Application of Improved Butterfly Optimization Algorithm Combined with Black Widow Optimization in Feature Selection of Network Intrusion Detection
Abstract
:1. Introduction
2. Basic Algorithms
2.1. Butterfly Optimization Algorithm (BOA)
2.2. Black Widow Optimization (BWO) Algorithm
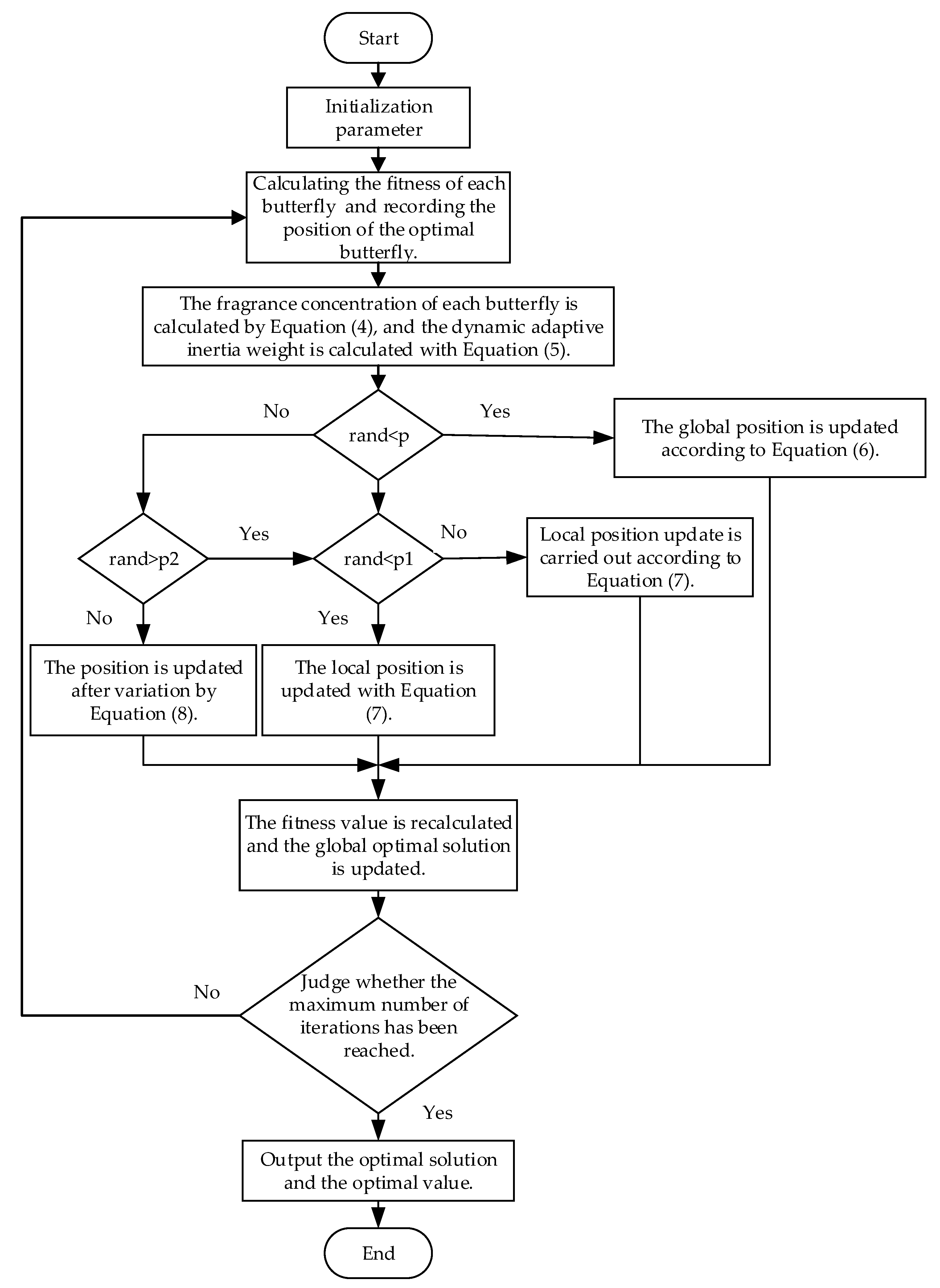
3. Proposed BWO-BOA Algorithm
3.1. Dynamic Adaptive Search Strategy
3.2. Black Widow Search Strategy
3.3. Pseudo-Code of BWO-BOA Algorithm
| Algorithm 1: BWO-BOA pseudocode. |
| Initialize population , iteration times , Dimension , upper and lower bounds and parameters. |
| 1: Calculate the fitness of each butterfly and record the optimal position. |
| 2: while (<) |
| 3: for < |
| 4: Calculate and , respectively, using Equations (4) and (5). |
| 5: if rand< |
| 6: Update the global position with Equation (6). |
| 7: else |
| 8: if rand< |
| 9: Update local position with Equation (7). |
| 10: else |
| 11: The position of the mutation is updated with Equation (8). |
| 12: end if |
| 13: end if |
| 14: end for |
| 15: end while |
| 16: Output the optimal value. |
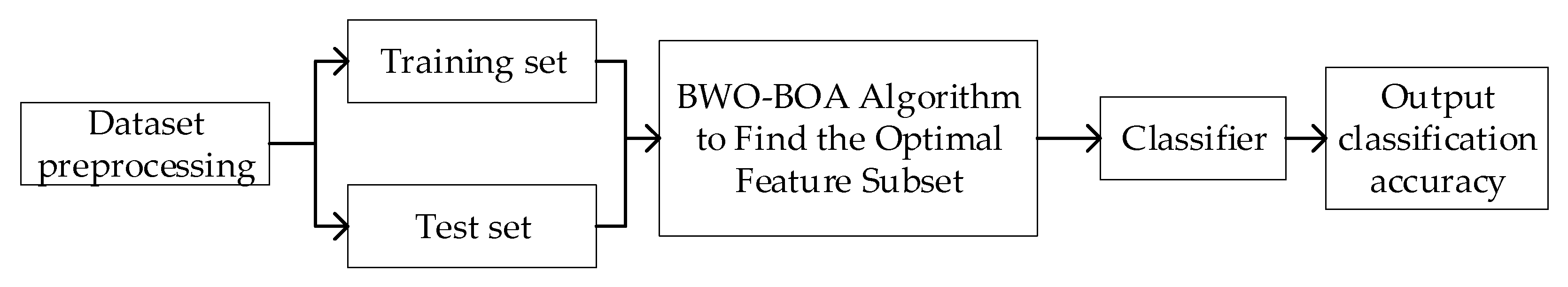
4. Feature Selection Model Based on BWO-BOA Algorithm for Network Intrusion Detection
4.1. Fitness Function
4.2. Evaluation Indicators
4.3. Proposed Feature Selection Model Based on BWO-BOA Algorithm
5. Experimental Results
5.1. Dataset
5.2. Comparative Analysis of Feature Selection Models with Different Improvements in BWO-BOA Algorithm
5.2.1. Comparative Analysis of Different Improvements in Binary Classification and Multi-classification
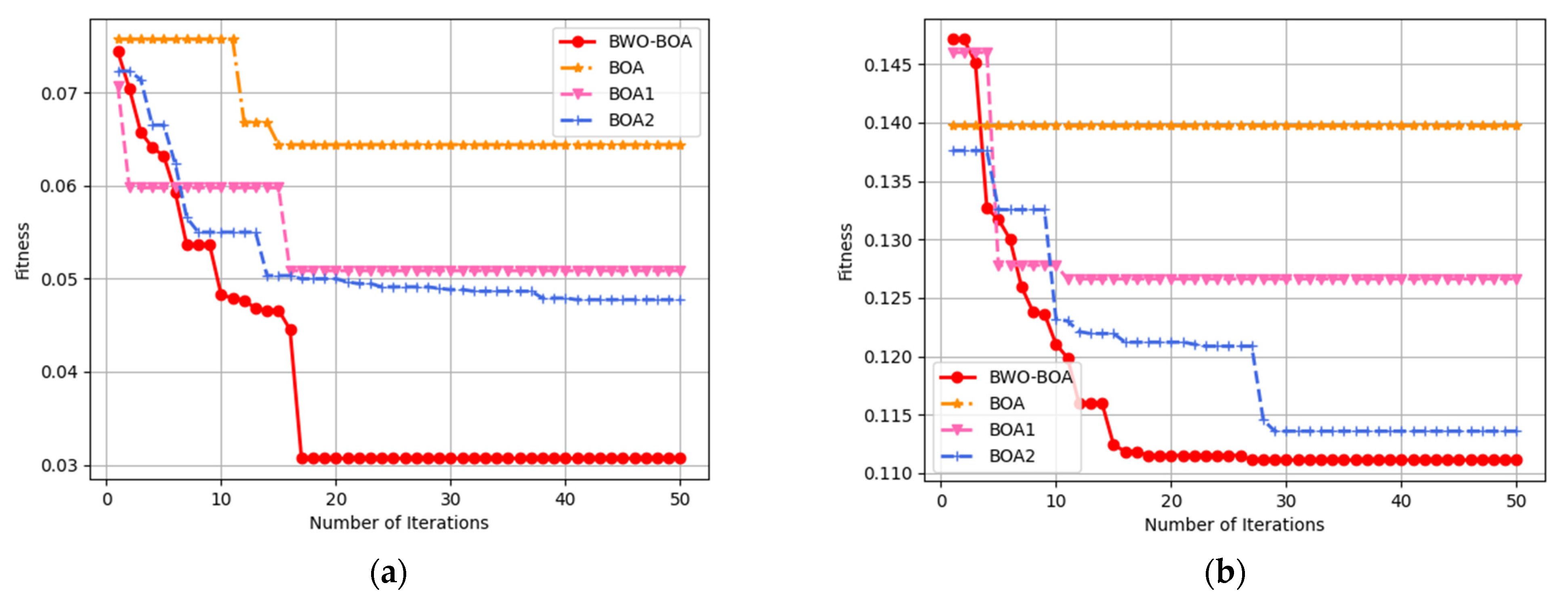
5.2.2. Comparison of Fitness for Different Strategies
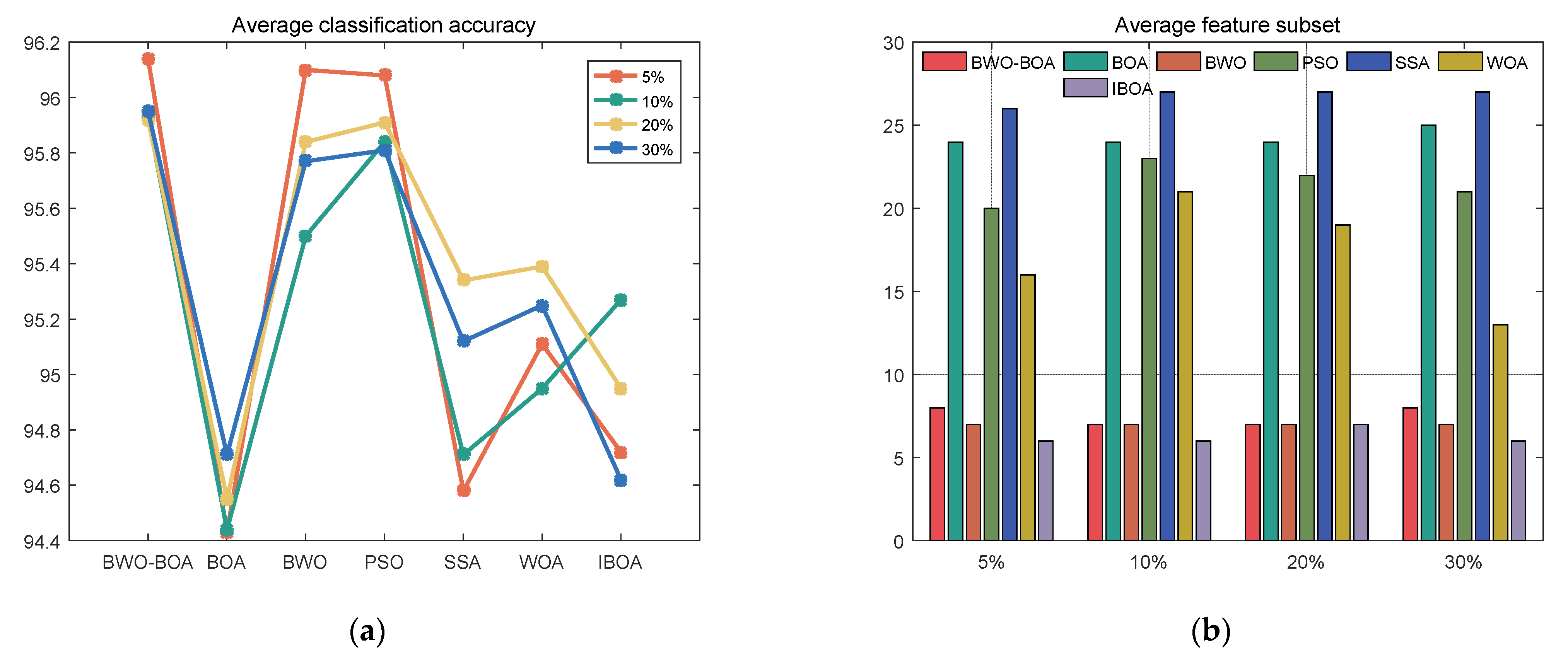
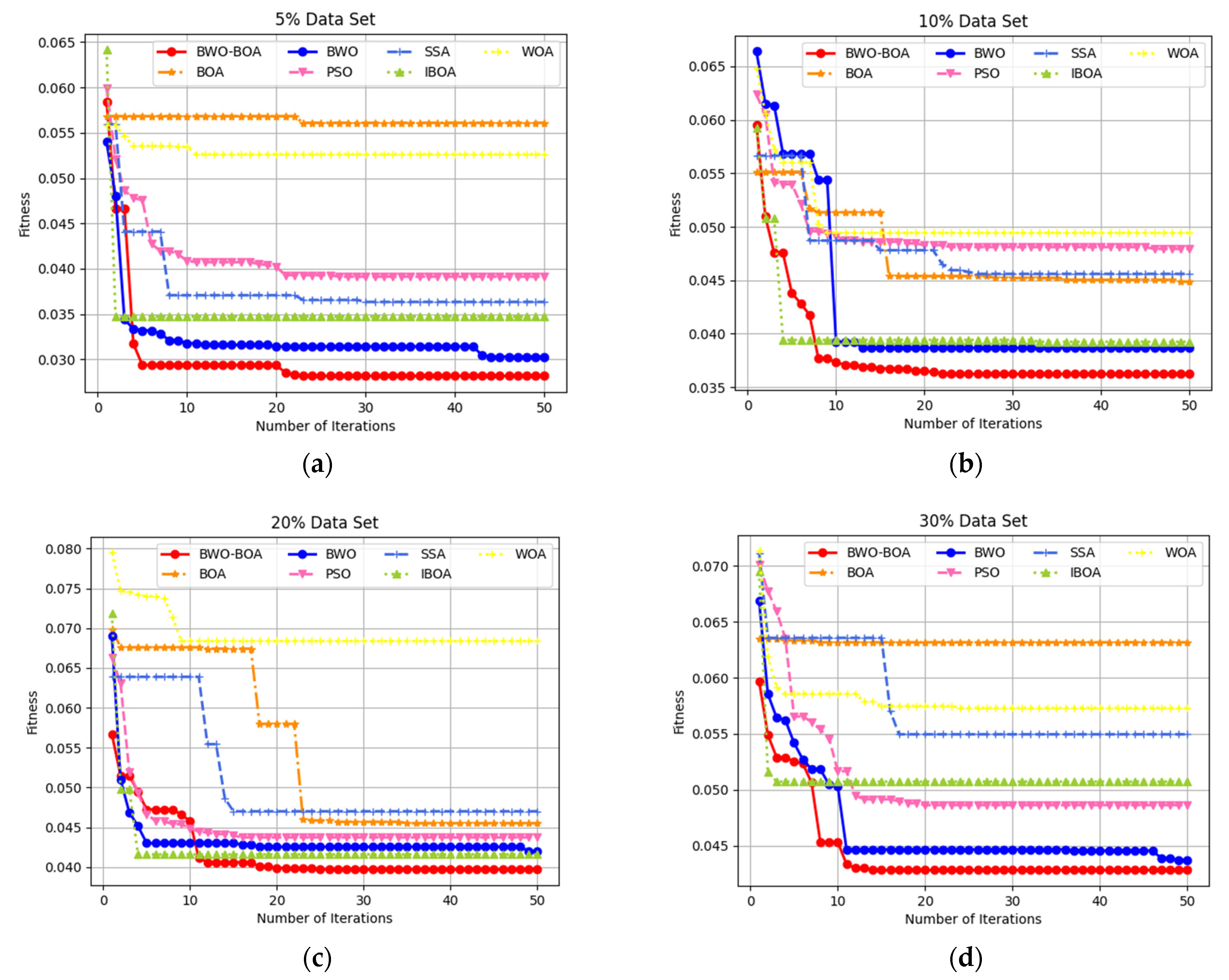
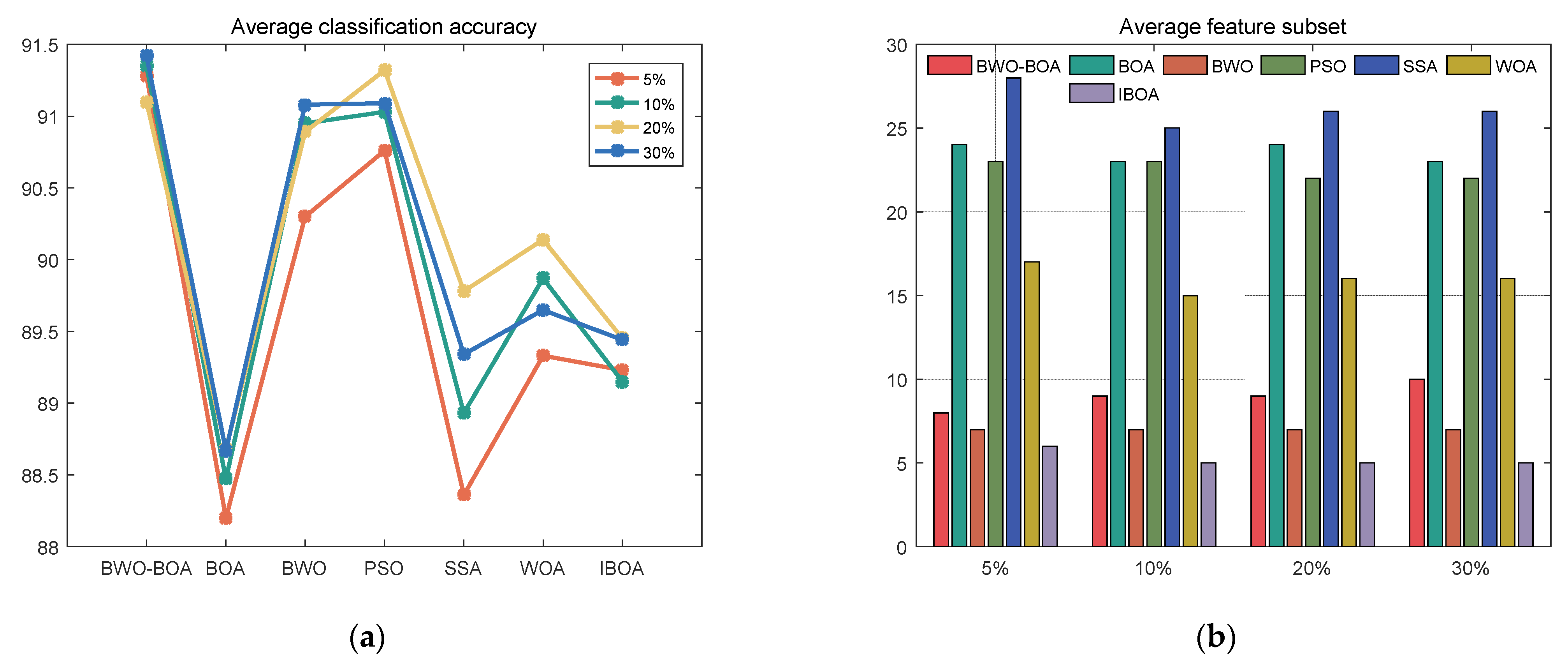
5.3. Comparative Experimental Results of Different Algorithms
5.3.1. Comparative Analysis of Binary Classification Results
5.3.2. Comparative Analysis of Multi-classification Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhou, Y.; Cheng, G.; Jiang, S.; Dai, M. Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput. Netw. 2020, 174, 107247. [Google Scholar] [CrossRef] [Green Version]
- Deng, M.; Wang, K.; Zhang, C.; Zhang, Y. A comparative study of network intrusion detection evaluation data sets. Mod. Comput. 2020, 20, 20–26. [Google Scholar]
- Alazzam, H.; Sharieh, A.; Sabri, K.E. A feature selection algorithm for intrusion detection system based on pigeon inspired optimizer. Expert Syst. Appl. 2020, 148, 0957–4174. [Google Scholar] [CrossRef]
- Alshamy, R.; Ghurab, M. A review of big data in network intrusion detection system: Challenges, approaches, datasets, and tools. Int. J. Comput. Sci. Eng. 2020, 8, 62–74. [Google Scholar]
- Zarei, M.; Rezai, A.; Hamidpour, S.S.F. Breast cancer segmentation based on modified gaussian mean shift algorithm for infrared thermal images. Comput. Methods Biomech. Biomed. Eng. Imaging Vis. 2021, 9, 574–580. [Google Scholar] [CrossRef]
