In this chapter, the architecture design and model scheme of the platform are described.
3.1. Platform Architecture
This article uses Hyperledger Fabric to develop a decentralized education and training management platform that supports identity verification, reliability, and data sharing. Organizations in the alliance network include education management departments, education and training institutions, and human resource departments. Together with the front-end management interface, it forms a management platform for education and training. The platform architecture is shown in
Figure 2. In the alliance network, each newly joined entity becomes a network node through the consensus stage and maintains a complete ledger.
In this paper, the management platform built with Hyperledger Fabric consists of three parts: the application service layer, the core layer, and the data storage layer. Each layer interacts in the form of an application programming interface (API) or software development kit (SDK). Each layer is developed and maintained relatively independently, which can reduce mutual influence and improve system scalability. The system uses a browser/server (B/S) architecture to provide services to users and separates the front- and back-ends to reduce module coupling. When operating information is transmitted, such as the basic information and assessment of newly added trainees, all data transmission is carried out in JavaScript Object Notation (JSON) format.
The application service layer is divided into education, training management, and a comprehensive monitoring platform for blockchain operations. The education and training management module includes functions to operate on role registration and related information. The front-end calls the API interface specified by the service layer and uploads the form request parameters (basic personnel information, training information, etc.) generated by the web page to the back-end, and the back-end calls the appropriate contract function (registration query, audit, and other contracts) to implement the requested business requirements. Connect to the blockchain network through the encapsulated API. According to the request parameters, select the connected channel and endorsement node to endorse the transaction, and finally, obtain the response data in JSON format. The web side parses the response data and renders the result on the page.
The blockchain operation’s comprehensive monitoring platform monitors and operates the nodes in the alliance network. The monitoring content includes smart contracts, the number and operation of nodes, transaction history, etc., as shown in
Figure 3.
The core layer includes functions such as chain code and MSP authorization. There will be no central node in the distributed network of blockchain. Therefore, a decision-making mechanism is needed to facilitate consensus decisions among participants in the network. The consensus mechanism is a mechanism for coordinating parties to process information [
34]. On this platform, we chose Raft (leader election) [
35] as the consensus algorithm. It can provide an efficient consensus method in the governance process. After the front-end is connected to the blockchain network, the transaction is sent to the designated channel. The endorsement nodes in the alliance endorse and return the endorsement result, together with the digital signature to the sender. After confirming that the transaction is correct, the sorting node in the blockchain network will sort the transaction through the Raft algorithm, and the completed transactions are stored in blocks [
36]. The accounting nodes in the network are synchronized through the P2P protocol, and the information is finally recorded in the ledger. Distributed ledgers are used to achieve multi-party, consistent, decentralized data storage, and broken ledgers can be repaired by synchronizing ledgers. The business-related smart contracts in this study run in Docker containers, and the chaincode service provides a secure container environment and lifecycle management.
The data storage layer ensures data persistence. In this consortium chain, all participating identity authentication information, trainee training records, and other business information are stored in CunchDB. We construct a MySQL database to store related data, such as system management information. By building a Redis cache database to store common transaction data, the concurrency and performance of a large number of transactions in the system can be improved. PostgreSQL to provide data for the monitoring page. It adopts the classic client-server model (C/S), that is, one client corresponds to one server daemon. This daemon process analyzes the query request from the client, retrieves data by generating a plan tree, and finally, formats and outputs the result and returns it to the client.
3.2. Platform Solution
There are several "roles" in the management chain process framework diagram of the training management platform based on Hyperledger Fabric.
Figure 4 shows the relationship between roles, education and training institutions (ETI), local education bureaus (LEB), and local human resources centers (LHRC) that form an alliance chain, with students (S), C-level teachers (CT), B-level teachers (BT), and A-level teachers (AT) together forming the RSETP. At system initialization, each organization contains a superadministrative account. According to the different identities of each participant, the corresponding level of read and write permissions is formulated [
37].
Education and Training Institutions(ETI): As an important platform and driving force for adult education, it ensures high-quality training for students. In order to prevent insufficient qualifications and false propaganda about education and training institutions, educational institutions need to apply for registration with the local education bureau and can only join the alliance chain after approval. Students can study at this educational institution and obtain corresponding training results and certificates.
Local Education Bureau (LEB): Focus on filing information on training institutions and teachers, including basic information, working experience, educational background, and whether they have teacher qualifications. Training institutions are required to strengthen their own platform management. If personnel engaged in training activities in training institutions violate laws and regulations, the violations will be recorded.
