Abstract
This study presents an innovative approach utilizing the new Shimizu–Morioka chaotic system. By integrating adaptive backstepping control with GYC partial region stability theory, we successfully achieve synchronization of a slave system with the proposed Shimizu–Morioka chaotic system. The architecture, encompassing the chaotic master system, synchronized slave system, adaptive backstepping controllers, and parameter update laws, has been implemented on an FPGA platform. Comparative analysis demonstrates that the synchronization convergence times (e1, e2, e3, and e4) are significantly reduced compared to conventional adaptive backstepping control methods, exhibiting speed enhancements of approximately 3.42, 3.55, 5.89, and 9.23 times for e1, e2, e3, and e4, respectively. Furthermore, the synchronization results obtained from continuous-time, discrete-time systems, and FPGA implementations exhibit consistent outcomes, validating the effectiveness of the proposed model and controller. Leveraging this validated synchronization framework, chaotic synchronization and secure image encryption are successfully implemented on the FPGA platform. The chaotic signal circuits are meticulously designed and integrated into the FPGA to facilitate a robust image encryption algorithm. In this system, digital signals generated by the synchronized slave chaotic system are utilized for image decryption, while the master chaotic system’s digital signals are employed for encryption. This dual-system architecture highlights the efficacy of the chaotic synchronization method based on the novel Shimizu–Morioka system for practical applications in secure communication.
1. Introduction
With the increasing adoption of mobile devices, the volume of mobile data has surged correspondingly. Among various types of mobile content, video content stands out due to its significantly higher bit rates, making it a primary driver of mobile traffic growth as projected for 2018. The annual growth in mobile video traffic per month is detailed in Ref. [1]. Since a large number of Internet video services fall within the realm of cloud-based applications, the trends in mobile cloud traffic closely mirror those of video content traffic. Despite the inherent memory and processing speed constraints of mobile devices, cloud services such as Netflix, YouTube, Pandora, and Spotify empower users to circumvent these limitations, delivering a seamless media consumption experience regardless of device capability.
Computer networks are inherently vulnerable to a wide range of security threats and attacks. For instance, unauthorized remote access by hackers can lead to data breaches and information compromise. Furthermore, malicious software can potentially erase data across numerous systems, causing substantial losses. Personal data, including sensitive images, messages, and videos, are also at risk of being permanently deleted. These pressing concerns underscore the critical need for robust encryption algorithms designed to enhance security and safeguard personal data from unauthorized access and destruction.
A variety of methods have been developed to encrypt messages and ensure secure transmission, yet the application of chaos in encryption represents a relatively recent innovation. Since the 1990s, researchers have identified a profound connection between chaos theory and cryptography [2,3,4,5]. The key distinction lies in their operational domains: cryptographic systems function within a finite field, whereas chaos theory applies to continuous domains. Despite this divergence, both fields exhibit notable parallels. Core principles of chaos theory, such as mixing, sensitivity to initial conditions, and parameter dependence, strongly correspond to cryptographic principles. For example, the mixing property in chaos theory closely mirrors the diffusion process in cryptographic systems [6]. Table 1 illustrates the shared attributes and distinctive features of these two fields [7,8,9].

Table 1.
Common characteristics between the properties of chaos and cryptography.
Since Edward Lorenz’s groundbreaking discovery of a chaotic system [10], numerous chaotic systems have been identified worldwide. Chaos is now recognized as an unpredictable and pervasive phenomenon in nature. Chaos theory has proven to be highly applicable across diverse domains, including digital communication, electronic engineering, biological systems, and secure communication [11,12,13,14,15,16,17,18]. Due to its unique and inherently unpredictable dynamic behavior, chaos presents significant challenges for analysis. As a result, the study of chaotic control and synchronization has garnered substantial attention in both theoretical research and practical applications.
This study proposes an innovative chaotic synchronization framework leveraging adaptive backstepping control and the GYC partial region stability theory [19]. This efficient strategy employs a control Lyapunov function formulated as a simple linear homogeneous function of the system states. As a result, the derived controllers and parameter update laws are substantially simplified, effectively reducing computational overhead and mitigating simulation inaccuracies. The synchronized chaotic systems, comprising the master system, slave system, adaptive backstepping controllers, and parameter update laws, have been successfully implemented on an FPGA platform.
The structure of this paper is as follows: Section 2 provides an overview of the Shimizu–Morioka chaotic system. Section 3 presents an innovative chaos synchronization approach leveraging adaptive backstepping control and the GYC partial region stability theory. The stability of the error dynamic system and the parametric error system is validated using Lyapunov theory, with the update laws derived in this section. Section 4 explores the discretization and FPGA-based implementation of chaos synchronization for the new Shimizu–Morioka system. Section 5 conducts a comprehensive security analysis of the system, highlighting its encryption speed and performance. Furthermore, it demonstrates the practicality of this approach through an FPGA hardware implementation for image encryption and decryption. Finally, Section 6 concludes the paper with key findings and insights.
2. Nonlinear Dynamics Analysis of the New Shimizu–Morioka System
The Shimizu–Morioka system is described by the following set of nonlinear differential equations: [20]:
The third item of Equation (1) changes to , and adds a fourth item to the four-wing Shimizu–Morioka system, transforming it into a new nonlinear dimensional system. This updated Shimizu–Morioka system is expressed as follows:
In this context, a, b, c, d, and r represent the parameters. For this section, the chosen values for these parameters are a = 0.45, b = 0.75, c = 1, d = 0.01, and r = 0.55.
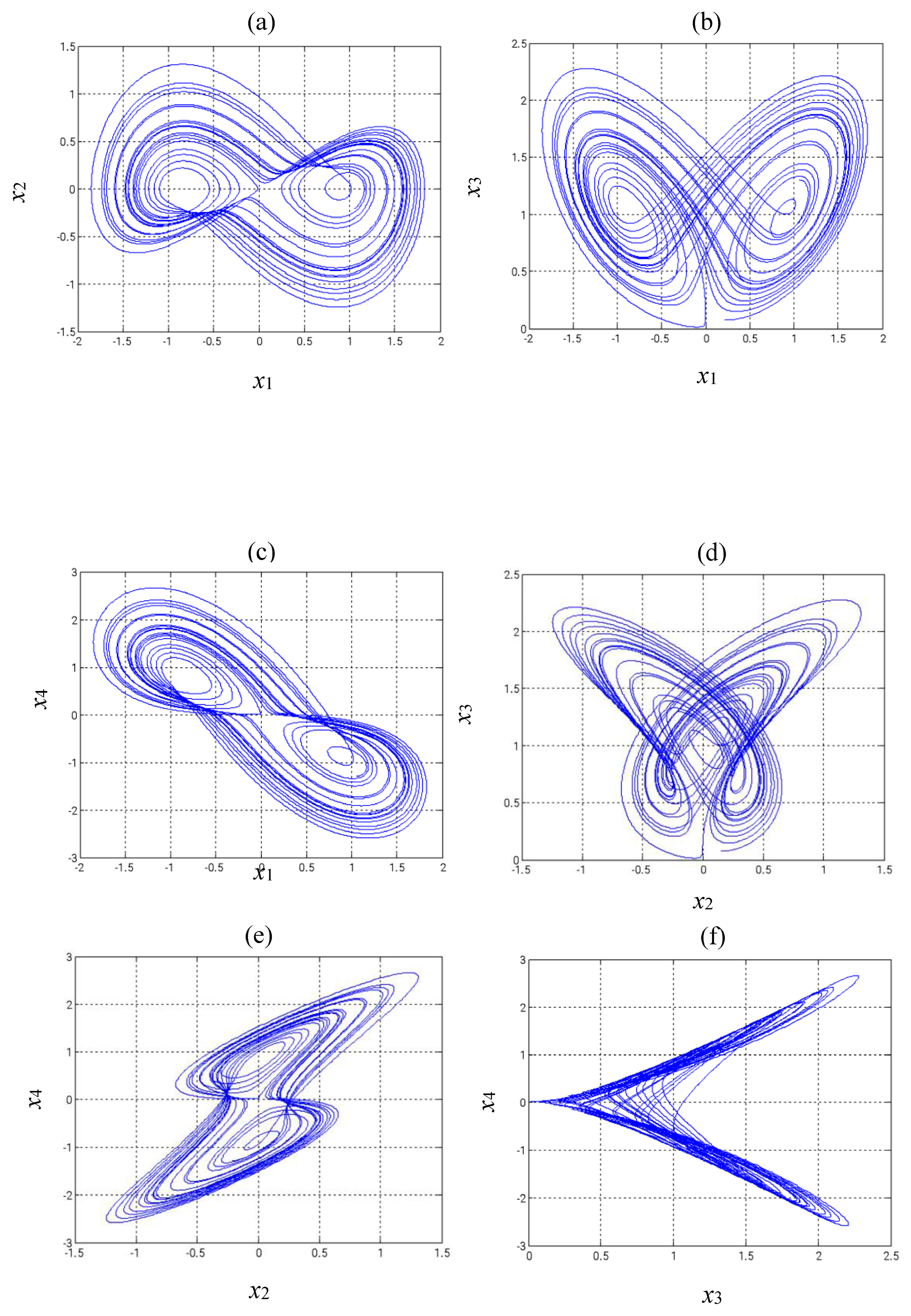
Figure 1 illustrates the two-dimensional phase diagrams of the modified Shimizu–Morioka system, which exhibit its chaotic dynamics.