- Darabi, N.; Rezai, A.; Hamidpour, S.S.F. Breast cancer detection using RSFS-based feature selection algorithms in thermal images. Biomed. Eng. Appl. Basis Commun. 2021, 33, 2150020. [Google Scholar] [CrossRef]
- Salimian, M.; Rezai, A.; Hamidpour, S.; Khajeh-Khalili, F. Effective features in thermal images for breast cancer detection. In Proceedings of the 2nd National Conference on New Technologies in Electrical and Computer Engineering, Isfahan, Iran, 6 February 2019; pp. 1–7. [Google Scholar]
- Li, Y.; Qin, J. Application of a feature-selection method based on improved genetic algorithm in coronary heart disease detection. J. Huaihua Univ. 2021, 40, 57–62. [Google Scholar]
- Shi, Q.; Pan, F.; Long, F.; Li, N.; Gou, H.; Su, H.; Xie, Y. Summary of research on feature selection methods. Microelectron. Comput. 2022, 39, 1–8. [Google Scholar]
- Liang, B. A Review of the Application of swarm intelligence in network intrusion’s feature selection. Comput. Knowl. Technol. 2020, 16, 30–32. [Google Scholar]
- Tawil, A.A.; Sabri, K.E. A feature selection algorithm for intrusion detection system based on moth flame optimization. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordanm, 14–15 July 2021; pp. 377–381. [Google Scholar]
- Chen, T.; Dong, H. Industrial anomaly intrusion detection using ant colony algorithm and deep reinforcement learning. J. Chin. Comput. Syst. 2022, 43, 779–784. [Google Scholar]
- Syarif, I.; Afandi, R.F.; Saputra, F.A. Feature selection algorithm for intrusion detection using cuckoo search algorithm. In Proceedings of the 2020 International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2020; pp. 430–435. [Google Scholar]
- Mahboob, A.S.; Moghaddam, M.R.O. An anomaly-based intrusion detection system using butterfly optimization algorithm. In Proceedings of the 2020 6th Iranian Conference on Signal Processing and Intelligent Systems (ICSPIS), Mashhad, Iran, 23–24 December 2020; pp. 1–6. [Google Scholar]
- Tubishat, M.; Alswaitti, M.; Mirjalili, S.; Al-Garadi, M.A.; Rana, T.A. Dynamic butterfly optimization algorithm for feature selection. IEEE Access 2020, 8, 194303–194314. [Google Scholar] [CrossRef]
- Selvakumar, B.; Muneeswaran, K. Firefly algorithm based feature selection for network intrusion detection. Comput. Secur. 2019, 81, 148–155. [Google Scholar]
- Saheed, Y.K. A Binary Firefly Algorithm Based Feature Selection Method on High Dimensional Intrusion Detection Data; Springer: Cham, Switzerland, 2022; Volume 109, pp. 273–288. [Google Scholar]
- Almomani, O. A feature selection model for network intrusion detection system based on PSO, GWO, FFA and GA algorithms. Symmetry 2020, 12, 1046. [Google Scholar] [CrossRef]
- Al-Yaseen, W.L. Improving intrusion detection system by developing feature selection model based on firefly algorithm and support vector machine. Int. J. Comput. Sci. 2019, 46, 534–540. [Google Scholar]
- Li, X.; Yi, P.; Wei, W.; Tian, L. LNNLS-KH: A feature selection method for network intrusion detection. Secur. Commun. Netw. 2021, 3, 1–22. [Google Scholar] [CrossRef]
