Blockchain and Interplanetary File System (IPFS)-Based Data Storage System for Vehicular Networks with Keyword Search Capability
Abstract
:1. Introduction and Background
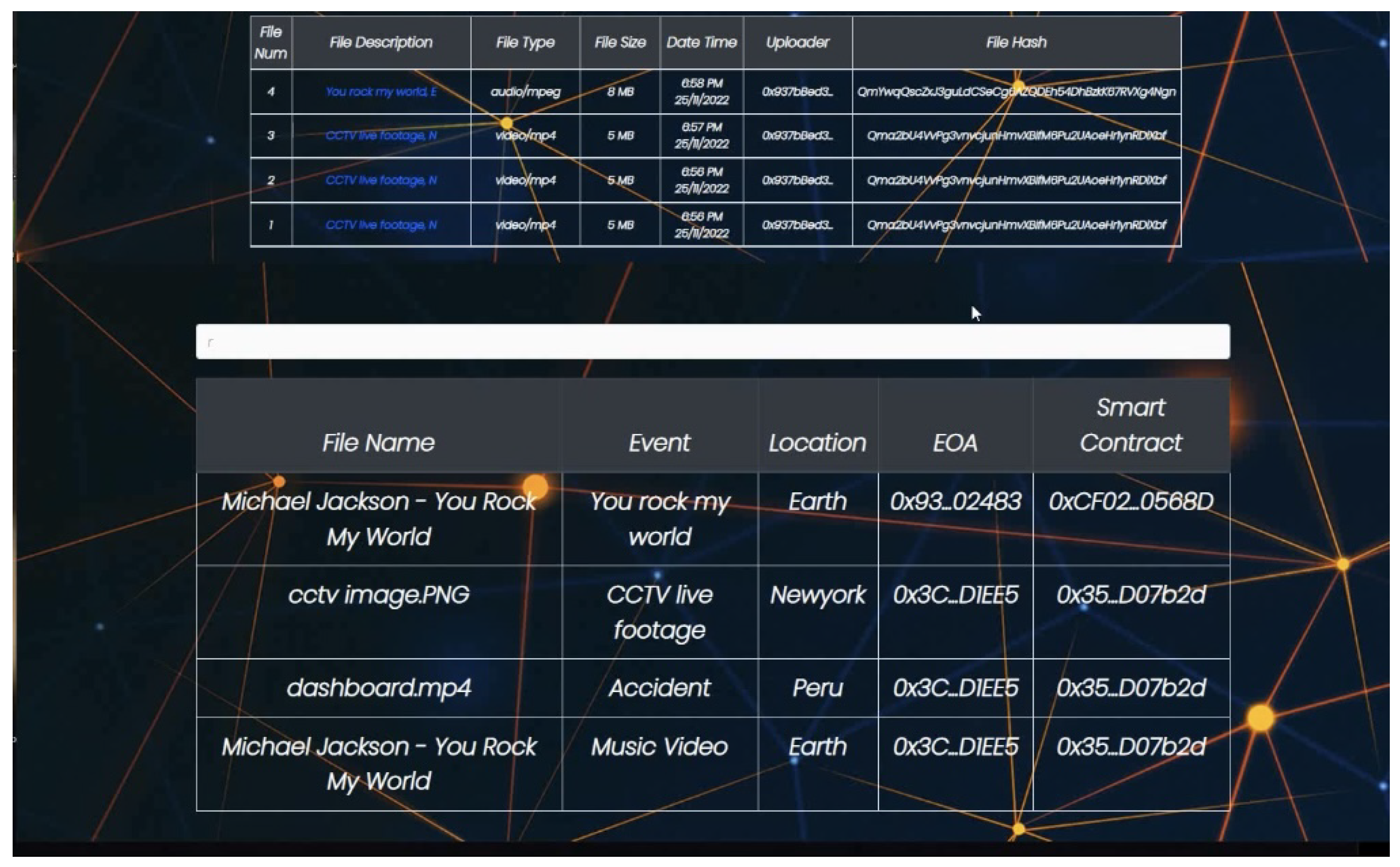
- Our proposed distributed storage application supports the storage of various file types since uploaded files are stored on IPFS and their hash values are stored in smart contracts on the Ethereum blockchain. Users need not remember the hash values since they can be retrieved from the blockchain later.
- DApp provides a keyword search feature to help users quickly find the necessary files based on Ethers.js’s smart contract event listener and contract.queryFilter.
- Our experiment shows that our DApp is resilient to system failure, and our system provides better transparency than is possible with centrally managed applications.
