Feature Cluster-Based Secure Data Transmission Method for Social Internet of Vehicles
Abstract
:1. Introduction
- The method considers mobile feature similarity, attribute feature similarity, and interaction feature similarity of users during the construction of the feature cluster, which not only ensures the stability of communication links but also enhances the trust relationship between users.
- We propose an efficient dynamic updating algorithm for feature clusters by dynamically generating random number keys. This not only reduces the system delay caused by the update of the feature cluster but also avoids the privacy threat caused by users outside the feature cluster.
- In order to resist intra-cluster attacks, we use a consortium blockchain to record the transmitted data of the sender, so that the receiver can verify the integrity and validity of the transmitted data through the consortium blockchain.
2. Related Work
2.1. Trust Management Mechanisms
2.2. Security Authentication Mechanism
3. Problem Description
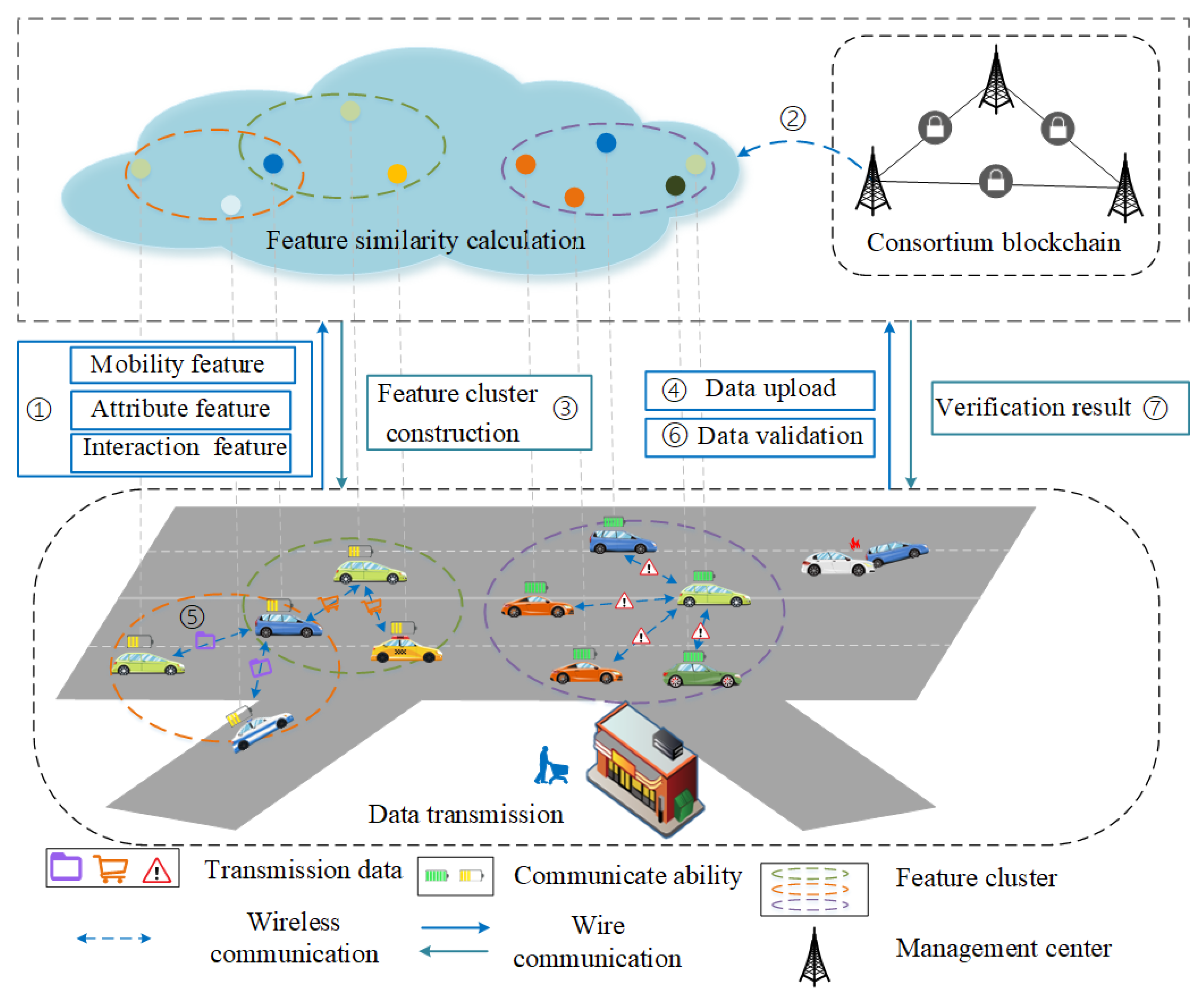
3.1. Data Transmission Scenario
- Management center: Management centers (MCs) belong to a category of public infrastructures, such as base stations (BSs); these are usually deployed and maintained by operators, and are responsible for providing vehicles with cellular network access [43]. The jurisdiction of each management center is a circle with its location as the center and communication distance as the radius. When users enter the management center’s wireless coverage area, they need to accept management by the management center (identity management, information analysis, key generation, etc.). In addition, the management center is responsible for calculating the feature similarity with other users and forming feature clusters for users with high similarity.
