Differential Privacy-Based Spatial-Temporal Trajectory Clustering Scheme for LBSNs
Abstract
:1. Introduction
- (1)
- We constructed a differential privacy-based spatial-temporal trajectory protection framework. The spatial-temporal activity privacy protection mechanism was proposed to achieve the protection of users’ spatial-temporal activity privacy;
- (2)
- We proposed a trajectory clustering technology that groups trajectories into different clusters through considering the semantic distance between trajectories;
- (3)
- We conducted an extensive experimental study to verify the functions and performance of the proposed DP-STTC scheme on two real datasets. The experiment results show that our DP-STTC scheme can cluster the trajectories privately.
2. Background and Related Work
2.1. Trajectory Clustering
2.2. Privacy Preserving of Trajectories
2.3. Spatial-Temporal Data Privacy Preservation
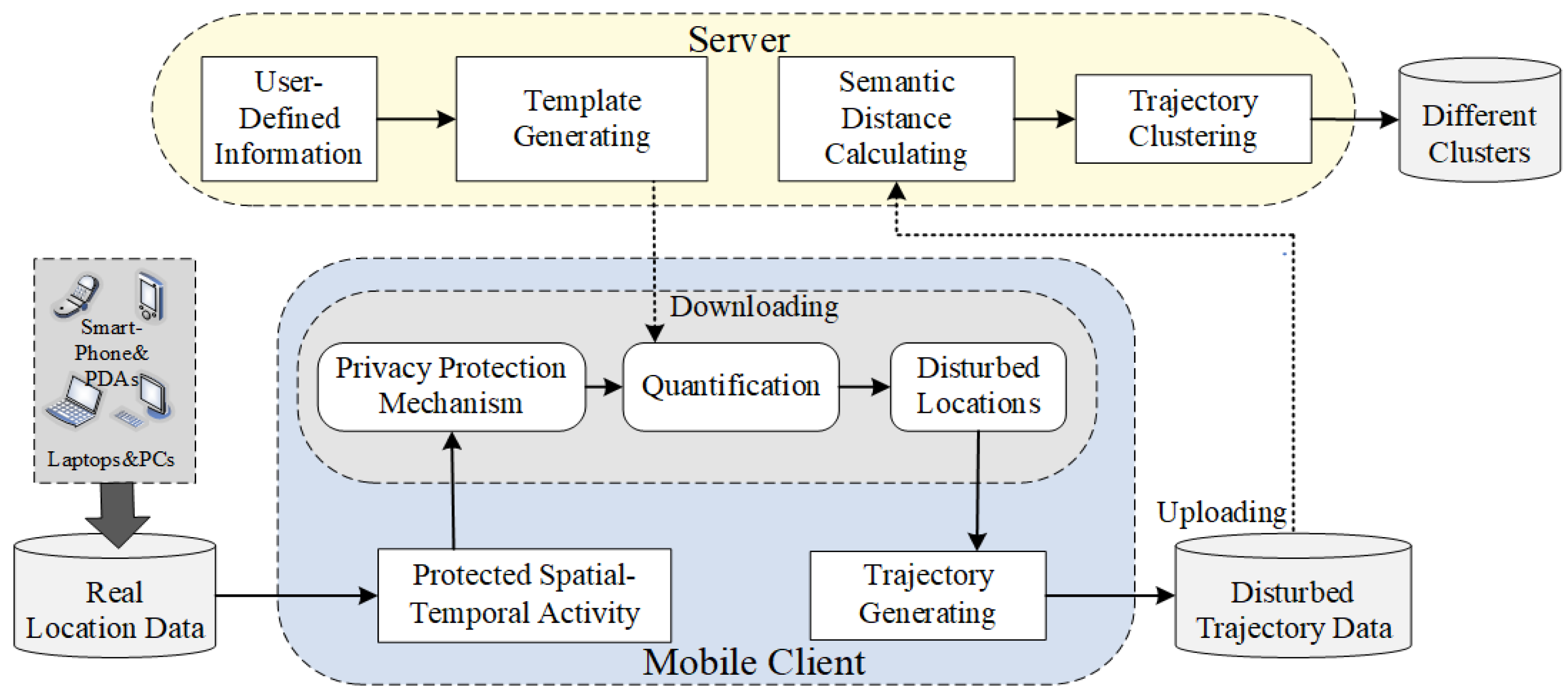
3. Overview of the DP-STTC Scheme
3.1. Problem Definition
3.2. Scheme Design
- (1)
- Acquiring a spatiotemporal activity template
- (2)
- Protecting spatiotemporal activity
- (3)
- Disturbed trajectory generation
- (4)
- Trajectory clustering
3.3. Attack Hypothesis
4. Models and Algorithms
4.1. Mobile Inference Models and -Location Set
4.2. Spatial-Temporal Activity Privacy Protection Mechanism
| Algorithm 1. Improved Spatial-Temporal Activity Privacy Protection Algorithm |
| Input: Actual Location , , LPPM, , Output: Disturbed location 1: if t in then 2: for t in do 3: generate disturbed location from real location with LPPM; 4: while -spatiotemporal activity privacy is not satisfied do 5: adjusting privacy parameters and generate ; 6: end while 7: release 8: end for 9: else 10: generate disturbed location from real location with LPPM; 11: release ; 12: end if |
4.3. Spatial-Temporal Activity Privacy Protection Mechanism
4.4. Disturbed Trajectory Generation
| Algorithm 2. Disturbed Trajectory Generation |
| Input: Disturbed location Output: Disturbed trajectory 1: Initialize ; Location collection 2: add into Location collection ; 3: sorting in chronological order throughout the day; 4: for in do 5: add into ; 6: end for 7: Return |
4.5. Trajectory Clustering
| Algorithm 3. Trajectory Clustering |
| Input: Trajectory sequences set Output: Trajectory clusters set 1: Define is the length of trajectory sequence, is the number of common sub-sequence between two trajectories 2: l = 0; 3: for i in do 4: for j in do 5: ; 6: for j in do 7: l = l + 1; 8: end for 9: 10: if then 11: Put into ; 12: else if then 13: Put into ; 14: else if then 15: Create , Put into ; 16: end if 17: end for 18: end for 19: Return |
5. Performance Evaluation
5.1. Experimental Setup
5.2. Evaluation Metrics
- (1)
- Precision
- (2)
- Recall
- (3)
- F1-Score
