity in a number of group operations.
Table 3 shows that the efficiency of our approach depends on that of . If has a constant communication/computation complexity, we observe that each complexity is almost the same across the schemes, and the efficiency of a scheme depends highly on the underlying group. The benchmark result on base groups in Table 2 shows that the sizes of the element in and are approximately and larger than that of , respectively. For the operation time, and are approximately and slower than that of , respectively.
The above discussion shows that our scheme based on an elliptic curve group in the discrete log setting is very promising in the case that we have an efficient . Unfortunately, currently known protocols have communication complexity for the number of bases, i.e., degree of a polynomial in our setting, which is not desirable for our purpose of logarithmic complexity. However, we emphasize that it is meaningful to observe that two independent cryptographic primitives are closely connected and suggest a stepping stone for the construction of an efficient, transparent polynomial commitment scheme with a recursive argument in the discrete log setting.
5.2. Security
We analyze perfect completeness (Definition 4) and witness-extended emulation (Definition 5) of the proposed polynomial commitment scheme.
Theorem 1.
Theprotocol of the polynomial commitment scheme Π has perfect completeness.
Proof of Theorem 1.
First, we show that the case of satisfies the perfect completeness. When , the valid input consists of the constant polynomial , , and . Thus, the verification equations checked by immediately hold.
Next, we consider the case of . For the polynomial , let and be the input and output tuples for every recursive step in the protocol. For the perfect completeness, it suffices to show that satisfies the relations , , and when the relations , , and hold for .
When is odd, we can see that from is exactly equal to from and Thus, the relation holds for . When is even, we have and , such that and . Thus, we can see that the following equations hold:
Finally, we have,
This completes the proof of the perfect completeness. □
We now prove that the protocol is sound, i.e., it has witness-extended emulation. In brief, we need to show that we can extract a witness polynomial from a tree of accepting transcripts, where the number of transcripts is bounded in a polynomial in . This can be done by extracting an intermediate secret polynomial at each iteration of , i.e., from Level to Level i in the tree. In Lemma 2, we first show that given two accepting transcripts, we can extract an intermediate witness polynomial at each iteration of the protocol. We then prove the witness-extended emulation for the whole protocol by using the lemma from leaf nodes to the root node sequentially in Theorem 2.
Lemma 2.
Let be the public parameter generated by . Suppose we have two accepting transcripts and for two distinct numbers α, , such that and . Furthermore, suppose and are polynomials in with a degree of at most d and . Then on the input of the above transcripts, there exists a probabilistic polynomial-time algorithm that extracts either with a degree of at most d such that , , or a breach of the binding property of the Pedersen commitment scheme relative to .
Proof of Lemma 2.
Because the two transcripts are valid, it holds that
We then have
Thus, is able to compute
from the binding property of the Pedersen commitment scheme. In addition, because it holds that
we let and . Then, and are identical to the evaluations of the above and at , respectively. □
Theorem 2.
The protocol has witness-extended emulation for a relation
if the discrete logarithm relation assumption holds for.
Proof of Theorem 2.
For witness-extended emulation, we call the general forking lemma (Lemma 1). Thus, we need to construct an expected polynomial-time extractor that extracts a witness from a tree whose number of leaves is bounded above by a polynomial in .
For the statement , we consider the following tree of the accepting transcripts. The root node is labeled with the first input statement to . Including the root node, let N be a node labeled with the statement . We denote the corresponding witness polynomial to by . N has two child nodes as follows. By rewinding the oracle two times with two different challenges and on the same input statement , each child node for the given challenge is labeled with the update statement . Finally, nodes with are leaf nodes of the tree. Because the number of levels with a branching factor of 2 is bounded by , there are at most transcripts in total, which is a polynomial in .
We now prove that there exists an extractor that extracts a witness from the above tree, which we construct in a recursive way. That is, we construct an extractor to extract for a statement at each node starting from the leaf nodes in the tree. We note that for the degree bound d in the root node is a desired extractor .
We fist consider to extract a witness from the leaves of the tree, i.e., . In this case, directly obtains a witness from the transcript given by the prover, such that and . We now move to the case of . From the construction of the tree, the node has two child nodes, where each node is labeled with the update statement on the same input statement with two distinct challenges and . We assume that we have the extractor that returns the valid witness for each child node. We then construct the extractor . extracts and with a degree of at most by applying Lemma 2. It then returns
whose degree is bounded by . Because the tree consists of the accepting transcripts, we have and . Then, by the general forking lemma, we conclude that Π has witness extended emulation. □
6. Extension to Zero-Knowledge Polynomial Evaluation
In this section, we extend the polynomial commitment scheme from Section 4 to a zero-knowledge version. The zero-knowledge protocol enables the prover to convince the verifier that the prover has a polynomial with such that for a public point but does not leak any other information about f that is formally defined in the notion of perfect SHVZK (Definition 7). For this, we require a hiding commitment scheme to polynomials, such as the generalization of the Pedersen commitment scheme, which uses randomness when generating a commitment []. Below, we give a formal description of the generalization of the Pedersen commitment scheme over the polynomials in .
