Social Trust Confirmation-Based Selfish Node Detection Algorithm in Socially Aware Networks
Abstract
1. Introduction
2. Related Works
3. Network Model and Assumptions
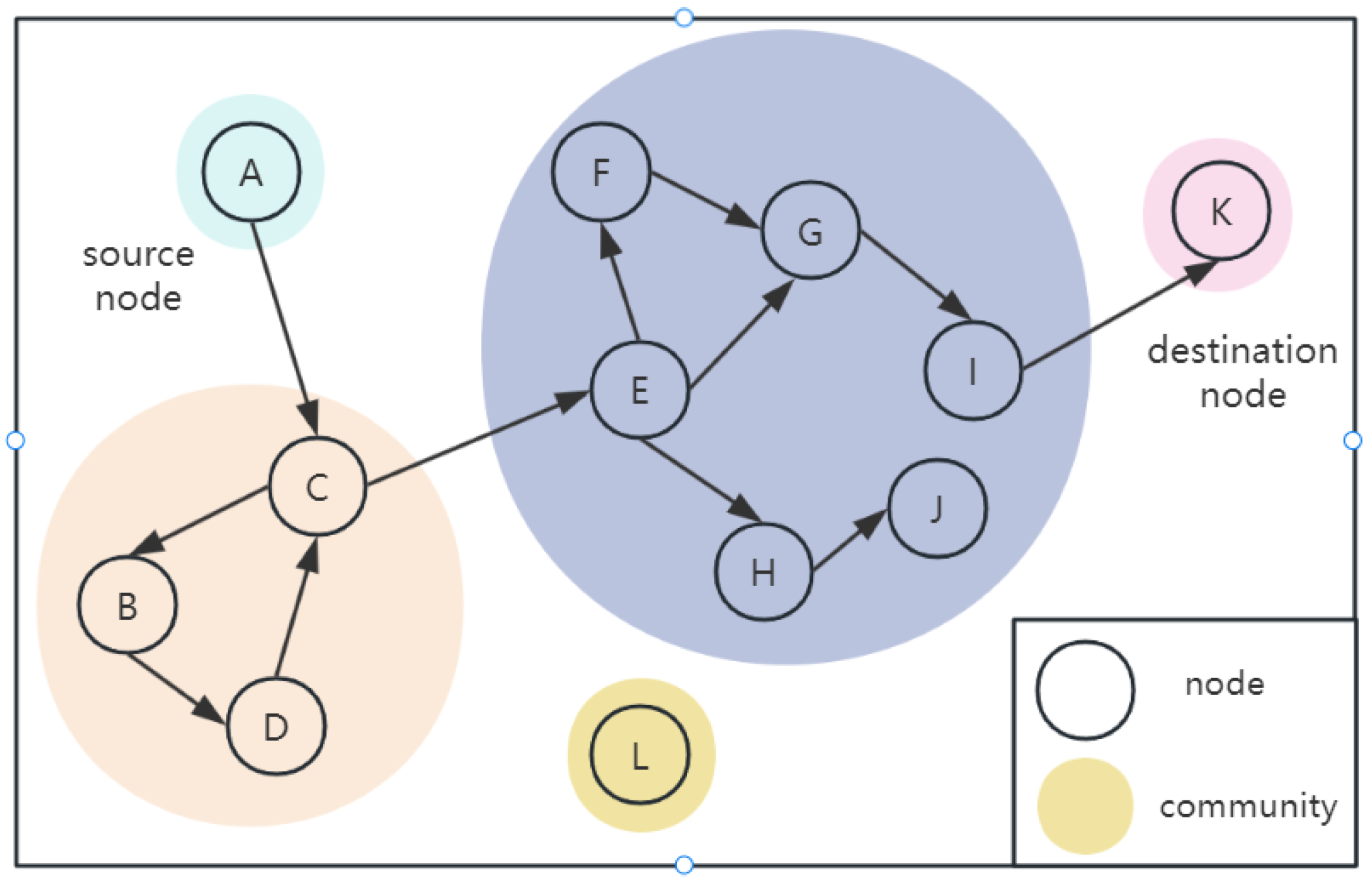
3.1. Network Model
3.2. Assumptions
- If a relay node is marked as selfish, it is assumed that the node is not the final recipient of the message. It will either reject messages from any other node or discard messages it has received;
- Selfish nodes do not engage in malicious activities, and nodes within the network do not alter their data information arbitrarily;
- Every node in the network possesses a distinct identifier, along with initial energy levels and cache capacity. Should a node’s energy be exhausted, it will automatically withdraw from the network.
