A Novel Traffic Obfuscation Technology for Smart Home
Abstract
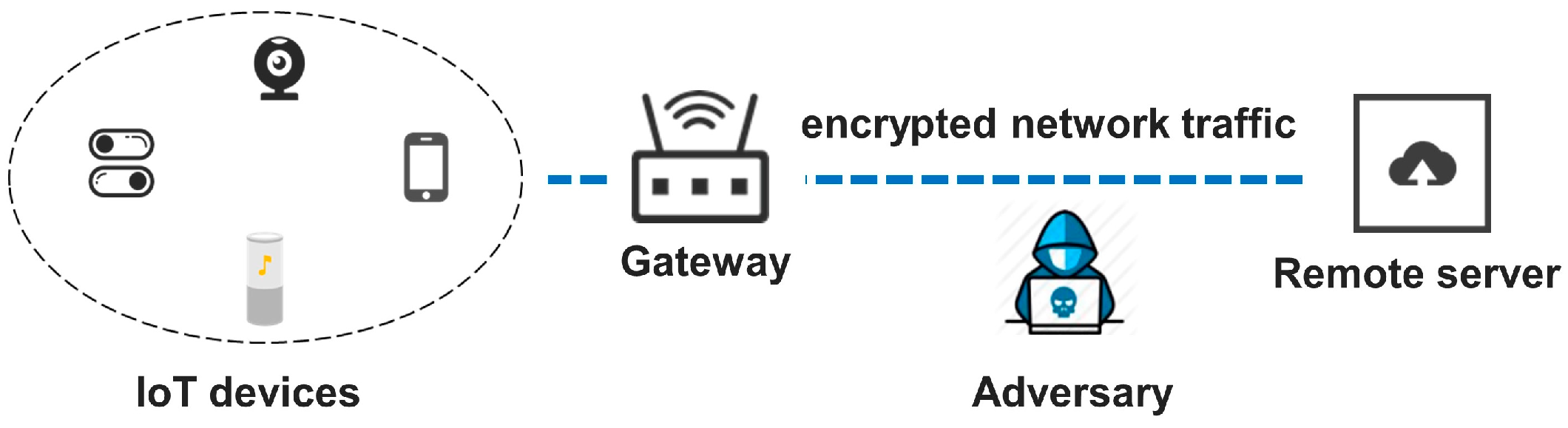
:1. Introduction
- (1)
- The proposal of an enhanced smart home traffic obfuscation method called SHTObfuscator based on the virtual user technology concept. By injecting traffic fingerprints of different device activities into the real traffic environment, we effectively reduce the effect of traffic classification attack models.
- (2)
- A smart home traffic privacy protection system SHTProtector is designed and implemented. Experiments of device identification monitoring, device fingerprint extraction, traffic obfuscation effect and traffic obfuscation overhead are carried out in the real environment of smart home, and the effectiveness of the proposed method is verified.
- (3)
- Achieved the balance between privacy preserving and communication overhead in accordance with the network condition.
2. Related Work
3. Motivation
3.1. Threat Model
3.2. Feature Selection
3.3. Goals and Challenges
4. Design
4.1. Overall Design
4.2. Event Fingerprint Extraction
4.3. Virtual User Generation
4.3.1. User Behavior Analysis
- (1)
- Device Behavior Segmentation
- (2)
- User Behavior Feature Extraction
- (3)
- User Behavior Connections Exploration
4.3.2. Behavior Sequence Generation
- (1)
- Construction of Virtual User Behaviors
| Algorithm 1. Virtual User Behavior Generation |
| INPUT: Initial behavior of virtual user <Ve0, Time0> Real user behavior probabilities P1, P2 Current context mode Xi, symmetry test parameter Mi Confusion level parameter f OUTPUT: Virtual user’s daily behavior pattern Va = <Ve0, Time0>, …, <Ven, Timen> DATA: SQLite Fingerprint Database DB
|
- (2)
- Device Event Sequence Generation
| Algorithm 2. Device Behavior Sequence Generation |
| INPUT: Virtual user behavior sequence Va Symmetry test parameter Mi Association between user behavior and device behavior BD Confusion level parameter f OUTPUT: Device behavior sequence Ea = {de1, de2, …, den}
|
4.4. Obfuscated Traffic Injection
5. Experimental Evaluation
5.1. Experimental Setup
5.1.1. Traffic Obfuscation Effectiveness Experiment
5.1.2. Traffic Obfuscation Overhead Experiment
5.2. Efficiency of Obfuscation
5.3. Overhead Evaluation
6. Conclusions and Prospect
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A

References
- Cisco, U. Cisco Annual Internet Report (2018–2023) White Paper; Cisco: San Jose, CA, USA, 2020. [Google Scholar]
- Acar, A.; Fereidooni, H.; Abera, T.; Sikder, A.K.; Miettinen, M.; Aksu, H.; Conti, M.; Sadeghi, A.R.; Uluagac, S. Peek-a-Boo: I See Your Smart Home Activities, Even Encrypted! In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Linz, Austria, 8 July 2020; ACM: New York, NY, USA, 2020; pp. 207–218. [Google Scholar]
- Salman, O.; Elhajj, I.H.; Kayssi, A.; Chehab, A. A Review on Machine Learning Based Approaches for Internet Traffic Classification. Ann. Telecommun. 2020, 75, 673–710. [Google Scholar]
- Alshehri, A.; Granley, J.; Yue, C. Attacking and Protecting Tunneled Traffic of Smart Home Devices. In Proceedings of the Tenth ACM Conference on Data and Application Security and Privacy, New Orleans, LA, USA, 16–18 March 2020; pp. 259–270. [Google Scholar]
- Trimananda, R.; Varmarken, J.; Markopoulou, A. Packet-Level Fingerprints for Smart Home Devices. In Proceedings of the 2020 Network and Distributed System Security Symposium, San Diego, CA, USA, 23–26 February 2020; pp. 1084–8045. [Google Scholar] [CrossRef]
