Abstract
Vehicular ad-hoc networks (VANETs) can significantly improve the level of urban traffic management. However, the sender unlinkability has become an intricate issue in the field of VANETs’ encryption. As the sender signcrypts a message, the receiver has to use the sender’s identity or public key to decrypt it. Consequently, the sender can be traced using the same identity or public key, which poses some security risks to the sender. To address this issue, we present an unlinkable and revocable signcryption scheme (URSCS), where an efficient and powerful signcryption mechanism is adopted for communication. The sender constructs a polynomial to generate a unique session key for each communication, which is then transmitted to a group of receivers, enabling the same secret message to be sent to multiple receivers. Each time a secret message is sent, a new key pair is generated, and an anonymization mechanism is introduced to conceal the true identity of the vehicle, thus preventing malicious attackers from tracing the sender through the public key or the real identity. With the introduction of the identification public key, this scheme supports either multiple receivers or a single receiver, where the receiver can be either road side units (RSUs) or vehicles. Additionally, a complete revocation mechanism is constructed with extremely low communication overhead, utilizing the Chinese remainder theorem (CRT). Formal and informal security analyses demonstrate that our URSCS scheme meets the expected security and privacy requirements of VANETs. The performance analysis shows that our URSCS scheme outperforms other represented schemes.
1. Introduction
With the increasing popularity of cars in ordinary families and the increasing complexity of urban roads, traffic accidents have become a major risk factor in modern society [1]. In order to reduce the traffic dangers encountered by people in daily life and improve the efficiency of information sharing between vehicles, VANETs have emerged [2]. Vehicles move at high speeds, and VANETs mainly use the dedicated short-range communications (DSRC) protocol [3], so it is easy for malicious attackers to listen, intercept, modify, and re-transmit messages [4], which poses great security risks to VANETs. Therefore, ensuring the legitimacy of the information source, ensuring that the received message is not tampered with, and ensuring the secret transmission of the message have become basic requirements in the field of vehicle networking security [5,6,7].
In recent years, signcryption technology has proven capable of completing the above three required functions in one operation simultaneously, which greatly reduces communication and computation overhead [8]. It has been widely used, especially in multi-receiver scenarios, such as VANETs, mobile communication devices, wireless body area networks, and maritime transportation systems. However, the traditional multi-receiver signcryption technology requires the sender to negotiate with each receiver and send different ciphertext, which significantly reduces the efficiency of message transmission [9,10,11,12,13,14,15,16,17]. Additionally, there is a problem that can be traced back to the sender. When the same sender sends multiple messages, it needs to use its own private key for signcryption, and the receiver uses the public key or real identity of the sender for unsigncryption. Therefore, malicious attackers can trace the sender based on the same public key or real identity used in the process of multiple signcryption. In order to solve this problem, Liang et al. [18] first proposed a scheme with multiple receivers and unlinkable to senders. An anonymous transmission is taken each time a message is sent and a key pair is updated by the sender, and uses CRT to transmit the public session key. However, their scheme can only be used for one-to-many transmission for road side units (RSUs).
In the context of VANETs, malicious vehicles will send malicious messages for various reasons, leading to various traffic problems. Therefore, TCC’s ability to track and revoke malicious vehicles is particularly important [19]. In VANETs, for the implementation of the revocation mechanism, the schemes [20,21,22] allocate a revocation list to each vehicle, resulting in high storage overhead for the entire system. At the same time, TCC needs to frequently update the revocation list to all vehicles, which also incurs high communication overhead. Scheme [18] implements revocation mechanisms by constructing polynomials, but since the number of parameters in the publicly disclosed revocation public key equals the number of vehicles, this method consequently faces the problem of high transmission overhead. In a resource-constrained VANET environment, a revocation mechanism can only be practically feasible if its cost is sufficiently low.
With the motivation of addressing the aforementioned issues, this paper proposes an unlinkable and revocable signcryption scheme (URSCS). Our main contributions are listed as follows:
- For the first time, in the scenario of vehicle networking, our URSCS scheme truly realizes the unlinkable communication for the sender in one-to-many or one-to-one modes at the same time. By introducing the identification of public and private key pairs instead of real identities, the receivers can be either the vehicles or the RSUs. In order to achieve unlinkability of the sender, our URSCS scheme takes the following approach: First, we provide conditional privacy through a pseudonym mechanism, which effectively hides the true identity of the vehicle, so that malicious attackers cannot track the sender through the real identity. Second, the vehicle updates its key pair and pseudonym before each signcryption, ensuring that a malicious attacker cannot link the sender to the message based on the public keys or pseudonyms;
- Based on CRT, we propose a comprehensive revocation key update mechanism that incurs low communication costs. Regardless of the number of vehicles within the domain covered by a Traffic Control Center (TCC), the revocation key information transmitted remains at 96 bytes. Consequently, the TCC can efficiently remove malicious vehicles from the system and promptly update the revocation public key to prevent them from transmitting further harmful information. Additionally, by incorporating several time thresholds, our URSCS scheme effectively prevents malicious vehicles from continuing to send messages, even if their revocation keys are reassigned to new vehicles;
- We conduct formal and informal security analyses of our URSCS scheme, which show that our scheme satisfies various security requirements and can effectively resist various known potential attacks;
- Rigorous performance evaluation confirms that with the increase in the number of receiving ends, the communication and computation overhead of the proposed URSCS scheme has significant advantages compared with other related schemes.
The remainder of this paper is organized as follows: the related works are introduced in Section 2. Some preliminaries are briefly introduced in Section 3, including the elliptic curve cryptosystem, classical hard problems, and the basic concepts of CRT. Section 4 outlines the system model and security and privacy goals of our URSCS scheme. The detailed design of our URSCS scheme is described in Section 5. And the security analysis and performance assessment are presented in Section 6 and Section 7, respectively. Finally, we conclude this paper in Section 8.
2. Related Work
In this section, we will extensively discuss the security techniques involved in transmitting information over an open channel, mainly focusing on signcryption, revocability, anonymity, and unlinkability.
2.1. Signcryption
Zheng Yuliang [23] first introduced a new cryptographic primitive named signcryption, performing both signature and encryption, and simultaneously ensuring the authentication, integrity, and confidentiality of the message. Compared to the sign-then-encrypt method, this mechanism also reduced the computation overhead and communication overhead, making it suitable for resource-constrained application scenarios [24,25]. In 2003, Al-Riyami et al. proposed a new cryptography primitive called certificateless public key cryptography in [26], which addresses both the certificate management problem in traditional public key infrastructure (PKI) [27] and the key escrow problem in identity-based cryptosystems [28]. Specifically, a certificateless public key cryptography system divides a user’s public key and private key into two parts. The key generation center (KGC) generates only part of the public key and private key for the user, while the other part is generated by the user themselves, and the part generated by the user is referred to as the secret value. In 2008, Barbosa Manuel and Farshim Pooya proposed the first certificateless signcryption (CLSC) scheme [29], which combines the certificateless cryptosystem and signcryption. Since then, researchers have proposed a number of CLSC schemes [30,31,32,33]. However, these schemes are based on bilinear pairing operations, and due to the high computation cost of bilinear pairing, they are unsuitable for devices with limited computational resources, such as on-board units (OBUs) in vehicles.
In order to accommodate resource-constrained scenarios such as the VANETs, many researchers began designing certificateless signcryption schemes without pairing operations. Cui et al. designed a new certificateless aggregate signcryption scheme [34], successfully eliminating the expensive pairing operation and thereby improving computational efficiency. However, Zhan et al. pointed out that Cui et al.’s protocol is not guaranteed to be unforgeable under the second type of attack. They subsequently designed a new CLSC scheme [35] which addresses the presence of unforgeability in the second type of attack. Since then, many unpaired certificateless signcryption schemes, such as [36,37,38], have been developed and applied in numerous resource-constrained scenarios. However, these schemes also face certain challenges. For instance, the scheme proposed by Shen et al. [36] does not incorporate a revocation mechanism, and Yu and Ren’s scheme [37] has been proven unable to withstand signature forgery attacks and collusion attacks. Recently, a considerable number of signcryption-based schemes have been developed by numerous researchers for multi-receiver scenarios, aiming to boost communication and computation performance [8,11,12,13,14,15,16,17]. However, these schemes still suffer from all kinds of shortcomings. Specifically, the schemes [11,14,15], and Ref. [38] lacked sender unlinkability, enabling the receiver to associate the sender with a fixed public key, and Ref. [16] failed to provide sender anonymity due to the sender communicating openly with their real identity. In addition, a handful of schemes, specifically [8,17], lacked both a tracing and revocation mechanism.
2.2. Revocability
In order to solve the vehicle revocation problem, many researchers have proposed anonymity-based conditional privacy schemes with revocation function [20,21,22]. However, in these schemes, to ensure anonymity and unlinkability, the vehicle needs to be pre-loaded with a large number of anonymous public keys and certificates. However, one of the challenges with this type of scheme is the large scale of certificate revocation lists (CRL), resulting in increased storage and verification costs. When a vehicle is revoked, its certificate is added to the CRL, further increasing its size and thus exacerbating transmission delays. Therefore, the scale of the CRL and the cost of exhaustive search become important constraints of this revocation mechanism.
Shim et al. proposed a conditional privacy-preserving authentication scheme based on public key cryptography [39], where public identities are used to verify the legitimacy of vehicle identities, and vehicle anonymity is achieved through two trusted agents, namely, the trace authority and the private key generator. However, Wang et al. [40] pointed out that Shim and Kyung-Ah’s scheme [39] would incur significant computational and communication costs with an increase in the number of vehicles, and the revocation process could not meet the requirements of V2V communication, and proposed an enhanced security certificateless conditional privacy-preserving authentication scheme with revocation [40]. However, since the vehicle keys are all generated by the trusted authority, there is an issue with key escrow.
