Abstract
Current proxy signature schemes are mostly identity-based proxy signatures that distinguish users by identity. This signature method faces some problems, such as identity information leakage and single access control. Attribute-based proxy signature (ABPS) divides the signer’s identity information into a collection of attributes; thus, users’ identity information can be protected and access control can become fine-grained. With the development of quantum computers, the security of signature schemes based on traditional number theory problems is under threat. Therefore, we construct a new attribute-based proxy signature scheme on a lattice that can resist quantum attacks. This scheme has the properties of both attribute-based signatures and proxy signatures, i.e., fine-grained access control and strong undeniability properties. Moreover, based on the small integer solution problem (SIS), our scheme is provably secure in the random oracle model and protects the proxy signer in the adaptive security model.
1. Introduction
With the rapid development of networks, security has become particularly important. Digital signatures can verify the integrity and reliability of a message, and so they have become an indispensable part of security authentication. Due to some special circumstances, the original signer needs to delegate the signature authority to the authorized proxy signer to generate a valid signature on their behalf. The appearance of proxy signatures has resulted in greater convenience. However, how to identify the signer and ensure the reliability of the message has become an important issue. With the improvement of requirements, the signature method has evolved from certificate-based signatures, certificateless signatures and identity-based signatures to attribute-based signatures. At present, most proxy signatures are still identity-based proxy signatures (IBPS), such as [1,2]. This method uses the identity of the signer as the authentication mark to ensure the nonrepudiation and other characteristics of the signature. However, at the same time, it also brings with it a series of problems, such as the possibility of exposing identity information, which is too singular as an identification mark. For this reason, the identity-based signature has been continuously optimized. In 2008, Maji et al. [3] proposed the first attribute-based signature (ABS) scheme, and showed that this signature method has the characteristics of fine-grained access and perfect privacy. The ABS method divides the identity information of the signer into a multiattribute set. The signature can be completed only when the signer’s attributes satisfy the conditions of access control. Thus, attribute-based proxy signature (ABPS) schemes are starting to receive more attention [4,5].
Research on quantum computers has been a hot topic in recent years, and the Shor algorithm [6] has proved that the current state of cryptography based on traditional number theory will no longer be reliable under quantum attacks, such as the ElGamal algorithm and Rivest, Shamir and Adleman (RSA) algorithm. NIST in the United States is also publicly soliciting postquantum cryptography algorithms. Currently, the recognized antiquantum algorithms include lattice-based cryptography, code-based cryptography, hash-based cryptography and multivariate-based cryptography. Lattice-based cryptography has the advantages of simple operation and can construct a variety of advanced cryptographic applications, so it is more widely used. Most ABS and proxy signature schemes are mainly based on traditional number theory problems, such as integer factorization, bilinear pairs and so on [7,8,9,10,11]. These options are more reliable security choices for constructing ABPS schemes based on lattice-based cryptography.
1.1. Related Works
ABS, as a new, important signature method, is used in many areas, such as emerging named data networks [12], edge computing [13], swarm intelligence awareness [14] and healthcare systems [15]. The first ABS scheme [3] was based on groups with bilinear pairs and can only be proved secure in the generic group model. Subsequently, due to these great advantages, ABS has received increasing amounts of attention, and a large number of ABS schemes have been proposed [16,17,18]. The first proxy signature scheme proposed [19] was a full delegation method. The delegation method in proxy signatures is mainly developed as three approaches: full delegation, partial delegation and delegation with warrant. Since delegation with warrant can protect both the proxy signer and the original signer, most of the current schemes use this approach. ABS and proxy signatures are both included in ABPS. The ABPS scheme from Sun [4] is existentially unforgeable against chosen-message attacks (EUF-CMA) in the random oracle model. However, this scheme is constructed on bilinear pairings, which cannot defeat the quantum attack, and there is no security model proposed for this ABPS scheme.
One of the most famous applications of lattice-based cryptography is fully homomorphic encryption [20]. Therefore, homomorphic signatures are widely used [21]. Proxy signature schemes and identity-based proxy signature schemes based on a lattice have also emerged [22,23,24]. Mao et al. [25] proposed the first ABS schemes based on lattices using the preimage sampling technique. Subsequently, more ABS schemes based on lattices were proposed [26,27,28].
1.2. Our Contributions
In this paper, we constructed a new ABPS scheme over a lattice, which is resistant to quantum attacks. Our scheme allows the original signer to sign a warrant using their attribute keys to delegate signing authority. Then, the proxy signer signs the message only when the attribute set of the original signer satisfies the access structure and the warrant is valid. The verifier also checks the original signer’s attributes and the validity of the signature. This feature provides fine-grained access. To sum up, our ABPS scheme has the following properties:
- Fine-grained access control. Only when a signer’s attribute set satisfies the access structure may they assign their signature rights to others. This feature can help us identify the signers in a fine-grained manner.
