Abstract
This study proposes a new approach and explores how pattern recognition enhances collaboration between users and Agile teams in software development, focusing on shared resources and decision-making efficiency. Using domain-specific modeling languages (DSMLs) within a security-by-design framework, the research identifies patterns that support team selection, effort estimation, and Agile risk management for Afghanistan’s ministries. These patterns align software development with governmental needs by clarifying stakeholder roles and fostering cooperation. The study builds on the p-mart-Repository-Programs (P-MARt) repository, integrating data mining, algorithms, and ETL (Extract, Transform, Load) processes to develop innovative methodologies. These approaches enable dynamic knowledge management, refine documentation, and improve project outcomes. Central to this effort is our new Pattern Shared Vision Refinement (PSVR) approach, which emphasizes robust collaboration, data security, and adaptability. By addressing challenges unique to governmental operations, PSVR strengthens Agile practices and ensures high-quality software delivery. By analyzing historical trends and introducing new strategies, the study underscores the critical role of pattern recognition in aligning development processes with organizational goals. It demonstrates how systematic pattern identification can optimize interaction and secure stakeholder consensus, ultimately enhancing software engineering outcomes in Afghanistan’s governmental context.
1. Introduction
The transformative environment in Afghanistan has fueled the challenging convergence of state structure and the great potential for the IT sector. Filling the gaps allows for adequate solutions that relate to agile methods that possess the characteristics of cooperation, adaptability and providing iterative improvement. The political shift in Afghanistan since 2021, marked by the Taliban’s rise and the suppression of US-aligned governance, has led to a restrictive economy and significant human rights violations. The denial of education and employment for women and children, alongside restrictions on information flow, has deepened economic fragility. This upheaval mirrors challenges in software development, where disrupted systems and a lack of access to resources hinder innovation and growth [1]. The new circumstances left little room for connecting information technology knowledge with the country’s economy.
The constrained environment in development can be restarted with an agile approach by involving stakeholders and achieving incremental progress. This approach will simplify the integration of IT solutions with the needs of the specific Afghan administration. The Agile approach is widely applied in different industries [2], from small businesses to large companies, to build high-quality software products. This approach is used to implement projects in various requirement domains. The success of the Agile approach depends on well-organized strategy and responsibilities [3,4] where we can establish successful collaboration and manage groups on a commercial and academic level [5,6,7]. Companies want competitive strategies to stay ahead, while organizations want greater programming capabilities and tools to enhance future projects [8,9]. Several more issues in Agile involve the growth of team activities to meet user objectives [10]. User contributions are essential to the project’s success [11,12].
Accessing and exchanging resources between users and Agile teams was frequently uncoordinated, resulting in incompatibilities between project outcomes and user expectations. This imbalance produced dissatisfaction among both users and development teams. Agile teams must constantly review and improve iterations to ensure that the product meets the standards of quality and user satisfaction. Where improved communication and collaboration promote innovation, it enables firms to respond quickly to changing software development requirements and the evolution of knowledge management over time.
In Afghanistan, web/mobile applications were required to address difficulties in governance, service delivery, and operational efficiency. These programs were created to accelerate operations, improve communication, and offer digital platforms for public services. To achieve these requirements, developers used technologies such as C#, ASP.NET Core 6, Java, and Python. The resulting applications covered land registration, financial management, statistical information, human resources, inventory, and specialized tools such as agricultural geoportals. These applications were designed to help with daily ministry chores using geographic information system (GIS) capabilities with geographic information system (QGIS) tools for spatial analysis and mapping. They also provide a statistical report to senior management in ministries [13,14]. The teams also coordinated the back-end and front-end components to create a consistent user experience and to monitor the ministry’s daily data flow. During the development phase, the Agile team communicated with users to gather requirements, test systems, deploy them, and build solutions [14]. The Agile team works to ensure that the project the software is successfully implemented in the development project. A deep understanding of business requirements, a strong commitment, and shared responsibility between end users and Agile teams are essential [15].
Key roles in this environment include delivery managers, product owners, scrum masters, developers, testers, UX designers, and business analysts [16]. Each role brings a unique contribution, from the refinement of requirements to the delivery of a product that meets the expectations of ministries, stakeholders, and end users alike. Shared responsibilities in these projects include requirements gathering, usability testing, and user feedback sessions. Other services between users and Agile teams include user training, user acceptance testing (UAT), and continuous integration/continuous deployment (CI/CD) [17,18,19,20].
Teams in Afghan ministries actively engage in documentation, feature prioritization, and bug tracking to improve collaboration across departments. These practices were adopted to encourage cross-functional support and organize teams. Clear definitions of responsibilities, particularly in areas like feedback gathering, are crucial for effective collaboration between end users and development teams. This paper examines approaches to enhance cooperation during software development and project implementation. Four ministries—electricity, agriculture, education, and higher education—have implemented software projects to improve communication and meet project needs. Tools like the Glacier System, the Statistical Information System, and GIS applications for agriculture were developed to collect data for decision-making and planning. These tools primarily serve ministry staff, facilitating interdepartmental coordination and internal services.
The focus of this study is to examine how iterative development methodologies and decision making can be adapted to enhance IT integration within Afghan government sectors, addressing the challenges of applying traditional practices in resource-limited, volatile environments [21]. The study aims to find and propose adapted techniques for analyzing essential later investment analysis approaches that might increase coordination, scalability, and user participation while taking into account Afghanistan’s particular cultural, infrastructure, and security restrictions. In addition, it seeks to develop new approaches for integrating diverse technologies and defining success metrics specific to public-sector applications.
There are several techniques for gathering specialized information on the research topic. In this manner, we intend to employ research questions to guide the path of this study. More thorough information about the research approach is offered in Section 3, Materials and Methods. As a result of our thorough research, we have identified certain topics as the focus of our investigation; therefore, we would like to get clarification on the following questions:
- What is the historical aspect of software development and the progression of knowledge in connection to modern methodologies?
- How can domain-specific modeling languages (DSMLs) be employed to suggest a security-by-design approach for pattern identification?
- How can applying organizational or design patterns help to address the challenges between an Agile team and its users on case inquiries for Afghanistan’s ministries?
- What is the impact of sequential pattern mining on acquiring pertinent results from targeted pattern mining?
The objective of this research is to explore how flexible development practices can be better implemented to meet the needs of Afghan ministries, improve resource use, and foster effective collaboration [22,23]. To ensure the success of software deployment, users and development teams must work together. Strong communication skills, resource management, and teamwork are required to align software solutions with government policies. As highlights, we would like to emphasize exploitative practices in software development, focusing on user-centered tactics and cost-effective, culturally relevant methods for overcoming resource and infrastructure restrictions in Afghanistan. However, a lack of coordination in resource use led to mismatches between project outcomes and user expectations, resulting in frustration and dissatisfaction with the approach of the development team.
The contributions of this study include the following:
- As a first contribution, we can present a summary of the exploitative progress in the field of software engineering, which is connected to certain patterns and software designs.
- The second contribution in Section 6.5 is a suggestion of our new organizational pattern, indicated as Pattern Shared Vision Refinement (PSVR). We would like to build user and Agile team collaboration based on software needs and specifications for Afghanistan’s Ministries. The proposed approach is used for implementation needs in environments that have limited resources and application possibilities, as well as complexity dictated by several different sides.
- The next contribution is that we analyzed the association of the pattern to build effective communication between stakeholders based on an analysis of existing dataset p-mart-Repository-Programs (P-MARts).
- The final contribution would be a pattern identified for project implementation-related challenges in user–Agile team cooperation. This should provide a generic and proven strategy as the best possible solution for more shared services between ministries in Afghanistan.
To better lead our extensive research, we created the following organizational framework, which divides the research into clearly defined sections, each covering a specific aspect of the topic. The introduction examines the context background in Afghanistan in relation to the limited computer hardware surroundings, contributions, questions, and objectives, while the literature review Section 2 provides context by summarizing relevant studies. The materials and methodologies Section 3, describes the methodologies and tools used for the realization of the research. Section 4 on software development and knowledge management progression examines technology implementation and advancements in processes concerning knowledge collection and Agile management techniques. Section 5, a case study: the challenges of the ministries in Afghanistan in the collaboration for software development, examines the case study with specific challenges encountered by Afghanistan’s ministries in collaborative software development. The findings are reported in the results Section 6, followed by the limitations, which highlight the study’s constraints which refer to the state system in Afghanistan and our proposed methods. The discussion Section 7, evaluates the findings, while the conclusion summarizes key takeaways and potential implications with the relevant future research.
2. Literature Review
The literature review part is intended to describe recent advances in our research field. We aim to discuss historical qualities and how they apply to present approaches to have a better understanding of aspects and difficulties related to software patterns across history. The historical context will be briefly reviewed, with an emphasis on the most crucial events in the exploitation revolution for software engineering and development. That is why we looked at older sources in the literature while also using the most recently disclosed data. This section examines the efficiency of shared services between users and Agile teams in software development. This is a significant topic for modern project management.
Based on the knowledge gathered by Casola et al. [24], he created a novel security-by-design methodology that stresses modeling and analyzing security quantitatively using service-level agreements (SLAs). This methodology can help us with our research into assuring the security of shared services between users and Agile teams. To gain a better understanding of software development, we will quickly examine certain historical features and select the units that appear to be most relevant to our research. We will include some potential investigation methods, which are as follows:
- Software development in early phases in the 1950s and 1960s: Explore the beginnings of computing scientists in the 1950s and 1960s, including their development of the first programming languages and the challenges found by early programmers.
- Historical Aspects of Software Development: We try to provide a comprehensive overview of the growth of software engineering, including key milestones, important perspectives, and important developments.
- The Rise of Software Development Approach, Knowledge, and Progress from 2000 to Today: We discuss significant improvements in software development since 2000, such as the rise of Agile approaches, DevOps, and the growing use of artificial intelligence and machine learning.
- Software development principals in the late 1990s and early 2000s: Assess the significant developments that occurred in software development throughout the late 1990s and early 2000s, such as the rise of the Internet and the creation of web-based applications.
- Domain-Specific Modeling Language (DSMLs): Assess the importance and advantages of domain-specific modeling languages in software development.
2.1. Historical Aspect of Software Development
The historical aspect of the development of software products and the use of technologies has undergone major transformations. The changes that have affected this area have been accompanied by the establishment of multiple designs, approaches, and improved technologies. From the early organized methodologies to the presentation of Agile and collaborative methods, it achieved a constant pace of development. This section covers significant events in the history of software development, focusing on the move from old approaches to current improvements.
2.1.1. Early Phases in 1950s and 1960s
Software development has evolved, with significant improvements in both methodology and technology. Initially, as demonstrated by Saravanos and Curinga [25], the waterfall model dominated, offering a linear, regulated approach to software development. However, as Royce [26] recognized, this approach failed to meet changing needs, leading to the development of iterative methods such as the Boehm [27] spiral model.
Open-source software development transformed the industry in the 1990s. Raymond [28] suggested that open-source projects, such as Linux, demonstrated the value of community-driven decentralized development. This era included the growth of Agile approaches, which Beck et al. [4] supported for their iterative cycles and commitment to client participation, eventually evolving into the dominant approach in the early 2000s.
Software development has grown significantly since its inception in the mid-19th century. In the early phases, during the 1950s and 1960s, software was built ad hoc using assembly and machine languages, sometimes by the same people who designed hardware. Based on a study from Campbell-Kelly [29] we can see that programming was first viewed as more an art than a formal discipline, and the concept of systematic software development methods was not yet established. The 1950s and 1960s were key periods in the history of software development and innovations that set the foundations for modern software engineering.
According to Royce et al. [26], software development has a long history. High-level programming languages like Cobol, Fortran, and C made programming easier to learn in the 1970s and 1980s. They also discussed structured programming, which focuses on a clear logical flow to improve code clarity. Royce’s waterfall model, which provided a linear method with defined phases for development, was criticized for its inflexibility in dealing with changes.
In a later period, Boehm’s spiral model [27] was established, which addressed some of the problems in software development by including iterative analysis into the development process. Its purpose was to address the shortcomings of the waterfall paradigm by encouraging prototyping, which resulted in better flexibility in meeting changing customer requirements. The spiral model has considerable advantages over other techniques since it incorporates an iterative sequential procedure that can be applied to even the most complicated software projects. The key advantage of the aforementioned strategy is the ability to manage risks and budgets effectively.
2.1.2. Late 1990s and Early 2000s
Agile approaches were introduced in the late 1990s and early 2000s, resulting in organizational transformation. The Agile Manifesto was announced in 2001 by the Agile Alliance [4] by a group of software developers and thought leaders. The authors Hohl et al. [30] identified fundamental values such as individuals and interactions, working software, customer collaboration, and adaptability to inflexible processes and technologies. Agile frameworks such as Scrum, Kanban, and Extreme Programming (XP) emphasized iterative development [3], flexibility, and close collaboration [6,31] with users and stakeholders, addressing the limitations of the previous model, adapting through continual planning, early deliveries, continuous improvements, and collaborative culture.
Software development has changed with new methods and technology, with the introduction of DevOps principles, which bridge the gap between development and operations teams to provide continuous delivery and integration. When integrated with Agile approaches, Bass et al. [32] covered how DevOps provides a comprehensive approach to software development that indicates collaboration, automation, rapid feedback, and continuous improvement, allowing teams to deliver value more quickly and efficiently. The emphasis has changed to providing high-quality software that meets the needs and expectations of users, with a focus on user-centric and collaborative development techniques.
Other effective process models, such as the Unified Process Model (UPM), established by Ivar Jacobson [33], Grady Booch, and James Rumbaugh and launched in the late 1990s, provide a structured approach to assigning tasks and responsibilities inside a development organization. It indicates iterative development, use-case-driven design, and risk management, which improve flexibility and adaptation to changing requirements. The first operating systems, such as the Compatible Time-Sharing System (CTSS) [34] and Atlas [35], were developed during the 1960s. These systems introduced the concept of time-sharing, allowing numerous users to connect to a computer at once. Software engineering originally appeared at the NATO Conference on Software Engineering in 1968. As noted by Naur and Randell (1969) [36], software development evolved from an ad hoc activity to a systematic engineering methodology.
An Agile approach to software development that promotes dynamic improvement is defined as an Extreme Programming (XP) approach that covers customer needs in shorter development phases. The mentioned approach was created by Kent Beck [37] in the late 1990s and introduces milestones that respond to changing customer needs. XP promotes approaches such as pair programming, test-driven development, and continuous integration.
Lean Software Development, as described by Mary and Tom Poppendieck [38], is based on lean manufacturing ideas and focuses on improving value through waste reduction, improved flow, and team empowerment. By emphasizing flexibility and ongoing improvement in the software development process, this strategy emphasizes rapidly producing value. Another approach is called feature-driven development (FDD), which is an incremental and iterative software development technique that combines several industry-accepted best practices. Although, Palmer and Felsing [39] covered how to support controlled, rapid, and predictable iterations and improve communication between developers and users. Feature-based planning and domain object modeling are essential components of FDD. Pioneering software development refers to the efforts of Alan Turing, John Von Neumann, and Gracie Hopper in 1936 [40] in the early stages of software development and their growth. Their ideas and contributions to the computer science community, programming languages, tools, and software engineering have opened the door for future technological advances.
2.2. Evolution of Agile Methods from 2000 to Today (2024)
Larusdottir et al. [41] discussed the process of selecting the best Agile team to develop a web service by evaluating performance factors and estimated costs. This approach can be applied to determine the most suitable team for projects that involve shared services between users and Agile teams, ensuring efficient collaboration and successful outcomes. Melnyk et al. [42] focused on decision support technology for sprint planning in software development. The emphasis was on the importance of planning and risk management in Agile methodologies such as Scrum.
Implementing this technology can enhance the planning process for shared services between users and Agile teams, leading to more effective project execution. Altaleb et al. [43] highlighted the importance of effort estimation in software development, particularly in Agile processes. Their proposed estimation technique can be utilized to improve the accuracy of planning and resource allocation for projects involving shared services between users and Agile teams. Muntes Mulero et al. [44] argued and discussed Agile risk management for multi-cloud software development, emphasizing the challenges and proposed frameworks for managing risks in Agile environments. The implementation of Agile risk management principles can increase the overall effectiveness of shared services between users and Agile teams in software development projects. Integrating the insights and methodologies presented in the literature can contribute to the effectiveness of shared services between users and Agile teams, using security-by-design methodologies, choosing the finest Agile teams, and leveraging decision support technology. By improving effort estimation approaches and using agile risk management tactics, businesses can improve cooperation and project outcomes in the setting of shared services.
Modern technological developments have significantly changed software development. Fowler and Lewis [45] underlined the shift to microservices and cloud computing, which allowed for more scalable and adaptable software architectures. Furthermore, as Karamitsos et al. [46] explained, integrating DevOps methods improved collaboration between the development and operations teams, allowing faster delivery cycles. Finally, Harman [47] explored the role of AI and big data in automating processes and improving decision making, demonstrating the continuous development of the field. Domain-Specific Modeling Languages (DSMLs) have drawn considerable amounts of interest in the field of software engineering because of their ability to abstract and simplify challenging domain notions. Kleppe et al. [48] suggest the integration of DSMLs into the Model-Driven Architecture (MDA) to facilitate model generation that is closely aligned with certain domains. This study demonstrates how DSMLs improve efficiency by promising that models are intelligible and maintainable by domain experts.
2.2.1. Early Form of DSMLs
Van Deursen and Klint [49] defined the concept of “little languages”, which could be considered an early form of DSMLs. They maintain that by offering domain-specific abstractions, these specialized languages facilitate software development and maintenance, reducing the complexity of domain-specific applications [49]. Kelly and Tolvanen [50] investigate the role of DSMLs in the generation of complete code, highlighting improvements in productivity and accuracy in software development when working at a higher level of abstraction closer to the problem domain.
2.2.2. Overview of the Fundamental DSMLs
Using DSMLs ensures that security features are integrated early in the development process. DSMLs, tailored to specific domains, facilitate the efficient modeling of security aspects such as encryption, authentication, and access control. This approach ensures that security is prioritized from the start, enhancing system resilience and reducing the risk of vulnerabilities.
