A Quantum-Inspired Ant Colony Optimization Approach for Exploring Routing Gateways in Mobile Ad Hoc Networks
Abstract
:1. Introduction
2. Related Works
3. The Suggested QACO-Based GW Discovery Approach
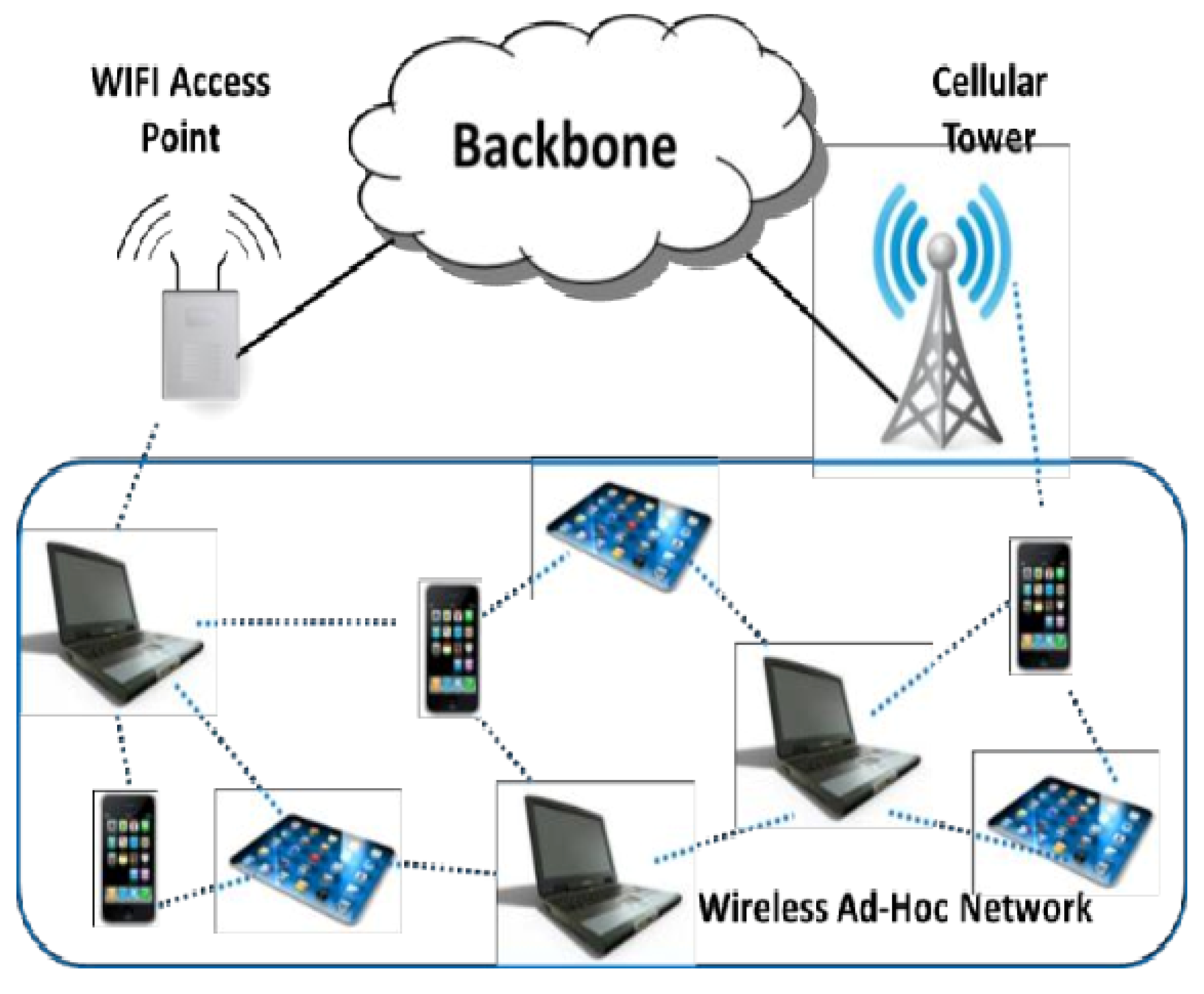
3.1. Offloading Phase
3.2. Reactive Phase
3.3. The Proactive Phase
| Algorithm 1: Initialization |
| K → Number of iterations constant; n → Total possible routes; → Weights along each path; Path encoding qubit count → Qubits corresponding to paths; → Supplementary qubits d → Pheromone distribution encoding qubit count; → Quantum bits for encoding pheromone distribution; → Classical register count for measurement purposes; Set → The qubits along x encoded pathways are quantum superposed. |
| Algorithm 2: Ant _Execute ( ) |
| While I in (0; n − 1) do If then do If then ; End End ; ; While , do If then End End End End ; Call Algorithm 3: Update_ Pheromone ( ) Reset ; Reset ; |
| Algorithm 3: Update_ Pheromone ( ) |
| ; Call Algorithm 4: Pheromone_ Deposition ( ) ; ; Call Algorithm 5: Pheromone_ Evaporation ( ) |
| Algorithm 4: Pheromone_ Deposition ( ) |
While ; End |
| Algorithm 5: Pheromone_ Evaporation ( ) |
; While ; End |
| Algorithm 6: QACO Procedure |
| Call Algorithm 1: Initialization While do Call Algorithm 2: Ant _Execute ( ) End ; , //Target phase-shifting for the best achievable route //Quantum Amplitude Amplification //global path convergence measurement |
4. Results
5. Conclusions
6. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Prasanna, Y.L.; Reddy, P.C. Analysis of AntHocNet and AODV performance using NS2. Int. J. Cybern. Inform. 2015, 4, 89–98. [Google Scholar]
- Anjum, S.S.; Noor, R.M.; Anisi, M.H. Review on MANET based communication for search and rescue operations. Wirel. Pers. Commun. 2015, 94, 31–52. [Google Scholar] [CrossRef]
- Hu, Y.; He, W.; Wei, H.; Yang, S.; Zhou, Y. Multi-Gateway multi-path routing protocol for 802.11 s WMN. In Proceedings of the 6th IEEE International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Niagara Falls, NY, USA, 11–13 October 2010; pp. 308–315. [Google Scholar]
- Shobana, M.; Karthik, S. A Performance analysis and comparison of various routing protocols in MANET. In Proceedings of the International Conference on Pattern Recognition, Informatics and Mobile Engineering (PRIME), Salem, India, 21–22 February 2013; pp. 391–393. [Google Scholar]
- Sharma, A.; Kumar, R. Performance comparison and detailed study of AODV, DSDV, DSR, TORA and OLSR routing protocols in Ad-Hoc networks. In Proceedings of the 4th IEEE International Conference on Parallel, Distributed and Grid Computing (PDGC), Waknaghat, India, 22–24 December 2016; pp. 732–738. [Google Scholar]