- Chen, H.; Ma, X.; Huang, S. A feature selection method for intrusion detection based on parallel sparrow search algorithm. In Proceedings of the 2021 16th International Conference on Computer Science & Education (ICCSE), Lancaster, UK, 17–21 August 2021; pp. 685–690. [Google Scholar]
- Yang, J.; Ye, Z.; Yan, L.; Wang, R. Modified naive bayes algorithm for network intrusion detection based on artificial bee colony algorithm. In Proceedings of the 2018 IEEE 4th International Symposium on Wireless Systems within the International Conferences on Intelligent Data Acquisition and Advanced Computing Systems (IDAACS-SWS) IEEE, Lviv, Ukraine, 20–21 September 2018; pp. 35–40. [Google Scholar]
- Alsaleh, A.; Binsaeedan, W. The influence of salp swarm algorithm-based feature selection on network anomaly intrusion detection. IEEE Access 2021, 9, 112466–112477. [Google Scholar] [CrossRef]
- Alzaqebah, A.; Aljarah, I.; Al-Kadi, O.; Damaševičius, R. A modified grey wolf optimization algorithm for an intrusion detection system. Mathematics 2022, 10, 999. [Google Scholar] [CrossRef]
- Xu, H.; Przystupa, K.; Fang, C.; Marciniak, A.; Kochan, O.; Beshley, M. A combination strategy of feature selection based on an integrated optimization algorithm and weighted k-nearest neighbor to improve the performance of network intrusion detection. Electronics 2020, 9, 1206. [Google Scholar]
- Li, J.; An, Q.; Lei, H.; Deng, Q.; Wang, G.-G. Survey of lévy flight-based metaheuristics for optimization. Mathematics 2022, 10, 2785. [Google Scholar] [CrossRef]
- Zhang, X.; Tan, H. Butterfly optimization algorithm with dynamic variance gaussian mutation. J. Yunnan Norm. Univ. (Nat. Sci. Ed.) 2022, 42, 31–36. [Google Scholar]
- Xu, H.; Lu, Y.; Ye, Z. Applying cooperative search strategies to improve butterfly optimization algorithm. In Proceedings of the 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hangzhou, China, 4–6 May 2022. [Google Scholar]
- Mojtahedi, A.; Sorouri, F.; Souha, A.N.; Molazadeh, A.; Mehr, S.S. Feature selection-based intrusion detection system using genetic whale optimization algorithm and sample-based classification. arXiv 2022, arXiv:2201.00584. [Google Scholar]
- Yuan, Q.; Lu, L. Network intrusion detection method based on combination of improved ant colony optimization and genetic algorithm. J. Chongqing Univ. Posts Telecommun. (Nat. Sci. Ed.) 2017, 29, 84–89. [Google Scholar]
- Xu, H.; Fu, Y.; Liu, X.; Fang, C.; Su, J. Applying improved grey wolf optimizer algorithm integrated with cuckoo search to feature selection for network intrusion detection. Adv. Eng. Sci. 2018, 50, 160–166. [Google Scholar]
- Kang, Y.; Wang, H.; Tao, L.; Yang, H.; Yang, X.; Wang, F.; Li, H. Hybrid improved flower pollination algorithm and gray wolf algorithm for feature selection. Comput. Sci. 2022, 49, 125–132. [Google Scholar]
- Arora, S.; Singh, S. Butterfly optimization algorithm: A novel approach for global optimization. Soft Comput. 2019, 23, 715–734. [Google Scholar] [CrossRef]
- Peña-Delgado, A.F.; Peraza-Vázquez, H.; Almazán-Covarrubias, J.H.; Cruz, N.T.; García-Vite, P.M.; Morales-Cepeda, A.B.; Ramirez-Arredondo, J.M. A novel bio-inspired algorithm applied to selective harmonic elimination in a three-phase eleven-level inverter. Math. Probl. Eng. 2020, 2020. [Google Scholar] [CrossRef]
