PLC Cybersecurity Test Platform Establishment and Cyberattack Practice †
Abstract
1. Introduction
2. Related Works
3. Materials and Methods
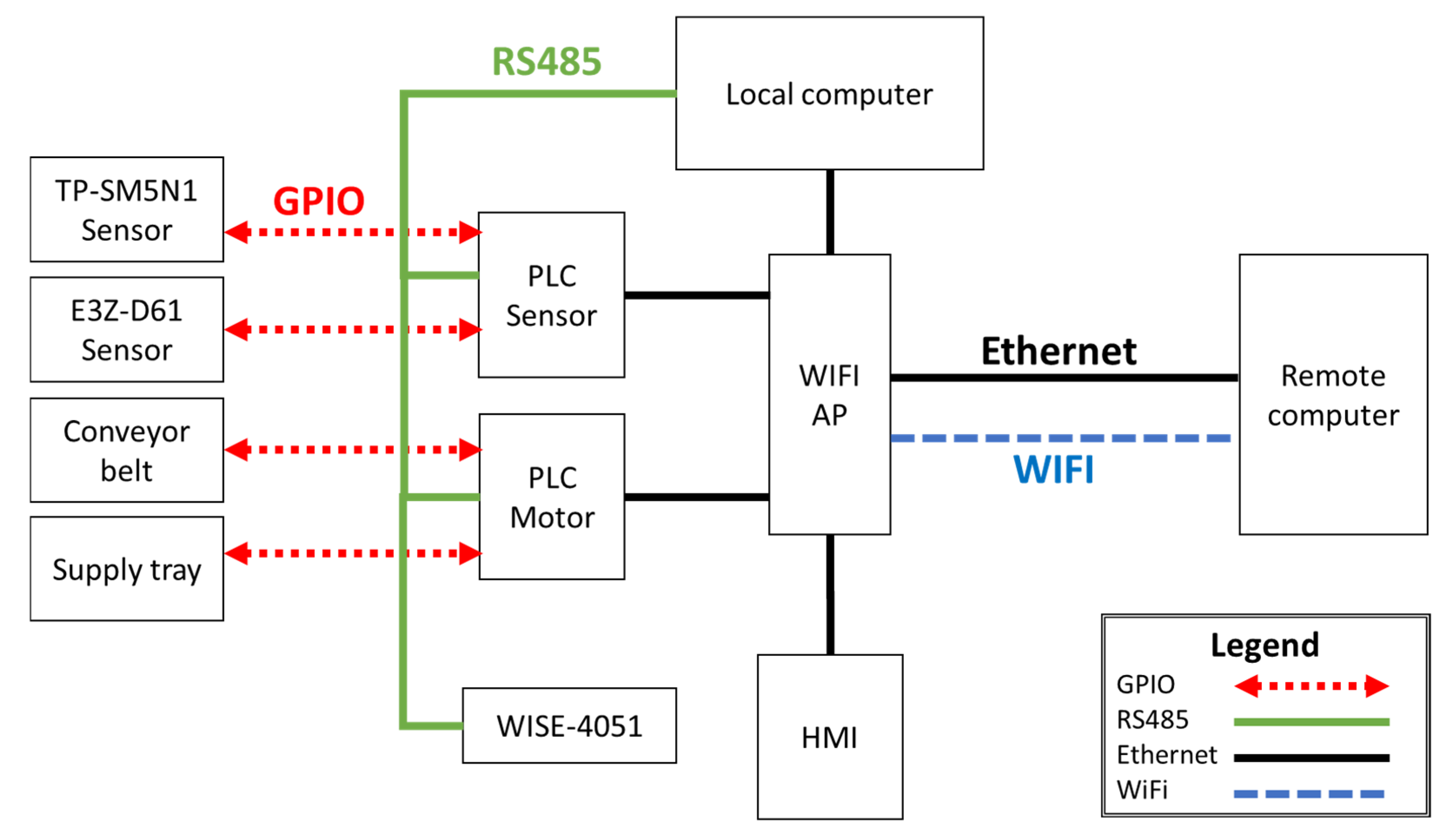
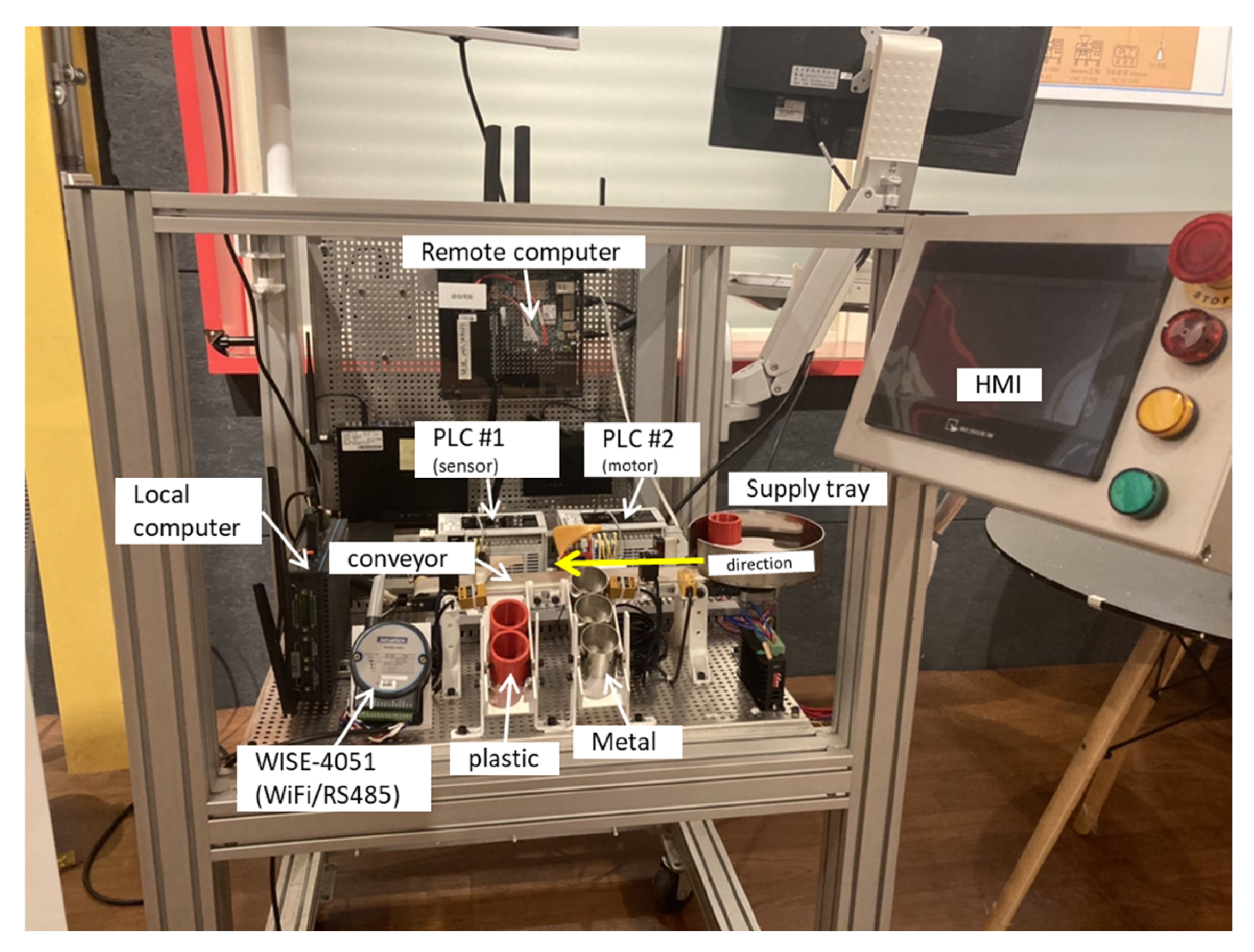
3.1. Automatic Conveyor (Test Platform)
3.2. Heterogeneous Industrial Networks
3.3. Protocol Stack
3.4. Software Toolset
3.5. System Network Architecture
3.6. PLC commands
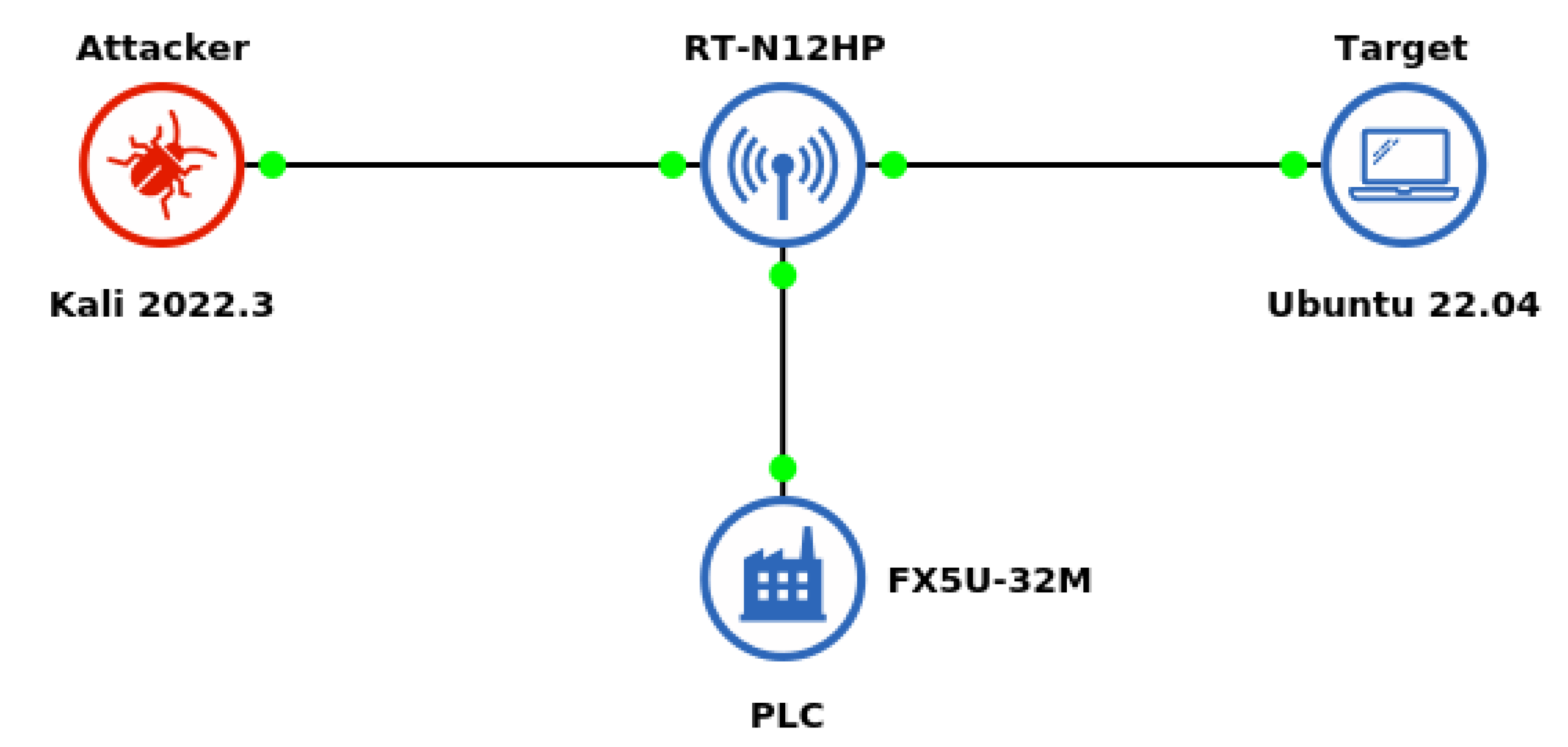