- Provable security. The ABPS scheme we constructed is provably secure in the random oracle model. It is also more secure than most current ABPS schemes.
1.3. Organization
The rest of the paper is sequenced as follows. Section 2 reviews some basic concepts of the lattice signature scheme. Section 3 introduces the background of the ABPS scheme. Section 4 presents our proposed new scheme. Section 5 analyzes the security of the constructed scheme. Section 6 evaluates the scheme’s performance. Section 7 concludes the paper.
2. Prelimnary
2.1. Lattice
With a set of linearly independent vectors as the lattice’s basis, the lattice can then be expressed as .
Definition 1
(Orthogonal lattice). The orthogonal lattice of Λ is defined as .
Definition 2
(Small integer solution (SIS) problem; see [29]). For a matrix ← , the problem aims to find a nonzero vector ∈ that satisfies = 0 q and β, where β is a real number.
2.2. Gaussian on Lattice
For a positive real number with a center of ∈ , the Gaussian function is defined as ∈ , = .
The discrete Gaussian distribution over lattice is defined as .
2.3. Preimage Sampling Technique
Lemma 1
(see [30]). Given a matrix ∈ , a short trapdoor basis ∈ of , a vector ∈ and a Gaussian parameter s, there exists a probabilistic polynomial-time algorithm, denoted by SamplePre . It outputs a sample e within negligible statistical distance of .
2.4. Bonsai Trees
Bonsai trees contains four main techniques. We predominantly use three of them: controlled growth, extending control and randomizing control.
The following lemma states how the controlled growth technique generates a random lattice under control.
Lemma 2
(see [31]). There exists a probabilistic polynomial-time algorithm GenBasis : given a constant C and m ≥ , GenBasis outputs ∈ and ∈ , such that is the basis of ; ≤ = . The distribution of is within of the uniform, in terms of statistical distance.
Here, we describe the extending control technique, which can extend the control of a lattice to an arbitrary higher-dimensional extension.
Lemma 3
(see [32]). Given ∈ , ∈ and an arbitrary matrix ∈ , where is the basis of , there exists a probabilistic polynomial-time algorithm ExtBasis = | that can output an arbitrary basis ∈ of . Furthermore, satisfies = . However, a disadvantage is that this cannot guarantee the dependence of and .
Finally, we show the randomizing control technique. This technique can randomize the basis of a lattice, such that the resulting basis is independent of the original basis.
Lemma 4
(see [32]). Then, there exists a probabilistic polynomial-time algorithm, denoted by RandBasis . is the basis of , and s ≥ is a Gaussian parameter. This algorithm outputs another basis , satisfying ≤ . For the two different bases of the same lattice, when s ≥ , the outputs of RandBasis and RandBasis( are within in terms of statistical distance.
3. Attribute-Based Proxy Signature Scheme
3.1. Syntax of ABPS Scheme
An ABPS scheme consists of six phases, Setup, Key Extraction, Delegate Generation, Key Extraction for Proxy Signer, Proxy Signing and Verification:
- Setup: In this phase, with a security parameter n as input, it returns the system parameters and the master private key ;
- Key Extraction: The attribute authority selects the original signer’s attribute public key and generates their attribute private key ;
- Delegate Generation: The original signer uses their attribute key to sign a delegate warrant ;
- Key Extraction for Proxy Signer: The proxy signer verifies the warrant and generates their signing key ;
- Proxy Signing: When the original signer’s attribute set satisfies the access structure, the proxy signer generates a signature of the message ;
- Verification: A verifier checks whether the original signer’s attributes satisfies the access structure, then checks the warrant and the signature .
3.2. Security of the ABPS Scheme
An ABPS scheme is mainly concerned with the following security properties: unforgeability, perfect privacy and key dependence.
3.2.1. Unforgeability
Our scheme is strongly unforgeable under the chosen-message attack (SUF-CMA). In our proof, we take two types of adversaries, as follows:
Type I: An adversary knows the secret key of the original signer but cannot obtain the private key of the proxy signer.
Type II: An adversary obtains the secret key of the proxy signer but cannot obtain the private key of the original signer and the delegation of the proxy signer.
Definition 3
(Type I attack). When the following game’s running time is at most and receives hash queries at most times, if no type I adversary can win the game with a probability of at least , then we can say this ABPS scheme is unforgeable under with the type I attack.
Setup: With a security parameter, the challenger executes the Setup and Key Extraction phases. Then, they give the system parameters, the original signer’s attribute public–private key pair and the proxy signer’s public key, to the adversary , keeping the proxy signer’s private key secret.
Query:
- Hash queries:
- (a)
- queries: gives the hash value for any ∈ ;
- (b)
- queries: For the delegate information , returns a matrix of to ;
- Proxy sign queries: With a given message , sends a signature of this message to .
