Resilient Consensus for Multi-Agent Systems in the Presence of Sybil Attacks
Abstract
:1. Introduction
2. Preliminaries
2.1. Graph Theory
- 1
- ;
- 2
- ;
- 3
- .
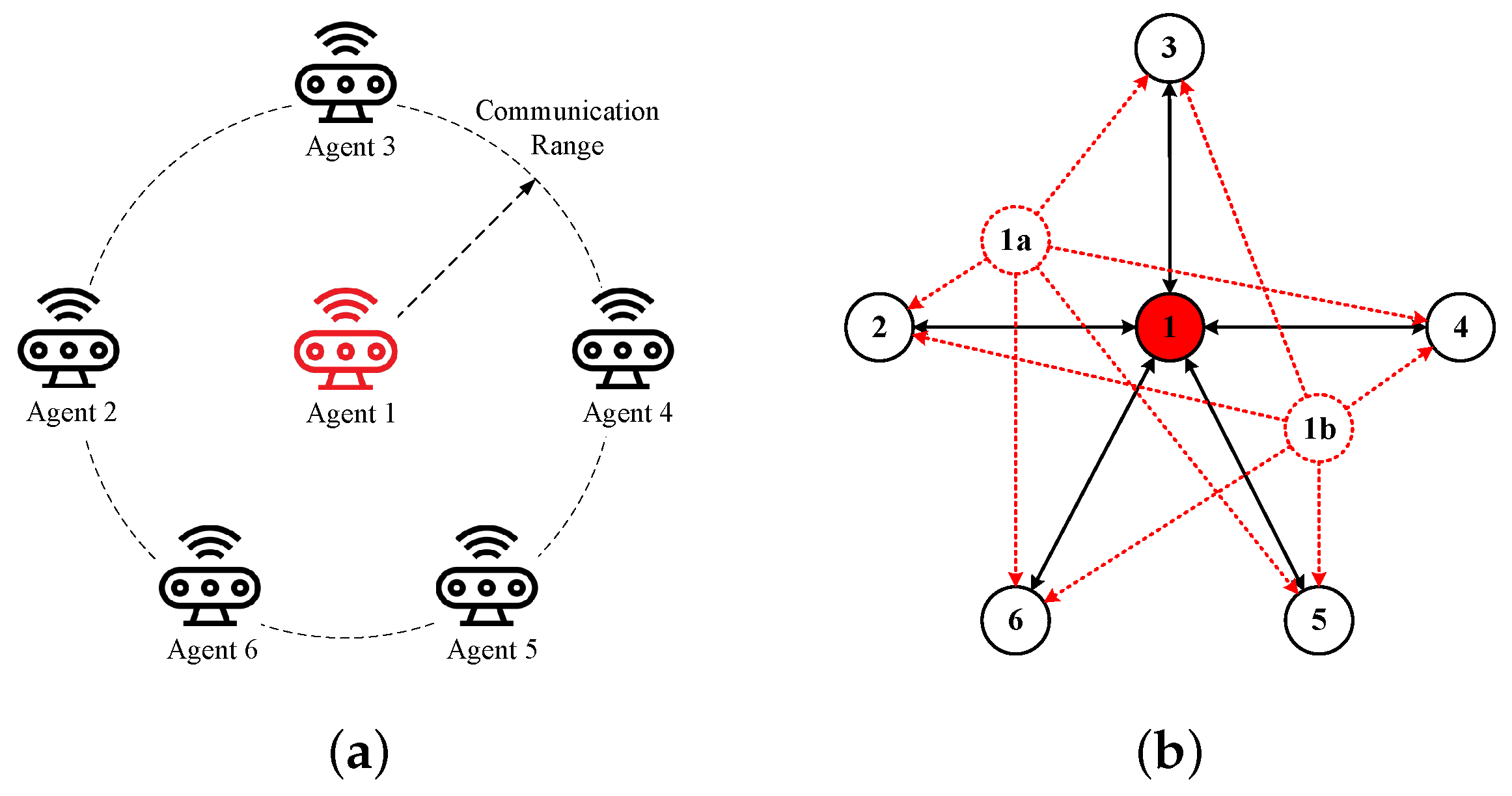
2.2. Sybil Attack Model
3. Node Verification Mechanism and Consensus Algorithm
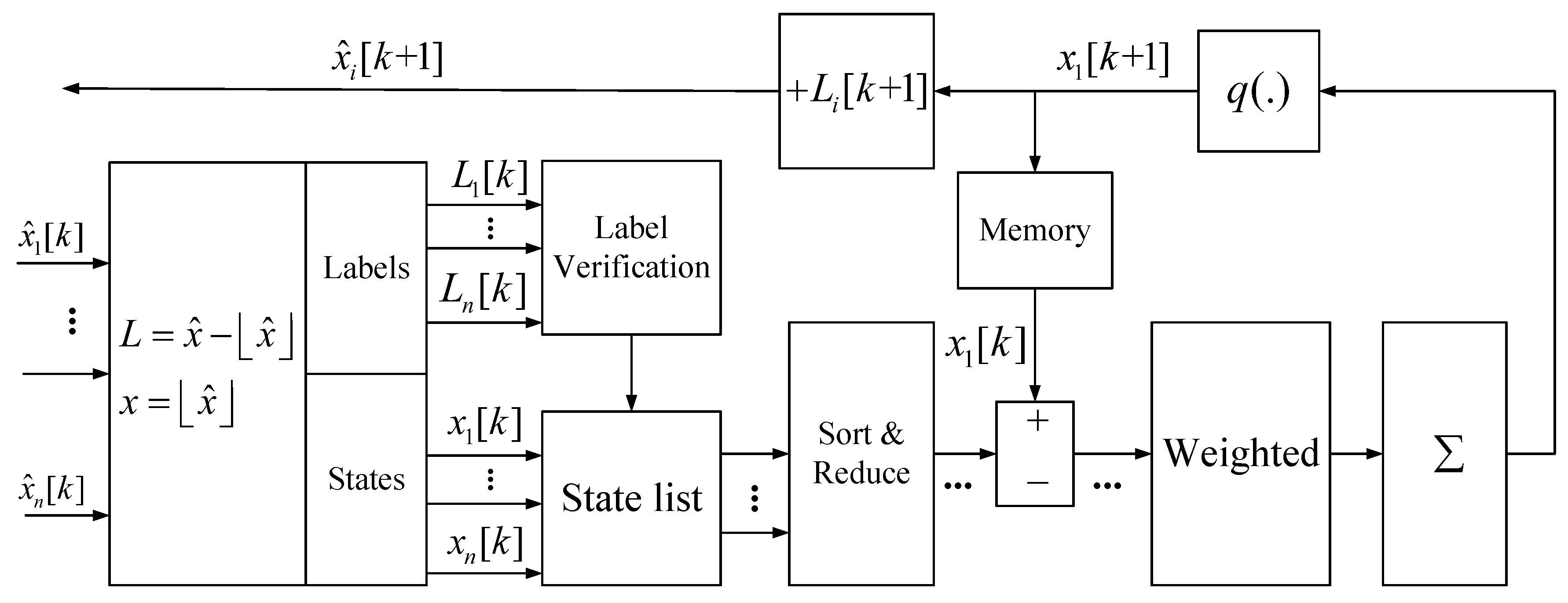
3.1. Information Processing and Verification Framework
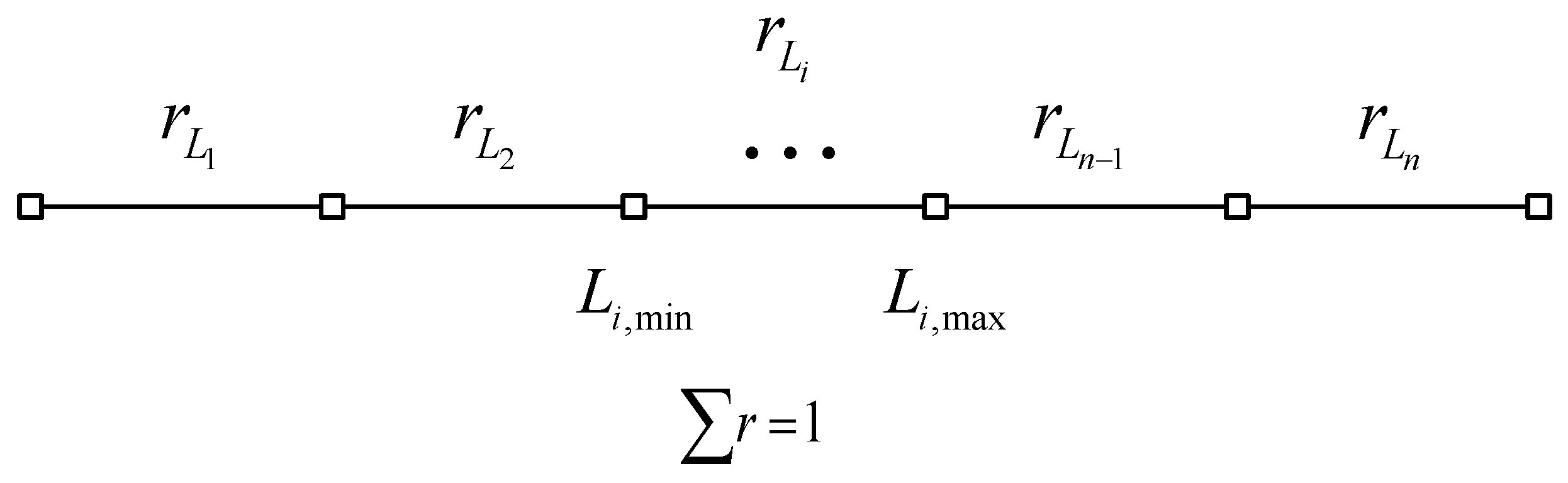
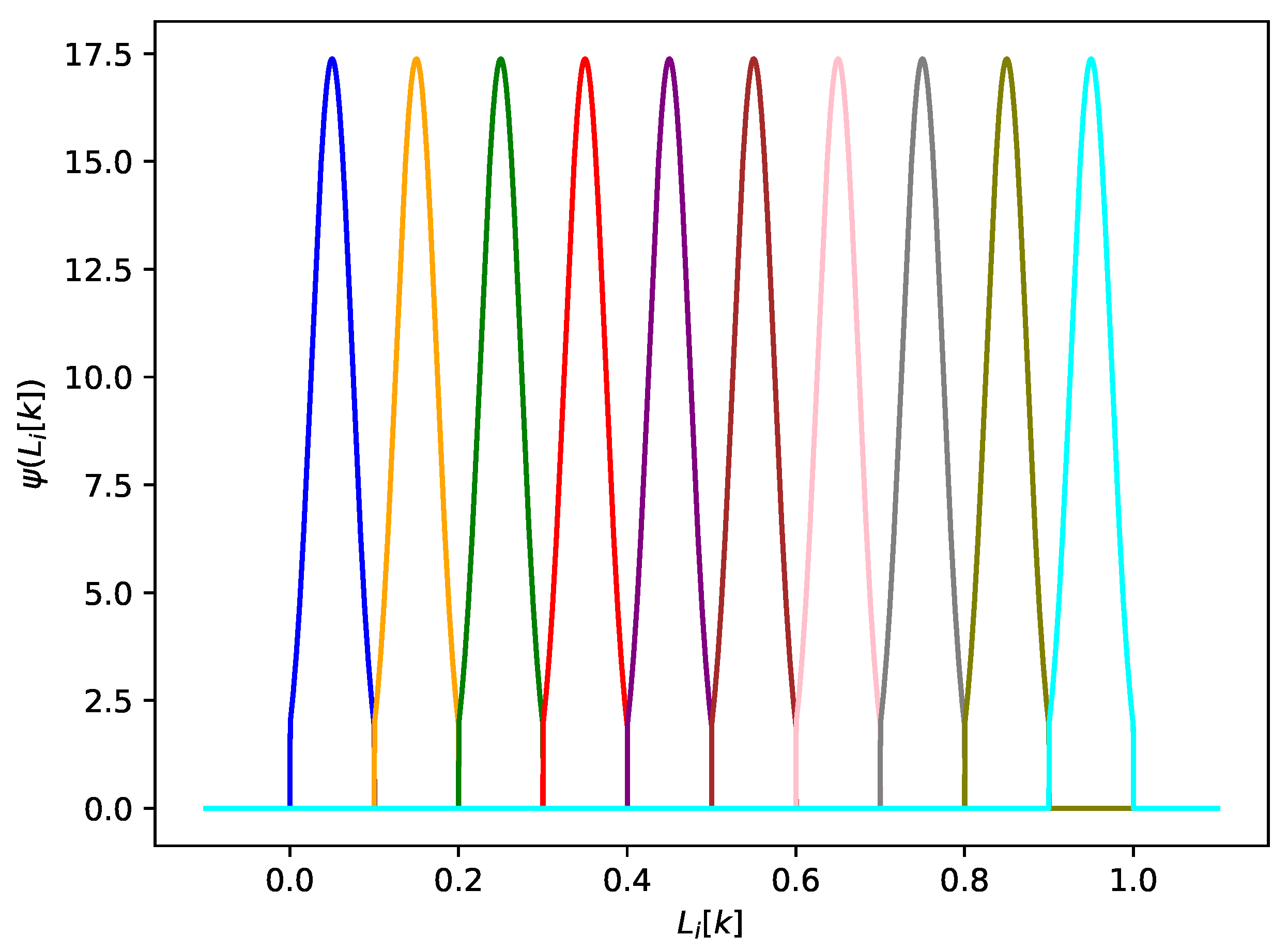