Voelter [51] provides a full overview of the fundamental DSMLs of the engineering process, describing how they could be customized for various domains concerning expressiveness and usefulness. This is compatible with the Model-Driven Engineering (MDE) principles defined by Schmidt [52], who shows how DSMLs assist in MDE through their tools for the design, analysis, and synthesis of complex software systems within specified domains.
Mernik et al. [53] described when and how to build DSMLs, emphasizing the decision-making process and advantages such as enhanced productivity and communication within the target area. A study by authors France and Rumpe [54] suggests a metamodel-based approach towards the integration of DSMLs, illustrating the role of metamodels in the interoperability and integration of DSML for more comprehensive modeling solutions.
2.2.3. Principles of DSML Design Patterns and Security
Spinellis’s [55] study describes the principles of DSML design patterns and contains helpful perspectives to build effective and reusable DSMLs that encapsulate domain knowledge while enhancing software modularity. Voelter and Visser [56] focus on the importance of modularization and composition in the design of DSMLs, highlighting the use of the Meta-Programming System (MPS) in the construction of modular and composable DSMLs.
Using a security-by-design framework, covered by Kreitz [57] incorporates security measures from the very beginning of the system development process, addressing potential vulnerabilities early and consistently. We see that this strategy develops more secure systems by incorporating features such as encryption, access control, and threat modeling from the start, lowering risks and increasing compliance. Since it appears to be widespread in software engineering, security is mostly taken care of between the design and testing phases.
2.2.4. Testing and Analyses with DSMLs
Software development, especially in testing, analyzes how DSMLs may simplify test case generation while enhancing the expressiveness of test scripts. Current research shows how DSMLs can bridge the gap between software requirements and testing procedures, thus improving the software quality assurance process [58]. According to the literature studied, DSMLs provide important benefits in terms of abstraction, productivity, and maintainability in software development. However, the benefits remain in developing, implementing, and integrating DSMLs in such a way that they maximize their benefits while maintaining flexibility and usability within specified domains.
2.3. Visual Representation of the Literature Review
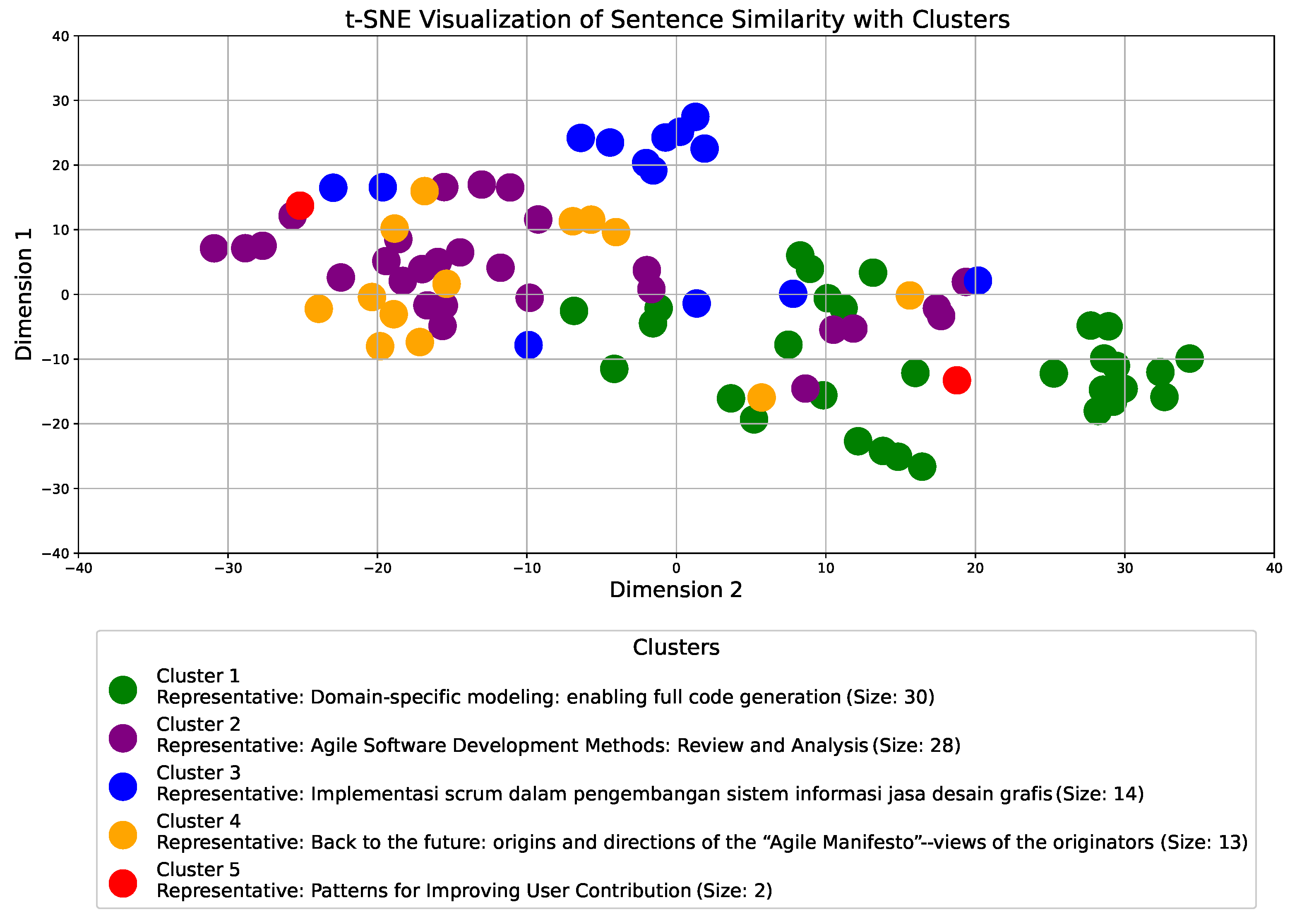
During the analysis of the issue, it was necessary to study a larger amount of the available literature due to the connection of the analyzed issue with various aspects of source code used in all sectors, not only computer science. We started from the definition in the paper by Hinton and Roweis [59], which established a method to project each point in a 2D space. It is based on the assumption that similar objects will be displayed close to each other. From the t-SNE similarity of the titles of the analyzed articles shown in Figure 1, we can confirm the assumption of a relatively even representation of scientific articles in the entire research area.
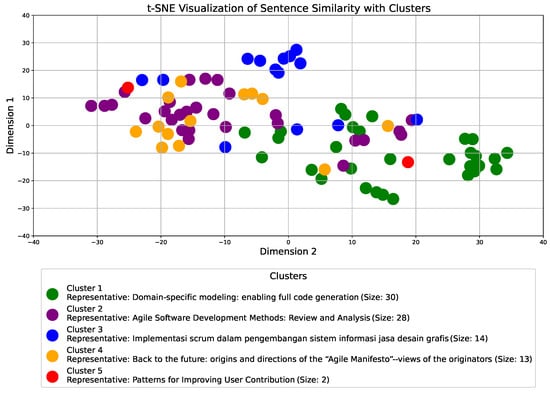
Figure 1.
Visualizing sentence similarity with clusters using the t-SNE. Source: author’s contribution.
The diagram in Figure 1 presents a t-SNE (t-distributed Stochastic Neighbor Embedding) visualization of sentence similarity derived from a bibtex file that contains all titles in the literature. The plot displays five distinct clusters, each represented by a different color, indicating groups of titles that share similar semantic meanings.
The x-axis (Dimension 2) and y-axis (Dimension 1) are bounded within a range of −40 to 40, offering a comprehensive perspective on the cluster distribution. Clusters are numbered sequentially based on size, starting with “Cluster 1” for the largest group. The legend provides a concise overview, displaying each cluster’s representative title alongside its size, which reflects the total number of titles within the cluster shown in Figure 1. The clusters are as follows:
- Cluster 1: The largest cluster, containing the most titles, represents a specific thematic grouping of the literature.
- Cluster 2: The second largest cluster, which may indicate a related but distinct theme from Cluster 1.
- Cluster 3: A smaller cluster that captures another unique aspect of the structure of the literature.
- Cluster 4: Represents a different thematic grouping, potentially overlapping with other clusters.
- Cluster 5: The smallest cluster, which may contain niche titles or themes.
Clusters are arranged with vertical spacing to improve visual separation, making it easier to identify and analyze relationships between groups. The legend, spanning the width of the diagram and positioned below the plot, ensures that all cluster details are clearly visible and accessible. Each legend entry includes the cluster number, a representative title, and the cluster size, offering a concise summary of each group’s content.
This visualization effectively reveals the relationships and thematic connections among the titles in the literature. The distinct cluster spacing and detailed legend enhance comprehension, allowing for a deeper exploration of patterns within the literature we have collected during the research.
3. Materials and Methods
The application of the research questions and the processing of the resulting data, which is public and available for research purposes under appropriate permissions, will serve as the foundation for the research strategy. This study uses empirical research methods to evaluate exploitative practices in software development in government software projects in Afghanistan.
Afghan administration and decision-making are profoundly influenced by historical events, economic conditions, cultural factors, and security challenges. Decades of conflict have restructured governance systems, requiring ministries to navigate fragmented administrative frameworks, ethnic complexities, and significant reliance on international aid. This context highlights the importance of studying methods on how software policies are shaped and implemented under such unique and often adverse circumstances. Examples include gender-sensitive education programs, and mobile health initiatives in conflict zones. Governance in Afghanistan often depends on inclusive stakeholder participation, decentralized decision-making, and balancing short-term crisis management with strategic growth.
To address this multifaceted context, we leveraged a dataset provided by the Ptidej Team, which was made publicly accessible via its GitHub repository, Ref. [60] p-mart-Repository-Programs (P-MARt). Licensed under the Lesser General Public License (LGPL) [61], the dataset, totaling 1.47 GB, is suited for research purposes without permitting the modification of the original data. Using this resource, the study employs a mixed-methods approach to explore the processes behind pattern identification comprehensively. Our empirical research focuses on analyzing exploitative patterns in software development and deployment, with an eye on their evolution over time and potential future trends. By applying widely recognized methodologies, we aim to generate insights that not only deepen the understanding of such patterns but also offer predictions to guide the field. This dual focus—on the current landscape and future opportunities—seeks to bridge gaps in knowledge, providing actionable findings for software systems and their implications in contexts like governance, where robust, adaptable systems are critical.
This study will take a mixed-methods approach, using the most commonly used approaches to acquire a full knowledge of the process of pattern identification. Through empirical research, we try analyzing exploitative patterns in software development and deployment across time, as well as future predictions for this area. For this study, we used time-series analysis and non-parametric methods to investigate a dataset from the P-MARt repository, a comprehensive program that supports empirical research on design patterns.
P-MARt contains micro-architectures, which depict design motifs as solutions to various design patterns and are derived from a variety of programs with publicly available code bases. Time-series analysis was utilized to discover trends and patterns in the data across time, but non-parametric methods gave robust insights that did not rely on tight distributional assumptions. This combination enabled us to effectively evaluate different, complicated micro-architectures while ensuring adaptability and accuracy in interpreting the dataset’s patterns and linkages.
3.1. Observation, Experimentation, and Data Collecting
This study approach uses research questions, observation, experimentation, and data collection to examine real-world events from various sources, including developer code. We look at empirical studies to identify distinct patterns, behaviors, and outcomes of exploitative software activities. During data collection and analysis, any sensitive information is eliminated, and the success of the planned software development process is evaluated. The main focus is on identification and the eventual possibility of creating a new pattern, which would help in more effective communication. That is why the paper contains several earlier sources of the literature. Their significance is shown in the relevance and established foundations that have previously contributed to the development of new techniques and methods of software development. Incorporating earlier sources of literature into our study, such as studies on exploitative software practices, is crucial for a variety of reasons.
The mention of data collection by observation necessitates additional clarity on how the observations were recorded. In this case, a structured observation was used to document crucial behaviors and interactions. To augment this, questionnaires and interviews were utilized to collect extra qualitative data, which provided deeper insights into participants’ contexts and experiences. This combination of methodologies resulted in a comprehensive and nuanced comprehension of the observed participants. Part of the findings were realized in the earlier study carried out by the authors Haiderzai and Khattab [62], and this research is a continuation of further research that may be carried out by looking at specific features that can connect and use the patterns.
They provide historical background, which helps to explain the evolution of practices and long-standing concerns across time. Older theories serve as the foundation for the present study, while long-term trends reveal recurring exploitative behaviors. That is why we will not do a thorough examination of all publications produced during specific periods. Instead, we will focus on those that we believe are relevant to our research. Since lessons from previous ethical quandaries can inform contemporary practices, historical precedents can serve as warning signs for ethical standards and teachers of life through the historical framework.
3.2. Use of Older Literature Sources
Examining older literature sources sheds light on early technical ideas, which aids in the comparative investigation of exploitative changes. Interdisciplinary perspectives broaden understanding, and examining prior materials can help discover gaps in current study. Finally, including these sources improves the academic rigor of the research and demonstrates a thorough mastery of the subject. Various tools, programming languages, and process models have evolved and supported industries and academia over antiquity, impacting modern software techniques that are highly efficient, collaborative, and adaptable across numerous platforms.
Throughout the investigation, we used both historical and contemporary materials. With these materials, we can demonstrate the transition from traditional processes to Agile ways that provide a thorough understanding of software development. Since they are participants in the development process, Agile team connections has an impact on modern development methods. All this together requires the creation of new approaches and patterns that can be directly applied in practice.
3.3. Visual Depiction of a Research Process
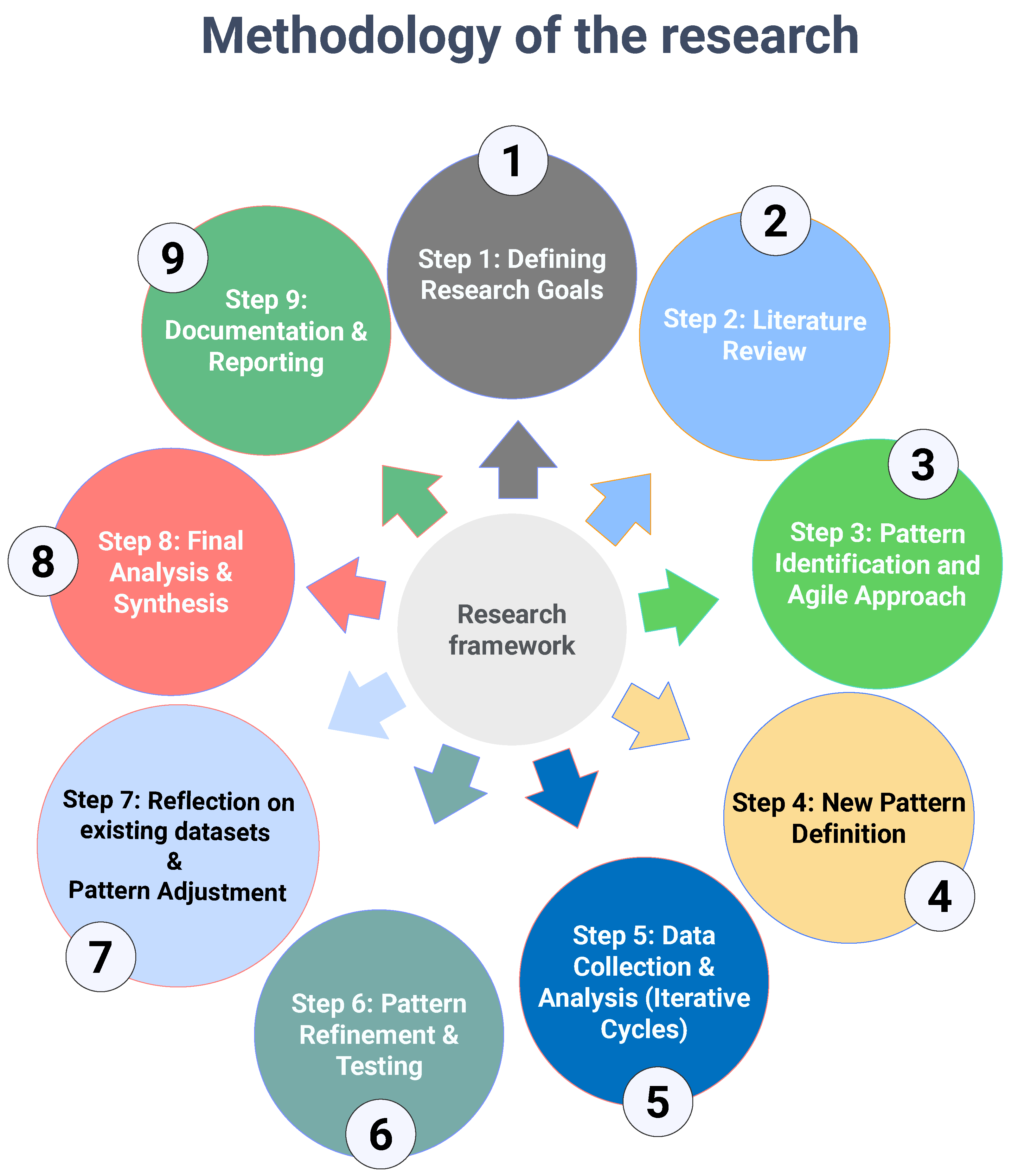
To effectively represent the study process, we will use a diagram that visually conveys its structure. This illustration emphasizes the step-by-step flow, capturing the iterative and adaptable nature inherent to Agile research methodologies. Key aspects of this approach will be highlighted, providing a clear and concise overview of the process, which can be seen in the schematic illustration in Figure 2.
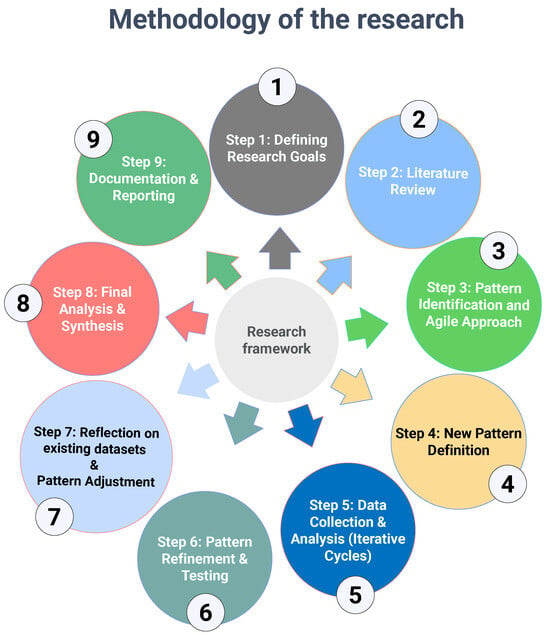
Figure 2.