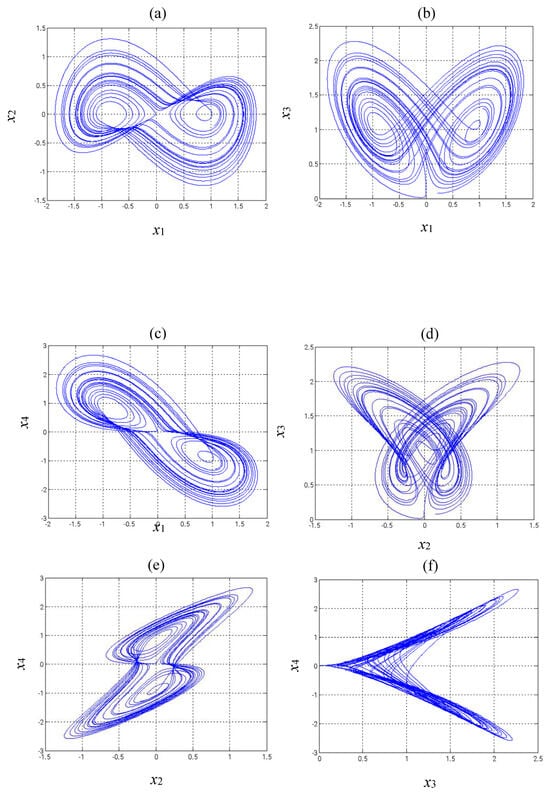
Figure 1.
Phase diagrams of the updated Shimizu–Morioka system: (a) - Phase, (b)- Phase, (c) - Phase, (d) - Phase, (e) - Phase, (f) - Phase.
3. Achieving Chaotic Synchronization of the Updated Shimizu–Morioka System Through Adaptive Backstepping Control and GYC Partial Region Stability Theory
3.1. Chaos Synchronization Method
Imagine two identical chaotic dynamical systems, where the master system is defined as follows:
where represents the state vector; is an constant coefficient matrix; f s a nonlinear vector function; and is a vector of constant coefficients in f.
The slave system is described as follows:
where represents the state vector; is an estimated coefficient matrix; is a vector of estimated coefficients in f; and is the control input vector.
Chaos synchronization is achieved as time approaches infinity, when the error vector tends to zero:
The constant Gk is chosen. The inclusion of Gk ensures that the error dynamics remain within the first quadrant at all times. By differentiating Equation (6), the error dynamic equations are obtained as follows:
Using GYC partial region stability theory, Lyapunov functions of the form of positive definite functions in the first quadrant were chosen:
where and . and must be greater than zero.
The derivative along any trajectory of the system described by the differential equations, including Equation (8) and the parameter update equations for and , are as follows:
where ui(t), , and are selected so that C1j, C2j, and C3j are negative values. The problem to realize the chaos synchronization between two identical chaotic systems now transforms to another problem on how to designed control laws ui and update laws and to make , and generally converge to zero with time increasing. The design of adaptive backstepping control, combined with GYC partial region stability theory, is employed to accomplish the desired objective.
This paper presents an example where the error dynamics and parameter dynamics are positioned within the first quadrant of the coordinate plane, leveraging the GYC partial region stability framework. The Lyapunov functions applied are simple linear homogeneous expressions of the states, facilitating the development of lower-order controllers that are more efficient and computationally less intensive compared to traditional methods.
3.2. Design and Numerical Analysis of Synchronization Using Adaptive Backstepping Control with the GYC Partial Region Stability Framework
GYC partial region stability theory [19] is utilized in this section to achieve adaptive backstepping control synchronization. By applying this framework, the new Shimizu–Morioka function can be expressed as a linear homogeneous form, streamlining the controller design process for chaotic synchronization.
This section examines two identical nonlinear dynamical systems, with the slave system tracking and governing the dynamics of the master system. The behavior of the master system is defined by the following set of equations:
where the values of parameters are a = 0.45, b = 0.75, c = 1, d = 0.01, and r = 0.55 in numerical simulation.
The slave system is described as follows:
The initial conditions of the master system, of the slave system, and of estimated parameters are , , , and , respectively.
The error function can be defined as follows:
When Gk = 1, inclusion of the constant Gk ensures that the error dynamics always remain in the first quadrant. From the derivative of Equation (13), the error dynamic equation be obtained as follows:
where , , , , and are the error of parameters, which are positive numbers. u1(t), u2(t), u3(t), and u4(t) are controllers. These controllers enable the two systems to achieve synchronization as time approaches infinity, with the error function converging to zero in the limit.
Step I. Starting with the first Equation (16), the application of GYC partial region stability theory involves selecting a Lyapunov function (V1), which is a positive definite function specifically defined within the first quadrant:
The time derivative of this function is expressed as follows:
The controller u1(t) is defined as follows:
Equation (16) can be reformulated as follows:
This function was shown to be a negative definite with respect to e1 in the first quadrant. As a result, it met the criteria for both the Lyapunov asymptotic stability theorem and the GYC partial region stability framework. The common origin of the error dynamic Equation (16) was determined to be asymptotically stable.
Step II. We consider e2 to act as the virtual controller.
To analyze the (,) system, the following was carried out:
According to , m1 is shown as follows:
Then, can be outlined as follows:
Using GYC partial region stability theory, a Lyapunov function (V2) was chosen as a positive definite function specifically formulated for the first quadrant:
The time derivative is transformed into the following:
The controller u2(t) and the parameter update rules () were formulated as follows:
Equation (23) can be reformulated as follows:
This function was shown to be a negative definite with respect to e1, e2, and in the first quadrant. As a result, it adhered to the conditions outlined in both the Lyapunov asymptotic stability theorem and the GYC partial region stability framework. The combined origin of the error dynamics (21) and parameter dynamics (25) was confirmed to exhibit asymptotic stability.
Step III. We designate e3 as the virtual control input.
To analyze the (,) system, the following was carried out:
According to , m2 is shown as follows:
Then, we can represent it as follows:
Using GYC partial region stability theory, a Lyapunov function (V3) was formulated as a positive definite function, specifically defined for the first quadrant:
The corresponding time derivative is expressed as follows:
The controller u3(t) and the parameter update law () were developed as follows:
Equation (31) can be reformulated in the following manner:
This function was confirmed to be a negative definite with respect to e1, e2, e3, and within the first quadrant. As a result, it fulfilled the conditions of both the Lyapunov asymptotic stability theorem and the GYC partial region stability framework. The shared origin of the error dynamics (29) and parameter dynamics (33) was determined to exhibit asymptotic stability.
Step IV. Finally, e4 is designated as the virtual control input.
For studying the (,) system, the following was carried out:
According to , m3 is shown as follows:
Then, we can outline it as follows:
Using the GYC partial region stability theory, a Lyapunov function (V4) was selected as a positive definite function specifically designed for the first quadrant:
The time derivative transforms into the following:
The controller u4(t) and update laws of parameters () were designed as follows:
Equation (39) can be reformulated as follows:
This function was confirmed to be a negative definite with respect to e1, e2, e3, e4, , , , and in the first quadrant. Consequently, it adhered to both the Lyapunov asymptotic stability theorem and the GYC partial region stability theorem. The shared origin of the error dynamics (37) and parameter dynamics (41) was found to be asymptotically stable.