Forgery: gives a new signature for the message . If this signature is valid for , then wins the game.
Definition 4
(Type II attack). When the following game’s running time is at most and receives hash queries at most times, if no type II adversary can win the game with a probability of at least , then we can say this ABPS scheme is unforgeable under with the type II attack.
Setup: With a security parameter, the challenger executes the Setup and Key Extraction phases. Then, they give the system parameters and the original signer’s attribute public key to the adversary , while keeping the original signer’s attribute private key secret.
Query:
- Hash queries: gives the hash value for any ∈ ;
- Delegate generation queries: For the delegate information , returns a warrant of to ;
- Extract proxy signer queries: With the warrant , returns the proxy signer’s signing key pair to .
Forgery: gives a new warrant . If the warrant is valid for the information , then wins the game.
3.2.2. Perfect Privacy
For the perfect privacy requirement, an adversary can obtain the same parameters and information of signers. When the adversary obtains the correct warrant signature, they cannot obtain information about the signer. An attribute-based proxy signature scheme can satisfy these conditions: All ← ABPS. Setup, all attributes sets , , all attribute secret keys ← ABPS. Key Extraction , ← ABPS. Key Extraction , all delegate information , and all claim access control L, such that = L. If the distributions of ABPS.Delegate Generation and ABPS.Delegate Generation are equal, as a result, this attribute-based proxy signature scheme provides perfect privacy.
3.2.3. Key Dependence
The proxy signer cannot sign a message without the original signer’s delegation.
4. Proposed ABPS Scheme
In this section, we present our scheme over a lattice.
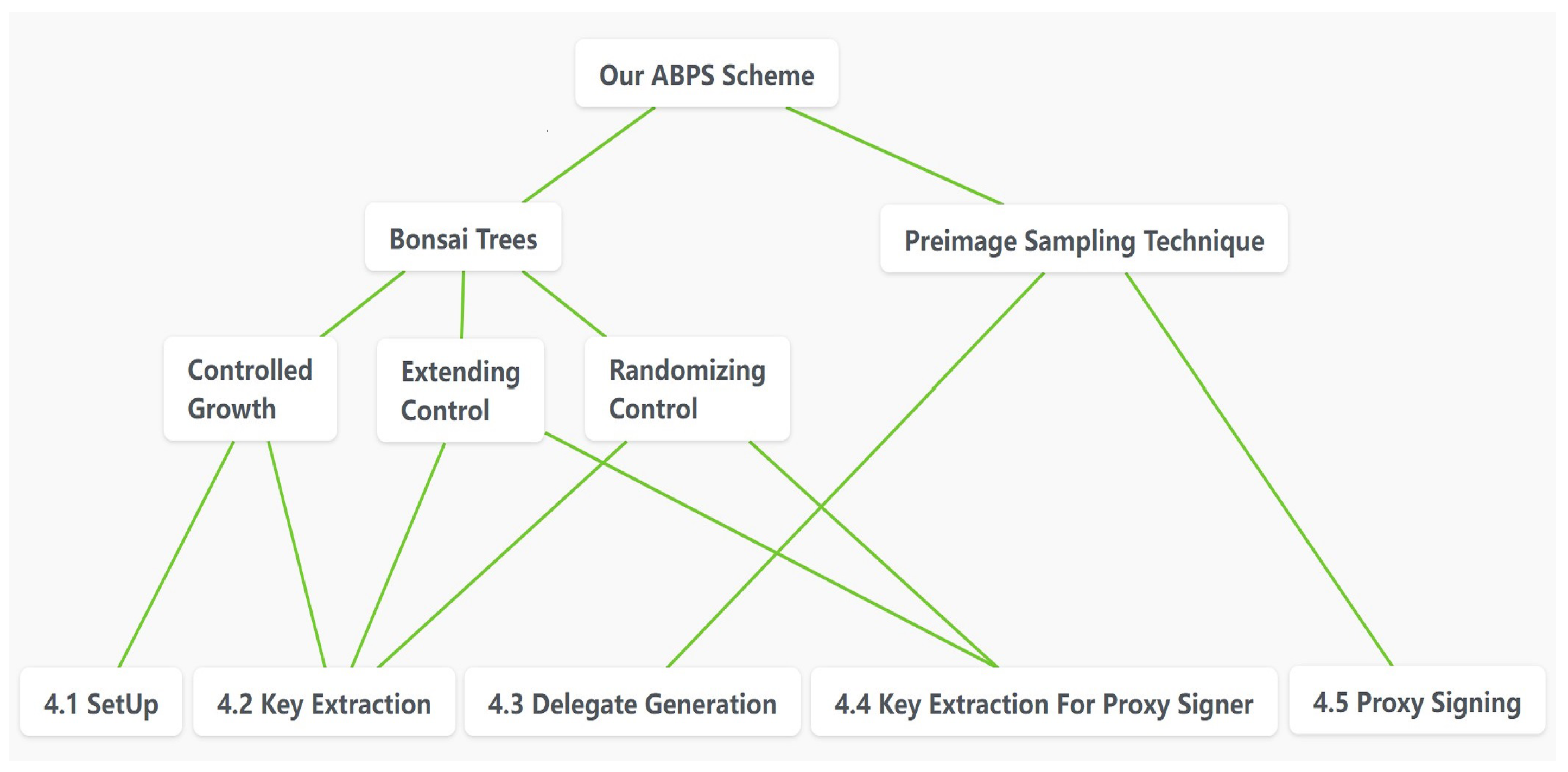
The main methods we use are bonsai trees and the preimage sampling algorithm. In our scheme, attributes led to an increase in the dimension of lattices, and bonsai trees can help generate the trapdoor of the growth lattice. Above all, the controlled growth in bonsai trees can generate the lattice and its trapdoor, such that the trapdoor satisfies the size we need. We set the lattice and its trapdoor as the initial key. Then, we combined the initial lattice generated for the original signer and some selected matrices as the original signer’s attribute public key, and the proxy signer’s signing public key was composed of the initial key generated for the proxy signer and a matrix generated by the original signer’s warrant. Then, the extending control and randomizing control technique was used to generate the original signer’s attribute private key and the proxy signer’s signing private key. Finally, we used the preimage sampling algorithm to complete the warrant and signature.