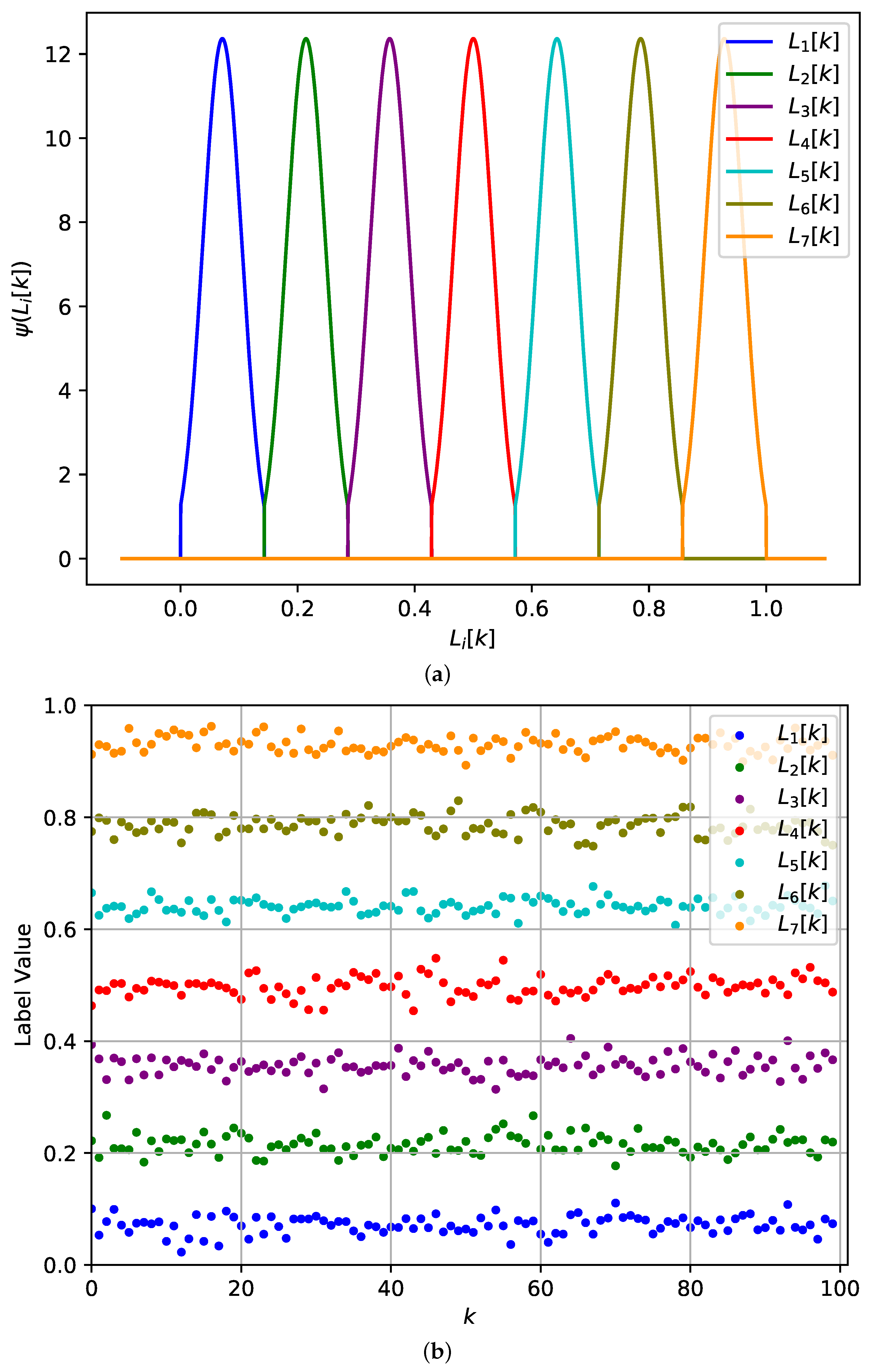
3.1.1. State Value Probabilistic Quantization
3.1.2. Verification Using Random Labels
- To avoid affecting the status value during the process of quantification, the label value shall be strictly less than one quantization step;
- To avoid different nodes generating the same label, the random label range of one agent shall be an open interval;
- To make labels time-sensitive, one node generates a random label at each time step.
- If , then .
- If , then.
- If , then.
3.2. Distributed Consensus Control Law Design
- 1
- Safety condition:For each set of quantized values of the normal agents, with the maximum value and minimum value of the initial state values of normal nodes, there exists a set such that for all normal agents , it holds that for .
- 2
- Agreement condition:There exists a finite time such that , where the consensus is defined as
Description of QWL-MSR Algorithm
| Algorithm 1 QWL-MSR |
Input: Output:
|
- Label Generation: At each time step k, each node (including Sybil nodes) calculates and generates an exclusive random label ;
- Message Exchange: Once node i updates its own state value, it will combine the message value with its newly generated status value and label value, i.e., . Then, it sends this message to its neighbors, and receives the message values from its neighbors .
