On Secrecy Performance of a Dual-Hop UAV-Assisted Relaying Network with Randomly Distributed Non-Colluding Eavesdroppers: A Stochastic Geometry Approach
Abstract
:1. Introduction
1.1. Background Information
1.2. Prior Work
1.3. Motivations and Contribution
- The CDF of the UAV with respect to the user and the eavesdroppers’ link are obtained through the stochastic geometric approach.
- The network CDF equivalent end-to-end SNR is derived via the DF relaying protocol.
- The analytical closed-form expressions of the security outage probability and strictly positive secrecy capacity (SPSC) at a lower bound are obtained for the proposed network.
- The exact closed-form expression of the average secrecy capacity is derived for the proposed network.
- With respect to [4], where the secrecy performance of a UAV-assisted-relaying network was studied under the presence of a single eavesdropper, the position of both the ground user and the eavesdropper were not considered. In this paper, the locations of nodes in the network are modeled through a stochastic geometric approach and multiple eavesdroppers are considered.
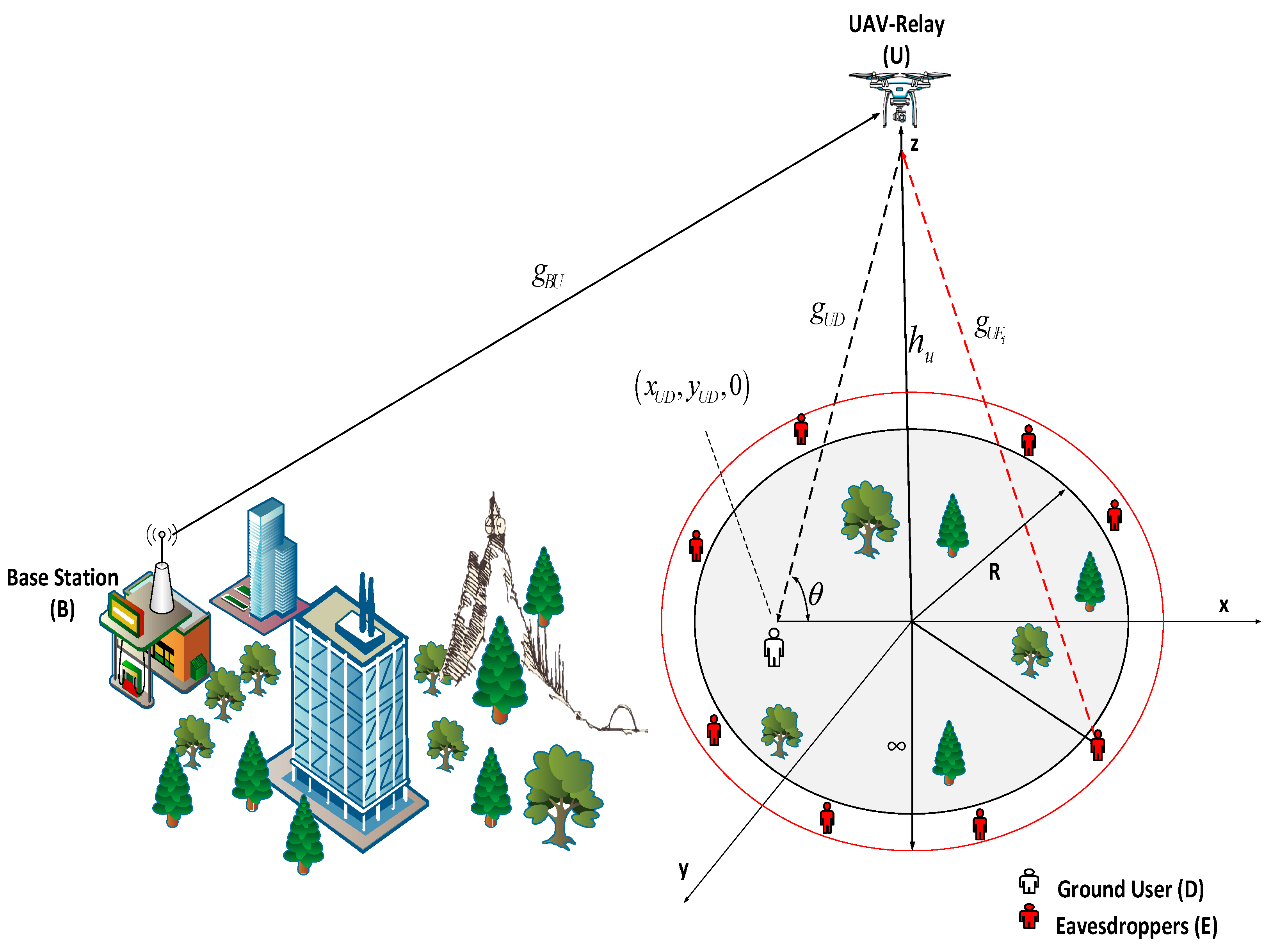
2. Network Description and Channels Model
2.1. Base Station-to-UAV Link
2.2. UAV-to-User and Eavesdroppers’ Links
3. Statistical Characteristics of Equivalent SNR
4. Secrecy Performance Analysis
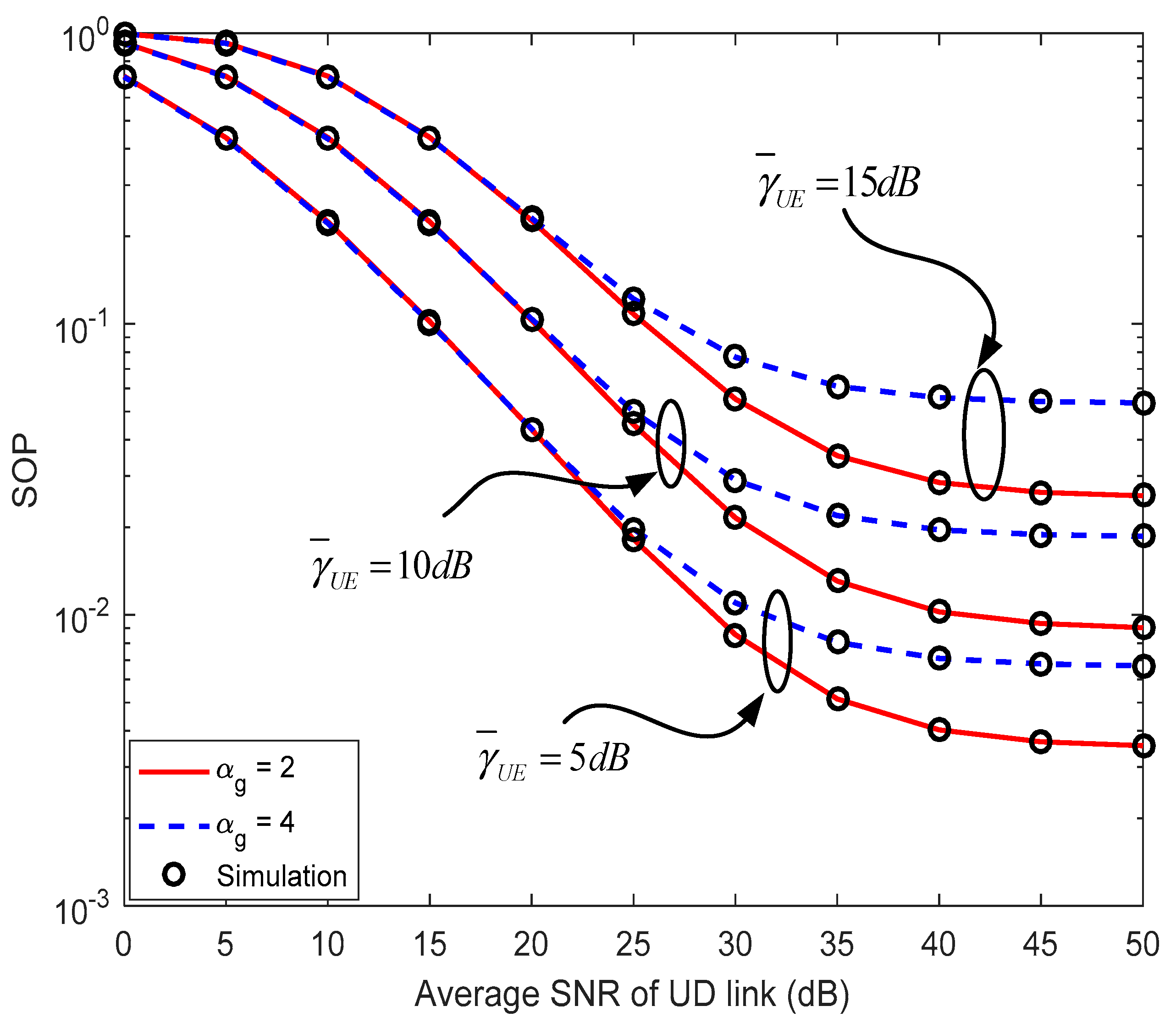
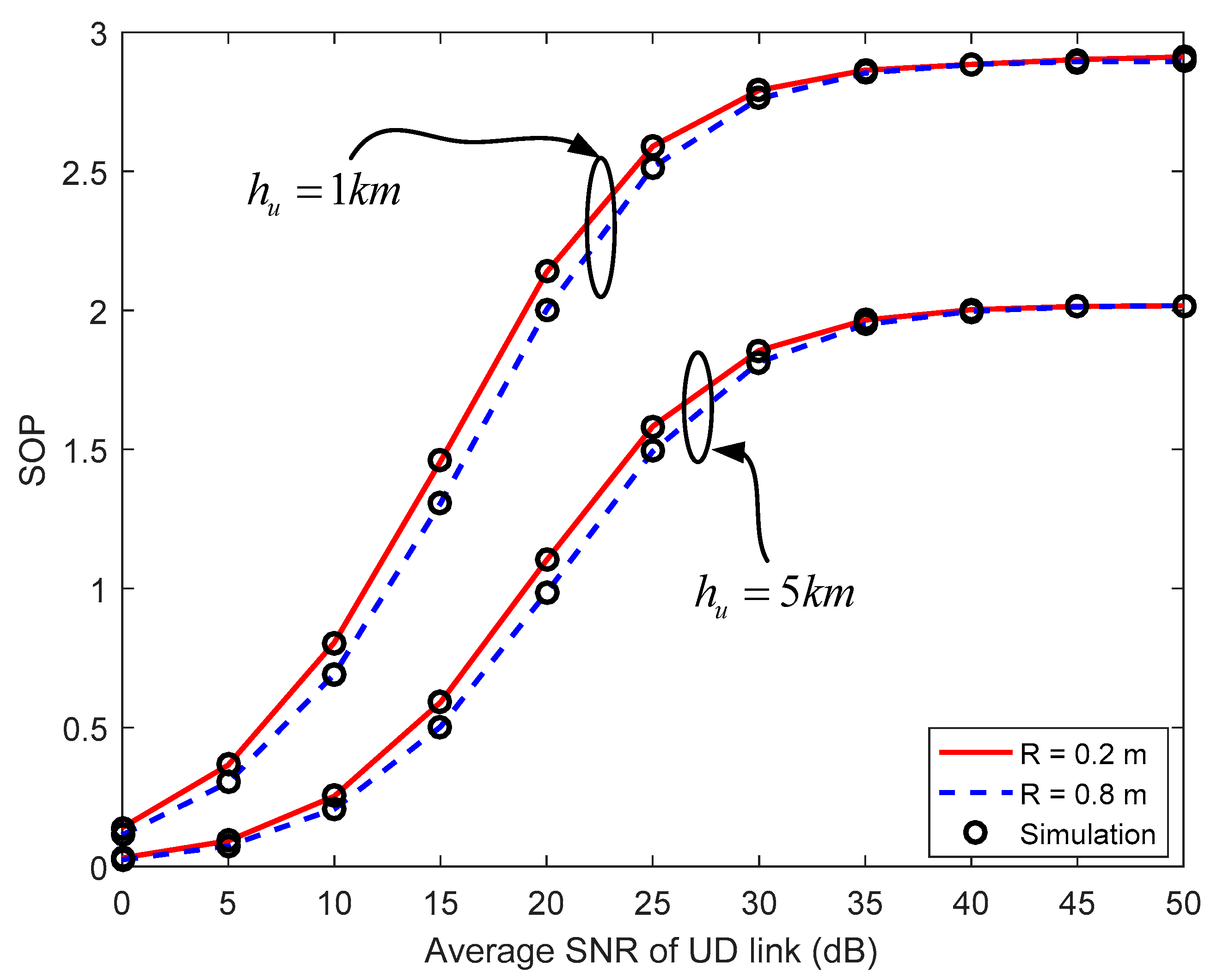
4.1. Secrecy Outage Probability (SOP)