- Vehicle: The vehicle contains a built-in on-board unit (OBU), which has limited computing and storage capabilities. Vehicles typically use the C-V2X or DSRC protocols to communicate with other entities on the road. When a vehicle registers with the management center for the first time, it is required to upload the user’s personal information, which can indirectly reflect the user’s social relationships. When a user initiates a feature cluster construction request to the management center that contains the user’s mobility, attribute, and interaction features, the management center calculates the user’s feature similarity. It creates different feature clusters for the user based on the calculated value. The sender in the feature cluster must upload the transmitted data to the consortium blockchain for the receiver to verify the data.
- Consortium blockchain: Blockchain can be seen as a decentralized and reliable platform that usually consists of blocks and chains [44]. Smart contracts, as code executed on the blockchain, can dictate the format in which data are transmitted by the sender [45,46]. Blockchain can be divided into public, private, and consortium blockchains according to openness. Compared to the other two blockchains, consortium blockchains are typically jointly managed and controlled by a specific set of nodes, so transactions are processed faster and more securely. Considering that vehicles in SIoV have a high speed and need to complete data transmission quickly and safely, this paper uses consortium blockchain to ensure secure data transmission between vehicles. In this paper, the nodes of the consortium blockchain are mainly composed of the authorization administration center, including the primary management center and the slave management centers. These nodes are responsible for maintaining and constructing the consortium blockchain [47].
3.2. Attack Model
3.3. Security Requirements
- Identity privacy protection. According to our proposed user model, this method should prevent other users in the feature cluster from obtaining the sender’s identity during data transmission.
- Communication security. The broadcast channel of SIoV is open and easily monitored by other users. The proposed method should implement the transmitted data access control so that users in the same feature cluster can only access the data.
- Feature cluster security. The users in the feature cluster change dynamically with time, and the proposed method should ensure the vehicles leaving the feature cluster cannot receive the transmission content of the feature cluster.
- Data integrity. Since the user’s decision depends on the integrity and the security of the transmission data, the method should ensure that the transmission data received by users in the feature cluster are not tampered with or forged.
4. The Proposed FC-SDTM Method
4.1. Initialization
Feature Cluster Construction
- (a)
- Calculation of user mobility feature similarity
- (b)
- Calculation of user attribute feature similarity.
- (c)
- Calculation of user interaction feature similarity.
4.2. Data Encryption
4.3. Feature Cluster Updating
| Algorithm 1 Communication key updating algorithm pseudo-code |
| Input: Change of feature cluster members; Output: New key ;
|
5. Security Analysis
6. Time Complexity Analysis
7. Simulation and Results Analysis
7.1. Secure Transmission Metrics
- (1)
- Confusion matrix.
- (2)
- Message exposure rate.
- (3)
- Running time.
- (4)
- Transmission accuracy rate.
