Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management
Abstract
1. Introduction
2. Related Work
2.1. Aviation Industry
- The Air Traffic Control Cyber Security Project (ACSP) [8], an air traffic control (ATC) information security project led by the U.S. Cyber Security Forum Initiative (CSFI) organization, aims to uncover and identify cyber security vulnerabilities in ATC system and airborne system in the NextGen project, which is currently being upgraded and promoted, and to minimize the risk of such vulnerabilities. They conducted penetration tests for scenarios in which attackers exploit ATC system vulnerabilities with a collaborative approach to launch cyber attacks on U.S. airports.
- The Global ATM Security Management (GAMMA) project in Europe [9] conducted a systematic study of cybersecurity management issues in SESAR program. The project, funded by the European Union’s Seventh Framework Program project, conducts a comprehensive assessment of possible serious security threats and vulnerabilities in ATM, and studies effective solutions to improve the security performance of the system.
- The German project Air Traffic Resilience (ARIEL) [10], based on the research results of the European SESAR project, provides an overall risk assessment of potential cyber attack threats to the critical infrastructure of the aviation system. At the same time, with the help of air traffic simulators, a scenario-oriented approach is used to analyze the risk of different cyber attack scenarios and ultimately achieve the goal of improving flight safety.
2.2. Academic Community
2.3. Contribution and Organization
3. ATM Security Concerns and Trends
