Abstract
In gas sensor networks, users can access the data collected by the sensor nodes, but there is a risk of data leakage during transmission. This paper proposes a lightweight bidirectional authentication protocol based on gas sensor physically unclonable functions (GS-PUFs) with authentication technology to guarantee the reliability of data from sensor nodes. A sensor PUF array is constructed by preparing gas sensors to enhance the data security of the physical layer and reduce hardware resource consumption. The authentication part of the protocol mainly uses lightweight encryption methods, consisting of PUF data, one-way cryptographic hash functions, and iso-or functions, to reduce the computational overhead of the authentication process. The protocol security is enhanced by encrypting the GS-PUF response as an irreversible hash value and verifying the hash value by the user, server, and sensor node to complete bidirectional authentication. The test results demonstrate that the protocol, verified through the ProVerif formal tool, can resist impersonation, replay, node tampering, and cloning attacks. Among the compared schemes, this protocol offers the highest security and the least resource overhead, making it effectively applicable in the Internet of Things and other fields.
1. Introduction
Sensor nodes play a critical role in sensor networks, as they collect and transmit environmental data in order to enable intelligent monitoring, control and decision-making functions for sensor platforms or other devices. They are a key component in building intelligent and automated IoT systems [1,2,3,4]. In recent years, with the rapid development of remote sensor nodes [5], the sensitive data involved with gas sensors have faced the risk of being tampered with or misappropriated by unauthorized users. Key management and authentication technologies can effectively reduce the risk of data corruption, ensuring the reliability and integrity of sensor networks. Physical Unclonable Functions (PUFs) [6,7,8,9,10,11], as novel hardware security primitives, have great potential and can be used to construct secure protocols for authentication and key exchange [12,13,14]. PUFs generate unique output responses from input challenges, verifying the challenge–response relationship to produce security parameters such as device identities and keys, ensuring the authenticity of devices and the security of communications. PUFs generate unique, non-replicable responses by leveraging the intrinsic physical properties of hardware or minor manufacturing variations, without needing additional random number generators or complex circuits, thus reducing resource consumption [7].
Authentication protocols based on sensor PUFs have been applied and researched in various fields, such as Radio Frequency Identification (RFID) systems, IoT devices, and wireless sensor networks (WSNs). Numerous PUF-based authentication protocols have been proposed. For example, reference [15] proposed a Cam-PUF based on commercial Complementary Metal Oxide Semiconductor (CMOS) image sensors for mobile device identification and anti-counterfeiting, but its fixed noise pattern may be affected by environmental changes, leading to instability. Reference [16] proposed a lightweight and privacy-preserving user authentication protocol for industrial wireless sensor networks, meeting the requirement for user access to node information, but its lightweight nature might reduce security. Reference [17] proposed a device fingerprinting technique based on the built-in microphones of smartphones for identifying and authenticating individual mobile devices. However, response consistency may be impacted by environmental noise and other factors affecting the physical properties of microphones. Reference [18] proposed a secure and lightweight mutual authentication and key agreement (MAAKA) protocol for wireless medical sensor networks (WMSNs), composed of hash and XOR operations over a fully public channel, which may not be suitable for point-to-point or multiparty communications. Reference [19] proposed an authentication key agreement protocol for electronic medical systems to address the efficiency issues of lightweight operations and employed PUFs to enhance security. However, medical sensing devices usually have limited computing resources, and the reliance on cloud server processing capabilities can lead to performance bottlenecks, making them vulnerable to attackers.
In summary, the research field of PUF-based secure authentication protocols encompasses various aspects such as security analysis, privacy protection, multi-PUF systems, and performance optimization [20]. The Gas Sensor Physical Unclonable Function (GS-PUF) possesses the capability to withstand physical attacks and reverse engineering, and it does not rely on additional hardware or power sources, making it particularly suitable for low-cost, low-power, and small-sized IoT devices [21]. To cite one example, a gas leakage detection system in a chemical plant may utilize GS-PUF technology to guarantee the uniqueness and tamper-proof nature of the sensor nodes, thereby enhancing the safety and reliability of the system. In IoT setups, users generally expect to receive up-to-the-minute data from designated gas sensor nodes, necessitating a dependable and secure communication protocol between users and the sensor nodes. To achieve this, an efficient lightweight bidirectional authentication protocol is designed to enhance the real-time data security of gas sensor nodes. This scheme only allows registered legitimate users to access the gas sensor nodes, without storing any sensitive information on the sensing devices, ensuring the security of both users and gas sensor nodes. The main contributions of this study on the GS-PUF-based secure authentication protocol are as follows:
- GS-PUF Preparation: A detailed introduction of the GS-PUF preparation method, along with the response extraction and analysis process, provides a foundation for subsequent research.
- Proposed Authentication Protocol: We provide the design of a lightweight bidirectional authentication protocol based on GS-PUF, aimed at enhancing the data security of sensor nodes and the efficiency of data transmission.
- Security Analysis: We conduct a security analysis and compare the designed protocol to verify its reliability and security, offering a dependable reference for practical applications.
2. Gas Sensor Physical Unclonable Function
This chapter presents the principles and methods of GS-PUF preparation and systematically analyses the responses generated by GS-PUF in the authentication domain. By exploring the characteristics of GS-PUF, its unique value and potential applications in the field of authentication are revealed.