4.2. Strictly Positive Secrecy Capacity (SPSC)
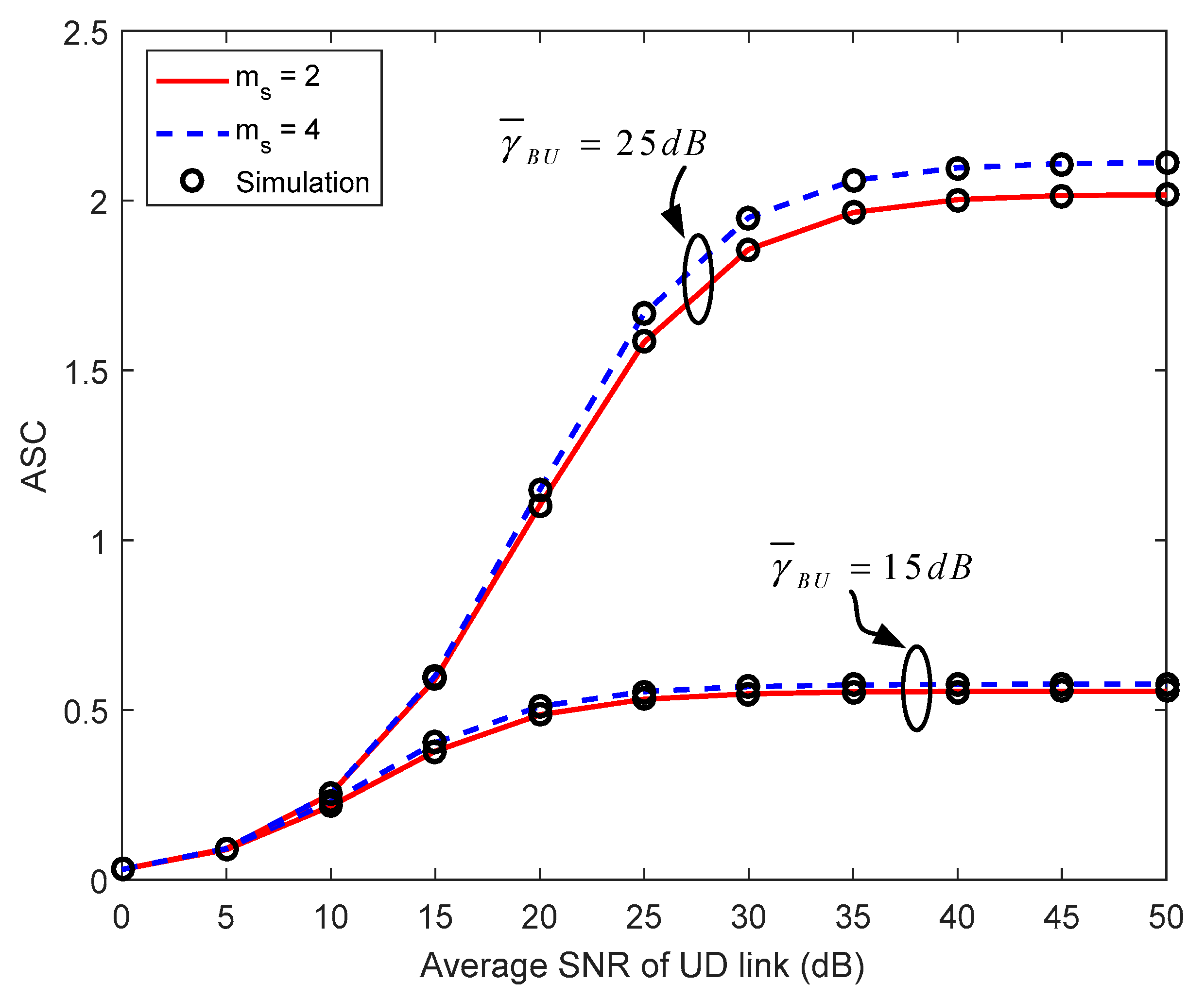
4.3. Average Secrecy Capacity
5. Numerical Results and Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Odeyemi, K.O.; Owolawi, P.A. A Mixed FSO/RF Integrated Satellite-High Altitude Platform Relaying Networks for Multiple Terrestrial Users with Presence of Eavesdropper: A Secrecy Performance. Photonics 2022, 9, 32. [Google Scholar] [CrossRef]
- Dan, Z.; Wu, X.; Zhu, S.; Zhuang, T.; Wang, J.-Y. On the outage performance of dual-hop UAV relaying with multiple sources. In Proceedings of the 2019 Cross Strait Quad-Regional Radio Science and Wireless Technology Conference (CSQRWC), Taiyuan, China, 18–21 July2019; pp. 1–3. [Google Scholar]
- Dang-Ngoc, H.; Nguyen, D.N.; Ho-Van, K.; Hoang, D.T.; Dutkiewicz, E.; Pham, Q.-V.; Hwang, W.-J. Secure Swarm UAV-assisted Communications with Cooperative Friendly Jamming. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Bao, T.; Yang, H.-C.; Hasna, M.O. Secrecy Performance Analysis of UAV-Assisted Relaying Communication Systems. IEEE Trans. Veh. Technol. 2019, 69, 1122–1126. [Google Scholar] [CrossRef]
- Qin, Y.; Kishk, M.A.; Alouini, M.-S. Stochastic Geometry-based Analysis of Multi-Purpose UAVs for Package and Data Delivery. arXiv 2022, arXiv:2209.05173. [Google Scholar]
- Hou, T.; Liu, Y.; Song, Z.; Sun, X.; Chen, Y. Multiple Antenna Aided NOMA in UAV Networks: A Stochastic Geometry Approach. IEEE Trans. Commun. 2018, 67, 1031–1044. [Google Scholar] [CrossRef] [Green Version]