- Lei, D.; Wang, T.; Li, J. Performance analysis and comparison of routing protocols in mobile Ad-Hoc network. In Proceedings of the 5th IEEE International Conference on Instrumentation and Measurement, Computer, Communication and Control (IMCCC), Qinhuangdao, China, 18–20 September 2015; pp. 1533–1536. [Google Scholar]
- Ismail, Z.; Hassan, R. Performance of AODV routing protocol in mobile Ad-Hoc network. In Proceedings of the IEEE International Symposium on Information Technology, Kuala Lumpur, Malaysia, 15–17 June 2010; pp. 1–5. [Google Scholar]
- Soni, S.J.; Shah, J.S. Evaluating performance of OLSR routing protocol for multimedia traffic in MANET using NS2. In Proceedings of the 5th IEEE International Conference on Communication Systems and Network Technologies, Gwalior, India, 4–6 April 2015; pp. 225–229. [Google Scholar]
- Nataraju, A.B.; Maheshappa, H.D.; Devkatte, A. Performance analysis of HWMP protocol for wireless mesh networks using NS3. In Proceedings of the IEEE Region 10 Conference (TENCON), Singapore, 22–25 November 2016; pp. 1593–1598. [Google Scholar]
- Bari, S.M.S.; Anwar, F.; Masud, M.H. Performance study of hybrid wireless mesh protocol (HWMP) for IEEE 802.11s WLAN mesh networks. In Proceedings of the IEEE International Conference on Computer and Communication Engineering (ICCCE), Kuala Lumpur, Malaysia, 3–5 July 2012; pp. 712–716. [Google Scholar]
- Singh, M.; Lee, S.G.; Lee, H. Non-root-based hybrid wireless mesh protocol for wireless mesh networks. Int. J. Smart Home 2013, 7, 71–84. [Google Scholar]
- Saleem, M.; di Caro, G.A.; Farooq, M. Swarm intelligence-based routing protocol for wireless sensor networks: Survey and future directions. Inf. Sci. 2011, 181, 4597–4624. [Google Scholar] [CrossRef]
- Gui, T.; Ma, C.; Wang, F.; Wilkins, D.E. Survey on swarm intelligence-based routing protocols for wireless sensor networks: An extensive study. In Proceedings of the IEEE International Conference on Industrial Technology (ICIT), Taipei, Taiwan, 14–17 March 2016; pp. 1944–1949. [Google Scholar]
- Ali, Z.; Shahzad, W. Analysis of routing protocols in Ad-Hoc and sensor wireless networks based on swarm intelligence. Int. J. Netw. Commun. 2013, 3, 1–11. [Google Scholar]
- Shaik, S.; Reddy, P.C. An evaluation study of Ant-Hoc-Net. Int. J. Netw. Syst. 2013, 2, 53–57. [Google Scholar]
- Harinakshi, C.; Khan, R.Z. Advanced Ant-Hoc-Net protocol for mobile Ad-Hoc networks. Int. J. Eng. Sci. Comput. 2016, 6, 6246–6250. [Google Scholar]
- Habboush, A.K. Ant Colony Optimization (ACO) based MANET routing protocols: A comprehensive review. Comput. Inf. Sci. 2019, 12, 82–92. [Google Scholar] [CrossRef]
- Lyridis, D.V. An improved ant colony optimization algorithm for unmanned surface vehicle local path planning with multi-modality constraints. Ocean Eng. 2021, 241, 109890. [Google Scholar] [CrossRef]
- An, L.; Song, X.; Ning, T. An improved quantum ant colony algorithm for fuzzy dynamic vehicle routing problem. In Proceedings of the IEEE 9th International Conference on Computer Science and Network Technology, Dalian, China, 22–24 October 2021; pp. 22–25. [Google Scholar]