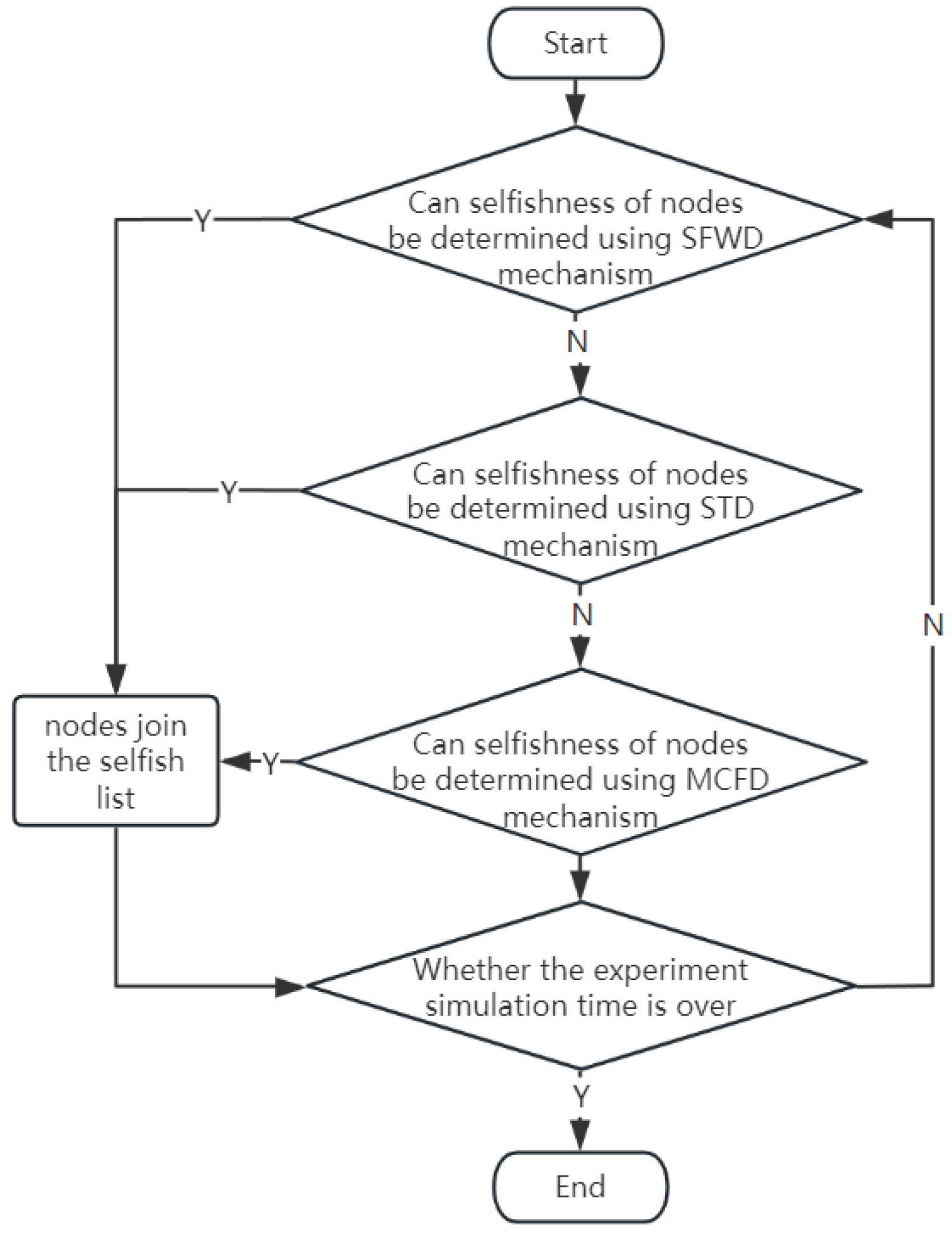
4. Social Trust Confirmation-Based Selfish Node Detection Algorithm (STCDA)
4.1. Subjective Forwarding Willingness Detection (SFWD) Mechanism
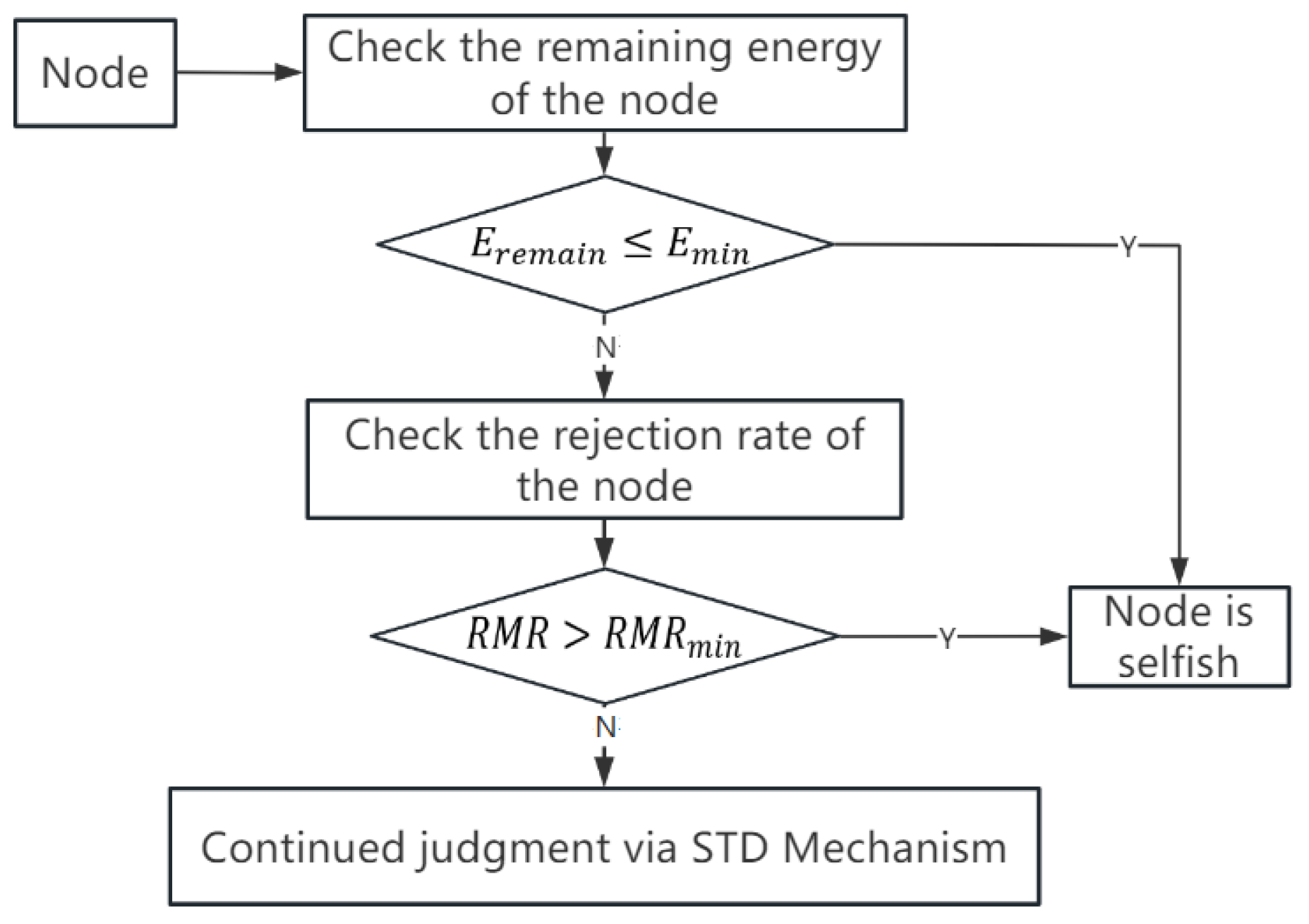
4.1.1. Energy Constraints of Nodes
4.1.2. Message Rejection Rate of Nodes
- (1)
- If , indicating that the residual energy of node is too low to support message forwarding, the node will exhibit selfish behavior by refusing to provide message-forwarding services. At this point, the node is selfish, and there is no need to consider the node’s message rejection rate because the node lacks the energy to forward messages and thus will not receive messages either.