- Copos, B.; Levitt, K.; Bishop, M.; Rowe, J. Is Anybody Home? Inferring Activity from Smart Home Network Traffic. In Proceedings of the 2016 IEEE Security and Privacy Workshops, San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Dong, S.; Li, Z.; Tang, D.; Chen, J.; Sun, M.; Zhang, K. Your Smart Home Can’t Keep a Secret: Towards Automated Fingerprinting of IoT Traffic with Neural Networks. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security, Taipei, Taiwan, 5–9 October 2020. [Google Scholar]
- Yao, Z.J.; Ge, J.G.; Zhang, X.D.; Zheng, H.B.; Zou, Z.; Sun, K.K.; Xu, Z.H. Research review on traffic obfuscation and its corresponding identification and tracking technologies. J. Softw. (In Chinese). 2018, 29, 3205–3222. [Google Scholar]
- Nicolazzo, S.; Nocera, A.; Ursino, D.; Virgili, L. A privacy-preserving approach to prevent feature disclosure in an IoT scenario. Future Gener. Comput. Syst. 2020, 105, 502–519. [Google Scholar] [CrossRef]
- Corradini, E.; Nicolazzo, S.; Nocera, A.; Ursino, D.; Virgili, L. A two-tier Blockchain framework to increase protection and autonomy of smart objects in the IoT. Comput. Commun. 2022, 181, 338–356. [Google Scholar] [CrossRef]
- Pinheiro, A.J.; Bezerra, J.M.; Campelo, D.R. Packet Padding for Improving Privacy in Consumer IoT. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 July 2018. [Google Scholar]
- Apthorpe, N.; Reisman, D.; Sundaresan, S.; Narayanan, A.; Feamster, N. Spying on the smart home: Privacy attacks and defenses on encrypted iot traffic. arXiv 2017, arXiv:1708.05044. [Google Scholar]
- Xiong, S.; Sarwate, A.D.; Mandayam, N.B. Defending against packet-size side-channel attacks in IoT networks. In Proceedings of the 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Calgary, AB, Canada, 15–20 April 2018; pp. 2027–2031. [Google Scholar]
- Pinheiro, A.J.; de Araujo-Filho, P.F.; Bezerra, J.D.M.; Campelo, D.R. Adaptive packet padding approach for smart home networks: A tradeoff between privacy and performance. IEEE Internet Things J. 2020, 8, 3930–3938. [Google Scholar]
- Wang, C.; Kennedy, S.; Li, H.; Hudson, K.; Atluri, G.; Wei, X.; Sun, W.; Wang, B. Fingerprinting encrypted voice traffic on smart speakers with deep learning. In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Linz, Austria, 8–10 July 2020; pp. 254–265. [Google Scholar]
- Prates, N.; Vergütz, A.; Macedo, R.T.; Santos, A.; Nogueira, M. A defense mechanism for timing-based side-channel attacks on IoT traffic. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Ibitoye, O.; Matrawy, A.; Shafiq, M.O. A GAN-based Approach for Mitigating Inference Attacks in Smart Home Environment. arXiv 2020, arXiv:2011.06725. [Google Scholar]
- Ranieri, A.; Caputo, D.; Verderame, L.; Merlo, A.; Caviglione, L. Deep adversarial learning on google home devices. arXiv 2021, arXiv:2102.13023. [Google Scholar]
- Apthorpe, N.; Reisman, D.; Feamster, N. Closing the blinds: Four strategies for protecting smart home privacy from network observers. arXiv 2017, arXiv:1705.06809. [Google Scholar]
- Hafeez, I.; Antikainen, M.; Tarkoma, S. Protecting IoT-environments against traffic analysis attacks with traffic morphing. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 196–201. [Google Scholar]