- Label Verification: After step 2, node i executes the label stripping algorithm (8) to the message value of the nodes in the list, then puts the labels into list . If there are any nodes with the same label value in the list, node i groups these nodes into the Sybil neighbor set , but only reserves the first node with that label value. It sorts the remaining state values into a descending order list at the same time.
- State Filtration: If there are less than f nodes for which state values are strictly larger or smaller than in the list , node i groups these nodes into the Sybil neighbor set . Otherwise, it groups the f largest and f smallest values of the nodes in the list into the set .
- State Update: According to the set obtained by the above operation, node i applies the following update:
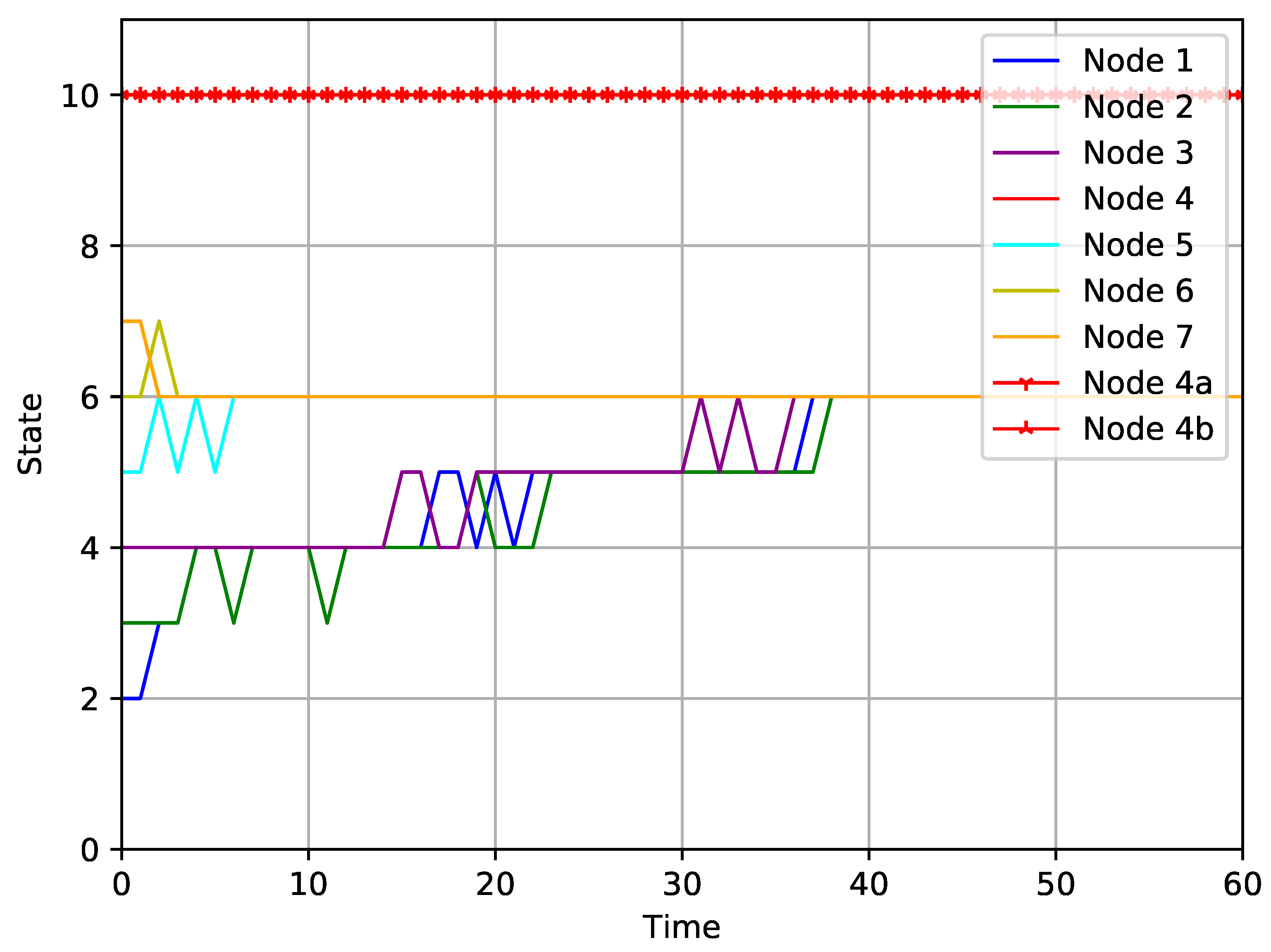
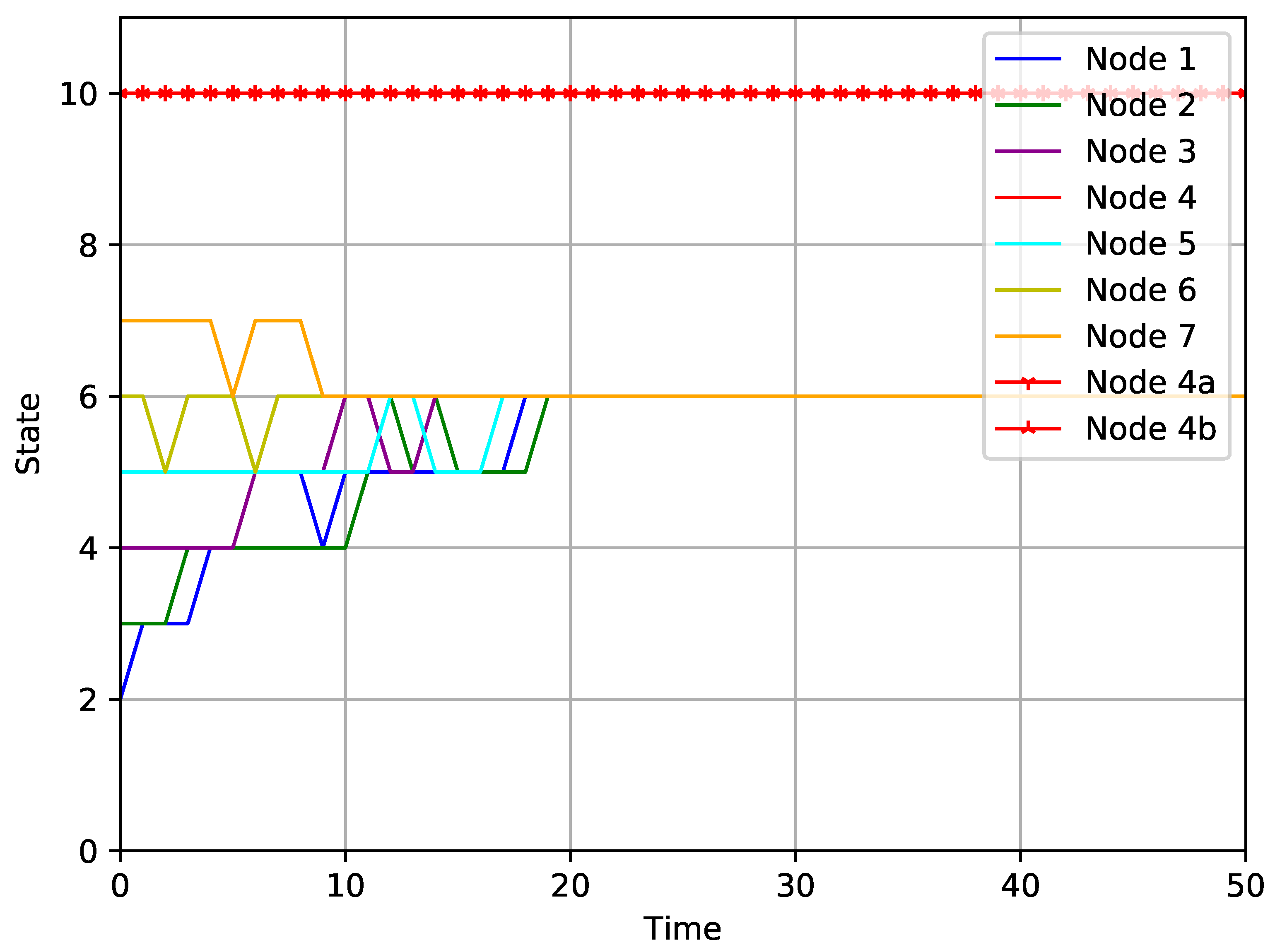
4. Main Results
- (1)
- C1. There is a finite state set for each normal node i, such that, for any , .
- (2)
- C2. There exists a finite time , such that, for state value , .
- (3)
- C3. If , then .