- (2)
- If , indicating that the residual energy of node is sufficient, and the node can expend some energy to forward messages, further consideration of the node’s message rejection rate is conducted to assess its selfishness.
- (3)
- If (the minimum threshold of message rejection rate that indicates node selfishness), this suggests that the node’s message rejection rate is excessively high. Even if some nodes reject messages due to a temporary insufficiency of cache space, a high RMR suggests a greater likelihood that the node is refusing messages to conserve cache space, thereby marking the node as selfish.
- (4)
- If , indicating that the node’s selfishness is likely due to temporary insufficiency of cache space, this suggests that there may be some rejection of the received messages. This, however, cannot prove that the node is selfish. Therefore, when the node’s subjective forwarding intention detection mechanism cannot determine selfish nodes, further judgment is made using the node’s social trust detection (STD) mechanism.
| Algorithm 1 SFWD algorithm |
| Input: , , , , Output: Boolean Value 1: if then 2: Boolean Value = YES 3: else 4: 5: if then 6: Boolean Value = YES 7: else 8: Apply STD Algorithm to judge 9: end if 10: end if |
4.2. The Node’s Social Trust Detection (STD) Mechanism
4.2.1. Selfish Node Model
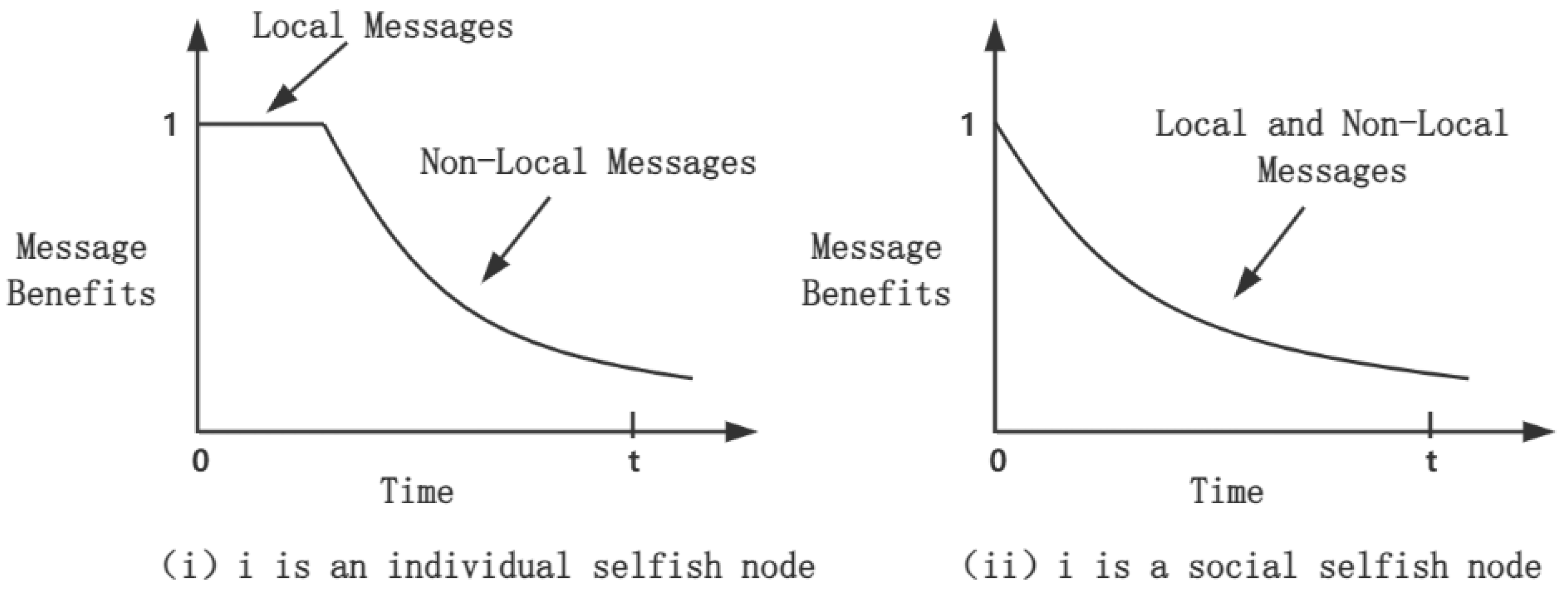
4.2.2. Node’s Social Relationships and Social Awareness Level
- Social pressure measure (SPM) is a new method for measuring the intimacy of node relationships based on three characteristics: frequent, sustained, and consistent interactions. That is, nodes are deemed as friends if they engage in regular and frequent communication over an extended duration. Consequently, the formula to determine the social pressure metric between node i and j at time t is outlined in Equation (5) as follows:where represents the remaining time until the next encounter between both nodes at time t. If two nodes are connected at time t, then . Otherwise, . is the time until their next encounter. T denotes the effect on of all encounters between two nodes in the time interval [0, T] at some point in the experimental run.
- Social similarity (socsim) is quantified by the count of mutual neighboring nodes shared by two nodes, reflecting their level of resemblance. Therefore, the formula for assessing the social similarity between node i and node j is presented in Equation (6) as :where denotes the common neighbor nodes’ number between node i and j, denotes the total number of neighbor nodes of node i, and denotes node j’s total neighbor node’s number.Since the social relationship, SR, between nodes is jointly determined by the social pressure measure, SPM, and social similarity socsim, according to the definitions of Equations (5) and (6), and the social relationship between node i and j. can be presented as Equation (7):where is the weighting factor that influences the importance of factor and to . .