2.1. GS-PUF Preparation
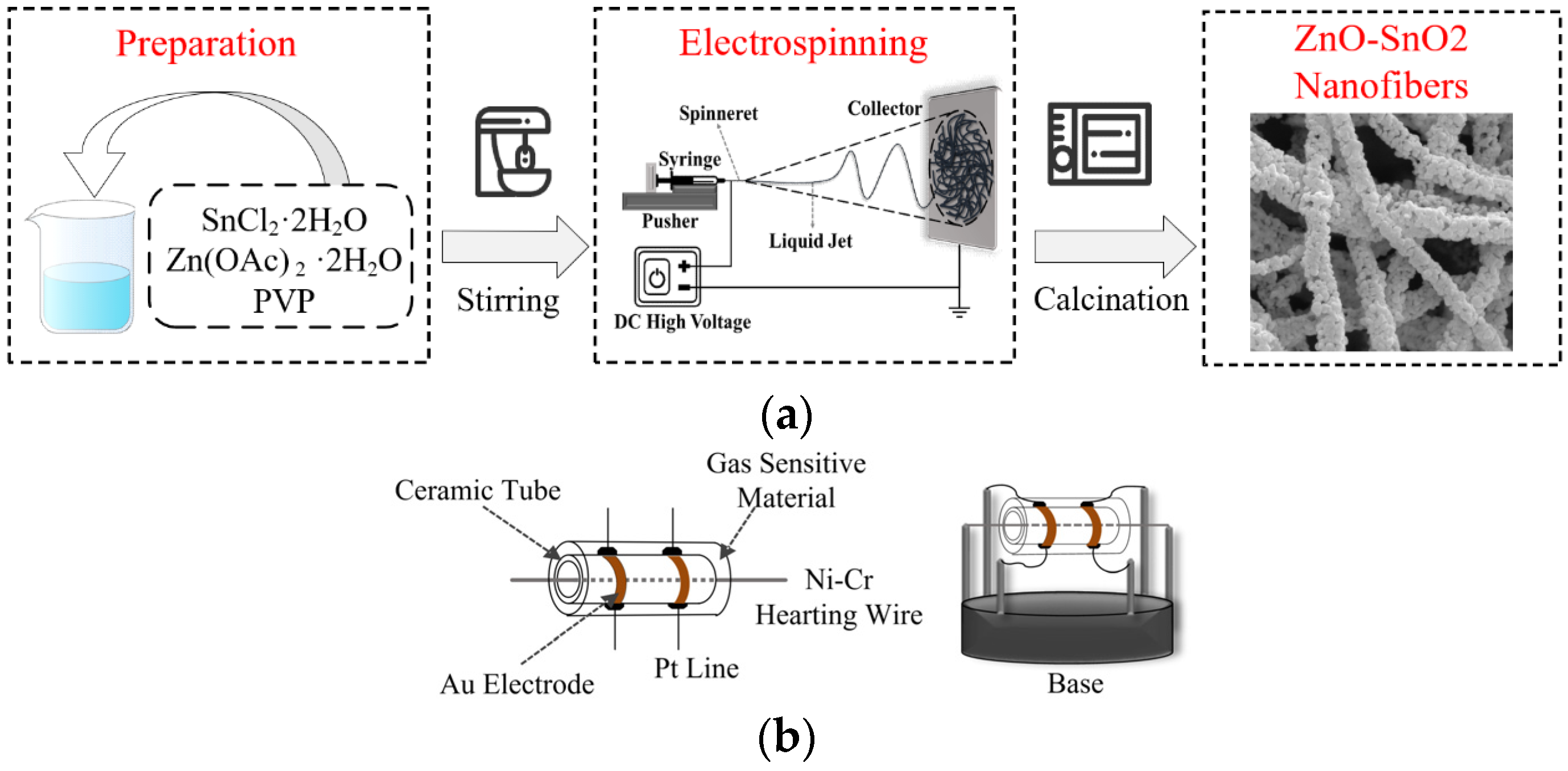
Nanomaterials exhibit composite forms of nanoparticles and nanofibers. Gas sensors are prepared using ZnO-SnO2 nanomaterials through electrospinning and electrospray techniques [22]. Figure 1 illustrates the preparation of the GS-PUF. By regulating the concentration of the polymer solution, different morphologies of nanomaterials are obtained, which can influence the electrical characteristics of the gas sensor. Initially, stannous chloride dihydrate and zinc acetate are added to a mixed solution, followed by the addition of polyvinyl pyrrolidone and stirring before injection. The voltage is adjusted to form a nanofilm on aluminum foil, which is then heated to 500 °C and allowed to cool naturally. Subsequently, the nanomaterials are blended with purified water to create a paste, which is applied to the surface of an alumina ceramic tube equipped with Au electrodes. A nickel–chromium heating wire is then inserted into the tube, aged at 200 °C for 20 h, and subsequently welded and secured to a base.
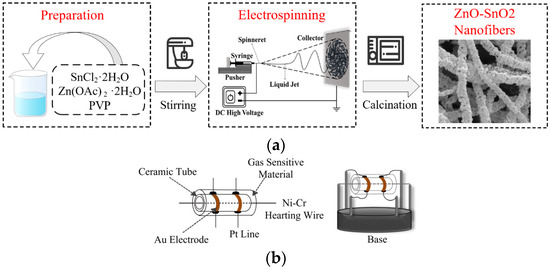
Figure 1.
GS-PUF: (a) ZnO-SnO2 nanomaterial preparation process; (b) ZnO-SnO2 gas sensor.
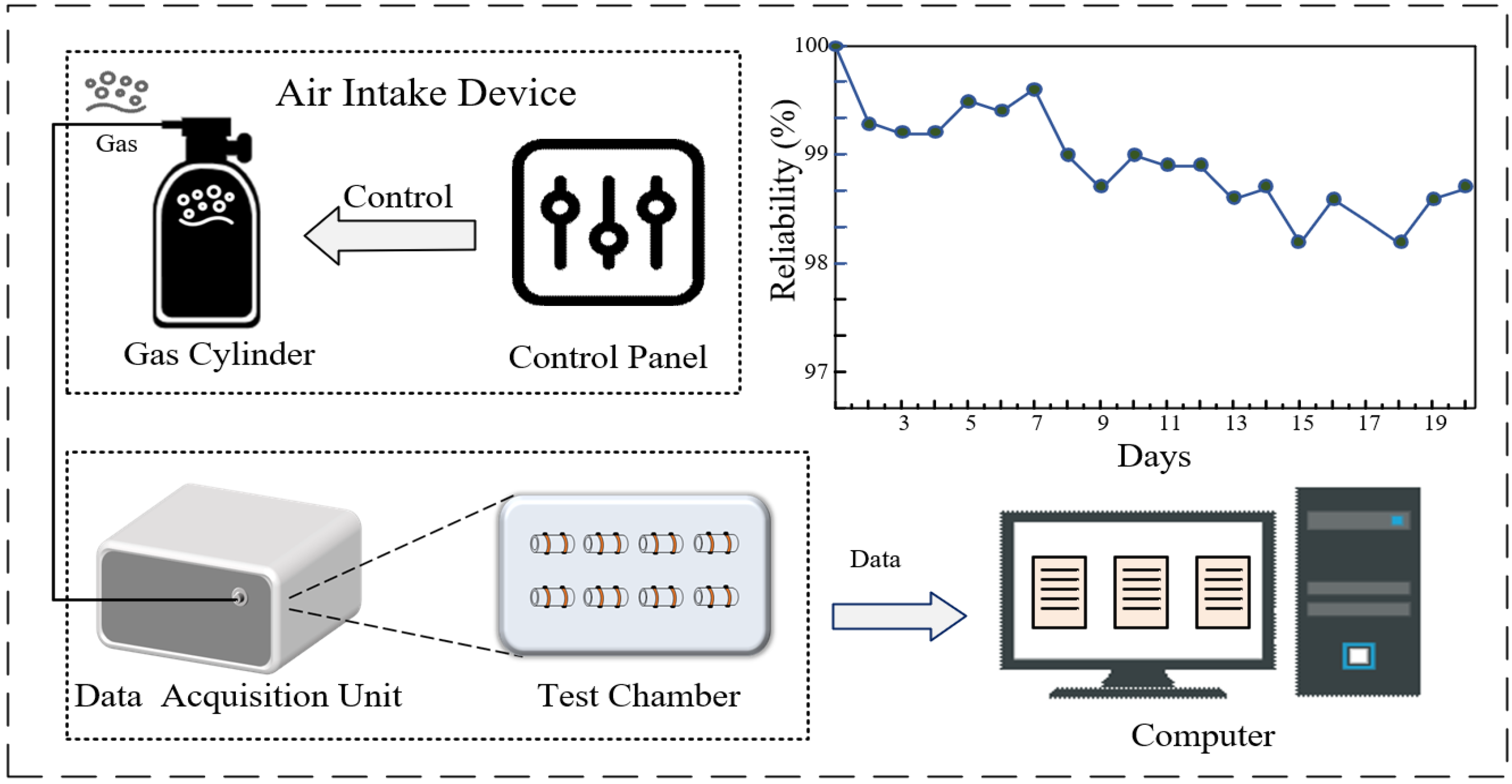
In our experiments, we used an Agilent 34970A data acquisition instrument, sourced from Agilent Technologies, Santa Clara, California, USA, to observe and analyze the changes in sensor resistance data. The gas sensor is configured into a reconfigurable sensor array, utilizing multiple sensors within the array to generate PUF responses, as depicted in Figure 2. To enhance the reliability of the gas sensor results, a median averaging filter method is employed for noise reduction. To more accurately assess the reliability of the ZnO-SnO2 gas sensor PUF, the GS-PUF response was recorded for 20 days using the initial day’s response as a reference. As illustrated in Figure 2, the PUF reliability was diminished due to the impact of sensor aging, yet it remained above 98%, effectively reducing the likelihood of the response flip phenomenon occurring when the gas sensors were compared.