5. Numerical Simulation
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zheng, Y.; Ma, J.; Wang, L. Consensus of Hybrid Multi-Agent Systems. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 1359–1365. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Dong, X.; Hu, G. Time-Varying Output Formation for Linear Multiagent Systems via Dynamic Output Feedback Control. IEEE Trans. Control. Netw. Syst. 2017, 4, 236–245. [Google Scholar] [CrossRef]
- Meng, D.; Jia, Y.; Du, J. Finite-time consensus protocols for networks of dynamic agents by terminal iterative learning. Int. J. Syst. Sci. 2014, 45, 2435–2446. [Google Scholar] [CrossRef]
- LeBlanc, H.J.; Zhang, H.; Koutsoukos, X.; Sundaram, S. Resilient Asymptotic Consensus in Robust Networks. IEEE J. Sel. Areas Commun. 2013, 31, 766–781. [Google Scholar] [CrossRef] [Green Version]
- Zhang, D.; Feng, G. A New Switched System Approach to Leader–Follower Consensus of Heterogeneous Linear Multiagent Systems With DoS Attack. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 1258–1266. [Google Scholar] [CrossRef]
- He, W.; Mo, Z.; Han, Q.L.; Qian, F. Secure impulsive synchronization in Lipschitz-type multi-agent systems subject to deception attacks. IEEE/CAA J. Autom. Sin. 2020, 7, 1326–1334. [Google Scholar] [CrossRef]
- Shang, Y. Resilient Consensus for Robust Multiplex Networks with Asymmetric Confidence Intervals. IEEE Trans. Netw. Sci. Eng. 2021, 8, 65–74. [Google Scholar] [CrossRef]
- Vaidya, N.H.; Tseng, L.; Liang, G. Iterative approximate byzantine consensus in arbitrary directed graphs. In Proceedings of the 2012 ACM Symposium on Principles of Distributed Computing, Madeira, Portugal, 16–18 July 2012; pp. 365–374. [Google Scholar]
- Dibaji, S.M.; Ishii, H. Resilient multi-agent consensus with asynchrony and delayed information. IFAC-PapersOnLine 2015, 48, 28–33. [Google Scholar] [CrossRef]
- Wang, D.; Zheng, N.; Xu, M.; Wu, Y.; Hu, Q.; Wang, G. Resilient Privacy-Preserving Average Consensus for Multi-agent Systems under Attacks. In Proceedings of the 16th International Conference on Control, Automation, Robotics and Vision (ICARCV), Shenzhen, China, 13–15 December 2020; pp. 1399–1405. [Google Scholar]
- Wen, G.; Lv, Y.; Zhou, J.; Fu, J. Sufficient and Necessary Condition for Resilient Consensus under Time-varying Topologies. In Proceedings of the 7th International Conference on Information, Cybernetics, and Computational Social Systems (ICCSS), IEEE, Guangzhou, China, 13–15 November 2020; pp. 84–89. [Google Scholar]
- Shang, Y. Resilient consensus of switched multi-agent systems. Syst. Control Lett. 2018, 122, 12–18. [Google Scholar] [CrossRef]
- LeBlanc, H.J.; Koutsoukos, X.D. Consensus in networked multi-agent systems with adversaries. In Proceedings of the 14th International Conference on Hybrid Systems: Computation and Control, Chicago, IL, USA, 12–14 April 2011; pp. 281–290. [Google Scholar]
- Gil, S.; Kumar, S.; Mazumder, M.; Katabi, D.; Rus, D. Guaranteeing spoof-resilient multi-robot networks. Auton. Robot. 2017, 41, 1383–1400. [Google Scholar] [CrossRef] [Green Version]
- Wu, Y.; He, X. Secure Consensus Control for Multi-Agent Systems with Attacks and Communication Delays. IEEE/CAA J. Autom. Sin. 2017, 4, 136–142. [Google Scholar] [CrossRef]
- Cheng, C.F.; Tsai, K.T. A recursive Byzantine-resilient protocol. J. Netw. Comput. Appl. 2015, 48, 87–98. [Google Scholar] [CrossRef]
- Li, C.; Hurfin, M.; Wang, Y. Approximate Byzantine consensus in sparse, mobile ad hoc networks. J. Parallel Distrib. Comput. 2014, 74, 2860–2871. [Google Scholar] [CrossRef]
- Kailkhura, B.; Brahma, S.; Varshney, P.K. Data Falsification Attacks on Consensus-Based Detection Systems. IEEE Trans. Signal Inf. Process. Over Networks 2017, 3, 145–158. [Google Scholar] [CrossRef] [Green Version]
- Shang, Y. Consensus of hybrid multi-agent systems with malicious nodes. IEEE Trans. Circuits Syst. II Express Briefs 2019, 67, 685–689. [Google Scholar] [CrossRef]
- Wu, Y.; Xu, M.; Zheng, N.; He, X. Event-Triggered Resilient Consensus for Multi-Agent Networks Under Deception Attacks. IEEE Access 2020, 8, 78121–78129. [Google Scholar] [CrossRef]