| Algorithm 2 Calculate social awareness degree |
| Input: Output: 1: Initialize: 2: for each do 3: if then 4: ; 5: Continue; 6: else 7: Break; 8: end if 9: end for 10: if then 11: ; 12: end if 13: for each do 14: update based on m; 15: ; 16: end for 17: return |
4.2.3. Update of Node’s Social Trust
| Algorithm 3 Update node social trust |
| Input: Output: , , 1: Initialize: ; 2: Initialize: ;; 3: Calculate 4: for each do 5: if then 6: ; 7: Continue; 8: end if 9: if then 10: ; 11: Break; 12: else 13: ; 14: end if 15: end for 16: for each do 17: if then 18: update ; 19: ; 20: else if and then 21: update ; 22: ; 23: else if and then 24: update ; 25: ; 26: end if 27: end for 28: return , , |
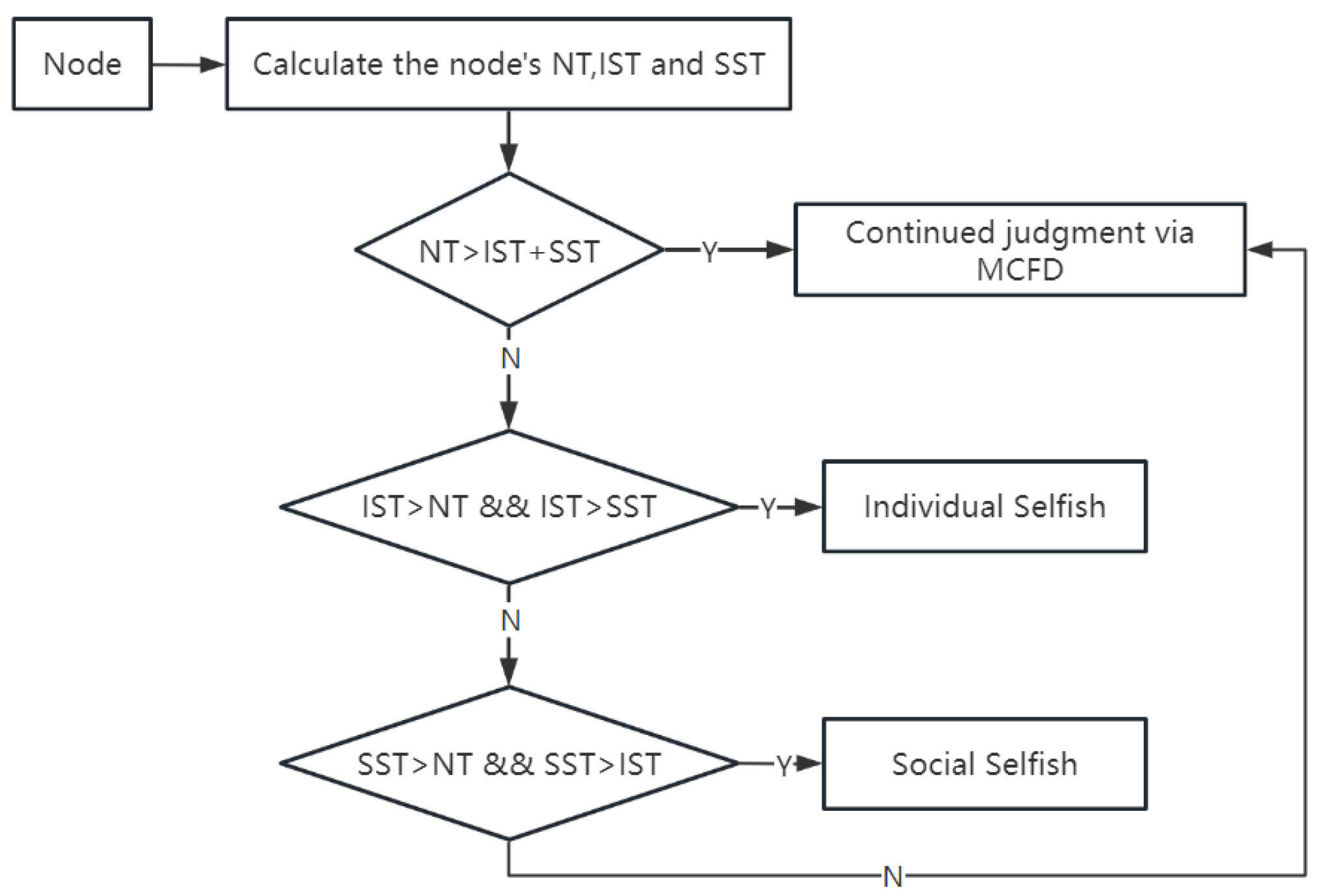
4.2.4. Node Social Trust Discrimination Rules
- (1)
- If , it indicates that node i has less probability of being a selfish node, excluding individual selfishness and social selfishness. It will continue to be judged more deeply through the message confirmation feedback detection (MCFD) mechanism.
- (2)
- If and , it indicates that node i is individually selfish and is marked as selfish. Otherwise, it proceeds to the judgment of rule (3).
- (3)
- If and , it indicates that node i is socially selfish and is marked as selfish. Otherwise, it continues to be judged more deeply through the message confirmation feedback detection (MCFD) mechanism.