Our scheme consists of six phases: Setup, Key Extraction, Delegate Generation, Key Extraction for Proxy Signer, Proxy Signing and Verification. The technical architecture of our scheme is shown in Figure 1.
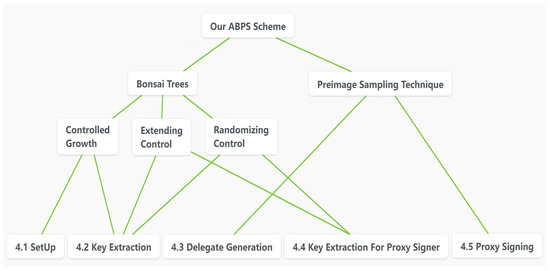
Figure 1.
The framework of our scheme.
Here, we describe this scheme in detail. In this scheme, for the attribute universe , we let .
4.1. Setup
In this phase, given a security parameter n, the public system parameter is then published, and the master private key is kept secret. The details are given in Algorithm 1.
| Algorithm 1 Setup |
|
4.2. Key Extraction
The algorithm of this phase is given in Algorithm 2. Firstly, we need a trusted attribute authority (AA) to generate the attribute public key for the original signer and then generate the attribute private key . The proxy signer’s public–private key pair is . We need to keep and secret.
| Algorithm 2 Key Extraction |
|
4.3. Delegate Generation
The original signer signs their delegate information by . Then, the warrant = is published. The algorithm is described in Algorithm 3.
| Algorithm 3 Delegate Generation |
|
4.4. Key Extraction for Proxy Signer
The proxy signer verifies the warrant using Algorithm 4. If the result is , then Algorithm 5 is executed to generate the signing key pair . is the signing public key, and is the private key.
| Algorithm 4 Verify Warrant |
|
| Algorithm 5 Key Extraction for Proxy Signer |
|
4.5. Proxy Signing
The proxy signer executes Algorithm 6 to generate the signature of message . Then, they send = to the verifier.
| Algorithm 6 Proxy Sign |
|
4.6. Verification
The verifier first runs the Verify I algorithm described in Algorithm 7. In this algorithm, they should check whether the attribute set of the original signer satisfies the access structure and the validity of warrant = . If the result is true, then the signature is verified in Algorithm 8, and it is decided whether to accept or reject it.
| Algorithm 7 Verify I |
|
| Algorithm 8 Verify II |
|
Remark 1.
This scheme is based on the SIS problem presented in Definition 2. Nevertheless, with the bonsai tree technique we used, the dimensions of the lattice and its trapdoor increase; thus, the SIS problem also changes here.
Theorem 1.
The achievement of a signature in our ABPS scheme is based on the problem, where .
Proof.
Assuming that ∈ is the matrix in the problem, then the target nonzero vector ∈ .
For the signature, = = | = |. Due to ∈ and = → , = | ∈ . Then, the aim is to find a nonzero vector ∈ .
So, the problem is based here on = . □
Theorem 2.
The achievement of a warrant in our ABPS scheme is based on the problem, where .
Proof.
Assuming that ∈ is the matrix in the problem, then the target nonzero vector ∈ .
For the warrant, = = ||…|. We know ∈ , where j ∈ k and b = in Algorithm 1; thus, ∈ . Then, the aim is to find a nonzero vector ∈ .