2.3. Anonymity and Unlinkability
In VANETs, anonymity means that no one can infer the sender’s identity information from the received message. Unlinkability ensures that no one (including the recipients of the messages) can determine whether two transmitted messages come from the same vehicle [18]. Currently, many researchers have proposed numerous authentication schemes for user anonymity [11,35,41,42,43,44]. However, most existing schemes in VANETs cannot fully achieve sender unlinkability. Specifically, the receiver must use the sender’s identity or public key to complete the verification process. Consequently, the receiver can link different messages to the same sender through the invariant elements, identity, or public key within the messages. For example, in [42], a new certificate-based identity authentication scheme was proposed to enhance the security of vehicular networks. However, when the sender is the same, the signing and verification process always uses the same pseudonym, allowing attackers to link multiple messages to the same sender through the identical pseudonym. Gayathri et al. [43] proposed a pairing-free certificateless authentication scheme to achieve batch verification in VANETs; however, each signature message generated by user contains an immutable parameter , an attacker can determine whether two messages are from the same sender by checking if the parameters in the signatures are equal. Liang et al. [18] achieved the first truly sender-unlinkable multi-receiver signcryption scheme. However, in Liang’s scheme, the real ID of the receiver must be used when transmitting information, which means that the receivers can only be RSUs, and V2V communication cannot be guaranteed.
3. Preliminaries
This section will provide a detailed introduction to the Chinese remainder theorem, the elliptic curve cryptosystem, and classic hardness assumptions.
3.1. Chinese Remainder Theorem (CRT)
The CRT is an important tool in number theory used to solve a class of problems related to systems of modular congruence equations. Consider a modular congruence system as follows.
where are given n integers, and are n coprime positive integers. If the congruence system (1) has a solution, then through the CRT, we can obtain a unique solution , where , is the multiplicative inverse of modulo . In this paper, the CRT is not used to solve for x in the congruence system; rather, its principles are employed to transmit public parameters.
3.2. Elliptic Curve Cryptosystem ECC
Assume is a finite field defined by modulo p, where p is a large prime number. We define an elliptic curve E over , which is in the form of a set of points , where a and b are elements of . And, the combination of an infinite point O along with every point on E comprises an additive elliptic curve group G, that possesses a prime order q. This group G satisfies the subsequent properties:
Point addition: For any P, , the following conditions hold: if , ; if , ; and if , , where is the intersection of elliptic curve E and the straight line connecting P and Q, R is the inverse of on G.
Scale multiplication: Given and , (n times).
3.3. Hard Problems
Elliptic Curve Discrete Logarithm Problem (ECDLP): Given P, , it is hard to compute the value of in a probabilistic polynomial-time (PPT), where .
Computational Diffie–Hellman Problem (CDHP): Given P, , , it is hard to compute in a PPT, where , .
4. System Model and Security Requirements
4.1. System Model
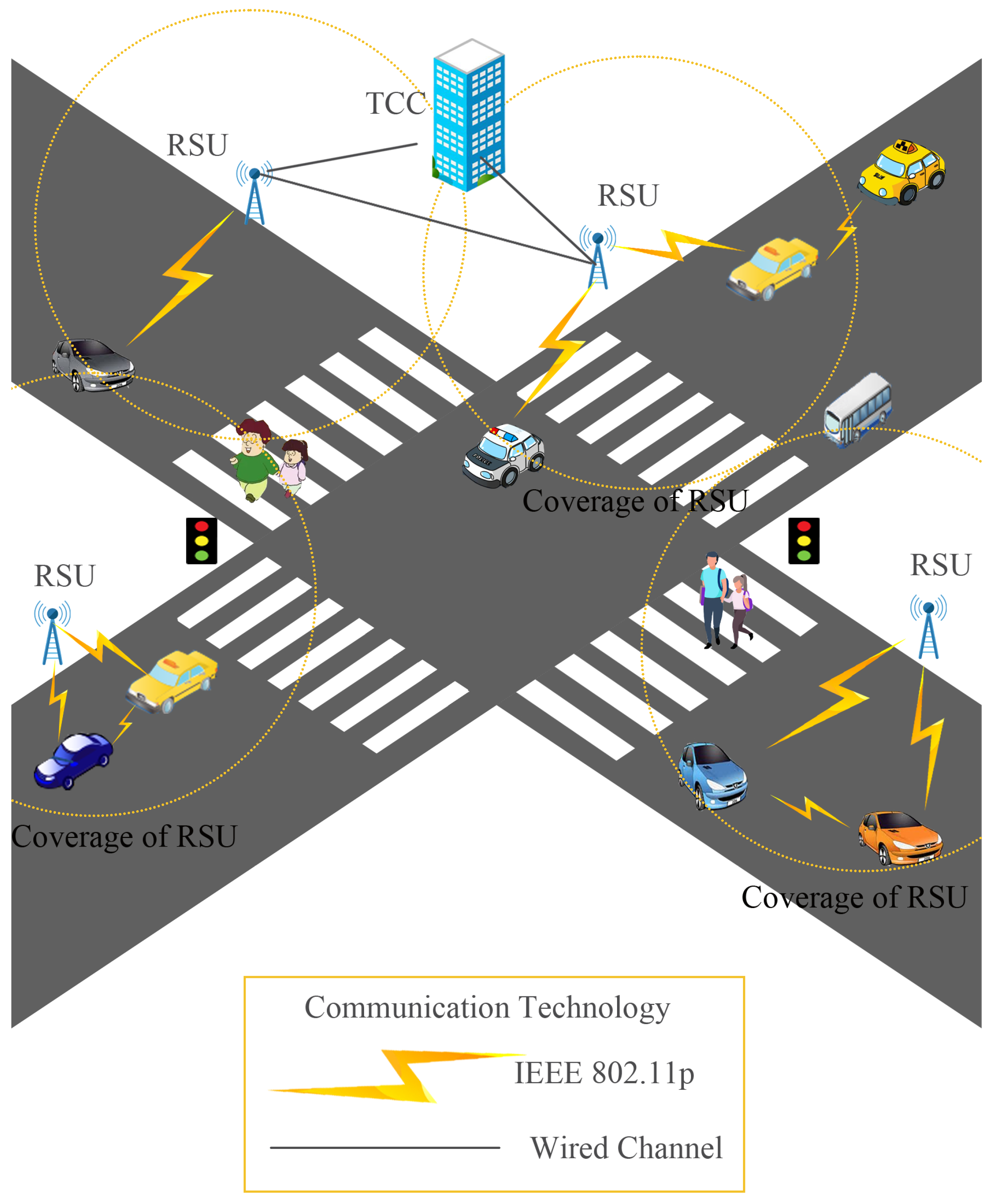
As shown in Figure 1, there are mainly three entities in our URSCS scheme: TCC, RSU, and Vehicle. Due to the huge geographical coverage of VANETs, we assume the existence of multiple TCCs. Communication between vehicles, as well as between vehicles and RSUs, is achieved through open dedicated short-range wireless signals, while communication between RSUs and between TCC and RSUs is performed through wired communication.
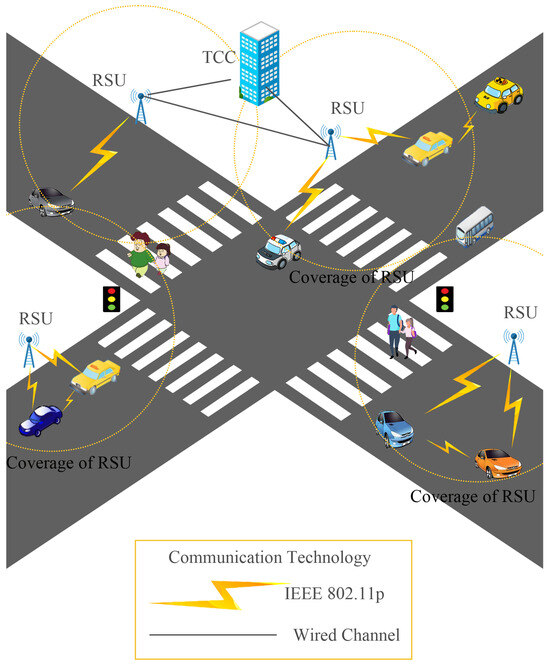
Figure 1.
System architecture.
TCC: It is assumed to be a trusted and secure entity with unlimited computational capability. It is mainly responsible for the initialization of the entire network, network management, registration of vehicles and RSUs, generating partial private keys, pseudonyms, revocation keys for vehicles, and it can track and revoke malicious vehicles.
RSU: Installed on both sides of various roads, it is a semi-honest entity, meaning it faithfully executes various instructions of the system, but it also tends to be curious and collects various information about the system. Its main responsibilities include collecting, decrypting, forwarding, and verifying the encrypted information of surrounding vehicles, as well as forwarding information from the TCC.
Vehicle: Each vehicle is eligible to be included in the system only after registering with the TCC. Furthermore, each vehicle must be equipped with a tamper-proof device (TPD) and an OBU to securely store and process sensitive data. Vehicles collect real-time traffic data, signciphers the information, and transmit the generated ciphertext to designated entity sets. At the same time, vehicles are always ready to receive instructions from the TCC and RSUs and respond promptly.
Figure 1 illustrates the system architecture within the scope of a single TCC. Communication between vehicles, as well as between vehicles and RSUs, is achieved through open dedicated short-range wireless signals, while communication between RSUs and between TCC and RSUs is performed through wired communication.
4.2. Definition of URSCS
Our URSCS system is mainly composed of the following ten algorithms, and we will introduce their basic definitions one-by-one. For the convenience of reading, the relevant symbols used in our URSCS scheme and their corresponding meanings are summarized in Table 1.

Table 1.
Definition of notations.
: On input security parameter k, the system initialization algorithm, which is run by the TCC, returns the public parameter and the system master secret key .
: On input the real identity of the registration vehicle, the vehicle registration algorithm, which is run by the TCC, computes the revocation secret key , identification secret key , and identification public key for the registration vehicle.
: On input the real identity of the registration RSU, the RSU registration algorithm, which is run by the TCC, generates the identification secret key and identification public key for the registration RSU.
: On input the real identity of the vehicle, the vehicle’s key generation algorithm, which is run by the vehicles, generates a set of corresponding key pairs .