Methodology of the research. Source: author’s contribution.
The research process is a dynamic and iterative journey that seeks to investigate and comprehend complicated phenomena systematically. This framework is based on an agAle, pattern-focused approach that prioritizes flexibility and iterative refinement to unearth valuable insights. The process, consisting of nine interconnected processes, begins with a clear statement of research aims and finishes with documenting and distributing findings.
This framework, which includes a comprehensive literature review, iterative data analysis, and pattern refining, enables researchers to modify and evolve their understanding in response to new data and discoveries. Each phase builds on the previous one, encouraging continual reflection and adjustment, ending in a rigorous and inventive synthesis of knowledge. This organized yet adjustable technique enables researchers to find, test, and refine patterns, resulting in significant insights for their field. Following those mentioned above, the conducted research was realized through the following steps:
- Step 1: Defining Research Goals
- Step 2: Review of the literature
- Step 3: Pattern Identification and Agile Approach
- Step 4: New Pattern Definition
- Step 5: Data Collection & Analysis (Iterative Cycles)
- Step 6: Pattern Refinement & Testing
- Step 7: Reflection on existing datasets & Pattern Adjustment
- Step 8: Final Analysis & Synthesis
- Step 9: Documentation & Reporting.
3.4. Selection Criteria
Regarding the selection criteria, we looked at several locations and views that we thought were important to our research. We conducted the investigation utilizing a variety of methodologies. As a result, the research will contain the following research types:
- Historical and empirical research: We will try to identify several methods of software development from the previous evolution that have had a significant impact on present methodologies, as well as the effective implementation of Agile techniques in modern software development.
- Case study: We examined real-world projects implemented in Afghanistan ministries that involved user and Agile team engagement, as well as practical application development in the organizations indicated in our research and in the execution of these methodologies. The process itself was realized through the introduction of new pattern methods, with the help of which it is possible to solve the problem of the communication and exchange of key information.
- Qualitative research: The research approach covers the analysis of users’ and Agile team observations and identifies the patterns that cover building their communication and collaboration and their impact on software quality.
To assess the documented patterns, project success metrics, user and Agile team feedback, satisfaction surveys, and communication efficiency assessments were conducted during the project implementation. Case studies in the ministries, user feedback iteration, and Agile metrics were utilized to evaluate software development team performance improvements and feature relevance, which was used as a parameter to measure the accomplished results.
3.5. Keywords
During our investigation, we have used some of the following keywords:
- Design and analysis of quality information for QA patterns;
- Data quality-driven design patterns for the Internet of Things;
- User and Agile team-related organizational patterns;
- Pattern association in the user working domain;
- Organizational patterns and software engineering;
- User and Agile team collaboration in software development for effective project implementation;
- Management and successful organization of teams using scrum and relevant methods.
Analysis with these carefully chosen keywords and their combination fills a knowledge gap concerning the structure and quality of patterns in software development, particularly under adverse external circumstances. The analysis techniques used also revealed hidden information that would not have been identified under standard analysis conditions without the keywords in question. An example can be the identification of patterns for quality control. Since this part is carried out in many ways and in a large amount of data, it is necessary to search for data about generally applicable design patterns that are hidden at first glance.
4. Software Development and the Progression of Knowledge Management
Every company initiative necessitates the organization of human resources, the maximization of their potential, and participation in certain projects. Project management takes on an important role in such instances. Agile management of human resources in project teams is a desirable leadership style [63]. All of the above necessitates the use of specific knowledge management approaches to ensure that all procedures are properly implemented inside a single software firm. Software development has expanded substantially over time, reflecting breakthroughs in knowledge management, particularly with the arrival of large-scale data. As firms strive for greater efficiency and agility, including knowledge management principles in software development processes have become critical [63,64]. This shift away from traditional management approaches enables teams to concentrate on less technical tasks while utilizing data-driven insights to detect penetration within systems and software [65].
Improved communication and collaboration promote innovation, allowing companies to respond quickly to changing needs [64,66]. As software development increasingly adopts Agile approaches, good knowledge management will be critical in optimizing processes and pushing the boundaries of what is feasible, ensuring that useful lessons are learned and utilized in future projects [67]. This is especially true in the information technology industry, where processes that have replaced traditional management methods must be updated regularly. Artificial intelligence, automation, digitalization, and large-scale data processing are all trends that have supplanted traditional business practices [67,68].
4.1. Traditional Management in IT Sector
Instead of traditional management, which was the leading way of doing business for a considerable period, there is an increasing amount of approaches using Agile business methods [69]. The IT sector aims to reduce risk through the use of the Scrum model. Although this model is significant in software applications, it has useful uses in the government sector and human resource management.
Agile teams include a smaller number of people who will solve specific technological and less technological tasks in the shortest possible time with as few errors as possible. From this arises the necessity of the strategic application of Agile project management. Agile project management changes the previous theory and practice of management by moving the boundaries from the traditional to the Agile principle of work [70,71]. The Scrum model is one of the leading and most popular software frameworks, including an Agile team, events, processes, and procedures [71,72].
4.2. Scrum Team, Benefits and Flaws
A scrum team consists of a scrum master, a product owner, and a development team, where the teams are highly self-organized, analytical, and functional [73]. To ensure the success of the scrum business, all team members must work to their utmost potential. Specifically, scrum volumes must be set aside and account for the time required to perform the activities as well as the task’s complexity. The scrum master is in charge of scheduling meetings and carrying out business procedures. The product’s owner must have a vision for its marketing, as well as comprehending the quantity that must be offered to the market. Regular updating of adequate information about the offer and requested products enables better positioning in the markets [74].
A thorough exploration of this shift is essential, as it highlights the key differences between traditional project management and Agile methodologies like Scrum. By thoroughly addressing these aspects, the study can provide a more comprehensive understanding of how to effectively implement Scrum, highlighting its advantages over traditional management methods and the potential benefits for project outcomes.
The move from traditional management to Scrum has received scant attention, leaving a huge vacuum in comprehending this transformative shift like in a pharmaceutical company [75]. Traditional management is based on hierarchy, strict phases, and thorough preparation, prioritizing predictability above adaptation. While it works well in static situations, it fails in dynamic ones. In contrast, Scrum values flexibility, cooperation, and iterative progress. It redefines success as adaptability and progress rather than strict obedience to a plan. Exploring this transformation exposes a broader ideological change—from control to empowerment, rigidity to resilience—highlighting how Scrum allows creativity in unpredictable, fast-paced projects [75,76].
The Agile Scrum method is gaining popularity among researchers year after year. According to a survey [77], the primary reason for Scrum’s success and increasing popularity in organizations is that it simplifies business practices, involves clients in the organizational process, and allows the primary team to maintain business continuity without time delays [77,78].
Some of the main benefits of Scrum are the following [79,80,81]:
- It allows for the rapid and easy management of complex projects.
- It allows a systems approach and the potential for self-management in the organization.
- It allows for holding regular meetings, ongoing monitoring and management, and allocating duties to the team every day.
- The Scrum team attempts to meet targets within given time-frames.
- Scrum enables the team to perform tasks without pressure.
- Scrum allows a retrospective view of events which makes it possible to prevent errors in the future.
According to the published information about resources, there are some acknowledged flaws in the use of the Agile technique, and the majority of developers oppose its use [82,83]. Based on this, we can show the following acknowledged downsides of Scrum that cannot be ignored [82,84,85]:
- Scrum prioritizes work planning and meetings, not product quality.
- The success of Scrum depends on experts and professionals.
- The team lacks time for document management, therefore, documentation is handled by separate teams, increasing the chance of errors.
- The owner of the product and its buyer must know the entire process with adequate knowledge and experience that will contribute to the success of Scrum.
- Scrum completely focuses on management, not on engineering and development activities.
- Scrum does not ensure global project development and its distribution.
- Requests that arrive later can lead to an increase in integration problems, which in turn hinders the work of Scrum.
An Agile approach to project management demands the acceptance of certain concepts that serve as the cornerstone for each project manager’s success. Interpreting specific principles guarantees the project’s success. First and foremost, the project must be completed by highly motivated and educated professionals with a well-defined scope of work.
The scope of the study is to explore how agile methodologies can improve the integration of information technology within Afghan government sectors. By analyzing software development patterns and leveraging open data, the research aims to develop resilient IT solutions tailored to volatile, resource-limited environments while proposing new approaches to address the shortcomings of existing methods. A key focus is on prioritizing customer requirements and adapting quickly to changes, ensuring effective collaboration among team members and fostering face-to-face communication. The flexibility of teams in meeting evolving demands is emphasized as critical to achieving project success within defined timeframes [86].
The innovative nature of an Agile team is evident in more efficient production and successful outcomes that outperform prior standard models. Business agility leads to increased company capacity and efficient responsiveness to changes. The necessity to adapt to a changing environment is driving the increase in corporate agility [87,88].
The significance of Agile approaches for the success of government initiatives’ Agile techniques are important for government initiatives in Afghanistan and the EU because they encourage flexibility, collaboration, and efficiency. Agile helps Afghanistan rebuild its infrastructure and government in tough times by focusing on adaptation and local engagement [89]. In contrast, the EU uses Agile for sophisticated digital transformations and cross-border services, leveraging its considerable institutional and technological resources [90]. Regardless of the context, whether it involves basic development needs in Afghanistan versus complex digital ecosystems in the EU, Agile’s focus on adaptability, transparency, and stakeholder involvement promotes success in both geographic areas [89,91,92].
5. Case Study: The Challenges of the Ministries in Afghanistan in the Collaboration for Software Development
The case study employed a qualitative research approach, analyzing documents, project guidelines, and insights from workshops with users, development teams, and ministry staff involved in internationally funded projects by donors such as the United Nations, World Bank, USAID, and various non-profit organizations. Data collection included interviews and lessons from the experiences of government officials and development teams, providing a comprehensive understanding of the challenges faced. A robust communication strategy throughout the project lifecycle was essential for facilitating effective discussions and addressing obstacles [93].
Despite the iterative approach promoting collaboration and incremental development, the project faced significant challenges in aligning user and development team interactions. Misaligned priorities and unclear user expectations often caused delays, and obtaining timely, actionable feedback from users remained a persistent issue. Afghanistan’s political and organizational landscape, shaped by decades of conflict and instability [94], has significantly affected public sector projects, including software development. Internationally funded initiatives in Afghan ministries frequently encountered fragmented decision-making, limited technical capacity, and challenges in fostering effective collaboration between users and development teams [95].
This study examines the challenges of adapting iterative methodologies to government projects in Afghanistan, focusing on the intersection of political and organizational dynamics [96,97] from 2018 to the new government transition in 2021. International donors, private companies, and the Afghan government carried out numerous initiatives. The research gives insights into the unique issues faced and techniques utilized to overcome them through the analysis of project instructions, workshop outcomes, interviews with ministry staff and development teams, and existing documentation. These findings contribute to the larger discussion on decision-making and collaboration in resource-constrained and politically risky circumstances, delivering significant insights and best practices for similar contexts around the world [97].
From 2018 to 2020, Agile teams developed complex databases, applications, and geoportals to meet the specific needs of various ministry departments. They efficiently managed large datasets using a hybrid approach, combining traditional relational databases like MySQL and PostgreSQL with modern NoSQL solutions such as MongoDB. This strategic combination ensured scalability and flexibility to handle diverse data requirements. The databases, containing over 80,000 entries per department, were secured with advanced encryption, anonymization, and role-based access control, safeguarding sensitive information and ensuring compliance with stringent government data protection standards.
Organizational issues such as poor communication and limited Agile implementation frequently result in faulty builds, disturbing workflows and incurring delays. This can weaken faith in projects funded by the government, preventing important objectives from being met. According to a Standish Group study [98], these factors cause 59% of Agile project delays. In a comparable manner in the EU, 37% of Agile projects failed to reach deadlines due to integration and communication issues. Addressing these gaps is critical to ensuring Agile produces efficient, timely outcomes that improve project success and customer happiness [98,99,100].
The major takeaway is that organizational issues, such as poor communication and ineffective Agile integration, may trigger delays and impair project effectiveness. These challenges erode confidence and impede growth. To ensure successful outcomes, it is critical to eliminate these gaps, improve communication, and fully implement Agile concepts. This results in more efficient, timely outcomes and higher user satisfaction [100].
5.1. Collaboration Among Stakeholders
The main goal was to improve collaboration among stakeholders and clearly define roles and responsibilities that are critical to project success. These efforts lay the foundation for a robust framework that supports the development of innovative, pattern-based methodologies. During project execution across Afghanistan’s ministries, the average internet speed for approximately 3500 users and each ministry’s software development team was 150 Mbps, with a maximum overload capacity of 100 Mbps. Monitoring technologies used included Nagios and Grafana, while IP addresses were handled using dynamic configuration distribution systems. Within their working infrastructure, the ministries methodically constructed 40-node clusters, each with an equal mix of 10 physical and virtual machines for operations. These clusters were constructed to maximize load distribution and monitored with Grafana and Nagios to ensure the stability of performance during software deployment and operations.
5.2. Technological Limits and Project Limitations
The project also had issues in obtaining user resources, which were limited or unavailable, resulting in bottlenecks for Agile teams. Another point of conflict was the articulation of user requirements, which were frequently ambiguous, incomplete, or unexpectedly changed throughout the process. Balancing customer requests with technological limits and project limitations became a complicated negotiation, often resulting in concessions that affected both deadlines and ultimate product quality. These issues resulted in delays, frequent misalignments, and the need for extensive rework, hurting the overall efficacy of the software development process and the project’s final results.
5.3. The Main Issue and Dissatisfaction with the Software Products
The key problem that we faced during the project was a substantial divergence between user expectations [11] and service delivery [64], particularly for shared services between ministries that use the same software solutions. The problem arose from a discrepancy between the desired functionality of the customers, which aimed to increase consumer engagement [101], and the comprehension of the development team of these needs. As a result, the team misinterpreted the request and created a product that only partially met the user’s requirements [74]. This miscommunication resulted in rework and delays, emphasizing the crucial need for clear communication [20] and correct demand validation in the development process.
Users regularly reported dissatisfaction with the software products, as the solutions provided by the development team did not meet their specific requirements [11]. While the project scope defined user requirements, the development team’s misunderstanding of business needs resulted in a significant gap between what was provided and what was intended [101]. This divergence highlighted the difficulties in aligning software features with business objectives, resulting in a mismatch between user requirements [24] and the end product. On the other hand, the development team was frustrated by the user’s lack of explicit and detailed needs. They discovered that crucial organizational data, such as operational characteristics and organizational structure, were frequently absent or insufficient, limiting the capacity to provide targeted solutions [102]. The lack of these essential data points worsened delays, increased expenses, and decreased customer satisfaction, resulting in many unfulfilled expectations and miscommunication.
The failure in communication [8] and data exchange between stakeholders, including consumers and developers, resulted in a long cycle of misunderstandings [102] and disappointed expectations. This cycle ultimately resulted in project delays, cost overruns, and decreased customer satisfaction. The conflict between users and developers explores the enormous challenges of ensuring that software development properly satisfies both company objectives and user needs, especially when clear and open communication is lacking [96].
5.4. Representation of Shared Services in Linked Ministries of Afghanistan
All ministries used the same applications, software products, and services developed by the Agile team in the project implementation. The ministries provided the services to the public, and management was used to ensure consistent access to the systems of all departments. These ministries had distributed HR systems to keep records of employees. The system includes an employment-to-retirement process, a common infrastructure for public communication, and a software platform for seamless information sharing and support.
The challenges related to the implementation of the e-Government in Afghanistan, software projects, including ICT and policy obstacles, have been explored in various studies. These studies emphasize the need to address legal, strategic, and policy barriers for effective public sector initiatives [95]. Other challenges include strategy and policy issues within Afghanistan’s public sector [103], the lack of political commitment and comprehensive policies as significant obstacles [94].
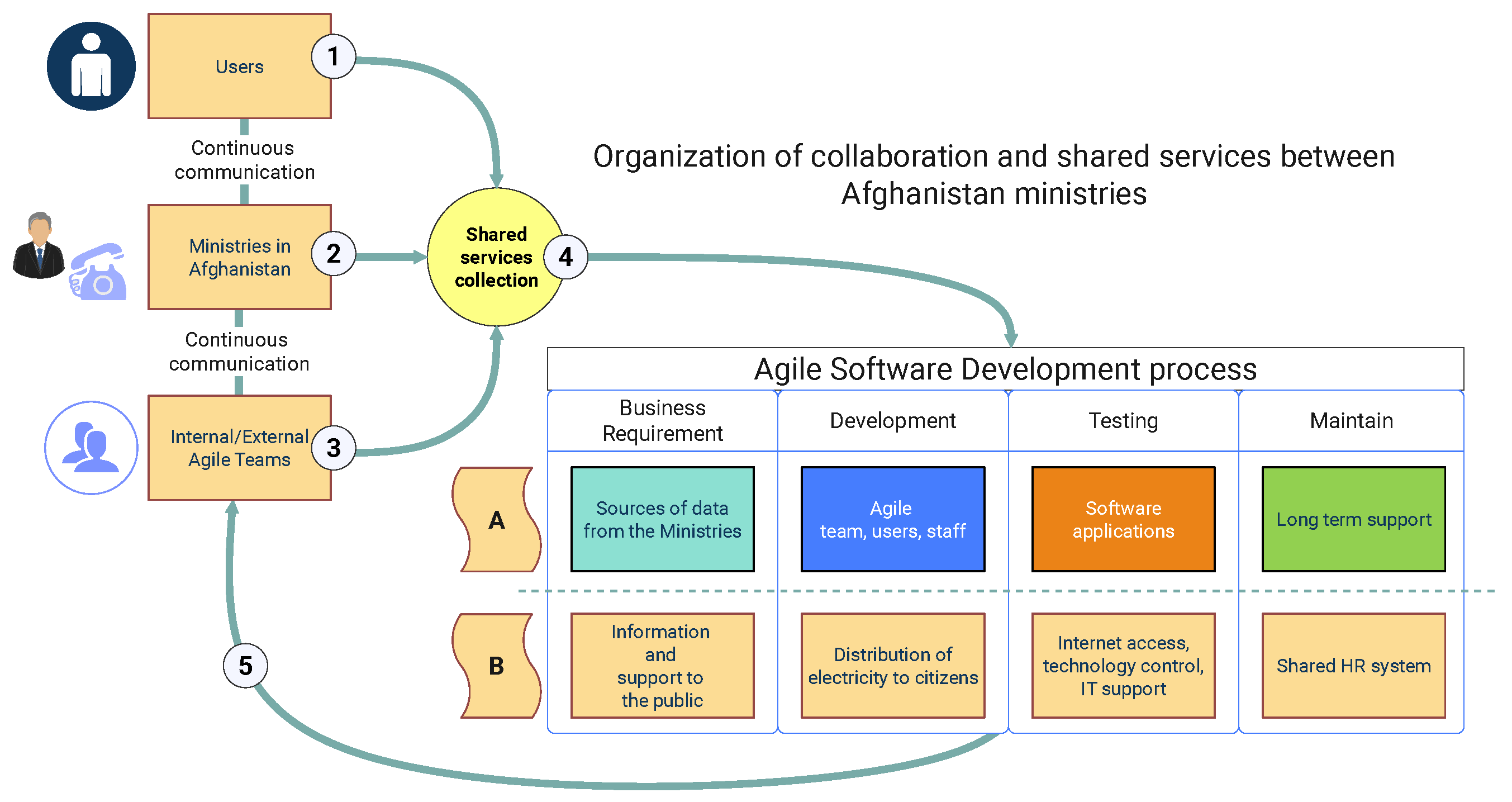
There was a shared infrastructure for public communication and a common software platform for seamless information sharing and support. The ministries had a shared infrastructure for public information and were presented as a communication bridge to spread information to people. They had shared services, each ministry with unique functions, connected to the distributed HR and public communication system. The shared services between users, Agile teams, and ministries are visualized in Figure 3.
