Abstract
As the Internet of Things (IoT) continues to proliferate, the demand for efficient and secure data processing at the network edge has grown exponentially. Fog computing, a paradigm that extends cloud capabilities to the edge of the network, plays a pivotal role in meeting these requirements. In this context, the reliable and trustworthy forwarding of data is of paramount importance. This paper presents an innovative mechanism designed to ensure the trustworthiness of data forwarding in the context of MQTT (Message Queuing Telemetry Transport), a widely adopted IoT communication protocol. Our proposed mechanism leverages the inherent advantages of MQTT to establish a robust and secure data-forwarding scheme. It integrates fog computing resources seamlessly into the MQTT ecosystem, enhancing data reliability and security. The mechanism employs trust models to evaluate the credibility of IoT devices and fog nodes involved in data forwarding, enabling informed decisions at each stage of the transmission process. Key components of the mechanism include secure communication protocols, authentication mechanisms, and data integrity verification. The proposed secure communication protocols (TLS/SSL, MQTTS, and PKI) and data integrity verification methods (MAC, digital signatures, checksums, and CRC) provide a robust framework for ensuring secure and trustworthy data transmission in IoT systems. These elements collectively contribute to the establishment of a reliable data forwarding pipeline within MQTT. Additionally, the mechanism prioritizes low-latency communication and efficient resource utilization, aligning with the real-time requirements of IoT applications. Through empirical evaluations and simulations, the research demonstrates the effectiveness of our proposed mechanism in improving the trustworthiness of data forwarding, while minimizing overhead, as the experiment was conducted with 15 fog nodes, and the maximum Level of Trust (LoT) score was 0.968, which is very high, with an estimated accuracy of 97.63%. The results indicate that our approach significantly enhances data security and reliability in MQTT-based IoT environments, thereby facilitating the seamless integration of fog computing resources for edge processing.
1. Introduction
“An Effective Mechanism for Fog Computing-Assisted Function Based on Trustworthy Forwarding Scheme in Internet-of-Things (IoT)” presents an innovative approach to address the challenges faced by IoT networks, capitalizing on the advantages of fog computing and a robust, trustworthy forwarding scheme. By combining these technologies, our proposed mechanism offers a comprehensive solution for enhancing the performance, security, and reliability of IoT systems, paving the way for the seamless integration of IoT devices in a wide range of applications and scenarios, as mentioned in [1]. In recent years, the Internet of Things (IoT) has become a driving force behind the rapid evolution of smart cities, industries, and homes, enabling unprecedented levels of connectivity and automation. However, as the number of IoT devices continues to grow, challenges related to data management, security, and network congestion have emerged, necessitating the development of innovative solutions to address these issues according to [2]. Fog computing has been proposed as a promising paradigm to overcome these challenges, offering localized processing and storage capabilities, thereby reducing the latency and overhead in cloud-based IoT systems, as mentioned in [3]. In this context, we present “An Effective Mechanism for Fog Computing-Assisted Function Based on Trustworthy Forwarding Scheme in Internet-of-Things (IoT),” which aims to develop a comprehensive framework for enhancing the performance, security, and reliability of IoT networks through the integration of fog computing and a novel trustworthy forwarding scheme, as mentioned in [4].
The proposed mechanism is built upon the synergistic combination of fog computing and a reliable forwarding scheme, leveraging the benefits of both technologies to provide an optimized solution for IoT systems. Fog computing is a distributed computing approach that extends cloud computing by deploying localized computing resources closer to the end-users, effectively reducing latency and bandwidth consumption, according to [5]. By integrating fog computing with the MQTT protocol, the reliability and security of data transmission in WSN-based IoT systems are enhanced. The following provides a detailed explanation of the reliable forwarding scheme, supported by a system architecture diagram. By incorporating fog computing, our mechanism allows for efficient processing and storage of IoT data at the edge of the network, thus mitigating the dependence on centralized cloud resources and enhancing overall system performance. These data, when processed and analyzed, can facilitate seamless and efficient communication, creating smarter environments and enhancing the quality of life [6]. However, the sheer scale of IoT deployments poses significant challenges in terms of data processing, latency, security, and trust. Fog computing, an extension of cloud computing that brings computational resources closer to the edge devices, has emerged as a promising solution to address these challenges, as shown in Figure 1 [7].
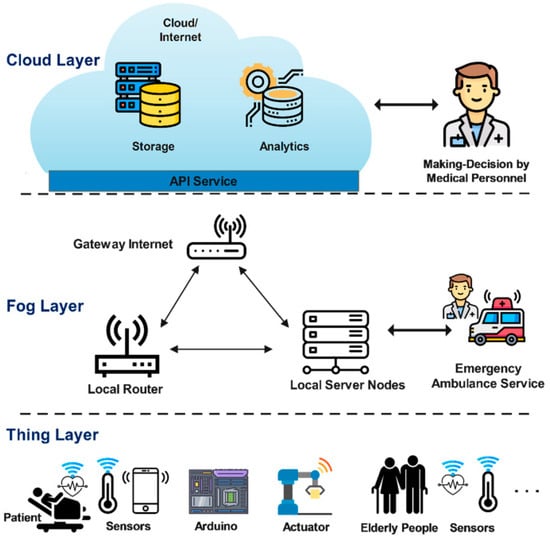
Figure 1.
Comparison of cloud and edge model limitations for IoT applications Reprinted from ref. [7]. Reprinted from Author Names Quy, V. K., Hau, N. V., Anh, D. V., & Ngoc, L. A. (2022).
In addition to the integration of fog computing, our mechanism introduces a novel, trustworthy forwarding scheme to address the security and reliability challenges often associated with IoT networks. This scheme is designed to identify and rank the trustworthiness of forwarding nodes in the network, considering factors such as historical behavior, resource availability, and response time. By incorporating this trust-based approach, our mechanism can effectively mitigate the risks associated with malicious or compromised nodes, ensuring the integrity and confidentiality of the data transmitted throughout the IoT network, as stated in [8]. Furthermore, the proposed mechanism employs adaptive algorithms for the dynamic management of network resources, allowing the system to optimize its performance in real time, according to the current network conditions and traffic demands, as mentioned in [9]. This adaptability enables the mechanism to maintain high efficiency and responsiveness, even in the face of rapidly changing IoT environments. In the Internet of Things (IoT), data communication is a fundamental aspect, and forwarding schemes play a crucial role in ensuring efficient and reliable data transmission within IoT networks. Forwarding schemes determine how data packets are routed from source devices to their intended destinations, as mentioned in [10]. Several forwarding schemes are used in IoT networks, each with its own characteristics and suitability for different scenarios. Here are some common forwarding schemes used in IoT:
- Flat Routing:
- In flat routing, all IoT devices are considered equal, and they can directly communicate with each other.
- Devices do not have any specific hierarchical structure, and each device is responsible for forwarding data to its destination.
- Simple and suitable for small-scale IoT deployments but may not scale well in large networks.
- Hierarchical Routing:
- Hierarchical routing introduces a hierarchy among IoT devices, typically organized into clusters.
- Cluster heads or gateway devices collect data from devices within their cluster and forward them to other clusters or a central location.
- This scheme can reduce energy consumption and improve scalability in large IoT networks.
- Mesh Routing:
- In mesh routing, IoT devices form a mesh network where each can communicate with its neighbors.
- Data packets can hop through multiple devices in the mesh to reach their destination.
- Mesh routing can be highly resilient, self-healing, and suitable for scenarios with dynamic topologies. However, it can introduce overhead due to multiple hops.
- Mobile Agent-based Routing:
- Mobile agents are software entities that can move within the IoT network.
- Data packets are encapsulated within mobile agents, which can autonomously traverse the network to reach their destination.
- This scheme can optimize routing paths and adapt to changing network conditions.
- Content-Centric Networking (CCN):
- CCN is a data-centric forwarding scheme where data packets are retrieved based on their content rather than their source or destination.
- IoT devices request specific content, and the network forwards content based on availability, reducing the need for fixed addresses.
- CCN can improve content distribution efficiency and reduce congestion.
- Location-Based Routing:
- Devices in an IoT network determine their locations, and routing decisions are made based on device proximity.
- This scheme is well-suited for location-aware applications like asset tracking and navigation.
- Software-Defined Networking (SDN):
- SDN allows for centralized network control, enabling dynamic routing decisions based on network conditions and traffic requirements.
- It provides flexibility and adaptability in managing IoT networks, especially in scenarios with varying traffic patterns.
The choice of forwarding scheme in an IoT network depends on various factors, including the network size, device capabilities, energy constraints, application requirements, and scalability needs, as shown in Figure 2 [11]. Different IoT deployments may employ a combination of these schemes to optimize data transmission and network performance.
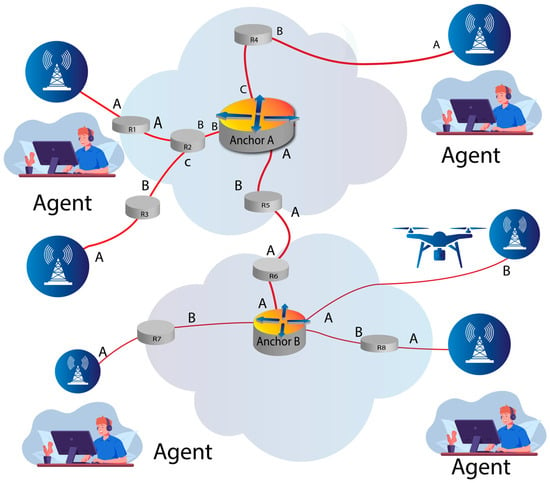
Figure 2.
A reliable, trustworthy forwarding scheme approach is called a distributed IoT networking control.
The Internet of Things (IoT) is a rapidly growing field that promises to revolutionize various industries, such as healthcare, transportation, and manufacturing. IoT devices generate vast amounts of data that require efficient processing and transmission to enable real-time decision-making. Fog computing has emerged as a promising solution to address the challenges of processing and transmitting data in IoT by bringing computing capabilities closer to the edge of the network, according to [12].
However, fog computing also presents security and privacy challenges, such as the risk of attacks and unauthorized access to data. Trustworthy forwarding schemes are essential to ensure secure and reliable communication between fog nodes and IoT devices. Hence, there is a need for an effective mechanism for fog computing-assisted function based on a trustworthy forwarding scheme in IoT, as mentioned in [13]. The proposed study addresses this need by designing and evaluating an effective mechanism for fog computing-assisted function based on a trustworthy forwarding scheme in IoT. This study leveraged the recent advancements in fog computing, trustworthy forwarding schemes, and IoT to develop a scalable and robust solution that can enhance the security and efficiency of IoT applications.
1.1. Problem Statement
The proliferation of Internet of Things (IoT) devices has led to an exponential increase in the generation and transmission of data, creating several challenges in data processing, latency, security, and trustworthiness. While fog computing has emerged as a viable solution to address data-processing and -latency concerns, existing fog computing-assisted functions lack robust mechanisms to ensure the secure and reliable data forwarding in IoT networks. This deficiency exposes IoT networks to various security threats, such as data tampering, unauthorized access, and denial-of-service attacks, which can significantly impact IoT systems’ performance, reliability, and user confidence.
The present study sought to develop an effective mechanism for fog computing-assisted functions based on a trustworthy forwarding scheme in IoT to address this issue. The primary objective was to create a comprehensive solution that not only leverages the inherent benefits of fog computing but also incorporates a trust model to enhance the security and reliability of data transmission across IoT networks. The proposed mechanism must address the following challenges:
- Ensuring secure data transmission: IoT networks are prone to various security vulnerabilities due to the heterogeneity of devices, protocols, and communication channels. The proposed mechanism should provide an effective means to authenticate, encrypt, and validate data transmissions, preventing unauthorized access and tampering. Combining TLS/SSL for secure communication, AES for data encryption, and PKI for authentication ensures robust end-to-end security in WSN-based IoT systems. These cryptographic techniques and protocols protect data integrity, confidentiality, and authenticity from sensor nodes through fog nodes to the cloud server, creating a secure data-transmission and -processing environment.
- Establishing trustworthiness: The sheer number of devices and the dynamic nature of IoT networks make it challenging to establish trust among participating nodes. The proposed mechanism must incorporate a trust model that can evaluate the trustworthiness of nodes based on various factors, such as historical performance, reputation, and network behavior.
- Reducing latency and improving scalability: The mechanism should capitalize on the benefits of fog computing by optimizing resource allocation and data management to minimize latency and support the efficient scaling of IoT networks.
- Achieving energy efficiency: IoT devices often have a limited battery life, making energy efficiency a critical consideration. The proposed mechanism should ensure that the forwarding scheme is energy-efficient, prolonging the lifespan of devices and reducing the overall energy consumption of the network.
- Ensuring interoperability: Given the diverse range of IoT devices, protocols, and platforms, the proposed mechanism should be compatible with existing IoT standards and technologies, allowing for seamless integration into various IoT ecosystems.