- Chen, J.; He, Q. Improved butterfly optimization algorithm based on cosine similarity. J. Comput. Appl. 2021, 41, 2668–2677. [Google Scholar]
- Gao, W.; Liu, S.; Xiao, Z.; Yu, J. Butterfly optimization algorithm based on convergence factor and gold sinusoidal guidance mechanism. Comput. Eng. Des. 2020, 41, 3384–3389. [Google Scholar]
- Zheng, H.; Feng, W.; Zhou, Y. Butterfly optimization algorithm based on sine cosine algorithm. Guangxi Sci. 2021, 28, 152–159. [Google Scholar]
- Liu, J.; Ma, Y.; Li, Y. Improved butterfly algorithm for multi-dimensional complex function optimization problem. Acta Electron. Sin. 2021, 49, 1068–1076. [Google Scholar]
- Shao, L.; Han, R. Beetle antenna search flower pollination algorithm. Comput. Eng. Appl. 2018, 54, 188–194. [Google Scholar]
- Moustafa, N.; Slay, J. Proceedings of the UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems (UNSW-NB15 Network DataSet), 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; pp. 1–6.
- Moustafa, N.; Slay, J. The evaluation of network anomaly detection systems: Statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inf. Syst. Secur. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Al-Daweri, M.S.; Ariffin, K.; Abdullah, S.; Senan, M. An analysis of the KDD99 and UNSW-NB15 datasets for the intrusion detection system. Symmetry 2020, 12, 1666. [Google Scholar] [CrossRef]
- Kennedy, J.; Eberhart, R. Particle swarm optimization. In Proceedings of the ICNN’95-International Conference on Neural Networks, Perth, WA, Australia, 27 November–1 December 1995; pp. 1942–1948. [Google Scholar]
- Mirjalili, S.; Gandomi, A.H.; Mirjalili, S.Z.; Saremi, S.; Faris, H.; Mirjalili, M.S. Salp swarm algorithm: A bio-inspired optimizer for engineering design problems. Adv. Eng. Softw. 2017, 114, 163–191. [Google Scholar] [CrossRef]
- Mirjalili, S.; Lewis, A. The Whale optimization algorithm. Adv. Eng. Softw. 2006, 95, 51–67. [Google Scholar]
- Ren, J.; Zhang, Y.; Zhang, B.; Li, S. Classification method of industrial internet intrusion detection based on feature selection. J. Comput. Res. Dev. 2022, 59, 12. [Google Scholar]


| Algorithm | Parameter |
|---|---|
| BWO-BOA | = 0.3 |
| BOA | , , = 0.01 |
| BWO | , |
| PSO | = c2 = 3 |
| SSA | |
| WOA | , , |
| IBOA | , , = 0.5 |
| Type | Feature |
|---|---|
| Object | proto, service, state, attack_cat |
| Integer | spkts, dpkts, sbytes, dbytes, sttl, dttl, sload, dload, swin, stcpb, dtcpb, dwin, smean, dmean, trans_depth, response_body_len, ct_srv_src, ct_state_ttl, ct_src_dport_ltm, ct_dst_ltm, ct_ftp_cmd, ct_flw_http_mthd, ct_src_ltm, ct_dst_sport_ltm, ct_dst_src_ltm, ct_srv_dst |
| Float | dur, rate, sloss, dloss, sinpkt, dinpkt, sjit, djit, tcprtt, synack, ackdat |
| Binary | is_sm_ips_ports, is_ftp_login, label |
| Algorithm | |||||
|---|---|---|---|---|---|
| BWO-BOA | 96.28 | 97.15 | 93.57 | 95.15 | 8 |
| BOA | 94.49 | 95.69 | 90.56 | 92.68 | 24 |