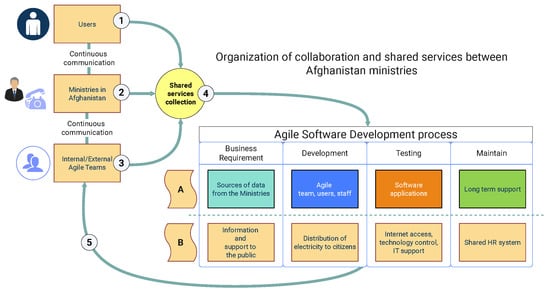
Figure 3.
Organization of collaboration and shared services between Afghanistan ministries, users, and Agile teams. Source: author’s contribution.
The user, Agile teams, and ministries are the key elements that contribute to shared services. The diagram includes the following items with a description:
- Users: the ministry staff who use the systems and applications and support the Agile team in requirement gathering;
- Ministries: they are the resource centers, using the shared services of the developed applications and providing services to the public;
- Agile team: implementing the projects and accessing the shared services to develop the applications;
- Shared services: the shared services are the collective services between ministries using the same software products and providing services to people;
- Ministries used an Agile software development strategy to complete the project. The agile team used the agile strategy following the project’s goals.
5.5. Organizational Patterns in User–Agile Team Working Environment for Afghanistan’s Ministries
This section addresses the unique challenges that ministries encounter while utilizing Agile techniques in software development [96]. The main challenges are assuring effective user and Agile team participation [104], encouraging cross-organization collaboration, and managing shared resources and needs. Ministries commonly use similar IT platforms, but they struggle to organize user involvement and requirement sharing for successful project delivery [93]. Furthermore, teams experience difficulties while attempting to obtain ministry resources required for development due to security concerns or bureaucratic obstacles [97].
A key research gap lies in adapting Agile methodologies to volatile, resource-limited environments [96] like Afghanistan, where challenges such as limited infrastructure, resource scarcity [93], security risks, and cultural constraints [97] hinder IT project implementation. Traditional Agile practices assume stable conditions and consistent user engagement, which may not align with the needs of Afghan ministries. Addressing scalability for public-sector applications, integrating diverse technologies, and defining success metrics for such unique contexts remain unexplored [105], highlighting the need for tailored and innovative frameworks.
So, we can present and solve the following challenges:
- User and Agile Team Engagement: Diverse goals make it challenging to engage both users and Agile teams, resulting in project implementation gaps [105].
- Inter-Ministry Collaboration: Ministries often collaborate on initiatives, but coordinating their efforts can be challenging, especially when data security and resource access are involved.
- Requirement and Documentation Management: Shared needs are vital, but they are typically presented incongruously between consumers and ministries, impeding project clarity and timetables. Incomplete documentation confuses and impedes Agile procedures.
- Data Security and Access: Agile groups require access to sensitive ministry data to design efficient solutions, but security procedures frequently restrict this access, resulting in delays and possible bottlenecks.
To overcome these challenges, ministries must cultivate an organizational culture that embraces flexibility, technological innovation, and collaborative tools. This transformation requires training staff on new systems, promoting cross-functional teamwork, and establishing secure, scalable access protocols. By fostering a culture of adaptability and continuous improvement, ministries can optimize software development processes, resulting in higher-quality solutions that align with both their specific needs and stringent security requirements.
6. Results
Our research has provided a thorough understanding of key historical events in software development, with a focus on one state’s ministries, and developed new methods for data mining and extraction. In this section, we present innovative techniques and algorithms for pattern recognition. By applying machine learning to an existing dataset and identifying patterns across various programming languages, we discovered common services used in software projects within Afghan ministries and examined the challenges faced in these projects.
To address the challenges of working with Agile teams and users, as well as to explain best practices, we propose pattern-based solutions that reduce project failure and improve product quality. This study’s findings underline the need for organizing and regulating knowledge, as well as facilitating knowledge sharing between both parties. This method promotes decision-making through collaboration, productivity, and the delivery of complex solutions that satisfy the highest user expectations. Agile methodology software development teams must present users with useful and actionable information. It is vital to devote efforts to looking at the following major factors of the outcome [104,106,107,108,109,110]:
- Offer a solution to enhance user and Agile team relationships, interaction, and project success.
- Create a diagram of shared services for users and the Agile team: A graphical representation of key shared services between Agile team responsibilities and users, including user input, Agile team performance, Agile team output, team success, mutual acceptance, and CI/CD.
- Agile team and user roles and responsibilities matrix: A table that connects various Agile roles (such as Product Owner, User, and Developer) to user actions.
- Methodology flow chart: An Agile team collaboration enhancement flowchart that outlines methods and actions for improving software development results.
- Mined organizational patterns in a user–Agile teamwork environment to facilitate productive collaboration as a solution to a recurring problem.
6.1. Experimental Setup
During project implementation, the research was carried out on a premises workstation powered by an Intel(R) Core(TM) i7-7700HQ CPU processor with 8 cores and 16 threads clocked at 3.4 GHz (up to 4.2 GHz boost). The computer system included 48 GB of DDR4 RAM running at 3200 MHz. The workstation included an SSD with a maximum read speed of 7200 MB/s and a maximum write speed of 7000 MB/s, as well as an NVIDIA Quadro K1200 GPU for computational tasks like statistical data analysis and report preparation for top-level management. Microsoft Windows 10 operating systems were used to help the project’s development and testing.
A comprehensive analytical toolkit, including Python 3.12, PySpark 3.4.4, Hadoop 3.4.1, and Delta Tables 2.1.0, was employed for statistical analysis and result generation. This suite enabled the efficient processing of vast datasets while ensuring data integrity and analytical accuracy. Python’s libraries, such as Pandas, NumPy, and SciPy, supported advanced statistical methods, while PySpark and Hadoop provided the necessary distributed computing power for handling large-scale data. Delta Tables enhanced the system with transactional consistency, versioning, and support for incremental updates, ensuring reliable, precise analyses. This well-architected framework optimized data processing and enabled the extraction of deep insights from complex datasets with unmatched efficiency through the application of different algorithms.
For ministry testing, the software deployment environment was created as a hybrid architecture, combining local resources with AWS EC2 instances to ensure scalability. Kubernetes acted as the orchestration platform, allowing for fast cluster management and optimal server and client scaling. Applications were installed on servers with internal IP addresses, following the ministry’s specific rules. To maintain a high level of security, tight access controls were installed, and the entire environment was limited in its exposure to external networks. This decreased the likelihood of unwanted access and guaranteed that critical data and systems were safeguarded. As a result, due to security considerations, we are unable to disclose the settings. In addition, isolated testing was carried out on Ubuntu 23.04 to ensure a controlled and secure environment for complete review and validation.
6.2. Dataset Collection and Analysis
In this section, we analyze the aforementioned dataset within research methods. This dataset was generated by the study group “Ptidej Team” and made available to the public on its GitHub repository [60] with the name: p-mart-Repository-Programs (P-MARt). As an initial step in the analysis, we performed a preliminary sorting of the folders to ensure the data was effectively organized and to evaluate its quality and relevance. By examining the structure, identifying patterns, and uncovering key insights within the data, we laid the groundwork for deeper analysis. This step is essential for identifying crucial trends and relationships, which inform decision-making, support the development of predictive models, and align with specific research or business objectives. A detailed description of the preprocessing workflow is provided in Appendix A. The analysis is detailed and presented in Appendix B and Appendix C, which is one of the contributions prepared in this article.
6.3. Sequential Pattern Mining and Identification in the Code
Input data extracted using sequential pattern mining (SPM) techniques can be classified according to patterns that occur frequently [111]. This technique is called sequential pattern mining and is often found when searching for similar clusters, for example, in an article on shared bicycles [102], or when predicting network loads [112] and the like.
When solving pattern search, this method can give us better-oriented results that are not visible to the eye [113]. In this way, we obtain the subsequences that repeat the most frequently [101], which we consider to be certain patterns, and we can optimize them for the needs of our research with suitable search parameters. We can see the proposed solution in the Algorithm 1, but for the needs of our solution, we will only use its basic construct to determine the number of subsequences.
The Algorithm 1 provides a general possibility of using the procedure in question, but the problem is determining the initial value , which means the frequency of identical characters within the pattern search process present in the code. In the data used for the evaluation, we tentatively set to the value of 3, which was recommended in several previous studies. However, with this setup, the control structures specific to a particular programming language are identified as repeated patterns found. Identifying them, we obtained the values shown in Table 1, which result in significant discrepancies between the values found by individual researchers and can confuse new researchers.
| Algorithm 1 A pseudo-algorithm for finding patterns in data. Source: [101] |
Input: Determination of the maximum required frequency .
Output: Frequent sequences from the source text. |

Table 1.
Patterns with incorrectly chosen input value were found. Source: author’s contribution.
6.4. Mathematical Formulas for Frequent Subsequence Mining Algorithm
This section describes the key mathematical formulas utilized in the frequent subsequence mining algorithm. The purpose of this method is to detect parts in a source text that occur frequently, using specified thresholds and criteria. For optimal accuracy and efficiency, the procedure is divided into steps that are mathematically specified.
To discover frequent subsequences, we first determine the maximum necessary frequency (). When the frequency of a subsequence surpasses this threshold, it is considered frequent and is chosen for further analysis. The algorithm loops through the subsequences, selecting and assessing them according to their fitness, until a termination condition is reached. If a subsequence’s frequency equals or exceeds the maximum needed frequency (), the algorithm exits the loop. If not, it resumes the search by referring to the previous phase.
During the implementation of pattern search, we encountered the problem of determining the optimal value. We performed the search with equal to 3, which identified patterns controlling the structures of individual programming languages, as we can see in Table 1. The determination of the value of this variable is not described in the reviewed articles and is often very poorly determined by new researchers in this field. It is necessary to implement a similar method to that used, for example, in text analysis [114,115] with the removal of unnecessary words in the form known as stop words. This will create a list of patterns that are used in individual programming languages and it is appropriate to implement their removal in the form of the pre-preparation of the source text.
In the end, the algorithm generates frequent subsequences that meet the required conditions, yielding the desired results for frequent subsequence mining. The formulas below represent the algorithm’s specific steps, each of which contributes to the overall process of frequent subsequence mining. Each of the steps can be presented through the following steps:
1. Determination of the Maximum Required Frequency:
Explanation:— is the threshold value. If the frequency of a subsequence exceeds this value, it is considered frequent.
2. Calculation of the fitness function:
Explanation:—S represents a subsequence from the source text.— computes how well subsequence S fits the text based on a predefined criterion (e.g., frequency, occurrence, etc.).
3. Selection Probability Using the Roulette Method:
Explanation:— is the probability of selecting subsequence .— is the sum of the fitness values of all subsequences.—This formula ensures that subsequences with higher fitness have a higher probability of being selected.
4. Selection process:
Explanation:— is the subsequence chosen based on its selection probability . Random selection is performed using this probability distribution.
5. Termination condition:
Explanation:— is the current frequency of the subsequence k at iteration k.—If the current frequency exceeds the threshold , the algorithm terminates.
6. Loop Iteration:
Explanation:—If is less than , the algorithm returns to step 3 to continue searching for subsequences.
7. Output frequency sequences:
Explanation:—Once the algorithm has completed the iterations or met the termination condition, it outputs the frequent subsequences that were selected during the process.
6.5. New Approach Pattern Shared Vision Refinement
To address the issues faced in software development, ministries can benefit from adopting structured methodologies that provide clarity and guidance. The integration of these methodologies into our approach—termed Pattern Shared Vision Refinement (PSVR)—focuses on enhancing collaboration, improving documentation practices, ensuring robust data security, and cultivating a culture of adaptability. By embracing these guiding principles, ministries can effectively navigate the complexities of software development and better meet their evolving demands.
PSVR includes thorough definitions of organizational patterns to guide the development process, promoting good communication, explicit role definitions, and conflict resolution methods. PSVR enables teams to more efficiently negotiate the complexities of software projects, ensuring that solutions are practical, adaptive, and sensitive to the unique problems faced in government operations. This strategy eventually tries to increase project outcomes and stakeholder satisfaction by establishing a common vision that aligns user and development goals.
This pattern-based approach has a foundation in a shared goal that evolves through continuous feedback and adjustment. Iterations only begin after a clear implementation plan is established, ensuring that all team members align on what needs to be created. This approach, rooted in complex systems and collective intelligence, highlights the importance of a unified vision for software development. Each iteration acts as a feedback loop, allowing the team to assess progress and adapt, reflecting adaptive systems in which outcomes emerge from dynamic interactions. Given emphasis is on the balance between individual understanding and collective goals, refining the vision with each cycle. Philosophically, it aligns with pragmatism, where truth evolves through practical engagement, and the vision becomes clearer through collaboration. So, in the end, the software engineers have the final decision on the proposed request, when they have collected all the necessary requests for the smaller solution prototype. After the above, engineers can start creating quick solutions where there is a clearer view and direction in which the project can be seen to continuously progress.
The approach as a solution in Figure 4 demonstrates how we could use organizational patterns to show that our pattern approach PSVR can address these specific challenges:
Figure 4.
Pattern for Shared Vision Refinement (PSVR) with steps and descriptions.
- Pattern part A1: Building Working Domain
- (a)
- The main problem identified: lack of team building and management, poor user and Agile team involvement.
- (b)
- Problem solved: organizing team, building team structure, building users and the Agile working environment to work for the project’s common goal.
- (c)
- Solution: Assign roles and responsibilities between users and Agile team members. Build communication bridges between team members and provide a supportive working environment.
- Pattern part A2: Infrastructure
- (a)
- The main problem identified: There was no specific project management plan and there were unreliable servers within the ministries. We found that the network in ministries was slow, had outdated hardware, and no CI/CD setup was organized.
- (b)
- Problem solved: Agile teams identified the problems and proposed new deployment strategies and tools.
- (c)
- Solution: The Agile team implemented Microsoft Azure cloud services for Scrum and DevOps, implemented the necessary tools, upgraded servers and hardware, improved network stability outlined in the project plan, and used pipelining and implemented CI/CD.
- Pattern part B1: Working Toward Goal
- (a)
- The main problem identified: The lack of a shared project objective causes misalignment in software development in ministries and unmet user expectations with the Agile team.
- (b)
- Problem solved: Connect and build user and Agile team collaboration to understand the common goal of the project.
- (c)
- Solution: In all projects, the goals are explained to the Agile team and users, creating motivation to work on common goals. The goal of the project is to build collaboration.
- Pattern part B2: Distribution and Scaling of Resources
- (a)
- The main problem identified: The lack of resource distribution causes delays in project implementation. There is a lack of on-time software deployment.
- (b)
- Problem solved: All project managers and resource allocators proposed clusters for applications.
- (c)
- Solution: In all projects, resources were distributed to Agile teams according to their assignment and project needs.
- Pattern part C1: Applying To All Patches
- (a)
- The main problem identified: There is a lack of coordination, breakdown structure, and no roles and responsibilities assigned.
- (b)
- Problem solved: Agile teams and users were given planned activities, assigned roles, and divided work into smaller portions to achieve the goal.
- (c)
- Solution: Collective solutions apply to all similar challenges in projects.
- Pattern part C2: List Of Shared Service
- (a)
- The main problem identified: The ministries have a lack of resource identification, an unidentified list of sources, and there was ambiguity in the service provided.
- (b)
- Problem Solved: User and Agile team engagement, inter-ministry collaboration was solved.
- (c)
- Solution: Establishing a clear, shared vision aligns the goals of ministry stakeholders and Agile teams, ensuring that all parties understand and agree on project objectives. Regular vision-sharing sessions and cross-functional workshops allow users and Agile teams to collaborate effectively, prioritize shared interests, and maintain engagement throughout the project life cycle.
- Pattern part D1: Defining Tasks And Priorities
- (a)
- Regarding inistry users and Agile team members in the country, the main problems identified were unassigned roles and responsibilities, no proper resource allocation, and no task management.
- (b)
- Problem solved: Requirement and documentation management were created.
- (c)
- Solution: Adopting a structured requirement refinement process helps clarify and document specific needs early in the project. By involving both initial refinement sessions, requirements are continually reviewed, prioritized, and adjusted based on user feedback. This process ensures accurate documentation and reduces misunderstandings, making requirements accessible and transparent across the team.