| Algorithm 4 STD Algorithm |
| Input: , , Output: Boolean value 1: if then 2: Apply the MCFD algorithm to judge 3: else if and then 4: Boolean value = YES and i is an individually selfish node 5: else if and then 6: Boolean value = YES and i is a socially selfish node 7: end if |
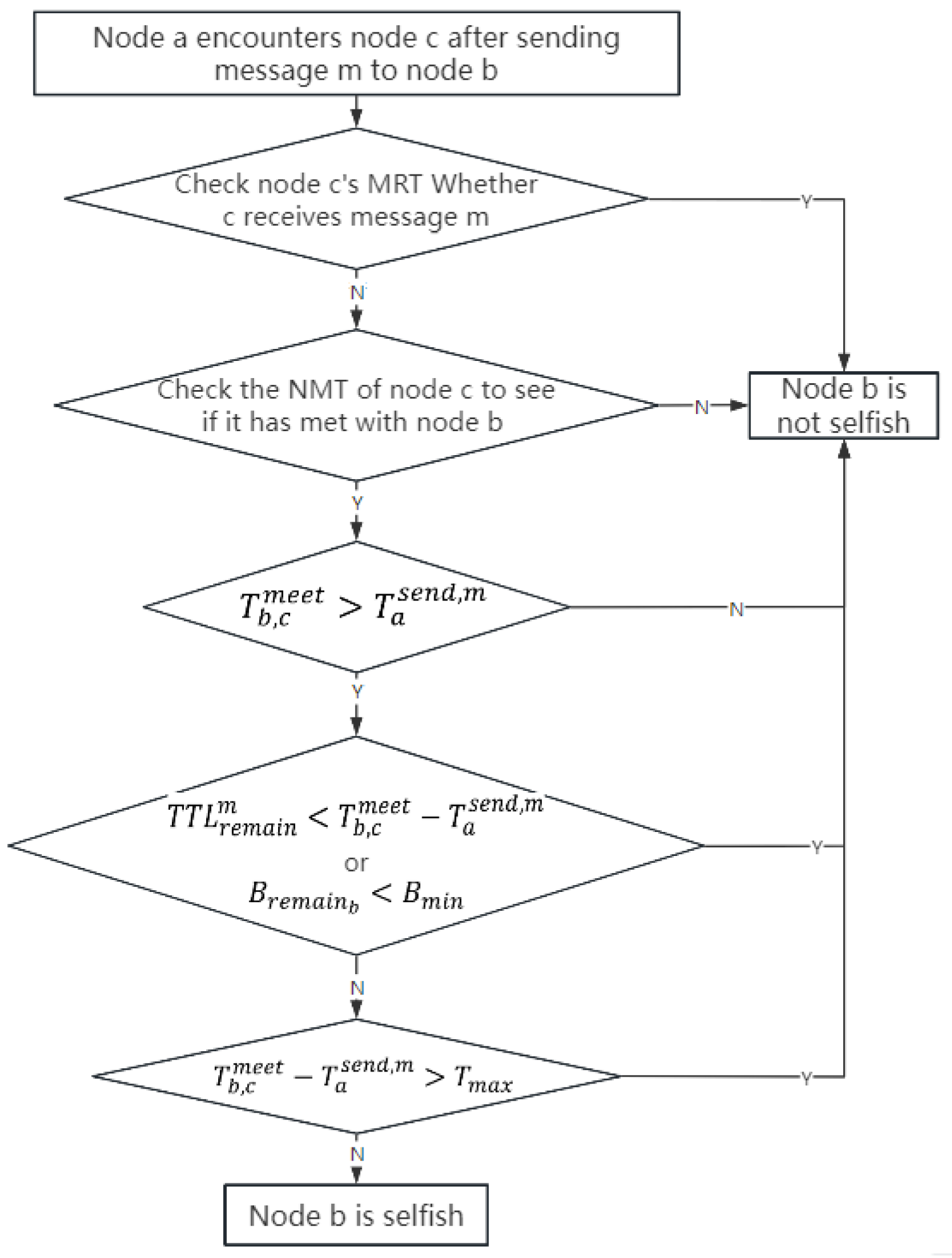
4.3. Message Confirmation Feedback Detection Mechanism (MCFD)
| Algorithm 5 MCFD algorithm |
| Input: , , , , Output: Boolean Value 1: if then 2: Boolean Value = NO 3: else if then 4: Boolean Value = NO 5: else if then 6: Boolean Value = NO 7: else if or then 8: Boolean Value = NO 9: else if then 10: Boolean Value = NO 11: else 12: Boolean Value = YES 13: end if |
5. Experimentation and Simulation
5.1. Simulation Parameters and Environment Settings
5.2. Simulation Scenarios and Performance Parameters
- (1)
- S+STCDA scheme: The network contains selfish nodes, and selfish behavior is identified using the STCDA detection method. The impacts of varying experimental conditions are analyzed by modifying experimental variables.
- (2)
- S+CCSDA scheme: The network includes some selfish nodes, identified using the CCSDA detection method. The effects are assessed by tweaking the experimental parameters as necessary.
- (3)
- S+DSNDA scheme: The presence of selfish nodes in the network is acknowledged, and their detection is facilitated by the DSNDA detection method. Observations of simulation outcomes are made by adaptively changing relevant experimental parameters.
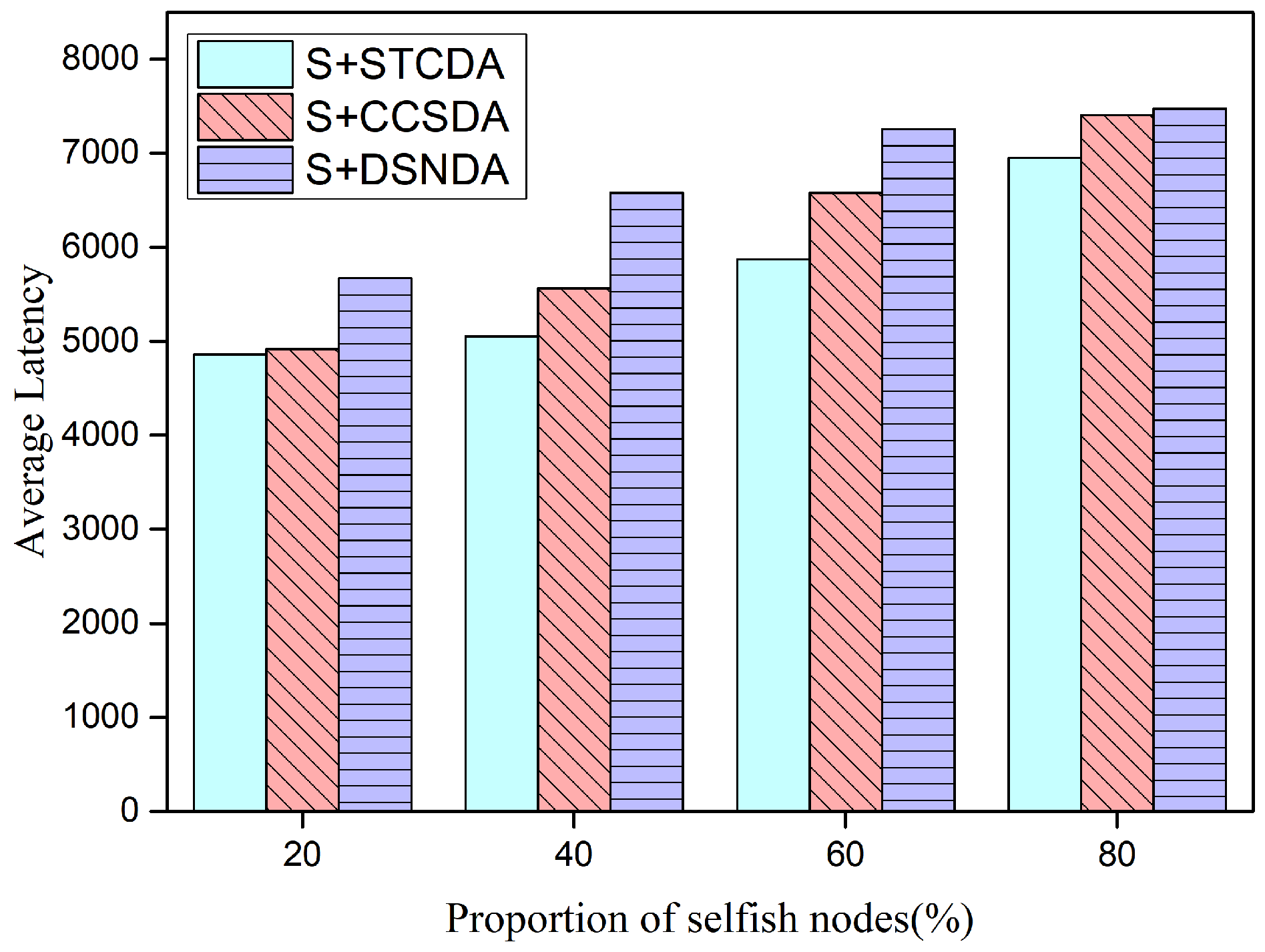
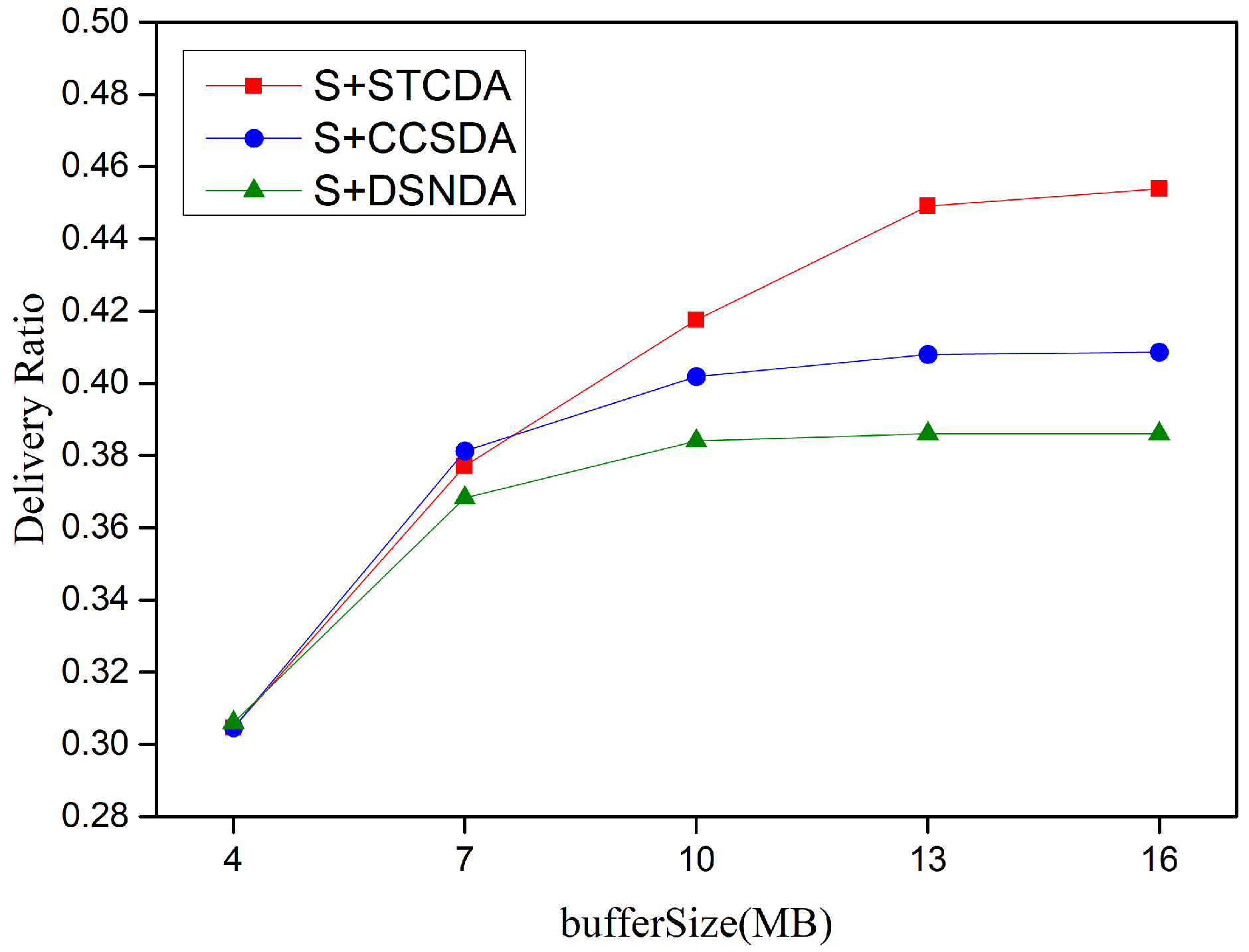
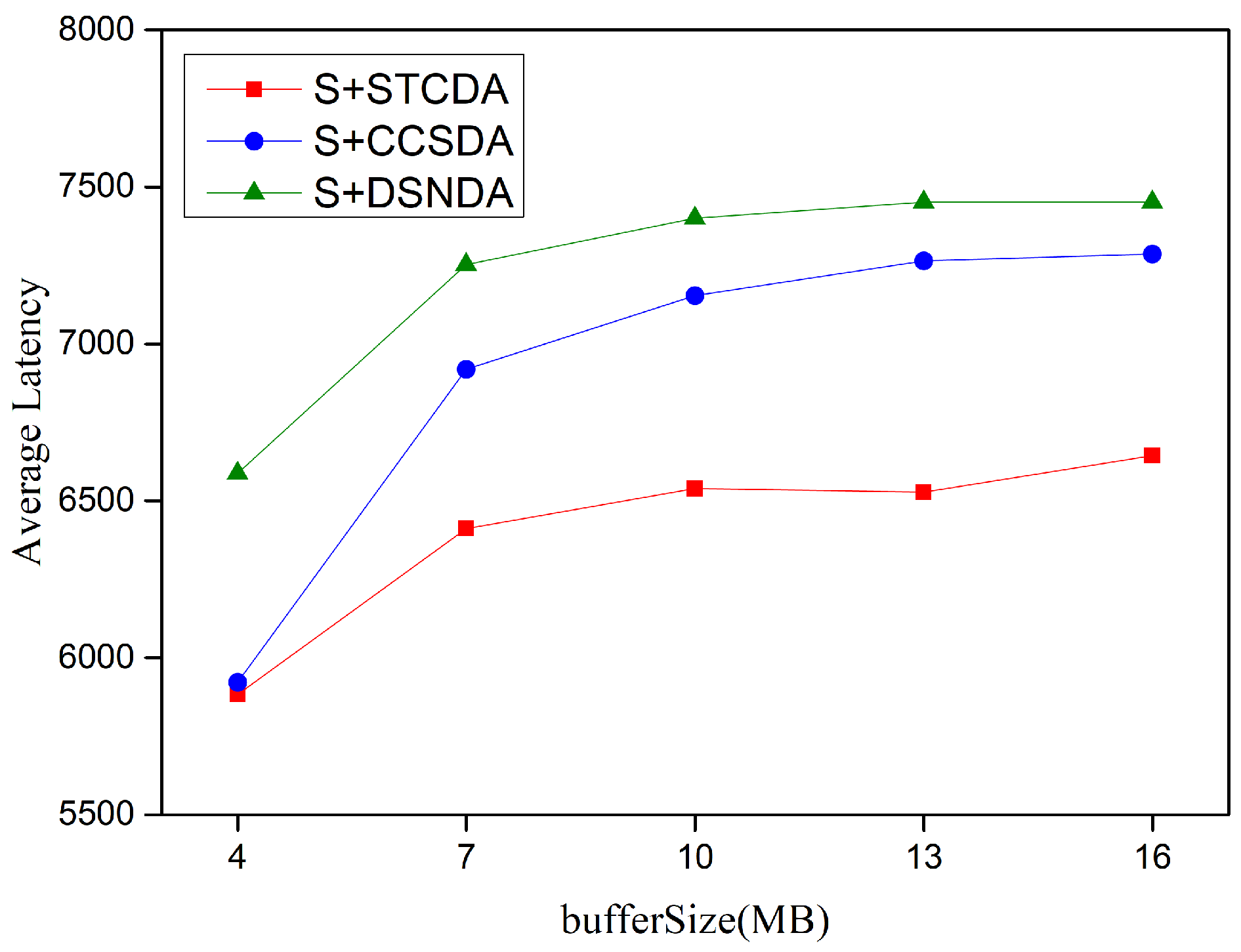
5.3. Simulation Results and Performance Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rappaport, T.S. Wireless Communications: Principles and Practice; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Hassani, S.; Dackermann, U. A Systematic Review of Advanced Sensor Technologies for Non-Destructive Testing and Structural Health Monitoring. Sensors 2023, 23, 2204. [Google Scholar] [CrossRef] [PubMed]
- Howard, J.; Murashov, V.; Cauda, E.; Snawder, J. Advanced sensor technologies and the future of work. Am. J. Ind. Med. 2021, 65, 3–11. [Google Scholar] [CrossRef] [PubMed]
- Xia, F.; Liu, L.; Li, J.; Ma, J.; Athanasios, V. Socially-Aware Networking: A Survey. IEEE Syst. J. 2015, 9, 904–921. [Google Scholar] [CrossRef]
- Puri, P.; Singh, M.P. A survey paper on routing in delay-tolerant networks. In Proceedings of the 2013 International Conference on Information Systems and Computer Networks, Mathura, India, 9–10 March 2013; pp. 215–220. [Google Scholar]