- Zhu, Q.; Yang, C.; Zheng, Y.; Ma, J.; Li, H.; Zhang, J.; Shao, J. Smart home: Keeping privacy based on Air-Padding. IET Inf. Secur. 2021, 15, 156–168. [Google Scholar]
- Xu, Z.; Khan, H.; Muresan, R. TMorph: A Traffic Morphing Framework to Test Network Defenses Against Adversarial Attacks. In Proceedings of the 2022 International Conference on Information Networking (ICOIN), Jeju-si, Republic of Korea, 12–15 January 2022; pp. 18–23. [Google Scholar]
- Liu, X.; Zeng, Q.; Du, X.; Valluru, S.L.; Fu, C.; Fu, X.; Luo, B. Sniffmislead: Non-intrusive privacy protection against wireless packet sniffers in smart homes. In Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses, San Sebastian, Spain, 6–8 October 2021; pp. 33–47. [Google Scholar]
- Liu, X.; Zeng, Q.; Du, X.; Valluru, S.L.; Fu, C.; Fu, X.; Luo, B. Privacyguard: Enhancing smart home user privacy. In Proceedings of the 20th International Conference on Information Processing in Sensor Networks (Co-Located with CPS-IoT Week 2021), Nashville, TN, USA, 18–21 May 2021; pp. 62–76. [Google Scholar]
- Apthorpe, N.; Reisman, D.; Feamster, N. A smart home is no castle: Privacy vulnerabilities of encrypted iot traffic. arXiv 2017, arXiv:1705.06805. [Google Scholar]
- Datta, T.; Apthorpe, N.; Feamster, N. A developer-friendly library for smart home IoT privacy-preserving traffic obfuscation. In Proceedings of the 2018 Workshop on IoT Security and Privacy, Budapest, Hungary, 20 August 2018; pp. 43–48. [Google Scholar]
- Dyer, K.P.; Coull, S.E.; Ristenpart, T.; Shrimpton, T. Peek-a-boo, i still see you: Why efficient traffic analysis countermeasures fail. In Proceedings of the 2012 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–23 May 2012; pp. 332–346. [Google Scholar]
- Asif, M.; Khan, T.A.; Taleb, N.; Said, R.A.; Siddiqui, S.Y.; Batool, G. A Proposed Architecture for Traffic Monitoring & Control System via LiFi Technology in Smart Homes. In Proceedings of the 2022 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 16–17 February 2022; pp. 1–3. [Google Scholar]
- Apthorpe, N.; Huang, D.Y.; Reisman, D.; Narayanan, A.; Feamster, N. Keeping the smart home private with smart (er) iot traffic shaping. Proc. Priv. Enhancing Technol. 2019, 2019, 128–148. [Google Scholar]
- Liu, J.; Zhang, C.; Fang, Y. Epic: A differential privacy framework to defend smart homes against internet traffic analysis. IEEE Internet Things J. 2018, 5, 1206–1217. [Google Scholar]
- Jmila, H.; Blanc, G.; Shahid, M.R.; Lazrag, M. A survey of smart home iot device classification using machine learning-based network traffic analysis. IEEE Access 2022, 10, 97117–97141. [Google Scholar] [CrossRef]
- Yoshigoe, K.; Dai, W.; Abramson, M.; Jacobs, A. Overcoming invasion of privacy in smart home environment with synthetic packet injection. In Proceedings of the 2015 TRON Symposium (TROnShOW), Tokyo, Japan, 9–11 December 2015; pp. 1–7. [Google Scholar]
- Yoshigoe, K.; Dai, W.; Abramson, M.; Jacobs, A. Anomaly traffic detection and correlation in smart home automation IoT systems. Trans. Emerg. Telecommun. Technol. 2022, 33, e4053. [Google Scholar]
- Uddin, M.; Nadeem, T.; Nukavarapu, S. Extreme SDN Framework for IoT and Mobile Applications Flexible Privacy at the Edge. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications, Kyoto, Japan, 11–15 March 2019. [Google Scholar]