- (4)
- Relative Error
5.3. Experimental Results and Performance Analysis
- (1)
- Effect of percentages of training data
- (2)
- Effect of the number of discovered clusters
- (3)
- Effect of the number of positive clusters
- (4)
- Effect of the privacy budget
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yadav, V.K.; Andola, N.; Verma, S.; Venkatesan, S. P2LBS: Privacy Provisioning in Location-Based Services. IEEE Trans. Serv. Comput. 2023, 16, 466–477. [Google Scholar] [CrossRef]
- Jiang, H.B.; Li, J.; Zhao, P.; Zeng, F.Z.; Xiao, Z.; Klyengar, A. Location privacy-preserving mechanisms in location-based services: A comprehensive survey. ACM Comput. Surv. CSUR 2021, 54, 1–36. [Google Scholar] [CrossRef]
- Saia, R.; Podda, A.S.; Pompianu, L.; Reforgiato Recupero, D.; Fenu, G. A blockchain-based distributed paradigm to secure localization services. Sensors 2021, 21, 6814. [Google Scholar] [CrossRef] [PubMed]
- Liu, B.; Zhou, W.; Zhu, T.; Gao, L.; Xiang, Y. Location Privacy and Its Applications: A Systematic Study. IEEE Access 2018, 6, 17606–17624. [Google Scholar] [CrossRef]
- Kim, T.H.; Goyat, R.; Rai, M.K.; Kumar, G.; Thomas, R. A novel trust evaluation process for secure localization using a decentralized blockchain in wireless sensor networks. IEEE Access 2019, 7, 184133–184144. [Google Scholar] [CrossRef]
- Shi, X.F.; Tong, F.; Zhang, W.A.; Yu, L. Resilient privacy-preserving distributed localization against dishonest nodes in Internet of Things. IEEE Internet Things J. 2020, 7, 9214–9223. [Google Scholar] [CrossRef]
- Do, H.J.; Jeong, Y.-S.; Choi, H.-J.; Kwangjo, K. Another dummy generation technique in location-based services. In Proceedings of the 2016 International Conference on Big Data and Smart Computing, Hong Kong, China, 18–20 January 2016; pp. 532–538. [Google Scholar]
- Hara, T.; Suzuki, A.; Iwata, M.; Arase, Y.; Xie, X. Dummy-Based User Location Anonymization Under Real-World Constraints. IEEE Access 2016, 4, 673–687. [Google Scholar] [CrossRef]
- Andrés, M.E.; Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Geo-Indistinguishability: Differential Privacy for Location-Based Systems. In Proceedings of the ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 901–914. [Google Scholar]
- Ardagna, C.A.; Cremonini, M.; Vimercati, D.C.; Samarati, P. An Obfuscation-Based Approach for Protecting Location Privacy. IEEE Trans. Dependable Secur. Comput. 2011, 8, 13–27. [Google Scholar] [CrossRef]
- Hwang, R.-H.; Hsueh, Y.-L.; Chung, H.-W. A Novel Time-Obfuscated Algorithm for Trajectory Privacy Protection. IEEE Trans. Serv. Comput. 2014, 7, 126–139. [Google Scholar] [CrossRef]
- Zhu, E.; Ma, R. An Effective Partitional Clustering Algorithm Based on New Clustering Validity Index. Appl. Soft Comput. 2018, 71, 608–621. [Google Scholar] [CrossRef]