3.1. Security Concerns
- (a)
- Simple information security product stacking.
- (b)
- The scope of information security protection and evaluation is limited.
- (c)
- Lack of systematic security assurance system structure.
3.2. The Trends
- (a)
- Networked ATM faces the control challenges of proliferation of flight density and diversification of air vehicle types, and its cyber security is under serious threat.
- (b)
- With the development of software-defined radio technology and the high versatility of ATM devices, the scope of cyber attacks against ATM is expanding, cyber attack modes are emerging, threat models are evolving, yet a unified and effective cyber threat model has not yet been constructed.
- (c)
- Due to the lack of effective and credible theoretical research results on the intrinsic connection between information security and flight safety, the analysis of the propagation path of the impact of cyber attacks in the ATM is still largely lacking, resulting in a gap in the understanding of the importance of ATM cyber security between the cyber security field and the ATM field.
- (d)
- ATM has special cyber security needs, and it is urgent to build a complete networked ATM cyber security defense solution to ensure the operational efficiency and flight safety of the system.
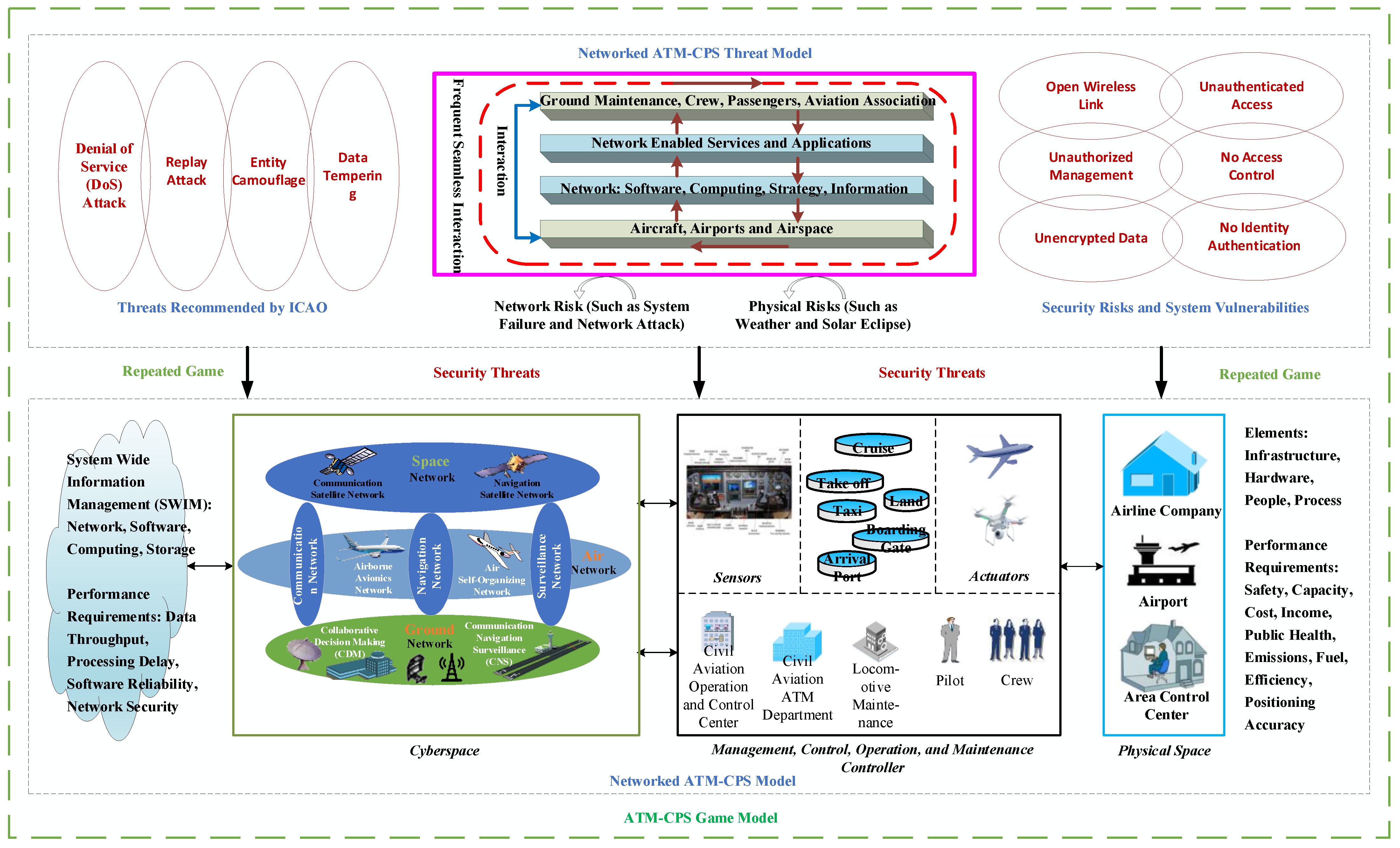
4. Networked ATM-CPS Model and Its Threat Model
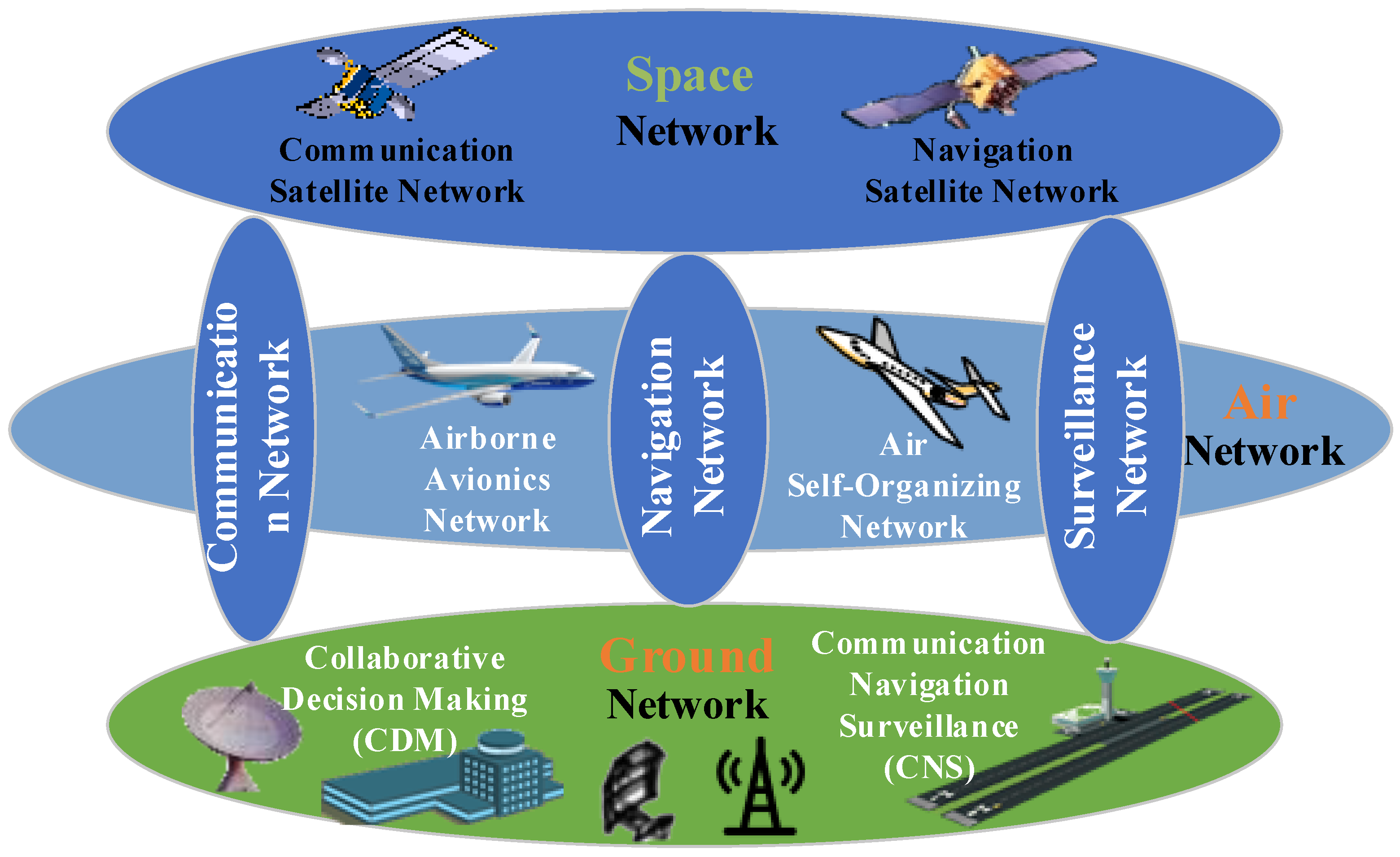
4.1. Networked ATM-CPS Model
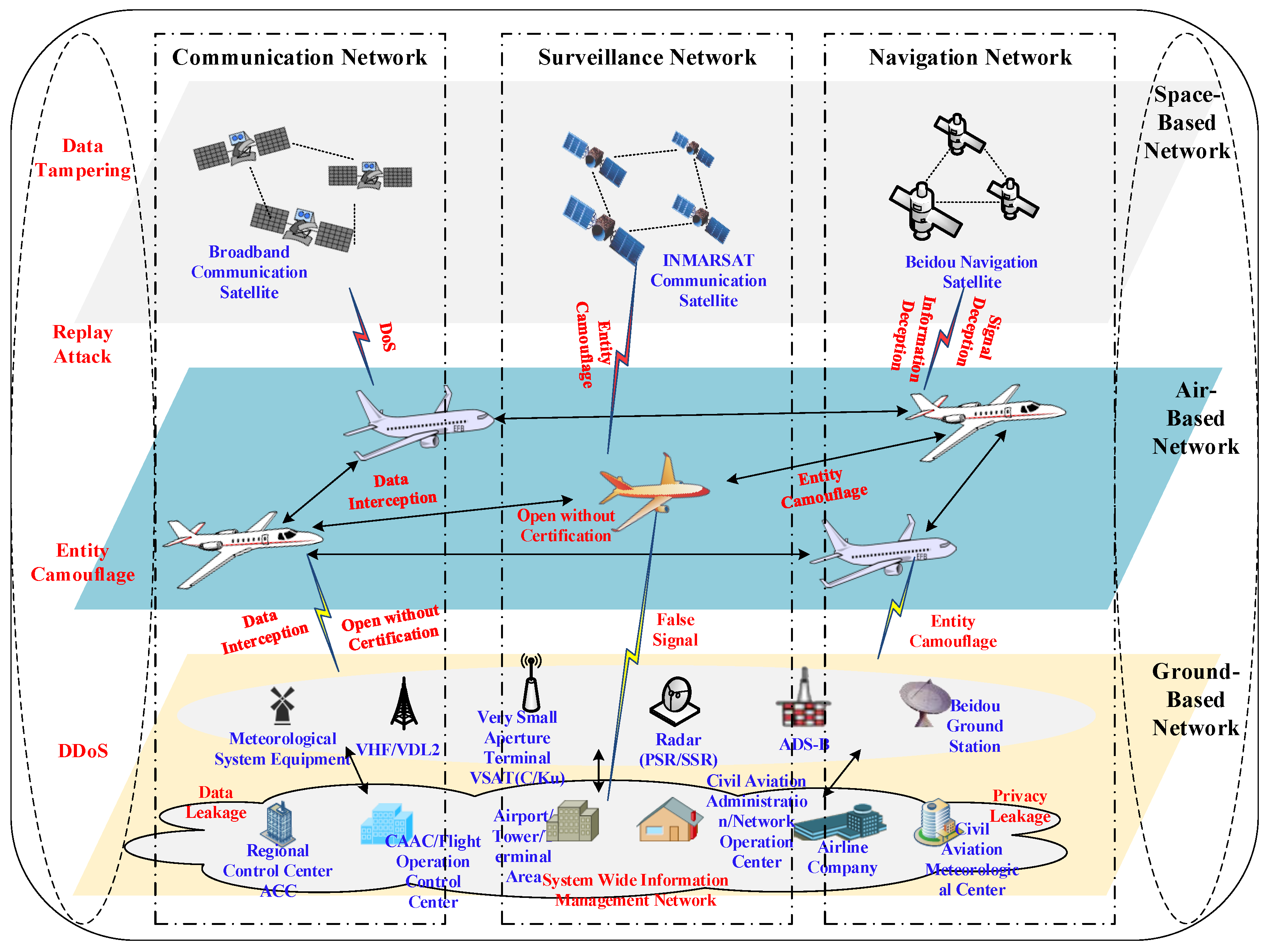
4.2. Networked ATM-CPS Threat Model
- (a)
- Quantitative analysis of the impact of security threats on the core performance of ATM system.
