1. Introduction
The security of critical infrastructure industries is a common element of government defense agencies. Industrial sectors, such as energy, finance, food, transportation, information and communication technology, health, water, or manufacturing, are classified as critical infrastructures according to the Canadian federal government [
1]. The incapacity or destruction of critical infrastructure systems would cause negative impacts on cybersecurity, national economic security, and national public health or safety, according to the U.S. Patriot Act of 2001 [
2]. The National Institute of Standards and Technology Cybersecurity Framework (NSIT-CSF) provides a tier list to benchmark the cybersecurity progress of a system. The four NIST implementation tiers are as follows; Partial (Tier 1), risk-informed (Tier 2), Repeatable (Tier 3), and Adaptive (Tier 4) [
3].
To understand the impact of cyberattacks on industrial companies, Trend Micro, in collaboration with Vanson Bourne (U.K.), conducted an online survey during the first quarter of 2022. There were 900 respondents in total from the United States (300), Germany (300), and Japan (300) who provided their insights in this survey. The participants were part of three primary industries; manufacturing (314), electricity (310), and oil and gas (276). Eighty-nine percent of the participants reported a disruption in their supply chain from cybercriminals per the report by Trend Micro from 2021 to 2022; the duration of this disruption varied across industries. Manufacturing companies reported a disruption of five days, whereas electricity and oil companies reported a more prolonged disruption, with an average of six days. The economic effects of cyberattacks were considerable for the participants. Manufacturing industries reported average financial damage of USD 1.8 M. Unfortunately, electricity, oil, and gas companies reported higher losses of USD 3.3 M. The status of cybersecurity progress between information technology (I.T.) and operational technology (O.T.) systems was significant. According to the report provided by Trend Micro, 30 percent of the O.T. systems were at the lowest level of cybersecurity (NSIT-CSF Tier-1).
In contrast, 40 percent of I.T. systems recognize cybersecurity risk at the organizational level (NSIT-CSF Tier-2). To hedge this risk, adopting new technologies, such as cloud services or private 5G networks, represent a typical driver for cybersecurity implementation across these industries. In addition, implementing new regulations provides another driver for implementing cybersecurity techniques during the next three years (2023 to 2025) [
4].
The status of cybersecurity also varies widely across different nations. The International Telecommunication Union (ITU) helps identify improvement areas regarding national cybersecurity measures. The latest release, the Global Cybersecurity Index of 2020 (GCI 2020), contains extensive information regarding five improvement points: legal measures, technical measures, organizational capacity development, and cooperative measures from 169 ITU member states. According to the ITU, the United States, the United Kingdom, and Saudi Arabia are the current front-runners in cybersecurity worldwide. Regarding cybersecurity progress in the Asia-Pacific region, South Korea, Singapore, Malaysia, and Japan are the regional leaders. In addition, GCI 2020 highlighted the urgent need to increase cybersecurity investment in the industrial sector. According to the ITU, the industrial sector’s investment lags compared to similar sectors, such as defense, financial services, or information and communication technologies (ICT) [
5].
The increasing geopolitical instability of 2022 led to a surging number of attacks by advanced persistent threat (APT) actors. This situation represents an opportunity window for cyberattackers, which aim to exploit the vulnerabilities of industrial systems. Cyberattacks against industrial conglomerates using O.T. systems have been frequent in this regard. The attacks can be coordinated either by nation-states or state-sponsored groups. The use of cyberattack techniques against critical infrastructure operations from APT actors has been defined as cyberwarfare [
6].
Kaspersky Lab summarized the most significant incidents in industrial cybersecurity during 2022. In this regard, hacktivist groups targeted Seliatimo Agrohub (Russia) and the Belarusian railway system to respond to the ongoing war in Ukraine. On the other hand, NVIDIA and Foxconn, significant companies in the electronics industrial space, suffered ransomware attacks. In addition, APT actors targeted Viasat Inc (USA), affecting the service of high-speed satellite broadband for European customers [
7].
The cybersecurity research field has an increasing number of contributions regarding PLC vulnerabilities, and many researchers provide extensive literature regarding equipment analysis from manufacturers such as Siemens, Schneider Electric, and Omron. In contrast, the literature regarding vulnerabilities from manufacturers such as Mitsubishi or Panasonic is less common in the cybersecurity community. In addition, industrial companies are reluctant to improve their security after cyberattacks. In this regard, 48 percent of organizations do not take action to reduce future disruptions, according to the survey report provided by Trend Micro. In other words, industrial companies lack security measures, such as intrusion detection systems (IDS) or intrusion prevention systems (IPS).