- Odeyemi, K.O.; Owolawi, P.A. Physical layer security in mixed Rf/FSO system under multiple eavesdroppers collusion and non-collusion. Opt. Quantum Electron. 2018, 50, 298. [Google Scholar] [CrossRef]
- Yu, C.; Ko, H.-L.; Peng, X.; Xie, W. Secrecy Outage Performance Analysis for Cooperative NOMA Over Nakagami-m Channel. IEEE Access 2019, 7, 79866–79876. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Sun, Y.; Ng, D.W.K.; Schober, R. Robust and Secure Wireless Communications via Intelligent Reflecting Surfaces. IEEE J. Sel. Areas Commun. 2020, 38, 2637–2652. [Google Scholar] [CrossRef]
- Yang, L.; Chen, J.; Hasna, M.O.; Yang, H.-C. Outage Performance of UAV-Assisted Relaying Systems with RF Energy Harvesting. IEEE Commun. Lett. 2018, 22, 2471–2474. [Google Scholar] [CrossRef]
- Ji, B.; Li, Y.; Zhou, B.; Li, C.; Song, K.; Wen, H. Performance Analysis of UAV Relay Assisted IoT Communication Network Enhanced with Energy Harvesting. IEEE Access 2019, 7, 38738–38747. [Google Scholar] [CrossRef]
- Alkama, D.; Ouamri, M.A.; Alzaidi, M.S.; Shaw, R.N.; Azni, M.; Ghoneim, S.S.M. Downlink Performance Analysis in MIMO UAV-Cellular Communication With LOS/NLOS Propagation Under 3D Beamforming. IEEE Access 2022, 10, 6650–6659. [Google Scholar] [CrossRef]
- Ouamri, M.A.; Alkanhel, R.; Gueguen, C.; Alohali, M.A.; Ghoneim, S.S.M. Modeling and Analysis of UAV-Assisted Mobile Network with Imperfect Beam Alignment. Comput. Mater. Contin. 2022, 74, 453–467. [Google Scholar] [CrossRef]