7.2. Results Analysis
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Amin, F.; Majeed, A.; Mateen, A.; Abbasi, R.; Hwang, S.O. A systematic survey on the recent advancements in the Social Internet of Things. IEEE Access 2022, 10, 63867–63884. [Google Scholar] [CrossRef]
- Jia, X.; Xing, L.; Gao, J.; Wu, H. A survey of location privacy preservation in social internet of vehicles. IEEE Access 2020, 8, 201966–201984. [Google Scholar] [CrossRef]
- Hbaieb, A.; Ayed, S.; Chaari, L. A survey of trust management in the Internet of Vehicles. Comput. Netw. 2022, 10, 2223. [Google Scholar] [CrossRef]
- Prathiba, S.B.; Raja, G.; Bashir, A.K.; AlZubi, A.A.; Gupta, B. SDN-assisted safety message dissemination framework for vehicular critical energy infrastructure. IEEE Trans. Ind. Inform. 2021, 18, 3510–3518. [Google Scholar] [CrossRef]
- Alfadhli, S.A.; Lu, S.; Fatani, A.; Al-Fedhly, H.; Ince, M. SD2PA: A fully safe driving and privacy-preserving authentication scheme for VANETs. Hum.-Centric Comput. Inf. Sci. 2020, 10, 38. [Google Scholar] [CrossRef]
- Hameed, K.; Garg, S.; Amin, M.B.; Kang, B. Towards a formal modelling, analysis and verification of a clone node attack detection scheme in the internet of things. Comput. Netw. 2022, 204, 108702. [Google Scholar] [CrossRef]
- Chen, C.; Liu, L.; Qiu, T.; Jiang, J.; Song, H. Routing With Traffic Awareness and Link Preference in Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2022, 23, 200–214. [Google Scholar] [CrossRef]
- Jing, T.; Liu, Y.; Wang, X.; Gao, Q. Joint Trust Management and Sharing Provisioning in IoV-Based Urban Road Network. Wirel. Commun. Mob. Comput. 2022, 2022, 6942120. [Google Scholar] [CrossRef]
- Mirzaee, P.H.; Shojafar, M.; Bagheri, H.; Chan, T.H.; Cruickshank, H.; Tafazolli, R. A two-layer collaborative vehicle-edge intrusion detection system for vehicular communications. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Norman, OK, USA, 27–30 September 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. TP2SF: A Trustworthy Privacy-Preserving Secured Framework for sustainable smart cities by leveraging blockchain and machine learning. J. Syst. Archit. 2021, 115, 101954. [Google Scholar] [CrossRef]
- Xing, L.; Ma, Q.; Jiang, L. Microblog user recommendation based on particle swarm optimization. China Commun. 2017, 14, 134–144. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. PEFL: Deep privacy-encoding-based federated learning framework for smart agriculture. IEEE Micro 2021, 42, 33–40. [Google Scholar] [CrossRef]
- Washio, N.; Matsuura, S.; Kakiuchi, M.; Inomata, A.; Fujikawa, K. A vehicle clustering algorithm for information propagation by inter-vehicle communications. In Proceedings of the 2015 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), St. Louis, MO, USA, 23–27 March 2015; pp. 111–116. [Google Scholar]
- Mukhtaruzzaman, M.; Atiquzzaman, M. Junction-based stable clustering algorithm for vehicular ad hoc network. Ann. Telecommun. 2021, 76, 777–786. [Google Scholar] [CrossRef]
- Chang, H.; Ning, N. An intelligent multimode clustering mechanism using driving pattern recognition in cognitive internet of vehicles. Sensors 2021, 21, 7588. [Google Scholar] [CrossRef] [PubMed]
- Ghimire, B.; Rawat, D.B. Dynamic Clustering in IoV Using Behavioral Parameters and Contention Window Adaptation. IEEE Trans. Veh. Technol. 2021, 71, 2031–2040. [Google Scholar] [CrossRef]
- Venitta Raj, R.; Balasubramanian, K. Trust aware similarity-based source routing to ensure effective communication using game-theoretic approach in VANETs. J. Ambient Intell. Humaniz. Comput. 2021, 12, 6781–6791. [Google Scholar] [CrossRef]
- Li, L.; Wang, W.; Gao, Z. Driver’s Social Relationship Based Clustering and Transmission in Vehicle Ad Hoc Networks (VANETs). Electronics 2020, 9, 298. [Google Scholar] [CrossRef]