So the problem here is based on = . □
4.7. Correctness Analysis
If we execute the phases in Section 4.1, Section 4.2, Section 4.3, Section 4.4, Section 4.5 and Section 4.6 correctly, then we can provide a correctness analysis. Here, we need to check both the warrant and the signature.
- Firstly, for the warrant, if , then , where , and . Furthermore, , so
- Secondly, for the signature, due to ,
5. Security Analysis
In this section, we analyze the following aspects of the security of this scheme: unforgeability, perfect privacy and key dependence.
5.1. Unforgeability
In the random oracle model, our ABPS scheme is strongly unforgeable under the adaptive chosen-message attack.
Theorem 3.
If a polynomial-time type I adversary successfully forges a valid signature in ROM, then the problem can be solved, where and .
Proof .
Assume the scheme can be broken by a type I adversary with a non-negligible probability. Then, the challenger can solve an example of the problem with non-negligible probability in polynomial time. This means that wins.
Setup: The security parameter n is inputted, and runs Algorithms 1 and 2 to generate , and . Then, sends , and to , keeping secret. creates several empty lists: L1, L2, L3 and L4. L1 records , L2 records , L3 records and L4 records , where is the signature of message .
Query: adaptively asks several queries of , and answers these, directed toward .
- queries:
- (a)
- sends delegate information to , and then finds in L1. returns the hash value to when it is found. Otherwise, chooses a vector at random, restores into L1 and returns ;
- (b)
- sends a message to , and finds in L3. returns the corresponding value to when it is found. Otherwise, chooses a vector ∈ at random, restores into L3 and returns .
- queries: first finds the warrant = in L2. returns the hash value to when it is found. Otherwise, chooses a matrix ∈ at random, restores into L2 and returns ;
- Proxy sign queries: finds the message in L4, if there exists , and then returns to . Otherwise, runs Algorithm 6 to generate the signature of , and then restores in L4 and sends to .
Forgery: After completing these queries, generates a forging signature on message with non-negligible probability. If this signature passes the phase in Section 4.6 and the message cannot be found in L3 and L4, then wins the game.
uses queries to obtain = , then generates the signature through the proxy sign phase. Then, we obtain | · = q and | · = q; so, | · − = 0 q. According to [30], we know that = happens with negligible probability without a trapdoor. ≤ and ≤ , and then − ≤ is an answer of . Therefore, can solve the instance with non-negligible probability . □
Theorem 4.
If a polynomial-time type II adversary successfully forges a valid signature in ROM, then the problem can be solved, where β = and = .
Proof .
Assume the scheme can be broken by a type II adversary with a non-negligible probability. Then, the challenger can solve an example of the problem with non-negligible probability in polynomial time. This means wins.
Setup: The security parameter n is input, and runs Algorithms 1 and 2 to generate , and . Then, sends , and to , keeping secret. creates several empty lists: L1, L2, L3 and L4. L1 records = , L2 records = , L3 records = and L4 records = , where is the warrant of .
Query: adaptively asks several queries of , and answers these, directed toward .
- queries:
- (a)
- sends delegate information to , and then finds in L1. returns the hash value to when it is found. Otherwise, chooses a vector ∈ at random, restores into L1 and returns ;
- (b)
- sends a message to , and finds in L3. returns the corresponding value to when it is found. Otherwise, chooses a vector ∈ at random, restores into L3 and returns .
- Delegate generation queries: For the delegate information , performs as follows:
- (a)
- First, is found in L4. If found, returns the value to . Otherwise, seeks it in L1;
- (b)
- If there exists in L1, then returns . Otherwise, carries out the queries. Then, generates ← SamplePre , restores = into L4 and returns to .
- queries: For the warrant = , performs as follows:
- (a)
- First, is found in L2. returns the hash value to when it is found. Otherwise, seeks in L4;
- (b)
- If cannot be found in L4, carries out the delegate queries. Then, chooses a matrix ∈ at random, restores into L2 and returns .
- Extract proxy signer queries: For the warrant , performs as follows:
- (a)
- First, in L2 is found. If found, obtains the hash value . Otherwise, carries out the queries;
- (b)
- Then, obtains = |, and runs RandBasis(ExtBasis( to obtain the private signing key ;
- (c)
- returns to .
Forgery: After completing these queries, generates a forging warrant = on delegate information with non-negligible probability. If the warrant passes the Algorithm 7 and cannot be found in L2 and L4, then wins the game.
looks up in L4, and if found, obtains the warrant . Otherwise, queries are used to obtain = , and then the warrant = is generated through the delegate generation phase. Then, we can obtain · = q and · = q, so · − = 0 q. According to the result in [30], we know that = happens with negligible probability without a trapdoor. Because ≤ and ≤ , then ≤ is an answer for . Therefore, can solve the instance with non-negligible probability . □
5.2. Perfect Privacy
Theorem 5.
