Multi-Constrained and Edge-Enabled Selection of UAV Participants in Federated Learning Process
Abstract
:1. Introduction
- We study the problem of participants selection in FL. The problem is formulated as an Integer Linear Program (ILP), where the objective is to select a subset of UAVs that are able to build local DL models, while increasing the learning accuracy. Noting that we leverage Python’s PuLP optimization package [15] to resolve our ILP.
- We show that the problem can be NP-hard and design a novel Tabu Search-based (TS) algorithm to determine near-optimal solutions. This is critical when the number of UAVs and their applications is very high and exact solutions are computationally costly.
- We validate the performance of the proposed scheme via simulation, showing our scheme to succeed in selecting the suitable UAV participants for FL process, while optimizing the aggregated accuracy of the generated learning models in FL.
2. Related Work
2.1. Client/Participant Selection in FL Process
2.2. Resource-Constrained Client/Participant Selection in FL Process
2.3. Comparative Study and Discussion
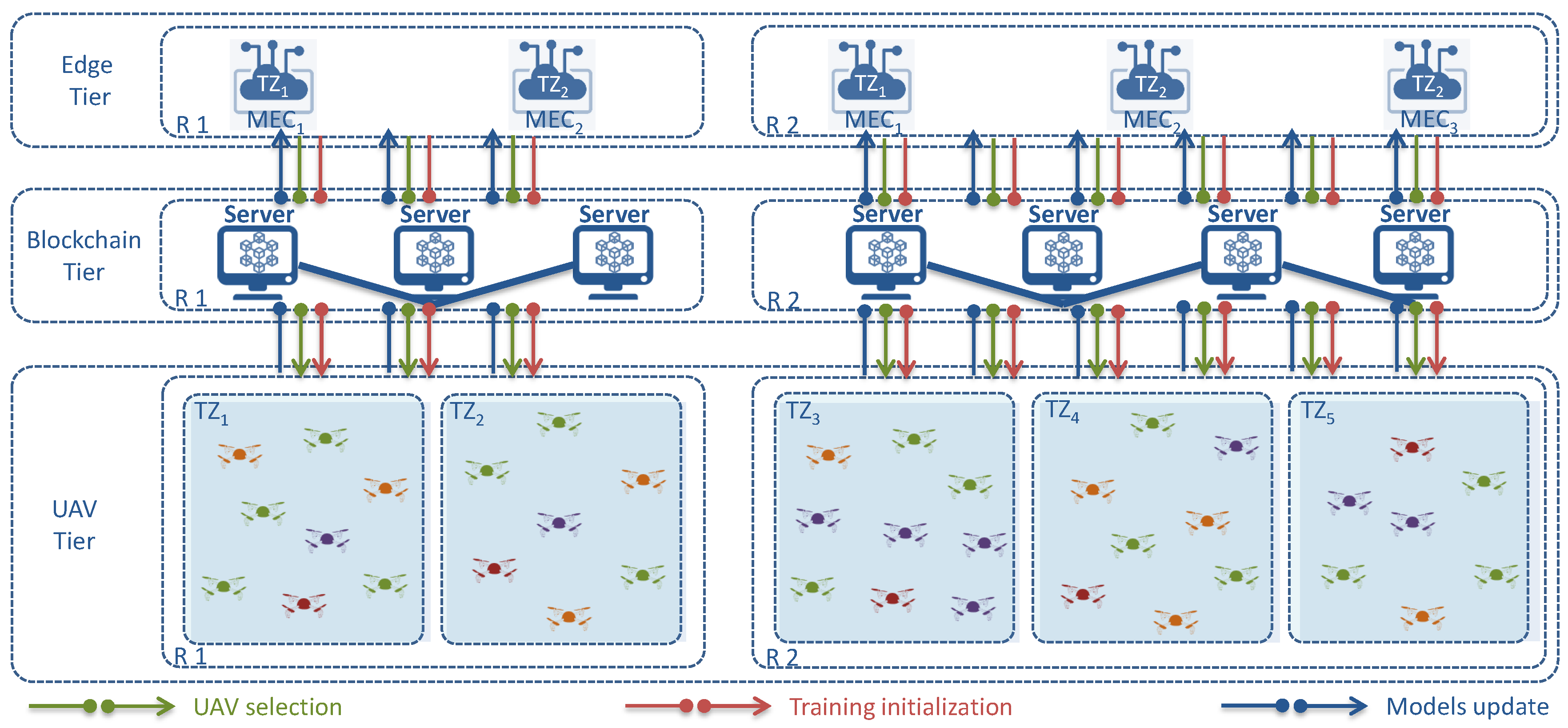
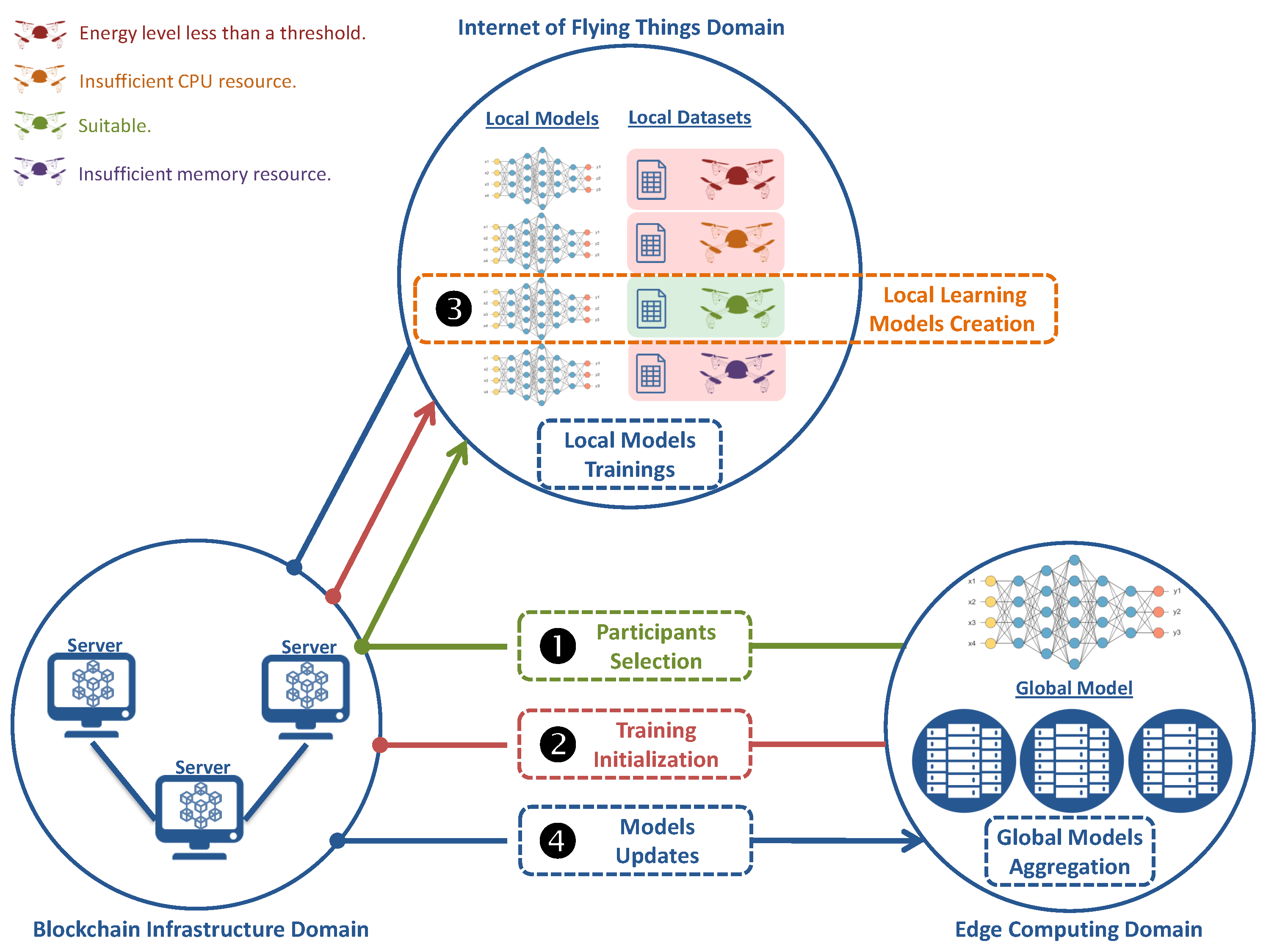
3. FedSel: Our S-MEC-Enabled Selection of UAVs Participants Framework
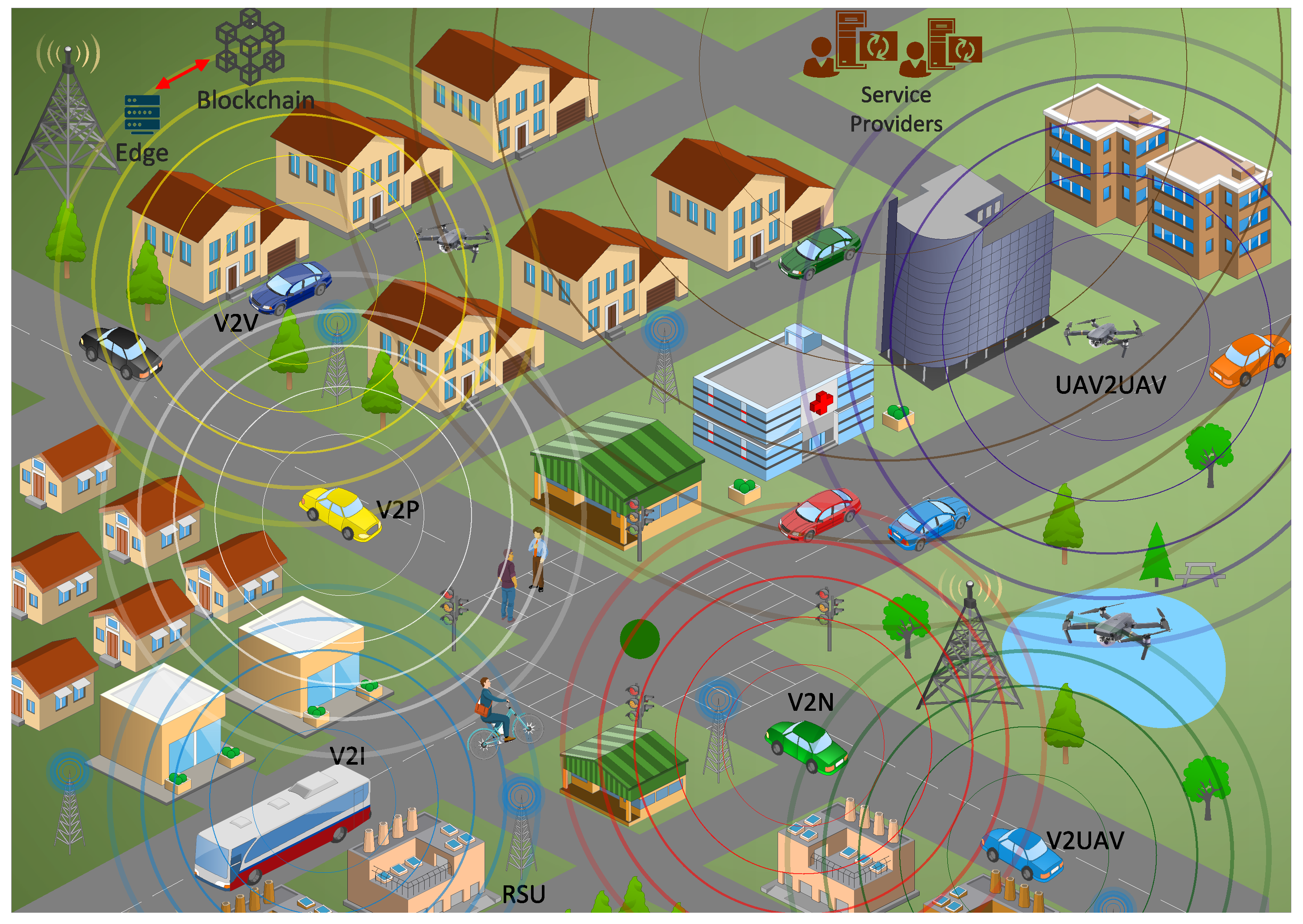
3.1. System Model
3.2. Uavs Selection Problem Formulation
3.3. Tabu-Search Problem Resolution
- Overview of Tabu Search: Tabu search (TS) is a mathematical optimization approach that uses a metaheuristic local search method to find sub-optimal solutions to large combinatorial problems, in many practical scenarios. To avoid cycles, TS prevents previously visited solutions or others using user-provided rules and short-term memory. The Tabu List (TL) is formed of these memory structures and comprises a list of recently visited locations. As a result, until a termination condition is met, a local search algorithm is applied to move from one solution to another within the neighborhood solution space. A predefined number of algorithm iterations or a threshold value is usually used as a termination condition.To construct an initial potential solution , the TS algorithm begins with an initialization phase. Note that the farther this solution is from the optimal solution, the greater is the overall execution time.
- TS-based UAVs participant selection: In the following, we describe how we use TS to optimize the selection of UAVs to participate in FL process. We first present the main elements of Tabu Search approach:
- For the first step, we select the available UAVs for an , excluding those that do not supply the ’s required services.