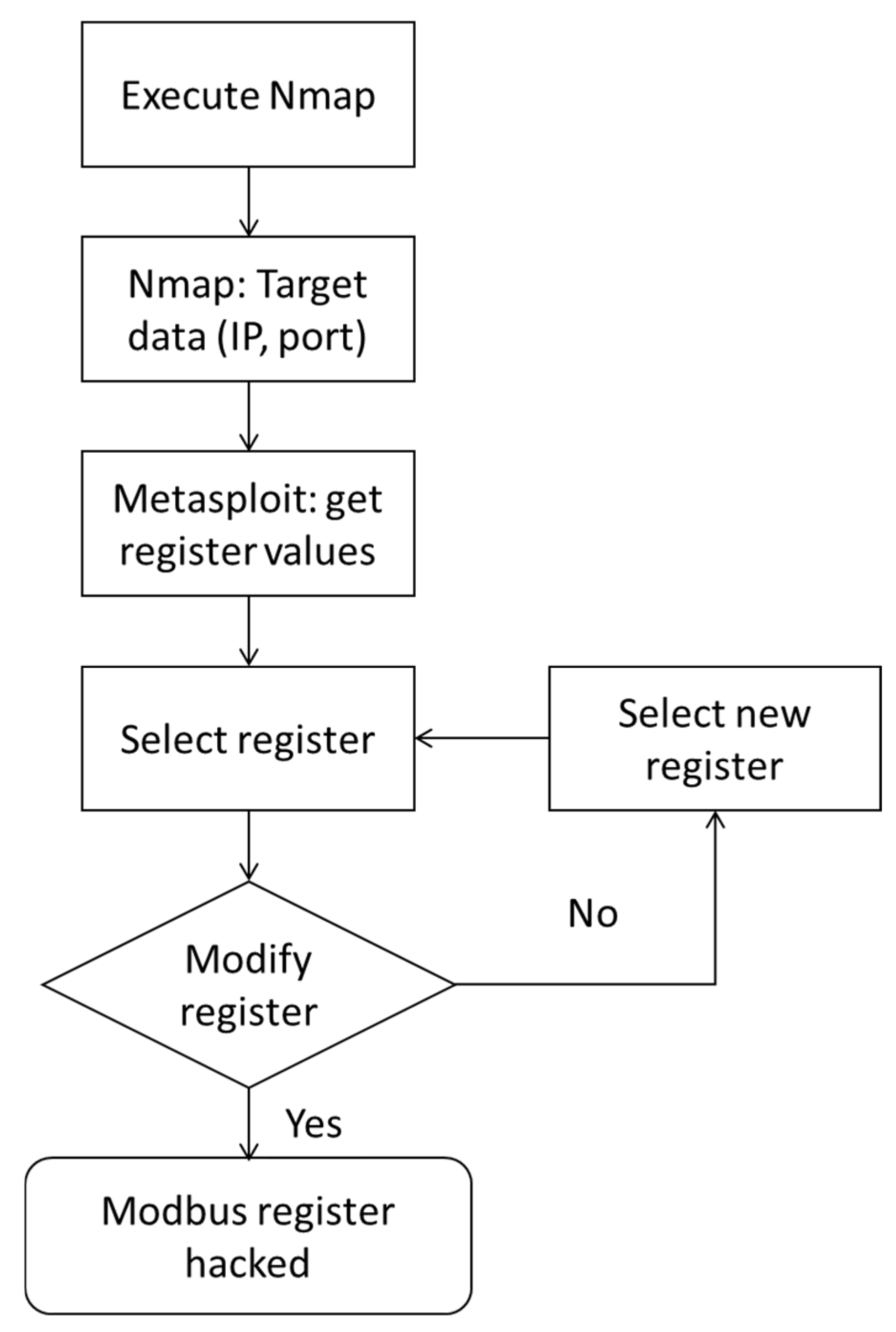
4. Attack Trials
4.1. Scanning I.P. and Ports (Nmap)
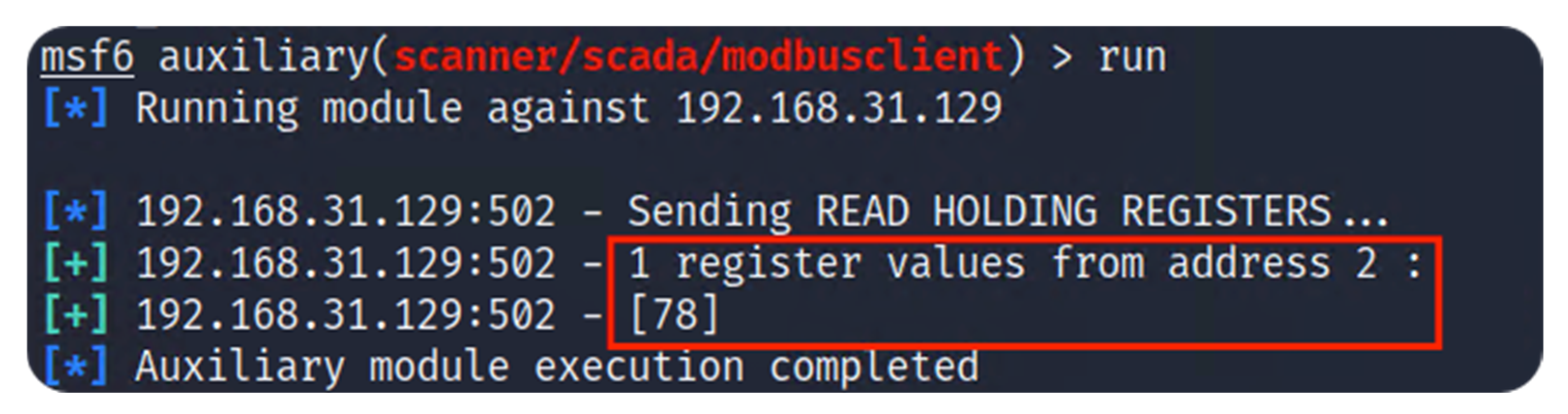
4.2. Obtain Register Values (Metasploit)
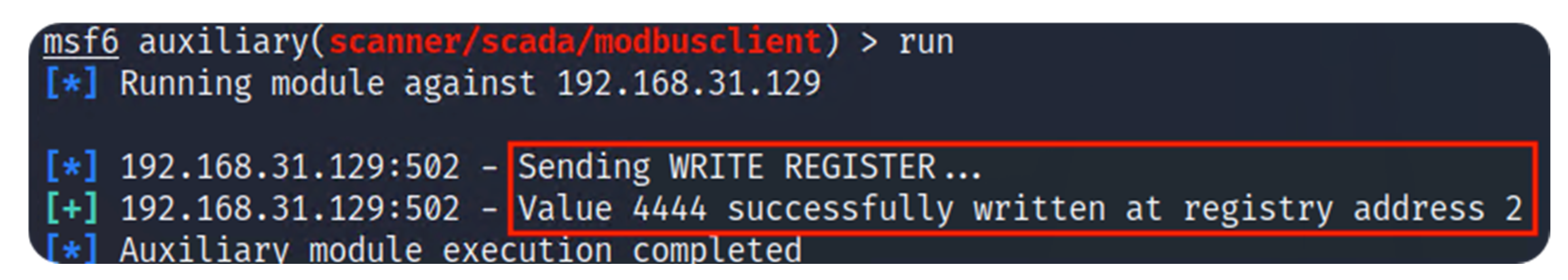
4.3. Modify Modbus Registers (Metasploit)
4.4. System Architecture for Training Purposes
5. Discussion
6. Conclusions
7. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption System |