: On input the system master secret key , the real identity and a set corresponding public keys , the vehicle’s pseudonyms and partial keys generation algorithm, which is run by the TCC, generates a set of corresponding pseudonyms and a set of corresponding partial private keys .
: On input the number of all legal vehicles in the current TCC domain and the corresponding revocation keys for each legal vehicle , the revocation key generation algorithm, which is run by the TCC, computes the revocation master key b, the corresponding master revocation public key .
: On input the message m, the pseudonym of the sender , the sender’s keys: , and a set of receivers consisting of vehicles and RSUs , the multi-receiver signcryption algorithm, which is run by the RSUs or vehicles, generates a ciphertext .
: On input a ciphertext , the multi-receiver designcryption algorithm, which is run by the RSUs or vehicles, outputs a message .
: On input the message m, the pseudonym of the sender , the sender’s keys: , the revocation key of the sender , and the identity public key of the sender , the single-receiver signcryption algorithm, which is run by vehicles, generates a ciphertext .
: On input the ciphertext , the single-receiver designcryption algorithm, which is run by the RSUs or vehicles, outputs a message .
4.3. Security and Privacy Goals
In this section, we elaborate on the critical security and privacy goals that must be achieved to ensure the safe operation of VANETs. These goals are paramount as they directly impact the trustworthiness of VANETs.
Authentication: Ensuring that all communication participants, including vehicles and RSU, are legitimate. Specifically, receivers (including both vehicles and RSUs) must be able to validate that the sending entities (vehicles) are genuine and not impersonating other legitimate nodes.
Data Confidentiality: In the VANET, sensitive data should be transmitted exclusively in encrypted (ciphertext) form over open channels to minimize the risk of information disclosure. Only authorized recipients with the corresponding decryption key can access and view the original data, thereby ensuring confidentiality and preventing eavesdroppers from deciphering the content of intercepted messages.
Data Integrity: To guarantee the correctness and dependability of information transmitted across V2I and V2V in the VANETs, receivers (including both vehicles and RSUs) must be able to validate that the data have not been maliciously tampered with or altered in any way during transmission. This ensures that the data received is identical to the data sent, thereby maintaining data integrity.
Anonymity: Vehicles employ pseudonyms for message transmission, leveraging a secure anonymity system that safeguards against linking or identifying the actual cars or drivers behind the data. This approach ensures that, apart from the TCC, no other party can infer the real identities of vehicles based solely on their pseudonyms.
Unlinkability: In VANETs, the unlinkability ensures that there is no discernible linkage between multiple signcrypted messages transmitted by the same vehicle. This mechanism effectively obscures the connection between messages, preventing any entity from distinguishing or inferring whether two captured messages originate from the same sender. As a result, privacy is significantly enhanced, as the identity and actions of individual vehicles remain unlinkable within the network.
Traceability: In the case of a dispute arising or the detection of malicious activity, exclusive access to trace the actual identity of vehicles engaged in such behavior, based on their pseudonyms, is granted solely to the TCC.
Revocability: Upon detection of malicious behavior, TCC has the authority to revoke the access of offending vehicles from the system, effectively disabling their ability to transmit any further valid information.
Resistance to Various Attacks: Our URSCS scheme must exhibit resilience against a broad spectrum of known attack vectors, encompassing impersonation attacks, replay attacks, ephemeral secret leakage attacks, man-in-the-middle attacks, and other potential threats that pose risks to the system’s integrity and confidentiality.
4.4. Security Model
According to the authors of [14], in certificateless signcryption schemes, there are two types of attackers. The attacker can replace a user’s public key but cannot obtain the system’s master secret key. The attacker possesses the system’s master secret key but cannot replace a user’s public key. In both cases, the signcryption scheme should achieve indistinguishability under adaptive chosen ciphertext attacks (IND-CCA2) and existential unforgeability against chosen message attacks (EU-CMA). For readability, we denote as attacker, where attacks confidentiality, and attacks unforgeability; we denote as attacker, where attacks the confidentiality, and attacks unforgeability.
4.4.1. Definition 1—Confidentiality (IND-CCA2-Secure)
If any PPT attackers and cannot win with a non-negligible advantage in the subsequent two games, Game I and Game , then a URSCS scheme is IND-CCA2-Secure.
Game I: This game is played between an adversary and a challenger . The specific process is as follows.
Initialization: Challenger executes the initialization function , obtains the system parameters and the system master secret key , sends the to adversary , and secretly retains the .
Phase 1: selects a vehicle with the real identity as the sender and chooses a set of receivers with identification public key .
sends the selected and to opponent , then submits some hash queries to challenger .
submits some oracle queries, and responds with relevant inquiry results, but these results cannot contain information related to the sender’s private key and .
Challenge: selects two messages of equal length and submits them to . Then, randomly chooses a number and performs the function. Finally, sends the signcryption ciphertext to .
Phase 2: After obtaining the signcryption ciphertext , submits another set of oracle queries, excluding .
Guess: outputs a guessed value . If , then wins the game.
Probability Advantage: The probability advantage of can be defined as: .
Game : This game is played between the adversary and . The specific process is as follows.
Initialization: executes the initialization function , obtains the system parameters and the system master private key , sends the them to adversary .
The intermediate process is similar to Game I, but is not allowed to submit an oracle query to the regarding the replacement of public keys.
Guess: outputs a guessed value . If , then wins the game.
Probability Advantage: The probability advantage of can be defined as: .
4.4.2. Definition 2—Unforgeability (EUF-CMA-Secure)
If any PPT attackers and cannot win with a non-negligible advantage in the subsequent two games, Game and Game , then a URSCS scheme is EUF-CMA-Secure.
Game : This game is played between the adversary and . The specific process is as follows.
Initialization: Initialization is similar to Game I.
Inquiry: submits oracle queries, and returns relevant results.
Forgery: outputs a forged ciphertext with and . If the forged ciphertext can be decrypted correctly by any recipient, wins the game.
Probability Advantage: The probability advantage of can be defined as: .
Game : This game is played between the adversary and . The specific process is as follows.
Initialization: Initialization is similar to Game .
Inquiry: submits oracle queries, and returns relevant results.
Forgery: outputs a forged ciphertext with and . If the forged ciphertext can be decrypted correctly by any recipient, wins the game.
Probability Advantage: The probability advantage of can be defined as:
.
5. The Proposed URSCS Scheme
5.1. Basic Algorithms
This section introduces the implementation details of basic algorithms one-by-one, which will be used to construct our URSCS scheme in Section 5.2.
(1) Given a security parameter k, the TCC generates an elliptic curve G with a generator P and order q. It chooses a random element as the system’s master private key and generates the corresponding master public key . Then, it generates six cryptographic hash functions: , , , , , and , where represents the length of the real ID and is determined by security parameter, is the length of the string representation of a point on the elliptic curve, and represents the length of a single message and is determined by security parameter. Then, TCC obtains the system’s master secret key and the common parameters .
(2) TCC chooses a random element as the identification secret key of RSU and generates the corresponding identification public key .
(3) When a vehicle with real identity requests registration, TCC first generates a revocation key for the vehicle as follows: TCC maintains a pool of prime numbers , each of which is unique, and when a vehicle needs to be assigned a revocation key, one is taken from the and assigned to it. Then, the real identity of the vehicle and its corresponding revocation key are saved to the association table of TCC in the form of , where the value indicates that the current vehicle is legal. This mechanism allows TCC to quickly retrieve the revocation key of any vehicle when necessary, while maintaining a record of the vehicle’s legitimacy status. When a vehicle is judged as malicious, its corresponding entity will be changed to , and the associated revocation key is sent to the revocation pool with the form , where indicates the timestamp of revocation. When a vehicle needs to be allocated a revocation key, but the prime numbers in have been exhausted, it is necessary to obtain a prime number from , and the prime number needs to be checked to see if its revocation time exceeds threshold . If the revocation time has exceeded , it can be reused; otherwise, the process will continue to wait. Since the survival time of each pseudonym, , is less than , if a malicious vehicle’s revocation key has been revoked for longer than , it means that the pseudonyms generated by the malicious vehicle before it was revoked are no longer available. This mechanism ensures that malicious vehicles cannot continue sending messages after their revocation keys have been reassigned to new vehicles. For more details, one can refer to Section 6.1.7. Subsequently, TCC selects a random number as the identification secret key and generates the corresponding identification public key .
(4) The vehicle with real identity selects n random numbers as private keys, generates the corresponding n public keys , keeps in secret, and publishes .
(5) The vehicle transmits its own real identity and a set of public keys to TCC, and TCC can verify whether the vehicle is legal by checking the association table . If the value in the association table corresponding to the and is , then TCC performs the following procedure, otherwise TCC returns ⊥.
- TCC generates a set of pseudonyms containing n elements associated with , each of which is structured as , where is the timestamp used to control the lifetime of , , , and .
- TCC randomly chooses n random elements , obtains n points on the corresponding elliptic curve, and then computes and , for , hence, TCC obtains a set of partial public-private key pairs .
(6) The here represents the number of existing legal vehicles in the TCC domain, and are the corresponding revocation secret keys for each legal vehicle. When there are vehicles joining or exiting, the value would be automatically changed accordingly. TCC first selects a random prime number as the master revocation secret key and then removes b from the . When the system needs to be allocated a master revocation secret key, but the prime numbers in have been exhausted, the handling mechanism employed is identical to the method. TCC generates and utilizes CRT to construct other parts of the master revocation public key, calculating . TCC computes the multiplicative inverse of modulo , satisfying . Since are different prime numbers, and are coprime, which implies that the multiplicative inverse of modulo exists. Next, TCC calculates and . Finally, TCC secretly keeps the master revocation secret key b and makes public.
(7) Assume that vehicle needs to send message m to a group of entities . Vehicle selects a set of unused , and performs the following calculations, removing these parameters from the vehicle parameter pool. The vehicle calculates the revocation master key , which is equivalent to the master revocation secret key b that is selected by TCC. The equivalence can be validated as follows.
In Equation (2), the values of the intermediate variables are set at the TCC side as follows: , , , . Obviously, the master revocation secret key b calculated by the sending vehicle is the same as b set by the TCC.