| BOA1 | 94.37 | 95.74 | 90.22 | 92.50 | 23 |
| BOA2 | 96.23 | 96.90 | 93.67 | 95.10 | 23 |
| Algorithm | Indicator | Analysis | Backdoor | DoS | Exploits | Fuzzers | Generic | Normal | Reconnaissance | Worms |
|---|---|---|---|---|---|---|---|---|---|---|
| BWO-BOA | (%) | 0 | 5.00 | 32.40 | 76.34 | 44.76 | 99.88 | 97.13 | 45.40 | 10.71 |
| (%) | 0 | 10.00 | 18.30 | 91.14 | 63.25 | 98.33 | 88.27 | 38.13 | 10.71 | |
| (%) | 0 | 6.66 | 22.66 | 83.04 | 51.86 | 99.10 | 92.45 | 39.94 | 9.52 | |
| (%) | 91.20 | |||||||||
| 8 | ||||||||||
| BOA | (%) | 0 | 0 | 22.90 | 67.81 | 35.36 | 99.73 | 96.90 | 46.05 | 2.22 |
| (%) | 0 | 0 | 12.98 | 89.51 | 46.59 | 98.04 | 80.26 | 32.26 | 6.66 | |
| (%) | 0 | 0 | 15.69 | 76.98 | 39.20 | 98.88 | 87.73 | 35.74 | 3.33 | |
| (%) | 88.21 | |||||||||
| 23 | ||||||||||
| BOA1 | (%) | 0 | 0 | 29.03 | 67.91 | 35.88 | 99.78 | 97.48 | 36.35 | 4.44 |
| (%) | 0 | 0 | 13.67 | 90.73 | 51.39 | 98.13 | 79.44 | 28.30 | 6.66 | |
| (%) | 0 | 0 | 17.41 | 77.55 | 41.44 | 98.94 | 87.47 | 29.33 | 5.33 | |
| (%) | 88.26 | |||||||||
| 28 | ||||||||||
| BOA2 | (%) | 0 | 5.55 | 32.18 | 75.36 | 44.52 | 99.83 | 97.36 | 47.51 | 9.33 |
| (%) | 0 | 11.11 | 17.62 | 91.16 | 62.77 | 98.25 | 87.14 | 41.62 | 10.00 | |
| (%) | 0 | 7.40 | 21.96 | 82.46 | 51.46 | 99.03 | 91.94 | 42.56 | 8.84 | |
| (%) | 91.01 | |||||||||
| 28 | ||||||||||
| Algorithm | |||||
|---|---|---|---|---|---|
| BWO-BOA | 96.14 | 96.88 | 93.49 | 94.98 | 8 |
| BOA | 94.43 | 95.64 | 90.14 | 92.41 | 24 |
| BWO | 96.10 | 96.71 | 93.52 | 94.94 | 7 |
| PSO | 96.08 | 96.76 | 93.24 | 94.79 | 20 |
| SSA | 94.58 | 95.72 | 90.46 | 92.66 | 26 |
| WOA | 95.11 | 96.09 | 91.43 | 93.41 | 16 |
| IBOA | 94.72 | 95.45 | 91.36 | 93.08 | 6 |
| Algorithm | |||||
|---|---|---|---|---|---|
| BWO-BOA | 95.93 | 96.85 | 92.96 | 94.66 | 7 |
| BOA | 94.44 | 95.75 | 90.30 | 92.57 | 24 |
| BWO | 95.90 | 96.76 | 92.96 | 94.64 | 7 |
| PSO | 95.84 | 96.66 | 92.88 | 94.54 | 23 |
| SSA | 94.71 | 95.86 | 90.87 | 92.96 | 27 |
| WOA | 94.95 | 95.88 | 91.44 | 93.32 | 21 |
| IBOA | 95.27 | 96.06 | 92.12 | 93.80 | 6 |
| Algorithm | |||||
|---|---|---|---|---|---|
| BWO-BOA | 95.92 | 96.66 | 93.09 | 94.66 | 7 |
| BOA | 94.55 | 95.78 | 90.61 | 92.75 | 24 |
| BWO | 95.84 | 96.55 | 93.01 | 94.57 | 7 |
| PSO | 95.91 | 96.51 | 93.23 | 94.68 | 22 |
| SSA | 95.34 | 96.22 | 92.10 | 93.88 | 27 |
| WOA | 95.39 | 96.19 | 92.25 | 93.96 | 19 |
| IBOA | 94.95 | 95.94 | 91.41 | 93.31 | 7 |
| Algorithm | |||||
|---|---|---|---|---|---|
| BWO-BOA | 95.95 | 96.64 | 93.15 | 94.69 | 8 |
| BOA | 94.71 | 95.88 | 90.86 | 92.97 | 25 |
| BWO | 95.77 | 96.40 | 92.92 | 94.46 | 7 |
| PSO | 95.81 | 96.68 | 92.80 | 94.50 | 21 |
| SSA | 95.12 | 96.28 | 91.51 | 93.55 | 27 |
| WOA | 95.25 | 96.31 | 91.79 | 93.74 | 13 |
| IBOA | 94.62 | 95.66 | 90.86 | 92.89 | 6 |
| Algorithm | Indicator | Analysis | Backdoor | DoS | Exploits | Fuzzers | Generic | Normal | Reconnaissance | Worms |
|---|---|---|---|---|---|---|---|---|---|---|
| BWO-BOA | (%) | 0 | 0 | 27.64 | 74.79 | 46.50 | 99.84 | 97.89 | 43.23 | 23.14 |
| (%) | 0 | 0 | 17.67 | 91.29 | 61.22 | 98.33 | 87.59 | 42.26 | 22.22 | |