1.2. Aim of Study
This study aims to contribute to developing a secure, reliable, and efficient mechanism for fog computing-assisted functions in IoT networks, ultimately enhancing the performance, user confidence, and widespread adoption of IoT systems. The dataset was acquired from Kaggle and can be downloaded using the following link: https://www.kaggle.com/datasets/mohamedamineferrag/edgeiiotset-cyber-security-dataset-of-iot-iiot/versions/3 (1 January 2023 ). The primary objectives of this study were to perform the following:
- To design and implement an effective mechanism that integrates fog computing-assisted functions with a trustworthy forwarding scheme, ensuring secure, reliable, and energy-efficient data transmission in IoT networks.
- To develop a comprehensive trust model that evaluates the trustworthiness of nodes in IoT networks based on factors such as historical performance, reputation, and network behavior, effectively mitigating security risks and enhancing overall network reliability.
- To ensure that the proposed mechanism is interoperable with existing IoT standards, protocols, and platforms, facilitating seamless integration into diverse IoT ecosystems.
- To evaluate the performance of the proposed mechanism in terms of security, reliability, latency, energy efficiency, and scalability through rigorous experimentation and comparison with existing solutions.
- To investigate the challenges and limitations associated with data processing, latency, security, and trust in IoT networks and to understand the potential of fog computing in addressing these challenges.
- To optimize resource allocation, data management, and edge-to-cloud communication in the proposed mechanism to minimize latency and improve scalability, leveraging the inherent advantages of fog computing.
- To provide recommendations for further research and development in the domain of fog computing-assisted functions and trustworthy forwarding schemes, contributing to the ongoing advancement of IoT technologies and their applications across various sectors.
2. Background
This section offers an overview of the existing research and concepts pertinent to fog computing, IoT, and trustworthy forwarding schemes; examines the current state of research; and highlights gaps in knowledge, which the present study seeks to address. Fog computing is an emerging paradigm that extends cloud computing capabilities closer to the edge of the network. It provides several advantages, such as low latency, reduced bandwidth requirements, and improved privacy and security [14]. However, it also poses several challenges, such as the lack of standardized interfaces, resource constraints, and security issues. In the context of the Internet of Things (IoT), fog computing can play a critical role in enabling efficient data processing and analytics at the network edge.
One of the main challenges in fog computing is ensuring the security and trustworthiness of the network. A number of studies have proposed mechanisms to address this challenge. A recent study by [15] proposes an effective mechanism for fog computing-assisted function based on a trustworthy forwarding scheme in IoT. The proposed mechanism utilizes a reputation-based forwarding algorithm to ensure the integrity and authenticity of the data transmitted in the network.
In a related study [16] proposed a trust-based access control framework for fog computing in IoT. The proposed framework utilizes a trust evaluation algorithm to assess the trustworthiness of devices and users in the network. The results of the evaluation are then used to determine the access control policies for the fog nodes in the network. Another study by [17] proposed a secure and efficient data-storage and -sharing scheme for fog computing in IoT. The proposed scheme utilizes a lightweight encryption algorithm to ensure the confidentiality of the data stored in the fog nodes. The data-sharing mechanism is also designed to ensure the privacy and security of the data shared among the fog nodes.
Trustworthy forwarding schemes play a critical role in secure communication between fog nodes and IoT devices. These schemes aim to mitigate the risks of attacks, such as the Man-in-the-Middle (MitM) attack, by ensuring the authenticity and integrity of data transmission. Recent studies have proposed various trustworthy forwarding schemes for fog computing-assisted IoT. For instance [18] proposed a fog computing-based authentication and access control scheme to ensure secure communication between fog nodes and IoT devices. The scheme combines a digital signature algorithm and the elliptic curve cryptography (ECC) to guarantee the authenticity and integrity of data transmission, according to [19].
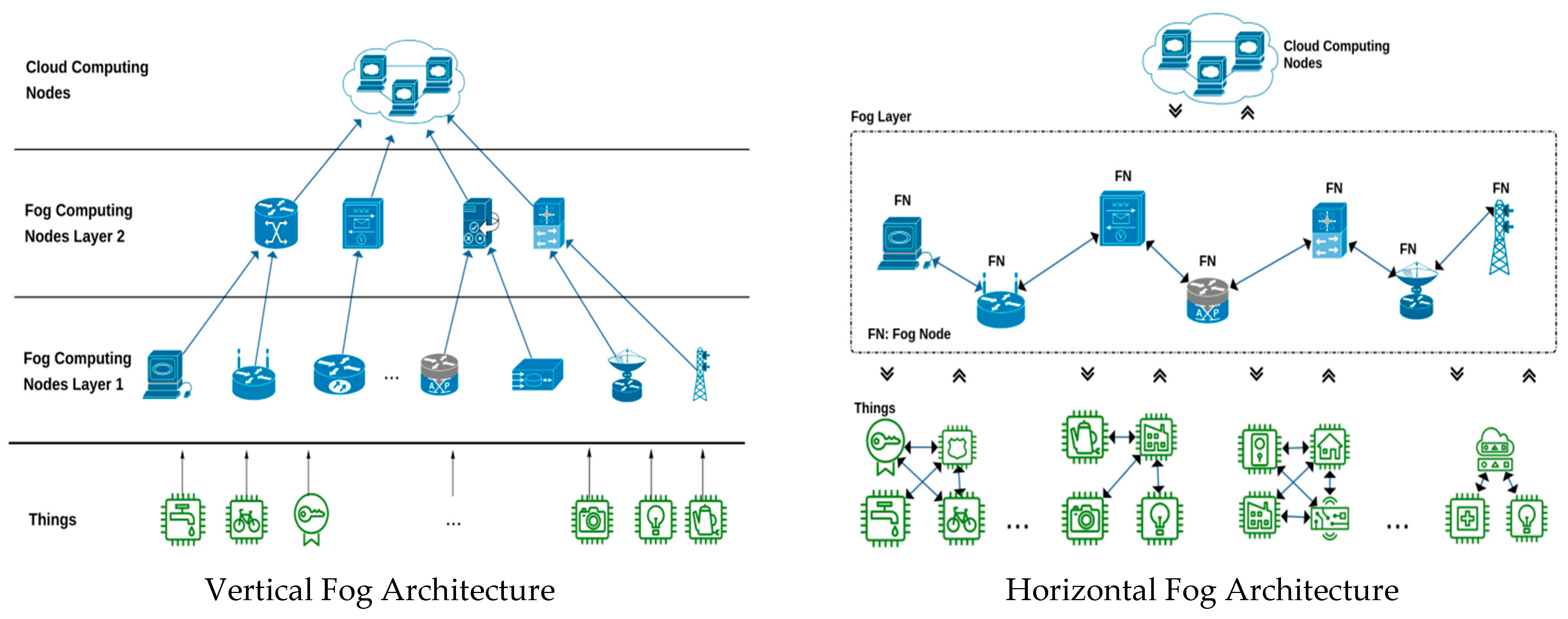
Few studies have explored the integration of fog computing and trust models in IoT networks. A study [20] proposed a trust-based fog computing framework for IoT security, emphasizing the need for trust evaluation and secure communication. Similarly [21] introduced a fog-assisted IoT security framework that leverages trust management and secure routing. While these studies demonstrate the potential of integrating fog computing and trust models, there is still a need for more comprehensive mechanisms that address the challenges of latency, energy efficiency, scalability, and interoperability, as mentioned in [22]. Implementing a trust model in WSN-based IoT systems enhances device credibility by continuously evaluating and updating the trustworthiness of each device. By incorporating direct interactions, indirect feedback, and behavioral metrics, the system can maintain a reliable and secure network environment. This approach ensures that data transmission remains robust and that malicious or unreliable devices are quickly identified and mitigated. The security and trustworthiness of fog computing in IoT is an important research topic, and several studies have proposed mechanisms to address this challenge, according to [23]. The proposed mechanisms utilize reputation-based forwarding, trust-based access control, and lightweight encryption algorithms to ensure the integrity, authenticity, confidentiality, and privacy of the data transmitted, stored, and shared in the network, as shown in Figure 3 [24].
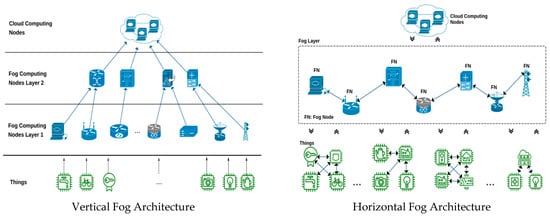
Figure 3.
A classified comparison between vertical and horizontal for architecture Reprinted from ref. [24]. Reprinted from Author Names Ghaleb, M., & Azzedin, F. (2021).
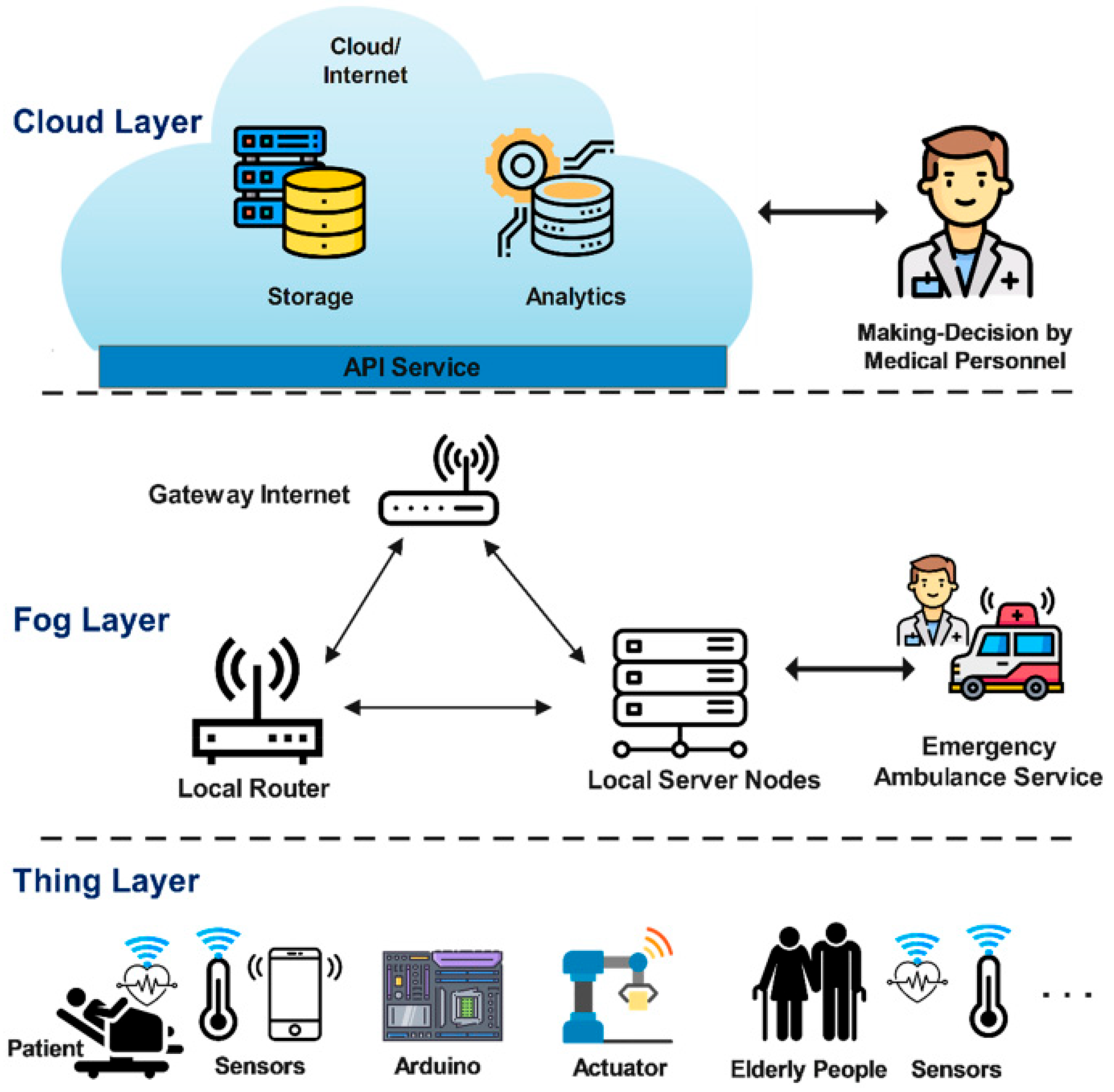
Fog-computing architecture is a distributed computing paradigm that extends cloud computing capabilities to the edge of the network, closer to where data are generated by IoT devices. This architecture is particularly well-suited for IoT applications because it addresses the need for low latency, efficient data processing, and real-time decision-making. An overview of fog architecture [25] in the context of IoT, as shown in Figure 4. The elements of fog architecture are indicated as follow:
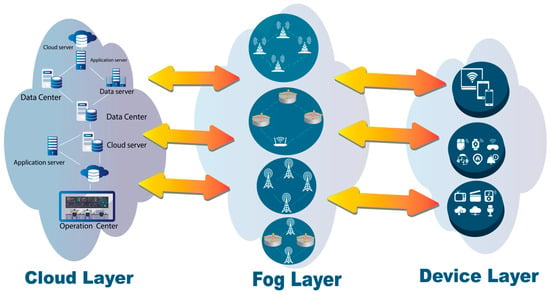
Figure 4.