- Dwab, C.; Ldab, C.; Hw, D.; Klab, C.; Rwab, C. Similarity Aware Safety Multimedia Data Transmission Mechanism for Internet of Vehicles. Future Gener. Comput. Syst. 2019, 99, 609–623. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, X.; Jain, D.K.; Khan, H.; Wang, Z. A Blockchain-Based Trusted Data Management Scheme in Edge Computing. IEEE Trans. Ind. Inform. 2019, 16, 2013–2021. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and Efficient Data Sharing Among Vehicles Based on Consortium Blockchain. IEEE Trans. Intell. Transp. Syst. 2021, 23, 8857–8867. [Google Scholar] [CrossRef]
- Lin, B.; Chen, X.; Wang, L. A cloud-based trust evaluation scheme using a vehicular social network environments. In Proceedings of the 24th Asia-Pacific Software Engineering Conference (APSEC), Nanjing, China, 4–8 December 2017; pp. 120–129. [Google Scholar]
- Xiao, Y.; Liu, Y. BayesTrust and VehicleRank: Constructing an Implicit Web of Trust in VANET. IEEE Trans. Veh. Technol. 2019, 68, 2850–2864. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Liu, Y.; Yang, W.; Gao, Z. BTDS: Bayesian-based trust decision scheme for intelligent connected vehicles in VANETs. Trans. Emerg. Telecommun. Technol. 2020, 31, e3879. [Google Scholar] [CrossRef]
- Zhang, J.; Zheng, K.; Zhang, D.; Yan, B. AATMS: An anti-attack trust management scheme in VANET. IEEE Access 2020, 8, 21077–21090. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Behavior analysis and blockchain based trust management in VANETs. J. Parallel Distrib. Comput. 2021, 151, 61–69. [Google Scholar] [CrossRef]
- Firdaus, M.; Rahmadika, S.; Rhee, K.H. Decentralized trusted data sharing management on internet of vehicle edge computing (IoVEC) networks using consortium blockchain. Sensors 2021, 21, 2410. [Google Scholar] [CrossRef] [PubMed]
- Javaid, U.; Aman, M.N.; Sikdar, B. A Scalable Protocol for Driving Trust Management in Internet of Vehicles with Blockchain. IEEE Internet Things J. 2020, 7, 11815–11829. [Google Scholar] [CrossRef]
- Wang, M.; Yan, Z. Privacy-preserving authentication and key agreement protocols for D2D group communications. IEEE Trans. Ind. Inform. 2017, 14, 3637–3647. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Sandila, M.; Javed, I.T.; Margaria, T.; Aslam, L. Authentication scheme for Unmanned Aerial Vehicles based Internet of Vehicles networks. Egypt. Inform. J. 2021, 23, 83–93. [Google Scholar] [CrossRef]
- Liu, H.; Wang, H.; Gu, H. HPBS: A Hybrid Proxy Based Authentication Scheme in VANETs. IEEE Access 2020, 8, 161655–161667. [Google Scholar] [CrossRef]
- Zheng, J.; Wang, X.; Yang, Q.; Xiao, W.; Sun, Y.; Liang, W. A blockchain-based lightweight authentication and key agreement scheme for internet of vehicles. Connect. Sci. 2022, 34, 1430–1453. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Wang, H.; Choo, K.K.R.; Wang, L.; He, D. A Secure and Efficient Multiserver Authentication and Key Agreement Protocol for Internet of Vehicles. IEEE Internet Things J. 2022, 9, 24398–24416. [Google Scholar] [CrossRef]
- Xu, Z.; Li, X.; Xu, J.; Liang, W.; Choo, K. A secure and computationally efficient authentication and key agreement scheme for Internet of Vehicles. Comput. Electr. Eng. 2021, 95, 107409. [Google Scholar] [CrossRef]
- Shen, M.; Lu, H.; Wang, F.; Liu, H. Secure and Efficient Blockchain-assisted Authentication for Edge-Integrated Internet-of-Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 12250–12263. [Google Scholar] [CrossRef]
- Zhao, G.; Di, B.; He, H. A novel decentralized cross-domain identity authentication protocol based on blockchain. Trans. Emerg. Telecommun. Technol. 2022, 33, e4377. [Google Scholar] [CrossRef]
- Hameed, K.; Garg, S.; Amin, M.B.; Kang, B. A formally verified blockchain-based decentralised authentication scheme for the internet of things. J. Supercomput. 2021, 77, 14461–14501. [Google Scholar] [CrossRef]
- Ahmad, F.; Franqueira, V.; Adnane, A. TEAM: A Trust Evaluation and Management Framework in Context-enabled Vehicular Ad-hoc Networks. IEEE Access 2018, 6, 28643–28660. [Google Scholar] [CrossRef]
- Page, L.; Brin, S.; Motwani, R.; Winograd, T. The PageRank Citation Ranking: Bringing Order to the Web. Stanf. Digit. Libr. Work. Pap. 1998, 8568, 138–145. [Google Scholar] [CrossRef]
- Efron, B. Bayes, oracle Bayes and empirical Bayes. Stat. Sci. 2019, 34, 177–201. [Google Scholar] [CrossRef]