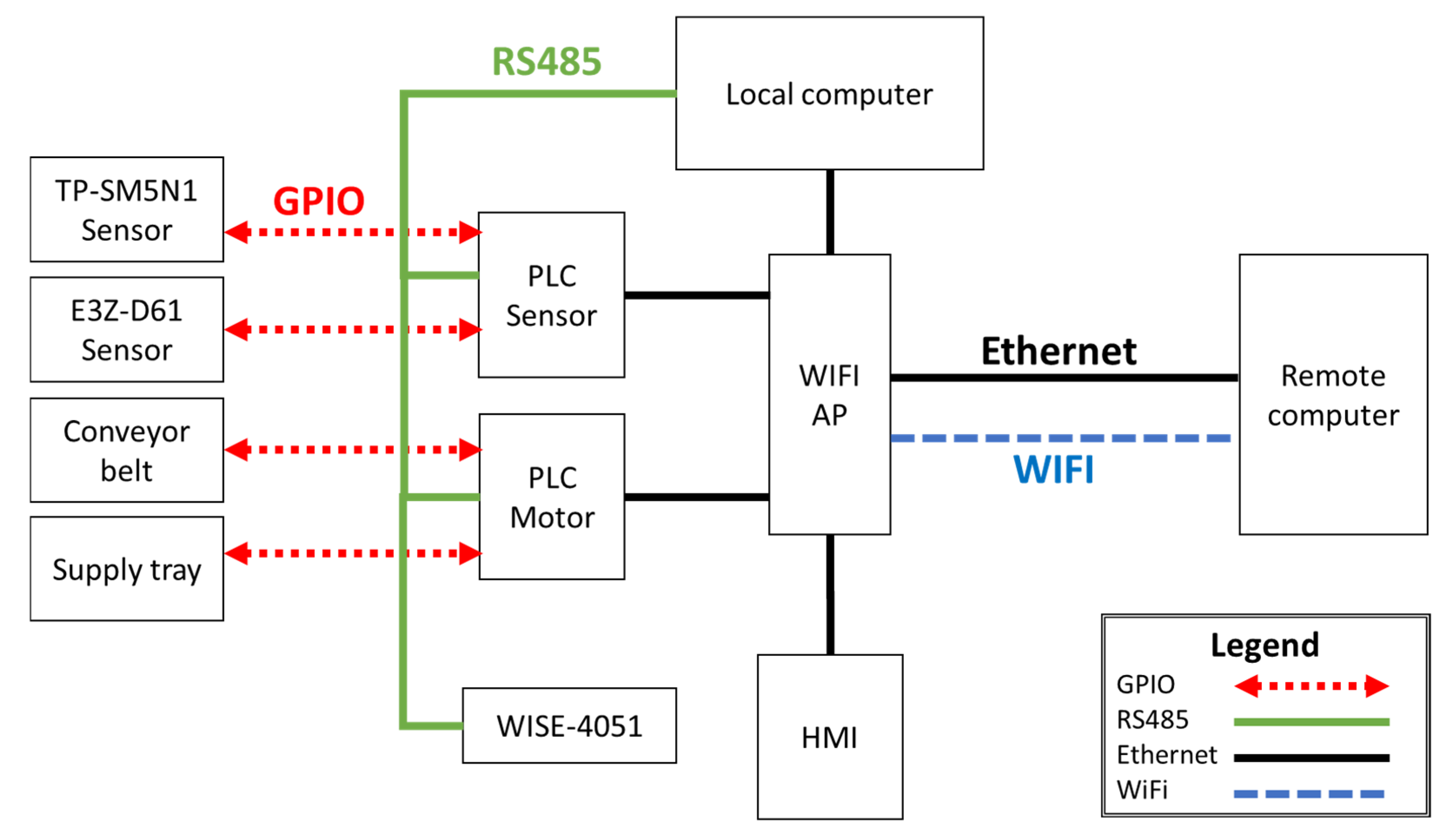
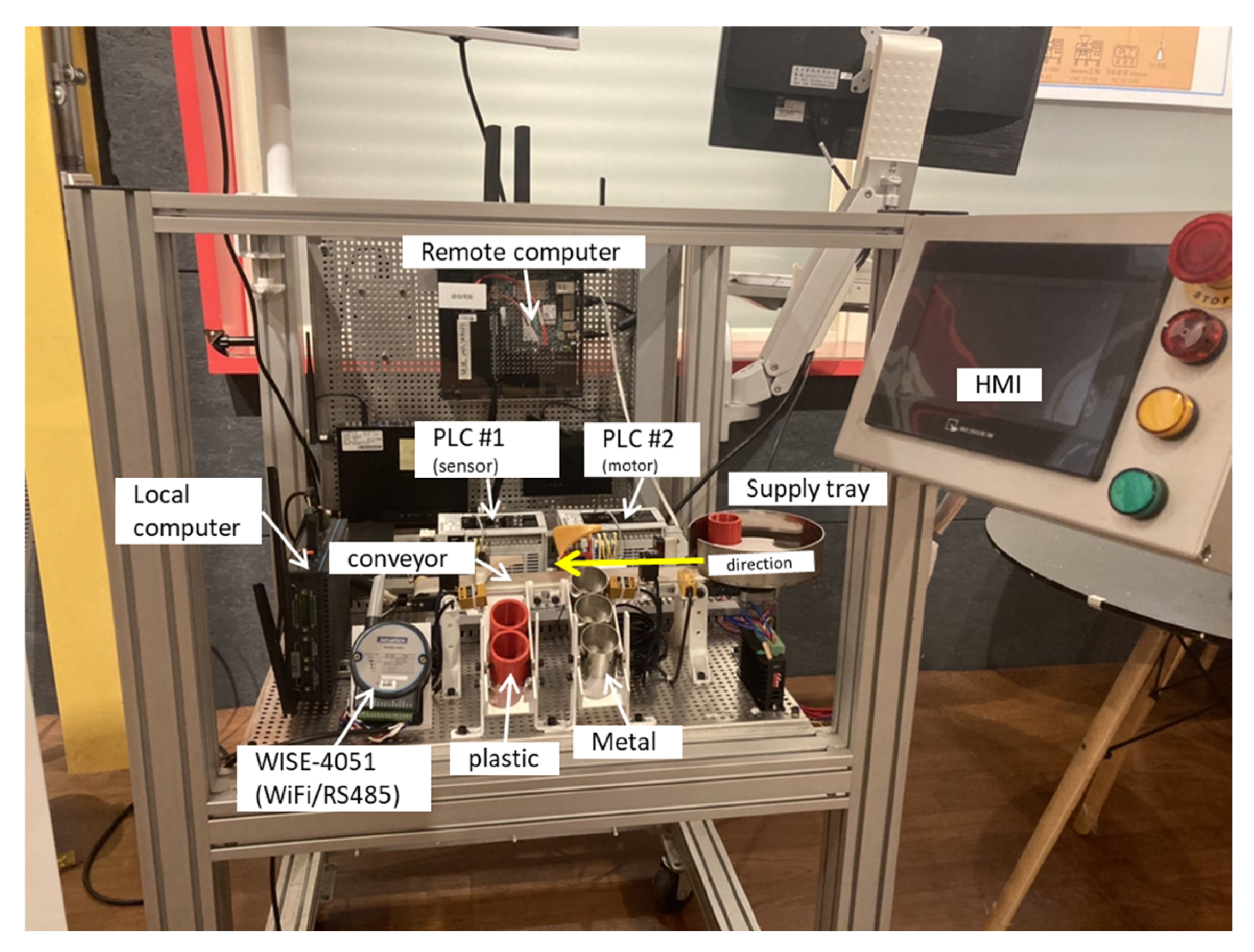
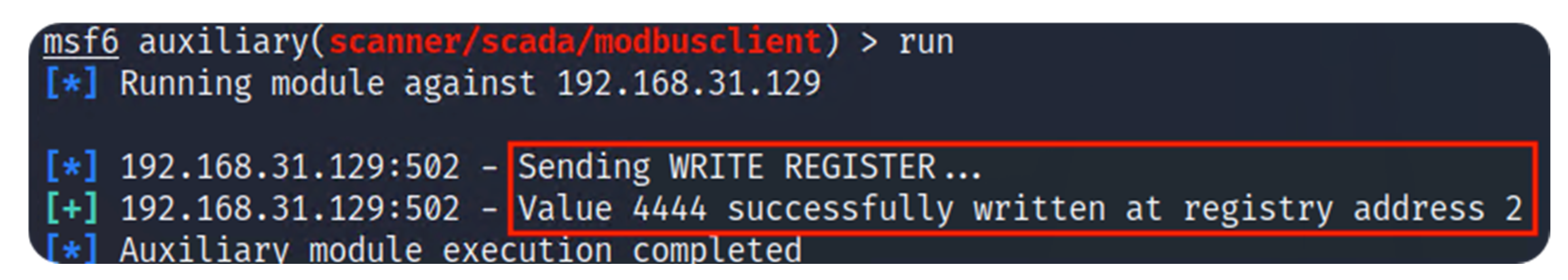
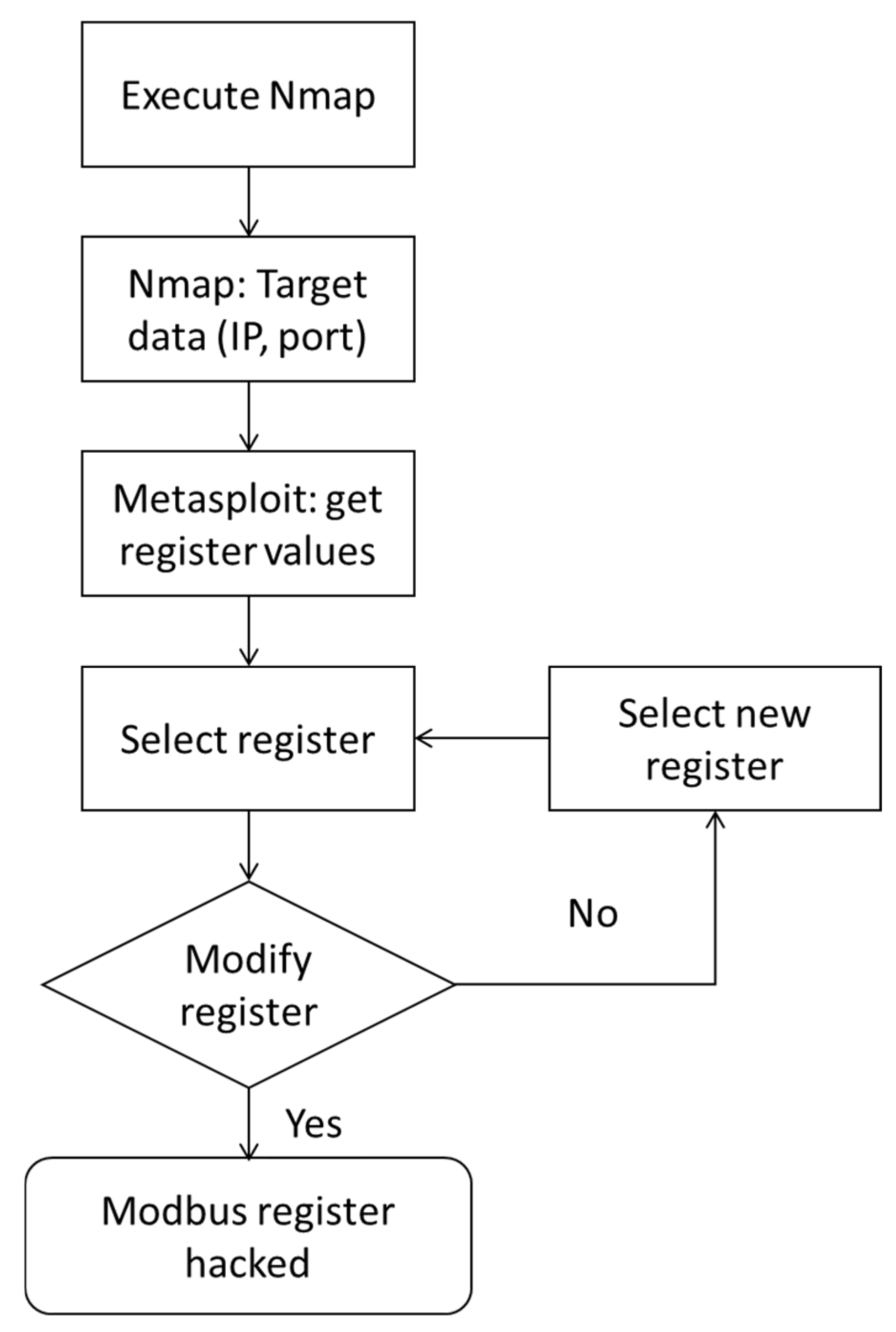
Based on the previous considerations, our study provides the needed components to simulate a small-scale production line. Implementing a physical test platform provides system modularity allowing the addition or exchange of parts in the industrial environment. The control of the components of the conveyor belt and logic control of sorting relies on two Mitsubishi PLCs (FX5U-32M). This work demonstrates a step-by-step packet reply to halt the operation, aiming to modify the Modbus registers in attack trials.