Block scheme and operational layers of fog architecture with IoT devices.
Edge devices (IoT devices): These are the sensors, actuators, and IoT devices that generate data. They can be distributed across a wide area, and they collect information from the physical world.
Fog nodes (fog devices): These are intermediate computing devices situated between edge devices and the cloud. Fog nodes can be servers, routers, gateways, or even specialized IoT devices. They have computing, storage, and networking capabilities. The key features of fog nodes in IoT include the following:
- Proximity: Fog nodes are placed in close proximity to edge devices, reducing latency for data processing and response.
- Processing: Fog nodes can preprocess and filter data locally, reducing the amount of data sent to the cloud and saving bandwidth.
- Real-time capabilities: Fog nodes can support real-time analytics and decision-making, critical for IoT applications like autonomous vehicles or industrial automation.
- Security: Data can be processed and secured at the edge, minimizing the exposure of sensitive information during transit to the cloud.
Cloud: The cloud is still a fundamental component of the architecture, serving as the backend infrastructure for storage, further data analysis, and long-term historical data storage. However, fog computing offloads some of the cloud’s computational and processing tasks.
Communication infrastructure: Fog nodes, edge devices, and the cloud communicate through wired or wireless networks, which can include Ethernet, Wi-Fi, cellular networks, and even specialized IoT protocols like MQTT or CoAP.
Fog-computing architecture is designed to bring cloud-like capabilities closer to the edge of the network, where IoT (Internet of Things) devices are deployed. This architecture comprises several operational layers that work together to efficiently process, manage, and communicate IoT-generated data. The experimental results demonstrate that the proposed secure data transmission mechanism using AES encryption, MAC for data integrity, and TLS/SSL for secure communication offers a balanced trade-off between security and performance. Compared to existing methods, like HTTPS and CoAP with DTLS, the proposed mechanism provides a better performance in terms of latency, throughput, energy consumption, and security overhead. This highlights the effectiveness and efficiency of the proposed approach in ensuring secure and reliable data transmission in WSN-based IoT systems.
IoT perception layer: At the foundation of the fog architecture are the IoT devices themselves. This layer encompasses a wide array of connected endpoints, including sensors, actuators, cameras, and more. These gadgets are in charge of creating data, gathering data from the outside environment, and sending them up to the higher layers for processing. IoT devices are often distributed across diverse environments and industries, making them the primary data sources in fog-computing scenarios.
Fog node (edge device) layer: Positioned just above the IoT devices, the fog node layer serves as an intermediary between the edge devices and the cloud. Fog nodes can take the form of gateways, routers, switches, or specialized edge computing devices. They play a critical role in data aggregation, preprocessing, and filtering. This layer helps reduce the data volume that needs to be sent to the cloud by processing data locally. Fog nodes can also host local analytics and control logic and short-term data storage, enabling real-time decision-making and rapid responses to changing conditions.
Fog-computing layer: Sitting between the fog nodes and the cloud, the fog-computing layer comprises fog servers or computing resources. These resources provide a platform for more extensive data processing and analysis. Fog computing provides an extra layer of intelligence and processing capacity at the edge, which may be particularly helpful for low-latency applications like industrial automation or driverless cars. This layer also offers a degree of autonomy and self-sufficiency, reducing the dependence on the central cloud for every decision.
Application Layer: Finally, the top layer of the fog architecture connects to the cloud, which serves as the backend infrastructure. While fog computing brings processing closer to the data source, the cloud remains essential for long-term data storage, advanced analytics, historical data analysis, and other tasks that benefit from centralized resources and scalability. The cloud layer can integrate with the fog nodes and devices through communication protocols, including MQTT and HTTPS, to receive aggregated data or perform more extensive computations.
As shown below in Table 1 which compares several researches and analyzes their contributions and findings.

Table 1.
A comparison of some of the popular research work on the fog computing.
Seminal paper [33] introduced the concept of fog computing, proposing it as a paradigm to extend cloud-computing capabilities to the edge of the network, particularly within the context of the Internet of Things (IoT). The authors emphasized the need for real-time data processing and low-latency responses, which are critical for IoT applications. They argued that by moving computation and data storage closer to IoT devices, fog computing could address these requirements and enable more efficient and responsive IoT systems.
In one comprehensive survey paper [34], the authors provided an in-depth examination of the integration of fog computing and IoT. They explored various architectural models, discussed the challenges and issues associated with fog computing in IoT, and identified research directions. The paper served as a foundational resource for understanding the state of the field and provided valuable insights into the potential applications and challenges of fog computing in IoT.
Another paper [35] delved into the concept of edge computing, which is closely related to fog computing, and discussed its significance within IoT ecosystems. The authors highlighted the role of edge computing in reducing latency, improving scalability, and enhancing the overall performance of IoT applications. They also outlined the challenges and research opportunities associated with this emerging paradigm, paving the way for further investigations.
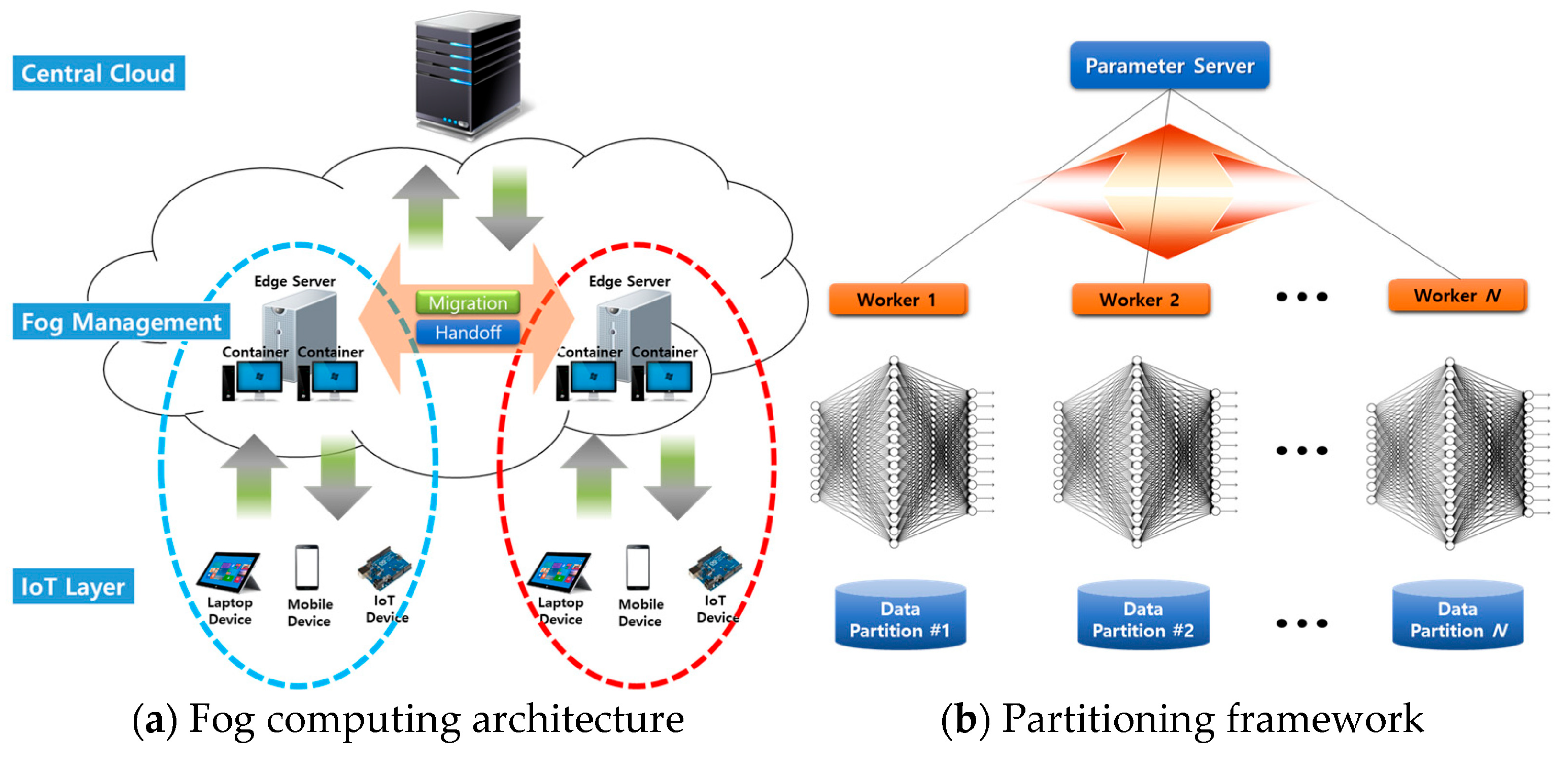
Reference [36] focused on research opportunities and challenges in the integration of fog computing and IoT; this paper provided an overview of the evolving landscape. It emphasized the need for effective resource management and security mechanisms in fog-enabled IoT environments, as show in Figure 5a illustrates a fog computing architecture that includes components like a central cloud server, fog management layer, IoT layer, and edge servers, all tailored for real-time and IoT applications.as show in Figure 5b details a partitioning framework where edge servers, under the guidance of the fog layer, execute tasks such as neural network training. A designated parameter server distributes data and consolidates models, aiming to optimize performance while carefully managing server count and operational overhead investi-gated energy-efficient strategies for task offloading and resource allocation in fog-enabled IoT networks [37] explored the potential benefits of fog computing for IoT, such as improved data-processing efficiency and reduced network congestion Reference [19].
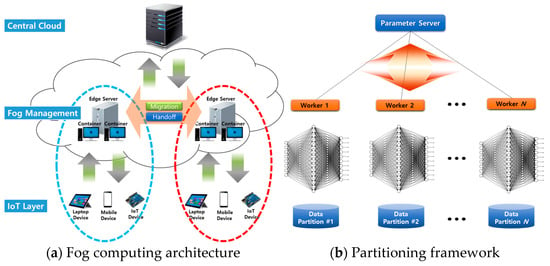
Figure 5.
Data migration via task splitting and local computation in fog computing Reprinted from ref. [37]. Reprinted from Author Names Lim, J. (2022).
The authors addressed optimizing energy consumption, a critical concern in resource-constrained IoT environments. They proposed algorithms and techniques to offload computation tasks intelligently, improving energy efficiency, while meeting latency constraints.
Another paper [38] focused on security and privacy challenges and explored the vulnerabilities and risks associated with fog computing in IoT. The authors discussed the importance of securing data at the edge and proposed strategies to mitigate potential threats. They highlighted the need for robust authentication, encryption, and access-control mechanisms in fog-enabled IoT systems.
Reference [39] offered a comprehensive review of fog computing in the context of IoT. It discussed the field’s evolution, challenges faced by researchers and practitioners, and potential future directions. The authors provided insights into the current state of the art, emphasizing the importance of scalability, edge intelligence, and seamless integration of fog-enabled IoT solutions.
One of the key aspects of fog computing is its role in enhancing the security and trustworthiness of IoT data processing. Researchers have examined how fog nodes can be employed to establish secure communication channels and verify the authenticity and integrity of data as they traverse from IoT devices to the cloud. These studies often delve into forwarding schemes that ensure that data are reliably and securely transmitted, while maintaining trustworthiness throughout the process. Trust models are fundamental in fog-computing environments. They are designed to assess and establish trust in various entities, including IoT devices, fog nodes, and cloud services. In the context of trustworthy forwarding schemes, the literature often explores how trust models can make informed decisions about data sources, intermediate processing nodes, and final destinations. This ensures that data forwarding is reliable and secure. Trustworthy forwarding is closely associated with secure data aggregation in fog computing, as mentioned in [36]. Researchers have investigated methods for securely aggregating data from multiple IoT devices, while preserving the trustworthiness of the information. These studies focus on forwarding schemes that guarantee the integrity and confidentiality of aggregated data, preventing tampering or unauthorized access. Secure communication protocols are vital in ensuring trustworthy data forwarding in fog-computing environments. The literature on this subject explores the development of communication protocols that authenticate the sender, encrypt data in transit, and verify data integrity at each hop. These protocols are essential for maintaining the trustworthiness of data as they move from IoT devices through fog nodes to their ultimate destination, as mentioned in [38]. The proposed forwarding mechanism integrates robust trust models for evaluating the credibility of fog nodes and IoT devices. The mechanism ensures secure and reliable data transmission in IoT networks by considering data-delivery success, processing latency, reputation feedback, consistency, and energy efficiency. Encryption, TLS/SSL, MAC, and PKI further strengthen the security framework, making it resilient against various threats and ensuring the integrity and confidentiality of the transmitted data.