- : On input of the security parameter , it first samples of a prime order p of length . It then chooses and returns .
- : For a secret polynomial it selects and outputs with secret opening information .
- : On input c and , a verifier computes and checks if in .
We present our zero-knowledge evaluation protocol in Algorithm 2. The protocol is also obtained by transposing the corresponding zero-knowledge evaluation protocol given by Bünz et al. under the discrete log setting []. The basic idea is to mask the prover’s secret polynomial with a random polynomial using the blinding technique introduced in [,,] and then run the protocol on it.
| Algorithm 2) | |
| |
| 1: samples a random polynomial of degree d | |
| 2: computes in for and in | // |
| 3: sends to | |
| 4: samples and sends it to | |
| 5: computes in and in | |
| 6: sends to | |
| 7: and compute in and in | // and |
| 8: and run | |
The protocol receives a hiding commitment to the prover’s secret polynomial on input, i.e., , which is perfectly indistinguishable to a random element in . To hand it over to the protocol, it is necessary to remove the randomization part from , which is equal to . However, because this reveals information on , the protocol lets the prover and the verifier collaboratively blind by (Line 5). Here, is a random polynomial selected by the prover (Line 1) and is a random number selected by the verifier (Line 4). Consequently, both the prover and the verifier succeed in generating a non-hiding commitment to under Π and the point , and then start the protocol (Lines 7–8).
Theorem 3.
The protocol has perfect completeness, witness-extended emulation, and perfect SHVZK for a relation
if the discrete logarithm relation assumption holds for .
Proof of Theorem 3.
(perfect completeness) We show that has perfect completeness. Because the protocol has perfect completeness (Theorem 1), it suffices to show that c and y are a valid input to . That is, c is the correct commitment to under and y is the evaluation of at in . Given of a degree of at most d and of degree d, we have
(witness-extended emulation) We show that has witness-extended emulation. From Theorem 2, we have an expected polynomial-time extractor that extracts for the protocol. Using , we construct an extractor to extract a witness from . The extractor runs the prover to obtain . At this point, then rewinds the oracle twice with distinct challenges and and obtains the corresponding commitments and to the witnesses and , respectively. Then, runs on inputs and and receives the corresponding witnesses and , respectively. Finally, is able to extract the witness from and , similarly to Lemma 2. This completes the proof of the witness-extended emulation. (perfect SHVZK) We construct the simulator . Given only the public input, the simulator outputs a simulated transcript that is identical to the valid transcript produced by the prover and the verifier in the real interaction. The simulator first samples a random polynomial of degree d and . In addition, samples a random challenge and computes and The simulator then simply applies the protocol honestly using as the witness. Because in a real execution, the values and are distributed uniformly at random over , the simulated and are identically distributed to real values. In addition, the real and ) are distributed uniformly at random over and of degree d, respectively, and the same distributions hold for the simulated and , respectively. The simulated is also distributed uniformly at random over , and thus the real is, because of the perfect hiding property of the underlying commitment scheme. Clearly, the simulated holds the relations
Finally, the protocol does not leak more than itself, which contains no information about . Therefore, the views of the simulated and real transcripts are identically distributed. This completes the proof of the perfect SHVZK. □
7. Conclusions
In this paper, we presented how to transpose a recursive argument of polynomial evaluation over a class group proposed by Bünz et al. to the discrete log setting as a way to improve the efficiency. The transposition follows from their information-theoretic abstraction. We found that the challenge for a transposition is to provide a monomial homomorphism for an underlying commitment scheme. We observed that when we use a polynomial encoding method that presents coefficients of the polynomial to the power of random group elements, an essential sufficient condition is a proof system for the equality of discrete logarithms () over multiple bases. We believe that our approach suggests a stepping stone for the construction of an efficient, transparent polynomial commitment scheme with a recursive argument in the discrete log setting. Currently, the efficiency of known proof systems for is not sufficient to hava logarithmic communication and verifier complexities. Therefore, in future work, we will continue to research how to improve the efficiency of , which leads to high-efficiency gains for the proposed construction in the discrete log setting.
Funding
This research received no external funding.
Acknowledgments
This work was supported by a research grant from Seoul Women’s University (2020-0454 and 2021-0093).
Conflicts of Interest
The author declares no conflict of interest.