2. Related Works
Critical infrastructure sectors such as electric power plants, transmission grids, or manufacturing facilities require dedicated industrial control systems (ICS). To automate the data collection process, industrial users commonly use systems such as supervisory control and data acquisition (SCADA) and programmable logic controllers (PLC).
To understand the basic concepts of cybersecurity, Nitul Dutta et al. analyzed threats, hardware vulnerabilities, and protective measures against cyber I.T. systems attacks [
8]. Integrating SCADA and PLC systems provides flexibility and remote connection capabilities, which are highly valuable for industrial users. However, attacks targeting O.T. systems are common among industrial cyberattacks. Industrial endpoints such as PLC, human–machine interface (HMI), edge devices, or outside computers are frequent targets. In addition, attacks exploiting SCADA vulnerabilities can be traced back to the Cold War [
9]. In addition, new state-of-the-art measures, such as two-factor authentication with biometric features, are gaining momentum across the cybersecurity space [
10].
The National Security Agency (NSA), in cooperation with the Cybersecurity and Infrastructure Security Agency (CISA), published a whitepaper regarding the main tools used against ICS/SCADA devices in 2022. The report highlighted the development of custom-made tools developed by multiple APT actors. Particular attention should be given to operations using equipment such as Schneider Electric PLC, OMRON Sysmac NEX PLC, and Open Platform Communications Unified Architecture servers (OPC UA) [
11].
Acknowledging the inherent risk of SCADA systems, Chen-Ching Liu et al. proposed a vulnerability assessment framework to evaluate the vulnerability level of cyber systems deployed in a power infrastructure [
12]. To validate the input of the SCADA system, the research conducted by Gregory et al. suggested the implementation of a “Trust System” architecture for SCADA networks—the proposed system aimed to identify risk and harmful data across an industrial communications network [
13].
Phan Duy Anh and Truong Dinh Chau proposed a component-oriented architecture of SCADA software. The study aimed to increase the flexibility and interoperability of SCADA systems [
14]. To increase the security of distributed control systems (DCS), Sergi et al. proposed the incorporation of public key infrastructure (PKI), helping to generate a “security by default” implementation scenario [
15]. Additional efforts to improve the infrastructure of industrial automation and control systems (IACS) were proposed by Pramod et al. [
16]. Rezai et al. summarized the existing key management schemes in SCADA networks, highlighting issues requiring extensive research, such as cryptographic authority or protocol vulnerability assessments [
17]. To perform less intrusive assessment analysis on SCADA systems, the research conducted by Adam Hahn and Manimaran Govindarasu highlights the inherent difference between I.T. and O.T. assessment tools. The authors recommend using dedicated tools for O.T. systems, such as security content automation protocol (SCAP) or bandolier [
18].
Regarding communication capabilities, the emerging use of private 5G networks represents an opportunity to increase the bandwidth capabilities of large-scale DCS deployments, according to the research of Zhi Lu et al. [
19]. However, implementing security standards in industrial control systems is still ongoing. According to William et al., the presence of standards is still relatively low compared to the number of guidelines from government, industry, and standardization bodies [
20].