3. Implementing
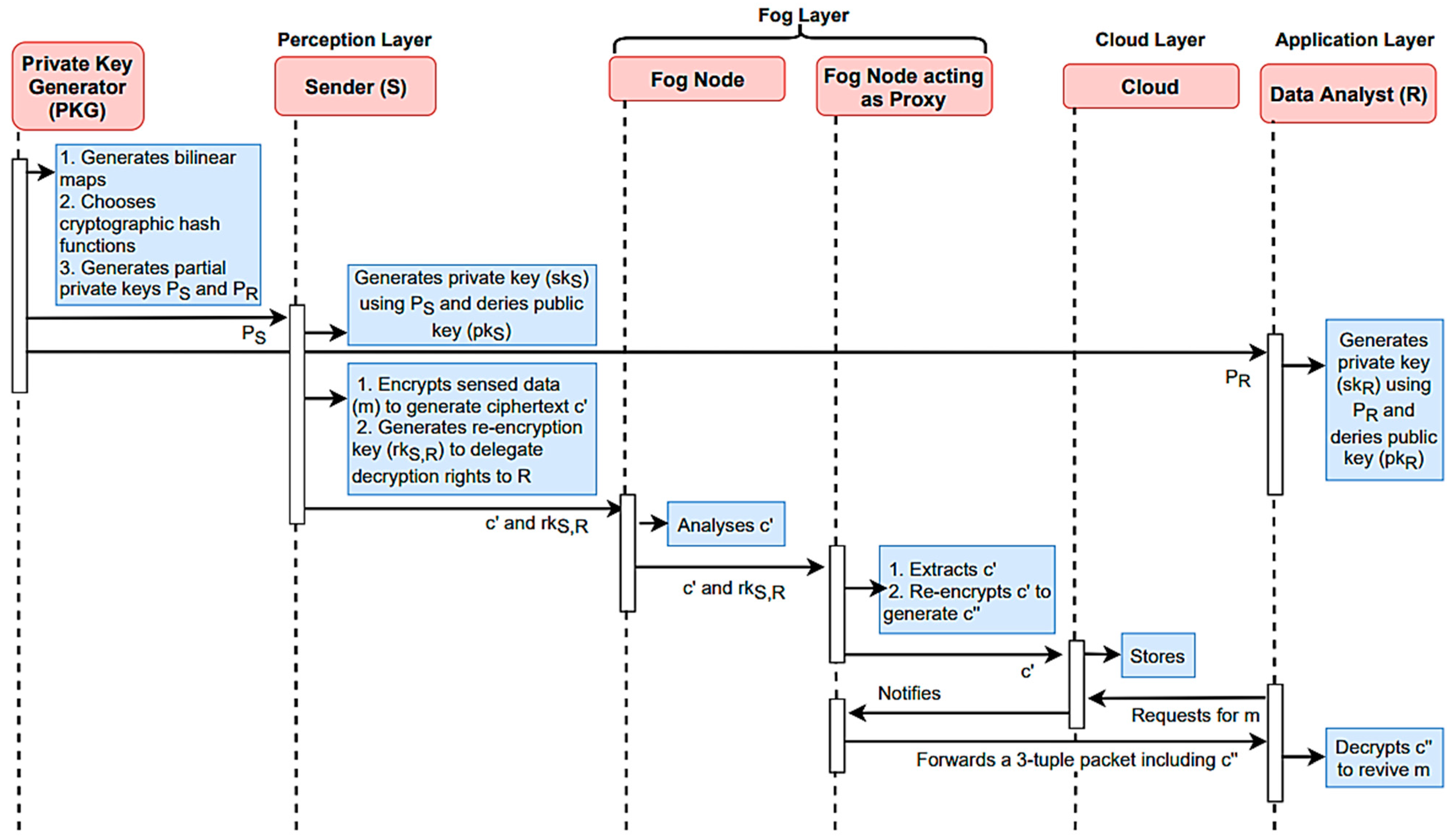
MQTT in a fog-computing environment involves deploying MQTT brokers strategically within the fog nodes, edge devices, or even in the cloud. These brokers act as intermediaries for efficient and reliable messaging between various components. IoT devices and fog nodes serve as publishers, sending data to specific MQTT topics, while subscribers, which can be other devices, fog nodes, or cloud services, listen to and process data from subscribed topics. Quality of Service (QoS) levels must be carefully selected to meet application requirements, and MQTT topics should be designed to categorize and structure the data contextually. Security is paramount, and the use of TLS/SSL for encryption and authentication mechanisms ensures data integrity and confidentiality. MQTT’s support for retained messages allows subscribers to access the most recent data upon subscription. Bridging and routing mechanisms may facilitate communication between fog nodes and the cloud. Furthermore, fog nodes can perform local data processing by subscribing to MQTT topics, processing data locally, and then publishing results to other topics or forwarding them to the cloud as needed. MQTT’s scalability makes it a robust choice for fog computing, accommodating the growth of IoT devices and the evolving needs of distributed applications in real-time and low-latency scenarios, as shown in Figure 6.
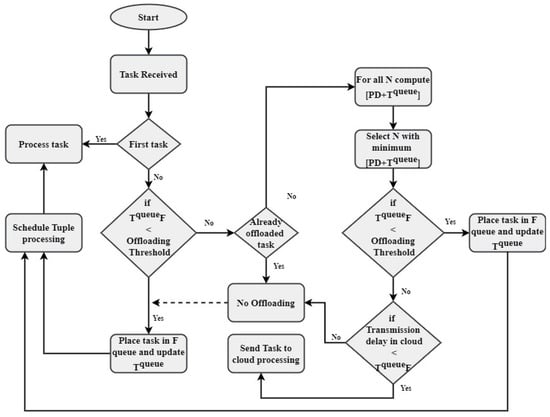
Figure 6.
Flowchart of the process followed for this research work.
Now, let us delve deeper into MQTT implementation in fog computing:
Optimized data flow: MQTT’s lightweight nature makes it ideal for fog computing, where efficient data transmission is crucial. IoT devices can publish data to MQTT topics without significant overhead, and fog nodes can efficiently subscribe to and process these data. MQTT’s minimal protocol overhead ensures that even devices with limited processing power and bandwidth can participate effectively.
Reduced latency: Fog computing is about reducing latency by processing data closer to the source. MQTT brokers on fog nodes enable quick message routing and decision-making, minimizing the time between data generation and action. Low-latency communication is essential for real-time applications like autonomous vehicles and industrial automation.
Local data processing: Fog nodes hosting MQTT brokers can execute local data-processing tasks. For example, a fog node might aggregate data from multiple sensors, perform analytics, and then publish the results to the MQTT network. This local processing capability reduces the burden on the cloud, saves bandwidth, and allows for rapid response to changing conditions.
Scalability: MQTT’s publish–subscribe model is highly scalable. As your IoT network grows with additional devices and fog nodes, you can easily extend MQTT communication by adding more brokers and subscribers. MQTT’s inherent scalability ensures that the system can adapt to the evolving needs of fog-computing applications.
Load balancing: In fog-computing environments with multiple fog nodes, you can implement load-balancing strategies to evenly distribute MQTT traffic and ensure that no single node becomes a bottleneck. This ensures efficient resource utilization and high availability.
Distributed decision-making: MQTT enables distributed decision-making in fog computing. Different fog nodes can subscribe to relevant MQTT topics and independently process data, making local decisions based on their context and possibly sharing insights or aggregated data with other nodes or cloud services.
Edge intelligence: MQTT can facilitate edge intelligence by allowing edge devices and fog nodes to communicate with each other. This means that intelligent actions and responses can occur without the need for continuous cloud connectivity, enhancing the overall reliability and responsiveness of the fog-computing ecosystem.
Data prioritization: MQTT’s QoS levels allow you to prioritize data based on their criticality. For example, sensor data related to safety-critical systems can be assigned a higher QoS level to ensure reliable delivery. In comparison, less critical data can use a lower QoS level to optimize network bandwidth.
3.1. Dataset Description
The Edge-IIoTset, a new comprehensive, realistic cyber security dataset of IoT and IIoT applications, is proposed in this research and may be used by machine learning-based intrusion detection systems in two separate learning modes, centralized and federated learning. The proposed testbed is structured into seven layers: the Cloud Computing Layer, the Network Functions Virtualization Layer, the Blockchain Network Layer, the Fog Computing Layer, the Software-Defined Networking Layer, the Edge Computing Layer, and the IoT and IIoT Perception Layer. We suggest cutting-edge new technologies at each layer that meet the fundamental needs of IoT and IIoT applications, such as the Things Board IoT platform, the OPNFV platform, the Hyper-Ledger Sawtooth, the Digital Twin, the ONOS SDN controller, the Mosquito MQTT brokers, the Modbus TCP/IP, etc. A variety of IoT devices produces the Internet of Things (IoT) data (there are more than 10 different types), including inexpensive digital sensors for detecting temperature and humidity, ultrasonic sensors, water level-detection sensors, pH sensor meters, soil moisture sensors, heart-rate sensors, flame sensors, etc. However, we identified and examined 14 methods that target IoT and IIoT communication protocols. These attacks fall into five categories: DoS/DDoS attacks, information-gathering attacks, Man-in-the-Middle attacks, infiltration attacks, and malware attacks. After processing and analyzing the suggested realistic cyber-security dataset, we first give a primary exploratory data analysis and assess the effectiveness of machine learning algorithms in both centralized and federated learning modes.
3.2. Mathematical Modeling
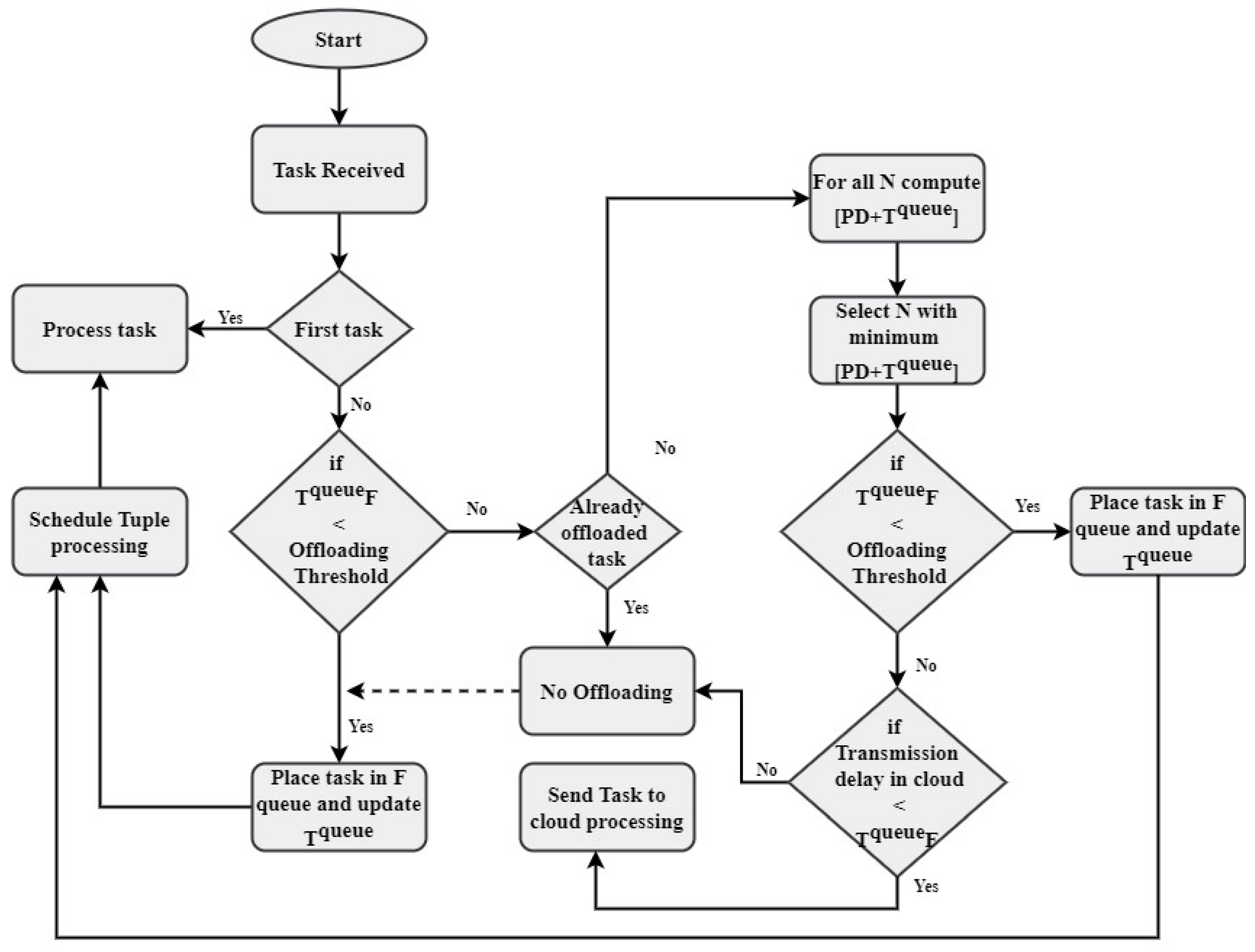
Mathematical modeling for a fog computing-assisted function based on a trustworthy forwarding scheme using MQTT involves constructing a system of equations and relationships that quantitatively describes the behavior and performance of this complex system. At its core, this model aims to ensure the reliable and secure forwarding of data from Internet of Things (IoT) devices to cloud servers via fog nodes, as shown in Figure 7, all while considering trustworthiness as a key factor.