Local Human Resource Center (LHRC): The trainees’ information, including basic information and educational background, is filed at the LHRC. When the employer hires the trainee, the trainee’s training information and process can be clearly questioned. The trainee’s training record can be queried by accessing the alliance network, and the illegal or falsified results can be traced back to ensure the fairness of each trainee’s education and training.
Student (S): Students who want to join the education alliance training institution need to provide their own basic information. After passing the certification process for educational institutions, they can enter the institution for training. The trainee’s information is stored on the blockchain.
C-level Teacher (CT): Each institution has different levels of training teachers, and each teacher needs to be certified by ETI and LEB. After confirming the corresponding training qualifications, he can join the network for teaching and assessing students. The CT will judge the day’s performance based on each student’s daily performance and upload the daily training situation to the alliance network for storage.
B-level Teacher (BT): Score each student’s one-week training situation, and after confirming that it is correct, upload the information to the alliance network for storage.
A-level Teacher (AT): Refer to each trainee’s one-month comprehensive training situation to score the trainee. After the training is over, it will be decided, according to the trainee’s performance during the whole training period, whether the trainee can get the certificate of passing the training, and the trainee who does not meet the graduation standard will not be awarded a graduation certificate.
During the entire training management process, if there is a new educational institution in a certain place to carry out training courses, the educational training institution will form an alliance chain with the local education bureau and the local human resources center, a certificate authority (CA) in the federation issues digital certificates and public and private keys to each organization. Each organization creates its own nodes, including peer nodes, ordering nodes, etc. Each peer node in the organization can install multiple chain codes to meet different business needs and store a blockchain ledger. When new students or teachers join the institution for training, the institution first verifies and stores their information. Teachers of different levels in each institution have different grading permissions. According to the pre-established scoring details, each student is scored, and each scoring record is saved to the blockchain network. If, after the trainee graduates, the employer finds that the trainee’s level is not up to standard, it can appeal to the human resources department to review the trainee’s training information.
Figure 5 shows the specific workflow of the system. From the acceptance of students by educational institutions to the graduation of students, the process can be divided into the following steps, in detail:
- Step 1.
This step will register each role in the blockchain network. All participants in the system need to register on the network and record their identity information. The network will provide each participant with a unique identity. Before each transaction, the identity information of both parties needs to be verified. Only after the identity information has been correctly verified can the transactions and information exchange in the network continue.
- Step 2.
When a student signs up for training at an educational institution, the corresponding institution will record basic information, such as the student’s identity information, training courses, and time. After the information is confirmed to be correct, all information will be uploaded to the blockchain network through the designated ordering node for storage.
- Step 3.
After the training every day, the CT will evaluate the performance of all the students on the day, according to the pre-established assessment standards and upload the evaluation information for each S to the blockchain network. The corresponding contract will automatically detect the evaluation information, and the information of an authentication failure will not be recorded in the blockchain network. for example, if the assessment score exceeds the maximum standard score. After confirming that the information is correct, the ledger will be updated.
- Step 4.
The BT judges the weekly results of the students, scores them weekly, and uploads them to the blockchain network. In order to execute the smart contract corresponding to the weekly assessment, and after confirming that the information is correct, it will be uploaded to the blockchain network for storage.
- Step 5.
The AT will give students a monthly score after the monthly training. The AT will carry out the final assessment and certification of each S after all the training courses are over. Whether the S has passed the education and training, based on his or her performance throughout the entire training period, is determined. All data will be operated at various stages in the chain, and the integrity of the data will be guaranteed.
- Step 6.
As an authoritative third party, the local education bureau needs to authenticate and record various information about the teachers in the education alliance institution. Only teachers who meet the teaching conditions can serve in the institution and assess the students to ensure the teaching quality of the teachers. The local human resources center mainly records the training situation of the training and assessment personnel. According to actual needs, managers can trace the specified training records in the alliance network to check whether the assessment records for each S are accurate. By viewing the signature information of each administrator, the legitimacy and validity of the assessment information can be verified. Once the assessment information is untrue and the student’s grades are unqualified, etc., the assessment teacher can be traced back according to the transaction records.