| (%) | 0 | 0 | 20.99 | 82.12 | 51.61 | 99.07 | 92.41 | 41.26 | 22.03 | |
| (%) | 91.28 | |||||||||
| n | 8 | |||||||||
| BOA | (%) | 0 | 0 | 23.51 | 66.23 | 40.38 | 99.72 | 97.16 | 34.27 | 12.50 |
| (%) | 0 | 0 | 14.94 | 90.04 | 50.63 | 98.19 | 78.76 | 27.80 | 20.83 | |
| (%) | 0 | 0 | 17.23 | 76.13 | 43.31 | 98.95 | 86.88 | 28.64 | 15.55 | |
| (%) | 88.20 | |||||||||
| 24 | ||||||||||
| BWO | (%) | 0 | 0 | 30.63 | 73.49 | 47.10 | 99.71 | 97.48 | 44.41 | 8.33 |
| (%) | 0 | 0 | 13.54 | 90.86 | 66.32 | 98.08 | 85.42 | 41.89 | 4.62 | |
| (%) | 0 | 0 | 17.89 | 81.19 | 54.42 | 98.89 | 90.99 | 41.48 | 5.55 | |
| (%) | 90.30 | |||||||||
| 7 | ||||||||||
| PSO | (%) | 0 | 12.50 | 29.66 | 75.08 | 45.15 | 99.80 | 97.55 | 46.66 | 21.05 |
| (%) | 0 | 10.00 | 21.22 | 91.09 | 62.48 | 98.34 | 85.59 | 39.40 | 17.10 | |
| (%) | 0 | 10.00 | 24.25 | 82.23 | 51.63 | 99.07 | 91.11 | 41.54 | 17.89 | |
| (%) | 90.76 | |||||||||
| 23 | ||||||||||
| SSA | (%) | 0 | 1.92 | 29.81 | 65.17 | 42.30 | 95.80 | 97.76 | 38.03 | 16.66 |
| (%) | 0 | 3.84 | 16.62 | 81.21 | 62.70 | 94.77 | 78.65 | 31.38 | 11.11 | |
| (%) | 0 | 2.56 | 20.50 | 70.55 | 49.79 | 95.22 | 87.11 | 32.72 | 12.96 | |
| (%) | 88.36 | |||||||||
| 28 | ||||||||||
| WOA | (%) | 0 | 3.12 | 29.57 | 69.95 | 51.05 | 91.49 | 91.68 | 40.48 | 22.64 |
| (%) | 0 | 6.25 | 22.82 | 89.40 | 62.15 | 89.19 | 79.46 | 33.31 | 23.52 | |
| (%) | 0 | 4.16 | 24.92 | 77.94 | 54.50 | 89.99 | 84.82 | 35.05 | 22.54 | |
| (%) | 89.33 | |||||||||
| 17 | ||||||||||
| IBOA | (%) | 0 | 0 | 25.05 | 68.68 | 37.74 | 99.74 | 96.26 | 31.00 | 1.42 |
| (%) | 0 | 0 | 12.17 | 91.24 | 46.99 | 98.03 | 82.68 | 20.10 | 3.57 | |
| (%) | 0 | 0 | 15.61 | 78.21 | 39.29 | 98.88 | 88.85 | 21.99 | 2.04 | |
| (%) | 89.23 | |||||||||
| 6 | ||||||||||
| Algorithm | Indicator | Analysis | Backdoor | DoS | Exploits | Fuzzers | Generic | Normal | Reconnaissance | Worms |
|---|---|---|---|---|---|---|---|---|---|---|
| BWO-BOA | (%) | 0 | 6.14 | 32.07 | 76.39 | 46.78 | 99.84 | 97.71 | 59.24 | 35.96 |
| (%) | 0 | 7.89 | 19.19 | 91.52 | 65.74 | 98.43 | 86.70 | 50.36 | 32.42 | |
| (%) | 0 | 6.84 | 23.49 | 83.24 | 54.00 | 99.13 | 91.85 | 53.08 | 31.85 | |
| (%) | 91.35 | |||||||||
| 9 | ||||||||||
| BOA | (%) | 0 | 8.33 | 19.72 | 68.27 | 39.83 | 97.25 | 95.05 | 33.03 | 18.13 |
| (%) | 0 | 5.55 | 12.42 | 88.71 | 53.37 | 95.91 | 79.01 | 24.62 | 9.21 | |
| (%) | 0 | 6.48 | 14.20 | 76.89 | 45.00 | 96.57 | 86.19 | 27.43 | 11.84 | |
| (%) | 88.47 | |||||||||
| 23 | ||||||||||
| BWO | (%) | 0 | 0 | 35.50 | 75.93 | 44.25 | 99.82 | 97.13 | 49.11 | 28.38 |
| (%) | 0 | 0 | 20.22 | 91.03 | 58.89 | 98.37 | 86.46 | 43.56 | 18.09 | |
| (%) | 0 | 0 | 25.44 | 82.76 | 47.23 | 99.09 | 91.43 | 43.67 | 21.57 | |
| (%) | 90.95 | |||||||||
| 7 | ||||||||||
| PSO | (%) | 0 | 15.74 | 35.48 | 76.48 | 45.86 | 99.83 | 97.92 | 52.06 | 27.31 |
| (%) | 0 | 12.96 | 23.29 | 91.51 | 64.76 | 98.45 | 85.72 | 42.52 | 12.18 | |
| (%) | 0 | 13.70 | 27.53 | 83.28 | 53.38 | 99.13 | 91.38 | 45.97 | 15.67 | |
| (%) | 91.03 | |||||||||
| 23 | ||||||||||