- Chen, J.; Yu, P.S. A Domain Adaptive Density Clustering Algorithm for Data with Varying Density Distribution. IEEE Trans. Knowl. Data Eng. 2021, 33, 2310–2321. [Google Scholar] [CrossRef]
- Jafarzadegan, M.; Safi-Esfahani, F.; Beheshti, Z. Combining Hierarchical Clustering Approaches Using the PCA Method. Expert Syst. Appl. 2019, 137, 1–10. [Google Scholar] [CrossRef]
- Lee, J.-G.; Han, J.; Whang, K.-Y. Trajectory Clustering: A Partition-and-Group Framework. In Proceedings of the ACM SIGMOD International Conference on Management of Data, Beijing, China, 11–14 June 2007; pp. 593–604. [Google Scholar]
- Cheng, Z.; Jiang, L.; Liu, D.; Zheng, Z. Density Based Spatio-Temporal Trajectory Clustering Algorithm. In Proceedings of the IEEE International Geoscience and Remote Sensing Symposium, Valencia, Spain, 22–27 July 2018; pp. 3358–3361. [Google Scholar]
- Wang, C.; Yang, J.; Zhang, J.-P. Privacy Preserving Algorithm Based on Trajectory Location and Shape Similarity. J. Commun. 2015, 36, 144–157. [Google Scholar]
- Qiao, D.; Liang, Y.; Ma, C.; Zhang, H. Semantic Trajectory Clustering via Improved Label Propagation with Core Structure. IEEE Sens. J. 2022, 22, 639–650. [Google Scholar] [CrossRef]
- Xu, C.; Zhu, L.; Liu, Y.; Guan, J.; Yu, S. DP-LTOD: Differential Privacy Latent Trajectory Community Discovering Services over Location-Based Social Networks. IEEE Trans. Serv. Comput. 2021, 14, 1068–1083. [Google Scholar] [CrossRef]
- Shaham, S.; Ding, M.; Liu, B.; Dang, S.; Lin, Z.; Li, J. Privacy Preserving Location Data Disturbed: A Machine Learning Approach. IEEE Trans. Knowl. Data Eng. 2021, 33, 3270–3283. [Google Scholar] [CrossRef]
- Kido, H.; Yanagisawa, Y.; Satoh, T. Protection of Location Privacy Using Dummies for Location-Based Services. In Proceedings of the 21st International Conference on Data Engineering Workshops (ICDEW’05), Tokyo, Japan, 3–4 April 2005; p. 1248. [Google Scholar]
- Gao, S.; Ma, J.; Shi, W.; Zhan, G.; Sun, C. TrPF: A Trajectory Privacy-Preserving Framework for Participatory Sensing. IEEE Trans. Inf. Forensics Secur. 2013, 8, 874–887. [Google Scholar] [CrossRef]
- Gruteser, M.; Liu, X. Protecting Privacy, in Continuous Location-Tracking Applications. IEEE Secur. Priv. 2004, 2, 28–34. [Google Scholar] [CrossRef]
- Dwork, C. Differential Privacy: A Survey of Results. In Theory and Applications of Models of Computation: Proceedings of the 5th International Conference, TAMC 2008, Xi’an, China, 25–29 April 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 4978, pp. 1–19. [Google Scholar]
- Hua, J.; Gao, Y.; Zhong, S. Differentially Private Publication of General Time-Serial Trajectory Data. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 549–557. [Google Scholar]