- Liu, W.; Sidhu, A.; Beacom, A.M.; Valente, T.W. Social network theory. Int. Encycl. Media Eff. 2017, 1, 1–12. [Google Scholar]
- Tsugawa, S. A survey of social network analysis techniques and their applications to socially aware networking. IEICE Trans. Commun. 2019, 102, 17–39. [Google Scholar] [CrossRef]
- Xu, F.; Xu, Q.; Xiong, Z.; Xiao, N.; Xie, Y.; Deng, M.; Hao, H. Intelligent distributed routing scheme based on social similarity for mobile social networks. Future Gener. Comput. Syst. 2019, 96, 472–480. [Google Scholar] [CrossRef]
- Xu, F.; Xiao, N.; Deng, M.; Xie, Y.; Xiong, Z.; Xu, Q. Efficient opportunistic routing with social context awareness for distributed mobile social networks. Concurr. Comput. Pract. Exp. 2019, 34, 472–480. [Google Scholar] [CrossRef]
- Memon, S.; Olaniyan, R.; Maheswaran, M. Towards a Model for Intelligent Context-Sensitive Computing for Smart Cities. In Handbook of Smart Cities: Software Services and Cyber Infrastructure; Springer: Berlin/Heidelberg, Germany, 2018; pp. 205–226. [Google Scholar]
- Yan, M.; Chan, C.A.; Gygax, A.F.; Yan, J.; Campbell, L.; Nirmalathas, A.; Leckie, C. Modeling the total energy consumption of mobile network services and applications. Energies 2019, 12, 184. [Google Scholar] [CrossRef]
- Dai, W.; Qiu, M.; Qiu, L.; Chen, L.; Wu, A. Who moved my data privacy protection in smartphones. IEEE Commun. Mag. 2017, 55, 20–25. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Zhao, H.; Sun, X. Resource management in sustainable cyber-physical systems using heterogeneous cloud computing. IEEE Trans. Sustain. Comput. 2017, 3, 60–72. [Google Scholar] [CrossRef]
- Wang, E.K.; Chen, C.M.; Yiu, S.M.; Hassan, M.M.; Alrubaian, M.; Fortino, G. Incentive evolutionary game model for opportunistic social networks. Future Gener. Comput. Syst. 2020, 102, 14–29. [Google Scholar] [CrossRef]
- Xiao, N.; Song, K.; Deng, M.; Xiong, Z.; Xu, Q.; Xu, F. A study of incentives for selfish nodes in opportunity networks. J. Hubei Eng. Coll. 2020, 40, 9. [Google Scholar]
- Xu, F.; Lyu, Y.; Ahmed, M.; Xiong, Z.; Deng, M.; Wang, W.; Khan, U.S.; Jiang, S.; Liang, C. Improving routing performance in social internet of things with FNRA: The free node-based approach. Alex. Eng. J. 2024, 88, 68–79. [Google Scholar] [CrossRef]
- Xiong, Z.; Zeng, M.; Zhang, X.; Zhu, S.; Xu, F.; Zhao, X.; Wu, Y.; Li, X. Social similarity routing algorithm based on socially aware networks in the big data environment. J. Signal Process. Syst. 2022, 94, 1253–1267. [Google Scholar]