Our ABPS scheme is perfectly private, if the outcomes of RandBasis and RandBasis are within statistical distance.
Proof .
Assume that the outputs of ABPS.Delegate Generation ( ) and ABPS.Delegate Generation ( ) can be distinguished by an adversary with non-negligible probability. Then, the challenger can distinguish an example of the outputs of RandBasis( s) and RandBasis( s) with non-negligible probability in polynomial time. This means that wins.
Setup: runs Algorithm 1 with the security parameter n to generate and . Then, with the attribute sets and , the game runs as follows:
- generates the warrant with the attribute set : Firstly, generates the attribute signing key ← ABPS.Key Extraction ; then, for the delegate information , generates the warrant ← ABPS. Delegate Generation ( );
- generates the warrant with the attribute set : Firstly, generates the attribute signing key ← ABPS.Key Extraction ; then, for the delegate information , generates the warrant ← ABPS. Delegate Generation ( ).
Distinguish: After game 3 finishes, attempts to distinguish the warrants and on delegate information with non-negligible probability. If can distinguish the warrants and successfully, then wins the game.
When , Algorithm 2 selects the same . With the same system parameters and , Algorithm 2 generates the = ||…| and = ||…|. Thus, = . For the warrant = , = , there exists · = q and · = q. winning game 3 means · ≠ q and · ≠ q. Due to these conditions, = , and the same delegate information and the same hash function = → . This means can distinguish ← RandBasis(ExtBasis( s) and ← RandBasis(ExtBasis( s).
According to Lemma 4, RandBasis( s) and RandBasis( s) are statistically indistinguishable. ← SamplePre( and ← SamplePre( are on the same Gaussian distribution with negligible statistical distance. Thus, cannot distinguish ← RandBasis(ExtBasis( s) and ← RandBasis(ExtBasis( s). Our scheme is perfectly private. □
5.3. Key Dependence
Theorem 6.
Our ABPS scheme has the key dependence property if the adversary cannot sign a message without the delegate warrant.
Proof .
Assume that there is a signature generated by an adversary without a delegate warrant. Then, the challenger can complete this proxy signature independently with non-negligible probability in polynomial time. This means that wins.
Setup: The security parameter n is inputted, and runs Algorithms 1 and 2 to generate and . Then, sends and to . creates several empty lists, including L1. L1 records = .
Query: adaptively asks several queries of , and answers these, directed toward .
- queries: sends a message to , and finds in L1. returns the corresponding value to when it is found. Otherwise, selects a vector ∈ randomly, then restores into L1 and returns .
- Extract proxy signer queries: Because there is no warrant in this game, then decides the key pair ( ) for the proxy signer’s signing key and informs .
Forgery: After these queries, outputs a signature of message with non-negligible probability. If it can pass Algorithms 7 and 8 during phase verification, then wins the game.
However, there is no warrant and delegate information, so this signature cannot pass Algorithm 8. Furthermore, owns the signing key without warrant information. Thus, this signature is only ’s own signature, not a proxy signature, and therefore cannot pass Algorithm 7. cannot complete the proxy signature scheme with the non-negligible probability of no delegation. Thus, this scheme has the key dependence property. □
6. Performance Evaluation
In this section, we compare our scheme with two IBPS schemes over a lattice and one ABPS scheme over bilinear pairings from three fields: computation costs, storage size and security properties.
6.1. Computational Cost
Firstly, we compare the computation costs of these schemes in Table 1 and define some notations as follows: is the execution time of a SamplePre() operation; is the execution time of a polynomial multiplication; is the execution time of a scale multiplication of the bilinear pairing; is the the execution time of a bilinear pairing operation; and is the execution time of a general hash function operation.

Table 1.
A comparison of computation costs.
The IBPS scheme from Kim [22] and our scheme use the same preimage sampling technique to sign the delegate warrant and achieve the signature, with a scheme signing cost of . The two signing lattices in Kim’s scheme are both , which resulted in a verification cost of . In our scheme, the lattices of the original signer and proxy signer are and , respectively. Thus, our scheme’s verification cost is also . The IBPS scheme from Zhu [1] uses the rejection sampling technique in the NTRU lattice, which has lower computation costs. Furthermore, the ABPS scheme from Sun [4] is built on bilinear pairings.
6.2. Storage
We compare the storage size of these schemes in Table 2 and define some notations as follows: OPK: the original signer’s public key size; OSK: the original signer’s secret key size; WS: the warrant’s size; PPK: the proxy signer’s public key size; PSK: the proxy signer’s secret key size; and SS: the signature size. In Kim’s scheme [22], and . The parameters are denoted in Zhu’s scheme [1] as follows: , , and . Furthermore, in Sun’s scheme, is a cyclic group with a prime order p. is a security parameter.