- Ou, L.; Qin, Z.; Liao, S.; Hong, Y.; Jia, X. Releasing Correlated Trajectories: Towards High Utility and Optimal Differential Privacy. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1109–1123. [Google Scholar] [CrossRef]
- Yang, Z.; Wang, R.; Wu, D.; Wang, H.; Song, H.; Ma, X. Local Trajectory Privacy Protection in 5G Enabled Industrial Intelligent Logistics. IEEE Trans. Ind. Inform. 2022, 18, 2868–2876. [Google Scholar] [CrossRef]
- Zheng, Z.; Li, Z.; Jiang, H.; Zhang, L.Y.; Tu, D. Semantic-Aware Privacy-Preserving Online Location Trajectory Data Sharing. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2256–2271. [Google Scholar] [CrossRef]
- Wu, L.; Qin, C.; Xu, Z.; Guan, Y.; Lu, R. TCPP: Achieving Privacy-Preserving Trajectory Correlation with Differential Privacy. IEEE Trans. Inf. Forensics Secur. 2023, 18, 4006–4020. [Google Scholar] [CrossRef]
- Chatzikokolakis, K.; Palamidessi, C.; Stronati, M. A Predictive Differentially-Private Mechanism for Mobility Traces. In Privacy Enhancing Technologies: Proceedings of the 14th International Symposium, PETS 2014, Amsterdam, The Netherlands, 16–18 July 2014; Springer: Cham, Switzerland, 2014; pp. 21–41. [Google Scholar]
- Xiao, Y.; Xiong, L. Protecting Locations with Differential Privacy under Temporal Correlations. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1298–1309. [Google Scholar]
- Wang, H.; Xu, Z. CTS-DP: Disturbed Correlated Time-Series Data via Differential Privacy. Knowl.-Based Syst. 2017, 122, 167–179. [Google Scholar] [CrossRef]
- Cao, Y.; Yoshikawa, M.; Xiao, Y.; Xiong, L. Quantifying Differential Privacy in Continuous Data Release Under Temporal Correlations. IEEE Trans. Knowl. Data Eng. 2019, 31, 1281–1295. [Google Scholar] [CrossRef]
- Ghane, S.; Kulik, L.; Ramamohanarao, K. TGM: A Generative Mechanism for Disturbed Trajectories with Differential Privacy. IEEE Internet Things J. 2020, 7, 2611–2621. [Google Scholar] [CrossRef]
- Dwork, C. Differential Privacy. In Automata, Languages and Programming: Proceedings of the 33rd International Colloquium, ICALP 2006, Venice, Italy, 10–14 July 2006; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4052, pp. 1–12. [Google Scholar]
- Cao, Y.; Xiao, Y.; Xiong, L.; Bai, L. PriSTE: From Location Privacy to Spatiotemporal Event Privacy. In Proceedings of the IEEE 35th International Conference on Data Engineering, Macao, China, 8–11 April 2019; pp. 1606–1609. [Google Scholar]
- Cao, Y.; Xiao, Y.X.; Xiong, L.; Bai, L.Q.; Yoshikawa, M. Protecting Spatiotemporal Event Privacy in Continuous Location-Based Services. IEEE Trans. Knowl. Data Eng. 2021, 33, 3141–3154. [Google Scholar] [CrossRef]
- Zheng, Y.; Xie, X.; Ma, W. GeoLife: A Collaborative Social Networking Service among User, location and trajectory. IEEE Data Eng. Bull. 2010, 33, 32–40. [Google Scholar]