- Security hazards. There is a need to analyze and study the openness and lack of authentication issues for ADS-B system links, ground and air data link systems, and Beidou civil navigation messages in networked ATM.
- System vulnerabilities. The system vulnerabilities, such as explicit data transmission (without encryption/decryption processing) of networked ground–space data link and VSAT network (C/Ku-band) in ATM, as well as the modem of ATM automation system (especially when its port is open), are to be identified and excavated.
- Security threats. The security threats faced by the networked ATM are dissected individually, such as entity masquerading to generate fake signals in ADS-B systems, data tampering in ACARS systems, location information spoofing in Beidou civil navigation messages, entity masquerading, and DDoS attack.
- (b)
- Establishment of influencing factors and system model of networked ATM system security metrics.
- (c)
- Quantitative reference framework and expression method for studying safety characteristics of ATM.
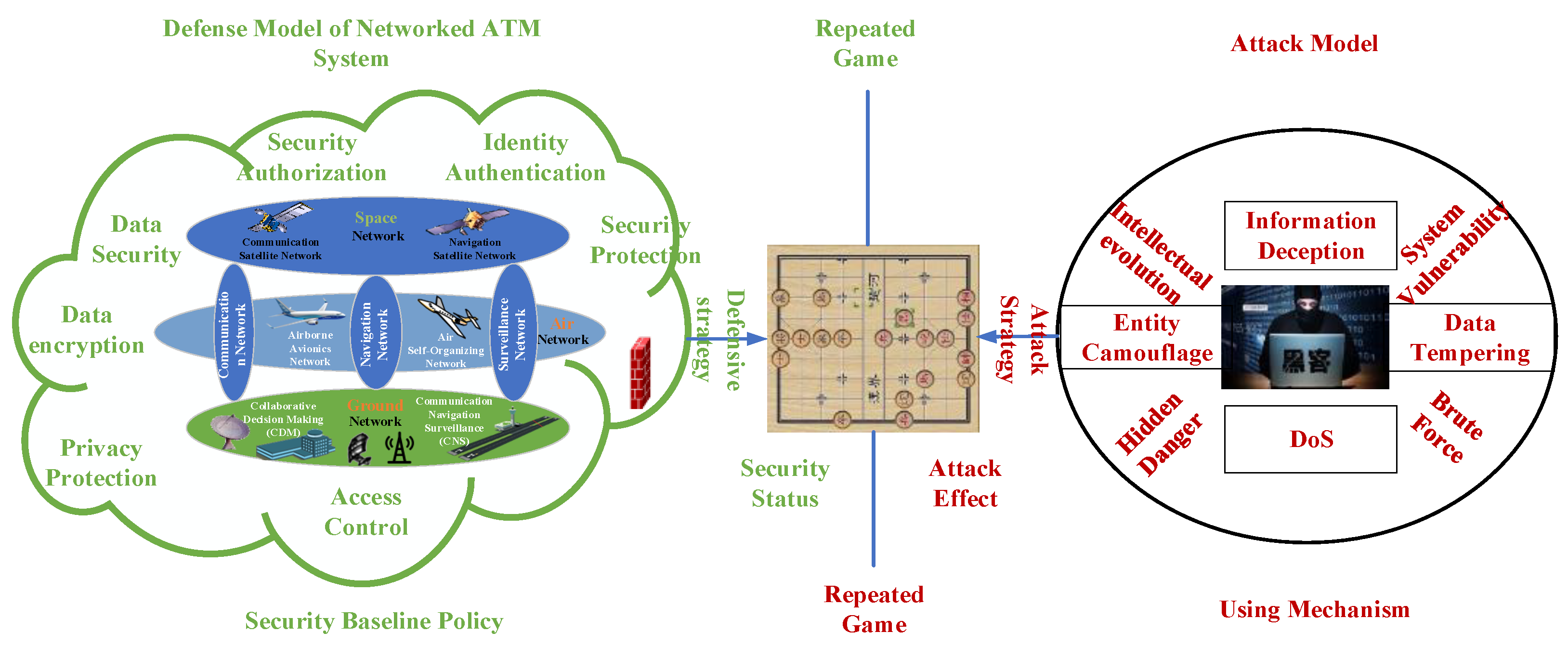
5. Networked ATM-CPS Game Model
5.1. Game Modeling of Networked ATM-CPS
- (a)
- ATM-CPS information security situation assessment.
- Design the architecture of security situational awareness system of ATM system based on multi-sensor. For the processing mode of distributed collection and acquisition of ATM business data by ATM system equipment, the resource equipment and system mesh physical structure of ATM system and the hierarchical model of equipment layer, transmission layer, and application layer should be designed.
- Design a solution for eXML format of multi-source heterogeneous security information in ATM. The system structure framework of security situation awareness of the ATM system is divided into information collection layer, element extraction layer, and situation decision-making layer from bottom to top, including three steps: detection data fusion, establishment of threat propagation network (TPN), and evaluation of CPS game model. The CPS game model is used to comprehensively evaluate the security situation of each subsystem of the ATM system from the perspectives of attack and defense, and the development trend of the security situation of the entire networked ATM system is obtained through the quantitative evaluation method of network security situation, thus providing a reference for the security situation prediction of the ATM.
- (b)
- ATM-CPS information security situation prediction.
- Security event embedding method. The security events faced and suffered by networked ATM should be sorted out, and the security event embedding method should be investigated to represent them as dense vectors using Neural Tensor Network (NTN) and train them for security events.
- Dynamic prediction model of security situation based on deep convolutional neural network. The deep convolutional neural network should be used to model the impact of security incidents in the networked ATM; thus, a dynamic prediction model of the security situation of the networked ATM based on the deep convolutional neural network is established. Genetic algorithm should be used to optimize the model and realize the nonlinear time series prediction of the security situation of networked ATM.
- (c)
- Bayesian Nash equilibrium security protection strategy for ATM-CPS.
- A dynamic Bayesian game model is proposed to determine the type of attackers, the equilibrium strategies of both sides of the game are obtained according to the process of repeated game, and the incomplete information game is converted into the complete information game to obtain the Bayesian Nash equilibrium solution.
- The game tree is established through reverse induction, and the attack process facing the ATM-CPS is analyzed to obtain the equilibrium path of the game tree. According to the known attack types faced by the ATM-CPS determined by the threat model and the unknown attack types determined by the Bayesian game strategy, the best protection measures are selected. It provides decision-making for ATM-CPS information security protection, and lays a foundation for building a systematic ATM-CPS information security assurance architecture.