Table 2.
A comparison of storage overheads.
6.3. Security Properties
Finally, we compare the security properties of these schemes in Table 3, and some notations are defined as follows: EUF-CMA: existentially unforgeable against chosen-message attacks; EUF-sA-CMA: existentially unforgeable under selective attributes and adaptive chosen-message attacks; and SUF-CMA: strongly unforgeable against chosen-message attacks.

Table 3.
A comparison of security properties.
Among these schemes, Zhu’s scheme is constructed on an NTRU lattice. With the rejection sampling technique, their scheme has the lowest costs. Our ABPS scheme uses the preimage sampling and extending control technique of “bonsai trees” to ensure that the attribute can be protected in keys. This causes our scheme to have higher costs.
Notwithstanding, in Table 3, our scheme is strongly unforgeable under a chosen-message attack, whereas all others are existentially unforgeable under a chosen-message attack. Furthermore, our ABPS scheme has the perfect privacy property. Lastly, our scheme over a lattice can resist quantum attacks; thus, this scheme provides more robust security.
7. Conclusions
In this paper, we design an ABPS scheme that can resist quantum attacks. The new scheme allows a signer whose attributes satisfy the access structure to delegate their signing rights to other people. This scheme supplies many features, such as fine-grained access and perfect privacy. Then, based on the lattice SIS problem, we present the security proof of this scheme under the random oracle model. Finally, performance analysis was used to evaluate the computing, storage and security comparisons. The results show that our scheme has stronger unforgeability and is more secure. However, our solution still suffers from high computational and storage consumption. In the future, we will consider using the rejection sampling technique to implement the ABPS scheme. The rejection sampling technique can help to reduce the computational and storage costs compared with the preimage sampling technique.
Author Contributions
Conceptualization, L.W.; methodology, L.W.; software, L.W. and D.L.; validation, L.W.; resources, D.L.; data curation, Z.L.; writing—original draft preparation, L.W.; writing—review and editing, L.W. and D.L.; supervision, D.L.; project administration, D.L.; funding acquisition, D.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (no. 61662004).
Data Availability Statement
No new data were created.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhu, H.; Tan, Y.; Yu, X.; Xue, Y.; Zhang, Q.; Zhu, L.; Li, Y. An identity-based proxy signature on NTRU lattice. Chin. J. Electron. 2018, 27, 297–303. [Google Scholar] [CrossRef]
- Wu, F.; Zhou, B.; Zhang, X. Identity-based proxy signature with message recovery over NTRU lattice. Entropy 2023, 25, 454. [Google Scholar] [CrossRef]
- Maji, H.; Prabhakaran, M.; Rosulek, M. Attribute-based signatures: Achieving attribute-privacy and collusion-resistance. Cryptol. ePrint Arch. 2008, 1–23. [Google Scholar]
- Sun, C.; Guo, Y.; Li, Y. One secure attribute-based proxy signature. Wirel. Pers. Commun. 2018, 103, 1273–1283. [Google Scholar] [CrossRef]
- Hong, H.; Sun, Z.; Xia, Y. Achieving secure and fine-grained data authentication in cloud computing using attribute based proxy signature. In Proceedings of the 2017 4th International Conference on Information Science and Control Engineering (ICISCE), Changsha, China, 21–23 July 2017; pp. 130–134. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Su, J.; Cao, D.; Zhao, B.; Wang, X.; You, I. ePASS: An expressive attribute-based signature scheme with privacy and an unforgeability guarantee for the Internet of Things. Future Gener. Comput. Syst. 2014, 33, 11–18. [Google Scholar] [CrossRef]
- Sakai, Y.; Attrapadung, N.; Hanaoka, G. Attribute-based signatures for circuits from bilinear map. In Public-Key Cryptography–PKC 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 283–300. [Google Scholar] [CrossRef]
- Sun, Y.; Xu, C.; Yu, Y.; Mu, Y. Strongly unforgeable proxy signature scheme secure in the standard model. J. Syst. Softw. 2011, 84, 1471–1479. [Google Scholar] [CrossRef]
- Boldyreva, A.; Palacio, A.; Warinschi, B. Secure proxy signature schemes for delegation of signing rights. J. Cryptol. 2012, 25, 57–115. [Google Scholar] [CrossRef]
- Lee, N.Y.; Lee, M.F. The security of a strong proxy signature scheme with proxy signer privacy protection. Appl. Math. Comput. 2005, 161, 807–812. [Google Scholar] [CrossRef]