Then, vehicle selects a random number , and calculates . For each identity public key , vehicle calculates and . Then, it randomly selects a session key , constructs a polynomial , and calculates the ciphertext . The vehicle then selects a timestamp t and calculates , , , . The vehicle can obtain the signcrypted information , which is broadcast to all entities, including many vehicles or RSUs.
(8) Assuming that vehicle receives the signcrypted message , it first checks the validity of the timestamp t. If the timestamp has expired, it returns ⊥, rejecting the signcrypt information. If the timestamp is valid, the vehicle obtains the timestamp from , and then verifies whether the existence time of the exceeds threshold . If the existence time exceeds , it returns ⊥; otherwise, it continues to perform the following operations. Note that should be less than to prevent malicious vehicles from continuing to send messages after their revocation keys are reassigned to the new vehicles.
Vehicle uses the master revocation public key B, its own identity private key , the identity public key , R and from the signcrypted message to calculate , , and constructs a polynomial according to the received elements . Then vehicle calculates the session key , , and computes , , , . Vehicle verifies if Equation (3) holds.
If the equality in (3) holds, it accepts the message m; otherwise, it rejects the message. If the target receiving vehicle is the same as the current receiving vehicle , the calculated values will be the same as those of the sending vehicle. The correctness of Equation (3) can be validated as follows.
In Equation (4), the intermediate variables were set at the sending side as follows: , , , , , , and the values , , and on the sending side are: , , .
(9) Assume that vehicle needs to send message m to a specific vehicle or RSU. The vehicle calculates the revocation master key , which would be equivalent to the master revocation secret key b that is selected by TCC. Then, it selects a random number and calculates . Next, vehicle selects a set of unused parameters , performs the following steps, and removes these parameters from the vehicle parameter pool. Using the identity public key of the receiving vehicle or RSU, it calculates , and computes the ciphertext . The vehicle then selects a timestamp t and calculates , , , . The vehicle can obtain the signcryption information , which is broadcast to all entities.
(10) Assuming that vehicle receives the signcrypted message , it first checks the validity of the timestamp t. If the timestamp has expired, it returns ⊥, rejecting the signcrypt information. If the timestamp is valid, the vehicle obtains the timestamp from , and then verifies whether the existence time of the exceeds threshold . If the existence time exceeds , it returns ⊥; otherwise, it continues to perform the following steps. The vehicle uses the master revocation public key B, its own identification private key , the identification public key , the random point R and from the signcrypted message to calculate , , and computes , , , . Vehicle verifies if Equation (5) holds.
If true, it accepts the message m; otherwise, it rejects the message. The validity of Equation (5) can be proved as in Equation (4).
5.2. URSCS Construction
This section utilizes the algorithms detailed in the previous section to form our URSCS scheme. It consists of five stages, namely, initialization, registration, signcryption, designcryption, as well as trace and revocation.
5.2.1. Initialization
First, TCC executes the system initialization algorithm , obtaining the system master key and system public parameters . Next, it publicly discloses and secretly holds the system master key .
5.2.2. Registration
The vehicle sends its real identity to TCC to request registration. TCC executes the algorithm, generates the identification secret key , the identification public key , and the revocation key . TCC sends , , and to the registering vehicle through a secure channel. The vehicle secretly stores and within the tamper-proof device of the OBU and publishes the identification public key . cannot be disclosed, so the is used instead of the as the long-term identity and made public to all entities.
The RSU sends its to TCC to request registration. TCC executes the algorithm, generates the identification secret key and the identification public key . TCC then sends and to the registering RSU through a secure channel. The RSU secretly keeps the and publishes the . In the multi-receiver signcryption scenario, the receivers can be either vehicles or RSUs. To unify the identifiers of the receivers, the identification public keys of the RSUs are used to replace their real IDs.
The registered vehicle executes the vehicle key generation algorithm , generating a set of public-private key pairs: , . The vehicle sends and to the TCC to request generation of pseudonyms and partial keys. Upon receiving this request, TCC executes the algorithm, verifies the legitimacy of the requesting vehicle, then generates a set of pseudonyms and a set of partial keys , and sends these pseudonyms and partial keys to the requesting vehicle through a secure channel. And then, to facilitate information retrieval, the vehicle correctly matches each pseudonym with its corresponding public-private key pair and partial key pair, and stores them in a secure pool as . To ensure unlinkability, the vehicle consumes one of these tuples each time it sends a message.
TCC executes the revocation key generation algorithm , thereby obtaining the current system’s master revocation secret key b, master revocation public key B, and the auxiliary value . Finally, TCC secretly keeps the master revocation secret key b and publishes .
5.2.3. Signcryption
Vehicles can signcrypt messages for multiple recipients or a single recipient.
In the multiple recipients scenario, each time a vehicle sends a message, it first selects a pseudonym and a key tuple from the secure pool, and removes this pseudonym and its related key pair from the pool. When the pseudonyms and key tuples in the pool are about to be depleted, the vehicle re-executes the algorithm and requests TCC to execute the algorithm to replenish the pool. The vehicle selects specific recipients , and executes the multi-recipient signcryption algorithm to obtain the signcrypted information , and broadcasts it to multiple recipients.
In the single-recipient scenario, each time a vehicle sends a message, it first selects a pseudonym and a key tuple from the secure pool. The vehicle selects a specific recipient and executes the single-recipient signcryption algorithm , obtains and broadcasts the signcrypted information . The management of pseudonyms and keys in the secure pool is the same as in the multi-recipient signcryption scenario.
5.2.4. Designcryption
The designcryption stage also includes multi-recipient designcryption and single-recipient designcryption.
In multi-recipient designcryption, only the recipient specified by the sender can obtain the correct session key and successfully designcryption the message if calculated by the recipient matches calculated by the sender.
Single-recipient designcryption shares the same principles as in multi-recipient designcryption and is omitted here.
5.2.5. Trace and Revocation
If an RSU or vehicle detects suspicious behavior from a malicious vehicle, it can submit the corresponding pseudonym to TCC. Then, TCC calculates using the system master secret key and the pseudonym to obtain of the malicious vehicle.
Then, TCC receives the revocation secret key from the association pair of the association table, removes the of the malicious vehicle from the revocation key set , and adds it to as , then changes the association pair to . TCC then randomly selects a new master revocation secret key and calculates . By employing CRT, TCC re-executes the procedure of generating the remaining part of the master revocation public key, the specific implementation procedure can be found in the algorithm described in Section 5.1. Note that the revocation secret key of the malicious vehicle has been deleted, so , where represents the number of legitimate vehicle. Finally, TCC secretly keeps the new master revocation secret key and publishes the new master revocation public key . The vehicle whose revocation secret key has been deleted cannot obtain the latest master revocation secret key using mod , but other normal vehicles can.
6. Security Analysis
In this section, we provide the informal security analysis, and formal security proof of the proposed URSCS scheme.
6.1. Informal Security Analysis
We show that the proposed scheme URSCS meets the security and privacy goals proposed in Section 4.3.
6.1.1. Authentication
In the proposed URSCS scheme, only the legitimate vehicle can obtain revocation secret key through registration; furthermore, only the legitimate vehicle can obtain the master revocation secret key b using and send messages. From another perspective, only legitimate vehicles can obtain their own secret keys and compute using their own secret keys, and receivers can verify the validity of using the sender’s public key, the system’s master public key, and the system’s master revocation public key. The formal security analysis, Theorems 3 and 4, also demonstrate the unforgeability of signatures under the CDHP. Therefore, our URSCS scheme achieves vehicle authentication, ensuring that senders are legitimate vehicles in the system.
6.1.2. Data Confidentiality
The confidentiality of message m is protected by the session key . The sender encrypts m as , and only the legitimate recipient can compute the session key , and then obtain the decrypted message . Additionally, formal security proofs of Theorems 1 and 2 would demonstrate that if the CDHP is hard to solve, then malicious users cannot obtain the real data, ensuring the confidentiality of the data.
6.1.3. Data Integrity
As shown in Section 5.1, the recipient needs to calculate the hash values , , and before receiving the message in designcryption process. Since , , and are calculated in the same manner at both the sender’s and receiver’s ends, for example, the calculation method for at both ends is . The message m is one of the inputs to the hash function . Suppose the message m is tampered with during transmission, the hash values , , calculated at the sender’s end will be different from those calculated by the recipient, and the verification process will fail. Therefore, our scheme ensures data integrity.
6.1.4. Anonymity
In our URSCS scheme, a pseudonym mechanism is employed to achieve sender anonymity. To extract RID, an attacker needs to calculate ; therefore, the attacker must obtain or solve the ECDLP problem. Since only TCC knows the system’s master secret key , and the ECDLP is hard to solve, the adversary cannot infer the real from . Thus, our scheme achieves sender anonymity.
On the other hand, the identification public key is used to replace real for message reception. Other than the sender, no other entity can infer the message recipient from intercepted ciphertext messages. Therefore, our URSCS achieves receiver anonymity.
6.1.5. Unlinkability
Our URSCS scheme achieves anonymity by hiding the under . In generating pseudonyms, each pseudonym is calculated using a random number x. When a vehicle performs the signcryption function, the random numbers are used; thus, no adversary can link any vehicle through pseudonyms or ciphertexts from the same sender. Furthermore, even if the malicious vehicles obtain the public keys from the ciphertexts, they cannot link to the vehicle through the public keys because the vehicle needs to fetch a new pseudonym and the corresponding public-private key from the security pool before each signcryption operation. Therefore, our URSCS achieves unlinkability.
6.1.6. Traceability
In the event of a dispute or the discovery of malicious behavior, TCC can obtain the true identity of the vehicle through the equation , where is the real identity of the malicious vehicle and is the pseudonym of the malicious vehicle. Thus, our URSCS system can achieve tracking functionality while maintaining the anonymity of vehicles.