| SSA | (%) | 0 | 9.72 | 29.18 | 69.92 | 40.39 | 99.82 | 97.45 | 41.81 | 15.88 |
| (%) | 0 | 8.33 | 15.33 | 90.25 | 60.10 | 98.30 | 80.78 | 33.14 | 9.36 | |
| (%) | 0 | 8.33 | 19.52 | 78.68 | 47.91 | 99.05 | 88.27 | 35.88 | 11.03 | |
| (%) | 88.93 | |||||||||
| 25 | ||||||||||
| WOA | (%) | 0 | 5.20 | 28.78 | 72.10 | 38.49 | 99.75 | 97.42 | 40.73 | 19.44 |
| (%) | 0 | 5.20 | 15.79 | 90.03 | 55.15 | 98.34 | 84.09 | 33.22 | 11.62 | |
| (%) | 0 | 5.20 | 19.15 | 79.99 | 44.62 | 99.04 | 90.16 | 35.99 | 13.24 | |
| (%) | 89.87 | |||||||||
| 15 | ||||||||||
| IBOA | (%) | 0 | 0 | 21.40 | 69.12 | 37.09 | 99.70 | 97.11 | 27.86 | 13.85 |
| (%) | 0 | 0 | 11.02 | 91.32 | 40.16 | 98.23 | 82.60 | 22.82 | 12.69 | |
| (%) | 0 | 0 | 13.67 | 78.48 | 36.27 | 98.96 | 89.23 | 22.42 | 11.52 | |
| (%) | 89.15 | |||||||||
| 5 | ||||||||||
| Algorithm | Indicator | Analysis | Backdoor | DoS | Exploits | Fuzzers | Generic | Normal | Reconnaissance | Worms |
|---|---|---|---|---|---|---|---|---|---|---|
| BWO-BOA | (%) | 0 | 8.47 | 37.64 | 75.56 | 46.23 | 99.87 | 97.49 | 48.61 | 33.01 |
| (%) | 0 | 9.33 | 21.73 | 91.65 | 66.22 | 98.37 | 86.22 | 40.62 | 29.94 | |
| (%) | 0 | 7.93 | 26.75 | 82.77 | 54.06 | 99.11 | 91.49 | 43.14 | 30.16 | |
| (%) | 91.10 | |||||||||
| 9 | ||||||||||
| BOA | (%) | 0 | 5.55 | 26.78 | 68.50 | 41.56 | 99.82 | 97.78 | 39.25 | 23.33 |
| (%) | 0 | 2.66 | 14.30 | 90.19 | 53.92 | 98.05 | 81.57 | 30.37 | 8.33 | |
| (%) | 0 | 3.21 | 17.73 | 77.74 | 45.82 | 98.93 | 88.91 | 32.67 | 11.43 | |
| (%) | 88.68 | |||||||||
| 24 | ||||||||||
| BWO | (%) | 0 | 8.33 | 34.85 | 75.55 | 43.60 | 99.83 | 97.48 | 40.46 | 25.43 |
| (%) | 0 | 5.41 | 20.66 | 92.01 | 62.66 | 98.37 | 86.07 | 34.38 | 26.80 | |
| (%) | 0 | 5.61 | 25.48 | 82.93 | 51.30 | 99.10 | 91.41 | 36.15 | 24.63 | |
| (%) | 90.89 | |||||||||
| 7 | ||||||||||
| PSO | (%) | 0 | 5.25 | 38.83 | 77.11 | 46.80 | 99.86 | 97.47 | 51.28 | 37.43 |
| (%) | 0 | 12.50 | 24.47 | 91.21 | 65.11 | 98.39 | 87.12 | 42.63 | 29.97 | |
| (%) | 0 | 7.30 | 29.66 | 83.55 | 54.13 | 99.12 | 91.98 | 45.71 | 31.57 | |
| (%) | 91.32 | |||||||||
| 22 | ||||||||||
| SSA | (%) | 0 | 9.76 | 34.69 | 72.22 | 41.32 | 99.78 | 97.52 | 46.11 | 36.72 |
| (%) | 0 | 12.08 | 19.04 | 90.02 | 58.87 | 98.22 | 83.73 | 29.98 | 20.94 | |
| (%) | 0 | 9.66 | 24.04 | 80.01 | 48.22 | 98.99 | 90.04 | 34.64 | 25.22 | |
| (%) | 89.78 | |||||||||
| 26 | ||||||||||
| WOA | (%) | 0 | 4.30 | 33.79 | 79.21 | 41.33 | 99.80 | 96.25 | 41.74 | 30.31 |
| (%) | 0 | 5.41 | 17.29 | 90.19 | 56.56 | 98.21 | 85.51 | 36.00 | 21.24 | |
| (%) | 0 | 4.16 | 21.68 | 80.54 | 46.57 | 99.00 | 90.40 | 37.76 | 22.84 | |
| (%) | 90.14 | |||||||||
| 16 | ||||||||||
| IBOA | (%) | 0 | 10.83 | 24.93 | 70.25 | 40.21 | 99.73 | 97.04 | 31.46 | 45.11 |
| (%) | 0 | 15.41 | 15.96 | 91.09 | 53.09 | 98.30 | 82.63 | 25.68 | 23.75 | |
| (%) | 0 | 12.20 | 19.20 | 79.24 | 45.10 | 99.01 | 89.23 | 27.26 | 27.56 | |
| (%) | 89.45 | |||||||||
| 5 | ||||||||||
| Algorithm | Indicator | Analysis | Backdoor | DoS | Exploits | Fuzzers | Generic | Normal | Reconnaissance | Worms |