The literature on SCADA protocols, incidents, threats, and tactics is extensive. To provide a curated summary of SCADA systems, Dimitrios Pliatsios et al. conducted a survey where the authors observed current and future trends in this topic. In this regard, the authors highlighted the use of virtualization technologies to reduce the deployment cost of this type of system. In addition, this work also provided a list of threats and tactics to mitigate the vulnerabilities of SCADA systems. Regarding the list of incidents, the team highlighted the fifteen most essential incidents regarding SCADA systems since 2000. These attacks targeted critical infrastructure facilities of countries such as the United States, Saudi Arabia, and Ukraine.
The cyberattack methods range from user compromise to social engineering, viruses, or worms [
21]. Regarding future challenges for SCADA networks, Sagarika Gosh et al. highlighted the exposure of existing security standards to quantum computing attacks. Traditional cryptography standards such as Advanced Encryption Standard (AES), elliptic-curve cryptography (ECC), and secure hash algorithms are exposed against Shor’s algorithm. The deployment of Shor’s algorithm on a quantum computer could decrypt ECC targets. Currently, Bitcoin and Ethereum rely on the use of ECC for transaction verification [
22]. Attacks on PLC networks can be executed with a collection of multiple open-source software tools, as the study by Asem et al. suggested [
23]. Different attack methods, such as “man in the middle” (MITM) or replay attacks, are commonly seen in PLC network attacks. For this reason, improving PLC systems is a primary concern among researchers and corporations. Hajda et al. highlighted the need to improve the security standards regarding industrial communication protocols, network architecture, integrity checking, and software updates and reduce the human component element [
24].
The adoption of Modbus as the selected data communication protocol comes from its extended adoption in industrial environments. The research conducted by Gonzales et al. used a smart grid physical testbed to collect and represent the data obtained by multiple actuators. The data communication between sensors and the supervisory system was possible using the Modbus protocol [
25]. In addition, Modbus can be combined with other protocols to increase its flexibility. Due to its industrial nature, Modbus is a synchronous protocol. Complementary protocols such as message queuing telemetry transport (MQTT) can be considered to achieve asynchronous communication. Samer Jaloudi compared multiple communication protocols regarding industrial Internet of Things applications. The combination of Modbus and MQTT provides flexibility to the whole system. However, using multiple protocols increases industrial data’s payload [
26].
Regarding Modbus security, Santiago et al. suggested a central architecture for the validation phase. This “validation” concept has evolved into sandboxing technologies, providing virtual environments to confine the actions of a specific malware into an isolated environment. The authors proposed a new secure version of the Modbus protocol, where a central architecture design authorizes the client, server, and its Modbus frame [
27]. The current version of Modbus (Modbus TCP Security) guarantees the integrity and confidentiality of the established session. Modbus TCP Security uses port 802 as a safe port for communication, whereas the previous versions used port 502. In addition, public key infrastructure (PKI) and role-based access control (RBAC) are also included in its latest release. Martins et al. combined Modbus TCP Security with a MITM component to validate both the client and server [
28]. The measures mentioned above are defensive, aiming to increase the security of SCADA systems and the Modbus protocol.
In contrast, offensive measures aim to exploit the vulnerabilities of industrial hardware and software. Industrial application devices, such as PLC or controller modules, could expose an industrial operation to third-party attacks. Rongkuan et al. exposed the vulnerabilities of UWNTEK equipment in their research study. The team found a vulnerability in the UW5101 controller module, where the reboot command (0114H) did not require authentication and authorization when executed. This vulnerability provides access to the root user and allows telnet commands during restart, creating a backdoor in the firmware code. This backdoor allows complete control and execution of critical commands using remote access [
29].
Henry et al. extensively analyzed the vulnerabilities of Siemens PLC devices. The team generated valid network packages to conduct a replay attack, targeting Siemens S7 devices (S7-1211 PLC). The attacks comply with three main parts: packet capture (pcap), reverse engineering, and session attack. Firstly, the team performed a packet capture using Wireshark, an open-source packet analyzer. Secondly, the team conducted a reverse engineering analysis of two Siemens Firmware versions (v4.1 and v4.2). This analysis found firmware vulnerabilities which helped to craft an appropriate packet response. The study used WinDbg, a multipurpose Microsoft Windows operating system debugger, to perform the exercise. After analyzing the main attributes of the message, the researchers used Scapy, a packet manipulation tool for computer networks written in Python. Finally, using a custom Scapy script [
30], the team conducted a replay attack with valid network packages that exposed the vulnerabilities of Siemens S7 devices [
31].