- Yang, L.; Meng, F.; Zhang, J.; Hasna, M.O.; Di Renzo, M. On the Performance of RIS-Assisted Dual-Hop UAV Communication Systems. IEEE Trans. Veh. Technol. 2020, 69, 10385–10390. [Google Scholar] [CrossRef]
- Alnagar, S.I.; Salhab, A.M.; Zummo, S.A. Unmanned Aerial Vehicle Relay System: Performance Evaluation and 3D Location Optimization. IEEE Access 2020, 8, 67635–67645. [Google Scholar] [CrossRef]
- Li, X.; Wang, Q.; Peng, H.; Zhang, H.; Do, D.-T.; Rabie, K.M.; Kharel, R.; Cavalcante, C.C. A Unified Framework for HS-UAV NOMA Networks: Performance Analysis and Location Optimization. IEEE Access 2020, 8, 13329–13340. [Google Scholar] [CrossRef]
- Zan, J.; Lu, G.; Ye, Y. Outage performance of UAV-assisted AF relaying with hardware impairments. Phys. Commun. 2021, 46, 101334. [Google Scholar] [CrossRef]
- Kim, Y.H.; Chowdhury, I.A.; Song, I. Design and Analysis of UAV-Assisted Relaying with Simultaneous Wireless Information and Power Transfer. IEEE Access 2020, 8, 27874–27886. [Google Scholar] [CrossRef]
- Ajam, H.; Najafi, M.; Jamali, V.; Schober, R. Ergodic Sum Rate Analysis of UAV-Based Relay Networks with Mixed RF-FSO Channels. IEEE Open J. Commun. Soc. 2020, 1, 164–178. [Google Scholar] [CrossRef] [Green Version]
- Odeyemi, K.O.; Owolawi, P.A. Outage Performance of UAV-Based Relay in FSO Downlink Satellite Communication Networks Under Hovering Fluctuations. Int. J. Microw. Opt. Technol. 2022, 17, 303–310. [Google Scholar]