- Xu, Q.; Deng, M.; Xu, F.; Zhao, X.; Li, Z.; Xiong, Z.; Xiao, N.; Zhao, G.; Liu, Z. Routing Scheme Based on Community Correlation in Socially Aware Networking. IEEE Access 2020, 8, 208358–208367. [Google Scholar] [CrossRef]
- Li, Q.; Zhu, S.; Cao, G. Routing in socially selfish delay tolerant networks. In Proceedings of the 2010 Proceedings IEEE Infocom, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Li, Y.; Su, G.; Wang, Z. Evaluating the effects of node cooperation on DTN routing. AEU-Int. J. Electron. Commun. 2012, 66, 62–67. [Google Scholar] [CrossRef]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected Ad Hoc Networks; Technical Report; Duke University: Durham, NC, USA, 2000. [Google Scholar]
- Wang, R.; Wang, Z.; Ma, W.; Deng, S.U.; Huang, H. Epidemic routing performance in DTN with selfish nodes. IEEE Access 2019, 7, 65560–65568. [Google Scholar] [CrossRef]
- Shan, A.; Fan, X.; Zhang, X. Quantitative study on impact of node selfishness on performance of MANETs. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things (SmartIoT), Beijing, China, 14-16 August 2020; pp. 9–14. [Google Scholar]
- Marti, S.; Giuli, T.J.; Lai, K.; Baker, M. Mitigating routing misbehavior in mobile ad hoc networks. In Proceedings of the International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 255–265. [Google Scholar]
- Hernández-Orallo, E.; Olmos, M.D.S.; Cano, J.C.; Calafate, C.T.; Manzoni, P. A fast model for evaluating the detection of selfish nodes using a collaborative approach in MANETs. Wirel. Pers. Commun. 2014, 74, 1099–1116. [Google Scholar] [CrossRef]
- Balakrishnan, K.; Deng, J.; Varshney, V.K. TWOACK: Preventing selfishness in mobile ad hoc networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, New Orleans, LA, USA, 13–17 March 2005; Volume 4, pp. 2137–2142. [Google Scholar]
- Liu, K.; Deng, J.; Varshney, P.K.; Balakrishnan, K. An Acknowledgment-Based Approach for the Detection of Routing Misbehavior in MANETs. IEEE Trans. Mob. Comput. 2007, 6, 536–550. [Google Scholar] [CrossRef]
- Bigwood, G.; Henderson, T. IRONMAN: Using social networks to add incentives and reputation to opportunistic networks. In Proceedings of the IEEE Third International Conference on Social Computing (SocialCom), Boston, MA, USA, 9–11 October 2011; pp. 65–72. [Google Scholar]
- Jedari, B.; Xia, F.; Chen, H.; Das, S.K.; Tolba, A.; Zafer, A.M. A social-based watchdog system to detect selfish nodes in opportunistic mobile networks. Future Gener. Comput. Syst. 2019, 92, 777–788. [Google Scholar] [CrossRef]