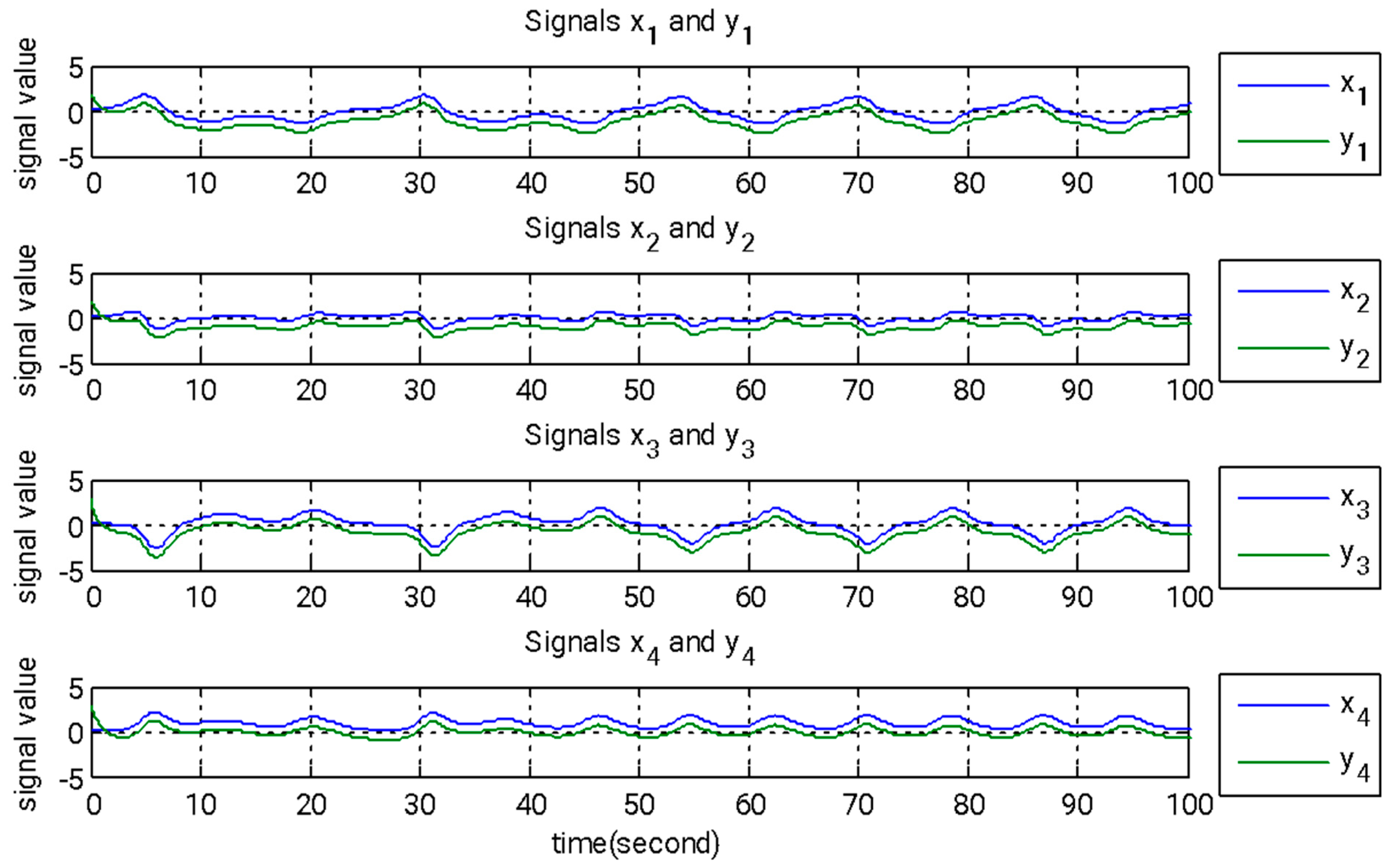
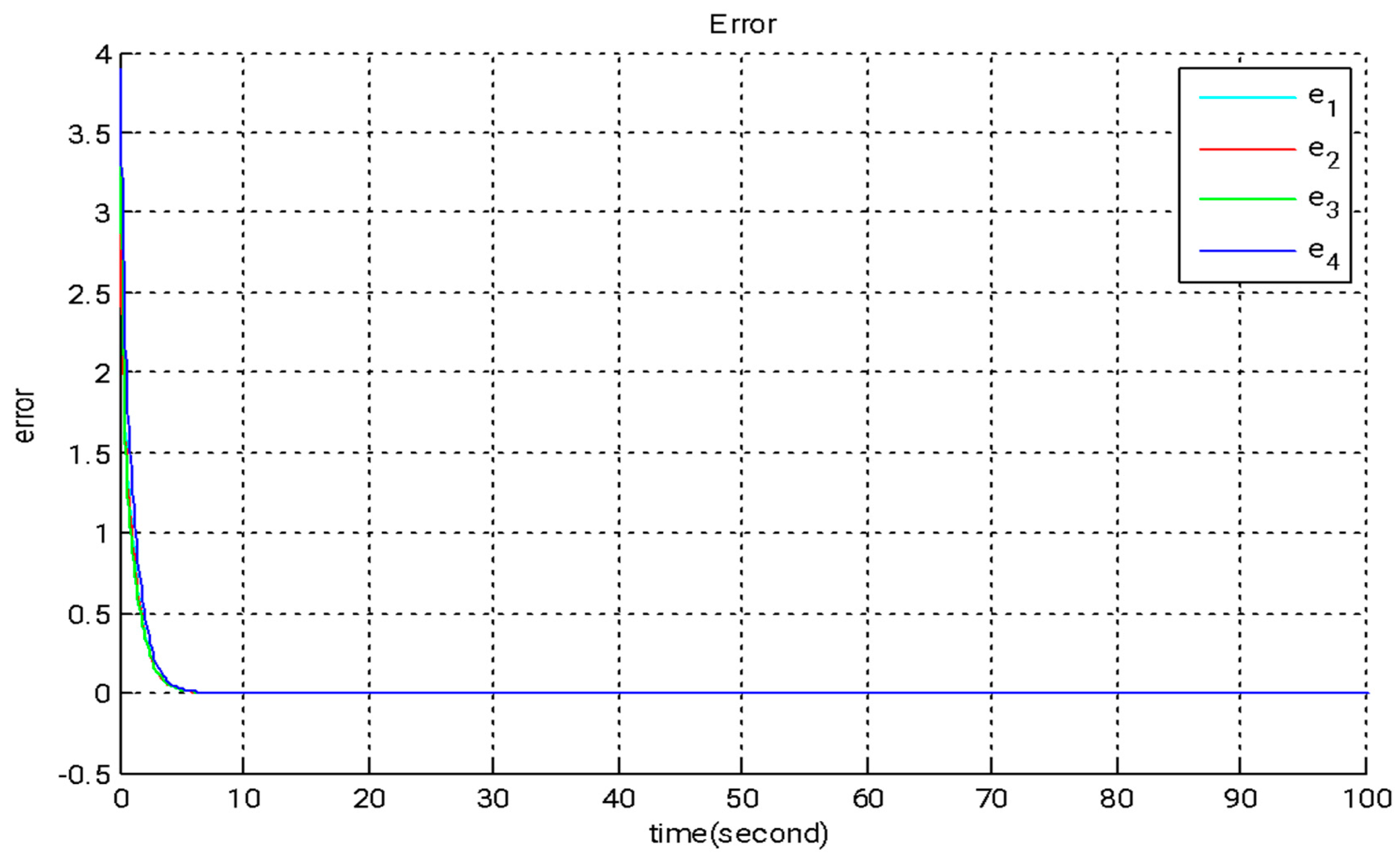
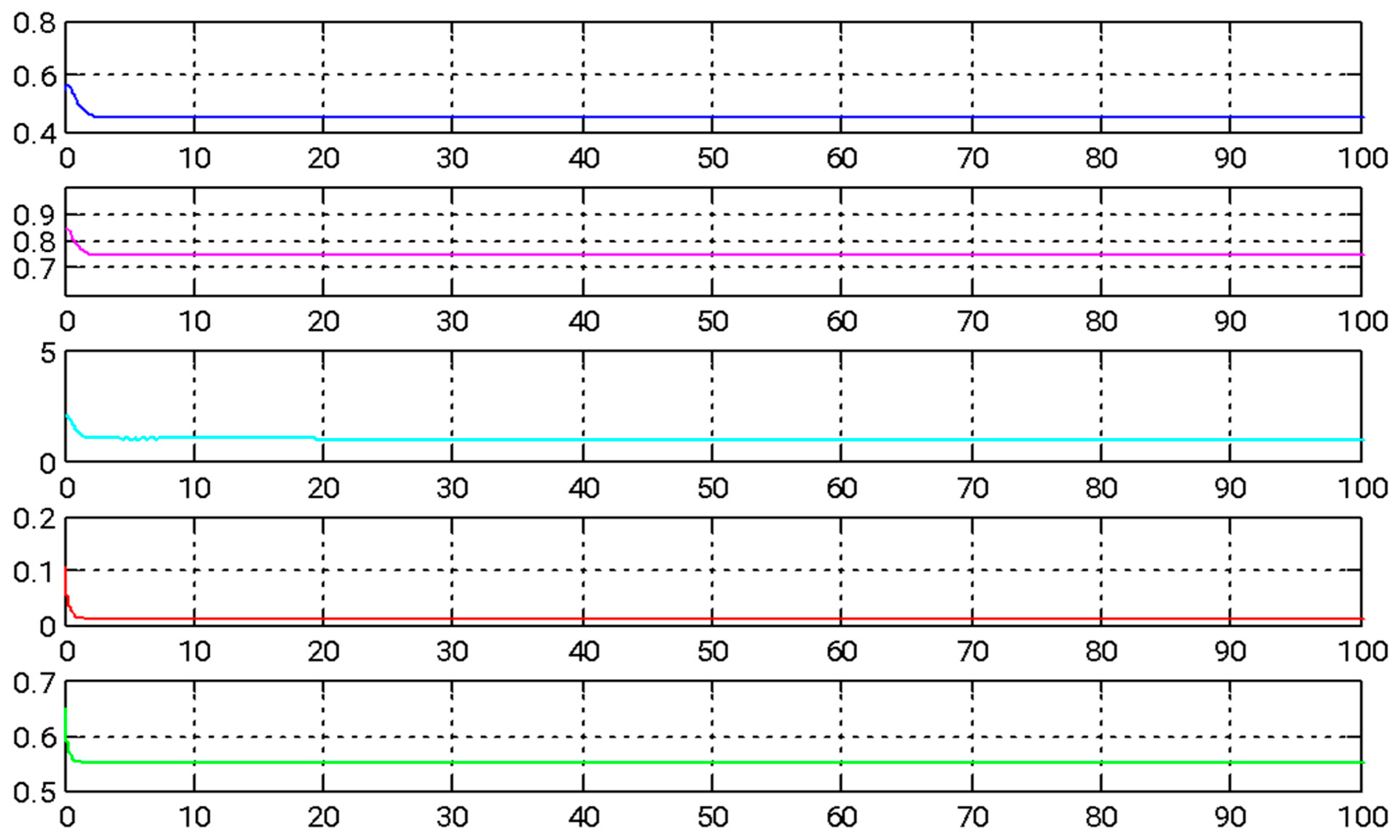
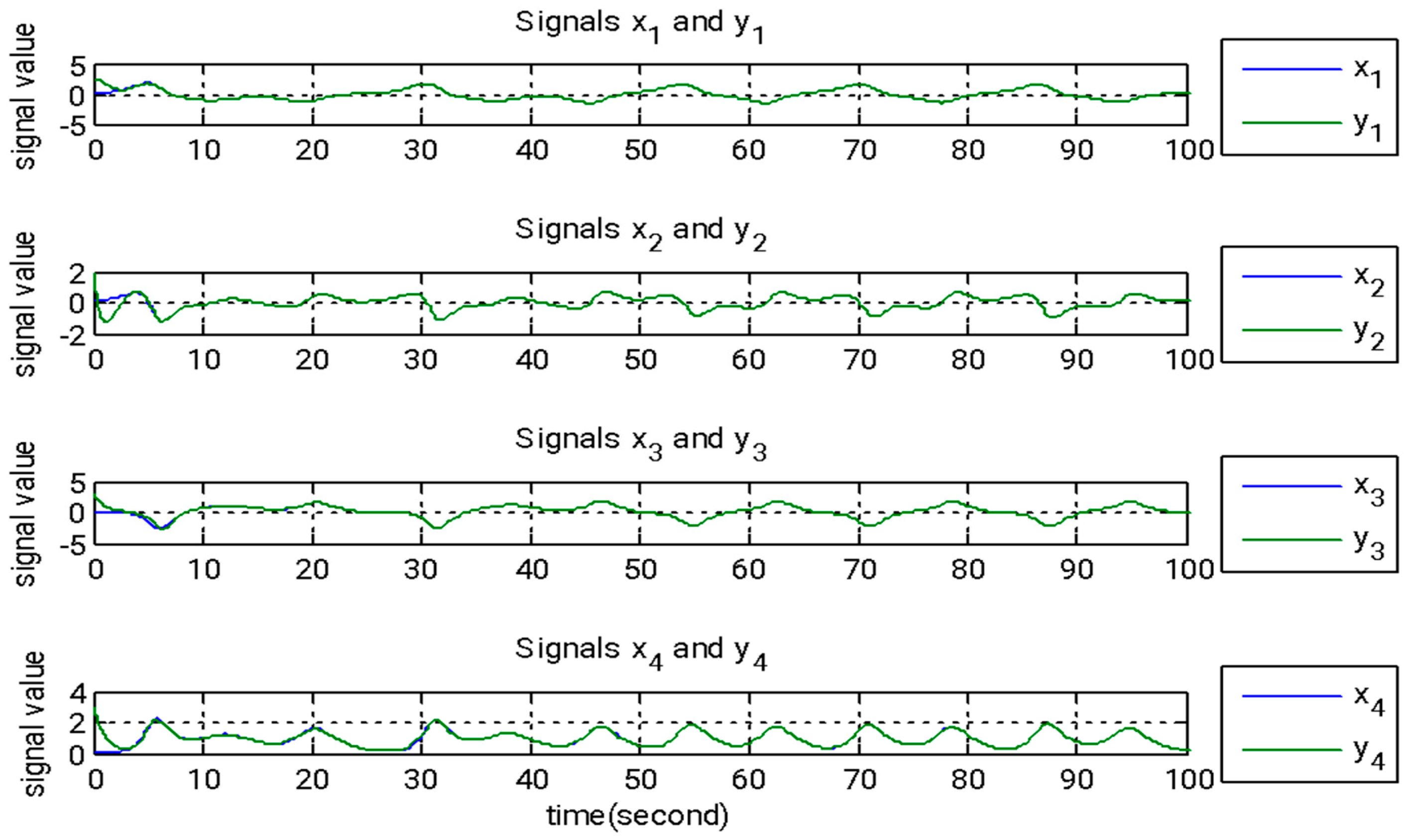
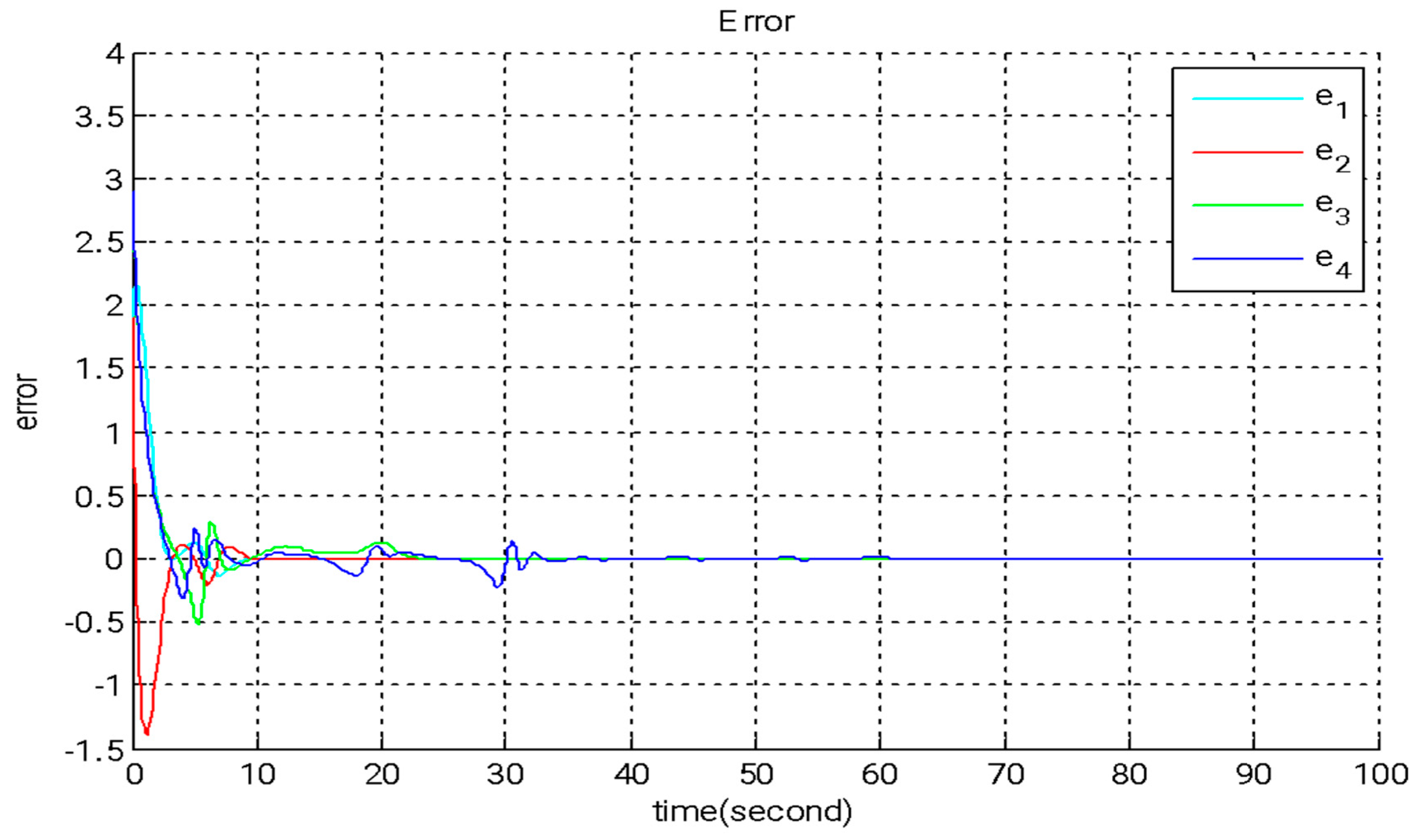
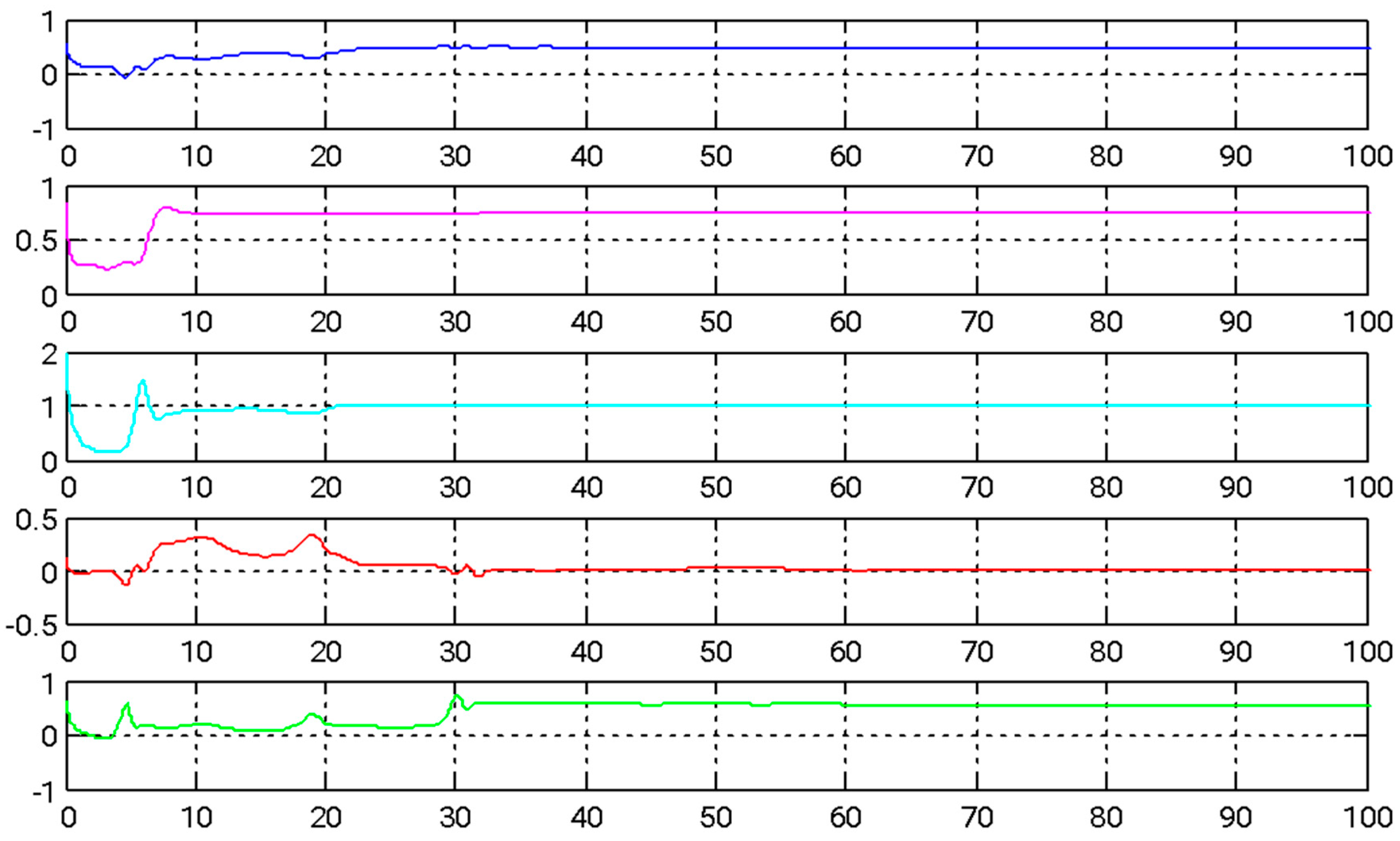
In this section, we introduce a novel method that combines adaptive backstepping control with the GYC partial region stability theory to accomplish chaos synchronization. This approach provides two major advantages: (I) the Lyapunov functions are formulated as straightforward linear homogeneous functions of system states and update rules; and (II) synchronization performance is greatly enhanced, especially in the context of parameter adaptation. Figure 2, Figure 3 and Figure 4 illustrate the simulation outcomes of the adaptive backstepping control strategy integrated with the GYC partial region stability framework. Figure 5, Figure 6 and Figure 7 display the simulation results of the traditional adaptive backstepping control method. Table 2 provides a comparison of the settling times for the steady-state error between the adaptive backstepping control with the GYC partial region stability theory and the traditional adaptive backstepping control approach.