2. Related Work
3. Preliminaries
3.1. IPFS
3.2. Ethereum
3.3. Web3.js
3.4. Ethers.js
3.5. Smart Contract
3.6. Smart Contract Events
3.7. Decentralized Applications (DApp)
3.8. React.js
3.9. Dependencies
3.9.1. Node Package Manager (NPM)
3.9.2. Node.js
3.9.3. MetaMask
3.9.4. Truffle Framework
4. Proposed Data Storing Scheme
4.1. File Uploading
- (i)
- Define data structure for the management of files:
- (ii)
- Store and list the files:
- (iii)
- Upload File:
- (iv)
- Creating an Event:
4.2. Keyword Searching
- (i)
- Read information from the blockchain:
- (ii)
- Keyword search text file creation:
5. Implementation
5.1. Steps to Create Private Ethereum Network
5.1.1. Download “Geth”
5.1.2. Make a Folder for Our Private Ethereum Network
5.1.3. Construct a Genesis Block
5.1.4. Run the Genesis File
5.1.5. Set Up the Private Network
5.1.6. Make Externally Owned Account (EOA)
5.1.7. Ethereum Mining on Our Private Chain
5.1.8. Connecting the Private Ethereum Network to Metamask
- –
- http.addr value:Listening interface for HTTP-RPC servers (default: “localhost”).
- –
- http.port value:Listening port for HTTP-RPC server (default: 8545).
- –
- http.corsdomain value:A list of domains separated by commas that will accept cross-origin queries (browser enforced). Because the HTTP server can be accessed from any local application, the server includes additional safeguards to prevent API abuse from web pages. The server must be configured to accept Cross-Origin requests in order to allow API access from a web page. The —http.corsdomain flag is used to accomplish this. The —http.corsdomain command accepts wildcards, allowing access to the RPC from any location: —corsdomain ’*’.
- –
- http.api value:APIs accessible via the HTTP-RPC protocol.
- –
- ws.api value: APIs accessible via the WS-RPC interface.
- –
- nodiscover:The peer discovery mechanism is disabled.
- –
- networkid value:Sets network id explicitly.
- –
- allow-insecure-unlock:When account-related RPCs are exposed via http, this allows for insecure account unlocking.
5.2. Running Our Own IPFS Node
5.3. Deploying Smart Contract
5.4. File Uploading and Retrieving
5.5. Keyword Searching
6. Performance Evaluation
- Scenario 1:
- Scenario 2:
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mateen, A.; Khalid, A.; Nam, S.Y. Management of Traffic Accident Videos using IPFS and Blockchain Technology. KICS Summer Conf. 2022, 1, 1366–1368. [Google Scholar]
- Singh, A.; Chatterjee, K. Cloud security issues and challenges: A survey. J. Netw. Comput. Appl. 2017, 79, 88–115. [Google Scholar] [CrossRef]
- Shin, Y.; Koo, D.; Hur, J. A survey of secure data deduplication schemes for cloud storage systems. ACM Comput. Surv. 2017, 49, 1–38. [Google Scholar] [CrossRef]
- Yinghui, Z.; Dong, Z.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar]
- Zhang, Y.; Chen, X.; Li, J.; Wong, D.S.; Li, H.; You, I. Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing. Inf. Sci. 2017, 379, 42–61. [Google Scholar] [CrossRef]
- Dropbox. Available online: https://www.theguardian.com/technology/2016/aug/31/dropbox-hack-passwords-68m-data-breach (accessed on 17 February 2023).
- Arrington, M. Gmail Disaster: Reports of Mass Email Deletions. December 2006. Available online: https://techcrunch.com/2006/12/28/gmail-disaster-reportsof-mass-email-deletions/ (accessed on 17 February 2023).
- Amazon. Amazon s3 Availability Event: 20 July 2008. Available online: https://simonwillison.net/2008/Jul/27/aws/ (accessed on 17 February 2023).
- Krigsman, M. Apple’s MobileMe Experiences Post-Launch Pain. July 2008. Available online: https://www.zdnet.com/article/apples-mobileme-experiences-post-launch-pain/ (accessed on 17 February 2023).
- Benet, J. Ipfs-Content Addressed, Versioned, p2p File System. 2014. Available online: https://arxiv.org/abs/1407.3561 (accessed on 17 February 2023).
- Geth. Available online: https://geth.ethereum.org/ (accessed on 17 February 2023).
- Metamask. Available online: https://metamask.io/ (accessed on 17 February 2023).