- Fayaz, M.; Mehmood, G.; Khan, A.; Abbas, S.; Fayaz, M.; Gwak, J. Counteracting selfish nodes using reputation based system in mobile Ad Hoc networks. Electronics 2022, 11, 185. [Google Scholar] [CrossRef]
- Xiao, N.; Xinyi, R.; Xiong, Z.; Xu, F.; Zhang, X.; Xu, Q.; Zhao, X.; Ye, C. A diversity-based selfish node detection algorithm for socially aware networking. J. Signal Process. Syst. 2021, 93, 811–825. [Google Scholar] [CrossRef]
- Xiong, Z.; Li, X.; Zhang, X.; Deng, M.; Xu, F.; Zhou, B.; Zeng, M. A comprehensive confirmation-based selfish node detection algorithm for socially aware networks. J. Signal Process. Syst. 2023, 92, 1371–1389. [Google Scholar] [CrossRef]
- Keranen, A. Opportunistic Network Environment Simulator; Special Assignment Report; Helsinki University of Technology, Department of Communications and Networking: Espoo, Finland, 2008. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and wait: An efficient routing scheme for intermittently connected mobile networks. In Proceedings of the 2005 ACM SIGCOMM Workshop On Delay-Tolerant Networking, Philadelphia, PA, USA, 26 August 2005; pp. 252–259. [Google Scholar]



| Parameter | Value |
|---|---|
| Simulation time | 12 h |
| Number of nodes | 180 |
| Simulation area | 4500 m × 3400 m |
| Transmit speed | 250 kB/s |
| Transmit range | 10 m |
| Movement model | ShortestPathMapBasedMovement |
| Routing protocol | Spray and Wait |
| Buffer size | 10 M |
| Movement speed | 0.5 m/s to 1.5 m/s |
| Message TTL | 300 min |
| Message creation interval | 25 s–35 s |
| Message Size | 500 kB–1 MB |
| 0.5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, X.; Rao, Y.; Xiong, Z.; Li, Y.; Zhang, X.; Hou, D.; Lou, Q.; Li, J. Social Trust Confirmation-Based Selfish Node Detection Algorithm in Socially Aware Networks. Electronics 2024, 13, 3797. https://doi.org/10.3390/electronics13193797
Chen X, Rao Y, Xiong Z, Li Y, Zhang X, Hou D, Lou Q, Li J. Social Trust Confirmation-Based Selfish Node Detection Algorithm in Socially Aware Networks. Electronics. 2024; 13(19):3797. https://doi.org/10.3390/electronics13193797
Chicago/Turabian StyleChen, Xiaowen, Ying Rao, Zenggang Xiong, Yuan Li, Xuemin Zhang, Delin Hou, Qiangqiang Lou, and Jing Li. 2024. "Social Trust Confirmation-Based Selfish Node Detection Algorithm in Socially Aware Networks" Electronics 13, no. 19: 3797. https://doi.org/10.3390/electronics13193797
APA StyleChen, X., Rao, Y., Xiong, Z., Li, Y., Zhang, X., Hou, D., Lou, Q., & Li, J. (2024). Social Trust Confirmation-Based Selfish Node Detection Algorithm in Socially Aware Networks. Electronics, 13(19), 3797. https://doi.org/10.3390/electronics13193797