6.1.7. Revocability
After tracking the malicious vehicle , TCC removes the revocation key of from the revocation secret key set and adds it to . Then, TCC randomly selects a new master revocation secret key and calculates . Next, TCC uses the CRT to construct the other part of the master revocation public key, and calculates ; thus, the revocation secret key of has been removed. Then, TCC calculates , finds the multiplicative inverse of , and computes , . Finally, the TCC retains the master revocation secret key secretly and publishes the master revocation public key . can no longer obtain the latest master revocation secret key through ; thus, will be unable to send valid messages again.
In our URSCS scheme, if is reallocated to a new vehicle, it implies that the existing time of in the revocation pool has exceeded threshold , as the threshold is less than the threshold ; therefore, the pseudonyms of cannot be used, and this method is used to prevent malicious vehicles from continuing to send messages after their revocation keys are reassigned to the new vehicles.
6.1.8. Resistance to Impersonation Attacks
In our URSCS scheme, the malicious vehicle with real identity can intercept the master revocation public key B, and the ciphertext , but it cannot obtain the private key of vehicle with the pseudonym . If the malicious vehicle wants to impersonate vehicle , it may attempt to use its key pair and the pseudonym of a legitimate vehicle to send information, since (which contains the pseudonym of the malicious vehicle). However, the malicious vehicle passed to the recipients, the receivers need to compute , and this will not satisfy the verification Equation (3). Therefore, our URSCS scheme can resist impersonation attacks.
6.1.9. Resistance to Replay Attacks
In our scheme, each transmitted ciphertext contains a timestamp t. After receiving these messages, the receiver can determine if a replay attack has occurred by checking their timestamps. Therefore, our scheme can resist replay attacks.
6.1.10. Resistance to Ephemeral Secret Leakage Attacks
In our scheme, the session key is randomly chosen by the sender for each transmission. Due to the randomness of the session key and the lack of correlation between the session keys chosen for different transmissions, even if a specific session key is disclosed, it does not threaten the already created session keys or those to be created. Therefore, our scheme ensures the freshness of the session keys, can resist ephemeral secret leakage attacks, and also possesses forward and backward security.
6.1.11. Resistance to Man-in-the-Middle Attacks
Since our scheme achieves authentication and integrity guarantee, it can resist man-in-the-middle attacks.
In the same manner, we have analyzed the security and privacy goals achieved by schemes [8,13,17,18]. Table 2 elaborates on the comparison of these properties between our USS-MR scheme and similar schemes, namely [8,13,17,18]. The identifiers Resis-Imper, Resis-Replay, Resis-ESL, and Resis-Man represent resistance to impersonation attacks, resistance to replay attacks, resistance to ephemeral secret leakage attacks, and resistance to man-in-the-middle attacks, respectively. As shown in Table 2, only our URSCS scheme and scheme [18] can meet all security and privacy goals.

Table 2.
Comparison of security properties.
6.2. Formal Security Proof
6.2.1. Confidentiality
Our URSCS scheme achieves confidentiality as shown in Theorems 1 and 2.
Theorem 1.
Assume that can win Game I with non-negligible advantage δ, then can solve CDHP with non-negligible advantage .
Proof of Theorem 1.
Assume that challenger obtains an instance of the CDHP and attempts to compute . The interaction between and is as follows.
Initialization: executes the initialization algorithm to generate system parameters , where , and sends the system parameters to .
Phase 1: selects a sender with real identity and u receivers with real identities for . executes the algorithm or where to obtain . publishes the receivers’ identification public keys and keeps the private keys of the receivers privately.
executes the algorithm to obtain and executes the algorithm to obtain . keeps five lists , , , , which are initially empty, and . Then, adaptively conducts a polynomially bounded number of queries as follows.
receives . If there exists a corresponding tuple in , sends to ; otherwise, selects and sends to . Also, the tuple is inserted into the list .
receives . If there exists a corresponding tuple in , sends to ; otherwise, selects and sends to . Also, the tuple is inserted into the list .
receives . If there exists a corresponding tuple in , sends to ; otherwise, selects and sends to . Also, the tuple is inserted into the list .
receives . If there exists a corresponding tuple in , sends to ; otherwise, selects and sends to . Also, the tuple is inserted into the list .
receives . If there exists a corresponding tuple in , sends to ; otherwise, selects and sends to . Also, the tuple is inserted into the list .
keeps three empty lists , , and . Next, responds to hash oracles queries from as follows.
revokeKeyExtractQuery: Upon receiving , if , terminates the game; otherwise, checks if there exists a corresponding tuple in . If true, sends to ; otherwise, randomly selects a prime number and sends it to . Also, inserts the tuple into .
secretValueExtractQuery: Upon receiving , if , terminates the game; otherwise, checks if there exists a corresponding tuple in . If true, sends to ; otherwise, randomly selects a , calculates , and sends to . Also, inserts the tuple into .
publicValueExtractQuery: Upon receiving , if , terminates the game; otherwise, checks if there exists a corresponding tuple in . If such a tuple exists, sends to ; otherwise, randomly selects a , calculates , and sends to . Also, inserts the tuple into .
partialPrivateKeyQuery: Upon receiving , if , terminates the game; otherwise, checks if there exists a corresponding tuple in . If such a tuple exists, sends to ; otherwise, randomly selects and computes , randomly selects , then executes to obtain , and sends to . Also, inserts the tuple into .
replacePublicKeyQuery: randomly selects within an appropriate range to replace the complete public key of identity . If , then stops the game; otherwise, updates the list with , and updates the list with .
mulSignCryptQuery: Upon receiving , and m, makes the following response:
(a) If , challenger makes , , , and to obtain . Next, runs to get , then sends it to .
(b) Otherwise, randomly chooses and . Next, calculates , , , constructs a polynomial , and calculates the ciphertext , and . Then, it updates , , and . Finally, sends to .
mulDeSignCryptQuery: Upon receiving to , obtains , and from , , , and . And calculates , and constructs a polynomial using the received polynomial coefficients: . Then calculates the session key , . Finally, sends to .
Challenge: After the above queries, generates , , and , then sends them to , where and are two messages of different content and equal length. Next, selects . randomly chooses and . Next, calculates , , , constructs a polynomial , and calculates the ciphertext , and . Then, it stores them in , , and , respectively. Finally, sends to .
Phase 2: can execute the same series of above queries except for .
Guess: guesses a bit and wins the game if .
If wants to succeed, it must obtain correct keys and the corresponding . Then, outputs the solution of CDHP: . Thus, can solve CDHP with an advantage in time . □
Theorem 2.
Assume that can win Game I with non-negligible advantage δ, then can solve CDHP with non-negligible advantage .
Proof of Theorem 2.
Suppose challenger obtains an instance of the CDHP problem and attempts to compute . and can perform the same interactions as Theorem 1. In this game knows , but it cannot initiate .
Guess: guesses a bit and wins the game if .
If wants to succeed, it must obtain correct keys and the corresponding . Then, outputs the solution of CDHP: . Thus, can solve CDHP with an advantage in time . □
6.2.2. Unforgeability
Our scheme can achieve unforgeability, which is shown in Theorems 3 and 4.
Theorem 3.
Assume that can win Game with non-negligible advantage δ, then can solve CDHP with non-negligible advantage .
Proof of Theorem 3.
Suppose challenger obtains a CDHP instance and attempts to compute . and can perform the same interactions as stage 1 and stage 2 in Theorem 1.
Forgery: outputs a forgery with . And cannot query the secret key on . If the equation holds, will succeed. Finally, receives the forged signature .
After the relevant queries are executed, the corresponding public key with the same identity will be changed. Therefore, can forge a signature with an advantage in time . □
Theorem 4.
Assume that can win Game with non-negligible advantage δ, then can solve CDHP with non-negligible advantage .
Proof of Theorem 4.
Assume that challenger obtains a CDHP instance and attempts to compute . and can perform the same interactions as stage 1 and stage 2 in Theorem 2.
Forgery: outputs a forgery with . And cannot query the secret key on . If the equation holds, will succeed. Finally, receives the forged signature .
After the relevant queries are executed, the corresponding public key with the same identity will be changed. Therefore, can forge a signature with an advantage in time . □
7. Performance Evaluation
In this section, we evaluate the performance of our URSCS scheme, and then compare computation overheads and communication overheads of our URSCS with those of the state-of-the-art provably secure signcryption schemes, specifically Yang et al., 2022 [8], Yang et al., 2022 [13], Deng 2020, [17], Liang et al., 2023 [18]. Since the registration phase is a one-time process in the scenario of VANETs, the computation and communication overheads can be neglected; therefore, we focus on the signcryption phase (the signcryption of messages during one-to-many communication) and the unsigncryption phase.
7.1. Computation Overhead
To calculate the computational overhead, we conducted simulations using a pairing-based cryptography library and a multi-precision integer and rational arithmetic C/C++ library. The execution times for common cryptographic operations were obtained by averaging multiple execution times with different input values. We denote the execution time of a modular exponentiation operation as , the execution time of a scale multiplication on ECC as , the execution time of a point addition on ECC as , the execution time of a bilinear mapping operation as , the execution time of a scale multiplication on bilinear pairing as , and the execution time of a hash operation as . Additionally, the execution times of those operations on a desktop equipped with an 11th Gen Intel(R) Core(TM) i7-11800H processor operating at 2.30 GHz and 16.0 GB of RAM are summarized in Table 3. The execution times of other operations, such as hashing, are so small that they can be neglected compared to the operations mentioned above; therefore, their times are not considered in our experiments.

Table 3.
Execution time of basic operations.
In our URSCS scheme, the signcryption phase requires scalar multiplications operations on ECC, hash operations, where u represents the number of receivers, so the signcryption cost of our scheme is . Similarly, the unsigncryption phase needs point addition operations on ECC, scalar multiplications operations on ECC, hash operations. Thus, the unsigncryption cost of our scheme is , and the total computation cost of our scheme can be expressed as .
In scheme Yang et al., 2022 [8], the signcryption needs scalar multiplication operations on ECC, point addition operations on ECC, and hash operations, so the signcryption cost is . Similarly, the unsigncryption needs scalar multiplication operations on ECC, point addition operations on ECC, hash operations, and 5 bilinear pairing operations, so the unsigncryption cost is , and the total computation cost of scheme Yang et al., 2022 [8] is .