5.2. A Game Modeling Method of Networked ATM-CPS Based on Bayesian Nash Equilibrium Strategy
- (a)
- Security situation assessment method of networked ATM-CPS based on Bayesian game theory.
- Using Bayesian game theory to simulate the attack characteristics of the attack modes (deception attack and DDoS attack) in the real networked ATM system and the defense characteristics of networked ATM system based on security baseline strategy, forming a non-cooperative incomplete information game.
- Analyzing the attack behavior of the networked ATM system and using Bayesian law to continuously modify the probability value of the resource subsystem or network containing malicious intrusion tendency in the networked ATM system.
- Predicting the networked ATM system and attackers according to the information they have obtained and quantitatively describing and depicting the change trend of the networked ATM system.
- Predicting the hacker’s behavior according to the security status of the current networked ATM system to make a prediction and evaluation of the security situation of the networked ATM system.
- (b)
- Constructing the ATM-CPS game model based on Bayesian Nash equilibrium strategy.
- Simulate the dynamic behavior of the ATM-CPS under normal conditions and the behavior under network attacks.
- Study the difference parameters based on ATM and attacker. For example, detection frequency, attacker’s understanding of the system, physical damage parameters, and attacker’s punishment attack detection results may affect the security of CPS.
- Use game theory to study the Bayesian Nash equilibrium strategy of attackers and ATM systems under different interdependence conditions and estimate the attack and detection probability according to special defensive and antagonistic parameters (known and unknown attacks can be detected and identified using intelligent algorithms).
- Evaluate the security indicators of the ATM-CPS on the basis of the threat model (e.g., availability, failure time).
6. Networked ATM-CPS Security Assurance Architecture
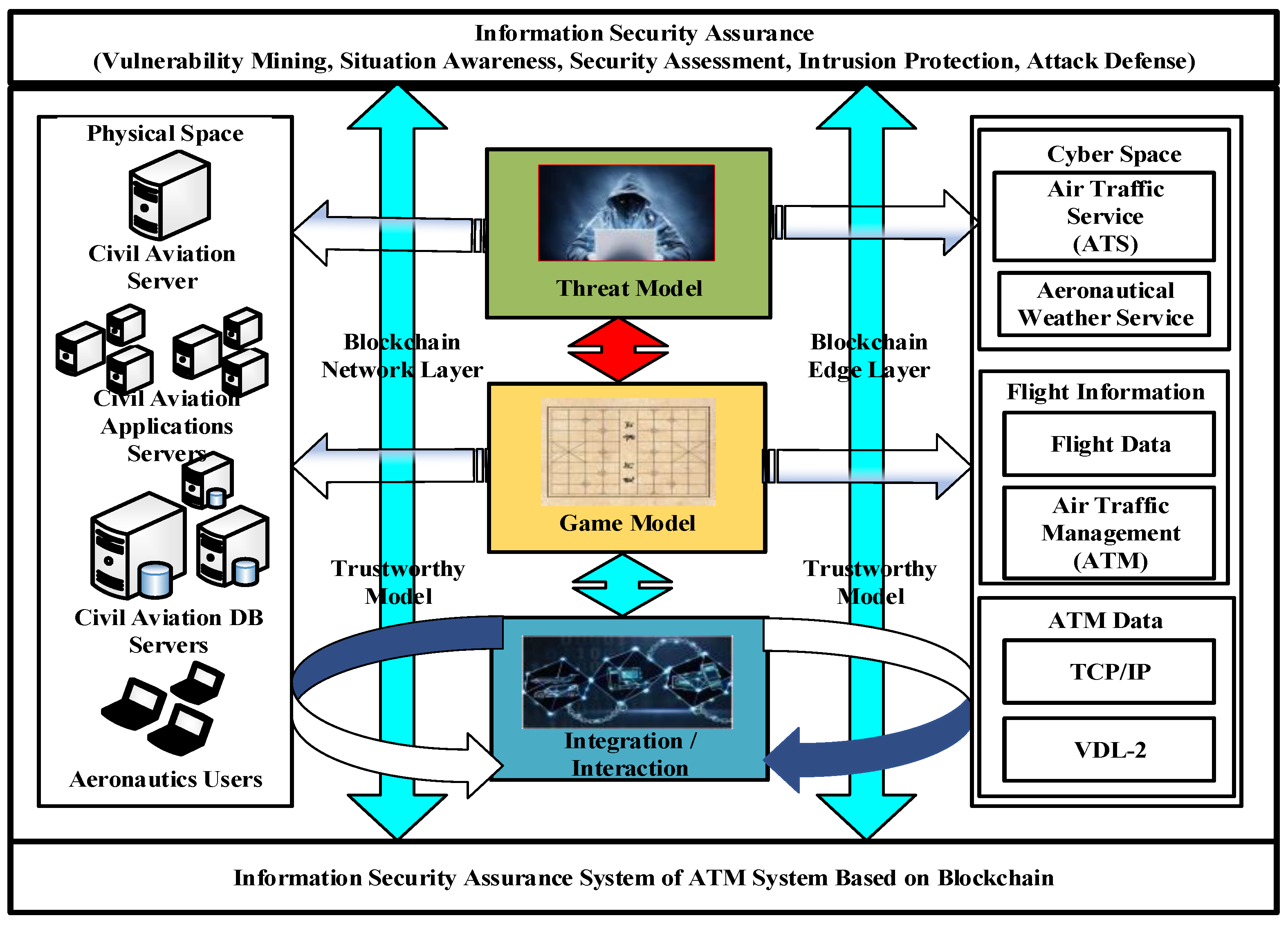
6.1. Construction of Networked ATM Information Security Assurance
- (a)
- The blockchain-based trust model of networked ATM.
- Digital signature technology and edge protection network are used to design a trust access verification mechanism to enable real-time monitoring of the networked ATM system and promote resource sharing and collaboration among various subsystem entities in the ATM system.
- An anonymous evaluation model based on Bayesian network is proposed to solve the anonymity problem in the ATM blockchain and ensure the authenticity of ATM management institutions and departments, airlines, airports, and other ATM users.
- Based on zero knowledge verification technology, using the account model of ATM system service providers and users and the multi resource model of ATM system, this paper proposes a privacy protection scheme for ATM system service providers and users based on blockchain, as well as a protection scheme for shared data security and sensitive information of ATM system.
- (b)
- The information security assurance architecture of networked ATM system based on trusted model is designed.
- Research the blockchain platform of networked ATM system and design the smart contract required for its operation. Among them, the blockchain helps the cooperation between business service providers and users in the ATM system, manages crowd sensing tasks on the basis of smart contracts, and uses distributed algorithms based on smart contracts to achieve trusted services between ATM business service providers and users.