- Zhang, J.; Zheng, X.; Pan, G.; Xie, Y. On secrecy analysis of UAV-enabled relaying NOMA systems. Phys. Commun. 2020, 45, 101263. [Google Scholar] [CrossRef]
- Mamaghani, M.T.; Hong, Y. On the Performance of Low-Altitude UAV-Enabled Secure AF Relaying with Cooperative Jamming and SWIPT. IEEE Access 2019, 7, 153060–153073. [Google Scholar] [CrossRef]
- Li, A.; Wu, Q.; Zhang, R. UAV-Enabled Cooperative Jamming for Improving Secrecy of Ground Wiretap Channel. IEEE Wirel. Commun. Lett. 2018, 8, 181–184. [Google Scholar] [CrossRef]
- Li, S.; Yang, L.; da Costa, D.B.; Yu, S. Performance Analysis of UAV-Based Mixed RF-UWOC Transmission Systems. IEEE Trans. Commun. 2021, 69, 5559–5572. [Google Scholar] [CrossRef]
- Shimamoto, S. Channel characterization and performance evaluation of mobile communication employing stratospheric platforms. IEICE Trans. Commun. 2006, 89, 937–944. [Google Scholar]
- Li, X.; Zhao, M.; Gao, X.-C.; Li, L.; Do, D.-T.; Rabie, K.M.; Kharel, R. Physical Layer Security of Cooperative NOMA for IoT Networks Under I/Q Imbalance. IEEE Access 2020, 8, 51189–51199. [Google Scholar] [CrossRef]
- Wang, Q.; Li, X.; Bhatia, S.; Liu, Y.; Alex, L.T.; Khowaja, S.A.; Menon, V.G. UAV-enabled non-orthogonal multiple access networks for ground-air-ground communications. IEEE Trans. Green Commun. Netw. 2022, 6, 1340–1354. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Odeyemi, K.O.; Owolawi, P.A.; Olakanmi, A.O.O. On the performance of reconfigurable intelligent surface in cooperative decode-and-forward relaying for hybrid RF/FSO systems. Prog. Electromagn. Res. M 2022, 110, 157–169. [Google Scholar] [CrossRef]
- Sun, Q.; Zhang, Z.; Zhang, Y.; Lopez-Benitez, M.; Zhang, J. Performance Analysis of Dual-Hop Wireless Systems Over Mixed FSO/RF Fading Channel. IEEE Access 2021, 9, 85529–85542. [Google Scholar] [CrossRef]
- Lou, Y.; Sun, R.; Cheng, J.; Liu, S.; Zhou, F.; Qiao, G. Physical-layer security for two-hop air-to-underwater communication systems with fixed-gain amplify-and-forward relaying. arXiv 2020, arXiv:2009.09550. [Google Scholar]
- Odeyemi, K.O.; Owolawi, P.A.; Olakanmi, O.O. Secrecy performance of cognitive underlay hybrid RF/FSO system under pointing errors and link blockage impairments. Opt. Quantum Electron. 2020, 52, 1–16. [Google Scholar] [CrossRef]
- Adamchik, V.; Marichev, O. The algorithm for calculating integrals of hypergeometric type functions and its realization in REDUCE system. In Proceedings of the International Symposium on Symbolic and Algebraic Computation, Tokyo, Japan, 20–24 August 1990; pp. 212–224. [Google Scholar]
- Lei, H.; Zhang, H.; Ansari, I.S.; Gao, C.; Guo, Y.; Pan, G.; Qaraqe, K.A. Performance Analysis of Physical Layer Security Over Generalized-K Fading Channels Using a Mixture Gamma Distribution. IEEE Commun. Lett. 2015, 20, 408–411. [Google Scholar] [CrossRef]