- Tseng, L.; Vaidya, N.H. Fault-tolerant consensus in directed graphs. In Proceedings of the 2015 ACM Symposium on Principles of Distributed Computing, Donostia-San Sebastián, Spain, 21–23 July 2015; pp. 451–460. [Google Scholar]
- Li, J. Fault tolerant consensus of multi-agent systems with linear dynamics. Math. Probl. Eng. 2013, 2013, 465671. [Google Scholar] [CrossRef]
- Deng, C.; Yang, G.H. Distributed adaptive fault-tolerant control approach to cooperative output regulation for linear multi-agent systems. Automatica 2019, 103, 62–68. [Google Scholar] [CrossRef]
- Pu, C. Sybil Attack in RPL-Based Internet of Things: Analysis and Defenses. IEEE Internet Things J. 2020, 7, 4937–4949. [Google Scholar] [CrossRef]
- Douceur, J.R. The sybil attack. In Proceedings of the International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 251–260. [Google Scholar]
- Dong, W.; Liu, X. Robust and secure time-synchronization against sybil attacks for sensor networks. IEEE Trans. Ind. Informatics 2015, 11, 1482–1491. [Google Scholar] [CrossRef]
- Jamshidi, M.; Darwesh, A.M.; Lorenc, A.; Ranjbari, M.; Meybodi, M.R. A precise algorithm for detecting malicious sybil nodes in mobile wireless sensor networks. IEIE Trans. Smart Process. Comput. 2018, 7, 457–466. [Google Scholar] [CrossRef]
- Huang, Y.; Wang, W.; Wang, Y.; Jiang, T.; Zhang, Q. Lightweight sybil-resilient multi-robot networks by multipath manipulation. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 2185–2193. [Google Scholar]
- Wheeler, T.; Bharathi, E.; Gil, S. Switching topology for resilient consensus using Wi-Fi signals. In Proceedings of the 2019 International Conference on Robotics and Automation (ICRA), Montreal, QC, Canada, 20–24 May 2019; pp. 2018–2024. [Google Scholar]
- Biryukov, A.; Feher, D. ReCon: Sybil-resistant consensus from reputation. Pervasive Mob. Comput. 2020, 61, 101109. [Google Scholar] [CrossRef]
- Levine, B.N.; Shields, C.; Margolin, N.B. A survey of solutions to the sybil attack. Univ. Mass. Amherst. Amherst. 2006, 7, 224. [Google Scholar]
- Renganathan, V.; Summers, T. Spoof resilient coordination for distributed multi-robot systems. In Proceedings of the 2017 International Symposium on Multi-Robot and Multi-Agent Systems (MRS), Los Angeles, CA, USA, 4–5 December 2017; pp. 135–141. [Google Scholar]
- Jiang, Y.; Li, D.; Wu, X.; Xu, Y. Resilient Consensus of Second-Order Multi-Agent Systems Based on WiFi Signals. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; pp. 5865–5870. [Google Scholar]
- Breslaw, J.A. Random sampling from a truncated multivariate normal distribution. Appl. Math. Lett. 1994, 7, 1–6. [Google Scholar] [CrossRef] [Green Version]
- Burkardt, J. The Truncated Normal Distribution; Department of Scientific Computing, Florida State University: Tallahassee, FL, USA, 2014. [Google Scholar]
- Wu, Y.; He, X.; Liu, S. Resilient consensus for multi-agent systems with quantized communication. In Proceedings of the American Control Conference (ACC), Boston, MA, USA, 6–8 July 2016; pp. 5136–5140. [Google Scholar]
- Dibaji, S.M.; Ishii, H.; Tempo, R. Resilient Randomized Quantized Consensus. IEEE Trans. Autom. Control. 2018, 63, 2508–2522. [Google Scholar] [CrossRef] [Green Version]




Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, X.; Wu, Y.; Xu, M.; Zheng, N. Resilient Consensus for Multi-Agent Systems in the Presence of Sybil Attacks. Electronics 2022, 11, 800. https://doi.org/10.3390/electronics11050800
Dong X, Wu Y, Xu M, Zheng N. Resilient Consensus for Multi-Agent Systems in the Presence of Sybil Attacks. Electronics. 2022; 11(5):800. https://doi.org/10.3390/electronics11050800
Chicago/Turabian StyleDong, Xiaochen, Yiming Wu, Ming Xu, and Ning Zheng. 2022. "Resilient Consensus for Multi-Agent Systems in the Presence of Sybil Attacks" Electronics 11, no. 5: 800. https://doi.org/10.3390/electronics11050800
APA StyleDong, X., Wu, Y., Xu, M., & Zheng, N. (2022). Resilient Consensus for Multi-Agent Systems in the Presence of Sybil Attacks. Electronics, 11(5), 800. https://doi.org/10.3390/electronics11050800