- Ramani, S.K.; Tourani, R.; Torres, G.; Misra, S.; Afanasyev, A. Ndn-abs: Attribute-based signature scheme for named data networking. In Proceedings of the 6th ACM Conference on Information-Centric Networking, Macao, China, 24–26 September 2019; pp. 123–133. [Google Scholar] [CrossRef]
- Li, Y.; Chen, X.; Yin, Y.; Wan, J.; Zhang, J.; Kuang, L.; Dong, Z. SDABS: A flexible and efficient multi-authority hybrid attribute-based signature scheme in edge environment. IEEE Trans. Intell. Transp. Syst. 2020, 22, 1892–1906. [Google Scholar] [CrossRef]
- Hong, H.; Hu, B.; Sun, Z. An efficient and secure attribute-based online/offline signature scheme for mobile crowdsensing. Hum.-Centric Comput. Inf. Sci. 2021, 11, 1–12. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. PAX: Using pseudonymization and anonymization to protect patients’ identities and data in the healthcare system. Int. J. Environ. Res. Public Health 2019, 16, 1490. [Google Scholar] [CrossRef]
- Chen, Y.; Li, J.; Liu, C.; Han, J.; Zhang, Y.; Yi, P. Efficient attribute based server-aided verification signature. IEEE Trans. Serv. Comput. 2021, 15, 3224–3232. [Google Scholar] [CrossRef]
- Gardham, D.; Manulis, M. Hierarchical attribute-based signatures: Short keys and optimal signature length. In Proceedings of the International Conference on Applied Cryptography and Network Security, Bogota, Colombia, 5–7 June 2019; Springer: Cham, Switzerland, 2019; pp. 89–109. [Google Scholar] [CrossRef]
- Herranz, J.; Laguillaumie, F.; Libert, B.; Rafols, C. Short attribute-based signatures for threshold predicates. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Francisco, CA, USA, 27 February–2 March 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 51–67. [Google Scholar] [CrossRef]
- Mambo, M.; Usuda, K.; Okamoto, E. Proxy signatures for delegating signing operation. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, New Delhi, India, 14–15 March 1996; pp. 48–57. [Google Scholar] [CrossRef]
- Gentry, C. Fully homomorphic encryption using ideal lattices. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, MD, USA, 31 May–2 June 2009; pp. 169–178. [Google Scholar]
- Gu, Y.; Shen, L.; Zhang, F.; Xiong, J. Provably secure linearly homomorphic aggregate signature scheme for electronic healthcare system. Mathematics 2022, 10, 2588. [Google Scholar] [CrossRef]
- Kim, K.S.; Hong, D.; Jeong, I.R. Identity-based proxy signature from lattices. J. Commun. Netw. 2013, 15, 1–7. [Google Scholar] [CrossRef]
- Li, W. An identity-based proxy signature scheme from lattices in the standard model. In Proceedings of the 2016 International Conference on Intelligent Networking and Collaborative Systems (INCoS), Ostrava, Czech Republic, 7–9 September 2016; pp. 167–172. [Google Scholar] [CrossRef]
- Yang, C.; Qiu, P.; Zheng, S.; Wang, L. An efficient lattice-based proxy signature scheme without trapdoor. In Proceedings of the 2015 International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Adelaide, SA, Australia, 23–25 September 2015; pp. 189–194. [Google Scholar] [CrossRef]
- Mao, X.p.; Chen, K.f.; Long, Y.; Wang, L.l. Attribute-based signature on lattices. J. Shanghai Jiaotong Univ. (Sci.) 2014, 19, 406–411. [Google Scholar] [CrossRef]
- Luo, F.; Al-Kuwari, S. Attribute-based signatures from lattices: Unbounded attributes and semi-adaptive security. Des. Codes Cryptogr. 2022, 90, 1157–1177. [Google Scholar] [CrossRef]
- Gardham, D.; Manulis, M. Revocable hierarchical attribute-based signatures from lattices. In Proceedings of the 20th International Conference on Applied Cryptography and Network Security, ACNS 2022, Rome, Italy, 20–23 June 2022; Springer: Cham, Switzerland, 2022; pp. 459–479. [Google Scholar]
- El Kaafarani, A.; Katsumata, S. Attribute-based signatures for unbounded circuits in the ROM and efficient instantiations from lattices. In Proceedings of the IACR International Workshop on Public Key Cryptography, Rio de Janeiro, Brazil, 25–29 March 2018; Springer: Cham, Switzerland, 2018; pp. 89–119. [Google Scholar] [CrossRef]
- Ajtai, M. Generating hard instances of lattice problems. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 99–108. [Google Scholar] [CrossRef]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar] [CrossRef]
- Alwen, J.; Peikert, C. Generating shorter bases for hard random lattices. Theory Comput. Syst. 2011, 48, 535–553. [Google Scholar] [CrossRef]
- Cash, D.; Hofheinz, D.; Kiltz, E.; Peikert, C. Bonsai trees, or how to delegate a lattice basis. J. Cryptol. 2012, 25, 601–639. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).