- Lei, H.; Dai, Z.; Ansari, I.S.; Park, K.H.; Pan, G.; Alouini, M.-S. On Secrecy Performance of Mixed RF-FSO Systems. IEEE Photon. J. 2017, 9, 1–14. [Google Scholar] [CrossRef]
- Prudnikov, A.P.; Brychkov, Y.A.; Marichev, O.I.; Romer, R.H. (Eds.) Integrals and Series; American Association of Physics Teachers: College Park, MD, USA, 1988. [Google Scholar]
- Lei, H.; Gao, C.; Ansari, I.S.; Guo, Y.; Pan, G.; Qaraqe, K.A. On Physical-Layer Security Over SIMO Generalized- K Fading Channels. IEEE Trans. Veh. Technol. 2015, 65, 7780–7785. [Google Scholar] [CrossRef]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Odeyemi, K.O.; Owolawi, P.A.; Olakanmi, O.O. On Secrecy Performance of a Dual-Hop UAV-Assisted Relaying Network with Randomly Distributed Non-Colluding Eavesdroppers: A Stochastic Geometry Approach. Electronics 2022, 11, 3302. https://doi.org/10.3390/electronics11203302
Odeyemi KO, Owolawi PA, Olakanmi OO. On Secrecy Performance of a Dual-Hop UAV-Assisted Relaying Network with Randomly Distributed Non-Colluding Eavesdroppers: A Stochastic Geometry Approach. Electronics. 2022; 11(20):3302. https://doi.org/10.3390/electronics11203302
Chicago/Turabian StyleOdeyemi, Kehinde Oluwasesan, Pius Adewale Owolawi, and Oladayo Olufemi Olakanmi. 2022. "On Secrecy Performance of a Dual-Hop UAV-Assisted Relaying Network with Randomly Distributed Non-Colluding Eavesdroppers: A Stochastic Geometry Approach" Electronics 11, no. 20: 3302. https://doi.org/10.3390/electronics11203302