| APT | Advanced Persistent Threat |
| DCS | Distributed Control System |
| ECC | Elliptic-Curve Cryptography |
| GPIO | General-Purpose Input/Output |
| HMI | Human-Machine Interface |
| I2C | Inter-Integrated Circuit |
| IACS | Industrial Automation and Control Systems |
| ICT | Information and Communication Technology |
| IDS | Intrusion Detection System |
| I.P. | Internet Protocol |
| IPS | Intrusion Prevention System |
| I.T. | Information Technology |
| LPWAN | Low-Power Wide Area Network |
| MITM | Man-in-the-middle |
| OPC UA | Open Platform Communications Unified Architecture |
| O.S. | Operating System |
| OSI | Open Systems Interconnection |
| PKI | Public Key Infrastructure |
| PLC | Programmable Logic Controller |
| SCADA | Supervisory Control and Data Acquisition |
| SLMP | Seamless Message Protocol |
| TCP | Transmission Control Protocol |
References
- Public Safety Canada. National Strategy of Critical Infrastructure; Public Safety Canada: Ottawa, ON, Canada, 2009; ISBN 978-1-100-11248-0. [Google Scholar]
- Congress.gov. H.R.3162-107th Congress (2001–2002): Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT ACT) Act of 2001. Available online: https://www.congress.gov/bill/107th-congress/house-bill/3162 (accessed on 26 October 2001).