- A potential solution is a (N ✕ M) assignment matrix ensuring that all the constraints in our formulation are met:
- To switch from one solution to another, we simply swap the assignments of two applications to two UAVs that are randomly chosen. As a result, a move m(N,M) is a matrix with all of its values equal to zero except the values corresponding to the new and old assignment positions, which are set to one.
- To achieve a neighborhood solution of or a new solution , we use the function: .
- The attribute of each solution is the value of its objective function. The TL is then updated by including the attribute, which represents the best-obtained solution.
| Algorithm 1: TS-based UAVs participant selection. |
 |
4. Experimental Results
4.1. Simulation Setup
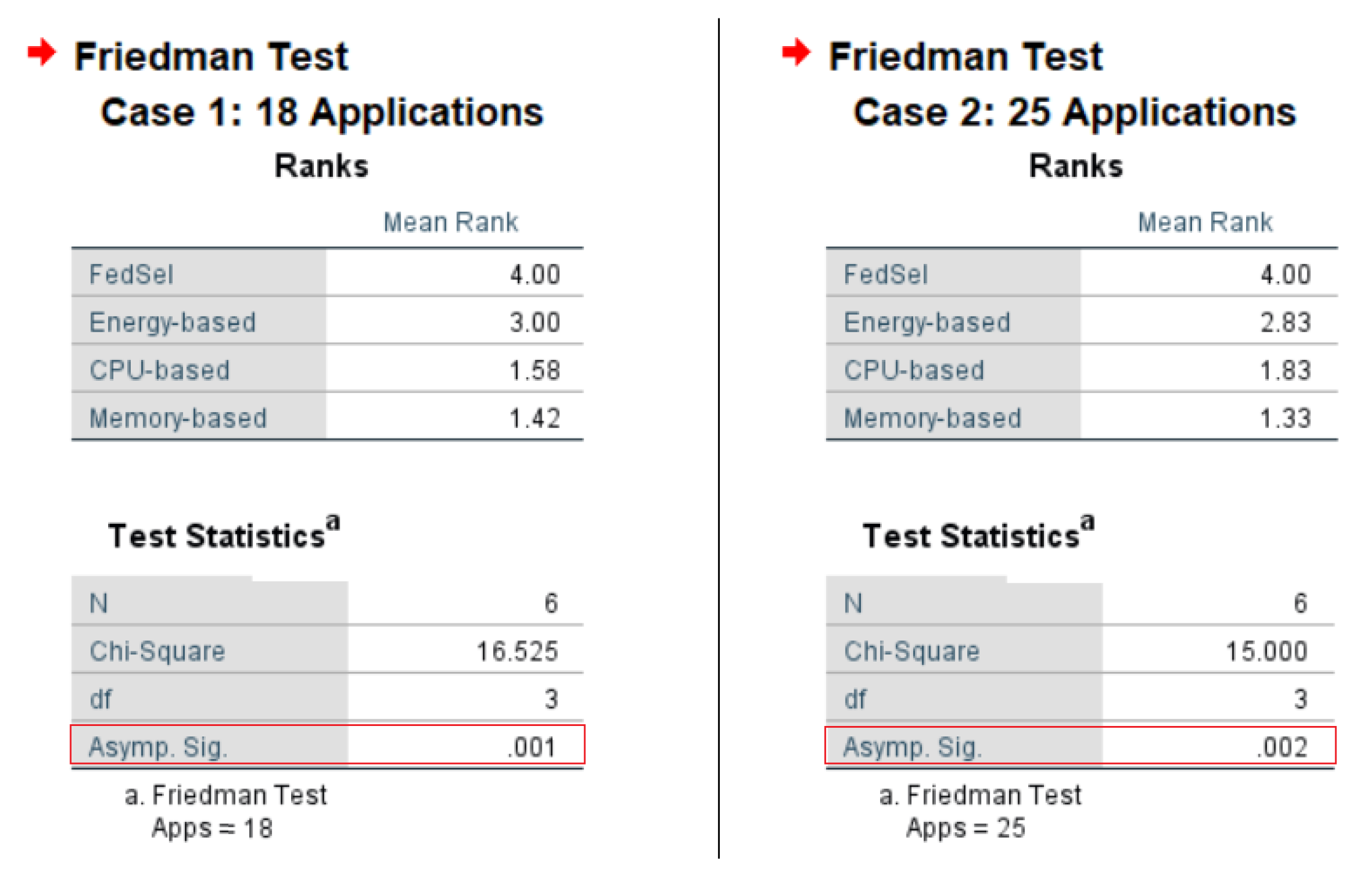
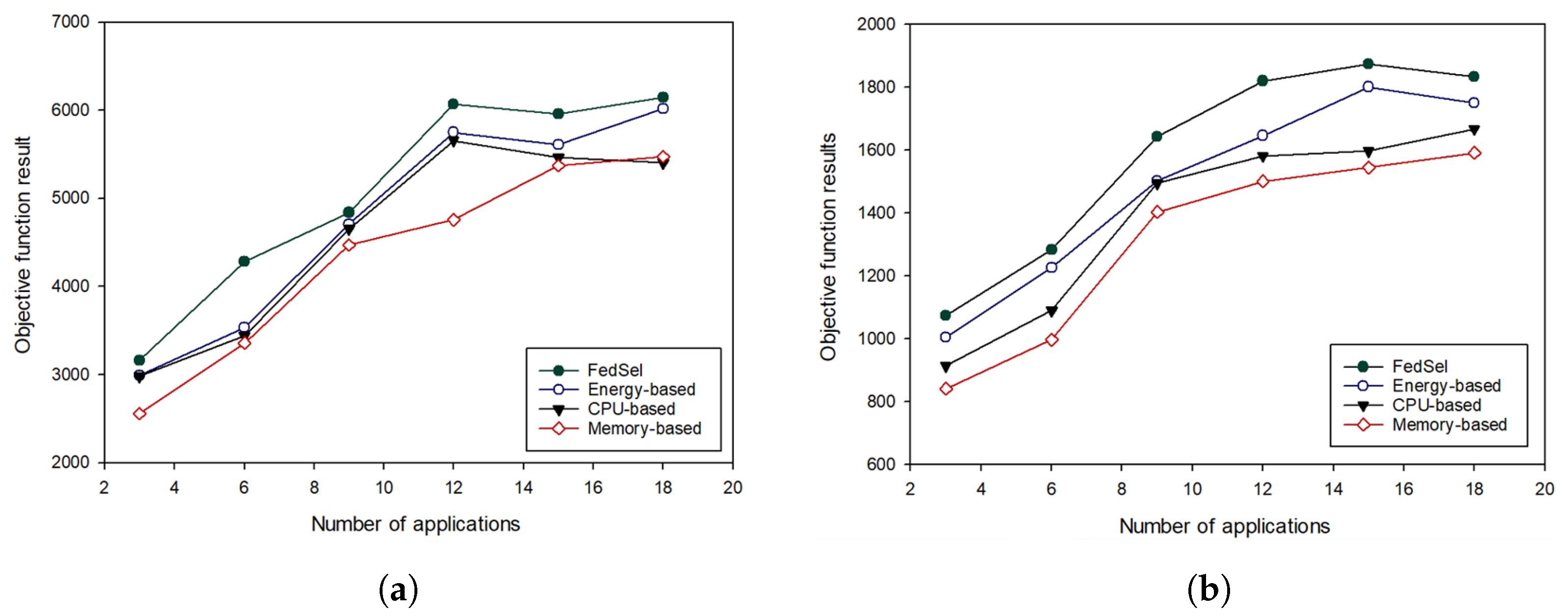
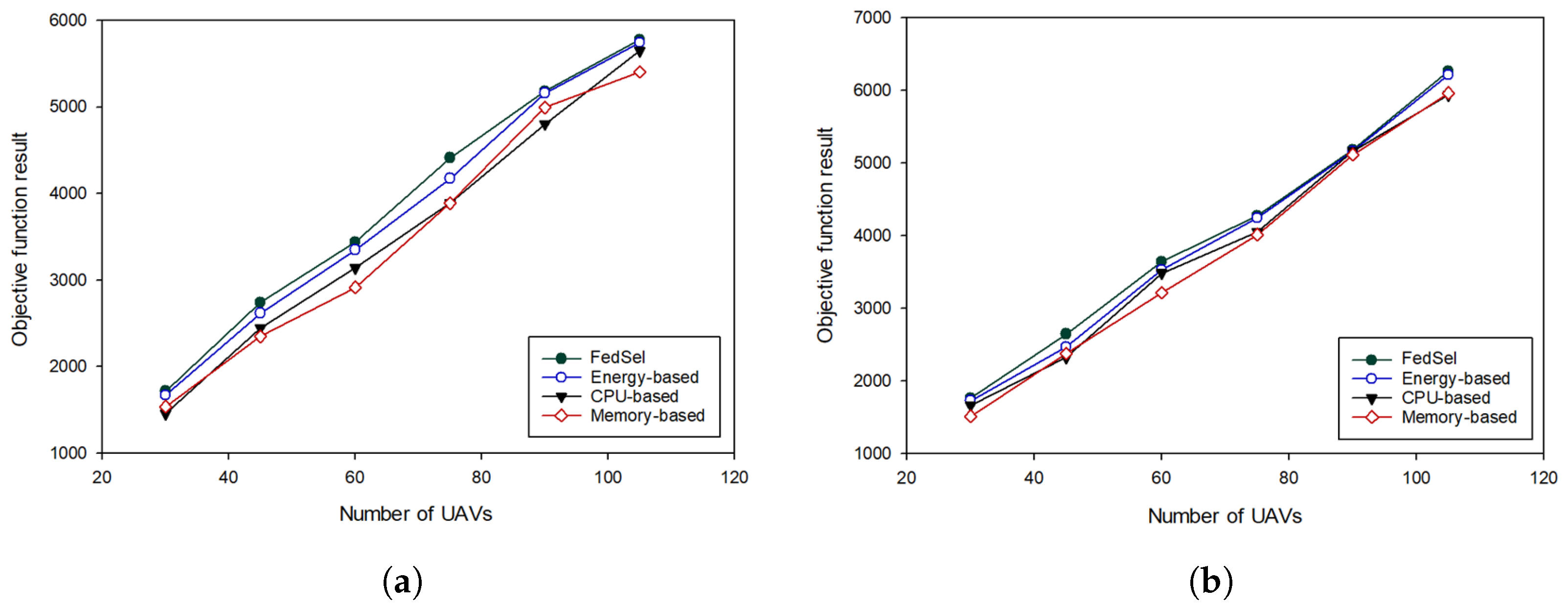
4.2. Performance Evaluation of Our UAV Selection Scheme
5. Conclusions and Future Directions
Author Contributions
Funding
Conflicts of Interest
References
- Billah, M.; Mehedi, S.; Anwar, A.; Rahman, Z.; Islam, R. A Systematic Literature Review on Blockchain Enabled Federated Learning Framework for Internet of Vehicles. arXiv 2022, arXiv:2203.05192. [Google Scholar]
- Syed, F.; Gupta, S.K.; Hamood Alsamhi, S.; Rashid, M.; Liu, X. A survey on recent optimal techniques for securing unmanned aerial vehicles applications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4133. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. UAV task allocation based on clone selection algorithm. Wirel. Commun. Mob. Comput. 2021, 2021, 5518927. [Google Scholar] [CrossRef]
- Kayalvizhi, M.; Ramamoorthy, S. Review of Security Gaps in Optimal Path Selection in Unmanned Aerial Vehicles Communication. In Sustainable Advanced Computing; Springer: Singapore, 2022; pp. 439–451. [Google Scholar]