- Pattern part D2: Result And Consequences
- (a)
- The main problem identified: there was no accountability considered for ministries, users, and Agile teams. The same tasks were repeated, mistakes were made, and goals were not scored.
- (b)
- Problem solved: Project managers define tasks and estimate the results and accountability in ministries staff, users, and Agile teams.
- (c)
- Solution: The Agile team and the users were responsible for the work based on the project priority, task, and requirements. Project managers set measurable project goals and enforce accountability between the Agile team and members.
By implementing iterative and adaptive software development approaches, ministries may efficiently address user and development team concerns while encouraging seamless communication and collaborative execution. This strategy emphasizes shared responsibility, fosters a culture of flexibility and continual improvement, and guarantees the execution of high-quality, successful projects. The outcomes are validated and verified through ongoing user feedback, extensive testing, and review against predetermined acceptance criteria. Pilot testing validates real-world functionality, while post-implementation assessments evaluate performance, dependability, and user satisfaction. Regular maintenance and regression testing prevent functionality loss and ensure continuing alignment with project objectives throughout the software’s lifespan [116].
Working closely with users and development teams, results are validated at each project stage, beginning with the use of organizational patterns during project execution. Metrics are constantly evaluated via feedback loops, ensuring that evaluations remain aligned with project objectives and encouraging continual progress throughout the development process. The representation in the organizational pattern diagram incorporates real-time data from ministry resources to ensure correctness. The study draws on the first author’s experience implementing software projects in three Afghan ministries as well as problems identified in the literature to analyze organizational patterns, documentation, and observations. These projects featured Agile teams and users working together to implement software projects [116,117,118].
To solve the challenges between users and the Agile team in effectively communicating and implementing the project on time, we propose the following pattern with the following name: Pattern Shared Vision Refinement (PSVR). PSVR shown in Figure 4 shows, as a new paradigm, creating the processes on how the user and Agile team can collaborate. The aforementioned pattern seeks to improve the language of communication by visualizing and displaying the processes in several stages. Figure 4 depicts the working environment constructed utilizing an organizational pattern language to cover the complete project process from start to finish. The Agile team and users interact and collaborate to implement the software. The project implementation from start to end is illustrated in Figure 4, which provides a solution to implementation projects effectively through organizational patterns. The figure is further explained in detail with the defined alphabets starting from A1 to D2.
The setup of users and the Agile team are visualized in Figure 4, and the documented and observed patterns with their structure are explained in the next Section 6.5.1.
6.5.1. Pattern Format
The pattern structures in Section 6.5.2, Section 6.5.3, Section 6.5.4, Section 6.5.5, Section 6.5.6, Section 6.5.7, Section 6.5.8 and Section 6.5.9 are described in Coplien and Harrison’s pattern format [119] and are further enhanced by explicitly expressing the conflict of the most prominent contradicting forces in the but form.
This is the format:
<Pattern Name>
…—Describe the context of pattern occurrence.
✥✥✥—The text in bold describes the actual problem as a conflict of the two most prominent contradicting forces.
Therefore—Therefore, describe the generic solution of the defined problems as a final solution.
✥✥✥—This part is optional and it provides the consequences of the pattern application (optional).
Description—This is an optional description to explain the pattern.
The results are measured by evaluating the effectiveness of organizational patterns in improving user and Agile team collaboration, building team engagement, and successfully implementing projects.
6.5.2. Building Working Domain
… Poor coordination among participants leads to miscommunication and inefficiency in achieving project goals. Without close collaboration between Agile teams and users, a sustainable project status and task completion are impossible. Users and Agile teams in project implementation work together to build an organized working environment for effective interactions and provide iterative feedback to the team for further progress. Collaboration between stakeholders aims to remove the gaps in software development and support users and the Agile team, leading to the successful implementation of the project.
Therefore,
Create a building working domain for participants in the projects. Establish a fair working environment between users and Agile teams to participate in project implementation, build communication between developers, users, and Agile teams, encourage them to share resources, and support each other in continuous feedback to achieve the common goals of the project.
Applying a building working domain pattern in project implementation supports Agile teams and users in understanding and building communication. This pattern helps the software development team and users understand their shared responsibility, eliminate misunderstandings, and ensure that the project changes in response to user needs.
6.5.3. Infrastructure
…To implement the project, there is a need to build effective collaboration between users, Agile teams, and ministry staff. Resources are required to be used to align team members with the scope of the project and maintain a testing environment so that success can be achieved on time.
A software development team prepares to test the product, deploy it, and maintain it. Incomplete infrastructure due to the lack of unified support and testing environments creates challenges. Teams often face inconsistencies such as unavailable infrastructure, which causes errors and duplicate workflows.
The Agile team and its members are working to prepare for the development and operation of the software product but lack experience in testing and deployment.
The team works to create a working environment and solutions for testing, deploying, and maintaining software products, or creating inconsistencies can cause challenges in development and deployment.
Software development needs infrastructure to test, deploy, and maintain the software products, but without reliable infrastructure as the backbone for collaboration with the Agile team, it results in poor productivity. If the infrastructure is not established for continuous development and integration, then productivity and quality in the deployment platforms will be reduced.
Therefore,
Establish a working environment that has a scalable infrastructure to test, develop, and deliver software products effectively to ensure consistency, efficiency, and stability throughout the software development process.
The preparation of the working environment in software development is an important part that the Agile team requires for continuous development and operation. The pattern is used to prepare the working environment for projects that use DevOps and pipelining. Agile teams must work on a consistent and scalable infrastructure that serves as the foundation for continuous integration/delivery, testing, and timely delivery of software products. To maintain consistency across working environments for the Agile team and users, it eliminates errors, speeds up workflows, and improves team cooperation.
6.5.4. Working Toward Goal
…The Agile team and users are working to implement the project and deliver the software products on time. Every team member wants to finish their task on time, participate in all processes, and achieve the project goal.
Development teams and users work together to achieve project goals, but a lack of a shared objective leads to misalignment in software development within ministries and results in unmet user expectations.
Agile teams, users, and stakeholders are working to complete the software project on time, but insufficient resources and unclear project goals hinder progress. While business requirements are gathered and teams are set up for collaboration, a lack of coordination and missing or unclear timelines contribute to project failure.
Therefore,
Work on the project goal and share the project objective with all stakeholders, including users and the Agile team, to work effectively to implement the project with the defined goal.
Work towards a clearly defined project goal and ensure it is communicated to all stakeholders, including users and development teams. Typically, project managers share this goal with all partners, assign roles, and set individual responsibilities. They prioritize tasks, allocate teams, and establish communication channels to initiate the project.
6.5.5. Distribution and Scaling of Resources
…The Agile team and users are working to effectively utilize and scale the required resources to test, deploy, and maintain the software products. They are trying to ensure efficient allocation and management to meet project demands and maintain the performance and cost-effectiveness of the clusters.
Project implementation is underway, and the development team, along with users, is setting up the working environment to meet all specifications. However, inadequate resource allocation leads to delays, preventing the timely delivery of the software product.
The Agile teams and users are working to manage and utilize resources, but insufficient resource allocation and poorly organized clusters hinder the software product development process. Ministry staff are using existing clusters and tools, but these are outdated and inadequate for testing, deploying, and maintaining applications.
Therefore,
Prepare and scale the resources based on the project needs and priorities when implementing the software project. The software project managers are required to provide the required resources to the Agile team and create clusters that meet the project requirements.
In the project implementation plan, the managers work to ensure that every team has sufficient resources and that the working environment is ready to begin the development process. Project managers work to ensure that the Agile team understands the business requirements and the organization of the working environment. While working on DevOps, the Agile team needs to ensure that the cluster for software development testing, deployment, and maintenance is available.
6.5.6. Applying to All Patches
…Software development requires effective communication between all parties. It is necessary to schedule tasks, assign roles, and apply the group solutions to similar tasks in the projects, which may resolve coordination, role clarity, and work breakdown obstacles in other similar challenges.
Agile teams and users want to perform their duties and participate in the project implementation. Without proper coordination between all team members, this results in misplaced efforts and inefficiencies in meeting project demands. Teams want to work based on the assigned roles and assignments, but unclear roles and unstructured tasks confuse teams and impede software development, contradicting the requirement for clear accountability and reasonable workloads in the project’s startup.
Therefore,
Establish structured planning in the project, assign roles, and divide the work into smaller parts to ensure that coordination and accountability are prepared throughout the team. Apply collective solutions to all similar challenges in projects.
Different projects have similar problems; in our case, the Agile teams, users, and stakeholders of other project work were required to follow the same guidelines. Therefore, the pattern Applying To All Patches is used in other projects to ensure coordination, assign roles, and task management is organized by providing collective solutions to recurring project challenges.
6.5.7. List of Shared Services
…Project collaboration between the development team, users, and partners is essential for successful software development. The process can be improved by organizing regular cooperation meetings and cross-functional workshops, which foster clear communication, goal alignment, and continuous participation throughout the project’s lifecycle.
Several projects have similar challenges to using the software product, but the implementation of the project requires a unified software solution to address all similar requirements and the requirements of the common department. However, each department has distinct requirements that may not be compatible with the common system.
When software solutions are developed in-house for a range of similar problems in organizations, they are often relevant across multiple work domains or use cases. However, specific project resources or software solution components that can be used for shared services are not explicitly stated or described in other projects. Developers are unaware of reused materials from software product projects, which can lead to many implementations of the same problem, resulting in varied quality and inefficient resource utilization.
Software solutions can be applied to all departments, but ministries do not have resource identification. There is an unidentified list of resources in ministries, and solutions are not identified to take advantage of ambiguities in the services provided by ministries.
Therefore,
Identify and document reusable components that have already been developed in projects or services, explicitly in software products, making them available as shared resources for other similar ones to accelerate the development process, reduce redundancy, and ensure consistency concerning similar challenges.
6.5.8. Defining Tasks and Priorities
…Building a collaboration for software development in a working environment with partners and stakeholders, assigning confusing roles, a lack of inadequate resource allocation, and a lack of task management obstruct the success of a project’s progress and result in poor quality.
When there are unstructured and misleading requirements in projects and the team wants to start implementation, the launch can cause misconceptions and delays through inadequate communication between stakeholders and software development teams. Changing priorities for project components and working with inconsistent requirements documents can lead to project failure.
The problem is based on the lack of defined roles, insufficient resource allocation, and inefficient task management, which leads to poorly defined requirements, frequent misunderstandings, and delays in project completion due to inconsistent communication and documentation practices.
Therefore,
The software development team uses the Defining Tasks And Priorities pattern to avoid misconceptions, list the priority of requirements, and better use the resource allowances to projects and teams. The software development team implements an organized requirement review process that involves regular discussions between ministry staff and team members to identify, prioritize, and review requirements, promising transparency and proper documentation.
The software development teams have established an organized process for improving requirements for all projects in these ministries by conducting regular discussions involving employees, software users, and partners, ensuring that requirements are continuously clarified, prioritized, and updated following the requirements of the same and the client’s needs.
6.5.9. Result and Consequences
…The final software products are acceptable mutually by the software development team and ministries when they meet the requirements. In a project development environment where stakeholders, partners, and the software development team lack clear responsibility, a lack of goal setting, repeated tasks, and repeated bugs can ultimately delay project delivery.
Customers and software developers want the final product to be of high quality and available on time, but project efficiency and development are hampered by repetitive tasks, preventable errors, and confusing priority lists that force teams and users to measure performance without accountability.
Therefore,
Apply the Result And Consequences pattern to avoid the same mistake in other projects. During project implementation and the delivery of the final product with project priorities and requirements, project managers made sure that ministry employees and Agile teams were responsible for their work by clearly defining tasks, evaluating results, and creating measurable objectives.
We wanted to assess the effectiveness of the software product’s outcome and adapt solutions from others to freshly formed initiatives. When implementing projects with government agencies, you may receive multiple custom requests with varying expectations, priorities, and criteria. Based on the project plan’s aims and criteria, project managers assign tasks, establish clear and measurable targets, and maintain accountability among software teams, users, and partners.
We identified eight new patterns that improved interaction between users and development teams, fostering collaboration between organizations. These patterns led to reduced project delivery times and improved communication efficiency and should contain the following:
- They should be reusable;
- Easy to implement;
- Effective for software engineers, development teams, and organizations;
- have option of addressing common challenges in software development and project implementation.
To summarize provided patterns, ministries face specific challenges when adopting Agile principles for software development, such as promoting effective collaboration, ensuring secure data access, aligning requirements across departments, and cultivating an Agile-friendly culture. Effective decision-making requires navigating Afghanistan’s complex socio-political environment, ensuring equitable resource distribution, leveraging local networks, and maintaining adaptability to shifting realities. These provided patterns and our approach Pattern for Shared Vision Refinement (PSVR) allows ministries to address immediate issues while fostering long-term resilience.
The effectiveness of these approaches can be measured by tracking key performance indicators (KPIs) such as project delivery time, communication efficiency, and user satisfaction. Metrics like the number of collaboration sessions, resource utilization rates, and the quality of requirement documentation can assess the success of coordination and participation. Additionally, there can be monitoring the frequency of security incidents, the alignment of departmental requirements, and the adoption rate.
For us, key open questions include how to enable active participation between users and development teams, improve requirement sharing and documentation, secure sufficient resources, and support the organizational shift towards Agility. Addressing these concerns will help ministries adopt more efficient, collaborative, and secure processes, enabling the delivery of higher-quality software tailored to the needs of public service.
6.6. Examples of How PSVR Patterns Can Be Applied in Various Industries
The Pattern Shared Vision Refinement (PSVR) can be efficiently used in a variety of sectors to improve user experience and operational efficiency. PSVR can be provided in the intended application throughout different sectors in the following manner:
- In healthcare, it can help with patient-centered care by incorporating continuous feedback into treatment regimens and telemedicine options. PSVR in education can help steer curriculum development and improve e-learning platforms by putting student input first.
- In the finance industry, PSVR can improve the customer experience by refining banking services based on user input and improving risk management measures. PSVR can help manufacturers optimize operations and product development by allowing for continuous worker input. PSVR can improve Agile software development and cybersecurity solutions by emphasizing user stories and experiences.
- Retailers can employ PSVR to improve consumer interaction and optimize inventory management based on user preferences. Public transportation systems can improve services based on user feedback, whereas logistics can benefit from real-time communication throughout the supply chain. Finally, hotel businesses may improve the guest experience by aggressively seeking and incorporating client input. Overall, PSVR promotes a user-centered strategy that drives continual innovation across multiple industries.
7. Discussion
The use of quantitative measures over anecdotal evidence is currently being disputed. Data-driven metrics can provide valuable insights for continuous improvement in shared services, helping developers to better address the challenges of software development and knowledge management. This positions students for success in a fast-changing environment driven by the quick advent of new technology. Our research into software development and knowledge management identified some significant aspects. The rapid evolution of technologies, particularly artificial intelligence, necessitates ongoing adaptation. Unlike old systems that rely on manual processes, newer approaches use AI to improve decision-making, streamline workflows, and automate repetitive tasks, resulting in dramatically increased productivity.
In our discussion, we highlight how PSVR effectively bridges the gap between user needs and development capabilities, underscoring the necessity for Agile frameworks to adapt to specific contexts. This contributes to the broader discourse on Agile methodologies. Practitioners can leverage PSVR to enhance project management strategies, systematically integrating user feedback for improved outcomes and satisfaction. In this study, we managed to introduce the Pattern Shared Vision Refinement (PSVR) framework, which focuses on addressing the unique challenges of software development within Afghan ministries. Unlike traditional Agile methodologies, PSVR is tailored for resource-constrained environments, enhancing collaboration and communication between Agile teams and users. In addition, PSVR incorporates robust data security principles and emphasizes continuous feedback loops, fostering responsiveness to user needs. Conflict resolution mechanisms further enhance project satisfaction, and clear role definitions improve accountability. Improvements in PSVR are implemented through a more detailed definition of the patterns applied in each process, focusing on continuous questioning rather than placing pressure on meetings and unnecessary activities.
A user-centric design approach is essential in modern approaches, stressing user feedback to guarantee that solutions are practical and effective. This contrasts with previous models, which were primarily concerned with technological parameters. The shift emphasizes the necessity of adaptation in meeting users’ ever-changing needs, bolstering the relevance of iterative and flexible approaches in achieving long-term success. Based on the defined questions, we obtained the following results:
7.1. RQ 1
Our findings demonstrated a major shift in software development habits, moving away from old linear management strategies and toward current iterative methodologies. Early software development was characterized by inflexible, linear methods that inhibited flexibility. As projects became more complicated, the industry adopted Agile techniques, which emphasize iterative development, collaboration, and real-time feedback, resulting in increased responsiveness to change.
We also acknowledged the growing relevance of knowledge management, particularly in the era of big data. Organizations have shifted away from traditional documentation-centric tactics and toward data-driven strategies to improve decision-making and expedite procedures. This transformation has made it easier to collect and share insights, allowing teams to apply what they’ve learned to better future project outcomes.
7.2. RQ 2
We learned a lot about how to incorporate security-by-design concepts into development workflows using (DSMLs). These specialized languages improve our capacity to identify patterns by offering a systematic framework for collecting recurrent security solutions targeted to specific domains. Using DSMLs to model and thoroughly assess security-critical components allows vulnerabilities to be found earlier in the development process. These languages provide new opportunities for developing, adapting, and reusing security patterns, assuring consistency, and eliminating errors.
The inclusion of advanced automation technologies within DSMLs allows us to efficiently analyze designs against security criteria, providing rapid feedback and facilitating iterative changes. This method improves our understanding of the relationship between domain-specific demands and broad security frameworks. By reducing complexity to a manageable, safe basis, this strategy promotes the development of inherently resilient systems, providing the door for innovation based on strong security principles.
7.3. RQ 3
Using organizational and design patterns, we discovered clearer strategies for overcoming communication difficulties between Agile teams and ministry users in Afghanistan. These patterns highlight recurrent challenges in shared services, such as misplaced expectations and a misunderstanding of responsibilities and objectives.
We gained knowledge of how to structure interactions such that technical teams and non-technical users share the same language and goals. Tools like boundary objects and collaborative frameworks have helped bridge communication gaps by offering a consistent platform for conversations and case inquiries. We standardized communication channels by introducing alignment methodologies based on design principles, making complex operations easier to grasp. This method not only reduces uncertainty but also aids in managing the inherent complexity of shared services, resulting in improved mutual understanding.