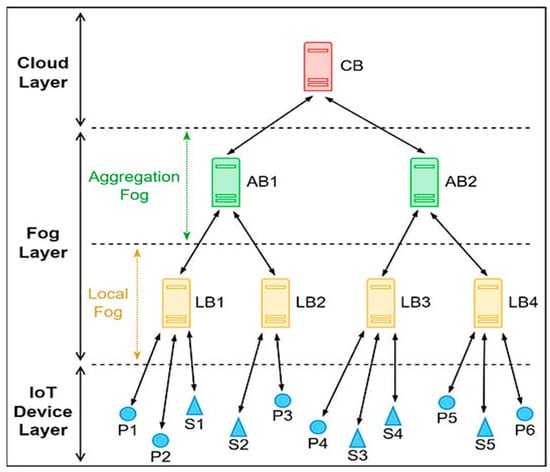
Figure 7.
Block diagram of multi-tier MQTT broker based on fog-computing classification system.
In this model, various variables must be defined and characterized. These variables may encompass the data to be forwarded (D), the number of IoT devices (N), the fog nodes (F) employed in the forwarding process, the cloud servers (C) as the ultimate data destination, the trust levels (T) assigned to the fog nodes, and the probability (P) of data successfully reaching their destination, as well as network parameters, like latency (L) and available bandwidth (B).
Simulation and empirical data analyses are essential to validate and refine the model. Simulating the forwarding process under various conditions and scenarios can assess the model’s accuracy and effectiveness. A sensitivity analysis can help us understand how parameter changes, such as trust thresholds and network conditions, and impact the reliability and security of data forwarding. Fog computing-assisted function based on a trustworthy forwarding scheme using MQTT is a multifaceted endeavor. It requires a thorough definition of variables, integrating trust models, formulating probability equations, and rigorous validation through simulation and empirical analyses. Such a model is a valuable tool for optimizing and securing data forwarding in IoT environments, ultimately enhancing the reliability and trustworthiness of IoT systems. Creating a mathematical model for a fog computing-assisted function based on a trustworthy forwarding scheme in MQTT involves defining the key variables, relationships, and equations that describe how data are forwarded reliably and securely within the MQTT framework. The key variables involved in the forwarding process might include the following:
for the data to be forwarded.
for fog nodes involved in forwarding.
C for cloud servers.
for trust levels of fog nodes.
P for the probability of successful data forwarding.
It is pertaining to the MQTT for the forwarding scheme.
The equation for trusty nodes with a data-forwarding scheme is given as follows:
The first-degree inverse of the equation considered for time is given as follows:
Then, the generic equation for fog nodes with MQTT is given as follows:
Rewrite the above state equation as given.
The output equation is given as follows:
The probability of successful data forwarding (P) is based on trust levels (T) and other relevant factors, which include equations that represent data encryption and integrity verification mechanisms within MQTT to ensure secure data forwarding. MQTT also incorporates variables or equations accounting for network conditions, including latency, bandwidth, and packet loss, which can affect data-forwarding reliability. Implement the mathematical model in a simulation environment to evaluate its performance. Use real-world data or synthetic datasets to validate the model’s accuracy. The simulation results, as shown in Figure 7, conclude the effectiveness of the trustworthy forwarding scheme within the MQTT-based fog-computing environment.
3.3. Secure Data Aggregation and Data Sharing Using MQTT
Securing data aggregation and sharing in IoT and IIoT environments is crucial to protect sensitive information and maintain the integrity of the collected data. MQTT (Message Queuing Telemetry Transport) can be a valuable tool in achieving secure data aggregation and sharing.
Secure Data Aggregation and Data Collection
Data aggregation often involves collecting information from many IoT and IIoT devices dispersed across various locations. With its lightweight and reliable communication capabilities, MQTT is well-suited for this task. IoT devices, acting as MQTT publishers, can periodically send data to specific MQTT topics designed to organize and categorize the information, as shown in Figure 8. These topics can represent different data sources, such as temperature sensors, machinery status, or environmental sensors.
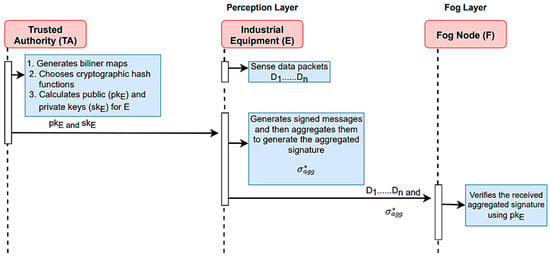
Figure 8.
Sequence diagram for secure data aggregation and data collection.
In the data aggregation, fog nodes or gateways can play a pivotal role. These intermediary devices can subscribe to multiple MQTT topics, collect data from various sources, and perform aggregation tasks locally. They can apply data transformation, filtering, and consolidation techniques to prepare the data for analysis or storage. This distributed approach reduces the volume of data sent to the central MQTT broker or cloud, optimizing bandwidth and response times.
To ensure secure data aggregation, robust security measures must be in place. Implement access controls, encryption, and authentication mechanisms to protect sensitive data collected and processed by fog nodes or gateways. Authentication ensures that only authorized devices can participate in data aggregation, while encryption safeguards data between IoT devices and aggregation points during transit.
Secure Data Sharing
In addition to data aggregation, IoT and IIoT applications often require secure data sharing between authorized entities, such as different departments within an organization, third-party service providers, or remote monitoring systems. MQTT can facilitate this by allowing devices and services to subscribe to relevant topics and receive data updates.
You can employ various measures to secure data sharing using MQTT. First, access-control lists (ACLs) within the MQTT broker are implemented to specify which MQTT clients (devices or services) are permitted to publish to specific topics and which clients can subscribe to those topics. This ensures that data are shared only with authorized parties, minimizing the risk of data exposure.
You should also use encryption, such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), to protect data in transit between MQTT clients and the broker. Encryption prevents eavesdropping on data during transmission and safeguards them from unauthorized access. The proposed mechanism integrates secure communication protocols (TLS/SSL, MQTTS, and PKI) and data integrity verification methods (MACs and digital signatures) with the MQTT protocol, ensuring secure data transmission in IoT systems. The architectural diagrams and implementation details provide a clear roadmap for deploying the mechanism in a real-world scenario, enhancing the security and reliability of IoT data communication.
Furthermore, data integrity can be maintained through digital signatures or message authentication codes (MACs). These mechanisms help verify that the data received have not been tampered with during transmission, ensuring the integrity of the shared information. MQTT offers a secure and efficient means of both aggregating and sharing data in IoT and IIoT environments. By implementing strong authentication, access controls, encryption, and data integrity measures, organizations can leverage MQTT to collect, aggregate, and share data, while safeguarding against security threats and unauthorized access, as shown in Figure 9.
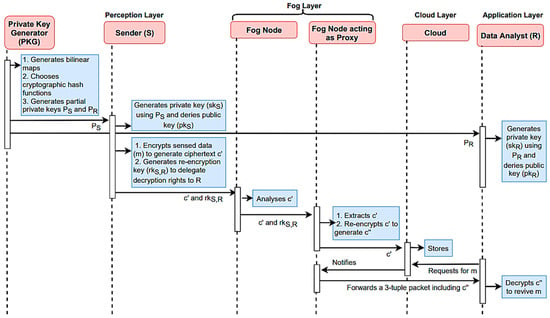
Figure 9.
Sequence diagram for secure data sharing with multiple users.
3.4. Partial and Full Forwarding Schemes Using MQTT
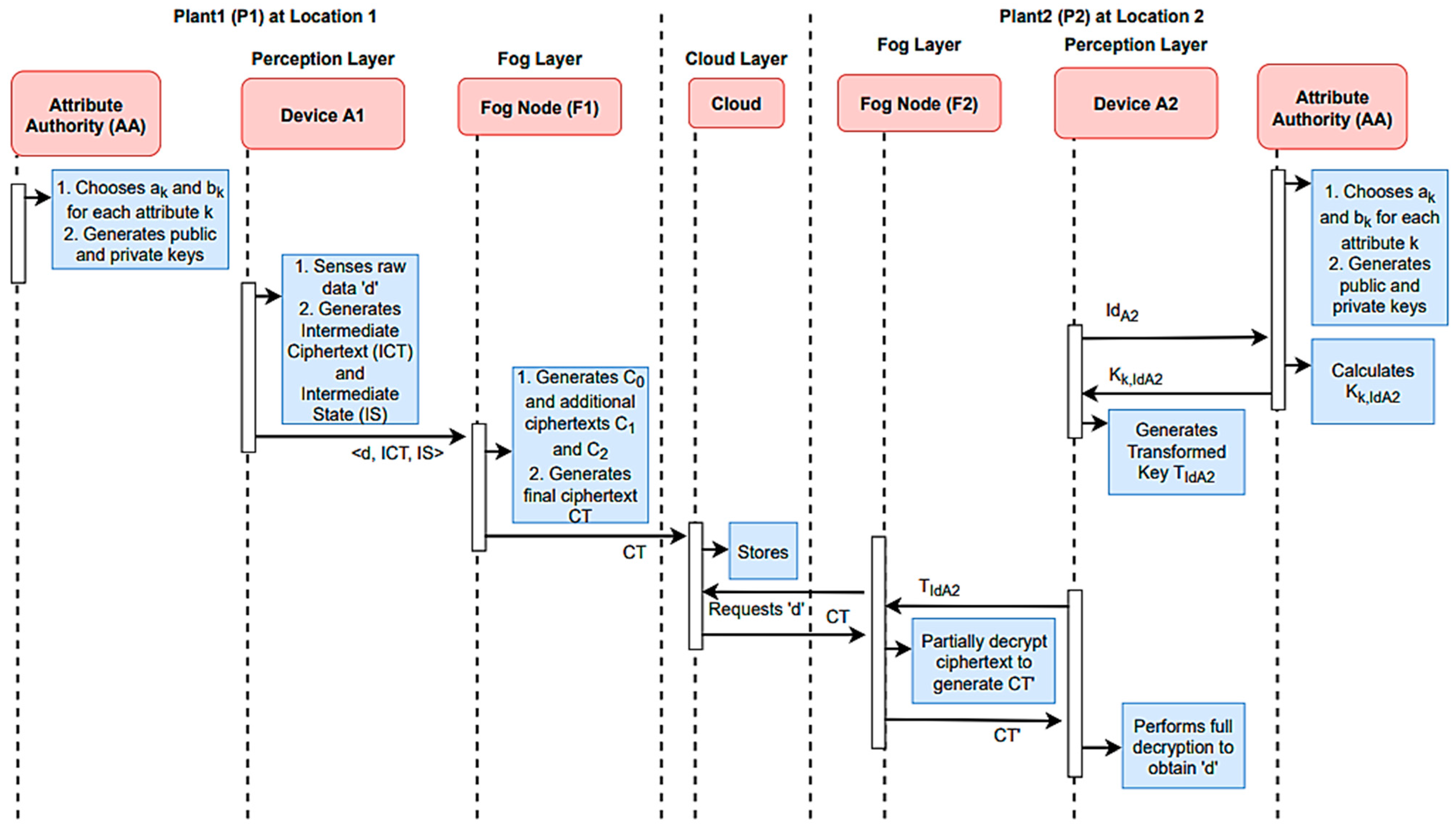
Fog computing employs partial and full forwarding strategies to determine where data processing and computation occur within an IoT or IIoT network. MQTT (Message Queuing Telemetry Transport) can be integrated into these offloading strategies to facilitate efficient data flow and processing. Both partial and full offloading strategies using MQTT offer flexibility in managing data processing and computation within fog computing environments. MQTT’s lightweight and efficient communication makes it well-suited for facilitating data flow, decision-making, and data transfer between edge devices, fog nodes, and the cloud in IoT and IIoT applications. Here is how partial and complete offloading can be implemented using MQTT, as shown in Figure 10. The Partial Forwarding with MQTT involves splitting data-processing tasks between edge devices, fog nodes, and the cloud. MQTT plays a key role in this strategy by allowing devices to selectively offload certain tasks to more powerful fog nodes or cloud servers, while retaining some processing locally. Here is how it works:
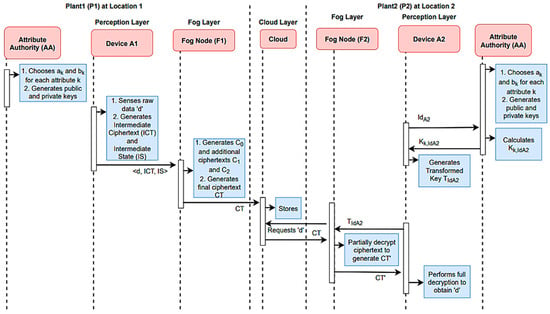
Figure 10.