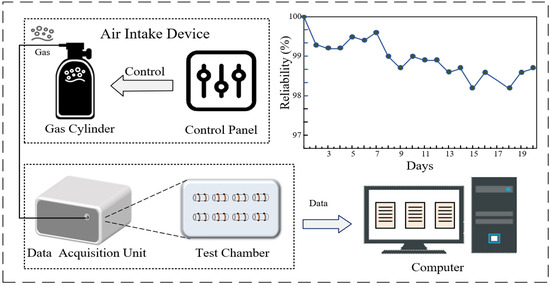
Figure 2.
Gas sensor detection platform.
2.2. GS-PUF Response Analysis
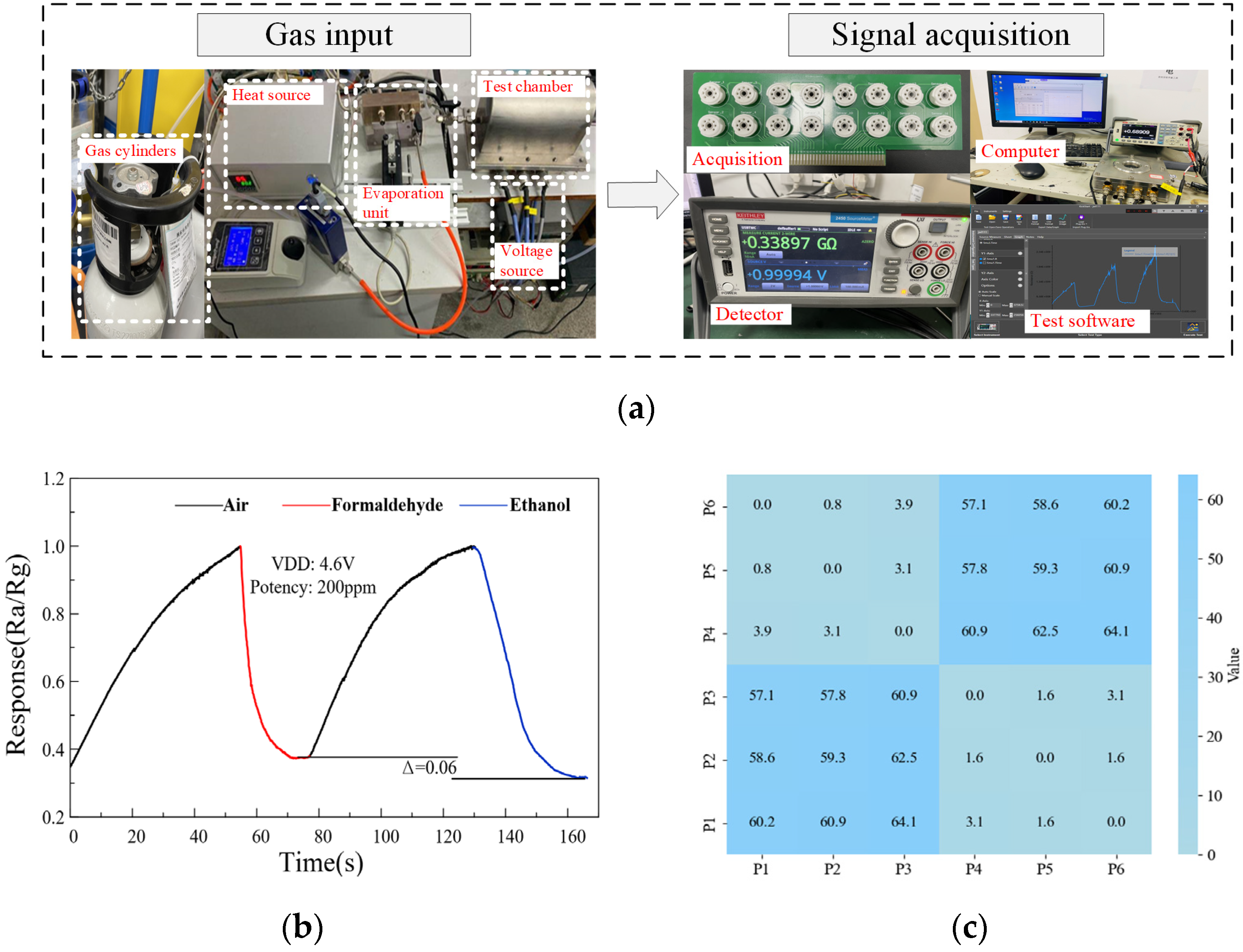
This section uses ethanol and methanol gases as examples. In practice, the actual engineering should encompass the evaluation of a diverse range of gases. In practical scenarios, a variety of gases will invariably be present, and the computer is able to correct and deconvolute the sensor’s response data through the application of machine learning and data processing algorithms. By training the model to identify and separate the characteristic responses of different gases, the impact of cross-response can be effectively reduced, thereby enhancing the accuracy of gas detection. The sensor response can be obtained through normal operation of the device without the need for additional specialized measuring equipment. The experimental setup is shown in Figure 3a. First, air is introduced into a sealed chamber, and the operating voltage of the sensor array is adjusted to 4.6 V. At this stage, the resistance values of the sensors can be observed to gradually increase. Following this step, formaldehyde gas at a concentration of 200 ppm is introduced into the chamber, resulting in a rapid decrease in sensor resistance values until reaching a steady state. Following this, air is reintroduced to restore the gas sensors to their original state. Finally, ethanol gas at a concentration of 200 ppm is introduced until achieving a stable state. The reactions of the gas sensors to formaldehyde and ethanol are illustrated in Figure 3b; Δ is the difference between the resistance response of the two gases. The analogous trend in the response of gas sensors to formaldehyde and ethanol may result in a considerable challenge for gas sensor nodes that rely on resistive response to detect target gases.
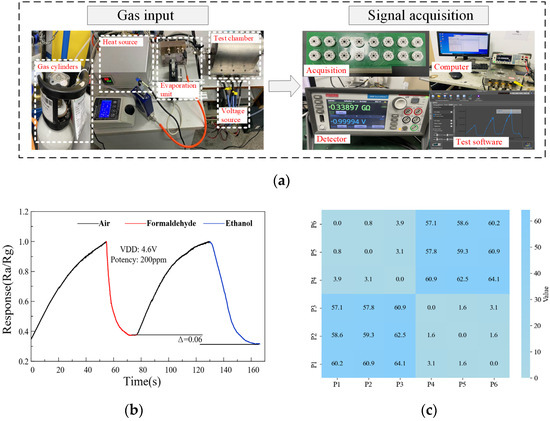
Figure 3.
GS-PUF test: (a) gas sensor experimental platform; (b) gas sensor response to formaldehyde and ethanol; (c) intergroup Hamming distance (HD).
To illustrate potential disruptions in the operational environment more effectively, a deviation of 0.1 V is applied to the operational voltage of the gas sensors. Three sets of experiments are carried out for each gas, aligning with three distinct operational voltages: 4.5 V, 4.6 V, and 4.7 V. PUF responses are generated at these three different operating voltages, and the Hamming distances between different PUF responses are tested. The Hamming distances of the GS-PUF are normalized during the calculation process where HD (i, j) is equal to HD (j, i). The test results are shown in Figure 3c. The GS-PUF data at different voltages are symmetrical [23].