As a result of the stated and specified research issue, we developed a novel approach, Pattern Shared Vision Refinement (PSVR), that combines eight patterns into one and its application. Here is a brief overview: PSVR is designed to establish a clear, shared understanding across a team through constant refinement. The fundamental outcome of this technique is a product or solution that evolves with each iteration, influenced by collective ideas and feedback. The process begins only when a detailed implementation strategy has been prepared, ensuring that all team members understand the project’s objectives. This alignment promotes teamwork and reduces misunderstandings over time. We believe that the project vision will become more focused and cohesive, responding to new insights and guaranteeing that the ultimate result is both relevant and successful in meeting the team’s goals.
These strategies emphasize the importance of translating the existing Agile’s dynamic, iterative character into real, practical tasks. By implementing organizational or design principles, the distance between an Agile team and users in Afghanistan’s ministries can be bridged through clear communication channels, increased responsiveness, and feedback that is precisely aligned with user needs and local circumstances. These patterns assist in guaranteeing that both teams and users have a consistent understanding and work toward well-defined goals, resulting in better collaboration and project success.
7.4. RQ 4
Analysis of these challenges reveals that data security is a significant aspect. As enterprises increasingly rely on big data analytics, understanding the nuances of GDPR compliance has become critical, which is a fundamental shift from previous approaches that sometimes neglected privacy concerns.
Future research must address the complex interplay between knowledge management and software development, focusing on open communication and effective collaboration. Strengthening this relationship not only drives continuous improvement but also improves the organization’s capacity and efficiency to respond to changing user needs, resulting in a more responsive and innovative approach to software development.
Equally important is creating an organizational culture that promotes agility and continuous learning. Modern frameworks, as opposed to traditional hierarchical arrangements, prioritize cross-departmental collaboration, breaking down larger challenges into smaller sections, and encouraging creativity. This cultural revolution ensures that businesses remain resilient and forward-thinking in an ever-changing technological landscape.
7.5. Open Questions
These open questions show the complexities and specific challenges that ministries face while using Agile methodologies. Addressing these concerns wisely will improve collaboration and efficiency while also ensuring the successful completion of software projects that meet government agencies’ high standards and security requirements. By proactively addressing these concerns, ministries can encourage a more adaptive, robust, and user-centered approach to software development. This approach will lay the groundwork for future progress, resulting in improved project outcomes and enabling public institutions to better serve their stakeholders in an increasingly digital world.
Embracing continuous learning and iterative development will position ministries as leaders in Agile government processes, establishing standards for innovation, transparency, and responsiveness. As a result, we can give the following open questions and their corresponding areas:
- Area in Alignment and Communication: How can ministries effectively communicate and maintain a shared vision across diverse departments and ensure the alignment of Agile team goals with ministry priorities throughout the project lifecycle?
- Area in Data Security and Access: What secure access controls can balance Agile teams’ need for information with ministry data protection policies, ensuring compliance with privacy regulations while enabling efficient development?
- Area in User Involvement and Feedback Integration: What practices will engage users continuously without disrupting their primary duties, and how can Agile teams prioritize and integrate feedback promptly despite typically slower ministry decision cycles?
Future ministries can support fruitful debates and encourage successful solutions to each open topic by selecting a presentation structure that reflects the audience’s demands and the complexity of the issues at hand. Our working hypothesis for future research is that everyone is interested in information and possesses the necessary skills for its use and exchange.
7.6. Limitations of the Study
Every research study has boundaries beyond which conclusions may be challenged. In the case of our study, important limitations arise from a reluctance to accept new approaches, which can impede the practical application of research findings. Furthermore, the lack of longitudinal studies limits our ability to analyze the long-term impact of Agile methods and knowledge management systems.
One limitation of our analysis is that we looked at only one dataset, the p-Mart-Repository-Programs, which we determined best suited the goals of our study. Although it has proven to be extremely useful in our research, it has one significant limitation: its size. The dataset may not fully capture the richness and complexity of the larger population we seek to understand. As a result, the insights gained from this dataset may be limited, limiting the generalizability of our conclusions. Incorporating larger or more diverse datasets in future research could provide a more comprehensive understanding of the topic.
This study has several limitations that may affect our findings. We primarily focus on software development, organizational patterns, and knowledge management within government ministries, but not on limiting its applicability to other industries. Additionally, the research centers on Afghan ministries, which operate in a unique environment of political instability, international funding reliance, and significant organizational challenges. These contextual factors make the findings particularly relevant to resource-constrained and conflict-affected settings but less transferable to more stable or differently structured contexts. As such, the insights into Agile practices provided by this study are most applicable within environments that share similar constraints.
Privacy and security concerns hampered access to massive databases, potentially resulting in inaccurate depictions of real-world scenarios. Challenges in involving a diverse range of stakeholders resulted in potential biases in remarks, limiting the breadth and utility of the recommendations. Time limits make longitudinal evaluations difficult to conduct, limiting our understanding of the long-term implications of the techniques employed. The quick speed of technological advancement may render certain judgments obsolete in an ever-changing context. Recognizing these limitations emphasizes the significance of conducting new research to review, refine, and extend the study’s findings, so assuring their continued relevance and utility.
To mitigate the limitations identified in the study, several measures can be proposed. First, expanding data collection to include a wider range of software projects is essential. Conducting long-lasting studies can provide insights into the long-term effects of the PSVR approach. Engaging a diverse range of stakeholders can help reduce biases and ensure that varied perspectives to be considered. Additionally, exploring how the PSVR can be applied in different contexts, especially in government settings, would be beneficial. Cross-national comparisons can reveal how different governance structures influence the success of the PSVR approach. It is also critical to implement future strong privacy and security protocols when handling data. Regular updates to the PSVR versions, based on new findings and technological advancements, can help maintain its relevance. Furthermore, integrating emerging technologies like AI and the Metaverse can enhance the effectiveness.
8. Conclusions
This study provides a comprehensive analysis of exploitative practices in software development, emphasizing the factors influencing user experiences and proposing actionable strategies to address them. By adopting a mixed-methods approach that integrates qualitative and quantitative tools, the research identifies key incentives driving exploitative behavior in the software industry. The findings sought to establish ethical standards by advocating for user-centered software design that fosters trust and increases user satisfaction. The primary goal of this research was to address fasts with limited resources and infrastructure constraints that are common in Afghanistan, necessitating cost-effective and accessible methods. Incorporating culturally relevant participatory techniques boosts involvement by ensuring that data reflect both local contexts and practical constraints while satisfying research objectives.
One of the study’s primary contributions is the identification of eight new patterns that improve collaboration between users and Agile teams. These patterns, encapsulated in the Pattern Shared Vision Refinement (PSVR) approach, fostered more effective interaction, reduced project delivery time, and enhanced responsiveness and innovation in government programs. The PSVR methodology emphasizes collaboration, security, and adaptability, directly addressing challenges such as inter-departmental alignment and structural inefficiencies within software development.
This research highlights the critical importance of aligning user expectations with development goals, especially in complex and resource-constrained environments like Afghan ministries. Through a robust security-by-design framework and the integration of domain-specific modeling languages (DSMLs), this approach enhances team selection, effort estimation, and risk management, ultimately improving project outcomes and stakeholder satisfaction. The study underscores the necessity of fostering adaptability and knowledge sharing to ensure high-quality software solutions tailored to the unique requirements of public-sector organizations.
As the next step, this research invites exploration into how evolving technologies and methodologies can deepen the impact of the PSVR framework. Investigating the role of artificial intelligence, blockchain, and predictive analytics in augmenting collaboration, scalability, and security could provide valuable insights. Additionally, future research should examine the applicability of these patterns in countries with differing state structures and governance models, as well as in similar state institutions and ministries facing unique operational challenges. Cross-national comparisons could illuminate how organizational frameworks and cultural contexts influence the success of these approaches.
The findings highlight the relevance of combining user feedback with adaptive approaches to improve project outcomes. This research provides useful insights that might drive future studies and practices in software engineering, ultimately leading to more successful and user-centered solutions.
In the future, we may see the integration of advanced tools such as AI agents, metaverse applications, and other emerging technologies that could revolutionize software development processes. These innovations hold the potential to offer more effective and adaptive solutions for public-sector challenges. Exploring how these tools can be incorporated into frameworks like PSVR will be essential for keeping pace with technological advancements. Furthermore, evaluating their impact on collaboration, resource optimization, and security within diverse organizational contexts will help ensure their practical relevance and effectiveness. This forward-looking perspective underscores the importance of ongoing adaptation and innovation in addressing the complexities of software development in a dynamic global environment.
Author Contributions
Conceptualization, data curation, formal and data analysis, investigation, methodology, project administration, validation, visualization, and writing—original draft and editing: M.D.H., I.S., P.D., M.A. and V.T.; visualization, data curation, formal and data analysis, review—writing and project administration: I.S., P.D., V.T. and M.D.H.; methodology, conceptualization, visualization, data curation, review—writing, editing, proofreading, project administration, and supervision: P.D., V.T. and M.A.; funding acquisition and project administration: P.D. and M.A. All authors contributed equally. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data used in the form of a dataset was developed by the “Ptidej Team” study group, which is available at reference [60]. Their GitHub repository, p-mart-Repository-Programs (P-MARt), contains the dataset we used for the study, which is licensed under the Lesser General Public License. The LPGL [61] permits the use of obtained data for research purposes but without the ability to modify the original data. The entire collection contains 1.47 GB of collected data for numerous software programs and their multiple versions throughout their development. The used dataset was employed as a foundation for developing a suitable pattern in code identification without changing its content. Hence, no new data were generated.
Conflicts of Interest
The authors declare no conflicts of interest.
List of Abbreviations
| P-MARt | p-mart-Repository-Programs |
| PSVR | Pattern Shared Vision Refinement |
| DOAJ | Directory of open access journals |
| SPM | Sequential pattern mining |
| TLA | Three letter acronym |
| LD | Linear dichroism |
| MDA | Model-Driven Architecture |
| LPGL | Lesser General Public License |
| t-SNE | t-distributed stochastic neighbor embedding |
| MPS | Meta-Programming System |
| FDD | Feature-Driven Development |
| XP | Extreme Programming |
| DSMLs | Specific Modeling Languages |
| UAT | User Acceptance Testing |
| CI/CD | Continuous integration/Continuous deployment |
| CTSS | Compatible Time-Sharing System |
| GIS | Geographic information system |
| QGIS | Geographic information system |
| SLAs | Service-level agreements |
| UPM | Unified Process model |
| ETL | Extract, Transform, Load |
Appendix A. Data Processing
In data processing, we convert initial data into useful information that can be analyzed and used to make decisions. Our method entails gathering, cleaning, organizing, and analyzing data to discover patterns and insights. We ensure accuracy and usability by implementing tools and techniques such as statistical methodologies, machine learning, and data visualization. This vital effort lays the groundwork for corporate analytics, research, and artificial intelligence, resulting in informed decisions and innovation.
This organized folder structure allows for a detailed evaluation of file distribution and programming language usage across a wide directory system, as seen in Figure A1. Figure A1 shows a word cloud that depicts the distribution of typical patterns found inside directory topologies, with a particular emphasis on file kinds and technologies. The cloud emphasizes broad directory management ideas including folder hierarchy, file organization, naming conventions, and metadata, all of which are essential for file structure. Specific technology names are prominently shown, such as Apache, Dataset, Xerces, POI (Apache POI), and JFreeChart, which represent the largest collections of files in the directory. Each term’s magnitude in the word cloud corresponds to its prevalence, providing a visual depiction of how files are distributed across these technologies in the current context.
Figure A1.
Common patterns in directories. Source: author’s contribution.
Figure A1.
Common patterns in directories. Source: author’s contribution.
Appendix B. Data Preprocessing
Data preprocessing is a critical step in preparing raw data for analysis. It involves cleaning, converting, and arranging the data to ensure accuracy, consistency, and usefulness. This procedure is a necessary component of ETL (Extract, Transform, Load) operations, which entail extracting data from various sources, converting it for compatibility, and loading it into a structured format for future use.
Data Preprocessing Details
Organizing folders as datasets into well-structured data lakes significantly enhances efficiency, allowing seamless access, streamlined management, and improved scalability. Preprocessing plays a pivotal role in ensuring data integrity by addressing missing values to provide a basis for creating certain new approaches that involve patterns, standardizing formats, and resolving discrepancies. These efforts establish a strong foundation for exploratory data analysis and empower advanced applications such as machine learning and predictive analytics.
The dataset under analysis is extensive, encompassing a total of 247,931 files distributed across 23,757 unique directories. This comprehensive collection is meticulously structured into 247,931 rows, each featuring the following four key columns:
- language specifies the programming language or file type, such as HTML or JavaScript.
- file_path provides the full path to each file within the directory structure.
- file_name lists the name of the file.
- directory indicates the folder or directory where the file resides.
Appendix C. Data Processing Details
Appendix C.1. Box Plot and File Size Distribution by Language
Figure A2 depicts the distribution of file sizes for several programming languages, such as HTML, CSS, Java, JavaScript, C++, PHP, C, and Ruby. The y-axis displays file sizes on a logarithmic scale, and the x-axis lists the languages. Each box plot shows the median, interquartile range, and whiskers indicating the minimum and maximum values, with outliers represented by individual dots. This figure enables an easy comparison of file size distributions across languages.
Figure A2.
Box plot distribution by languages. Source: author’s contribution.
Figure A2.
Box plot distribution by languages. Source: author’s contribution.
Appendix C.2. Time-Based Visualizations
Figure A3, with a line graph titled “Yearly File Trends”, is showing the number of files from 2020 to 2023. The y-axis indicates the number of files, ranging from about 61,900 to 62,150, while the x-axis represents the years. Key observations include the following:
- An increase in file numbers from 2020 to a peak in 2021.
- A notable decline in 2022.
- A slight increase in 2023, though this is still below the 2021 peak.
The graph highlights the fluctuations in file counts over the specified years. The graph presented in Figure A3 illustrates time-based visualizations, which are essential for analyzing data over specific time-periods to identify trends and patterns. Line graphs, bar charts, and area charts are commonly used in fields such as corporate analytics, finance, healthcare, and environmental studies. These visualizations aid in trend analysis, forecasting, and informed decision-making by offering clear insights into temporal changes in data. Overall, the graph effectively captures the fluctuations in file counts over time, providing a comprehensive view of their dynamic progression.
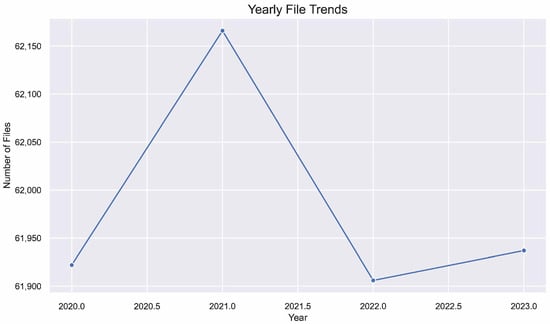
Figure A3.
Fluctuations in file counts over the specified years of 2020–2023. Source: author’s contribution.
Figure A3.
Fluctuations in file counts over the specified years of 2020–2023. Source: author’s contribution.
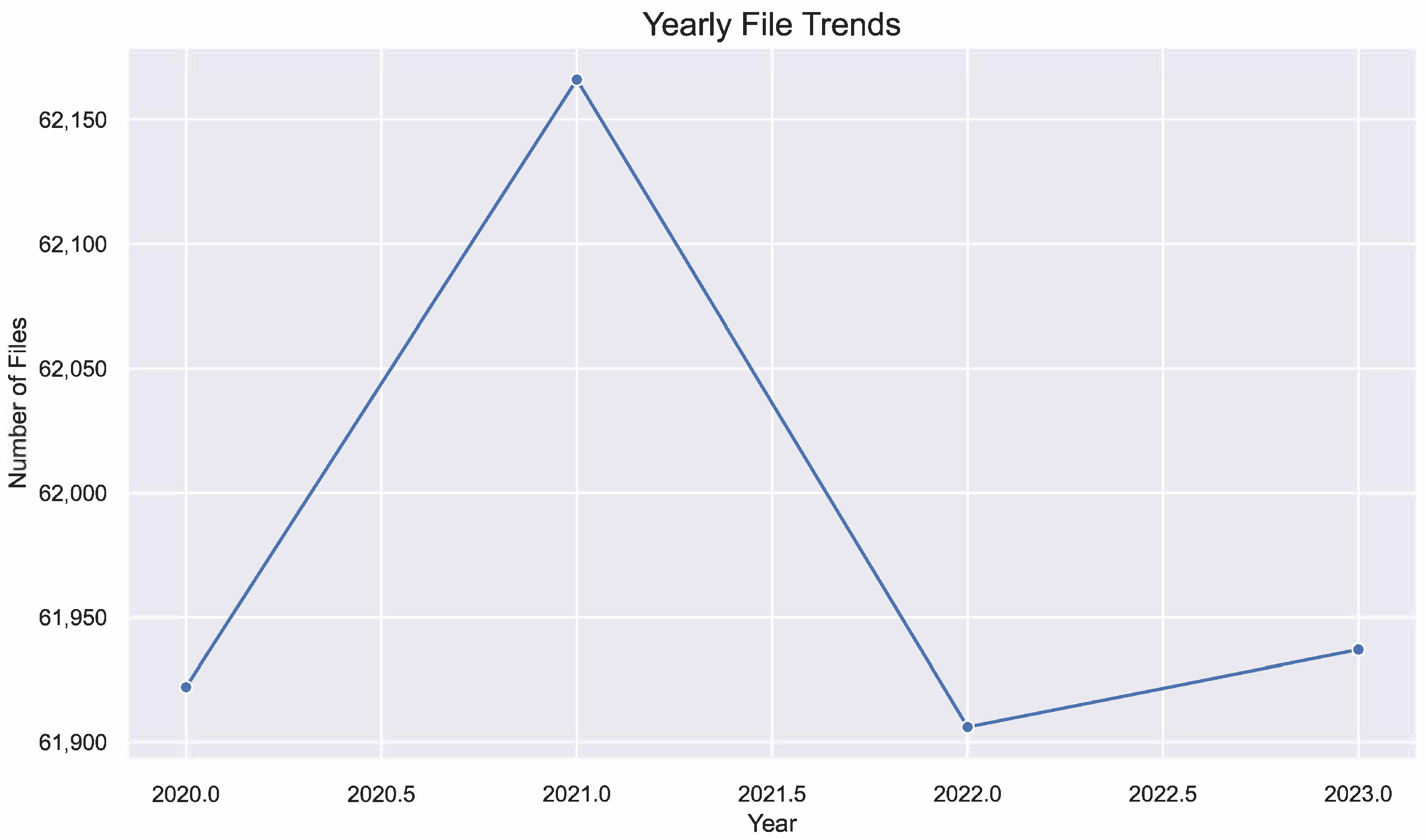
Figure A4 presents a heatmap titled “Monthly File Trends (Yearly Breakdown)”, illustrating the number of files recorded each month from 2020 to 2023. The y-axis represents the years, while the x-axis corresponds to the months (1 to 12). Each cell displays the file count for a given month and year, with color intensity indicating the magnitude of the values—darker shades reflect higher file counts.