In scheme Yang et al., 2022 [13], the signcryption phase needs scalar multiplication operations on ECC, u point addition operations on ECC, u modular exponentiation operations, and hash operations, so the signcryption cost is . Similarly, the unsigncryption phase needs scalar multiplication operations on ECC, point addition operations on ECC, hash operations, and u bilinear pairing operations, so the unsigncryption cost is . Then, the total computation cost of scheme Yang et al., 2022 [13] is .
In scheme Deng 2020, [17], the signcryption phase needs scalar multiplication operations on ECC and u bilinear pairing operations, so the signcryption cost is . Similarly, the unsigncryption phase needs one bilinear pairing operation and one modular exponentiation operation, so the unsigncryption cost is . Then, the total computation cost of scheme Deng 2020, [17] is .
In scheme Liang et al., 2023 [18], the signcryption phase needs scalar multiplication operations on ECC, hash operations. So the signcryption cost is . Similarly, the unsigncryption phase needs scalar multiplication operations on ECC, point addition operations on ECC, and hash operations, so the unsigncryption cost is . Then, the total computation cost of schemeLiang et al., 2023 [18] is .
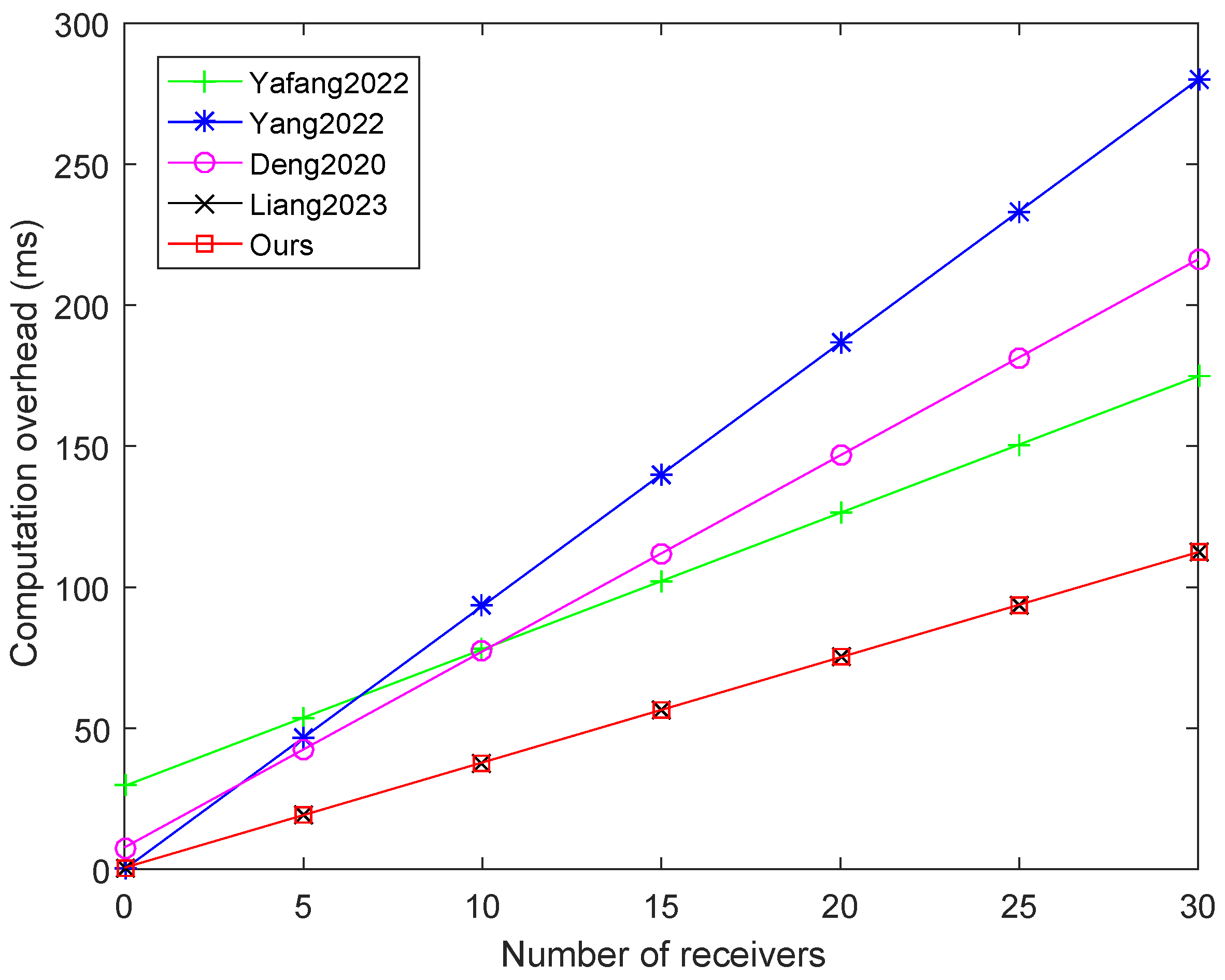
Also, Table 4 shows the total computation cost of each algorithm, respectively. The experimental comparison is depicted in Figure 2, where the number of receivers has increased from 0 to 30. This figure evidently shows that our scheme has apparent advantages over schemes Yang et al., 2022 [8], Yang et al., 2022 [13], Deng 2020, [17]. The efficiency of scheme Liang et al., 2023 [18] is similar to that of our scheme, but its receivers are limited to RSUs, while the receivers of our scheme can be both RSUs and vehicles, with greater flexibility.

Table 4.
Comparison of computation overhead.
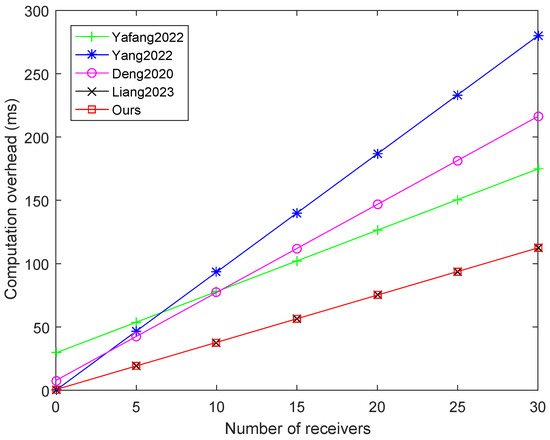
Figure 2.
Comparison of computation overhead for different number of receivers [8,13,17,18].
7.2. Communication Overhead
In this section, given a secure length of 128 bits [13], we compared the communication overhead of our URSCS scheme with those of the state-of-the-art provably secure signcryption schemes, specifically Yang et al., 2022 [8], Yang et al., 2022 [13], Deng 2020, [17], Liang et al., 2023 [18]. In schemes based on bilinear pairing, the size of the element in is 128 bytes, namely bytes; while in schemes based on ECC, the size of the elements in G is 64 bytes, namely bytes. The size of the elements in , real identity, message, the timestamp are 32 bytes, 32 bytes, 32 bytes, 4 bytes, respectively, namely bytes, bytes, bytes, bytes.
In our URSCS scheme, during the processes of signcryption and unsigncryption, the information that needs to be transmitted is , where the size of pseudonym is bytes, the size of ciphertext is bytes, and u indicates the number of receivers. So the total communication overhead is = bytes.
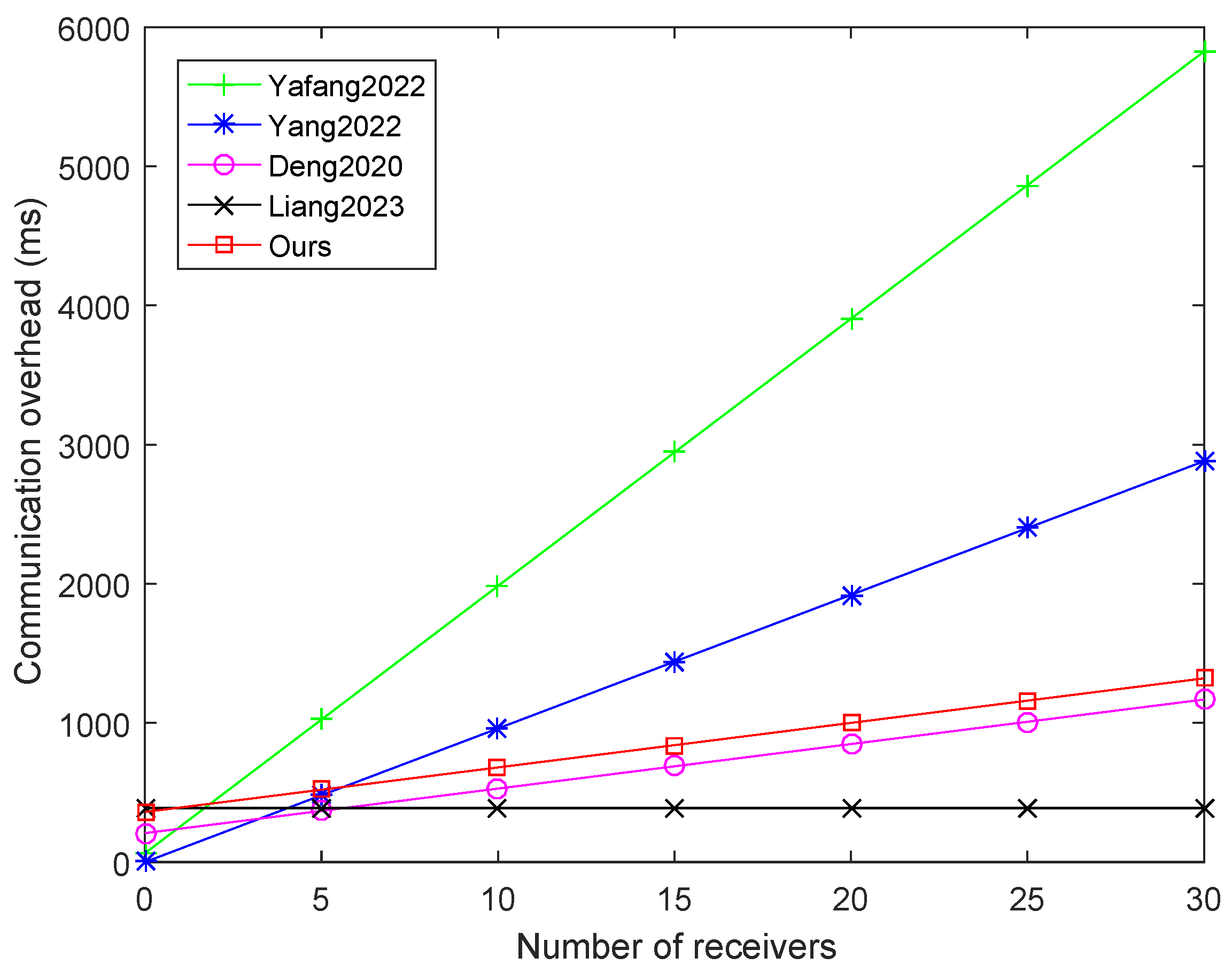
We utilized the same method to compute the communication overheads of the schemes [8,13,17,18], where the results are illustrated in Figure 3 and Table 5. Compared to other schemes, our approach has lower communication overhead. Although the communication overhead of the scheme Liang et al., 2023 [18] is lower than that of our scheme, but it did not consider the issue of elements needing to be coprime in the CRT, and it also has the limitation that messages can only be sent to RSUs. Similarly, although scheme Deng 2020, [17] has lower communication overhead, its computational cost is too high, and it lacks tracking and revocation functions.