At the same operating voltage, the minimum Hamming distance (HD) between GS-PUFs in different gas environments is 57.1%. Conversely, the maximum HD between GS-PUFs in the same gas environment is 3.9% at different operating voltages, which is significantly less than 57.1%. The distinctive equilibrium affinities of formaldehyde and ethanol result in varying effects on the PUF response, enabling precise differentiation between these gases. The uniqueness of the GS-PUF can be utilized to identify whether the gas environment has been altered. After obtaining response data from the gas sensor, it is compared with the reference PUFs for different gases pre-stored in the server database. The threshold THD is set to the maximum HD of 3.9% between gas sensor PUFs in the same gas environment. If the HD difference between the generated PUF and the reference PUF is below a defined threshold, the database is able to identify this gas. Conventional methods only trigger an alarm based on a sensor resistance threshold without having the ability to identify a particular type of gas.
3. GS-PUF-Based Authentication Protocol
Before gas authentication, it is necessary to authenticate sensor nodes in order to safeguard the confidentiality of data in the sensor from unauthorized access. This section will focus on the key design elements of the protocol, as well as its encryption and decryption methods in the authentication process. Starting with the overall architecture of the protocol, the specific processes and mechanisms of the registration phase and the authentication phase will be discussed. Each phase’s functions and characteristics will be analyzed, and the full process of the GS-PUF lightweight bidirectional authentication protocol will be introduced.
3.1. Overall Architecture of the Protocol
The proposed bidirectional authentication protocol is based on lightweight security primitives. In resource-constrained sensor nodes, using XOR operations and hash functions instead of traditional encryption algorithms can effectively reduce resource overhead [24]. The proposed bidirectional authentication protocol includes the following stages: user registration stage, gas sensor node registration stage, and authentication stage. It is crucial to keep session keys confidential before identity authentication as a compromise of these keys would jeopardize the entire system’s security [25,26]. Table 1 lists the important symbols used in this paper.

Table 1.
Notations.
3.2. User Registration Phase
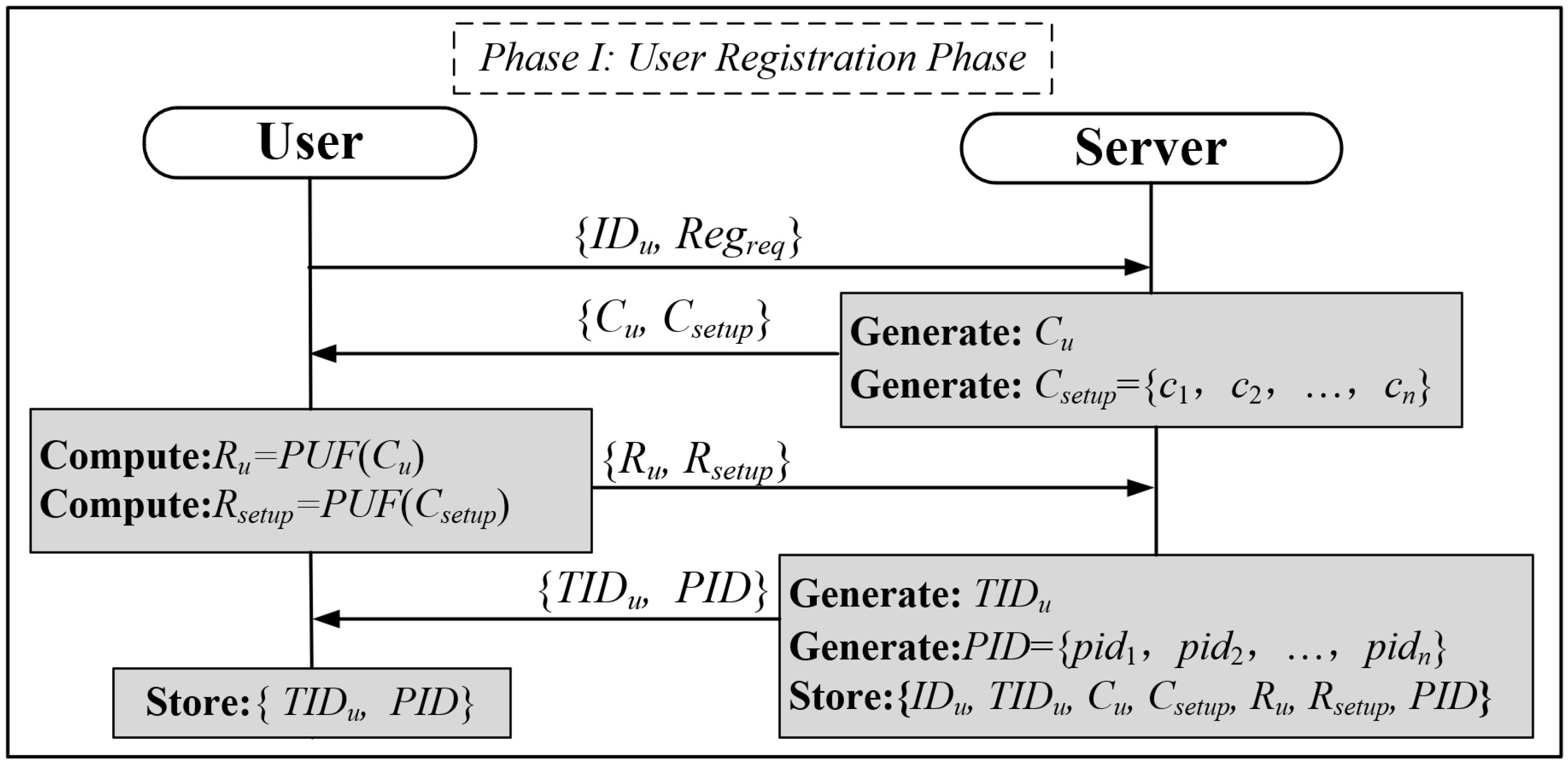
Assuming that the user wishes to access real-time data from the gas sensor node, they need to register with the server, and the user registration process is shown in Figure 4.
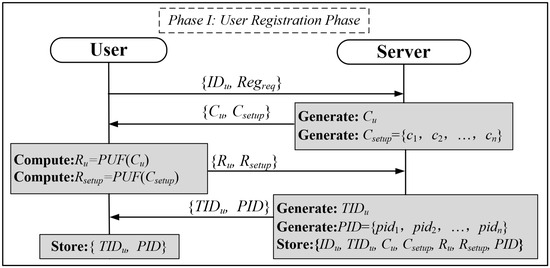
Figure 4.
User registration phase.
Step 1: The user sends an identification IDu and Regreq to the server, where Regreq is a registration request.
Step 2: Upon receipt of the registration message from the user, the server generates a random incentive Cu for authentication and a set of incentives Csetup = {c1, c2, …, cn} for synchronization of the information, packaging the information and sending it to the user.
Step 3: After receipt of {Cu, Csetup}, the user generates the response Ru and Rsetup using their own PUF and transmits the corresponding response message to the server.
Step 4: The server generates a unique user temporary identity TIDu and a set of pseudo-identities PID, stores all the information pertaining to the user, and transmits {TIDu, PID} to the user.
Step 5: The user saves the received {TIDu, PID}.