- Research the information security assurance architecture of networked ATM system on the basis of blockchain technology. This includes such key technologies as high fidelity and fast reproduction of ATM business process, replication of ATM user behavior, automatic configuration and fast release of ATM resources, system security isolation and trusted interaction, engine construction for ATM business tasks, and playback of real communication and transmission data flow for each subsystem of ATM system.
6.2. The Method of ATM-CPS Information Security Assurance Based on Blockchain Trusted Model
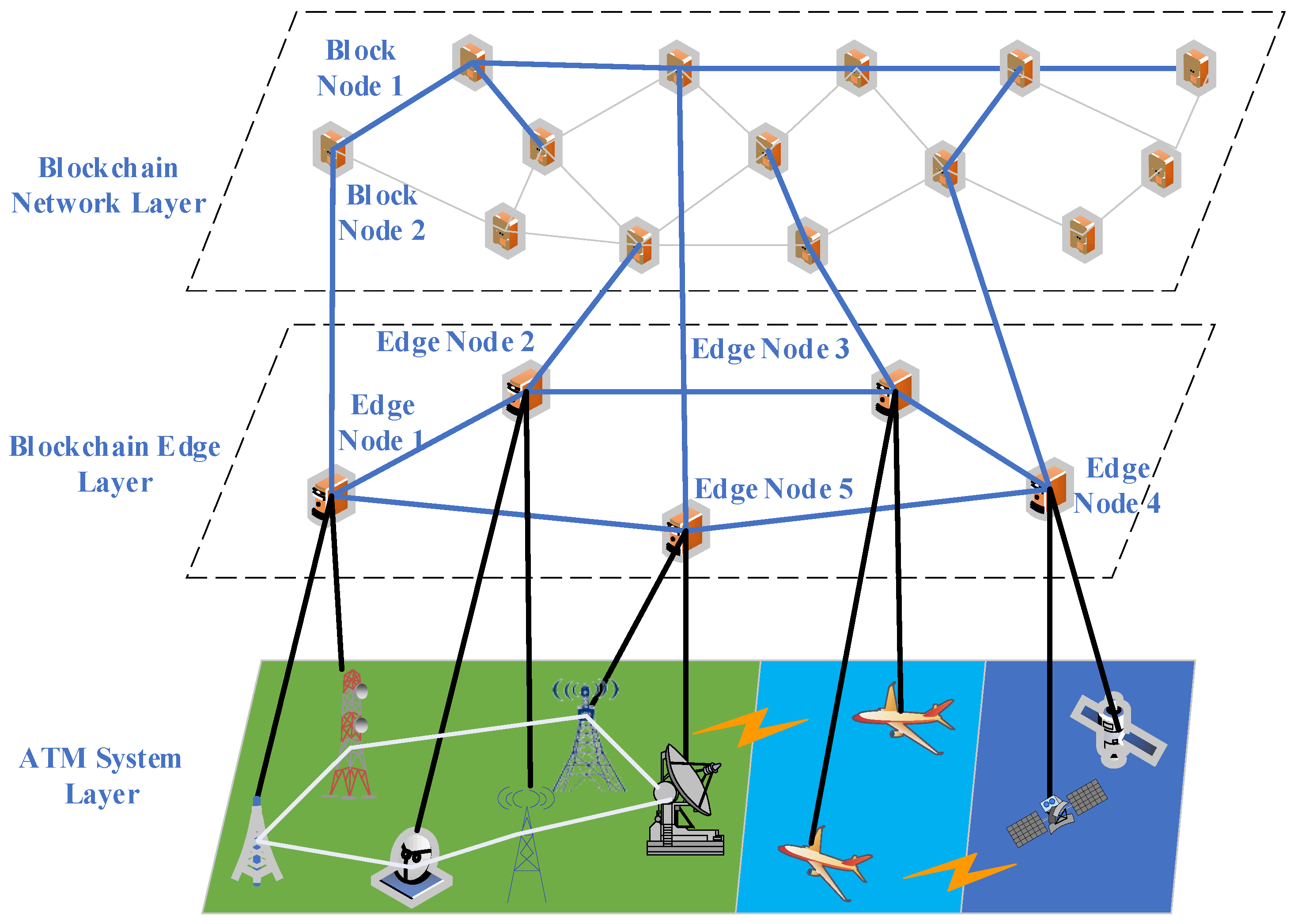
- (a)
- Blockchain network layer.
| Algorithm 1: Ring signature is performed on message M. |
| start Calculate // in group GT Generate Calculate Calculate Calculate Calculate // Calculate ; // the ring signature of message M. end |
| Algorithm 2: Verification. |
| start Calculate Calculate // Calculate Calculate Calculate if Verification failed else // for each KGC Sends to node A through a secure channel Calculates // as the signature private key. end |
- (b)
- Blockchain edge layer.
- (c)
- ATM system layer.
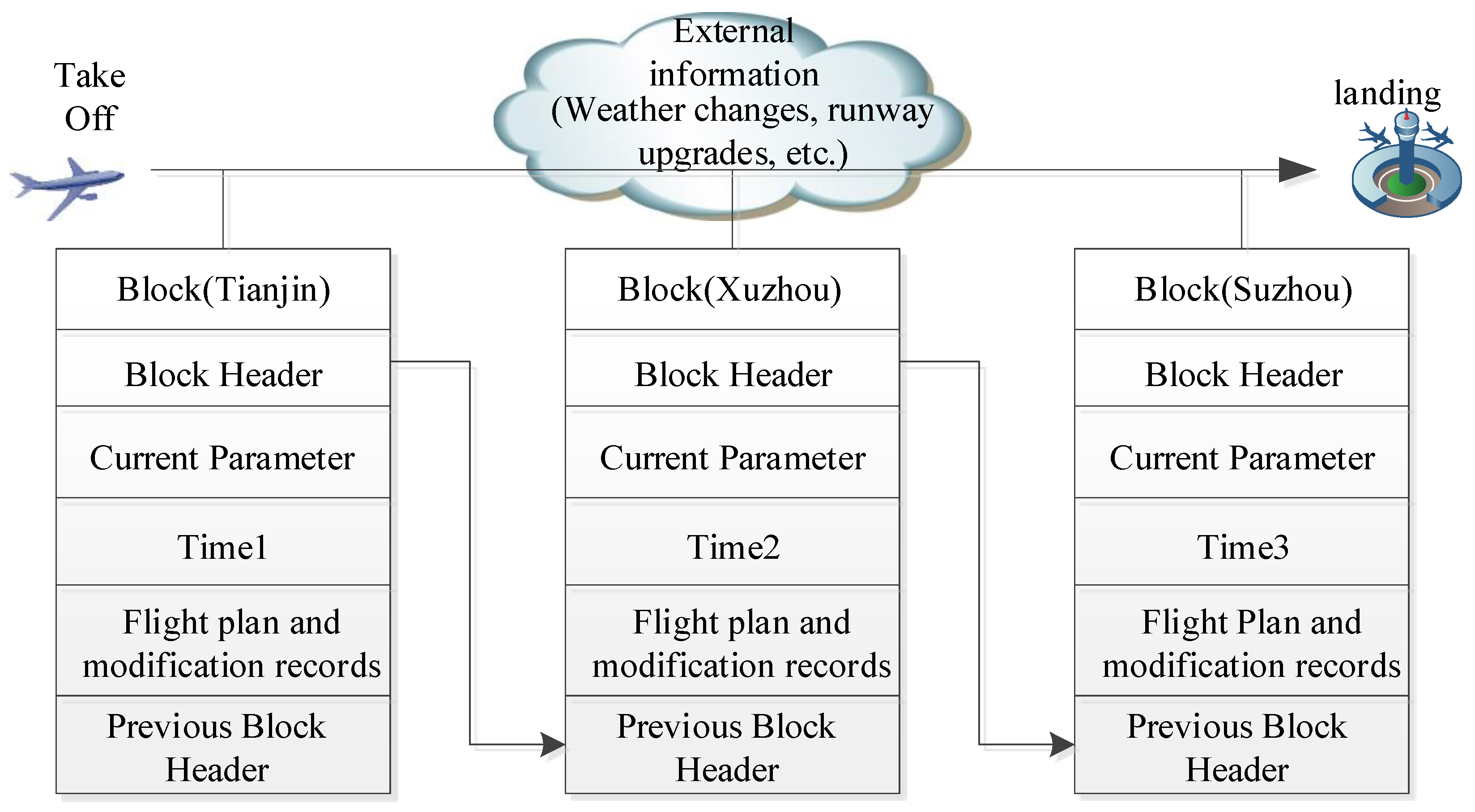
- (d)
- The example scenario.