- Hussain, A.M.; Oligeri, G.; Voigt, T. The Dark (and Bright) Side of IoT: Attacks and Countermeasures for Identifying Smart Home Devices and Services; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]





| Component | Specifications |
|---|---|
| CPU | i5-8400 |
| RAM | 8 GB |
| OpenWrt | 19.07 |
| DNSmasq | 2.8.5 |
| Hostapd | v2.10-devel |
| Manufacturer | Name | Function | Device Behavior |
|---|---|---|---|
| Lenovo | Camera | Fingerprinting | View monitoring |
| Xiaomi | Smart Pan-Tilt Camera | Fingerprinting | Recording |
| Hikvision | Ezviz Camera | Fingerprinting | Recording |
| Baidu | Xiaodu Speaker | Fingerprinting | Conversation |
| Aqara | Smart Light | Fingerprinting | On/Off |
| Aqara | Motion Sensor | Fingerprinting | Motion detection |
| Aqara | Smart Switch | Fingerprinting | On/Off |
| Huawei | Mate20 Smartphone | Background | Video browsing |
| Lenovo | IdeaPad 16 Laptop | Background | File downloading |
| Lenovo | ThinkPad Laptop | Background | Standby |
| Device Behavior | Real | Virtual | |
|---|---|---|---|
| Device | Behavior | F1 Score (%) | F1 Score (%) |
| Xiaomi Camera | Record | 91.7 | 91.1 |
| Aqara Switch | Turn On | 98.0 | 98.3 |
| Xiaodu Speaker | Talk | 91.5 | 93.0 |
| Smart Light | Turn On | 97.4 | 96.3 |
| Motion Sensor | Sensor | 96.6 | 96.5 |
| User Behavior | Relevant Device Behavior |
|---|---|
| Control Smart Light | Turn on, turn off, change color, adjust brightness |
| Control Smart Plug | Turn on, turn off |
| Talk to Smart Speaker | Turn on and engage in conversation with smart speaker |
| Sleep | Activate camera, turn on motion sensor, turn off smart light |
| Wake Up | Turn off motion sensor, turn off camera, turn on speaker |
| Leave Home | Turn off motion sensor, turn on camera, turn off light, unlock/lock door |
| Back Home | Unlock/lock door, turn on light, turn on motion sensor, turn off camera |
| Original | Level I | Level II | Level III | |
|---|---|---|---|---|
| Behavior | F1 Score (%) | |||
| Leave Home | 92.2 | 31.4 | 27.3 | 22.6 |
| Return Home | 91.4 | 29.1 | 23.1 | 21.4 |
| Sleep | 90.6 | 28.0 | 24.6 | 19.3 |
| Wake Up | 91.3 | 26.3 | 22.7 | 18.0 |
| Walk | 94.5 | 25.6 | 22.8 | 19.5 |
| Method | Effectiveness (%) | Traffic | Overhead (%) |
|---|---|---|---|
| Original Traffic | - | 310 MB | - |
| Obfuscation Level I | 29.4 | 331 MB | 6.7 |
| Obfuscation Level II | 25.5 | 346 MB | 11.6 |
| Obfuscation Level III | 20.6 | 365 MB | 17.8 |
| Packet Padding | 21.3 | - | 87.5 |
| Traffic Shaping | 33.2 | - | 29.0 |
| Fake Traffic Injection | 28.3 | - | 31.1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Shen, F.; Liu, Y.; Yang, Z.; Lv, X. A Novel Traffic Obfuscation Technology for Smart Home. Electronics 2023, 12, 3477. https://doi.org/10.3390/electronics12163477
Zhang S, Shen F, Liu Y, Yang Z, Lv X. A Novel Traffic Obfuscation Technology for Smart Home. Electronics. 2023; 12(16):3477. https://doi.org/10.3390/electronics12163477
Chicago/Turabian StyleZhang, Shuo, Fangyu Shen, Yaping Liu, Zhikai Yang, and Xinyu Lv. 2023. "A Novel Traffic Obfuscation Technology for Smart Home" Electronics 12, no. 16: 3477. https://doi.org/10.3390/electronics12163477
APA StyleZhang, S., Shen, F., Liu, Y., Yang, Z., & Lv, X. (2023). A Novel Traffic Obfuscation Technology for Smart Home. Electronics, 12(16), 3477. https://doi.org/10.3390/electronics12163477