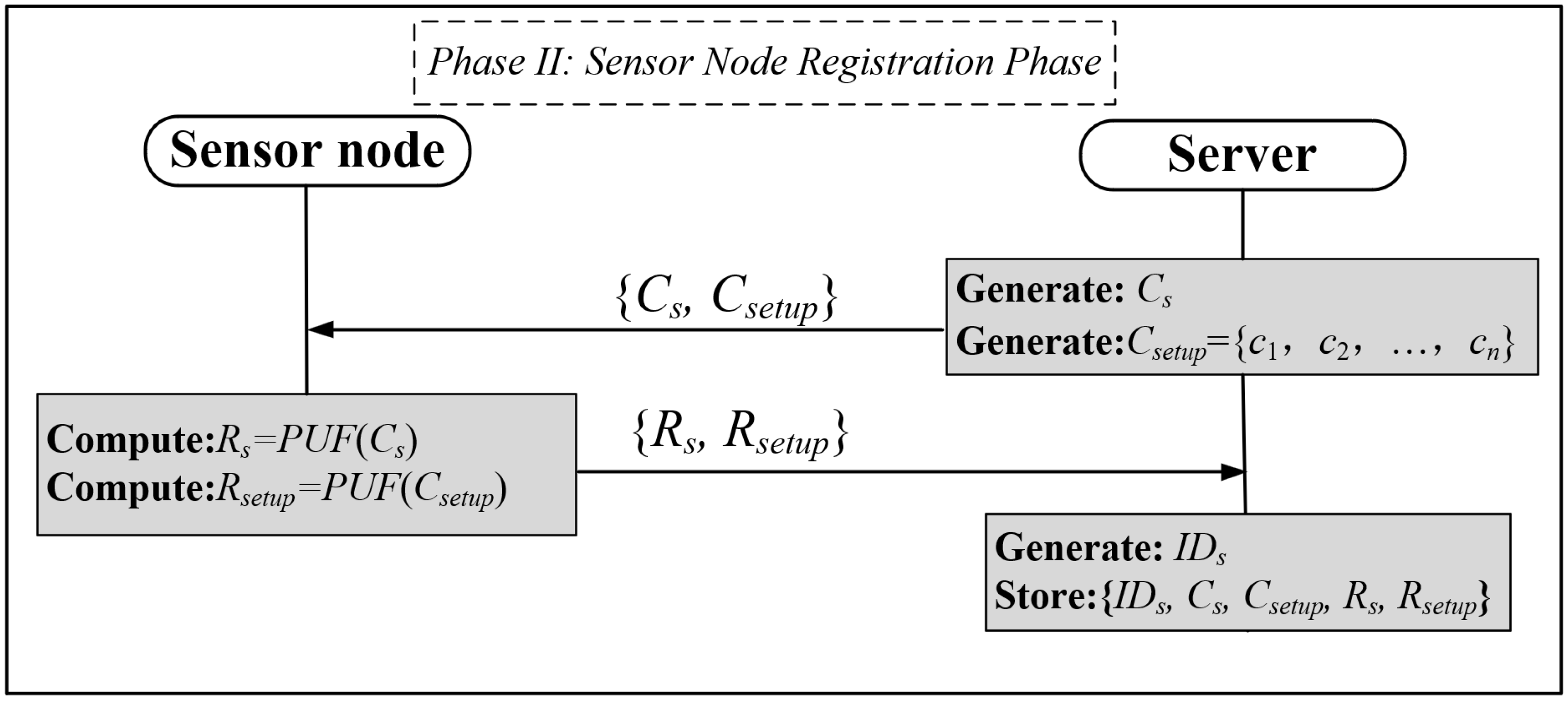
3.3. Sensor Node Registration Phase
It is also necessary to register the sensor nodes on the server in order to guarantee that users are able to access only sensor nodes that have been duly authorized. The registration process for a sensor node is illustrated in Figure 5.
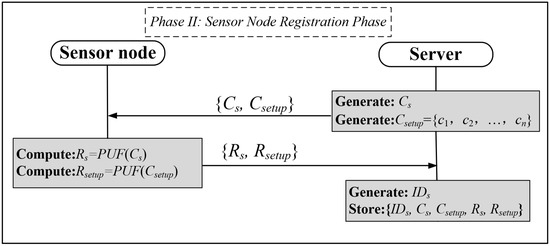
Figure 5.
Gas sensor node registration phase.
Step 1: The server first generates the incentives Cs for authentication with the sensor node and also generates a new set of incentives Csetup = {c1, c2, …, cn} to synchronize with the sensor node and transmits the information {Cs, Csetup} to the sensor node.
Step 2: After receiving the registration information, the sensor node generates a PUF response Rs = PUF(Cs), Rsetup = PUF(Csetup) and packages {Rs, Rsetup} for transmission to the server.
Step 3: The server assigns a unique identity IDs to the sensor node and stores the registration data {IDs, Cs, Csetup, Rs, Rsetup} in the database.
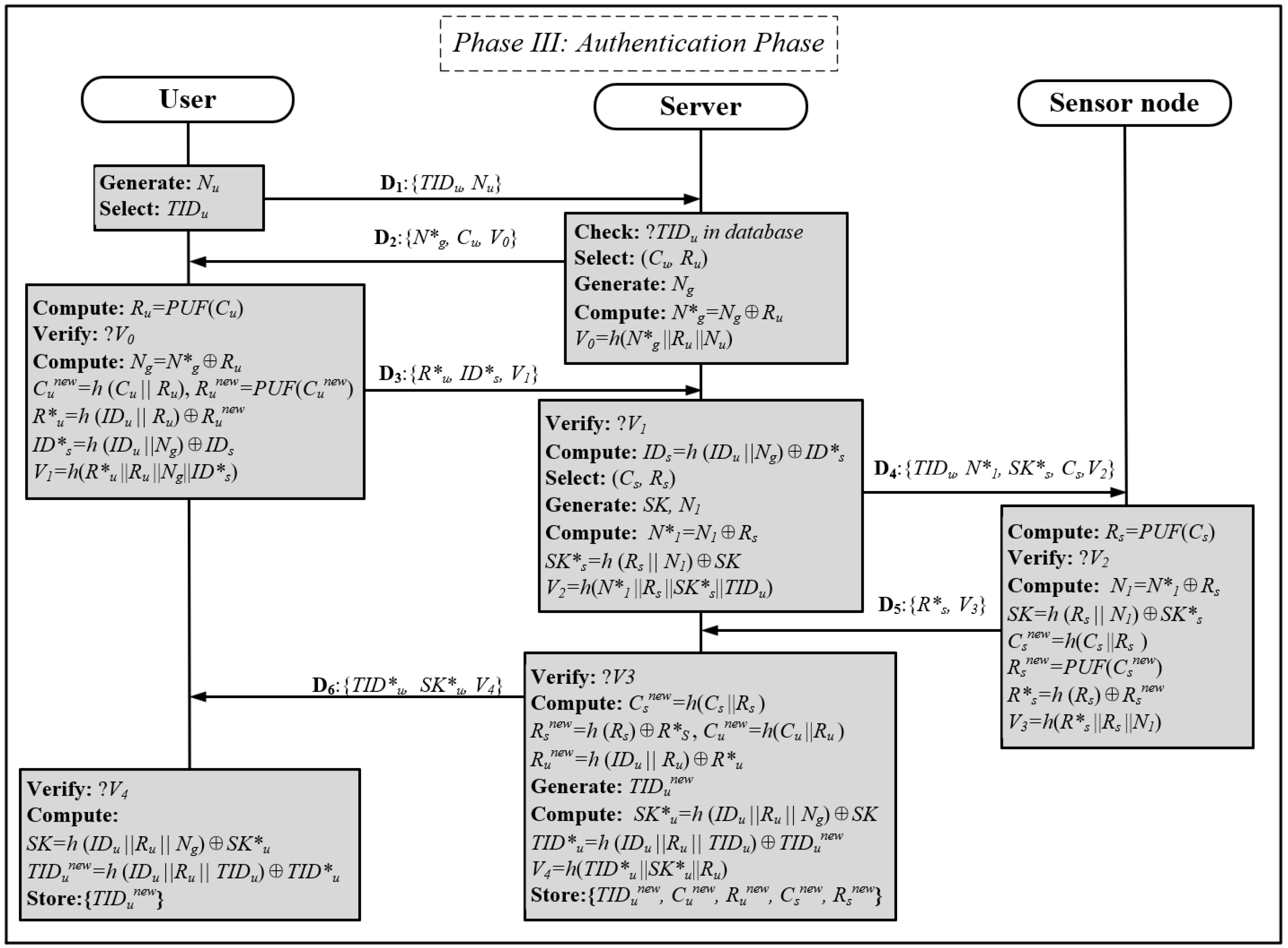
3.4. Authentication Phase
Assuming that the user wishes to access the real-time data from the gas sensors at work, bidirectional authentication with the server and the sensor node is required. The authentication process is illustrated in Figure 6.