- (e)
- The storage structure.
7. Scientific Issues and Deployment Implementation Routes
7.1. The Scientific Issues
- (a)
- Scientific Issue 1: Complex game relationship of networked ATM-CPS.
- Master the security threats and degrees faced by the networked ATM, and build a unified and effective threat model;
- Analyze the requirements of information security assurance of ATM system, design the technology of information security assurance of ATM system, and build a systematic information security assurance architecture of ATM system.
- (b)
- Scientific Issue 2: Networked ATM-CPS information security situation awareness.
- Security situation prediction. The change of security situation of networked ATM system is a complex nonlinear process. An intelligent prediction model based on neural network is established by using deep learning method. Nonlinear time series prediction is conducted for time-based sequence actions in ATM operation. The depth neural network model is used to calculate the nonlinear time series data, and the security situation of the networked ATM system is obtained through approximation and fitting;
- Security assessment. According to the requirements of the National Security Classification Protection Guide, an approach based on security baseline strategy is adopted to conduct a multi-dimensional security assessment of the networked ATM system from three dimensions: static (functional design and technical measures), dynamic (operation status and development trend), and status (security status and security attributes).
- (c)
- Scientific Issue 3: Systematic ATM-CPS information security assurance mechanism.
- Analyzing the characteristics of the ATM system and the demand for information security assurance, formulating the information security assurance strategy of the ATM system, launching the ATM-CPS information security assurance plan, and building a systematic information security assurance architecture of the ATM system;
- Specifying the requirements, guidelines, and specifications for ATM-CPS information security assurance and designing specific core algorithms, special methods, and key technologies for information security assurance.
7.2. The Key Technologies
- (a)
- Information security modeling technology of networked ATM-CPS based on game theory.
- Model the dynamic behavior of CPS under the normal operation and network attack of ATM system;
- Study the system parameters (detection rate, defense effect, physical interruption time, etc.) and attack parameters (attack intensity, attack duration, attack mode, etc.) that affect CPS security, accurately predict the performance of both players in the game, and reduce the impact on normal operation of ATM system in the game with attackers;
- Study the strategy selection of attackers and ATM system under different situations in the mutual game according to game theory and estimate the attack performance and detection probability according to the defensive and antagonistic parameters of ATM-CPS;
- Use the security evaluation algorithm to calculate the security indicators, such as mean-time-to-shutdown (MTTSD) and availability of ATM-CPS, and obtain an accurate evaluation of ATM-CPS security through the comprehensive evaluation of the indicator system;
- (b)
- Networked ATM information security situation awareness technology based on ATM-CPS game model.
- Situation assessment. In the networked ATM system, various resource subsystem devices—all of which are data sensors used for receiving (collecting) and sending (transmitting) ATM business data—are distributed in different locations in a wide area and are connected by different communication protocols and interfaces to form a typical sensor network. Aimed at the processing mode of distributed collection and acquisition of ATM business data by ATM system equipment, the structure framework of security situation awareness system of ATM system based on multi-sensor is studied (divided into three levels from bottom to top: information collection level, element extraction level, and situation decision-making level), and the network physical structure of ATM system and the hierarchical model of equipment layer, transmission layer, and application layer are designed. On the basis of the structural framework of the security situation awareness system of the ATM system, the eXML format solution for multi-source heterogeneous security information of the ATM system is proposed. It includes three steps: detection data fusion, establishment of threat propagation network (TPN), and evaluation of CPS game model. The CPS game model is used to comprehensively evaluate the security situation of each resource subsystem of the ATM system from the perspectives of attack and defense, and the development trend of the security situation of the entire networked ATM system is obtained through the quantitative evaluation method of network security situation, thus providing a reference for timely adjustment of the system security strategy.
- Situation prediction. The deep learning model is used to predict the security situation of networked ATM system. First, we sort out the network attack events suffered by the networked ATM, study the method of event embedding, express the security events as dense vectors using neural tensor network (NTN), and conduct security event training. Then, the deep convolutional neural network is used to model the impact of security incidents, and a dynamic prediction model of networked ATM system security situation is established on the basis of the deep convolutional neural network. Genetic algorithm is used to optimize the model and realize the nonlinear time series prediction of the security situation of networked ATM system.
- (c)
- Building trust mechanism technology of networked ATM based on blockchain.
- Adopt the characteristics of blockchain decentralization, asymmetric encryption, distributed storage, etc., and realize point-to-point communication in the ATM system through the distributed accounting method of the underlying public chain so as to ensure that all devices in the ATM system can securely exchange data in a trusted environment;
- Adopt smart contract technology to convert and write the registered network access information of all component resource subsystem equipment in the ATM into the blockchain. The characteristics of blockchain technology ensure that the entire process of storage, reading, and execution of business data of ATM is transparent, traceable, and tamper-proof. It can solve the trust problems among the equipment of the ATM, airlines, airports, and ATM departments and between the ATM operators and the ATM;
- Establish a tamper-proof intelligent trust mechanism in the networked ATM system by using the blockchain network; this can resist the tampering of core data by internal personnel of the ATM, identify false data injection, and resist the deceptive attack facing satellite navigation information. On the basis of the blockchain, design the technology of building the trust mechanism of the networked ATM with the functions of certificate authorization, smart contract support, and aviation sensitive information protection, and realize the sharing and information security of ATM big data according to the terms specified in the form of a smart contract.