This visualization effectively captures the fluctuations in file activity over time, highlighting seasonal trends and variations. The color-coded format allows for easy comparison across months and years, facilitating the identification of patterns in file management. The data reveals recurring peaks and troughs, with certain months consistently exhibiting higher activity, which could inform resource allocation and future planning.
Key Observations:
- 2020: File counts remained relatively stable, ranging from 4810 to 5388, with a peak in May (5388).
- 2021: This year saw the highest file counts, particularly in the first half, with notable peaks in January (5381) and May (5370). Monthly counts generally remained above 5000.
- 2022: There was a decline in file counts compared to 2021, with the highest monthly count reaching 5275 in January. Fluctuations were more pronounced, with some months falling below 5000.
- 2023: A slight recovery is evident, with file counts ranging from 4867 to 5337. January (5301) and May (5328) saw the highest values, suggesting an upward trend compared to 2022.
- This heatmap serves as a valuable tool for analyzing temporal trends in file management, offering clear insights into variations and helping to anticipate future needs.
The data demonstrate significant changes in file numbers across months and years. The highest readings were observed in 2021, notably during the first half of the year. Overall, file numbers fluctuate regularly, with certain months having higher counts over time.
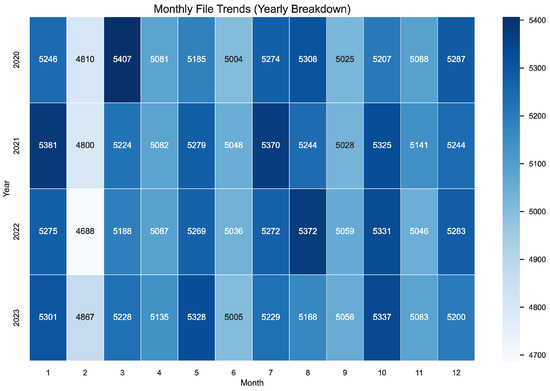
Figure A4.
Monthly file trends (yearly breakdown). Source: author’s contribution.
Figure A4.
Monthly file trends (yearly breakdown). Source: author’s contribution.
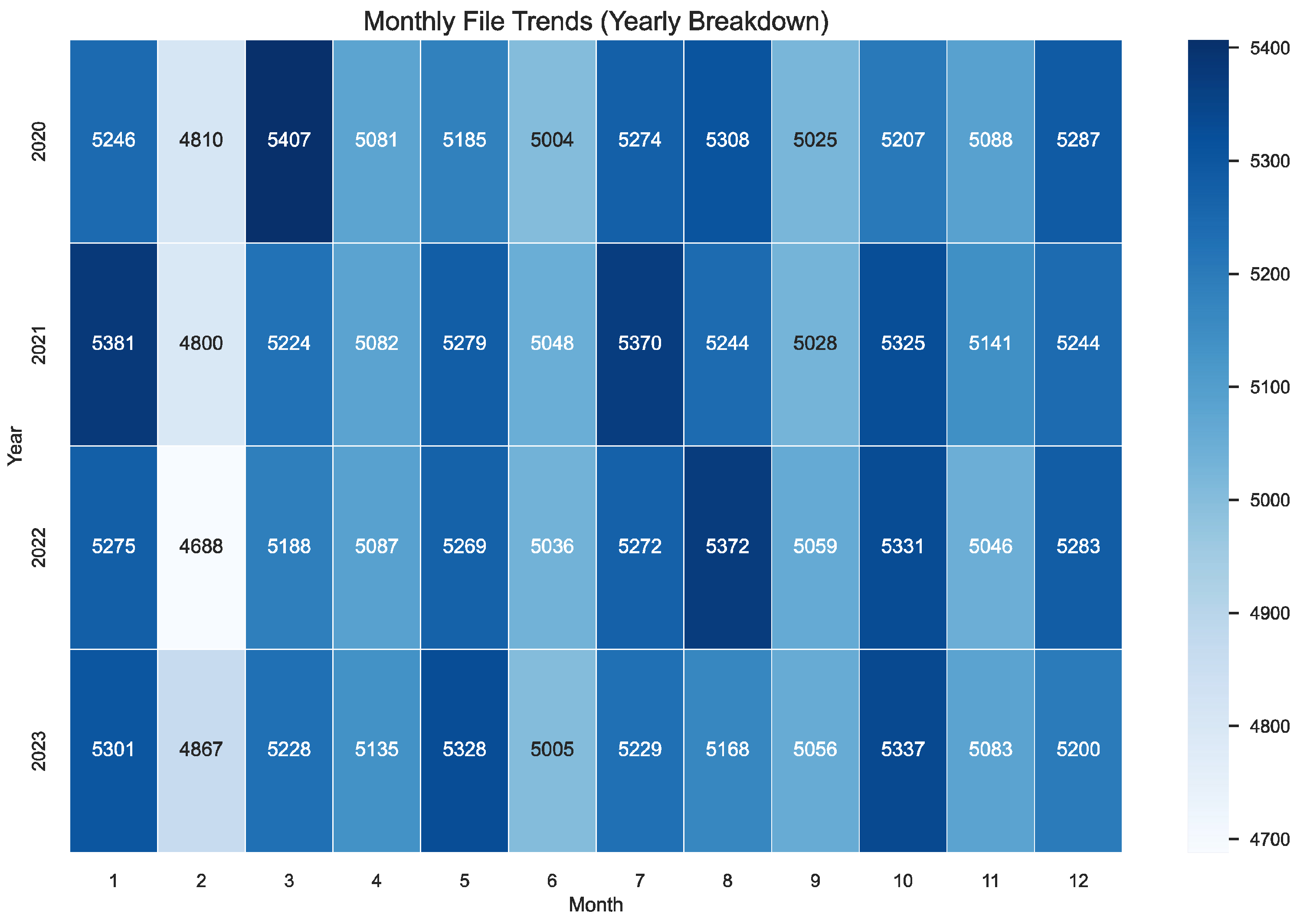
Figure A5 presents a scatter plot titled “Daily File Trends”, showing the number of files recorded daily from January 2020 to January 2024. The y-axis represents file counts, ranging from approximately 140 to 220, while the x-axis displays the corresponding dates. The plot reveals considerable variability in daily file counts, with peaks reaching around 220 files on certain days, indicating occasional bursts of activity. While the overall trend suggests stability in daily file numbers, noticeable fluctuations and irregularities are observed.
This scatter plot effectively captures daily variations, offering valuable insights into trends and patterns over time. It can help identify specific days of unusually high or low activity, providing a deeper understanding of the factors influencing file management. This visualization is a useful tool for planning and resource allocation.
Figure A5.
Daily file trends. Source: author’s contribution.
Figure A5.
Daily file trends. Source: author’s contribution.
References
- Hassan, T. World Report 2024: Rights Trends in Afghanistan; Human Rights Watch: New York, NY, USA, 2024. [Google Scholar]
- Stupavsky, I.; Dakic, P.; Todorovic, V.; Aleksic, M. Historical aspect and impact of fake news on business in various industries. In Proceedings of the 96th International Scientific Conference on Economic and Social Development–“Era of Global Crises”, Belgrade, Serbia, 18–19 May 2023; Varazdin Development and Entrepreneurship Agency (VADEA): Varazdin, Croatia, 2023. [Google Scholar]
- Lee, W.T.; Chen, C.H. Agile software development and reuse approach with Scrum and software product line engineering. Electronics 2023, 12, 3291. [Google Scholar] [CrossRef]
- Beck, K.; Beedle, M.; Van Bennekum, A.; Cockburn, A.; Cunningham, W.; Fowler, M.; Grenning, J.; Highsmith, J.; Hunt, A.; Jeffries, R.; et al. Manifesto for Agile Software Development; Agile Alliance: Dallas, TX, USA, 2001. [Google Scholar]
- Almeida, F.; Bálint, B. Approaches for Hybrid Scaling of Agile in the IT Industry: A Systematic Literature Review and Research Agenda. Information 2024, 15, 592. [Google Scholar] [CrossRef]
- Ciancarini, P.; Giancarlo, R.; Grimaudo, G. Scrum@ PA: Tailoring an Agile Methodology to the Digital Transformation in the Public Sector. Information 2024, 15, 110. [Google Scholar] [CrossRef]
- Pacheco-Cubillos, D.B.; Boria-Reverter, J.; Gil-Lafuente, J. Transitioning to Agile Organizational Structures: A Contingency Theory Approach in the Financial Sector. Systems 2024, 12, 142. [Google Scholar] [CrossRef]
- Sepúlveda, S.; Cravero, A.; Fonseca, G.; Antonelli, L. Systematic Review on Requirements Engineering in Quantum Computing: Insights and Future Directions. Electronics 2024, 13, 2989. [Google Scholar] [CrossRef]
- Babiuch, M.; Foltynek, P. Implementation of a Universal Framework Using Design Patterns for Application Development on Microcontrollers. Sensors 2024, 24, 3116. [Google Scholar] [CrossRef] [PubMed]
- Dahinine, B.; Laghouag, A.; Bensahel, W.; Alsolamy, M.; Guendouz, T. Evaluating Performance Measurement Metrics for Lean and Agile Supply Chain Strategies in Large Enterprises. Sustainability 2024, 16, 2586. [Google Scholar] [CrossRef]
- Bano, M.; Zowghi, D. Users’ involvement in requirements engineering and system success. In Proceedings of the 2013 3rd International Workshop on Empirical Requirements Engineering (EmpiRE), Rio de Janeiro, Brazil, 15 July 2013; IEEE: New York, NY, USA, 2013; pp. 24–31. [Google Scholar]
- Haiderzai, M.D.; Vranić, V. Patterns for Improving User Contribution. In Proceedings of the 28th European Conference on Pattern Languages of Programs, Irsee, Germany, 5–9 July 2023; pp. 1–9. [Google Scholar]
- Hoptsii, D.; Siedov, A.; Anopriienko, T.; Khainus, D.; Yaremko, D. Advantages of using QGIS to solve spatial planning tasks. Balt. Surv. 2023, 18, 50–56. [Google Scholar]
- QGIS Project. Documentation for QGIS 3.34—QGIS Documentation Documentation. 2024. Available online: https://docs.qgis.org/3.34/en/docs/index.html (accessed on 20 September 2024).
- Dakić, P.; Todosijević, A.; Pavlović, M. The importance of business intelligence for business in marketing agency. In Proceedings of the International Scientific Conference ERAZ 2016 Knowledge Based Sustainable, Belgrade, Serbia, 16 June 2016. [Google Scholar]
- Dakić, P.; Lojaničić, D.; Issa, H.R.; Bogavac, M. Choosing, Creating and Developing Managers. Oditor 2021, 7, 105–134. [Google Scholar] [CrossRef]
- Dakic, P.; Todorovic, V.; Vranic, V. Financial Justification for using CI/CD and Code Analysis for Software Quality Improvement in the Automotive Industry. In Proceedings of the 2022 IEEE Zooming Innovation in Consumer Technologies Conference (ZINC), Novi Sad, Serbia, 25–26 May 2022; IEEE: New York, NY, USA, 2022; pp. 149–154. [Google Scholar] [CrossRef]
- Golis, T.; Dakić, P.; Vranić, V. Creating Microservices and using infrastructure as code within the CI/CD for dynamic container creation. In Proceedings of the 2022 IEEE 16th International Scientific Conference on Informatics (Informatics), Poprad, Slovakia, 23–25 November 2022; IEEE: New York, NY, USA, 2022; pp. 114–119. [Google Scholar] [CrossRef]
- Hroncova, N.; Dakic, P. Research Study on the Use of CI/CD Among Slovak Students. In Proceedings of the 2022 12th International Conference on Advanced Computer Information Technologies (ACIT), Ruzomberok, Slovakia, 26–28 September 2022; IEEE: New York, NY, USA, 2022; pp. 458–461. [Google Scholar] [CrossRef]
- Cák, F.; Dakić, P. Configuration Tool for CI/CD Pipelines and React Web Apps. In Proceedings of the 2024 14th International Conference on Advanced Computer Information Technologies (ACIT), Ceske Budejovice, Czech Republic, 19–21 September 2024; IEEE: New York, NY, USA, 2024; Volume 16, pp. 586–591. [Google Scholar] [CrossRef]
- Dakić, P.; Filipović, L.; Starčević, M. Application of Fundamental Analysis in Investment Decision Making Example of a Domestic Business Entity; Association of Economists and Managers of the Balkans-Udekom Balkan: Belgrade, Serbia, 2019. [Google Scholar]
- Kaunert, C.; Sahar, A. Violence, Terrorism, and Identity Politics in Afghanistan: The Securitisation of Higher Education. Soc. Sci. 2021, 10, 150. [Google Scholar] [CrossRef]
- Sarwari, F.; Ono, H. A Study on Urban Ethnic Segmentation in Kabul City, Afghanistan. Sustainability 2023, 15, 6589. [Google Scholar] [CrossRef]
- Casola, V.; De Benedictis, A.; Rak, M.; Villano, U. A novel Security-by-Design methodology: Modeling and assessing security by SLAs with a quantitative approach. J. Syst. Softw. 2020, 163, 110537. [Google Scholar] [CrossRef]
- Saravanos, A.; Curinga, M.X. Simulating the Software Development Lifecycle: The Waterfall Model. Appl. Syst. Innov. 2023, 6, 108. [Google Scholar] [CrossRef]
- Royce, W.W. Managing the development of large software systems. In Proceedings of the IEEE WESCON, Los Angeles, CA, USA, 25–28 August 1970; pp. 328–388. [Google Scholar]
- Boehm, B.W. A spiral model of software development and enhancement. Computer 1988, 21, 61–72. [Google Scholar] [CrossRef]
- Raymond, E. Homesteading the Noosphere, the Cathedral, and the Bazaar: Musings on Linux and Open Source by an Accidental Revolutionary; O’Reilly & Associates: Sebastopol CA, USA, 1999; Volume 2, p. 8. [Google Scholar]
- Campbell-Kelly, M. From Airline Reservations to Sonic the Hedgehog: A History of the Software Industry; MIT Press: Cambridge, MA, USA, 2004. [Google Scholar]
- Hohl, P.; Klünder, J.; van Bennekum, A.; Lockard, R.; Gifford, J.; Münch, J.; Stupperich, M.; Schneider, K. Back to the future: Origins and directions of the “Agile Manifesto”–views of the originators. J. Softw. Eng. Res. Dev. 2018, 6, 15. [Google Scholar] [CrossRef]
- Haputhanthrige, V.; Asghar, I.; Saleem, S.; Shamim, S. The Impact of a Skill-Driven Model on Scrum Teams in Software Projects: A Catalyst for Digital Transformation. Systems 2024, 12, 149. [Google Scholar] [CrossRef]
- Bass, L.; Weber, I.; Zhu, L. DevOps: A Software Architect’s Perspective; Addison-Wesley Professional: Boston, MA, USA, 2015. [Google Scholar]
- Jacobson, I. The Unified Software Development Process; Pearson Education: Noida, India, 1999. [Google Scholar]
- Corbató, F.J.; Saltzer, J.H.; Clingen, C.T. Multics: The first seven years. In Proceedings of the Spring Joint Computer Conference, Atlantic City, NJ, USA, 16–18 May 1972; pp. 571–583. [Google Scholar]
- Kilburn, T.; Edwards, D.B.; Lanigan, M.J.; Sumner, F.H. One-level storage system. Ire Trans. Electron. Comput. 1962, EC-11, 223–235. [Google Scholar] [CrossRef]
- Naur, P.; Randell, B. Software Engineering: Report of a conference sponsored by the NATO Science Committee. In Proceedings of the NATO Software Engineering Conference, Garmisch, Germany, 7–11 October 1968; Scientific Affairs Division, NATO: Brussels, Belgium, 1969. [Google Scholar]
- Beck, K. Extreme Programming Explained: Embrace Change; Addison-Wesley: Boston, MA, USA, 2000. [Google Scholar]
- Poppendieck, M.; Poppendieck, T. Lean Software Development: An Agile Toolkit; Addison-Wesley: Boston, MA, USA, 2003. [Google Scholar]
- Palmer, S.R.; Felsing, M. A Practical Guide to Feature-Driven Development; Pearson Education: London, UK, 2001. [Google Scholar]
- Turing, A.M. On computable numbers, with an application to the Entscheidungsproblem. J. Math 1936, 58, 5. [Google Scholar]
- Larusdottir, M.K.; Kyas, M. Selecting the Best Agile Team for Developing a Web Service. In Human Computer Interaction and Emerging Technologies: Adjunct Proceedings from the INTERACT 2019 Workshops; Cardiff University Press: Cardiff, UK, 2020; pp. 289–302. [Google Scholar] [CrossRef]
- Melnyk, K.V.; Hlushko, V.N.; Borysova, N.V. Decision support technology for sprint planning. Radio Electron. Comput. Sci. Control 2020, 1, 135–145. [Google Scholar] [CrossRef]
- Altaleb, A.; Altherwi, M.; Gravell, A. A Pair Estimation Technique of Effort Estimation in Mobile App Development for Agile Process: Case Study. In Proceedings of the 2020 The 3rd International Conference on Information Science and System, ICISS 2020, Cambridge, UK, 19–22 March 2020; ACM: New York, NY, USA, 2020; pp. 29–37. [Google Scholar] [CrossRef]
- Muntés-Mulero, V.; Ripolles, O.; Gupta, S.; Dominiak, J.; Willeke, E.; Matthews, P.; Somosköi, B. Agile risk management for multi-cloud software development. IET Softw. 2019, 13, 172–181. [Google Scholar] [CrossRef]
- Lewis, J.; Fowler, M. Microservices: A Definition of This New Architectural Term. 2014, Volume 25, p. 12. Available online: https://MartinFowler.com (accessed on 15 October 2024).