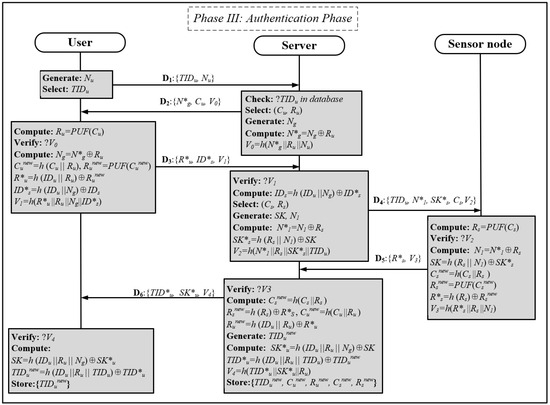
Figure 6.
Secure lightweight physically secure anonymous authentication protocol for real-time data access of sensor nodes.
Step 1: The user generates a random number Nu and transmits this number and its unique identification TIDu to the server.
Step 2: Upon receipt of the authentication information, the server first verifies the TIDu in the database. Then, the server selects the incentive response pair for authentication, generates the random number Ng, and employs the XOR function and hash function to generate the encrypted data N*g and the hash value V0. Finally, the server transmits the authentication data {N*g, Cu, V0} to the user.
Step 3: After receiving the message D2, the user generates the PUF response Ru corresponding to Cu and verifies the hash value V0. If the verification is successful, Ng is restored, Cunew = h(Cu||Ru) is computed, and the PUF response Runew is generated. Then, the user enters the identity IDu as well as the sensor node identity IDs of the sensor nodes that need to be accessed, and computes the encrypted data R*u, ID*s and the hash value V1 for the server to authenticate the user. Finally, the user sends {R*u, ID*s, V1} to the server.
Step 4: Following receipt of the message D3, the server verifies V1. Upon successful verification, the server decrypts the sensor node identity IDs and selects the excitation response pairs for verification of the sensor node. Subsequently, the server encrypts the generated random numbers and keys to obtain N*1 and SK*s, and then uses the encrypted information to calculate the hash value V2. Finally, the message D4 is transmitted to the sensor node for verification.
Step 5: Upon receipt of the message D4, the sensor node generates the PUF response Rs, corresponding to Cs, and verifies the hash value V2. If the verification is successful, the node decrypts N1 and SK*s, computes Csnew = h(Cs||Rs) and the corresponding response Rsnew, and uses Rsnew to compute R*s and the hash value V3. Finally, the sensor node sends the {R*s, V3} to the server.
Step 6: The server verifies the hash value V3 after receiving D5; if the verification is successful, it selects the new challenge–response pair used to authenticate the sensor node and the user. Then, it updates the temporary identity of the user and encrypts SK and TIDunew and calculates the hash value V4. Finally, the server stores the data {TIDunew, Cunew, Runew, Csnew, Rsnew} to be used for the next authentication and sends the encrypted data together to the user to update the identity.
Step 7: The subscriber verifies the hash value V4 after receiving the message D6; if the verification is successful, the session key SK for transmitting the gas data is decrypted and the identity is updated in TIDunew.
In the event of an unsuccessful authentication step, the authentication process will be terminated, resulting in the user being unable to access the sensor node information. Subsequently, the user is permitted to reapply for authentication using the pseudo-identity pidi ∈ PID. Upon successful authentication, the system will delete the previously used pidi, thus ensuring the anonymity and security of the identity information.
4. Analysis of Protocol Security
4.1. Analysis of Formal Security
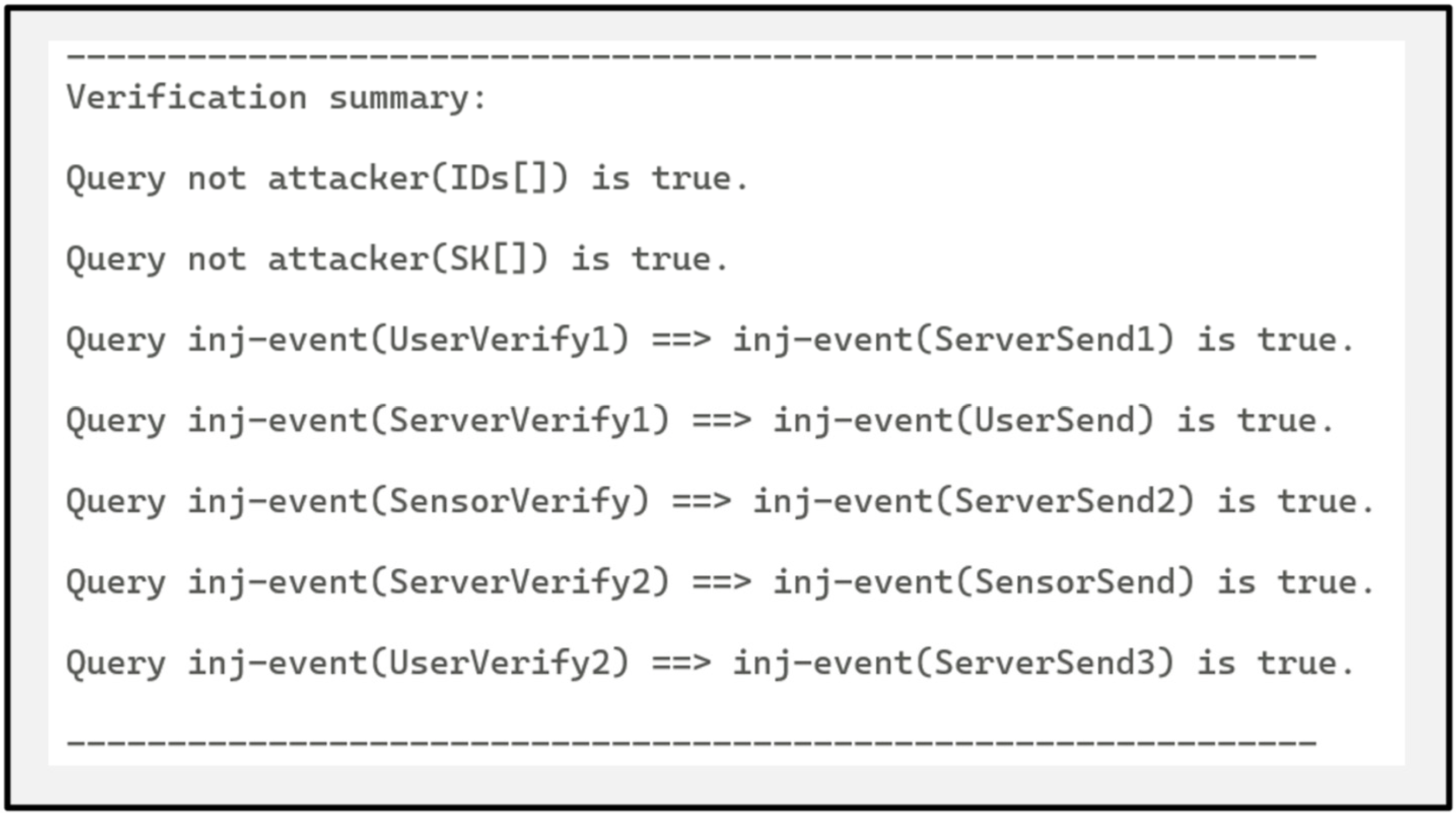
ProVerif is an automated tool for formally verifying the security of cryptographic protocols [27]. It does not require users to perform tedious manual calculations, and it supports multiple attack models, including passive and active attacks, which can simulate the behavior of attackers in different scenarios and provide us with comprehensive analysis of protocol security. To test the security of a protocol designed for testing, ProVerif. 2.05 is used to verify the protocol flow, as shown in Figure 7, which is the preset part of ProVerif.