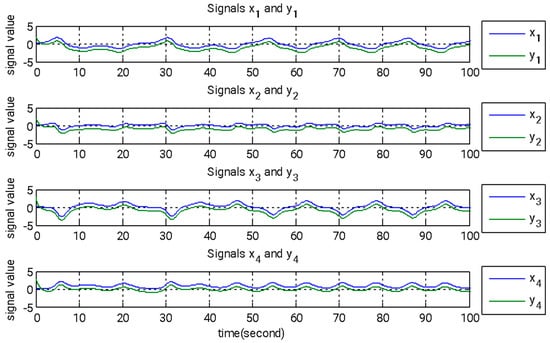
Figure 2.
State signals of the master and slave systems governed by adaptive backstepping control, incorporating the GYC partial region stability framework.
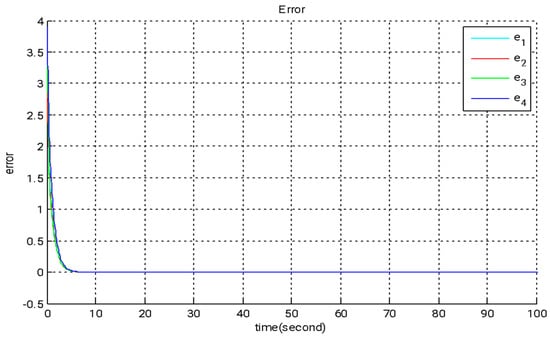
Figure 3.
The time evolution of error states under adaptive backstepping control utilizing the GYC partial region stability framework.
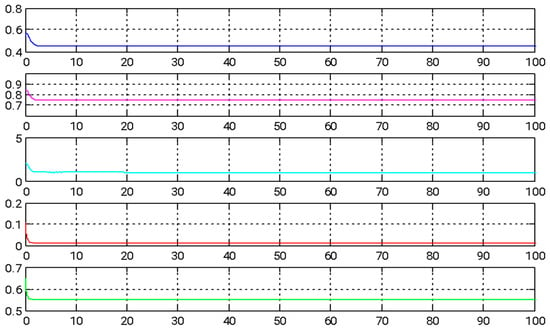
Figure 4.
The temporal evolution of estimated parameters under adaptive backstepping control employing the GYC partial region stability framework.
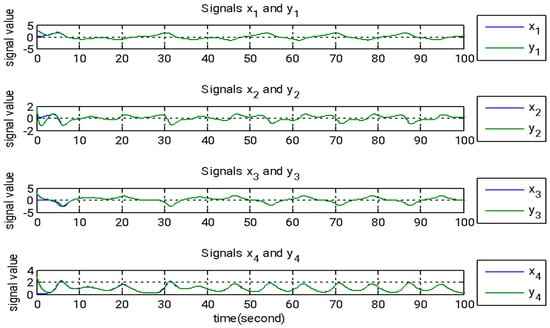
Figure 5.
The state signals of the master and slave systems under adaptive backstepping control.
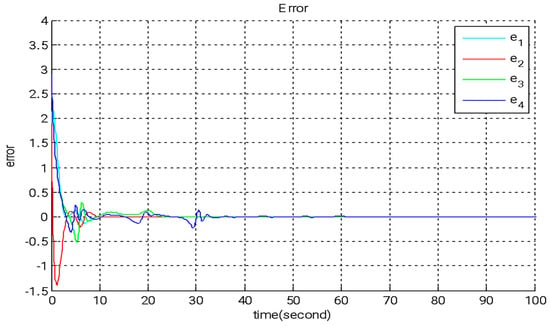
Figure 6.
The temporal progression of error states under adaptive backstepping control.
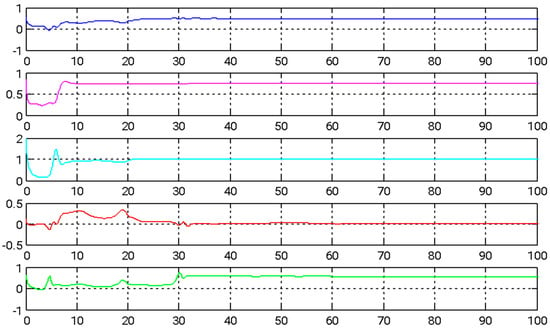
Figure 7.
The time evolution of estimated parameters during adaptive backstepping control.

Table 2.
The duration required for error states in a continuous-time system to reach stability.
4. The Process of Discretizing the Chaos Synchronization Mechanism for the Updated Shimizu–Morioka System
The master system in continuous time can be represented as follows:
The slave system in continuous time is represented as follows:
For the numerical simulation, the following parameter values are used: a = 0.45, b = 0.75, c = 1, d = 0.01, and r = 0.55. The starting conditions for both the master and slave systems are as follows: x1 = x2 = x3 = x4 = 0.1, y1 = −2, y2 = 2, y3 = 3, and y4 = −3. The initial conditions for the update rule are as follows: , and . These controllers guarantee synchronization between the two systems as time tends toward infinity, with the error function eventually converging to zero. The error function is expressed as follows:
When Gk = 1, the inclusion of this constant ensures that the error dynamics remain within the first quadrant, thus maintaining positive error states. By differentiating Equation (45), the error dynamic equations can be derived as follows:
where , , , , and . The parameter dynamics must remain positive.