References
- Ben-Sasson, E.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized Anonymous Payments from Bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 459–474. [Google Scholar]
- Eberhardt, J.; Tai, S. ZoKrates–Scalable Privacy-Preserving Off-Chain Computations. In Proceedings of the 2018 IEEE International Conference on Blockchain, Halifax, NS, Canada, 30 July–3 August 2018; pp. 1084–1091. [Google Scholar]
- Chiesa, A.; Hu, Y.; Maller, M.; Mishra, P.; Vesely, N.; Ward, N.P. Marlin: Preprocessing zkSNARKs with Universal and Updatable SRS. In Advances in Cryptology—EUROCRYPT 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 738–768. [Google Scholar]
- Maller, M.; Bowe, S.; Kohlweiss, M.; Meiklejohn, S. Sonic: Zero-Knowledge SNARKs from Linear-Size Universal and Updatable Structured Reference Strings. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security (CCS 2019), London, UK, 11–15 November 2019; pp. 2111–2128. [Google Scholar]
- Gabizon, A.; Williamson, Z.J.; Ciobotaru, O. PLONK: Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge. IACR Cryptol. ePrint Arch. 2019, 953. [Google Scholar]
- Bünz, B.; Fisch, B.; Szepieniec, A. Transparent SNARKs from DARK Compilers. In Advances in Cryptology—EUROCRYPT 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 677–706. [Google Scholar]
- Wahby, R.S.; Tzialla, I.; Shelat, A.; Thaler, J.; Walfish, M. Doubly-Efficient zkSNARKs Without Trusted Setup. In Proceedings of the 2018 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–24 May 2018; pp. 926–943. [Google Scholar]
- Kattis, A.; Panarin, K.; Vlasov, A. RedShift: Transparent SNARKs from List Polynomial Commitment IOPs. IACR Cryptol. ePrint Arch. 2019, 1400. [Google Scholar]
- Fiat, A.; Shamir, A. How to Prove Yourself: Practical Solutions to Identification and Signature Problems. In Advances in Cryptology—CRYPTO 1986; Springer: Berlin/Heidelberg, Germany, 1986; pp. 186–194. [Google Scholar]
- Kate, A.; Zaverucha, G.M.; Goldberg, I. Constant-Size Commitments to Polynomials and Their Applications. In Advances in Cryptology—ASIACRYPT 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 177–194. [Google Scholar]
- Hamdy, S.; Möller, B. Security of Cryptosystems Based on Class Groups of Imaginary Quadratic Orders. In Advances in Cryptology—ASIACRYPT 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 234–247. [Google Scholar]
- Buchmann, J.; Hamdy, S. A survey on IQ cryptography. In Public Key Cryptography and Computational Number Theory; De Gruyter: Berlin, Germany; New York, NY, USA, 2011; pp. 1–16. [Google Scholar]
- Dobson, S.; Galbraith, S.D. Trustless Groups of Unknown Order with Hyperelliptic Curves. IACR Cryptol. ePrint Arch. 2020, 2020, 196. [Google Scholar]
- Bootle, J.; Cerulli, A.; Chaidos, P.; Groth, J.; Petit, C. Efficient Zero-Knowledge Arguments for Arithmetic Circuits in the Discrete Log Setting. In Advances in Cryptology—EUROCRYPT 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 327–357. [Google Scholar]
- Pedersen, T.P. Non-Interactive and Information-Theoretic Secure Verifiable Secret Sharing. In Advances in Cryptology—CRYPTO 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 129–140. [Google Scholar]
- Papamanthou, C.; Shi, E.; Tamassia, R. Signatures of Correct Computation. In Theory of Cryptography, Proceedings of the 10th Theory of Cryptography Conference (TCC), Tokyo, Japan, 3–6 March 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 222–242. [Google Scholar]
- Zhang, Y.; Genkin, D.; Katz, J.; Papadopoulos, D.; Papamanthou, C. vSQL: Verifying Arbitrary SQL Queries over Dynamic Outsourced Databases. In Proceedings of the 2017 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–24 May 2017; pp. 863–880. [Google Scholar]
- Zhang, Y.; Genkin, D.; Katz, J.; Papadopoulos, D.; Papamanthou, C. A Zero-Knowledge Version of vSQL. IACR Cryptol. ePrint Arch. 2017, 1146. [Google Scholar]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short Proofs for Confidential Transactions and More. In Proceedings of the 2018 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 21–23 May 2018; pp. 315–334. [Google Scholar]