Dragos Inc., a state-run cybersecurity firm founded by the United States government, recently released information about Pipedream. Pipedream is an industrial control system (ICS)-specific malware developed to disrupt industrial processes. Specifically, Pipedream targets PLCs from Omron and Schneider Electric, possibly targeting and attacking controllers from multiple additional vendors. The released whitepaper lists the leading models vulnerable to malware attacks. In addition, the whitepaper declares that it is possible to target industrial technologies, such as Modbus Transmission Control Protocol (Modbus TCP), OPC UA, Codesys, and Windows. The main objective of this whitepaper is to provide a standard operation procedure (SOP) to avoid cyberattacks from Pipedream or similar malware attacks on both public and private institutions [
32].
5. Discussion
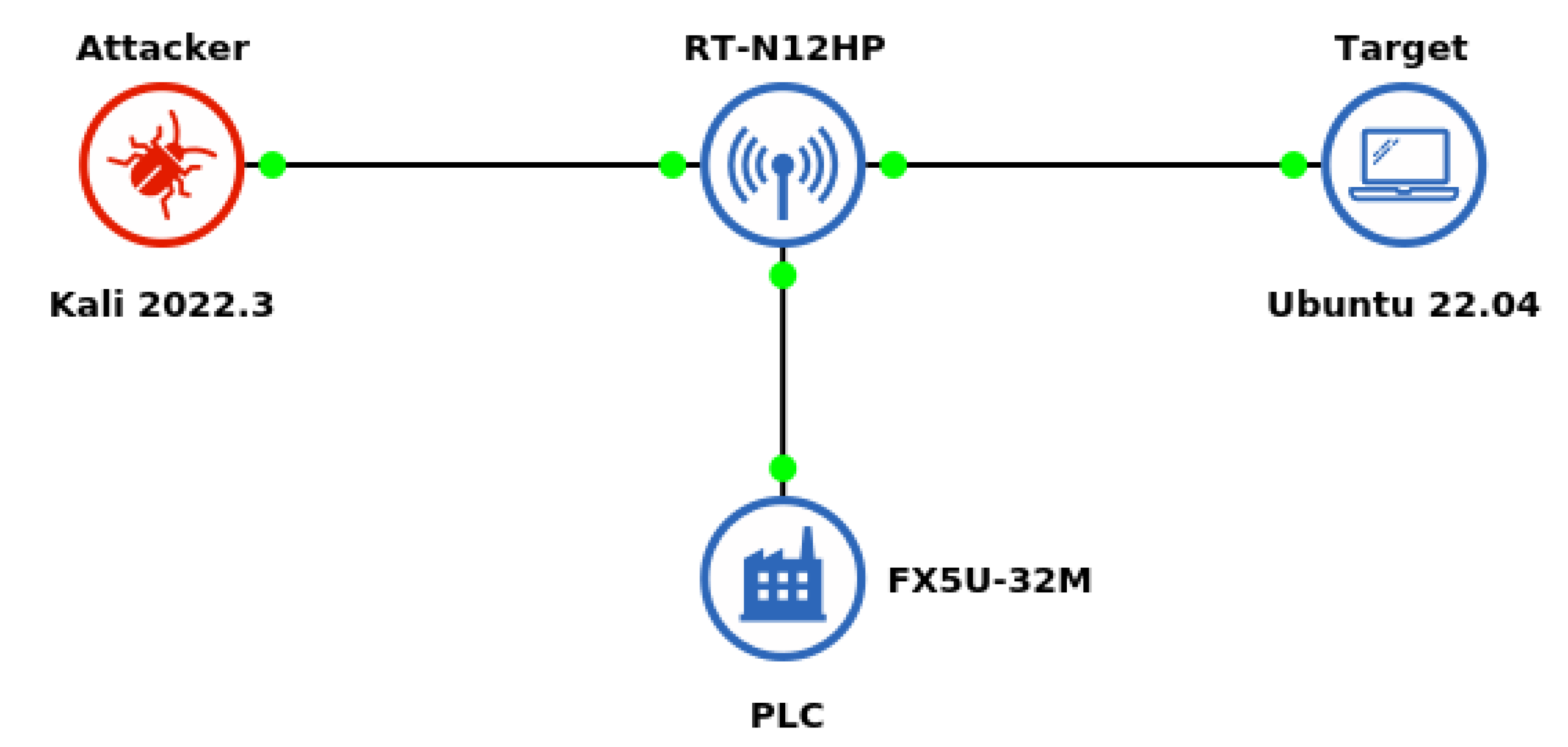
Establishing an industrial cybersecurity testbed environment provides a safe space to observe the common vulnerabilities of industrial networks. Ethernet is the primary wired computer networking technology due to its high adoption in industrial Internet environments, where clients prioritize wired connections over wireless solutions. Therefore, the Industrial Internet of Things (IIoT) and Industry 4.0 systems require secure Ethernet connections for data transmission. The use of Mitsubishi FX5U-32M as our selected PLC responds to two primary needs; firstly, it is a widely adopted model of PLC in the Asian region, and secondly, the analysis of vulnerabilities of this type of equipment is moderate compared to leading brands such as Siemens or Omron.