- Oh, E.; Lee, H. Effective route generation framework using quantum mechanism-based multi-directional and parallel ant colony optimization. Comput. Ind. Eng. 2022, 169, 108308. [Google Scholar] [CrossRef]
- Das, M.; Roy, A.; Maity, S.; Kar, S. A Quantum-inspired Ant Colony Optimization for solving a sustainable four-dimensional traveling salesman problem under type-2 fuzzy variable. Adv. Eng. Inform. 2023, 55, 101816. [Google Scholar] [CrossRef]
- Sureshkumar, A.; Ellappan, V.; Manivel, K. A comparison analysis of DSDV and AODV routing protocols in mobile Ad-Hoc networks. In Proceedings of the IEEE Conference on Emerging Devices and Smart Systems (ICEDSS), Tiruchengode, India, 3–4 March 2017; pp. 234–237. [Google Scholar]
- Patel, D.N.; Patel, S.B.; Kothadiya, H.R.; Jethwa, P.D.; Jhaveri, R.H. A survey of reactive routing protocols in MANET. In Proceedings of the IEEE International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; pp. 1–6. [Google Scholar]
- Ahmed, F.; Rahim, M.S. Performance investigation on two-classes of MANET routing protocols across various mobility models with QOS constraints. Int. J. Comput. Netw. Commun. 2011, 3, 197–215. [Google Scholar] [CrossRef]
- Kumar, A.; Hans, R. Performance analysis of DSDV, I-DSDV, OLSR, ZRP proactive routing protocol in mobile Ad-Hoc networks in IPv6. Int. J. Adv. Sci. Technol. 2015, 77, 25–36. [Google Scholar] [CrossRef]
- Patel, B.; Srivastava, S. Performance analysis of zone routing protocols in mobile Ad-Hoc networks. In Proceedings of the IEEE National Conference on Communications (NCC), Chennai, India, 29–31 January 2010; pp. 1–5. [Google Scholar]
- Gandhi, S.; Chaubey, N.; Shah, P.; Sadhwani, M. Performance evaluation of DSR, OLSR and ZRP protocols in MANETs. In Proceedings of the IEEE International Conference on Computer Communication and Informatics, Coimbatore, India, 10–12 January 2012; pp. 1–5. [Google Scholar]
- Yang, K.; Ma, J.; Miao, Z. Hybrid routing protocol for wireless mesh network. In Proceedings of the IEEE International Conference on Computational Intelligence and Security, Beijing, China, 11–14 December 2009; pp. 547–551. [Google Scholar]
- Liu, X. Routing protocols based on ant colony optimization in wireless sensor networks: A survey. IEEE Access 2017, 5, 26303–26317. [Google Scholar] [CrossRef]
- Gupta, A.K.; Sadawarti, H.; Verma, A.K. MANET routing protocols based on ant colony optimization. Int. J. Model. Optim. 2012, 2, 42–49. [Google Scholar] [CrossRef]
- Zhang, H.; Wang, X.; Memarmoshrefi, P.; Hogrefe, D. A survey of ant colony optimization-based routing protocols for mobile Ad-Hoc Networks. IEEE Access 2017, 5, 24139–24161. [Google Scholar] [CrossRef]