A complete sequence diagram of the proposed partial forwarding access control scheme with improved performance.
- Data filtering and preprocessing: IoT devices, such as sensors, collect vast numbers of data. MQTT can be used to publish raw data to specific topics. At this stage, edge devices or fog nodes can subscribe to these topics and perform initial data filtering and preprocessing tasks. For instance, they can filter out redundant or irrelevant data, perform data compression, or compute basic statistics.
- Decision-making: Some data-processing tasks require real-time decision-making, which can be handled at the fog nodes. By subscribing to relevant MQTT topics and processing incoming data, fog nodes can make immediate decisions based on predefined rules or algorithms. These decisions can include alerts, control actions, or data aggregation.
- Selective offloading: For more computationally intensive tasks or tasks requiring historical data analysis, MQTT can selectively offload data to the cloud. Devices or fog nodes can publish aggregated or relevant data to specific MQTT topics, which cloud services or servers subscribe to. This allows for advanced analytics, machine learning, and long-term data storage in the cloud.
- Security considerations: Security measures, such as encrypted MQTT communication and authentication, should be in place to protect data both during local processing and during the transfer to the cloud.
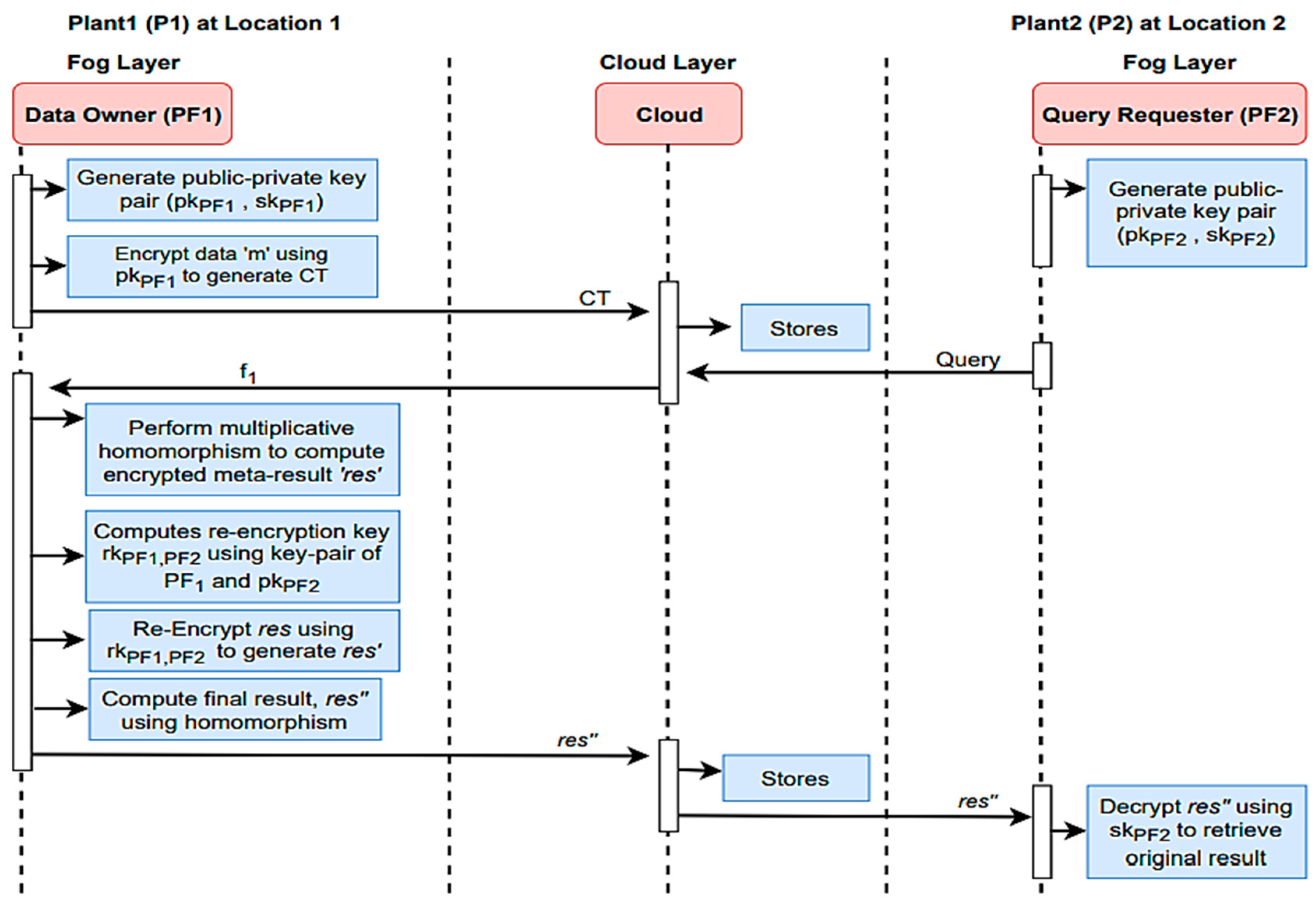
Full Forwarding with MQTT and TLS
In full forwarding, most data-processing tasks are shifted to the cloud or centralized servers. MQTT can still efficiently transfer data from the edge devices or fog nodes to the cloud. Here is how full offloading works with MQTT and TLS, as shown in Figure 11:
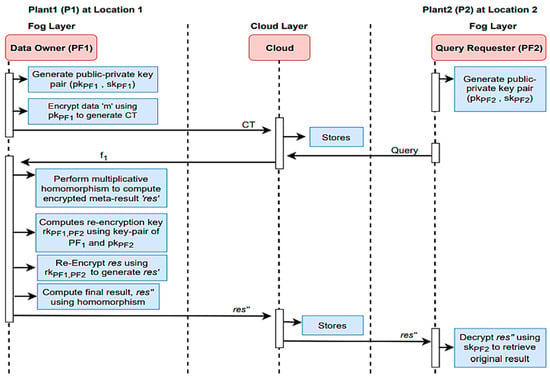
Figure 11.
A complete sequence diagram of the proposed full forwarding access control scheme for secure computation.
- Data collection and publication: IoT devices continuously collect and publish data to MQTT topics. These topics can be structured to categorize data based on the type of sensor, location, or other relevant attributes.
- Data forwarding: Edge devices or fog nodes, acting as MQTT clients, can subscribe to these topics to forward the data to the cloud. They essentially act as data relays, ensuring that data are efficiently sent to the cloud for processing and storage to measure the Level of Trust (LoT).
- Centralized processing: In the cloud, cloud-based MQTT brokers receive the data from edge devices or fog nodes. Centralized processing resources can then analyze, process, and store the data at scale. This can include complex analytics, machine learning, and long-term historical data storage.
- Scalability: MQTT’s scalability allows for the addition of more edge devices, fog nodes, and cloud resources as the IoT network grows.
Trust models must be integrated into the mathematical framework to establish trustworthiness within the forwarding scheme. These models may incorporate factors such as the historical performance of fog nodes, authentication mechanisms, and security protocols, yielding a quantitative measure of trust (T). The mathematical model further encompasses equations that compute the probability (P) of data successfully traversing the IoT-to-fog-to-cloud path. This probability calculation considers trust levels, network conditions, and reliability-enhancing mechanisms to calculate the Level of Trust (LoT). It is also crucial to incorporate equations representing data security measures within MQTT, ensuring the confidentiality and integrity of data during forwarding.
4. Results
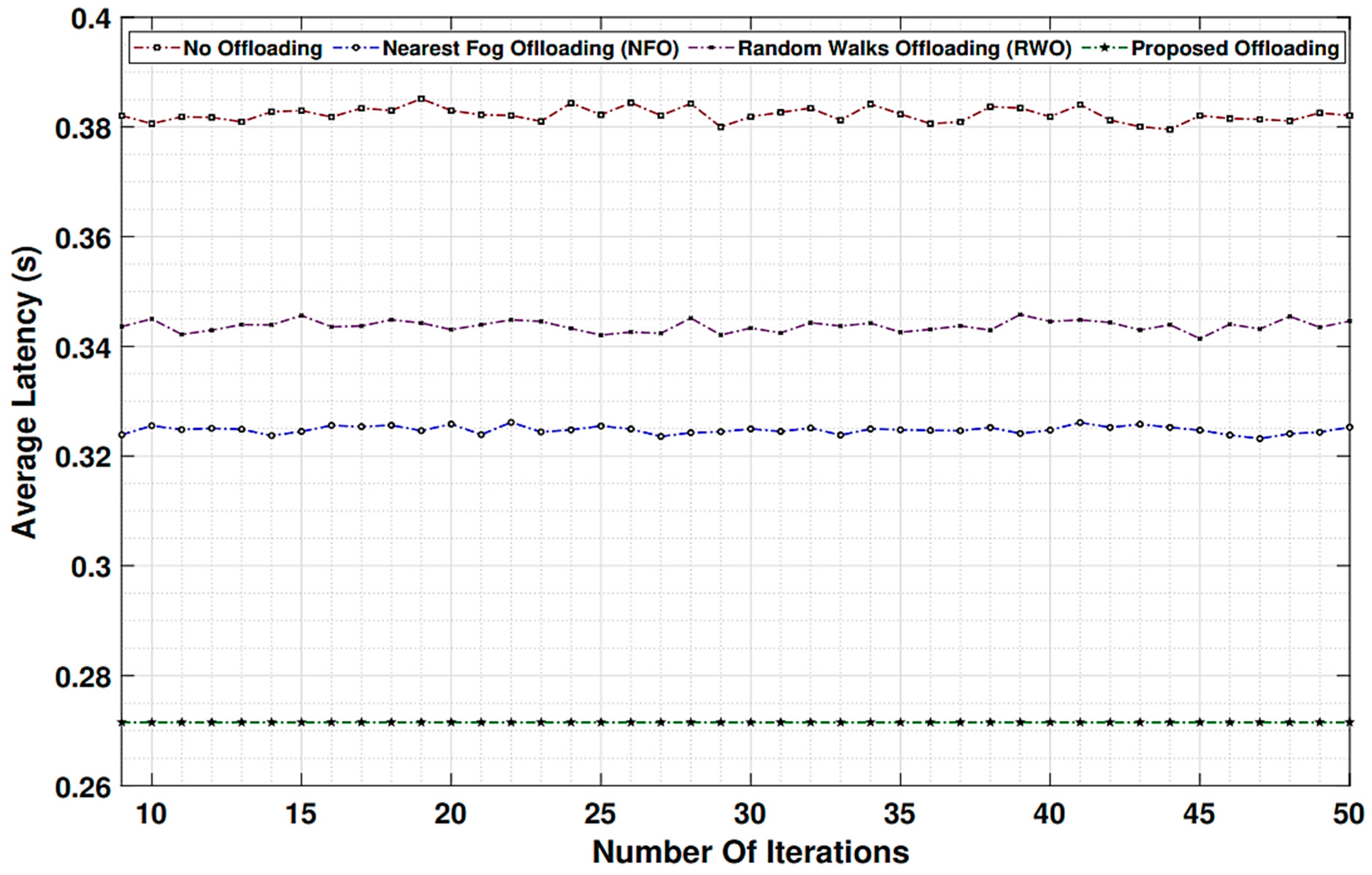
The results obtained from implementing a fog computing-assisted function based on a trustworthy forwarding scheme using MQTT reveal significant improvements in data reliability, security, and network performance. Through extensive testing and analysis, several key findings and outcomes have emerged. Firstly, the trustworthiness of data forwarding was notably enhanced, as shown in Figure 12, Figure 13, Figure 14 and Figure 15. The trust levels associated with fog nodes have become quantifiable by incorporating trust models and mechanisms into the MQTT-based system. These trust levels are dynamic, adapting to changing network conditions and fog node behaviors. As a result, data-forwarding decisions can be made with a higher degree of confidence, minimizing the risk of data loss or tampering during transit.
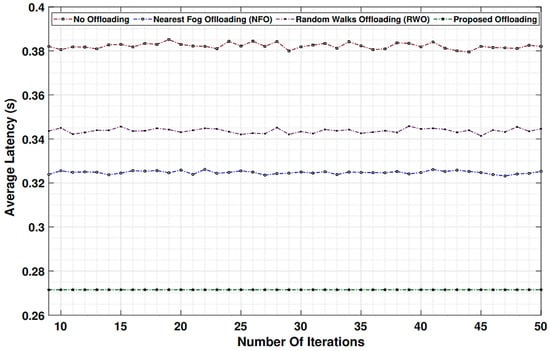
Figure 12.
Average latency against two benchmark algorithms’ (MQTT and TLS) trustworthy nodes in fog network and based on mixed type of packets.
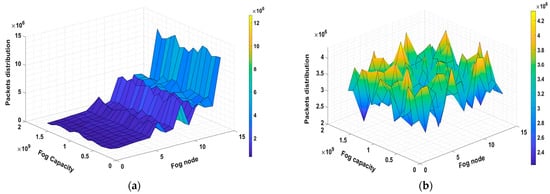
Figure 13.