- National Institute for Standards and Technology (NSIT). Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1; NSIT: Gaithersburg, MD, USA, 2018. [Google Scholar] [CrossRef]
- Trend Micro Inc. The State of Industrial Cybersecurity; Whitepaper, Trend Micro Survey Report; Trend Micro Inc.: Tokyo, Japan, 2022. [Google Scholar]
- International Telecommunication Union (ITU). Global Cybersecurity Index 2020; Whitepaper; ITU Publications: Geneva, Switzerland, 2022; ISBN 978-92-61-33921-0. [Google Scholar]
- Robinson, M.; Jones, K.; Janicke, H. Cyber Warfare: Issues and Challenges. Comput. Secur. 2015, 49, 70–94. [Google Scholar] [CrossRef]
- H1 2022–A Brief Overview of the Main Incidents in Industrial Cybersecurity|Kaspersky ICS CERT, Kaspersky ICS CERT|Kaspersky Industrial Control Systems Cyber Emergency Response Team. 2022. Available online: https://ics-cert.kaspersky.com/publications/reports/2022/09/08/h1-2022-a-brief-overview-of-the-main-incidents-in-industrial-cybersecurity/ (accessed on 19 September 2022).
- Dutta, N.; Jadav, N.; Tanwar, S.; Sarma, H.K.; Pricop, E. Introduction to cybersecurity. Stud. Comput. Intell. 2021, 995, 1–16. [Google Scholar] [CrossRef]
- Reed, T.C.; Bush, G. At the Abyss: An Insider’s History of the Cold War; Ballantine Books/Presido Press: New York, NY, USA, 2004; ISBN 0-89141-821-0. [Google Scholar]
- Obaidat, M.; Traore, I.; Woungang, I. Biometric-Based Physical and Cybersecurity Systems; Springer: Cham, Switzerand, 2019; ISBN 978-3-319-98734-7. [Google Scholar]
- Cybersecurity & Infrastructure Security Agency (CISA), APT Cybersecurity Tools Targeting ICS/SCADA Devices. Available online: https://www.cisa.gov/uscert/sites/default/files/publications/AA22-103A_APT_Cyber_Tools_Targeting_ICS_SCADA_Devices.pdf (accessed on 28 December 2022).
- Liu, C.-C.; Ten, C.-W.; Govindarasu, M. Cybersecurity of SCADA Systems: Vulnerability Assessment and Mitigation. In Proceedings of the 2009 IEEE/PES Power Systems Conference and Exposition, Seattle, WA, USA, 15–18 March 2009. [Google Scholar]
- Coates, G.M.; Hopkinson, K.M.; Graham, S.R.; Kurkowski, S.H. A trust system architecture for SCADA network security. IEEE Trans. Power Deliv. 2010, 25, 158–169. [Google Scholar] [CrossRef]
- Anh, P.D.; Chau, T.D. Component-based design for SCADA architecture. Int. J. Control. Autom. Syst. 2010, 8, 1141–1147. [Google Scholar] [CrossRef]
- Blanch-Torne, S.; Cores, F.; Chiral, R.M. Agent-based PKI for Distributed Control System. In Proceedings of the 2015 World Congress on Industrial Control Systems Security (WCICSS), London, UK, 14–16 December 2015. [Google Scholar]
- Pramod, T.C.; Thejas, G.S.; Iyengar, S.S.; Sunitha, N.R. CKMI: Comprehensive key management infrastructure design for industrial automation and control systems. Future Internet 2019, 11, 126. [Google Scholar]
- Rezai, A.; Keshavarzi, P.; Moravej, Z. Key management issue in SCADA Networks: A Review. Eng. Sci. Technol. Int. J. 2017, 20, 354–363. [Google Scholar] [CrossRef]
- Hahn, A.; Govindarasu, M. An evaluation of Cybersecurity Assessment Tools on a SCADA Environment. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011. [Google Scholar]
- Lu, Z.; Lu, Y.; Yuan, M.; Wang, Z. A Heterogeneous Large-Scale Parallel SCADA/DCS Architecture in 5G OGCE. In Proceedings of the 2017 10th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), Shanghai, China, 14–16 October 2017. [Google Scholar]