- Fathima, K.S.A.; Sindhanaiselvan, K. Ant colony optimization based routing in wireless sensor networks. Int. J. Adv. Netw. Appl. 2013, 4, 1686–1689. [Google Scholar]
- Zhang, M.; Yang, M.; Wu, Q.; Zheng, R.; Zhu, J. Smart perception and autonomic optimization: A novel bio-inspired hybrid routing protocol for MANET. Future Gener. Comput. Syst. 2017, 81, 505–513. [Google Scholar] [CrossRef]
- Sarkar, D.; Choudhury, S.; Majumder, A. Enhanced-Ant-AODV for optimal route selection in mobile ad-hoc network. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 1186–1201. [Google Scholar] [CrossRef]
- Taraka, N.; Emani, A. Routing in Ad Hoc Networks Using Ant Colony Optimization. In Proceedings of the IEEE International Conference on Intelligent Systems, Modelling and Simulation, Langkawi, Malaysia, 27–29 January 2014; pp. 546–550. [Google Scholar]
- Rahman, S.U.; Nam, J.C.; Khan, A.; Cho, Y. Improved AntHocNet with bidirectional path setup and loop avoidance. J. Korean Inst. Commun. Inf. Sci. 2017, 42, 64–76. [Google Scholar] [CrossRef] [Green Version]
- Brill, C.; Nash, T. A comparative analysis of MANET routing protocols through simulation. In Proceedings of the IEEE International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 244–247. [Google Scholar]
- Li, F.; Liu, M.; Xu, G. A quantum ant colony multi-objective routing algorithm in WSN and its application in a manufacturing environment. Sensors 2019, 19, 3334. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Du, Z.; Lu, F.; Wang, S.; Wang, L. Vehicle scheduling model and optimization of crowdsourcing logistics distribution. J. Northeast. Univ. (Nat. Sci.) 2021, 42, 1210–1216. [Google Scholar]
- Yan, T.; Lu, F.; Wang, S.; Wang, L.; Bi, H. A hybrid metaheuristic algorithm for the multi-objective location-routing problem in the early post-disaster stage. J. Ind. Manag. Optim. 2023, 19, 4663–4691. [Google Scholar] [CrossRef]
- Nayyar, A. Improvised Energy Efficient Routing Protocol Based on Ant Colony Optimization (ACO) for Wireless Sensor Networks. Ph.D. Thesis, Department of Computer Science, Desh Bhagat University, Mandi Gobindgarh, India, 2017. [Google Scholar]
- Lu, F.; Feng, W.; Gao, M.; Bi, H.; Wang, S. The fourth-party logistics routing problem using ant colony system-improved grey wolf optimization. J. Adv. Transp. 2020, 2020, 8831746. [Google Scholar] [CrossRef]
- Lu, F.; Bi, H.; Huang, M.; Duan, S. Simulated annealing genetic algorithm based schedule risk management of IT outsourcing project. Math. Probl. Eng. 2017, 2017, 6916575. [Google Scholar] [CrossRef] [Green Version]
- Ghosh, M.; Dey, N.; Mitra, D.; Chakrabarti, A. A novel quantum algorithm for ant colony optimization. IET Quantum Commun. 2022, 3, 13–29. [Google Scholar] [CrossRef]
- Ducatelle, F.; di Caro, G.A.; Gambardella, L.M. Using ant agents to combine reactive and proactive strategies for routing in mobile Ad-Hoc network. Int. J. Comput. Intell. Appl. 2005, 5, 169–184. [Google Scholar] [CrossRef] [Green Version]