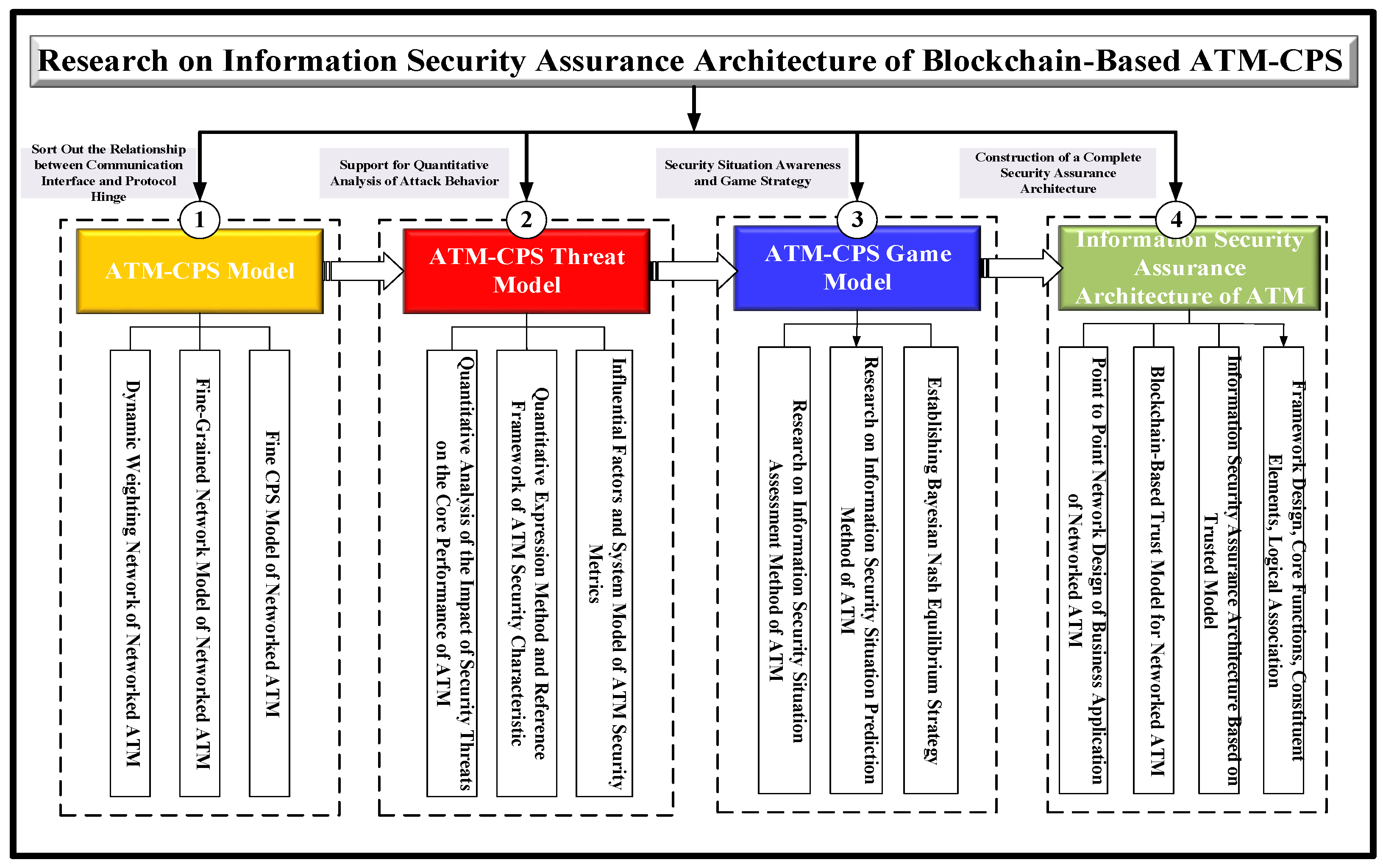
7.3. The Technical Route
- (a)
- ATM-CPS model.
- Determine the dynamic weighting network of the ATM system;
- Establish fine granularity network model of the ATM system;
- Establish the refined CPS model of the ATM system.
- (b)
- ATM-CPS threat model.
- Carry out quantitative analysis on the impact of security threats on the core performance of the ATM system;
- Design the quantitative expression method and reference frame of the ATM system security characteristics;
- Establish the influencing factors and system model of the ATM system security measurement.
- (c)
- ATM-CPS game model.
- Study the information security situation assessment method of the ATM system;
- Study the information security situation prediction method of the ATM system;
- Establish Bayesian Nash equilibrium strategy.
- (d)
- Information security assurance architecture of the networked ATM system.
- Study the point-to-point network design of the business application of the networked ATM system;
- Establish the blockchain-based trust model of networked ATM system;
- Design the information security assurance architecture on the basis of the trusted model;
- Complete the design of information security assurance framework of the networked ATM system, including core functions, constituent elements, and logical associations.
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ATM | Air Traffic Management |
| CPS | Cyber-Physical System |
| ATC | Air Traffic Control |
| CNS | Communication, Navigation, and Surveillance |
| ICAO | International Civil Aviation Organization |
| GNSS | Global Navigation Satellite System |
| ADS-B | Automatic Dependent Surveillance-Broadcast |
| SWIM | System-Wide Information Management |
| DDoS | Distributed Denial of Service |
| KGC | Key Generation Center |
References
- ICAO. Global Air Navigation Plan. ICAO Doc 9750, 6th ed.; ICAO: Montréal, QC, Canada, 2019. [Google Scholar]
- Sampigethaya, K.; Poovendran, R. Aviation Cyber–Physical Systems: Foundations for Future Aircraft and Air Transport. Proc. IEEE 2013, 101, 1834–1855. [Google Scholar] [CrossRef]
- ICAO. Security and Facilitation Strategic Objective: Aviation Cyber-Security Strategy; ICAO: Montréal, QC, Canada, 2019. [Google Scholar]
- Arthur, P. A Systems Approach to Protecting the U.S. Air Traffic Control System Against Cyber-Terrorism. Presentation PPT. 2012. Available online: https://www.federalregister.gov/documents/ (accessed on 2 December 2022).
- Homeland Security. National Strategy for Aviation Security of the United States of America; Homeland Security: Washington, DC, USA, December 2018. [Google Scholar]
- Mehan, D.J. Systems Security—The Federal Aviation Administration’s Layered Approach. TR News 2000, 211, 8–13. Available online: https://www.nstl.gov.cn/paper_detail.html?id=c4f0fcec6bb53e1a2cd5d1d3349d2638 (accessed on 2 December 2022).