Subsequently, continuous-time Equations (43) and (44) are discretized by using a small sampling interval T, transforming them into their equivalent discrete-time forms.
and
where J = kT and j = (k − 1)T, k. The kth time step is represented, with the time step measured in milliseconds. The discrete-time error function can then be expressed as follows:
where , , , , and These represent errors in the parameters, which are all positive values. u1(t), u2(t), u3(t), and u4(t) denote the adaptive backstepping controllers, which are formulated as follows:
The parameter update rule is selected as follows:
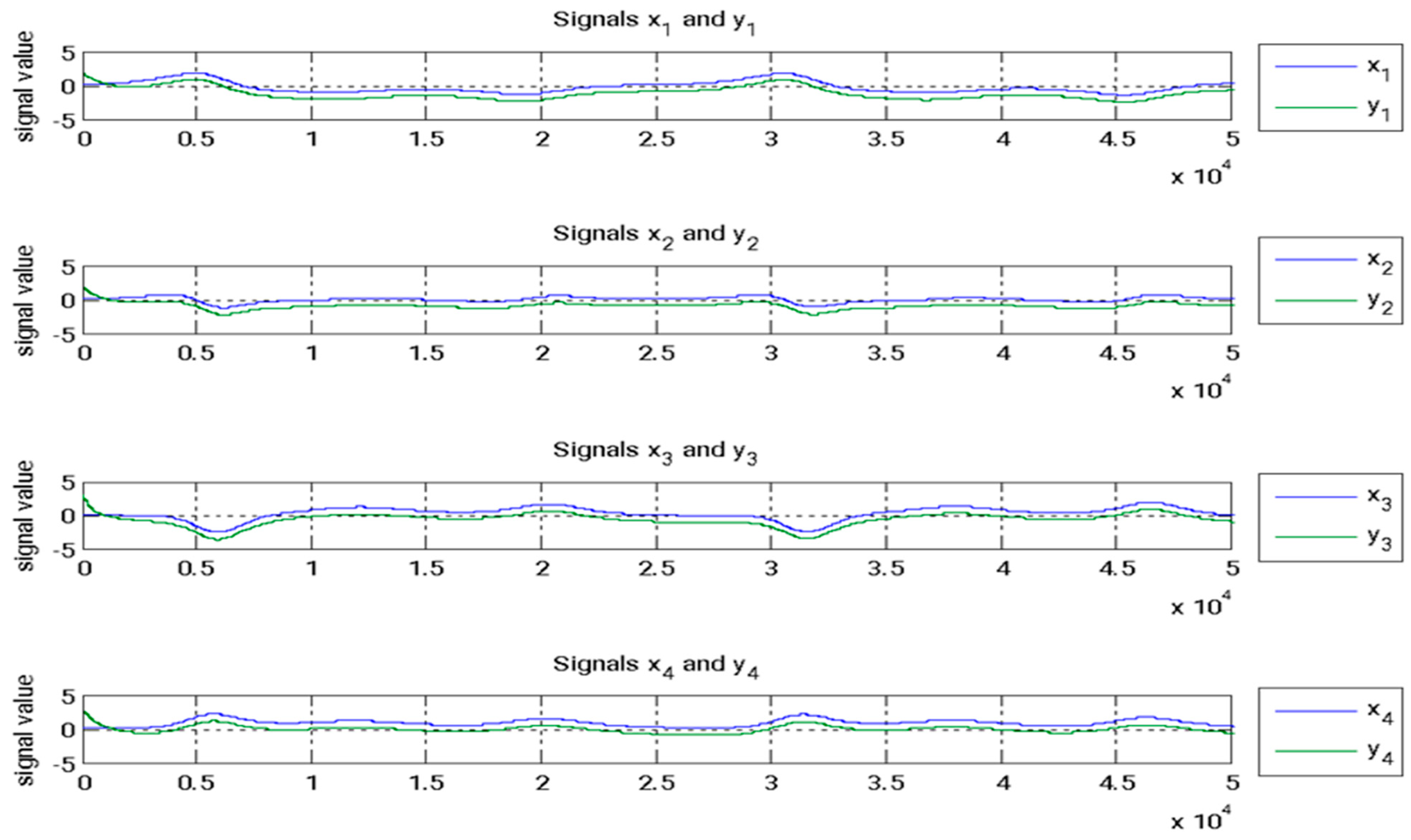
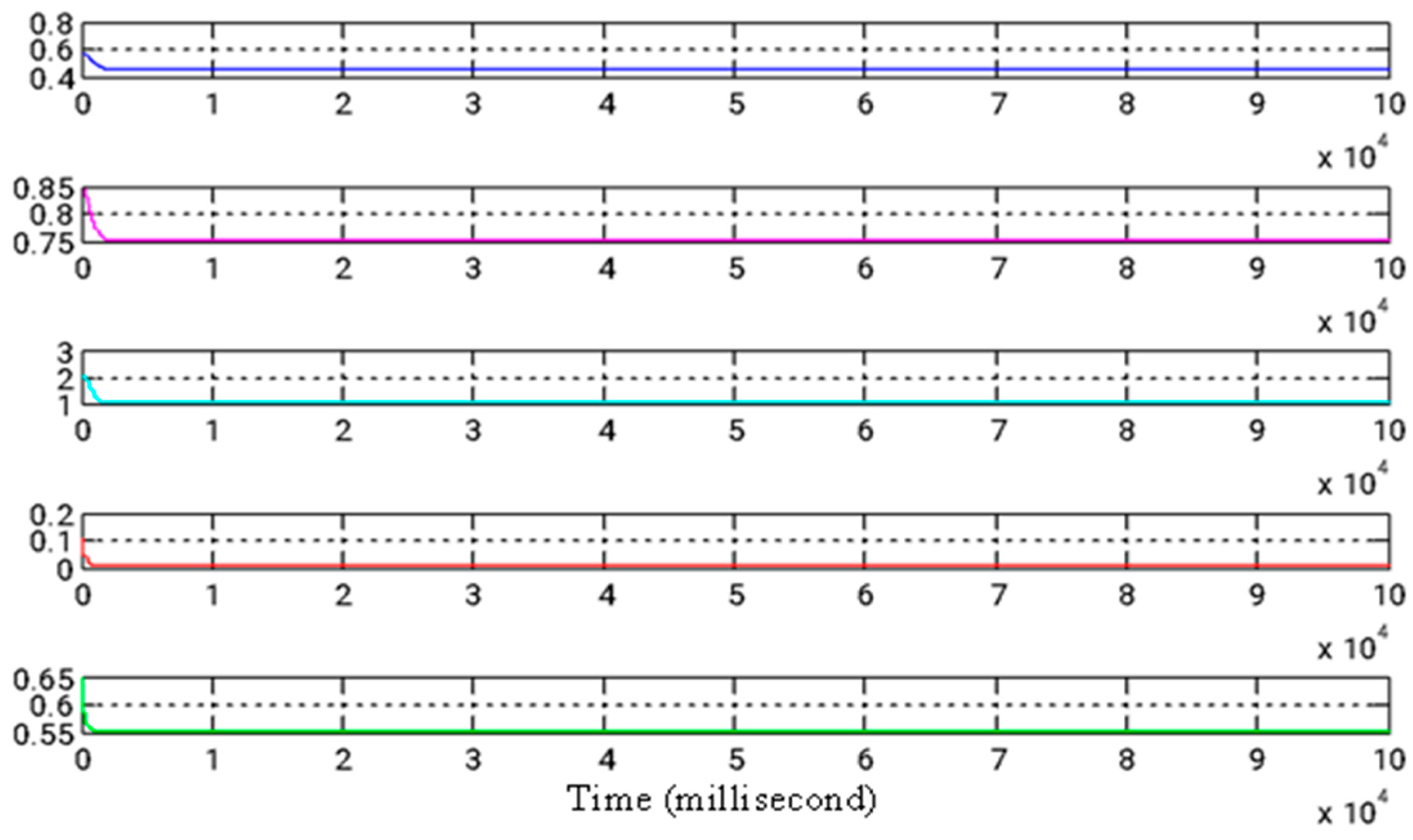
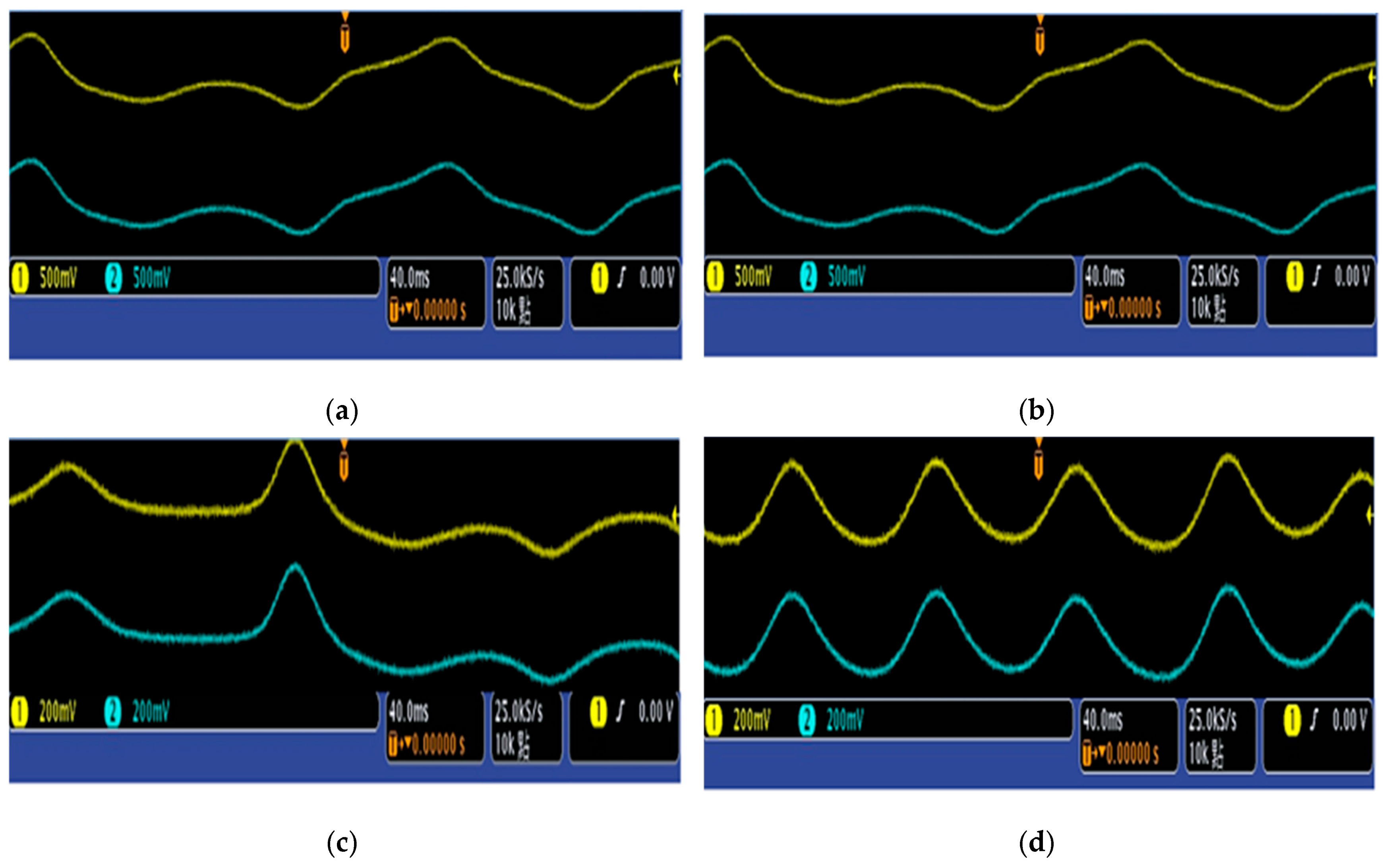
Figure 8 illustrates the state signals for both the master and slave systems. The evolution of the estimated parameters over time is shown in Figure 9. The synchronized waveforms for both systems, captured via FPGA, are presented in Figure 10. Table 3 outlines the settling times for the error states, while Table 4 provides the corresponding settling times for the FPGA system. A comparison of the results from Table 3 and Table 4 clearly demonstrates that adaptive backstepping control, enhanced by the GYC partial region stability theory, offers superior performance compared to traditional methods.