- Nguyen, D.C.; Hosseinalipour, S.; Love, D.J.; Pathirana, P.N.; Brinton, C.G. Latency Optimization for Blockchain-Empowered Federated Learning in Multi-Server Edge Computing. arXiv 2022, arXiv:2203.09670. [Google Scholar]
- Liu, X.; Deng, Y.; Mahmoodi, T. A Novel Hybrid Split and Federated Learning Architecture in Wireless UAV Networks. In Proceedings of the IEEE ICC, Seoul, Korea, 16–20 May 2022; IEEE: Manhattan, NY, USA, 2022. [Google Scholar]
- Brik, B.; Messaadia, M.; Sahnoun, M.; Bettayeb, B.; Benatia, M.A. Fog-Supported Low-Latency Monitoring of System Disruptions in Industry 4.0: A Federated Learning Approach. ACM Trans. Cyber-Phys. Syst. 2022, 6, 14. [Google Scholar] [CrossRef]
- Yang, H.; Zhao, J.; Xiong, Z.; Lam, K.Y.; Sun, S.; Xiao, L. Privacy-preserving federated learning for UAV-enabled networks: Learning-based joint scheduling and resource management. IEEE J. Sel. Areas Commun. 2021, 39, 3144–3159. [Google Scholar] [CrossRef]
- Brik, B.; Ksentini, A.; Bouaziz, M. Federated learning for UAVs-enabled wireless networks: Use cases, challenges, and open problems. IEEE Access 2020, 8, 53841–53849. [Google Scholar] [CrossRef]
- Brik, B.; Ksentini, A. On Predicting Service-oriented Network Slices Performances in 5G: A Federated Learning Approach. In Proceedings of the 2020 IEEE 45th Conference on Local Computer Networks (LCN), Sydney, Australia, 16–19 November 2020; pp. 164–171. [Google Scholar] [CrossRef]
- Saraswat, D.; Verma, A.; Bhattacharya, P.; Tanwar, S.; Sharma, G.; Bokoro, P.N.; Sharma, R. Blockchain-Based Federated Learning in UAVs Beyond 5G Networks: A Solution Taxonomy and Future Directions. IEEE Access 2022, 10, 33154–33182. [Google Scholar] [CrossRef]