3.3. Ledger Design
RSETP is a permission-based network that provides some needed services to designated users. Our system consists of three main components: a permissioned consortium chain, on-chain and off-chain storage, and manipulation of student-centric information through the RSETP client interface. Hyperledger can generate new identities for modeling participants as needed and append them to the participant registry. The Hyperledger network requires blockchain identities as a form of credential, storing a mapping of genetic characters to participants in the identity registry [
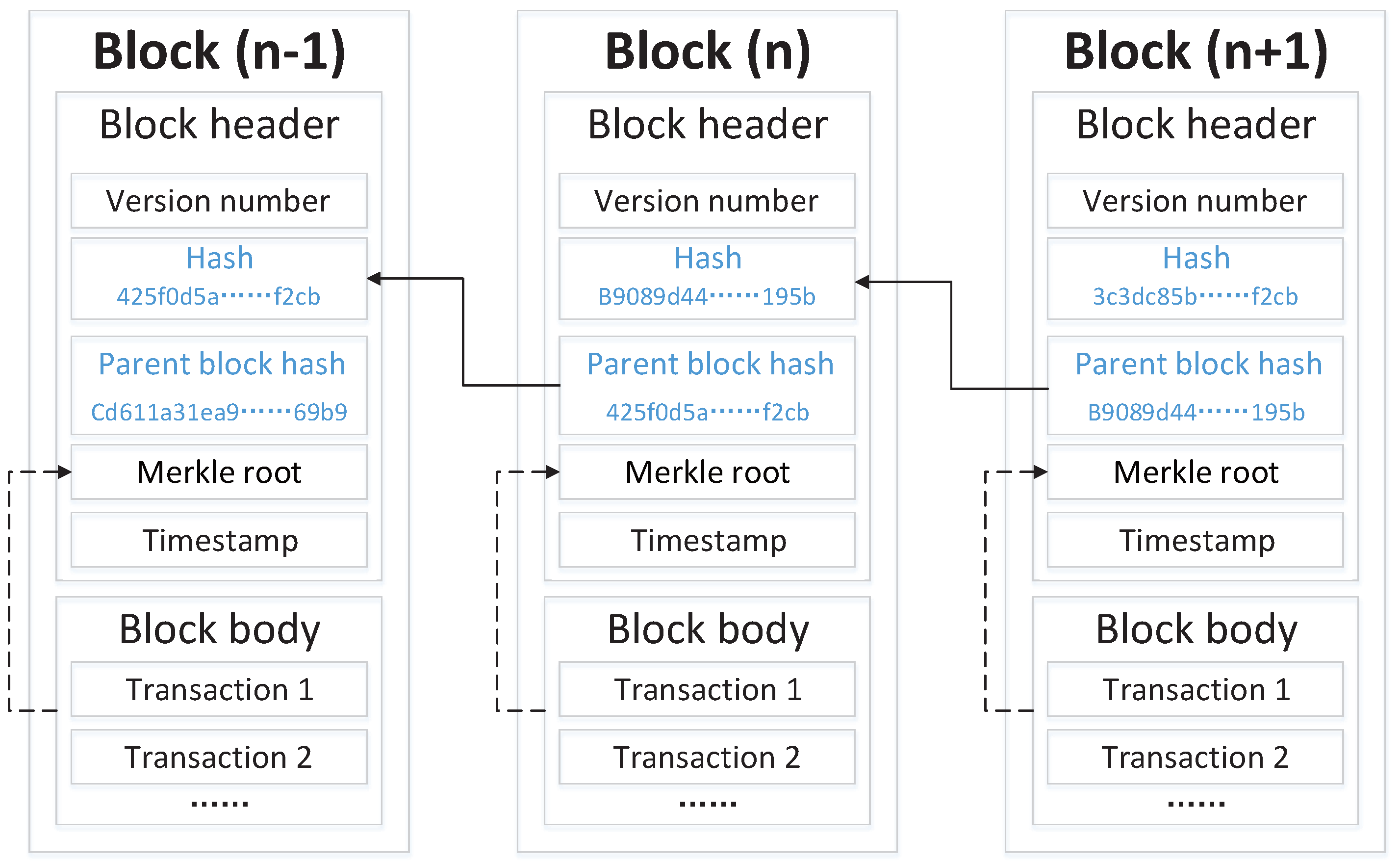
38]. All identity management services are performed by peers controlled by the organization deploying the blockchain consortium. In our RSETP, at any time, new participants (S, AT, etc.) with appropriate identity functions can be added. The permissions of each role in the organization have been set in the access authorization rules, so only the roles that have completed registration on the platform and passed identity verification have the corresponding authority to authorize transactions. Without the correct private key, no one can gain access to the blockchain platform. In RSETP, the administrator passes the request data generated by the web page to the blockchain network through the corresponding API, and the data is encoded and packaged into blocks during the transaction process. Each block has a block header, which is used to verify the validity of the entire block.
The ledger contains the state of the world and a blockchain. The essence of the world state is a database that saves the current state of the network ledger [
39]. The chain on the peer is a transaction log that records changes in the state of the world. The world state is saved in the form of key-value pairs, which have good interactions with the data in JSON format.
Figure 6 depicts the relationship between state entities. Students or teachers are associated with training institutions and other departments through a specific relationship table, and the information exchange between various regulatory agencies enables managers to perform flexible operations.