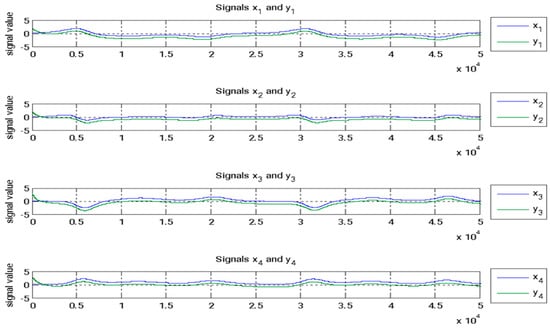
Figure 8.
State signals for both the master and slave systems.
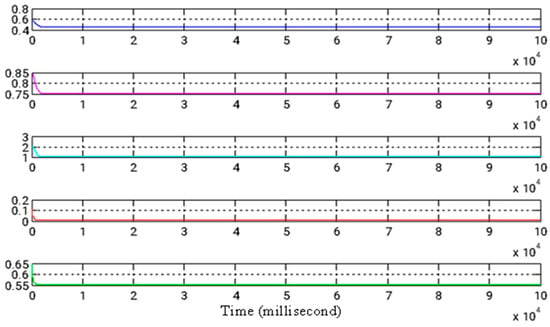
Figure 9.
The temporal progression of estimated parameters.
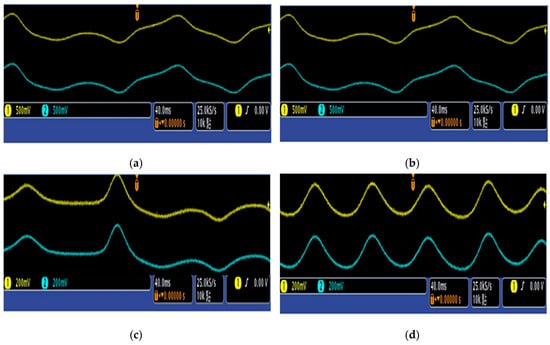
Figure 10.
Actual oscilloscope images of synchronized waveforms for both the master and slave systems, captured using FPGA: (a) (b) (c) and (d)

Table 3.
The settling time of error states of the discrete time system.

Table 4.
The settling time for the error states in the FPGA system.
5. FPGA-Based Implementation of the Updated Shimizu–Morioka System for Image Encryption
5.1. Research and Method
FPGA is capable of implementing a wide range of circuits, including control systems, chips, and digital signal processing. The circuit is described using VHDL (VHSIC Hardware Description Language) or Verilog HDL (Verilog Hardware Description Language) for simulation, synthesis, and validation. In this chapter, we utilize an Altera DE2-115 development board. The updated Shimizu–Morioka system is compiled for a DE2-115 board using an Altera Cyclone IV 4CE115 chip with VHDL code. The encrypted image is generated using Verilog code. During the practical experiment, a Terasic MTL (Multi-Touch LCD) module is connected to the DE2-115 board to display either the input (GPIO) image or the encrypted image [21,22]. The hardware implementation of the transmitter is carried out using Quartus II. With the RTL Viewer tool in Quartus II, a schematic diagram of the circuit system can be visualized.
5.2. Image Encryption
In cryptography, the XOR cipher is a basic example of an additive cipher. For example, the string can be 「11101110 00000111」. The string can be encrypted with a cyclic key 「10101111」 in the following manner in Table 5.

Table 5.
Encryption principle of XOR cipher.
The XOR operation is a key element in many advanced ciphers. However, when utilized with a simple, repeating key, a basic XOR cipher becomes highly susceptible to frequency analysis, making it easy to break. If any part of the message is recognizable or can be guessed, the key is vulnerable. Despite these flaws, the XOR cipher is popular for its ease of implementation and minimal computational demand.
Having understood the XOR encryption technique, we apply it to image encryption in this section. The image has a resolution of 800 × 480 pixels and is in BMP format. To transmit the image, three channels are used for the red (R), green (G), and blue (B) components. Therefore, each pixel consists of 8 × 3 = 24 bits. The total image size is 800 × 480 × 24 = 9,216,000 bits. We can modify each bit of the image by combining it with a chaotic digital signal to achieve encryption. The following are encryption steps:
Step 1: Designing the image output on FPGA.
Step 2: Designing the circuit for the chaotic master system.
Step 3: To integrate these signals together.
Step 4: Producing four distinct signals from the chaotic system (x1, x2, x3, and x4). Choose x1, x2, x3 to correspond to the color signal (IR, IG, IB) of the original image.
Step 5: Chaotic signal using sort function of sort shift, and converted into . Let the color gamut signal (IR, IG, IB) correspond to sequence signal (). Let them use logic operation (XOR) to obtain IMix_R, IMix_G, IMix_B.
Step 6: Finally, output IMix_R, IMix_G, IMix_B to GPIO, and display the encrypted image IMix on MTL module.
5.3. Image Decryption
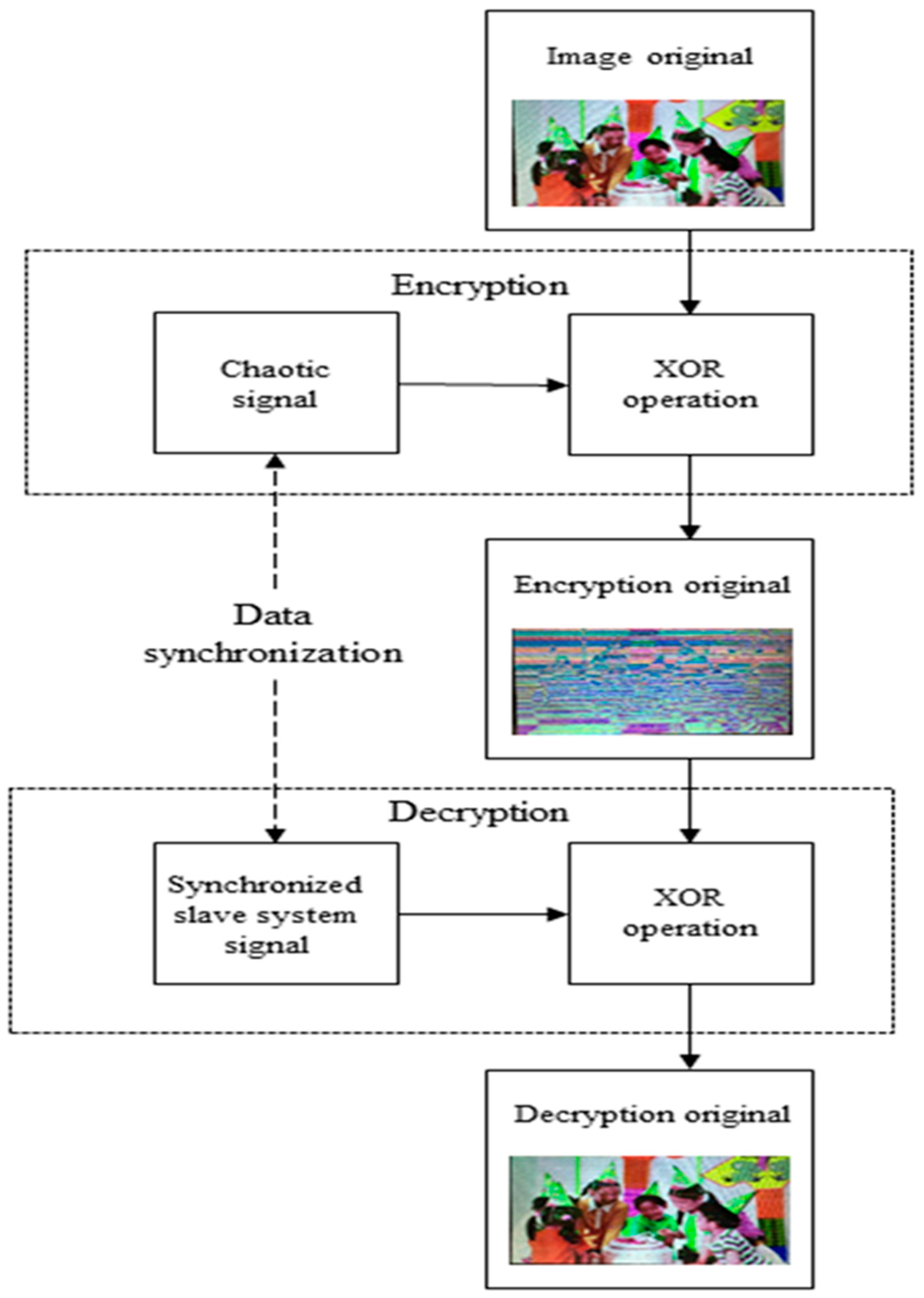
As we have established the synchronization of the new Shimizu–Morioka system in Section 4, we can now use the slave system to decrypt the image encrypted by the master system. The decryption process is illustrated in the flowchart in Figure 11.