Figure 7.
ProVerif preset contents.
In the provided ProVerif script, “value” denotes a private bit string or constant, “function” denotes an encrypted function or operation included, “event” denotes an event used to define a security attribute, and “query” denotes the security query being verified. The preset parts c and sc represent the public channel and secure channel, respectively. PUF(), XOR(), h1(), h2(), h3(), and h4() represent the actual PUF generation function, XOR operation, and different bit-length hash operations in the protocol, respectively. The 13 events defined are to verify whether bidirectional authentication is implemented between users, servers, and sensors. Attackers can eavesdrop on messages in the public channel to try to analyze important information such as the session’s security key and identity (ID). The security of the designed protocol flow is evaluated by asking for ID, SK, and the order of event occurrence. The security verification results of ProVerif on the terminal are shown in Figure 8.
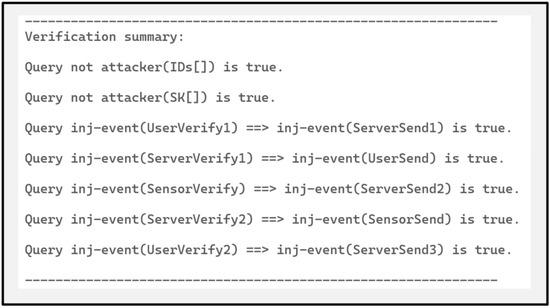
Figure 8.
ProVerif security verification results.
4.2. Informal Safety Analysis
- Mutual authentication: In the above authentication process, the user verifies the hash value V0 to determine the legitimacy of the server and the server checks the hash value V1 to verify the user. The hash value is obtained from Ru, which is a confidential dataset. Consequently, it is not possible for an attacker to mimic a legitimate user or forge an identity to obtain the hash value used for authentication. The authentication process between the sensor and the server is similar, where the sensor authenticates V2 and the server matches V3 to authenticate the sensor. The proposed protocol implements two-way authentication to ensure the legitimacy of the identities of the two communicating parties.
- Anonymous identity: In the protocol, the server is the sole repository of the users’ authentic identity. The user’s temporary identity is generated randomly and is not the same every time the user applies for authentication. Consequently, it is not possible for an attacker to restore the user’s real identity from the eavesdropped messages. When synchronization is lost or a DoS attack occurs, the user can use the pseudo-identity pidi ∈ PID stored during the registration phase, and then the server and user need to delete it to further enhance the user’s anonymity and the untraceability of the scheme. The user encrypts the sensor’s identity IDs; ID*s = h(IDu||Ng) ⊕ IDs. The hash function is irreversible, and an attacker cannot distinguish the encrypted result from a random string. Therefore, the proposed protocol achieves identity anonymity for users and sensors.
- Forward secrecy: After a session, the attacker may attempt to guess the session key SK using captured information, but it will not affect the security of subsequent sessions, because in the next session, the server will generate (Cu, Ru) and (Cs, Rs) and update the database, and the information obtained by the attacker in the previous session is not time-sensitive, so it cannot crack the session key SK. Therefore, the session has forward secrecy.
- Resistance to common attacks: The protocol involves the establishment of two-way authentication between sensors, users, and servers, which means that data transmission can only be performed after mutual verification to prevent malicious attackers from posing as legitimate identities to attack. The (Cu, Ru), (Cs, Rs), TIDu, SK in the protocol are all one-time, which can prevent attackers from repeatedly using data and spoofing legitimate identities. In addition, the SK*u = h(IDu||Ru||Ng) ⊕ SK involved in the protocol process is relatively confidential, and the GS-PUF can generate an exponential number of responses. Attackers cannot obtain SK*u by brute-force attack using exhaustive search.
- Physical attack resistance: If the attacker physically tampers with the sensor node or the user device, the GS-PUF will be unable to provide the correct response of Ru and Rs during the authentication phase of the protocol. The server is therefore able to ascertain whether it has been subjected to an attack based on the presence of erroneous data. In addition, PUF is not cloneable and cannot create an identical PUF structure. Therefore, this scheme has the effect of resisting physical attacks.
4.3. Comparative Analysis
As shown in Table 2, several existing sensor protocol schemes are compared in terms of their security features and computational overhead during the protocol authentication phase. From the table, it can be observed that the protocol in [18] does not update the private key generated during the registration phase and cannot resist desynchronization attacks. The protocol in [19] involves computations that are not fully secure, making it susceptible to brute-force attacks and incapable of preventing DoS attacks. The protocol in [25] requires users to apply for and successfully authenticate the key for updates, lacking forward secrecy and being unable to resist desynchronization attacks, man-in-the-middle attacks, and DoS attacks. To ensure the fairness, accuracy, and reliability of the results produced by the methods in [18,19,25], computational costs consisting of irreversible hash functions and bitwise XOR operations were used. TH represents the time for the hash function, and TXOR represents the time for the XOR operation. The computational cost of bitwise XOR is much lower than that of the hash operation. The authentication experiments were conducted on a laptop with an Intel Core i9-12900H processor, 2.50 GHz frequency, and 16 GB of memory. The sensor node experiments were conducted on a desktop computer with an Intel Core i5-9500 processor, 3.00 GHz frequency, and 8 GB of memory. As evidenced in Table 2, the proposed protocol exhibits a markedly reduced computational overheads relative to existing approaches. The highest Percentage Reduction in Total Computational Time (PRTCT) is 49.01%, contributing to a notable reduction in the computational burden.

Table 2.
Comparison of security and computational overhead.
5. Conclusions
This paper analyzes the PUF response of GS-PUF in different gas environments and utilizes the excitation response relationship to determine the authentication scheme. The output of GS-PUF is based on physical properties that are challenging to replicate, thereby rendering it difficult for attackers to counterfeit or tamper with the device. Furthermore, the GS-PUF is highly reliable, responding correctly to the gas environment and guaranteeing the correctness of the data. We propose an anonymous bidirectional authentication protocol based on GS-PUF to protect the security of data during transmission. The protocol encrypts the data using physically unclonable functions, irreversible hash functions, and XOR functions for data encryption, aiming to reduce computational overhead through lightweight encryption. In the security analysis and overhead comparison, the proposed authentication scheme not only ensures multiple critical security properties but also reduces computational costs, thereby enhancing the security of sensor data. With this scheme, gas sensors can operate under server monitoring, ensuring that users receive authentic and reliable gas sensor data while maintaining the security of legitimate users.