- Karamitsos, I.; Albarhami, S.; Apostolopoulos, C. Applying DevOps practices of continuous automation for machine learning. Information 2020, 11, 363. [Google Scholar] [CrossRef]
- Harman, M. The role of artificial intelligence in software engineering. In Proceedings of the 2012 First International Workshop on Realizing AI Synergies in Software Engineering (RAISE), Zurich, Switzerland, 5 June 2012; IEEE: New York, NY, USA, 2012; pp. 1–6. [Google Scholar]
- Kleppe, A.G.; Warmer, J.B.; Bast, W. MDA Explained: The Model Driven Architecture: Practice and Promise; Addison-Wesley Professional: Boston, MA, USA, 2003. [Google Scholar]
- Deursen, A.V.; Klint, P. Little languages: Little maintenance? J. Softw. Maint. Res. Pract. 1998, 10, 75–92. [Google Scholar] [CrossRef]
- Kelly, S.; Tolvanen, J.P. Domain-Specific Modeling: Enabling Full Code Generation; John Wiley & Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- Voelter, M.; Benz, S.; Dietrich, C.; Engelmann, B.; Helander, M.; Kats, L.C.; Visser, E.; Wachsmuth, G. DSL Engineering-Designing, Implementing and Using Domain-Specific Languages; CreateSpace Independent Publishing Platform: Scotts Valley, CA, USA, 2013. [Google Scholar]
- Schmidt, D.C. Model-driven engineering. Comput.-IEEE Comput. Soc. 2006, 39, 25. [Google Scholar] [CrossRef]
- Mernik, M.; Heering, J.; Sloane, A.M. When and how to develop domain-specific languages. ACM Comput. Surv. (CSUR) 2005, 37, 316–344. [Google Scholar] [CrossRef]
- France, R.; Rumpe, B. Domain specific modeling. Softw. Syst. Model. 2005, 4, 1–3. [Google Scholar] [CrossRef]
- Spinellis, D. Notable design patterns for domain-specific languages. J. Syst. Softw. 2001, 56, 91–99. [Google Scholar] [CrossRef]
- Voelter, M. Language and IDE Modularization and Composition with MPS. In International Summer School on Generative and Transformational Techniques in Software Engineering; Springer: Berlin/Heidelberg, Germany, 2011; pp. 383–430. [Google Scholar]
- Kreitz, M. Security by design in software engineering. ACM SIGSOFT Softw. Eng. Notes 2019, 44, 23. [Google Scholar] [CrossRef]
- Kosar, T.; Bohra, S.; Mernik, M. Domain-specific languages: A systematic mapping study. Inf. Softw. Technol. 2016, 71, 77–91. [Google Scholar] [CrossRef]
- Hinton, G.E.; Roweis, S. Stochastic Neighbor Embedding. In Advances in Neural Information Processing Systems; Becker, S., Thrun, S., Obermayer, K., Eds.; MIT Press: Cambridge, MA, USA, 2002; Volume 15. [Google Scholar]
- Guéhéneuc, Y.G. p-mart-Repository-Programs. 2024. Available online: https://github.com/ptidejteam/p-mart-Repository-Programs (accessed on 24 November 2024).
- GNU Lesser General Public License. 2023. Available online: https://www.gnu.org/ (accessed on 24 November 2024).
- Haiderzai, M.D.; Khattab, M.I. How software testing impact the quality of software systems? Int. J. Eng. Comput. Sci. 2019, 1, 5–9. [Google Scholar] [CrossRef]
- Weichbrodt, J.; Kropp, M.; Biddle, R.; Gregory, P.; Anslow, C.; Bühler, U.M.; Mateescu, M.; Meier, A. Understanding Leadership in Agile Software Development Teams: Who and How? In Agile Processes in Software Engineering and Extreme Programming; Springer International Publishing: Berlin/Heidelberg, Germany, 2022; pp. 99–113. [Google Scholar] [CrossRef]
- Chan, H.M.H.; Cho, V.W.S. An Empirical Study: The Impact of Collaborative Communications on New Product Creativity That Contributes to New Product Performance. Sustainability 2022, 14, 4626. [Google Scholar] [CrossRef]
- Dakic, P.; Zivkovic, M.; Jovanovic, L.; Bacanin, N.; Antonijevic, M.; Kaljevic, J.; Simic, V. Intrusion detection using metaheuristic optimization within IoT/IIoT systems and software of autonomous vehicles. Sci. Rep. 2024, 14, 22884. [Google Scholar] [CrossRef] [PubMed]
- Vărzaru, A.A.; Bocean, C.G. Digital Transformation and Innovation: The Influence of Digital Technologies on Turnover from Innovation Activities and Types of Innovation. Systems 2024, 12, 359. [Google Scholar] [CrossRef]
- Karppi, M.; Aramo-Immonen, H.; Hyrkkänen, U.; Jokisaari, M. Emergence of shared leadership in project teams: The role of events. Proj. Leadersh. Soc. 2024, 5, 100145. [Google Scholar] [CrossRef]
- Moutsatsos, P. Beyond Agility: Flex to the Future. Pulse of the Profession; Project Management Institute: Newtown Square, PA, USA, 2021. [Google Scholar]
- Mitrović, Z.; Petrović, D.; Mihić, M. Rethinking success in software projects. Tehnika 2020, 75, 639–645. [Google Scholar] [CrossRef]
- Appelo, J. Management 3.0: Leading Agile Developers, Developing Agile Leaders; Addison-Wesley Signature Series (Cohn); Pearson Education: London, UK, 2010. [Google Scholar]
- Nerur, S.; Mahapatra, R.; Mangalaraj, G. Challenges of migrating to agile methodologies. Commun. ACM 2005, 48, 72–78. [Google Scholar] [CrossRef]
- Zaimovic, T.; Kozic, M.; Efendić, A.; Džanić, A. Self-Organizing Teams in Software Development–Myth or Reality. TEM J. 2021, 10, 1565–1571. [Google Scholar] [CrossRef]
- Mutawalli, L.; Fathoni, B.K.; Asyari, H. Implementasi scrum dalam pengembangan sistem informasi jasa desain grafis. J. Manaj. Inform. Sist. Inf. 2020, 3, 116–122. [Google Scholar] [CrossRef]
- Anggraeny, M.D.; Kurniawati, A.; Anggraini, D. Tingkat Kematangan Implementasi Scrum Menggunakan Scrum Maturity Model Pada Direktorat TSI. G-Tech J. Teknol. Terap. 2023, 8, 247–254. [Google Scholar] [CrossRef]
- Azanha, A.; Argoud, A.R.T.T.; Camargo Junior, J.B.d.; Antoniolli, P.D. Agile project management with Scrum: A case study of a Brazilian pharmaceutical company IT project. Int. J. Manag. Proj. Bus. 2017, 10, 121–142. [Google Scholar] [CrossRef]
- Mahalakshmi, M.; Sundararajan, M. Traditional SDLC vs scrum methodology–a comparative study. Int. J. Emerg. Technol. Adv. Eng. 2013, 3, 192–196. [Google Scholar]
- Ashraf, S.; Aftab, S. Pragmatic Evaluation of IScrum & Scrum. Int. J. Mod. Educ. Comput. Sci. 2018, 10, 24–35. [Google Scholar] [CrossRef]
- Qureshi, R.J.; Alassafi, M.O.; Shahzad, H.M. Lean Agile Integration for the Development of Large Size Projects. Int. J. Mod. Educ. Comput. Sci. 2019, 11, 24–33. [Google Scholar] [CrossRef]
- Abrahamsson, P.; Salo, O.; Ronkainen, J.; Warsta, J. Agile Software Development Methods: Review and Analysis. arXiv 2017, arXiv:1709.08439. [Google Scholar] [CrossRef]
- Qureshi, R.; Basheri, M.; A Alzahrani, A. Novel Framework to Improve Communication and Coordination among Distributed Agile Teams. Int. J. Inf. Eng. Electron. Bus. 2018, 10, 16–24. [Google Scholar] [CrossRef]
- Ibrahim, M.; Aftab, S.; Bakhtawar, B.; Ahmad, M.; Iqbal, A.; Aziz, N.; Javeid, M.; Ihnaini, B. Exploring the Agile Family: A Survey. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2020, 20, 163–179. [Google Scholar] [CrossRef]
- Qureshi, M.R.J. Empirical Evaluation of the Proposed eXScrum Model: Results of a Case Study. IJCSI Int. J. Comput. Sci. 2012, 8, 150–157. [Google Scholar] [CrossRef]
- Ashraf, S.; Aftab, S. IScrum: An Improved Scrum Process Model. Int. J. Mod. Educ. Comput. Sci. 2017, 9, 16–24. [Google Scholar] [CrossRef]
- Sremath Tirumala, S.; Ali, S.; Babu G, A. A Hybrid Agile model using SCRUM and Feature Driven Development. Int. J. Comput. Appl. 2016, 156, 5. [Google Scholar] [CrossRef]
- Shahane, D.; Jamsandekar, P.; Shahane, D. Factors influencing the agile methods in practice—Literature survey & review. In Proceedings of the 2014 International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 5–7 March 2014; IEEE: New York, NY, USA, 2014; Volume 10, pp. 556–560. [Google Scholar] [CrossRef]
- Petrović, D. Implementation of agile management and business agility. Tehnika 2022, 77, 485–491. [Google Scholar] [CrossRef]
- Todorović, V.; Dakić, P.; Stupavský, I. The future of robotic vehicles with the contradictions of process in the green agenda and production of different power sources. MB Univ. Int. Rev. 2024, 2, 6–27. [Google Scholar] [CrossRef]
- Heričko, T.; Šumak, B.; Karakatič, S. Commit-Level Software Change Intent Classification Using a Pre-Trained Transformer-Based Code Model. Mathematics 2024, 12, 1012. [Google Scholar] [CrossRef]
- Carroll, N.; Conboy, K.; Wang, X. From transformation to normalisation: An exploratory study of a large-scale agile transformation. J. Inf. Technol. 2023, 38, 267–303. [Google Scholar] [CrossRef]
- Holbeche, L. The Agile Organization: How to Build an Engaged, Innovative and Resilient Business; Kogan Page Publishers: London, UK, 2023. [Google Scholar]
- Poth, A. Facilitating the Agile Transformation of Large-Scale Industrial Organizations for Quality Management in Light of the Digital Era. Ph.D. Thesis, Université Grenoble Alpes, Saint-Martin-d’Hères, France, 2021. [Google Scholar]
- Galantini, L.; Messina, A.; Ruggiero, M. Software requirements complexity analysis to support the “advisory network in to the nation forces build-up”. In Proceedings of the 6th International Conference in Software Engineering for Defence Applications: SEDA 2018, Rome, Italy, 7–8 June 2018; Springer: Cham, Switzerland, 2020; pp. 187–197. [Google Scholar]
- Elias, B. Identifying Success and Failure Factors of Agile software development in afghan software Companies. Int. J. Res. Anal. Rev.-IJRAR 2024, 11. [Google Scholar] [CrossRef]
- Baheer, B.A.; Sousa, S.; Lamas, D. Readiness of Afghan government for the deployment of e-government solutions. In Proceedings of the 8th International Conference on Theory and Practice of Electronic Governance, Guimaraes, Portugal, 27–30 October 2014; pp. 488–489. [Google Scholar]
- Samsor, A.M. Challenges and Prospects of e-Government implementation in Afghanistan. Int. Trade Politics Dev. 2021, 5, 51–70. [Google Scholar] [CrossRef]
- Fangmann, J.; Looks, H.; Thomaschewski, J.; Schön, E.M. Agile transformation in e-government projects. In Proceedings of the 2020 15th Iberian Conference on Information Systems and Technologies (CISTI), Sevilla, Spain, 24–27 June 2020; IEEE: New York, NY, USA, 2020; pp. 1–4. [Google Scholar]
- Ahmadzai, S.; Bakhsh, M. An Empirical Investigation on Lean Method Usage: Issues and Challenges in Afghanistan. In AI and IoT for Sustainable Development in Emerging Countries: Challenges and Opportunities; Springer: Cham, Switzerland, 2022; pp. 255–264. [Google Scholar]
- The Standish Group. The Standish Group CHAOS Report 2020; The Standish Group: Boston, MA, USA, 2020. [Google Scholar]
- VersionOne. State of Agile Report 2021; VersionOne: Alpharetta, GA, USA, 2021. [Google Scholar]
- McKinsey Company. The Agile Revolution: McKinsey’s Global Agile Survey 2020; McKinsey & Company: New York, NY, USA, 2020. [Google Scholar]
- Wang, H. Homology Feature Extraction Method of Malware Based on Genetic Algorithm and Association Mining. In Proceedings of the 2021 IEEE 16th Conference on Industrial Electronics and Applications (ICIEA), Chengdu, China, 1–4 August 2021; pp. 1127–1130. [Google Scholar] [CrossRef]
- Tian, Y.; Zhang, X.; Yang, B.; Wang, J.; An, S. An individual-based spatio-temporal travel demand mining method and its application in improving rebalancing for free-floating bike-sharing system. Adv. Eng. Inform. 2021, 50, 101365. [Google Scholar] [CrossRef]
- Ismail, E.; Alariqi, A.A.; Jawid, A.; Wall, J.; Abdulrab, M. Strategy, Policy, and Legal Barriers to E-Gov Implementation in Afghanistan. IEEE Access 2022, 10, 13800–13812. [Google Scholar] [CrossRef]
- Ali, T.E.; Ali, F.I.; Dakić, P.; Zoltan, A.D. Trends, prospects, challenges, and security in the healthcare internet of things. Computing 2024, 107, 28. [Google Scholar] [CrossRef]
- Shafiei, N.; Puttanna, K. An investigation into the factors causing international development project failure in developing countries: Focus on Afghanistan. J. Proj. Manag. 2021, 6, 157–170. [Google Scholar] [CrossRef]
- Dakić, P.; Źivković, M. An overview of the challenges for developing software within the field of autonomous vehicles. In Proceedings of the 7th Conference on the Engineering of Computer Based Systems, ECBS 2021, Novi Sad, Serbia, 26–27 May 2021; ACM: New York, NY, USA, 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Ali, T.E.; Ali, F.I.; Abdala, M.A.; Norbert, P.; Tejfel, M.; Zoltán, A.D. Exploring Application Deployment on Edge Solutions: A Focus on Mobile Edge Computing, Akraino Eliot, EdgeX, and OpenVINO for Healthcare Applications. In Proceedings of the International Conference on Recent Innovations in Computing, ICRIC 2023, Jammu, India, 26–27 October 2023; Springer Nature: Singapore, 2024; pp. 851–862. [Google Scholar] [CrossRef]
- Dakić, P.; Stupavský, I.; Todorović, V. The Effects of Global Market Changes on Automotive Manufacturing and Embedded Software. Sustainability 2024, 16, 4926. [Google Scholar] [CrossRef]
- Eyvazov, F.; Ali, T.E.; Ali, F.I.; Zoltan, A.D. Beyond Containers: Orchestrating Microservices with Minikube, Kubernetes, Docker, and Compose for Seamless Deployment and Scalability. In Proceedings of the 2024 11th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 14–15 March 2024; IEEE: New York, NY, USA, 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Dakić, P. Significance of Standards Compliance Organizations for the Sustainable Automotive Software and Car Production. Acta Polytech. Hung. 2024, 21, 325–344. [Google Scholar] [CrossRef]
- Meng, C.; Chen, N. TinyLog: Log Anomaly Detection with Lightweight Temporal Convolutional Network for Edge Device. In Proceedings of the 2024 International Joint Conference on Neural Networks (IJCNN), Yokohama, Japan, 30 June–5 July 2024; pp. 1–8. [Google Scholar] [CrossRef]
- Jahani, A.; Zare, K.; Mohammad Khanli, L. Short-term load forecasting for microgrid energy management system using hybrid SPM-LSTM. Sustain. Cities Soc. 2023, 98, 104775. [Google Scholar] [CrossRef]
- Latypova, V. Work with Free Response Implementation Process Analysis Based on Sequential Pattern Mining in Engineering Education. In Proceedings of the 2022 VI International Conference on Information Technologies in Engineering Education (Inforino), Moscow, Russia, 12–15 April 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Stupavský, I.; Vranić, V. Analysing the controversial social media community. In Proceedings of the 2022 IEEE 16th International Scientific Conference on Informatics (Informatics), Poprad, Slovakia, 23–25 November 2022; pp. 299–303. [Google Scholar] [CrossRef]
- Stupavský, I.; Dakić, P.; Vranić, V. The Impact of Fake News on Traveling and Antisocial Behavior in Online Communities: Overview. Appl. Sci. 2023, 13, 11719. [Google Scholar] [CrossRef]
- Ilieva, G.; Yankova, T.; Ruseva, M.; Dzhabarova, Y.; Zhekova, V.; Klisarova-Belcheva, S.; Mollova, T.; Dimitrov, A. Factors Influencing User Perception and Adoption of E-Government Services. Adm. Sci. 2024, 14, 54. [Google Scholar] [CrossRef]
- Rojas, L.F.; Quiñones, D.; Cubillos, C. FRAMUX-EV: A Framework for Evaluating User Experience in Agile Software Development. Appl. Sci. 2024, 14, 8991. [Google Scholar] [CrossRef]
- Tessarolo, F.; Petsani, D.; Conotter, V.; Nollo, G.; Conti, G.; Nikolaidou, M.; Onorati, G.; Bamidis, P.D.; Konstantinidis, E.I. Developing ambient assisted living technologies exploiting potential of user-centred co-creation and agile methodology: The CAPTAIN project experience. J. Ambient. Intell. Humaniz. Comput. 2024, 15, 2661–2676. [Google Scholar] [CrossRef]
- Coplien, J.O.; Harrison, N.B. Organizational Patterns of Agile Software Development; Prentice-Hall: Saddle River, NJ, USA, 2004. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).