- Abou El Houda, Z.; Brik, B.; Ksentini, A.; Khoukhi, L.; Guizani, M. When Federated Learning Meets Game Theory: A Cooperative Framework to secure IIoT Applications on Edge Computing. IEEE Trans. Ind. Inform. 2022, 1. [Google Scholar] [CrossRef]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H. A Federated Learning and Blockchain-enabled Sustainable Energy-Trade at the Edge: A Framework for Industry 4.0. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Mathlouthi, I.; Gendreau, M.; Potvin, J.Y. A metaheuristic based on Tabu search for solving a technician routing and scheduling problem. Comput. Oper. Res. 2021, 125, 105079. [Google Scholar] [CrossRef]
- Mitchell, S.; OSullivan, M.; Dunning, I. PuLP: A Linear Programming Toolkit for Python; The University of Auckland: Auckland, New Zealand, 2011; Volume 65. [Google Scholar]
- Lai, F.; Zhu, X.; Madhyastha, H.V.; Chowdhury, M. Oort: Efficient federated learning via guided participant selection. In Proceedings of the 15th USENIX Symposium on Operating Systems Design and Implementation (OSDI 21), Santa Clara, CA, USA, 14–16 July 2021; pp. 19–35. [Google Scholar]
- Chai, Z.; Ali, A.; Zawad, S.; Truex, S.; Anwar, A.; Baracaldo, N.; Zhou, Y.; Ludwig, H.; Yan, F.; Cheng, Y. Tifl: A tier-based federated learning system. In Proceedings of the 29th International Symposium on High-Performance Parallel and Distributed Computing, Stockholm, Sweden, 23–26 June 2020; pp. 125–136. [Google Scholar]
- Li, L.; Duan, M.; Liu, D.; Zhang, Y.; Ren, A.; Chen, X.; Tan, Y.; Wang, C. FedSAE: A novel self-adaptive federated learning framework in heterogeneous systems. In Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN), Shenzhen, China, 18–22 July 2021; pp. 1–10. [Google Scholar]
- Wang, H.; Kaplan, Z.; Niu, D.; Li, B. Optimizing federated learning on non-iid data with reinforcement learning. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 1698–1707. [Google Scholar]