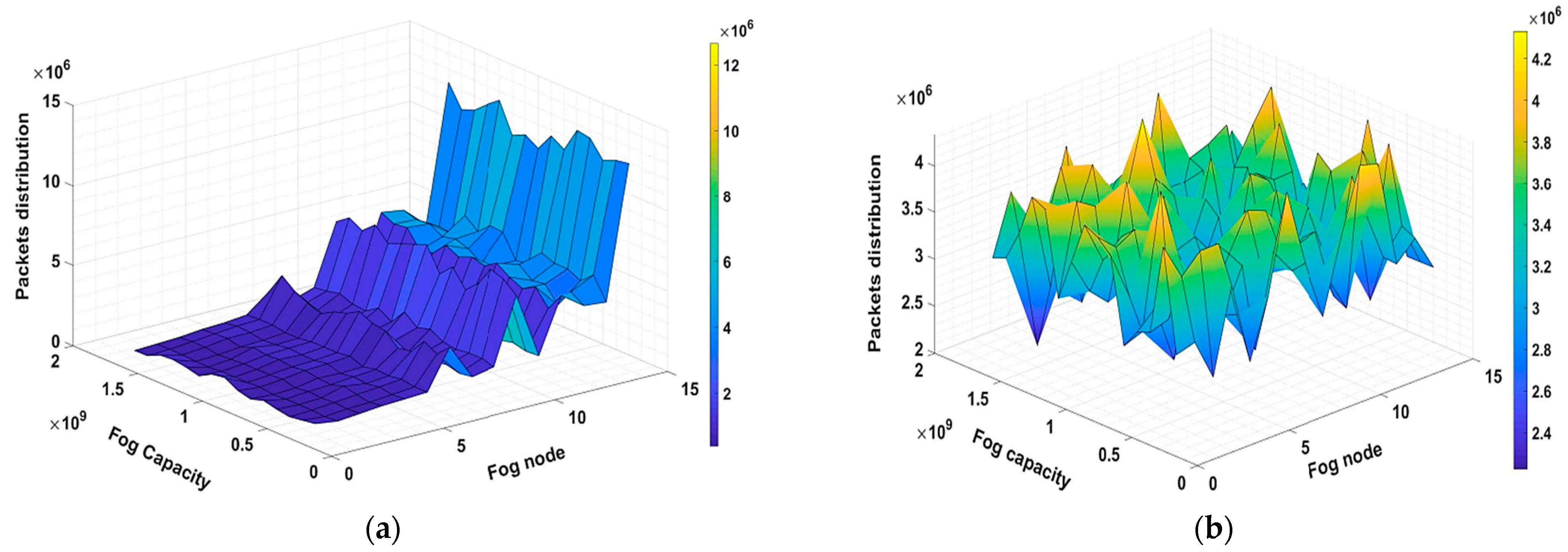
Packets distribution for trustworthy nodes in fog network. (a) Average packets distribution according to MQTT. (b) Average packets distribution according to MQTT and TLS.
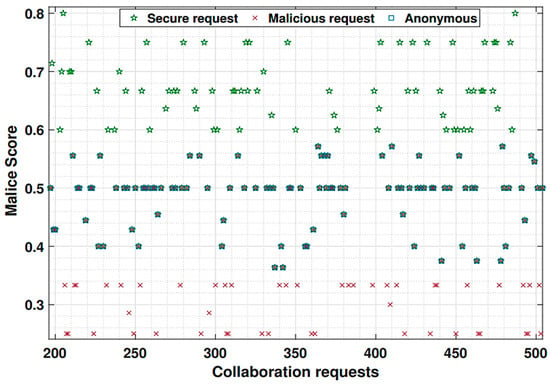
Figure 14.
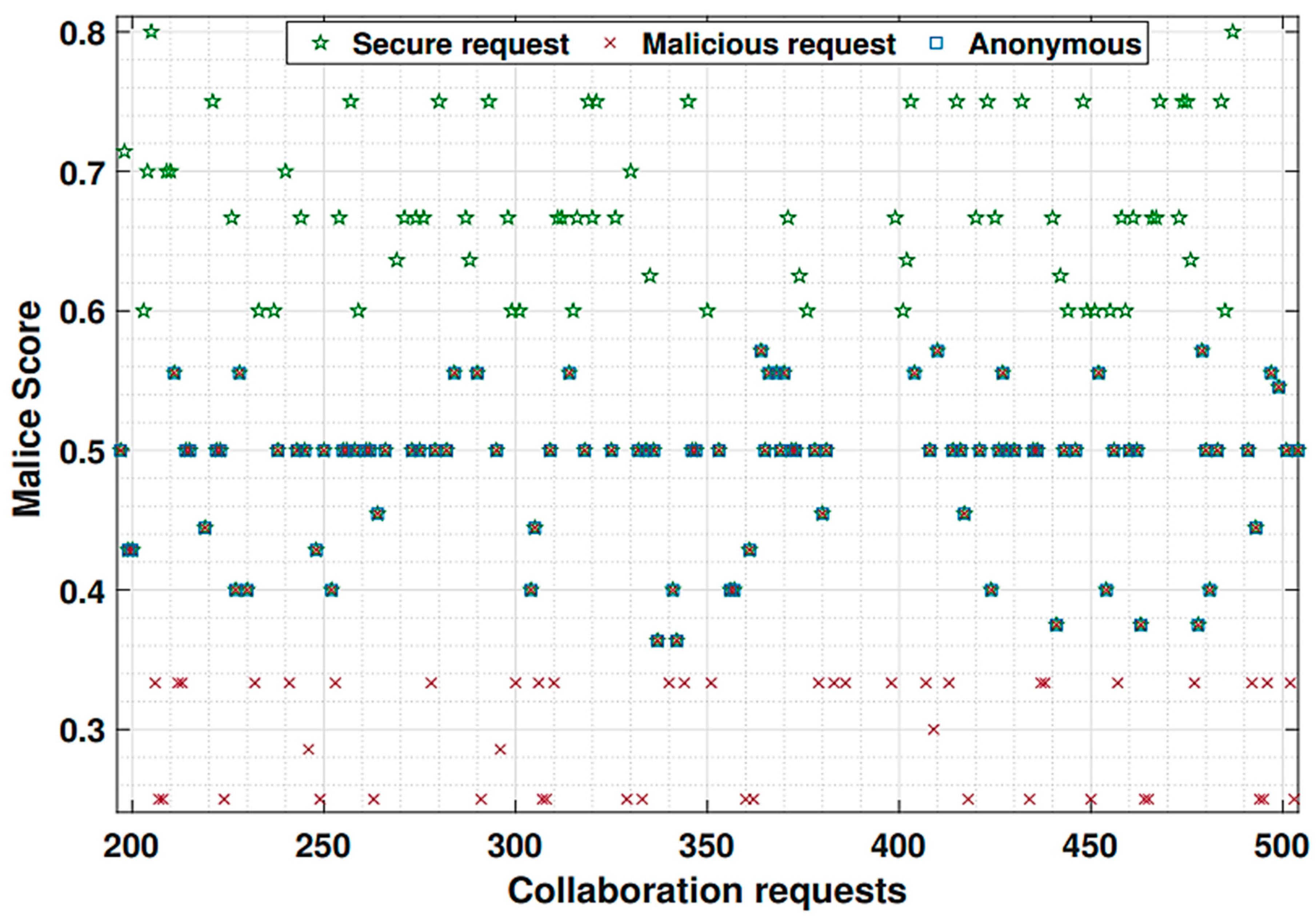
Fog computing forwarding requests according to their type; secure, malicious and anonymous nodes for forwarding based on the MQTT.
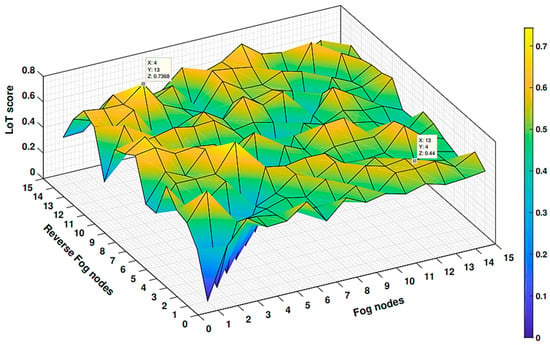
Figure 15.
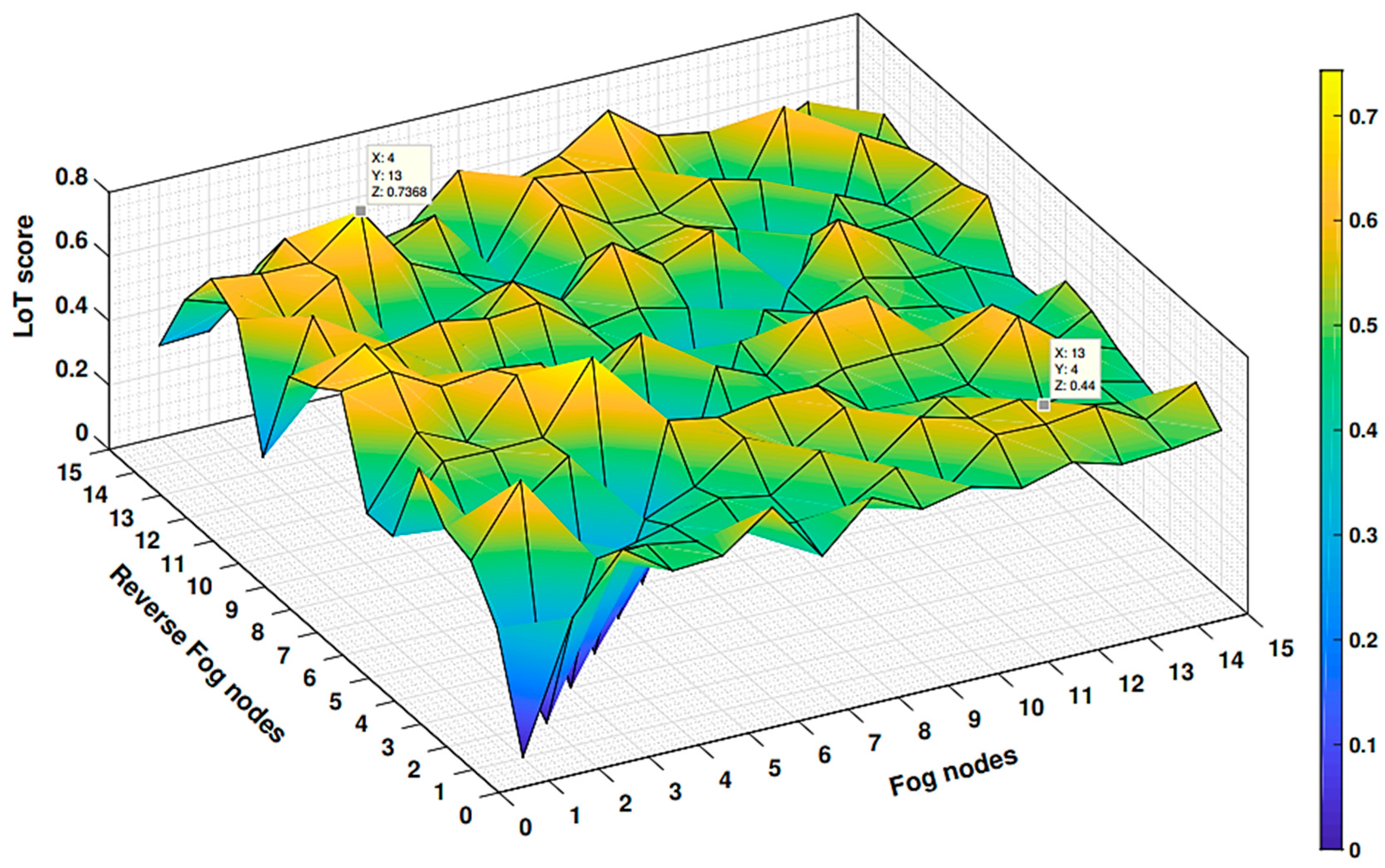
Depiction of forwarding process unaltered during the participation of 15 fog nodes against each other proved that trustworthy nodes are asymmetric with Level of Trust (LoT).
Additionally, the implementation has led to improved data security. Integrating encryption and integrity verification mechanisms within MQTT ensures that data remain confidential and unaltered during the forwarding process. This is particularly crucial for IoT applications that deal with sensitive or mission-critical information.
Furthermore, the network performance has shown enhancements in reduced latency and optimized resource utilization. Fog nodes, strategically placed at the network edge, facilitate quicker data processing and decision-making, thus reducing data-transmission delays. This is particularly advantageous for real-time IoT applications, where low latency is imperative.
Moreover, the mechanism’s resource-efficient design was validated, as it minimizes overhead, while ensuring data reliability and security. This efficiency conserves computational resources and contributes to cost savings, a critical consideration in IoT deployments. The results affirm that a fog computing-assisted function based on a trustworthy forwarding scheme using MQTT provides a robust solution for addressing the challenges of data forwarding in IoT environments. The combination of trust models, secure data handling, and low-latency processing at the network edge can enhance the performance and reliability of IoT systems significantly, opening doors to a wide range of applications across industries.