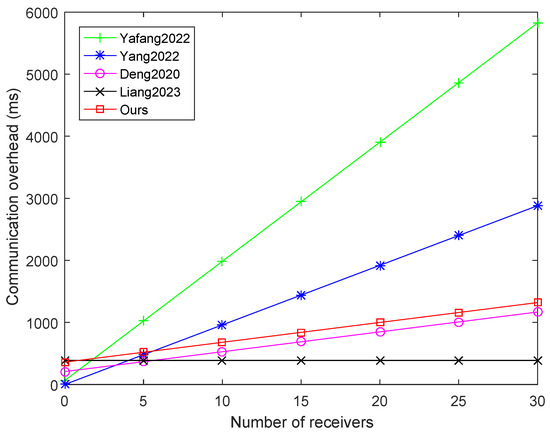
Figure 3.
Comparison of communication overhead for different number of receivers [8,13,17,18].

Table 5.
Comparison of communication overhead.
7.3. Comparison of Revocation Public Key Transmission Overhead
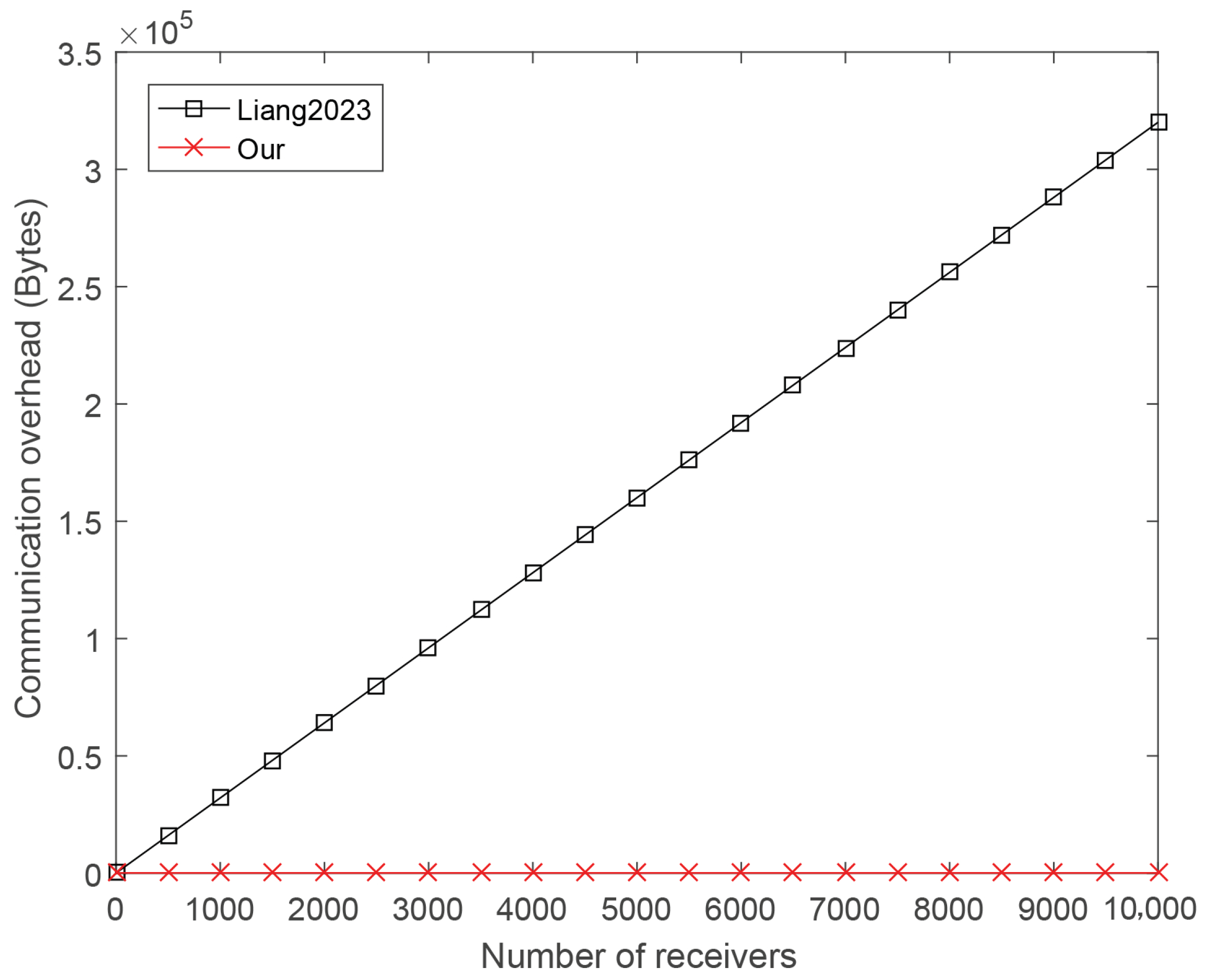
Scheme Liang et al., 2023 [18] is the most outstanding unlinkable multi-recipient scheme with revocation mechanism so far. However, the implementation of its revocation key mechanism requires the construction of a complex polynomial. The number of coefficients of the polynomial is the same as the number of vehicles. The master revocation public key parameters to be transmitted are , where B is a point on the discrete elliptic curve group, and , which are the coefficients of the polynomial. Therefore, the communication overhead for transmitting the master revocation public key parameters is bytes. When there are a large number of vehicles within the domain of a TCC, such as 100,000 vehicles, the master revocation public key parameters generated at one time will include 100,001 numbers. On the other hand, the update of the master revocation public key is relatively frequent. When a vehicle joins the TCC’s domain or a vehicle needs to be revoked, the master revocation secret key and master revocation public key need to be updated again. Thus, the overhead of scheme Liang et al., 2023 [18] in transmitting the master revocation public key is significant.
To reduce the communication overhead of transmitting the revocation public key, we present a new revocation key mechanism based on CRT. The revocation public key parameters to be transmitted are , where B is a point on the discrete elliptic curve group, and . Regardless of the number of vehicles within the TCC domain, the communication overhead for transmitting the master revocation public key parameters is fixed, namely 96 bytes . Thus, our URSCS scheme has an absolute advantage in the transmission overhead of the revocation public key. Figure 4 demonstrates the apparent advantage of our scheme in transmission overhead of transmitting the revocation public key.
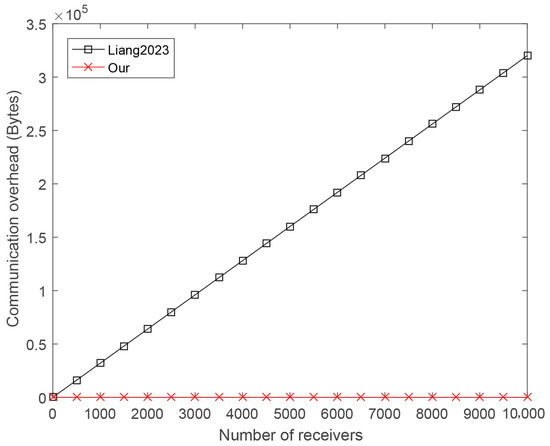
Figure 4.
Comparison of revocation public key transmission overhead [18].
8. Conclusions
Based on the advantages of certificateless and signcryption, we developed a secure multi-receiver unlinkable communication scheme, allowing a sender to send the same signcryption information to multiple receivers, which can be either vehicles or RSUs. Through anonymous transmission and the instant update of key pairs when sending messages, our scheme ensures that malicious attackers cannot trace the sender through multiple messages originating from the same source, thereby achieving the unlinkability of the sender. Moreover, this paper also constructed a revocation key mechanism with low communication cost by utilizing CRT. Furthermore, the comprehensive security analysis demonstrated that our scheme exhibits superior security performance. In comparison with the state-of-the-art schemes, our scheme has low communication overhead and computation overhead. Note that this scheme solely focuses on a secure multi-receiver communication scheme under only one TCC, and the secure communication among various TCCs remains unexplored in this paper, which will be a key focus of our future research.