- Yang, M.; Wang, X.; Zhu, H.; Wang, H.; Qian, H. Federated learning with class imbalance reduction. In Proceedings of the 2021 29th European Signal Processing Conference (EUSIPCO), Dublin, Ireland, 23–27 August 2021; pp. 2174–2178. [Google Scholar]
- Nishio, T.; Yonetani, R. Client Selection for Federated Learning with Heterogeneous Resources in Mobile Edge. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- Dai, Z.; Zhang, Y.; Zhang, W.; Luo, X.; He, Z. A Multi-Agent Collaborative Environment Learning Method for UAV Deployment and Resource Allocation. IEEE Trans. Signal Inf. Process. Over Netw. 2022, 8, 120–130. [Google Scholar] [CrossRef]
- Kim, S.; Ibrahim, A.S. Byzantine-Fault-Tolerant Consensus via Reinforcement Learning for Permissioned Blockchain-Empowered V2X Network. IEEE Trans. Intell. Veh. 2022. [Google Scholar] [CrossRef]
- Ghdiri, O.; Jaafar, W.; Alfattani, S.; Abderrazak, J.B.; Yanikomeroglu, H. Offline and Online UAV-Enabled Data Collection in Time-Constrained IoT Networks. IEEE Trans. Green Commun. Netw. 2021, 5, 1918–1933. [Google Scholar] [CrossRef]
- Brik, B.; Frangoudis, P.A.; Ksentini, A. Service-oriented MEC applications placement in a federated edge cloud architecture. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Asim, M.; Mashwani, W.K.; A. Abd El-Latif, A. Energy and task completion time minimization algorithm for UAVs-empowered MEC SYSTEM. Sustain. Comput. Inform. Syst. 2022, 35, 100698. [Google Scholar] [CrossRef]
- Qi, N.; Huang, Z.; Zhou, F.; Shi, Q.; Wu, Q.; Xiao, M. A Task-driven Sequential Overlapping Coalition Formation Game for Resource Allocation in Heterogeneous UAV Networks. IEEE Trans. Mob. Comput. 2022, 1. [Google Scholar] [CrossRef]
- Welcome to Python. Available online: https://www.python.org/ (accessed on 20 June 2022).