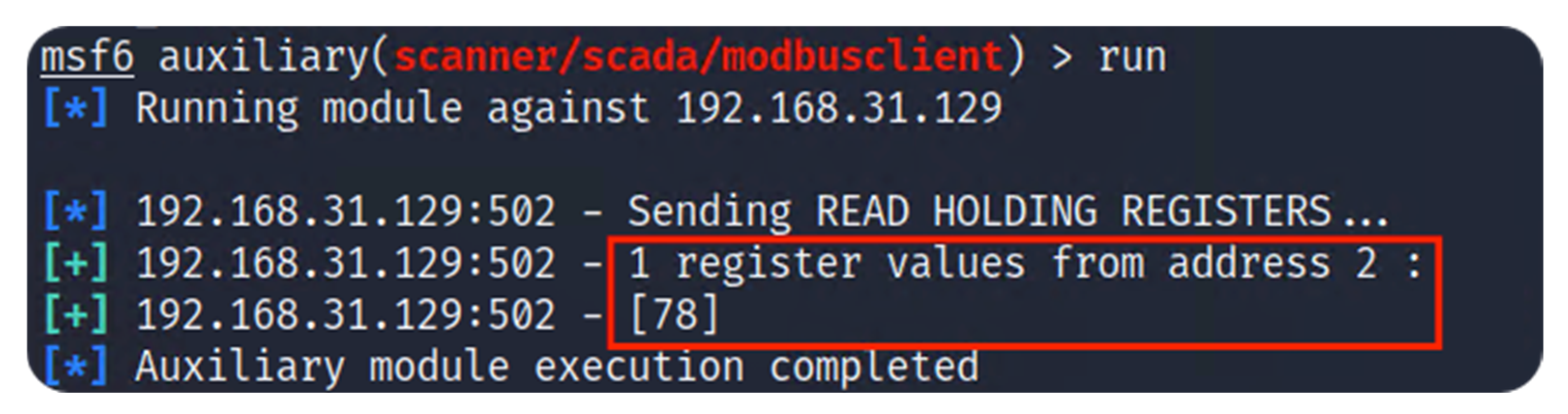
Modbus is a standard data communication protocol in industrial scenarios. However, this study highlights the vulnerabilities and the availability of software tools to disrupt industrial communications. Due to the lack of security measures, such as intrusion detection systems (IDS) or intrusion prevention systems (IPS), the network is vulnerable to attacks. Access to the local router provides communication across the whole network, facilitating packet reply attacks. In this study, the attacker could generate a network mapping and write registers due to the lack of preventive measures. Unfortunately, this lack of security is common among industrial networks, as the 2022 Trend Micro survey mentioned. This work provides information for industries on network cybersecurity tasks through the test platform and cyberattack demonstration.
Industrial operators could adopt open-source solutions with IDS and IPS capabilities to mitigate these risks. In this regard, Snort performs real-time traffic analysis, which allows the detection of stealth port scans, such as the one conducted by Nmap in this study [
46]. In addition, due to different industrial needs, the industrial network can adopt various network components. Wired solutions such as RS485 or Ethernet are conventional for Larger Area Networks (LAN). In contrast, wireless solutions, such as WiFi, LPWAN, or 5G, provide higher flexibility and can increase the data transmission distance between client and server topologies. The heterogeneous communication network environment in industrial scenarios requires a more detailed study. In this regard, the upcoming private 5G networks represent an opportunity to increase the security of industrial networks [
19].