- Knowles, W.; Prince, D.; Hutchison, D.; Disso, J.F.; Jones, K. A survey of cyber security management in Industrial Control Systems. Int. J. Crit. Infrastruct. Prot. 2015, 9, 52–80. [Google Scholar] [CrossRef]
- Pliatsios, D.; Sarigiannidis, P.; Lagkas, T.; Sarigiannidis, A.G. A survey on SCADA systems: Secure protocols, incidents, threats, and Tactics. IEEE Commun. Surv. Tutor. 2020, 22, 1942–1976. [Google Scholar] [CrossRef]
- Ghosh, S.; Sampalli, S. A survey of security in SCADA networks: Current issues and future challenges. IEEE Access 2019, 7, 135812–135831. [Google Scholar] [CrossRef]
- Ghaleb, A.; Zhioua, S.; Almulhem, A. On PLC network security. Int. J. Crit. Infrastruct. Prot. 2018, 22, 62–69. [Google Scholar] [CrossRef]
- Hajda, J.; Jakuszewski, R.; Ogonowski, S. Security challenges in industry 4.0 PLC Systems. Appl. Sci. 2021, 11, 9785. [Google Scholar] [CrossRef]
- González, I.; Calderón, A.J.; Portalo, J.M. Innovative multi-layered architecture for heterogeneous automation and monitoring systems: Application case of a photovoltaic smart microgrid. Sustainability 2021, 13, 2234. [Google Scholar] [CrossRef]
- Jaloudi, S. Communication protocols of an industrial internet of things environment: A comparative study. Future Internet 2019, 11, 66. [Google Scholar] [CrossRef]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Role-Based Access Control Model in Modbus SCADA Systems. A Centralized Model Approach. Sensors 2019, 19, 4455. [Google Scholar] [CrossRef] [PubMed]
- Martins, T.; Oliveira, S.V. Enhanced Modbus/TCP security protocol: Authentication and authorization functions supported. Sensors 2022, 22, 8024. [Google Scholar] [CrossRef] [PubMed]
- Ma, R.; Cheng, P.; Zhang, Z.; Liu, W.; Wang, Q.; Wei, Q. Stealthy Attack Against Redundant Controller Architecture of Industrial Cyber-Physical System. IEEE Internet Things J. 2019, 6, 9783–9793. [Google Scholar] [CrossRef]
- Scapy, Scapy Is a Powerful Interactive Packet Manipulation Program. Available online: https://scapy.net/ (accessed on 8 October 2022).
- Hui, H.; McLaughlin, K.; Sezer, S. Vulnerability analysis of S7 PLCs: Manipulating the security mechanism. Int. J. Crit. Infrastruct. Prot. 2021, 35, 100470. [Google Scholar] [CrossRef]
- DRAGOS. Pipedream: Chernovite’s Emerging Malware Targeting Industrial Control Systems; Whitepaper; DRAGOS Inc.: Hanover, MD, USA, 2022. [Google Scholar]
- Ramirez, R.; Chang, C.-K.; Liang, S.-H. PLC cyber-security challenges in Industrial Networks. In Proceedings of the 2022 18th IEEE/ASME International Conference on Mechatronic and Embedded Systems and Applications (MESA), Taipei, Taiwan, 28–30 November 2022. [Google Scholar] [CrossRef]
- Dutta, N.; Jadav, N.; Tanwar, S.; Sarma, H.K.; Pricop, E. Design of a virtual cybersecurity lab. Stud. Comput. Intell. 2021, 995, 143–157. [Google Scholar] [CrossRef]
- Open-Source PLC Software. Available online: https://openplcproject.com/ (accessed on 31 January 2023).
- Roomi, M.M.; Ong, W.S.; Hussain, S.M.; Mashima, D. IEC 61850 compatible openplc for Cyber attack case studies on smart substation systems. IEEE Access 2022, 10, 9164–9173. [Google Scholar] [CrossRef]
- Network Mapper (Nmap). Available online: https://nmap.org/ (accessed on 31 January 2023).
- Wireshark. Available online: https://www.wireshark.org/ (accessed on 14 February 2023).
- Penetration Testing Software, PEN Testing Security. Available online: https://www.metasploit.com/ (accessed on 14 February 2023).
- Penetration Testing and Ethical Hacking Linux Distribution. Available online: https://www.kali.org/ (accessed on 14 February 2023).