- Tong, M.; Chen, Y.; Chen, F.; Wu, X. An energy-efficient multi-path routing algorithm based on ant colony optimization for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 642189. [Google Scholar] [CrossRef] [Green Version]
- Ghawy, M.; Amran, G.; AlSalman, H.; Ghaleb, E.; Khan, J.; Al-Bakhrani, A.; Alziadi, A.; Ali, A.; Ullah, S. An Effective wireless sensor network routing protocol based on particle swarm optimization algorithm. Wirel. Commun. Mob. Comput. 2022, 2022, 8455065. [Google Scholar] [CrossRef]
- Alameri, I. A novel approach to comparative analysis of legacy and nature inspired ant colony optimization based routing protocol in MANET. J. Southwest Jiaotong Univ. 2019, 54, 1–10. [Google Scholar] [CrossRef]
- Zungeru, A.; Ang, L.; Seng, K. Classical and swarm intelligence based routing protocols for wireless sensor networks: A survey and comparison. J. Netw. Comput. Appl. 2012, 35, 1508–1536. [Google Scholar] [CrossRef]
- Zahedi, Z.; Akbari, R.; Shokouhifar, M.; Safaei, F.; Jalali, A. Swarm intelligence based fuzzy routing protocol for clustered wireless sensor networks. Expert Syst. Appl. 2016, 55, 313–328. [Google Scholar] [CrossRef]
- Bhatia, T.; Kansal, S.; Goel, S.; Verma, A. A genetic algorithm based distance-aware routing protocol for wireless sensor networks. Comput. Electr. Eng. 2016, 56, 441–455. [Google Scholar] [CrossRef]
- Benmansour, F.; Labraoui, N. A comprehensive review on swarm intelligence-based routing protocols in wireless multimedia sensor networks. Int. J. Wirel. Inf. Netw. 2021, 28, 175–198. [Google Scholar] [CrossRef]
| Classification | Algorithm-Based | Multi-Path Multi-GW | Advantages | Disadvantages | |
|---|---|---|---|---|---|
| AODV | Reactive | Non-root | Single-path Single-GW | 1- Low routing overhead over time 2- Widely used and easy to implement | 1- Single-path single-GW 2- No mechanism to find new GW 3- Packet delivery, and node energy need improvement |
| AODV-UU | Reactive | Non-root | Single-path Single-GW | 1- Supports IPv6 | 1- Same as AODV except supports IPv6 |
| AOMDV | Reactive | Non-root | Multi-path Multi-GW | 1- Supports multi-path data transmission | 1- Same as AODV except supporting multi-path 2- Increase the routing overhead |
| DSDV and I-DSDV | Proactive | Non-root and broadcast | Single-path Single-GW | 1- A table-driven routing protocol 2- Suitable for a small number of nodes | 1- Needs enhancement in end-to-end delay 2- Increases the broadcast caused by periodically routing updates sent by each node 3- Single-path single-GW |
| OLSR | Proactive | Non-root and broadcast | Single-path Single-GW | 1- A table-driven routing protocol 2- Better in end-to-end delay and packet delivery | 1- Increase the broadcast caused by periodically routing updates sent by each node 2- Requires more bandwidth 3- Single-path single-GW |