- Ben-Sasson, E.; Goldberg, L.; Kopparty, S.; Saraf, S. DEEP-FRI: Sampling Outside the Box Improves Soundness. In Proceedings of the 11th Innovations in Theoretical Computer Science Conference (ITCS), Washington, SA, USA, 12–14 January 2020; pp. 5:1–5:32. [Google Scholar]
- Zhang, J.; Xie, T.; Zhang, Y.; Song, D. Transparent Polynomial Delegation and Its Applications to Zero Knowledge Proof. In Proceedings of the 2020 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 18–20 May 2020; pp. 859–876. [Google Scholar]
- Lee, J. Dory: Efficient, Transparent arguments for Generalised Inner Products and Polynomial Commitments. IACR Cryptol. ePrint Arch. 2020, 1274. [Google Scholar]
- Boneh, D.; Drake, J.; Fisch, B.; Gabizon, A. Halo Infinite: Recursive zk-SNARKs from any Additive Polynomial Commitment Scheme. IACR Cryptol. ePrint Arch. 2020, 1536. [Google Scholar]
- Wesolowski, B. Efficient Verifiable Delay Functions. In Advances in Cryptology—EUROCRYPT 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 379–407. [Google Scholar]
- Boneh, D.; Bünz, B.; Fisch, B. Batching Techniques for Accumulators with Applications to IOPs and Stateless Blockchains. Advances in Cryptology—CRYPTO 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 561–586. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Wagner, D.A. Time-Lock Puzzles and Timed-Release Crypto; Technical Report; Massachusetts Institute of Technology: Cambridge, MA, USA, 1996. [Google Scholar]
- Buchmann, J.; Williams, H.C. A Key-Exchange System Based on Imaginary Quadratic Fields. J. Cryptol. 1988, 1, 107–118. [Google Scholar] [CrossRef]
- Belabas, K.; Kleinjung, T.; Sanso, A.; Wesolowski, B. A note on the low order assumption in class group of an imaginary quadratic number fields. IACR Cryptol. ePrint Arch. 2020, 1310. [Google Scholar]
- Lee, J. The security of Groups of Unknown Order based on Jacobians of Hyperelliptic Curves. IACR Cryptol. ePrint Arch. 2020, 289. [Google Scholar]
- Lindell, Y. Parallel Coin-Tossing and Constant-Round Secure Two-Party Computation. J. Cryptol. 2003, 16, 143–184. [Google Scholar] [CrossRef] [Green Version]
- Groth, J.; Ishai, Y. Sub-linear Zero-Knowledge Argument for Correctness of a Shuffle. In Advances in Cryptology—EUROCRYPT 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 379–396. [Google Scholar]
- Groth, J. Linear Algebra with Sub-linear Zero-Knowledge Arguments. In Advances in Cryptology—CRYPTO 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 192–208. [Google Scholar]
- Chaum, D.; Evertse, J.; van de Graaf, J. An Improved Protocol for Demonstrating Possession of Discrete Logarithms and Some Generalizations. In Advances in Cryptology—EUROCRYPT 1987; Springer: Berlin/Heidelberg, Germany, 1987; pp. 127–141. [Google Scholar]
- Chaum, D.; Pedersen, T.P. Transferred Cash Grows in Size. In Advances in Cryptology—EUROCRYPT 1992; Springer: Berlin/Heidelberg, Germany, 1992; pp. 390–407. [Google Scholar]
- Lovecruft, I.A.; de Valence, H. curve25519-dalek: A pure-rust implementation of group operations on ristretto and curve25519. Available online: https://github.com/zkcrypto/curve25519-dalek-ng (accessed on 28 December 2021).
- Jacobson, M.J., Jr.; van der Poorten, A.J. Computational Aspects of NUCOMP. In Proceedings of the 5th International Symposium Algorithmic Number Theory, Sydney, Australia, 7–12 July 2002; pp. 120–133. [Google Scholar]
- Hart, W. ANTIC—Algebraic Number Theory in C. Available online: https://github.com/wbhart/antic (accessed on 28 December 2021).
- Aranha, D.F.; Gouvêa, C.P.L.; Markmann, T.; Wahby, R.S.; Liao, K. RELIC Is an Efficient LIbrary for Cryptography. Available online: https://github.com/relic-toolkit/relic (accessed on 28 December 2021).
- Bowe, S. BLS12-381: New zk-SNARK Elliptic Curve Construction. Available online: https://electriccoin.co/blog/new-snark-curve/ (accessed on 23 December 2021).
- Pippenger, N. On the Evaluation of Powers and Monomials. SIAM J. Comput. 1980, 9, 230–250. [Google Scholar] [CrossRef] [Green Version]
- Chiesa, A.; Forbes, M.A.; Spooner, N. A Zero Knowledge Sumcheck and its Applications. arXiv 2017, arXiv:1704.02086. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).