- Hao, J.; Sun, Y.; Luo, H. A Safe and Efficient Storage Scheme Based on BlockChain and IPFS for Agricultural Products Tracking. J. Comput. 2018, 29, 158–167. [Google Scholar]
- Rajalakshmi, A.; Lakshmy, K.V.; Sindhu, M.; Amritha, P. A blockchain and IPFS based framework for secure Research record keeping. Int. J. Pure Appl. Math. 2018, 119, 1437–1442. [Google Scholar]
- Vimal, S.; Srivatsa, S.K. A new cluster P2P file sharing system based on IPFS and blockchain technology. J. Ambient. Intell Hum. Comput. 2019, 1–8. [Google Scholar] [CrossRef]
- Chen, Y.; Li, H.; Li, K.; Zhang, J. An improved P2P file system scheme based on IPFS and Blockchain. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2652–2657. [Google Scholar] [CrossRef]
- Wang, R.; Tsai, W.-T.; He, J.; Liu, C.; Li, Q.; Deng, E. A Video Surveillance System Based on Permissioned Blockchains and Edge Computing. In Proceedings of the 2019 IEEE International Conference on Big Data and Smart Computing (BigComp), Kyoto, Japan, 27 February–2 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sun, J.; Yao, X.; Wang, S.; Wu, Y. Blockchain-Based Secure Storage and Access Scheme For Electronic Medical Records in IPFS. IEEE Access 2020, 8, 59389–59401. [Google Scholar] [CrossRef]
- Ethereum. Available online: https://ethereum.org/ (accessed on 17 February 2023).
- Web3. Available online: https://web3js.readthedocs.io/en/v1.8.0/ (accessed on 17 February 2023).
- Ethers. Available online: https://docs.ethers.io/v5/ (accessed on 17 February 2023).
- Cai, W.; Wang, Z.; Ernst, J.B.; Hong, Z.; Feng, C.; Leung, V.C.M. Decentralized Applications: The Blockchain-Empowered Software System. IEEE Access 2018, 6, 53019–53033. [Google Scholar] [CrossRef]
- React. Available online: https://reactjs.org/ (accessed on 17 February 2023).
- Krichen, M.; Lahami, M.; Al-Haija, Q.A. Formal Methods for the Verification of Smart Contracts: A Review. In Proceedings of the 15th International Conference on Security of Information and Networks (SIN), Sousse, Tunisia, 11–13 November 2022; pp. 1–8. [Google Scholar]
- Infura. Available online: https://infura.io/ (accessed on 17 February 2023).
- Google. Available online: https://www.google.com/ (accessed on 17 February 2023).
- Facebook. Available online: https://www.facebook.com/ (accessed on 17 February 2023).






















| Constraints | Hao, J. et al. [13] | Rajalakshmi A. [14] | Sun, J. et al. [18] | Our Proposed Scheme |
|---|---|---|---|---|
| Delay | High delay Collected data is not directly written to an IPFS | Low delay | High delay Encryption of medical data | Low delay in uploading files to IPFS and file hash is automatically stored on BC with help of Smart contract |
| Tampering on the stored data | Possibilities of data tampering | No tampering | No tampering | No tampering of data as data is stored on IPFS and hash on Blockchain |
| Storage capacity | Less Storage capacity Stored on data server | More storage capacity | More storage capacity as the data stored on IPFS | More storage capacity as the data stored on IPFS |
| Heterogeneous data | Uploading only video and images on IPFS | Uploading only PDF’s | Only electronic medical record | Heterogeneous data upload |
| Keyword Search function | No Keyword search function | No Keyword search function | No Keyword search function | Supports Keyword search function |
| Variables | Why It Is Used |
|---|---|
| fileCount | Keeps track of how many files have been added to the current smart contract. |
| mapping File | key value store and lists the files |
| struct | Manage the files |
| event FileUploaded | Allows us to know when the file was uploaded |
| function fileUpload | Uploads new file |
| emit FileUploaded | Trigger an event |
| Scenario # | Description |
|---|---|
| 1 | The system unexpectedly shuts down. When the system restarted, the DApp’s event log vanished. We used ether.js to retrieve the event log. |
| 2 | The information in the keyword search text file was accidentally deleted. We recreated the keyword search text file by using information retrieved from the smart contract event log and performed a keyword search. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
N. Sangeeta; Nam, S.Y. Blockchain and Interplanetary File System (IPFS)-Based Data Storage System for Vehicular Networks with Keyword Search Capability. Electronics 2023, 12, 1545. https://doi.org/10.3390/electronics12071545
N. Sangeeta, Nam SY. Blockchain and Interplanetary File System (IPFS)-Based Data Storage System for Vehicular Networks with Keyword Search Capability. Electronics. 2023; 12(7):1545. https://doi.org/10.3390/electronics12071545
Chicago/Turabian StyleN. Sangeeta, and Seung Yeob Nam. 2023. "Blockchain and Interplanetary File System (IPFS)-Based Data Storage System for Vehicular Networks with Keyword Search Capability" Electronics 12, no. 7: 1545. https://doi.org/10.3390/electronics12071545
APA StyleN. Sangeeta, & Nam, S. Y. (2023). Blockchain and Interplanetary File System (IPFS)-Based Data Storage System for Vehicular Networks with Keyword Search Capability. Electronics, 12(7), 1545. https://doi.org/10.3390/electronics12071545