Author Contributions
Conceptualization, L.L. and Y.W.; methodology, L.L., Y.L. (Yangfan Liang) and D.C.; validation, Y.W. and Y.L. (Yangfan Liang); formal analysis, L.L. and D.C.; Software, X.W.; writing—original draft preparation, L.L. and D.C.; writing—review and editing, L.L., Y.W., X.W. and Y.L. (Yining Liu); visualization, D.C.; project administration, Y.L. (Yining Liu). All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The original data presented in the study are openly available in [Pairing-Based Cryptography Library] at [ https://crypto.stanford.edu/pbc] and [Miracl Library] at [https://github.com/miracl/MIRACL], both accessed on 9 August 2024.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Chowdhury, D.N.; Agarwal, N.; Laha, A.B.; Mukherjee, A. A vehicle-to-vehicle communication system using Iot approach. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; IEEE: New York, NY, USA, 2018; pp. 915–919. [Google Scholar]
- Zhang, J.; Jiang, Y.; Cui, J.; He, D.; Bolodurina, I.; Zhong, H. DBCPA: Dual Blockchain-Assisted Conditional Privacy-Preserving Authentication Framework and Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2024, 23, 1127–1141. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Alazzawi, M.A.; Anbar, M.; Manickam, S.; Al-Ani, A.K. A comprehensive survey on vehicular ad hoc networks (vanets). In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021; IEEE: New York, NY, USA, 2021; pp. 156–160. [Google Scholar]
- Liang, Y.; Liu, Y. Analysis and improvement of an efficient certificateless aggregate signature with conditional privacy preservation in VANETs. IEEE Syst. J. 2022, 17, 664–672. [Google Scholar] [CrossRef]
- Biswas, M.; Das, D.; Banerjee, S.; Mukherjee, A.; AL-Numay, W.; Biswas, U.; Zhang, Y. Blockchain-Enabled Communication Framework for Secure and Trustworthy Internet of Vehicles. Sustainability 2023, 15, 9399. [Google Scholar] [CrossRef]
- Liu, Z.; Wan, L.; Guo, J.; Huang, F.; Feng, X.; Wang, L.; Ma, J. PPRU: A Privacy-Preserving Reputation Updating Scheme for Cloud-Assisted Vehicular Networks. IEEE Trans. Veh. Technol. 2023, 1–16. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Xie, Q.; Tan, X.; He, D.; Tang, W. Blockchain-Based Traffic Accident Handling Protocol without Third-Party for VANETs. IEEE Internet Things J. 2024, 1. [Google Scholar] [CrossRef]
- Yang, Y.; Zhang, L.; Zhao, Y.; Choo, K.K.R.; Zhang, Y. Privacy-Preserving Aggregation-Authentication Scheme for Safety Warning System in Fog-Cloud Based VANET. IEEE Trans. Inf. Forensics Secur. 2022, 17, 317–331. [Google Scholar] [CrossRef]
- Cao, L.; Ge, W. Analysis of Certificateless Signcryption Schemes and Construction of a Secure and Efficient Pairing-free one based on ECC. KSII Trans. Internet Inf. Syst. (TIIS) 2018, 12, 4527–4547. [Google Scholar]
- Li, Y.; Qi, Y.; Lu, L. Secure and efficient V2V communications for heterogeneous vehicle ad hoc networks. In Proceedings of the 2017 International Conference on Networking and Network Applications (NaNA), Kathmandu City, Nepal, 16–19 October 2017; IEEE: New York, NY, USA, 2017; pp. 93–99. [Google Scholar]
- Ali, I.; Lawrence, T.; Omala, A.A.; Li, F. An efficient hybrid signcryption scheme with conditional privacy-preservation for heterogeneous vehicular communication in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 11266–11280. [Google Scholar] [CrossRef]
- Abouelkheir, E.; El-sherbiny, S. Pairing free identity based aggregate signcryption scheme. IET Inf. Secur. 2020, 14, 625–632. [Google Scholar] [CrossRef]
- Yang, Y.; He, D.; Vijayakumar, P.; Gupta, B.B.; Xie, Q. An efficient identity-based aggregate signcryption scheme with blockchain for IoT-enabled maritime transportation system. IEEE Trans. Green Commun. Netw. 2022, 6, 1520–1531. [Google Scholar] [CrossRef]
- Wang, L.; Guan, Z.; Chen, Z.; Hu, M. Multi-receiver signcryption scheme with multiple key generation centers through public channel in edge computing. China Commun. 2022, 19, 177–198. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Liu, C.H.; Song, J. Towards secure and privacy preserving collision avoidance system in 5G fog based Internet of Vehicles. Future Gener. Comput. Syst. 2019, 95, 488–499. [Google Scholar] [CrossRef]
- Ullah, I.; Khan, M.A.; Khan, F.; Jan, M.A.; Srinivasan, R.; Mastorakis, S.; Hussain, S.; Khattak, H. An efficient and secure multimessage and multireceiver signcryption scheme for edge-enabled internet of vehicles. IEEE Internet Things J. 2021, 9, 2688–2697. [Google Scholar] [CrossRef]
- Deng, L. Anonymous certificateless multi-receiver encryption scheme for smart community management systems. Soft Comput. 2020, 24, 281–292. [Google Scholar] [CrossRef]
- Liang, Y.; Yan, H.; Liu, Y. Unlinkable Signcryption Scheme for Multi-Receiver in VANETs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 10138–10154. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, X.; Dai, H.N.; Zhang, X.; Imran, M. A Data Reporting Protocol With Revocable Anonymous Authentication for Edge-Assisted Intelligent Transport Systems. IEEE Trans. Ind. Inform. 2023, 19, 7835–7847. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Li, J.; Lu, H.; Guizani, M. ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 938–948. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Hu, C. Distributed aggregate privacy-preserving authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 18, 516–526. [Google Scholar] [CrossRef]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) significantly less than cost (signature)+ cost (encryption). In Proceedings of the Advances in Cryptology—CRYPTO’97: 17th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Proceedings 17. Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Zhang, A.; Wang, L.; Ye, X.; Lin, X. Light-weight and robust security-aware D2D-assist data transmission protocol for mobile-health systems. IEEE Trans. Inf. Forensics Secur. 2016, 12, 662–675. [Google Scholar] [CrossRef]
- Zhou, C.X. An improved multi-receiver generalized signcryption scheme. Int. J. Netw. Secur. 2015, 17, 340–350. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Warsaw, Poland, 4–8 May 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Advances in Cryptology: Proceedings of CRYPTO 84 4, Santa Barbara, CA, USA, 19–22 August 1984; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar]
- Barbosa, M.; Farshim, P. Certificateless signcryption. In Proceedings of the 2008 ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 18–20 March 2008; Asia CCS ’08. ACM: New York, NY, USA, 2008; pp. 369–372. [Google Scholar]
- Wu, C.; Chen, Z. A new efficient certificateless signcryption scheme. In Proceedings of the 2008 International Symposium on Information Science and Engineering, Shanghai, China, 20–22 December 2008; IEEE: New York, NY, USA, 2008; Volume 1, pp. 661–664. [Google Scholar]
- Sun, Y.; Li, H. ID-based signcryption KEM to multiple recipients. Chin. J. Electron. 2011, 20, 317–322. [Google Scholar]
- Chen, J.; Wang, L.; Wen, M.; Zhang, K.; Chen, K. Efficient certificateless online/offline signcryption scheme for edge IoT devices. IEEE Internet Things J. 2021, 9, 8967–8979. [Google Scholar] [CrossRef]
- Xie, W.; Zhang, Z. Efficient and provably secure certificateless signcryption from bilinear maps. In Proceedings of the 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, Beijing, China, 25–27 June 2010; IEEE: New York, NY, USA, 2010; pp. 558–562. [Google Scholar]
- Cui, M.; Han, D.; Wang, J. An efficient and safe road condition monitoring authentication scheme based on fog computing. IEEE Internet Things J. 2019, 6, 9076–9084. [Google Scholar] [CrossRef]
- Xie, Z.; Chen, Y.; Ali, I.; Pan, C.; Li, F.; He, W. Efficient and Secure Certificateless Signcryption Without Pairing for Edge Computing-Based Internet of Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 5642–5653. [Google Scholar] [CrossRef]
- Shen, J.; Gui, Z.; Chen, X.; Zhang, J.; Xiang, Y. Lightweight and certificateless multi-receiver secure data transmission protocol for wireless body area networks. IEEE Trans. Dependable Secur. Comput. 2020, 19, 1464–1475. [Google Scholar] [CrossRef]
- Yu, H.; Ren, R. Certificateless elliptic curve aggregate signcryption scheme. IEEE Syst. J. 2021, 16, 2347–2354. [Google Scholar] [CrossRef]
- Pan, X.; Jin, Y.; Wang, Z.; Li, F. A pairing-free heterogeneous signcryption scheme for unmanned aerial vehicles. IEEE Internet Things J. 2022, 9, 19426–19437. [Google Scholar] [CrossRef]
- Shim, K.A. CPAS: An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks. IEEE Trans. Veh. Technol. 2012, 61, 1874–1883. [Google Scholar] [CrossRef]
- Wang, Y.; Liu, Y.; Tian, Y. ISC-CPPA: Improverd-Security Certificateless Conditional Privacy-Preserving Authentication Scheme With Revocation. IEEE Trans. Veh. Technol. 2022, 71, 12304–12314. [Google Scholar] [CrossRef]
- Zhu, F.; Yi, X.; Abuadbba, A.; Khalil, I.; Nepal, S.; Huang, X.; Yan, X. Certificate-based anonymous authentication with efficient aggregation for wireless medical sensor networks. IEEE Internet Things J. 2021, 9, 12209–12218. [Google Scholar] [CrossRef]
- Qiao, Z.; Ma, K.; Zhou, Y.; Yang, Q.; Xia, Z.; Yang, B.; Zhang, M. An Anonymous and Efficient Certificate-Based Identity Authentication Protocol for VANET. IEEE Internet Things J. 2024, 11, 11232–11245. [Google Scholar] [CrossRef]
- Gayathri, N.; Thumbur, G.; Reddy, P.V.; Ur Rahman, M.Z. Efficient Pairing-Free Certificateless Authentication Scheme with Batch Verification for Vehicular Ad-Hoc Networks. IEEE Access 2018, 6, 31808–31819. [Google Scholar] [CrossRef]
- Zhou, Y.; Xu, R.; Qiao, Z.; Yang, B.; Xia, Z.; Zhang, M. An Anonymous and Efficient Multimessage and Multireceiver Certificateless Signcryption Scheme for VANET. IEEE Internet Things J. 2023, 10, 22823–22835. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).