- Kont, M.; Pihelgas, M.; Wojtkowiak, J.; Trinberg, L.; Osula, A.-M. Insider Threat Detection Study. NATO Cooperative Cyber Defence Centre of Excellence (CCD COE). 2014. Available online: https://ccdcoe.org/uploads/2018/10/Insider_Threat_Study_CCDCOE.pdf (accessed on 14 January 2023).
- Cybersecurity and Infrastructure Security Agency (CISA). Insider Threat Mitigation Guide Version 1.1; CISA: Arlington, VA, USA, 2020. Available online: https://www.cisa.gov/sites/default/files/publications/Insider%20Threat%20Mitigation%20Guide_Final_508.pdf (accessed on 31 January 2023).
- MELSEC IQ-F FX5 User’s Manual (Ethernet Communication). Mitsubishi Electric. 2022. Available online: https://dl.mitsubishielectric.com/dl/fa/document/manual/plcf/jy997d56201/jy997d56201r.pdf (accessed on 22 September 2022).
- Sen, S. A survey of intrusion detection systems using evolutionary computation. In Bio-Inspired Computation in Telecommunications; Morgan Kaufmann: Burlington, MA, USA, 2015; pp. 73–94. [Google Scholar] [CrossRef]
- Prashanth, S.K.; Shitharth, S.; Praveen Kumar, B.; Subedha, V.; Sangeetha, K. Optimal feature selection based on evolutionary algorithm for intrusion detection. SN Comput. Sci. 2022, 3, 439. [Google Scholar] [CrossRef]
- CISCO Systems. Snort. Available online: https://www.snort.org/ (accessed on 17 February 2023).



| Model | Test Platform Components | ||
|---|---|---|---|
| Reference | Type | Connection Bus | |
| Mitsubishi | FX5U-32M | PLC | RS-232, RS-485, GPIO, I2C |
| Wicocc | DC12V 66RPM | Motor | GPIO |
| Tend | TP-SM5N1 | Sensor | GPIO |
| Omron | E3Z-D61 | Sensor | GPIO |
| Weinview | MT8051iP 1 | Display | RS-232, RS485 |
| Brand | Components for Heterogeneous Network | ||
|---|---|---|---|
| Model | Type | Connection | |
| ASUS | RT-N12HP | Router | Ethernet, WiFi |
| Advantech | WISE-4051 | IoT gateway | RS-485, WiFi |
| OSI Layer | Protocol Stack |
|---|---|
| Application | Modbus TCP, SLMP |
| Transport | TCP |
| Network | IPv4, IPv6 |
| Datalink | Ethernet, WiFi |
| Software | Cybersecurity Test Tools | ||
|---|---|---|---|
| Version | Type | Role | |
| Kali | 2022.3 | Penetration O.S. | Attacker |
| Nmap | 7.93 | Network discovery | Attacker |
| Metasploit | 6.1.34 | Exploit code | Attacker |
| Ubuntu | 22.04 | Operating system | Target |
| ModbusPal | 1.6 | Modbus emulator | Target |
| JavaSDK | 18.0.21 | Java Distribution | Target |
| Name | Command | Sub-Command |
|---|---|---|
| Remote Run | 1001H | 0000H 1 |
| Remote Stop | 1002H | 0000H |
| Remote Pause | 1003H | 0000H |
| Read Type Name | 0101H | 0000H |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramirez, R.; Chang, C.-K.; Liang, S.-H. PLC Cybersecurity Test Platform Establishment and Cyberattack Practice. Electronics 2023, 12, 1195. https://doi.org/10.3390/electronics12051195
Ramirez R, Chang C-K, Liang S-H. PLC Cybersecurity Test Platform Establishment and Cyberattack Practice. Electronics. 2023; 12(5):1195. https://doi.org/10.3390/electronics12051195
Chicago/Turabian StyleRamirez, Ramiro, Chun-Kai Chang, and Shu-Hao Liang. 2023. "PLC Cybersecurity Test Platform Establishment and Cyberattack Practice" Electronics 12, no. 5: 1195. https://doi.org/10.3390/electronics12051195
APA StyleRamirez, R., Chang, C.-K., & Liang, S.-H. (2023). PLC Cybersecurity Test Platform Establishment and Cyberattack Practice. Electronics, 12(5), 1195. https://doi.org/10.3390/electronics12051195