- Zhu, L.; Xu, C.; Guan, J.; Zhang, H. SEM-PPA: A semantical pattern and preference-aware service mining method for personalized point of interest recommendation. J. Netw. Comput. Appl. 2017, 82, 35–46. [Google Scholar] [CrossRef]
- Zhu, L.; Liu, X.; Jing, Z.; Yu, L.; Cai, Z.; Zhang, J. Knowledge-Driven Location Privacy Preserving Scheme for Location-Based Social Networks. Electronics 2023, 12, 70. [Google Scholar] [CrossRef]
- Zhu, L.; Xie, H.; Liu, Y.; Guan, J.; Liu, Y.; Xiong, Y. PTPP: Preference-Aware Trajectory Privacy-Preserving over Location-Based Social Networks. J. Inf. Sci. Eng. 2018, 34, 803–820. [Google Scholar]
- Tang, L.-A.; Zheng, Y.; Yuan, J.; Han, J.; Leung, A.; Hung, C.-C.; Peng, W.-C. On discovery of traveling companions from streaming trajectories. In Proceedings of the IEEE 28th International Conference on Data Engineering, Arlington, VA, USA, 1–5 April 2012; pp. 186–197. [Google Scholar]
- Leskovec, J.; Lang, K.; Mahoney, M. Empirical comparison of algorithms for network community detection. In Proceedings of the 19th International World Wide Web Conference, Raleigh, NC, USA, 26–30 April 2010; pp. 631–640. [Google Scholar]
- Chen, R.; Acs, G.; Castelluccia, C. Differentially private sequential data publication via variable-length n-grams. In Proceedings of the ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; pp. 638–649. [Google Scholar]
- Chen, R.; Fung, B.; Desai, B.; Sossou, N.M. Differentially private transit data publication: A case study on the montreal transportation system. In Proceedings of the ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Beijing, China, 12–16 August 2012; pp. 213–221. [Google Scholar]
- Wang, Z.; Zhang, D.; Zhou, X.; Yang, D.; Yu, Z.; Yu, Z. Discovering and Profiling Overlapping Communities in Location-Based Social Networks. IEEE Trans. Syst. Man Cybern. Syst. 2014, 44, 499–509. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, L.; Lei, T.; Mu, J.; Mu, J.; Cai, Z.; Zhang, J. Differential Privacy-Based Spatial-Temporal Trajectory Clustering Scheme for LBSNs. Electronics 2023, 12, 3767. https://doi.org/10.3390/electronics12183767
Zhu L, Lei T, Mu J, Mu J, Cai Z, Zhang J. Differential Privacy-Based Spatial-Temporal Trajectory Clustering Scheme for LBSNs. Electronics. 2023; 12(18):3767. https://doi.org/10.3390/electronics12183767
Chicago/Turabian StyleZhu, Liang, Tingting Lei, Jinqiao Mu, Jingzhe Mu, Zengyu Cai, and Jianwei Zhang. 2023. "Differential Privacy-Based Spatial-Temporal Trajectory Clustering Scheme for LBSNs" Electronics 12, no. 18: 3767. https://doi.org/10.3390/electronics12183767
APA StyleZhu, L., Lei, T., Mu, J., Mu, J., Cai, Z., & Zhang, J. (2023). Differential Privacy-Based Spatial-Temporal Trajectory Clustering Scheme for LBSNs. Electronics, 12(18), 3767. https://doi.org/10.3390/electronics12183767