- Hakeem, S.A.A.; Kim, H.W. Multi-Zone Authentication and Privacy-Preserving Protocol (MAPP) Based On the Bilinear Pairing Cryptography for 5G-V2X. Sensors 2021, 21, 665. [Google Scholar] [CrossRef]
- Yao, Y.; Chang, X.; Misc, J.; Misc, V.B.; Li, L. BLA: Blockchain-Assisted Lightweight Anonymous Authentication for Distributed Vehicular Fog Services. IEEE Internet Things J. 2019, 6, 3775–3784. [Google Scholar] [CrossRef]
- Chakroun, R.; Abdellatif, S.; Villemur, T. LAMD: Location-based Alert Message Dissemination scheme for emerging infrastructure-based vehicular networks. Internet Things 2022, 19, 100510. [Google Scholar] [CrossRef]
- Hsiao, S.J.; Sung, W.T. Blockchain-Based Supply Chain Information Sharing Mechanism. IEEE Access 2022, 10, 78875–78886. [Google Scholar] [CrossRef]
- Zou, W.; Lo, D.; Kochhar, P.S.; Le, X.; Xia, X.; Feng, Y.; Chen, Z.; Xu, B. Smart Contract Development: Challenges and Opportunities. IEEE Comput. Soc. 2021, 47, 2084–2106. [Google Scholar] [CrossRef]
- Gorski, T. The k + 1 Symmetric Test Pattern for Smart Contracts. Symmetry 2022, 8, 1686. [Google Scholar] [CrossRef]
- Singh, M. Tri-Blockchain based intelligent vehicular networks. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 860–864. [Google Scholar] [CrossRef]
- Kim, S. Automotive Vulnerability Analysis for Deep Learning Blockchain Consensus Algorithm. Electronics 2022, 11, 119. [Google Scholar] [CrossRef]
- Hu, W.; Hu, Y.; Yao, W.; Li, H. A Blockchain-Based Byzantine Consensus Algorithm for Information Authentication of the Internet of Vehicles. IEEE Access 2019, 7, 139703–139711. [Google Scholar] [CrossRef]
- Halbouni, A.; Gunawan, T.; Habaebi, M. CNN-LSTM: Hybrid Deep Neural Network for Network Intrusion Detection System. IEEE Access 2022, 10, 99837–99849. [Google Scholar] [CrossRef]





| Trust Management Mechanisms | Security Authentication Mechanisms | |||||||
|---|---|---|---|---|---|---|---|---|
| [22] | [23] | [24,25] | [26,27,28] | [29,30,31] | [32,33] | [34] | [35,36,37] | |
| Security | Low | Low | High | High | High | Medium | Medium | High |
| Efficiency | Low | Medium | Low | High | Low | High | High | High |
| Overhead | High | High | High | Medium | High | Low | Low | Medium |
| Symbol | Description |
|---|---|
| ⊕ | Exclusive-OR (XOR) operation |
| h(.) | Secure one-way hash function |
| u | Vehicle |
| Vehicle pseudonym | |
| Mobility features | |
| Attribute features | |
| Interaction features | |
| Attribute feature similarity | |
| Interaction feature similarity | |
| Feature similarity | |
| Mobility feature set | |
| Attribute feature set | |
| Interaction feature set | |
| Communication intensity | |
| Data transmission limit | |
| Mobility feature similarity |
| Parameters | Values |
|---|---|
| Simulation time | 30 mins |
| Vehicle speed | 0–45 km/h |
| Simulation area | 2000 m × 2000 m |
| Message transmission rate | 7 Mbit·s−1 |
| Number of vehicles | 50–450 |
| Number of management centers | 60 |
| Vehicle communication protocol | 802.11 p |
| Number of feature clusters | 0–50 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xing, L.; Liu, L.; Wu, H.; Jia, X.; Ma, H.; Zhang, X. Feature Cluster-Based Secure Data Transmission Method for Social Internet of Vehicles. Electronics 2023, 12, 2180. https://doi.org/10.3390/electronics12102180
Xing L, Liu L, Wu H, Jia X, Ma H, Zhang X. Feature Cluster-Based Secure Data Transmission Method for Social Internet of Vehicles. Electronics. 2023; 12(10):2180. https://doi.org/10.3390/electronics12102180
Chicago/Turabian StyleXing, Ling, Lulu Liu, Honghai Wu, Xiaofan Jia, Huahong Ma, and Xiaohui Zhang. 2023. "Feature Cluster-Based Secure Data Transmission Method for Social Internet of Vehicles" Electronics 12, no. 10: 2180. https://doi.org/10.3390/electronics12102180
APA StyleXing, L., Liu, L., Wu, H., Jia, X., Ma, H., & Zhang, X. (2023). Feature Cluster-Based Secure Data Transmission Method for Social Internet of Vehicles. Electronics, 12(10), 2180. https://doi.org/10.3390/electronics12102180