| ZRP, IZRP, TZRP and FZRP | Hybrid | Non-root and Broadcast with zone separation | Single-path Single-GW | 1- Divided the network to zones 2- Decreases the quantity of communication overhead 3- Works well with a large number of zones | 1- In a small number of zones behaves like reactive protocols 2- Creates overlapping zones 3- Single-path single-GW |
| HWMP | Hybrid | Tree-based | Single-path Single-GW | 1- Addresses mobility using tree-based routing and on-demand routing. | 1- Due to unreliable connection, requires frequent route reconstruction. 2- The tree-based proactive mode creates a root node bottleneck 3- Single-path single-GW |
| MGMP | Hybrid | Tree-based | Multi-path Multi-GW | 1- It seeks many paths in order to address the shortcomings HWMP | 1- Built-in tree-based method causes a bottleneck to the root node and more broadcast |
| Ant-AODV | Reactive | AODV and ACO | Single-path Single-GW | 1- Developed to overcome the limitations of AODV | 1- Still single-path single-GW |
| Ant-DSR | Reactive | DSR and ACO | Single-path Single-GW | 1- Developed to overcome the limitations of DSR and DSDV | 1- Still single-path single-GW |
| HOPNET | Hybrid | ACO and zones | Single-path Single-GW | 1- Developed to overcome the limitations of ZRP | 1- Still single-path single-GW |
| B-iHTRP | Hybrid | ACO, PAO and zones | Single-path Single-GW | 1- It is committed to combining the advantages of both ACO and PAO in order to boost effective efficiency | 1- It does not consider the actual mobility model of nodes that do not fit into the real MANET environment 2- Single-path single-GW |
| AntHocNet | Hybrid | ACO | Multi-path Multi-GW | 1- Low network overhead 2- Fast network discovery 3- Multi-path multi-GW | 1- Suffer from looping in some scenarios 2- Large energy consumption |
| QACMOR | Proactive | QACO | Optimal Path | 1- It is committed to combining the advantages of both ACO and quantum computing in order to select the best route. | 1- Single path (best route) |
| Parameter | Value |
|---|---|
| 1- Area | 1000 × 1000 m |
| 2- No of nodes | 100, 100+ |
| 3- No of GWs | 10 to 30 |
| 4- Radio type | 802.11 b |
| 5- Data Rate | 2 Mbps |
| 6- Channel frequency | 2.4 GHz |
| 7- No. of channel | 1 |
| 8- Antenna model | Omni-directional |
| 9- Application type | HTTP and video streaming |
| 10- Packet size (byte) | 512 |
| 11- Simulation time | 5, 10, 50, 100, and 500 s |
| Routing Protocols | Discovery Times (s) |
|---|---|
| AODV Protocol | 0.53 |
| HWMP Protocol | 0.55 |
| AntHocNet Protocol (ACO-based routing) | 0.51 |
| Proposed Protocol (QACO-based routing) | 0.39 |
| Routing Protocols | Discovery Times of All Newly Connected GWs (s) | |||
|---|---|---|---|---|
| 1 GW | 3 GWs | 5 GWs | 10 GWs | |
| AODV Protocol | 1.00 | 2.00 | 2.50 | 2.95 |