| Acronym | Definition |
|---|---|
| B5G | Beyond 5 Generation |
| CF | Coalition Formation |
| CPU | Central Processing Unit |
| D2D | Device-to-Device |
| DL | Deep Learning |
| ETSI | European Telecommunications Standards Institute |
| FAA | Federal Aviation Authority |
| FDL | Federated Deep Learning |
| FL | Federated Learning |
| GLS | Guided Local Search |
| HF | Hyper-ledger Fabric |
| ILP | Integer Linear Program |
| IoD | Internet of Drones |
| IoFT | Internet of Flying Things |
| IoT | Internet of Things |
| MAB | multi-armed bandit |
| MEC | Multi Access Edge Computing |
| ML | Machine Learning |
| NAS | National Airspace |
| NP | Non Polynomial |
| NP-Hard | Non Polynomial Hard |
| OCF | Overlapping Coalition Formation |
| RL | Reinforcement Learning |
| SA | Simulated Annealing |
| S-MEC | Multi Access Edge Computing |
| TL | Tabu List |
| TS | Tabu Search |
| TZ | Tracking Zone |
| UAV | Unmanned Aerial Vehicle |
| Ref. | Year | Used Technologies | Selection | Heterogeneity | Considered Parameters | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ML | FL | BC | Edge | UAV | Energy | CPU | Memory | |||||
| Res-F networks | [16] | 2021 | ✓ | ✓ | ✓ | |||||||
| [17] | 2020 | ✓ | ✓ | ✓ | ||||||||
| [18] | 2021 | ✓ | ✓ | ✓ | // | |||||||
| [19] | 2020 | ✓ | ✓ | ✓ | ✓ | |||||||
| [20] | 2021 | ✓ | ✓ | ✓ | ✓ | |||||||
| Res-C networks | [21] | 2019 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| [22] | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| [9] | 2020 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||
| [23] | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| [24] | 2021 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Our FedSel | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| Parameter | Value |
|---|---|
| Number of UAVs | 30, 45, 60, 75, 90, 105 |
| Number of MEC apps | 3, 6, 9, 12, 15, 18 25 |
| UAV accuracy | [15, 100] |
| CPU capacity | [15, 100] GHz |
| CPU required | [1, 15] GHz |
| Memory capacity | [15, 100] GB |
| Memory required | [1, 15] GB |
| Energy capacity | [15, 100] watt |
| Energy required | [1, 15] watt |
| Case 1: 18 Apps | Case 2: 25 Apps | |||||||
|---|---|---|---|---|---|---|---|---|
| UAVs Number | FedSel | Energy-Based | CPU-Based | Memory-Based | FedSel | Energy-Based | CPU-Based | Memory-Based |
| 30 | 1717 | 1668 | 1457 | 1539 | 1763 | 1727 | 1661 | 1514 |
| 45 | 2739 | 2620 | 2447 | 2351 | 2645 | 2463 | 2321 | 2375 |
| 60 | 3439 | 3350 | 3139 | 2915 | 3638 | 3529 | 3481 | 3212 |
| 75 | 4414 | 4177 | 3891 | 3891 | 4270 | 4241 | 4096 | 4013 |
| 90 | 5184 | 5162 | 4803 | 4996 | 5179 | 5158 | 5160 | 5113 |
| 105 | 5780 | 5745 | 5650 | 5405 | 6265 | 6210 | 5935 | 5962 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dahmane, S.; Yagoubi, M.B.; Brik, B.; Kerrache, C.A.; Calafate, C.T.; Lorenz, P. Multi-Constrained and Edge-Enabled Selection of UAV Participants in Federated Learning Process. Electronics 2022, 11, 2119. https://doi.org/10.3390/electronics11142119
Dahmane S, Yagoubi MB, Brik B, Kerrache CA, Calafate CT, Lorenz P. Multi-Constrained and Edge-Enabled Selection of UAV Participants in Federated Learning Process. Electronics. 2022; 11(14):2119. https://doi.org/10.3390/electronics11142119
Chicago/Turabian StyleDahmane, Sofiane, Mohamed Bachir Yagoubi, Bouziane Brik, Chaker Abdelaziz Kerrache, Carlos Tavares Calafate, and Pascal Lorenz. 2022. "Multi-Constrained and Edge-Enabled Selection of UAV Participants in Federated Learning Process" Electronics 11, no. 14: 2119. https://doi.org/10.3390/electronics11142119