|---|---|---|---|---|---|---|---|---|---|---|
| BWO-BOA | (%) | 0 | 8.33 | 40.22 | 77.69 | 46.93 | 99.85 | 97.55 | 52.06 | 47.28 |
| (%) | 0 | 13.42 | 25.58 | 91.13 | 69.03 | 98.61 | 85.79 | 45.18 | 40.10 | |
| (%) | 0 | 9.79 | 30.62 | 83.86 | 55.66 | 99.23 | 91.28 | 47.59 | 42.41 | |
| (%) | 91.42 | |||||||||
| 10 | ||||||||||
| BOA | (%) | 0 | 2.50 | 28.51 | 69.05 | 38.47 | 99.81 | 97.97 | 35.75 | 21.68 |
| (%) | 0 | 3.75 | 16.42 | 90.61 | 56.33 | 98.05 | 79.05 | 26.21 | 11.81 | |
| (%) | 0 | 2.91 | 20.24 | 78.24 | 45.42 | 98.92 | 87.43 | 29.75 | 14.12 | |
| (%) | 88.67 | |||||||||
| 23 | ||||||||||
| BWO | (%) | 0 | 3.08 | 35.08 | 75.60 | 45.79 | 99.84 | 96.74 | 39.66 | 34.31 |
| (%) | 0 | 4.16 | 21.22 | 91.56 | 60.94 | 98.40 | 86.70 | 34.83 | 27.26 | |
| (%) | 0 | 3.47 | 25.77 | 82.73 | 51.66 | 99.12 | 91.38 | 35.62 | 28.11 | |
| (%) | 91.08 | |||||||||
| 7 | ||||||||||
| PSO | (%) | 0 | 7.34 | 38.29 | 77.60 | 45.79 | 99.86 | 97.90 | 48.88 | 42.84 |
| (%) | 0 | 18.41 | 25.43 | 90.74 | 62.00 | 98.54 | 85.76 | 44.16 | 31.57 | |
| (%) | 0 | 9.85 | 30.31 | 83.61 | 52.20 | 99.20 | 91.42 | 45.79 | 34.51 | |
| (%) | 91.09 | |||||||||
| 22 | ||||||||||
| SSA | (%) | 0 | 4.55 | 27.80 | 72.12 | 40.85 | 99.84 | 96.86 | 39.93 | 35.19 |
| (%) | 0 | 3.91 | 18.30 | 89.54 | 57.79 | 98.43 | 82.05 | 32.29 | 14.85 | |
| (%) | 0 | 3.54 | 21.78 | 79.82 | 47.35 | 99.13 | 88.78 | 35.26 | 18.47 | |
| (%) | 89.34 | |||||||||
| 26 | ||||||||||
| WOA | (%) | 0 | 3.62 | 31.17 | 73.39 | 41.43 | 99.80 | 97.28 | 44.32 | 37.10 |
| (%) | 0 | 7.00 | 18.75 | 90.87 | 61.34 | 98.40 | 82.26 | 33.77 | 23.84 | |
| (%) | 0 | 4.05 | 23.17 | 81.11 | 49.35 | 99.09 | 89.09 | 36.08 | 26.73 | |
| (%) | 89.65 | |||||||||
| 16 | ||||||||||
| IBOA | (%) | 0 | 3.48 | 26.70 | 71.51 | 38.82 | 99.70 | 95.81 | 37.68 | 30.88 |
| (%) | 0 | 7.08 | 13.61 | 88.95 | 53.55 | 98.31 | 83.51 | 33.19 | 24.90 | |
| (%) | 0 | 4.17 | 17.10 | 79.16 | 44.27 | 99.00 | 89.07 | 34.33 | 26.06 | |
| (%) | 89.44 | |||||||||
| 5 | ||||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, H.; Lu, Y.; Guo, Q. Application of Improved Butterfly Optimization Algorithm Combined with Black Widow Optimization in Feature Selection of Network Intrusion Detection. Electronics 2022, 11, 3531. https://doi.org/10.3390/electronics11213531
Xu H, Lu Y, Guo Q. Application of Improved Butterfly Optimization Algorithm Combined with Black Widow Optimization in Feature Selection of Network Intrusion Detection. Electronics. 2022; 11(21):3531. https://doi.org/10.3390/electronics11213531
Chicago/Turabian StyleXu, Hui, Yanping Lu, and Qingqing Guo. 2022. "Application of Improved Butterfly Optimization Algorithm Combined with Black Widow Optimization in Feature Selection of Network Intrusion Detection" Electronics 11, no. 21: 3531. https://doi.org/10.3390/electronics11213531
APA StyleXu, H., Lu, Y., & Guo, Q. (2022). Application of Improved Butterfly Optimization Algorithm Combined with Black Widow Optimization in Feature Selection of Network Intrusion Detection. Electronics, 11(21), 3531. https://doi.org/10.3390/electronics11213531