Author Contributions
Conceptualization, S.H., H.H. and X.L.; methodology, S.H. and H.H.; software, S.H.; validation, S.H., H.H. and X.L.; formal analysis, S.H. and H.H.; investigation, S.H.; resources, H.H. and X.L.; data curation, S.H.; writing—original draft preparation, S.H.; writing—review and editing, S.H.; visualization, H.H.; supervision, P.W. and Y.Z.; project administration, P.W. and Y.Z.; funding acquisition, P.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Natural Science Foundation of China (62174121, 62234008, 62474100), the Science and Technology Innovation 2025 Major Project of Ningbo (2022Z203), Ningbo University and Ningbo Yongxin Microelectronics Technology Co., Ltd. Digital Integrated Circuit Design Joint Laboratory (XQ2022000005), and the Ningbo University Student Research and Innovation Program (2024SRIP1304).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare that this study received funding from Ningbo University and Ningbo Yongxin Microelectronics Technology Co., Ltd. Digital Integrated Circuit Design Joint Laboratory. The funder was not involved in the study design, collection, analysis, interpretation of data, the writing of this article or the decision to submit it for publication.
References
- Rosenfeld, K.; Gavas, E.; Karri, R. Sensor physical unclonable functions. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 112–117. [Google Scholar]
- Fukushima, K.; Hidano, S.; Kiyomoto, S. Sensor-based wearable PUF. In Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (ICETE 2016), Lisbon, Portugal, 26–28 July 2016; pp. 207–214. [Google Scholar]
- Gebali, F.; Mamun, M. Review of physically unclonable functions (PUFs): Structures, models, and algorithms. Front. Sens. 2022, 2, 748–751. [Google Scholar] [CrossRef]
- Li, X.; Wang, P.; Li, G.; Ni, L.; Zhang, Y. Design of interface circuits and lightweight PUF for tmr sensors. IEEE Sens. J. 2023, 23, 11754–11761. [Google Scholar] [CrossRef]
- Tang, J.; Karri, R.; Rajendran, J. Securing pressure measurements using sensor PUFs. In Proceedings of the 2016 IEEE International Symposium on Circuits and Systems (ISCAS), Montreal, QC, Canada, 22–25 May 2016; pp. 1330–1333. [Google Scholar]
- Ni, L.; Zhang, J. S2RAM PUF: An ultra-low power subthreshold SRAM PUF with zero bit error rate. In Proceedings of the 61th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 23–27 June 2024. [Google Scholar]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Cui, Y.; Li, J.; Chen, Y.; Wang, C.; Gu, C.; O’neill, M.; Liu, W. An efficient ring oscillator PUF using programmable delay units on FPGA. ACM Trans. Des. Autom. Electron. Syst. 2023, 1, 1–20. [Google Scholar] [CrossRef]
- Ni, L.; Wang, P.; Zhang, Y.; Li, X.; Li, G.; Ding, L.; Zhang, J. SI PUF: An SRAM and inverter-based PUF with a bit error rate of 0.0053% and 0.073/0.042 pJ/bit. IEEE Trans. Circuits Syst. II Express Briefs 2024, 71, 2339–2343. [Google Scholar] [CrossRef]
- He, Y.; Li, D.; Yu, Z.; Yang, K. 36.5 An automatic self-checking and healing physically unclonable function (PUF) with <3 × 10−8 bit error rate. In Proceedings of the 2021 IEEE International Solid-State Circuits Conference (ISSCC), San Francisco, CA, USA, 13–22 February 2021; pp. 506–508. [Google Scholar]
- Zhang, J.; Shen, C.; Guo, Z.; Wu, Q.; Chang, W. CT PUF: Configurable tristate PUF against machine learning attacks for IoT security. IEEE Internet Things J. 2021, 9, 14452–14462. [Google Scholar] [CrossRef]
- Lim, D.; Lee, J.W.; Gassend, B.; Suh, G.E.; Van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE VLSI Syst. 2005, 13, 1200–1205. [Google Scholar]
- Lee, J.W.; Lim, D.; Gassend, B.; Suh, G.E.; Van Dijk, M.; Devadas, S. A technique to build a secret key in integrated circuits for identification and authentication applications. In Proceedings of the 2004 Symposium on VLSI Circuits, Honolulu, HI, USA, 17–19 June 2004; pp. 176–179. [Google Scholar]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT security through authentication of wireless nodes using in-situ machine learning. IEEE Internet Things J. 2018, 8, 388–398. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, Y. CamPUF: Physically unclonable function based on CMOS image sensor fixed pattern noise. In Proceedings of the 2018 55th ACM/ESDA/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 24–28 June 2018; pp. 1–6. [Google Scholar]
- Gope, P.; Das, A.K.; Kumar, N.; Cheng, Y. Lightweight and physically secure anonymous mutual authentication protocol for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2019, 15, 4957–4968. [Google Scholar] [CrossRef]
- Lee, Y.; Li, J.; Kim, Y. Micprint: Acoustic sensor fingerprinting for spoof-resistant mobile device authentication. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 12–14 November 2019; pp. 248–257. [Google Scholar]
- Li, J.; Su, Z.; Guo, D.; Choo, K.K.R.; Ji, Y. PSL-MAAKA: Provably secure and lightweight mutual authentication and key agreement protocol for fully public channels in internet of medical things. IEEE Internet Things J. 2021, 8, 13183–13195. [Google Scholar] [CrossRef]
- Lee, T.F.; Lin, K.W.; Hsieh, Y.P.; Lee, K.C. Lightweight cloud computing-based RFID authentication protocols using PUF for e-healthcare systems. IEEE Sens. J. 2023, 23, 6338–6349. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: IoT security enhancement through authentication of wireless nodes using in-situ machine learning. In Proceedings of the 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018; pp. 205–208. [Google Scholar]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embed. Comput. Syst. 2017, 16, 1–25. [Google Scholar] [CrossRef]
- He, H.; Wang, P.; Li, X.; Zhang, Y.; Zhang, X. Highly reliable RS-PUF based on reconfigurable gas sensor array. IEEE Sens. J. 2024, 24, 16875–16882. [Google Scholar] [CrossRef]
- Arafin, M.T.; Gao, M.; Qu, G. VOLtA: Voltage over-scaling based lightweight authentication for IoT applications. In Proceedings of the 2017 22nd Asia and South Pacific Design Automation Conference (ASP-DAC), Chiba, Japan, 16–19 January 2017; pp. 336–341. [Google Scholar]
- Gope, P.; Lee, J.; Quek, T.Q. Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Fotouhi, M.; Bayat, M.; Das, A.K.; Far, H.A.N.; Pournaghi, S.M.; Doostari, M.A. A lightweight and secure two-factor authentication scheme for wireless body area networks in Health-care IoT. Comput. Netw. 2020, 177, 107333. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Chang, D.; Zhu, N.; Yang, Y. Security Analysis of SDN Access Control Protocol Based on ProVerif. In Proceedings of the 2021 IEEE 3rd International Conference on Civil Aviation Safety and Information Technology (ICCASIT), Changsha, China, 20–22 October 2021; pp. 1155–1159. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).