| HWMP Protocol | 0.65 | 0.64 | 0.67 | 0.68 |
| AntHocNet Protocol(ACO) | 0.72 | 0.73 | 0.75 | 0.79 |
| Proposed Protocol (QACO) | 0.50 | 0.39 | 0.40 | 0.41 |
| Routing Protocols | Discovery Times (s) |
|---|---|
| AODV Protocol | 0.53 |
| HWMP Protocol | 0.30 |
| AntHocNet Protocol (ACO) | 0.50 |
| Proposed Protocol (QACO) | 0.07 |
| Routing Protocols | Routing Overhead % | ||||
|---|---|---|---|---|---|
| 5 s | 10 s | 50 s | 100 s | 500 s | |
| AODV Protocol | 16 | 11 | 9 | 10 | 11 |
| HWMP Protocol | 21 | 18 | 19 | 19 | 18 |
| AntHocNet Protocol (ACO) | 18 | 13 | 12 | 13 | 14 |
| Proposed Protocol (QACO) | 18 | 12 | 8 | 6 | 6 |
| Routing Protocols | Gateway Overhead % | ||||
|---|---|---|---|---|---|
| 5 s | 10 s | 50 s | 100 s | 500 s | |
| AODV Protocol | 21 | 23 | 22 | 19 | 19 |
| HWMP Protocol | 23 | 16 | 14 | 14 | 15 |
| AntHocNet Protocol (ACO) | 21 | 23 | 18 | 17 | 17 |
| Proposed Protocol (QACO) | 4 | 3 | 5 | 4 | 4 |
| Tracing Parameter (s) | Result |
|---|---|
| 1- Initial discovery time | 0.93 |
| 2- Time to discover GWs | 1 GW = 0.5, 3 GWs = 0.39, 5 GWs = 0.40, and 10 GWs = 0.41 |
| 3- Time of new node to discover GWs | 0.07 |
| 4- Routing overhead over simulation running time | 18% in 5, 10% in 10, 8% in 50, 6% in 100, and 6% in 500 s |
| 5- Gateway’s overhead over simulation running time | 4% in 5, 3% in 10, 5% in 50, 4% in 100, and 4% in 500 s |
| Routing Protocols | Routing Overhead % | ||||
|---|---|---|---|---|---|
| 100 Node | 200 Node | 300 Node | 400 Node | 500 Node | |
| GA_HocNet Protocol | 10 | 13 | 17 | 22 | 27 |
| PSO_HocNet Protocol | 8 | 10 | 14 | 18 | 20 |
| ABC_HocNet Protocol | 7 | 8 | 12 | 16 | 17 |
| QACO_HocNet Protocol | 5 | 6 | 9 | 14 | 15 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khudair Madhloom, J.; Abd Ali, H.N.; Hasan, H.A.; Hassen, O.A.; Darwish, S.M. A Quantum-Inspired Ant Colony Optimization Approach for Exploring Routing Gateways in Mobile Ad Hoc Networks. Electronics 2023, 12, 1171. https://doi.org/10.3390/electronics12051171
Khudair Madhloom J, Abd Ali HN, Hasan HA, Hassen OA, Darwish SM. A Quantum-Inspired Ant Colony Optimization Approach for Exploring Routing Gateways in Mobile Ad Hoc Networks. Electronics. 2023; 12(5):1171. https://doi.org/10.3390/electronics12051171
Chicago/Turabian StyleKhudair Madhloom, Jamal, Hussein Najm Abd Ali, Haifaa Ahmed Hasan, Oday Ali Hassen, and Saad Mohamed Darwish. 2023. "A Quantum-Inspired Ant Colony Optimization Approach for Exploring Routing Gateways in Mobile Ad Hoc Networks" Electronics 12, no. 5: 1171. https://doi.org/10.3390/electronics12051171
APA StyleKhudair Madhloom, J., Abd Ali, H. N., Hasan, H. A., Hassen, O. A., & Darwish, S. M. (2023). A Quantum-Inspired Ant Colony Optimization Approach for Exploring Routing Gateways in Mobile Ad Hoc Networks. Electronics, 12(5), 1171. https://doi.org/10.3390/electronics12051171