- Aviation Cyber Security Strategy. Department for Transport and Civil Aviation Authority; Aviation Cyber Security Strategy: London, UK, 12 July 2018. [Google Scholar]
- Thompson, K.H.; Tran, H.T. Application of a Defender-Attacker-Defender Model to the U.S. Air Transportation Network. In Proceedings of the 2018 IEEE International Symposium on Technologies for Homeland Security (HST), Woburn, MA, USA, 23–24 October 2018; pp. 1–5. [Google Scholar]
- Hird, J.; Hawley, M.; Machin, C. Air Traffic Management Security Research in SESAR. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 486–492. [Google Scholar]
- Montefusco, P.; Casar, R.; Koelle, R.; Stelkens-Kobsch, T.H. Addressing Security in the ATM Environment: From Identification to Validation of Security Countermeasures with Introduction of New Security Capabilities in the ATM System Context. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 532–541. [Google Scholar] [CrossRef]
- United States Government Accountability Office. Information Security: FAA Needs to Address Weaknesses in Air Traffic Control Systems. Report to Congressional Requesters, GAO-15-221; United States Government Accountability Office: Washington, DC, USA, January 2015.
- The Boeing Company. Views on the Framework for Improving Critical Infrastructure Cybersecurity; National Institute of Standards and Technology: Gaithersburg, MD, USA, 9 February 2016. [Google Scholar]
- Holt, T.B.; Moallemi, M.; Weiland, L.; Earnhardt, M.; McMullen, S. Aircraft Cyber Security and Information Exchange Safety Analysis for Department of Commerce; Report; Embry-Riddle Aeronautical University: Washington, DC, USA, 2 June 2016. [Google Scholar]
- Elias, B. Protecting Civil Aviation from Cyberattacks; CRS Insights: Watford, UK, 18 June 2015. [Google Scholar]
- Stelkens-Kobsch, T.H. Security in ATM—A Validation Methodology for Security Prototype; Report; Deutscher Luftund Raumfahrtkongress (DLRK): Sacramento, CA, USA, 13–15 September 2016. [Google Scholar]
- Schaper, M.; Stelkens-Kobsch, T.H.; Carstengerdes, N. From preparation to evaluation of integrated ATM-security-prototype validations. In Proceedings of the 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC), St. Petersburg, FL, USA, 17–21 September 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Bogoda, L.; Mo, J.; Bil, C. A Systems Engineering Approach to Appraise Cybersecurity Risks Of CNS/ATM and Avionics Systems. In Proceedings of the 2019 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 9–11 April 2019; pp. 1–15. [Google Scholar] [CrossRef]
- Sampigethaya, K.; Poovendran, R. Cyber-physical Integration in Future Aviation Information Systems. In Proceedings of the 2012 IEEE/AIAA 31st Digital Avionics Systems Conference (DASC), Williamsburg, VA, USA, 14–18 October 2012. [Google Scholar]
- Sampigethaya, K.; Poovendran, R.; Shetty, S.; Davis, T.; Royalty, C. Future E-Enabled Aircraft Communications and Security: The Next 20 Years and Beyond. Proc. IEEE 2011, 99, 2040–2055. [Google Scholar] [CrossRef]
- Kumar, S.A.; Xu, B. Vulnerability Assessment for Security in Aviation Cyber-Physical Systems. In Proceedings of the 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud), New York, NY, USA, 26–28 June 2017; pp. 145–150. [Google Scholar]
- Koutsoukos, X.; Karsai, G.; Laszka, A.; Neema, H.; Potteiger, B.; Volgyesi, P.; Vorobeychik, Y.; Sztipanovits, J. SURE: A Modeling and Simulation Integration Platform for Evaluation of Secure and Resilient Cyber–Physical Systems. Proc. IEEE 2017, 106, 93–112. [Google Scholar] [CrossRef]
- Lan, M. The Information Assurance of Air Traffic Management System Based on SSE Theory. Ph.D. Thesis, Tianjin University, Tianjin, China, 2011. (In Chinese). [Google Scholar]
- Lan, M.; Zhijun, W. Air Traffic Management Information Security Assessment; Science Press: Beijing, China, 2015. (In Chinese) [Google Scholar]
- Schmidt, D.; Radke, K.; Camtepe, S.; Foo, E.; Ren, M. A Survey and Analysis of the GNSS Spoofing Threat and Counter-measures. ACM Comput. Surv. 2016, 48, 1–31. [Google Scholar] [CrossRef]
- Bian, S.; Ji, B.; Hu, Y. Research status and prospect of GNSS anti-spoofing technology. Sci. Sin. Inf. 2017, 47, 275–287. [Google Scholar] [CrossRef]
- Peng, Z.; Xu, J.; Hu, H.; Chen, L.; Kong, H. BlockShare: A Blockchain Empowered System for Privacy-Preserving Veri-fiable Data Sharing. IEEE Data Eng. Bull. 2022, 45, 14–24. [Google Scholar]
- Kaur, K.; Kaddoum, G.; Zeadally, S. Blockchain-Based Cyber-Physical Security for Electrical Vehicle Aided Smart Grid Ecosystem. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5178–5189. [Google Scholar] [CrossRef]
- Wang, W.; Xu, H.; Alazab, M.; Gadekallu, T.R.; Han, Z.; Su, C. Blockchain-Based Reliable and Efficient Certificateless Sig-nature for IIoT Devices. IEEE Trans. Ind. Inform. 2022, 18, 7059–7067. [Google Scholar] [CrossRef]
- Wang, H.; Xu, C.; Zhang, C.; Xu, J.; Peng, Z.; Pei, J. vChain+: Optimizing Verifiable Blockchain Boolean Range Queries. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 1927–1940. [Google Scholar]
- Wu, H.; Peng, Z.; Guo, S.; Yang, Y.; Xiao, B. VQL: Efficient and Verifiable Cloud Query Services for Blockchain Systems. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 1393–1406. [Google Scholar] [CrossRef]
- Ali, K.M.; Alexandre, S.; Nidhal, R. A Flight Plan Rescheduling in Air Traffic Management Problem: A Time Discret Event System Approach. IFAC Proc. Vol. 2012, 45, 285–290. [Google Scholar] [CrossRef]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, X.; Dong, R.; Wang, Q.; Zhang, L. Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management. Electronics 2023, 12, 1665. https://doi.org/10.3390/electronics12071665
Lu X, Dong R, Wang Q, Zhang L. Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management. Electronics. 2023; 12(7):1665. https://doi.org/10.3390/electronics12071665
Chicago/Turabian StyleLu, Xin, Ruochen Dong, Qing Wang, and Lizhe Zhang. 2023. "Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management" Electronics 12, no. 7: 1665. https://doi.org/10.3390/electronics12071665
APA StyleLu, X., Dong, R., Wang, Q., & Zhang, L. (2023). Information Security Architecture Design for Cyber-Physical Integration System of Air Traffic Management. Electronics, 12(7), 1665. https://doi.org/10.3390/electronics12071665