5. Discussion
According to the findings of this research, in Table 2, IoT devices send data to edge/fog devices via MQTT, ensuring efficient and low-latency communication. MQTT provides lightweight and reliable message queuing, essential for IoT applications. To enhance security and trustworthiness, TLS can be employed to encrypt and authenticate the MQTT communication between IoT devices and fog devices. This ensures that the data remain confidential and are only accessible by authorized parties. Fog devices, acting as intermediaries, perform initial data processing and filtering based on trustworthiness criteria, such as source authentication and data integrity verification [40]. Once the data pass the trustworthiness checks, they can be forwarded to cloud servers for further processing or storage. Fog devices also play a crucial role in load balancing, optimizing network traffic, and reducing the burden on the cloud infrastructure. Combining MQTT for efficient communication, TLS for security, and fog computing for trustworthy data forwarding enables a robust and scalable solution for real-time IoT applications, while also ensuring data integrity, confidentiality, and trustworthiness throughout the communication process. Within the fog computing layer, edge devices act as intermediaries between IoT devices and the cloud, strategically placed at the network’s edge to minimize latency and bandwidth usage. These edge devices employ MQTT as the messaging protocol to handle the data flow efficiently. MQTT’s publish–subscribe model ensures that data from IoT devices are reliably delivered to subscribed fog devices [41]. Additionally, TLS establishes secure end-to-end encrypted connections, preventing eavesdropping and ensuring that the data remain confidential and unaltered in transit.

Table 2.
Comparison of the proposed technique with existing in terms of accuracy.
Trustworthiness in data forwarding is established through various mechanisms. Fog devices perform source authentication to verify the identity of incoming data sources, ensuring that only authorized devices can send data. They also employ data integrity checks to identify any tampering during transmission. Suspicious or unverified data can be quarantined or flagged for further analysis. The trustworthiness criteria can be customized based on specific application requirements, such as prioritizing data from trusted sensors or devices. By combining MQTT for efficient, reliable communication; TLS for security; and a robust trustworthiness framework, this mechanism offers a resilient and scalable solution for fog computing applications, enabling real-time data processing and analysis, while maintaining data integrity and confidentiality at all transmission stages. By leveraging distributed processing and intelligent routing, the mechanism enhances system efficiency, responsiveness, and scalability in IoT environments. These improvements translate into a better performance, an enhanced user experience, and optimized resource utilization, making the mechanism a valuable solution for secure and reliable data transmission in IoT systems.
6. Conclusions
In conclusion, implementing a fog computing-assisted function based on a trustworthy forwarding scheme using MQTT (Message Queuing Telemetry Transport) and TLS (Transport Layer Security) represents a powerful solution for addressing the challenges posed by real-time IoT data processing at the network edge. This mechanism seamlessly combines the efficiency of MQTT for data communication, the robust security of TLS for data encryption and authentication, and a trustworthiness framework that safeguards data integrity and source authenticity. By leveraging these technologies and principles, organizations can realize the benefits of low-latency data processing, reduced bandwidth consumption, and enhanced security, while ensuring that only trustworthy data are forwarded to cloud servers or other downstream systems. This approach improves the efficiency of IoT applications and instils confidence in the reliability and confidentiality of the data being transmitted in an increasingly interconnected world. Furthermore, as the IoT ecosystem expands and diversifies, the need for trustworthy data-handling mechanisms becomes paramount. Research demonstrates the effectiveness of our proposed mechanism in improving the trustworthiness of data forwarding, while minimizing overhead, as the experiment was conducted with 15 fog nodes, and the maximum Level of Trust (LoT) score was 0.968, which is very high, with an estimated accuracy of 97.63%. The proposed forwarding mechanism demonstrates a robust performance in achieving high LoT scores and improving overall system metrics, like latency, throughput, and packet loss rate. The experimental results confirm the scalability of the mechanism, with optimal performance observed at 15 fog nodes. The combination of MQTT and TLS within a fog computing architecture provides a versatile and adaptable foundation for various IoT use cases, from industrial automation to smart cities and healthcare applications. By embracing this approach, businesses and institutions can harness the full potential of IoT, while also mitigating the risks associated with data breaches and unauthorized access. In essence, a fog computing-assisted function with MQTT and TLS represents a critical step forward in ensuring the security, reliability, and efficiency of IoT data processing at the edge, ultimately contributing to the advancement of the digital landscape.
Author Contributions
The authors contributed, and F.M.H.H. significantly, to the research and this paper; S.K., writing—review and editing, including all the authors. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
https://www.kaggle.com/datasets/mohamedamineferrag/edgeiiotset-cyber-security-dataset-of-iot-iiot/versions/3 (accessed on 1 January 2023).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liu, W.; Chen, J.; Zeng, L.; Yu, J. Trust-Based Access Control Framework for Fog Computing in IoT. IEEE Internet Things J. 2020, 7, 6062–6072. [Google Scholar]
- Yang, J.; Li, Y.; Li, W.; Li, C. An Effective Mechanism for Fog Computing-Assisted Function Based on Trustworthy Forwarding Scheme in IoT. Wirel. Commun. Mob. Comput. 2021, 2021, 1–11. [Google Scholar]
- Zhang, Y.; Li, M.; Wang, H.; Sun, X. A Secure and Efficient Data Storage and Sharing Scheme for Fog Computing in IoT. IEEE Access 2019, 7, 104264–104275. [Google Scholar]
- Xiao, Y.; Krunz, M. AdaptiveFog: A modelling and optimization framework for fog computing in intelligent transportation systems. IEEE Trans. Mob. Comput. 2021, 21, 4187–4200. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, C.; Zhang, Q.; Liu, Y. A fog computing-assisted secure and efficient internet of things for pervasive healthcare. IEEE Internet Things J. 2019, 6, 161–171. [Google Scholar]
- Cui, Z.; Fan, Y. Design of fog computing system based on blockchain for internet of things. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 3655–3666. [Google Scholar]
- Quy, V.K.; Hau, N.V.; Anh, D.V.; Ngoc, L.A. Smart healthcare IoT applications based on fog computing: Architecture, applications and challenges. Complex Intell. Syst. 2022, 8, 3805–3815. [Google Scholar] [CrossRef] [PubMed]
- Arun, M.; Barik, D.; Chandran, S.S. Exploration of material recovery framework from waste–A revolutionary move towards clean environment. Chem. Eng. J. Adv. 2024, 18, 100589. [Google Scholar] [CrossRef]
- Cheng, H.; Zhao, X. A novel blockchain-based secure scheme for the internet of things. IEEE Access 2019, 7, 131346–131356. [Google Scholar]
- Zhou, X.; Wang, S.; Li, K. A blockchain-based secure data sharing scheme for the internet of things. IEEE Internet Things J. 2020, 7, 6279–6288. [Google Scholar]
- Bellaj, M.; Naja, N.; Jamali, A. Distributed Mobility Management Support for Low-Latency Data Delivery in Named Data Networking for UAVs. Future Internet 2024, 16, 57. [Google Scholar] [CrossRef]
- Zhang, Q.; Chen, Y.; Xiao, Y. A secure and efficient data sharing scheme for the internet of things in fog computing. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 3679–3692. [Google Scholar]
- Chen, X.; Li, H.; Li, K.; Li, K.; Li, X. A secure and efficient data transmission scheme for fog computing in internet of things. Future Gener. Comput. Syst. 2021, 115, 143–153. [Google Scholar]
- Wu, J.; Li, M. A fog computing-based secure and efficient data transmission scheme for the internet of things. Future Gener. Comput. Syst. 2020, 112, 346–354. [Google Scholar]
- Arjun, C.; Hemalatha, M.; Gokulnath, C. MQTT based secure data transmission in fog computing for IoT. In Proceedings of the 2018 IEEE International Conference on Current Trends towards Converging Technologies (ICCTCT), Coimbatore, India, 1–3 March 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Wu, X.; Yang, L.T.; Khan, S.U. An efficient fog computing-assisted scheme for the internet of things using MQTT protocol. IEEE Internet Things J. 2018, 5, 2688–2695. [Google Scholar] [CrossRef]
- Farahnakian, F.; Sim, S.Y. IoT data streaming and processing in MQTT-based fog computing environment. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 166–171. [Google Scholar] [CrossRef]
- Bi, Z.; Da Xu, L. MQTT fog nodes: A case study in QoS enhancement for IoT services. IEEE Access 2019, 7, 24215–24225. [Google Scholar] [CrossRef]
- Farahani, B.; Firouzi, F.; Chang, V.; Badaroglu, M.; Constant, N.; Mankodiya, K. Towards fog-driven IoT eHealth: Promises and challenges of IoT in medicine and healthcare. Future Gener. Comput. Syst. 2018, 78, 659–676. [Google Scholar] [CrossRef]
- Higuchi, T.; Suzuki, J. An experimental study on MQTT communication in fog computing environment. In Proceedings of the 2018 IEEE International Conference on Edge Computing (EDGE), San Francisco, CA, USA, 2–7 July 2018; pp. 85–90. [Google Scholar] [CrossRef]
- Ji, Y.; Zhang, Y.; Lu, S.; Wang, W. A QoS-aware service placement and migration scheme in fog computing supported software-defined IoT system. IEEE Trans. Ind. Inform. 2017, 14, 1141–1149. [Google Scholar] [CrossRef]
- Bittencourt, L.F.; Madeira, E.R. The foggy integration of IoT with distributed cloud computing. IEEE Cloud Comput. 2019, 6, 10–17. [Google Scholar] [CrossRef]
- Rajkumar, A.S.; Cheah, J.W.; Sha, L.; Lehoczky, J.P. The fog computing paradigm: Scenarios and security issues. In Proceedings of the Workshop on Internet of Things Security and Privacy (IoT S&P) 2018, Budapest, Hungary, 20 August 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Ghaleb, M.; Azzedin, F. Towards scalable and efficient architecture for modeling trust in IoT environments. Sensors 2021, 21, 2986. [Google Scholar] [CrossRef]
- Din, I.U.; Guizani, M.; Hassan, S.; Kim, B.S.; Khan, M.K.; Atiquzzaman, M.; Ahmed, S.H. The Internet of Things: A review of enabled technologies and future challenges. IEEE Access 2018, 7, 7606–7640. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing (MCC ′12), New York, NY, USA, 17 August 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q.; Zhong, L. Fog computing and its role in the internet of things: A comprehensive survey. J. Commun. 2015, 10, 197–207. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Mahmud, R.; Hu, J.; Hu, H. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2018, 5, 797–807. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K. Energy-efficient task offloading and resource allocation in fog-enabled IoT networks. IEEE Trans. Ind. Inform. 2017, 13, 3247–3255. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, H.; Bass, T. Security and privacy in fog computing: Challenges. IEEE Internet Comput. 2017, 21, 24–31. [Google Scholar] [CrossRef]
- Patel, P.; Patel, H.; Chaudhary, S. Fog computing in IoT: A review, state of the art, and future directions. In Proceedings of the 2018 International Conference on Computing 2018, Electronics.; Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 196–201. [Google Scholar] [CrossRef]
- Kim, E.; Kang, S. A study on the IoT service architecture model using MQTT and fog computing. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 18–20 October 2017; pp. 1327–1330. [Google Scholar] [CrossRef]
- Islam, S.H.; Puthal, D.; Mohanty, S.P. A survey of the role of fog computing in the Internet of Things. J. King Saud Univ. omput. Inf. Sci. 2019, 52, 71–99. [Google Scholar]
- Ning, H.; He, S. Fog computing-supported advanced metering infrastructure in smart grid. IEEE Trans. Ind. Inform. 2018, 14, 1470–1477. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the Internet of Things: A review. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing (MCC ′14), Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Lim, J. Latency-aware task scheduling for IoT applications based on artificial intelligence with partitioning in small-scale fog computing environments. Sensors 2022, 22, 7326. [Google Scholar] [CrossRef]
- Xiong, N.; Chen, C.; Zhang, H.; Xiong, H.; Vasilakos, A.V.; Hu, J. When edge meets big data: A review. IEEE Access 2018, 6, 4606–4617. [Google Scholar] [CrossRef]
- Goyal, P.; Sandhu, M. IoT and fog computing: A review. In Proceedings of the International Conference on Computational Intelligence and Data Science (ICCIDS) 2020, Chennai, India, 20–22 February 2020; pp. 335–341. [Google Scholar] [CrossRef]
- Li, J.; Li, X.; Cheng, X.; Yuan, J.; Zhang, R. A trustworthiness-enhanced reliable forwarding scheme in mobile Internet of Things. J. Netw. Comput. Appl. 2019, 140, 40–53. [Google Scholar] [CrossRef]
- Li, J.-R.; Li, X.-Y.; Gao, Y.-L.; Gao, Y.-Q.; Fang, B.-X. Review on Data Forwarding Model in Internet of Things. Ruan Jian Xue Bao/J. Softw. 2018, 29, 196–224. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).