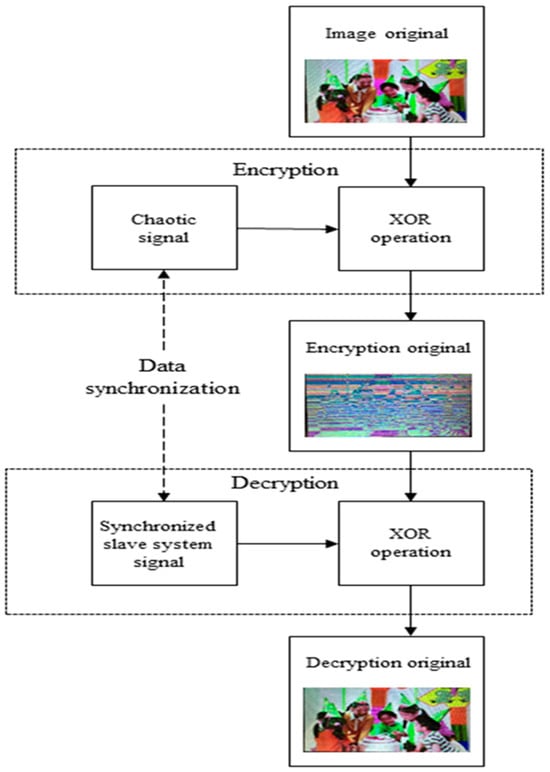
Figure 11.
A flowchart for encryption and decryption processes.
The steps for decrypting the image are as follows:
Step 1: Producing four distinct signals from the chaotic system. ( and ).
Step 2: We choose to correspond to the master chaotic signals (). Using sort function of sort shift, and converting into .
Step 3: To integrate these signal sequences.
Step 4: Let the encrypted image color gamut matrix (IMix_R, IMix_G, IMix_B) correspond to the slave system signals (). Encrypted image signals use sort function of logic operation (XOR). And we can use the XOR truth table and the slave system signals () to let every bit be original.
Step 5: Finally, encrypted image color gamut matrix (IMix_R, IMix_G, IMix_B) will be decrypted to the original image (IR, IG, IB).
5.4. Histogram Analysis
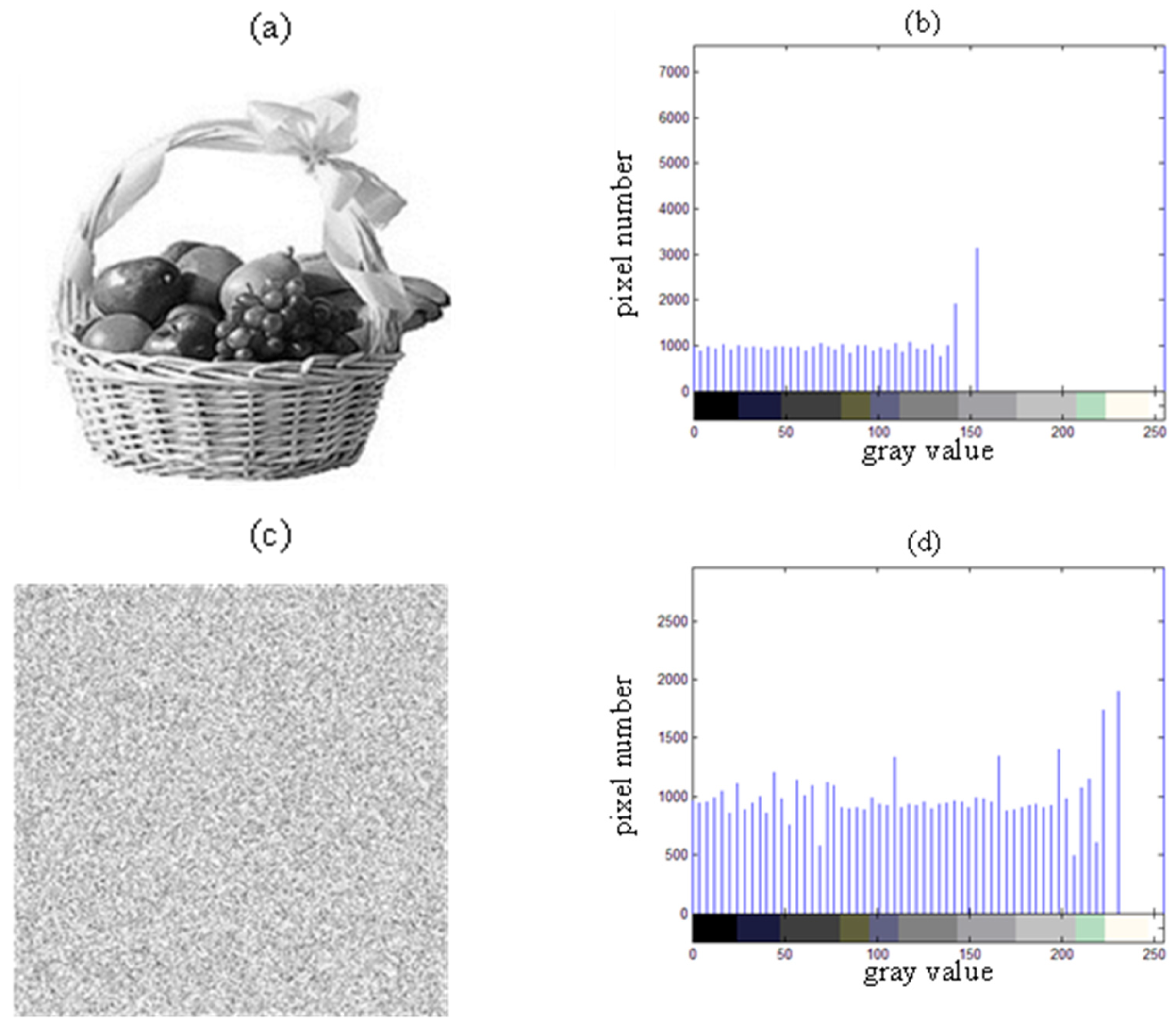
A histogram displays how pixel values are distributed across an image. In the case of an encrypted image, the ideal histogram should be uniformly distributed, significantly differing from the original image’s histogram. This ensures that attackers cannot retrieve meaningful statistical data. For our simulation, the test image used is called “Fruit”, with a resolution of 256 × 256 pixels.
Figure 12 demonstrates that the histograms of the encrypted images produced by the algorithm are evenly distributed, which is clearly different from the histogram of the original image. This shows that the encryption effectively masks any relevant information, preventing attackers from utilizing statistical methods to break the cryptosystem.
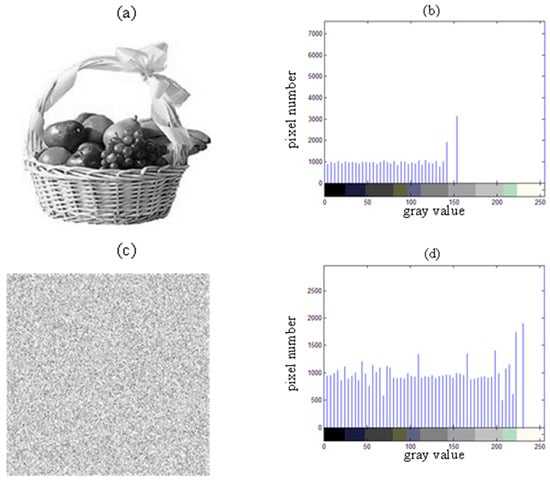
Figure 12.
(a) The original gray image of Fruit; (b) the histogram of the original grayscale image of Fruit; (c) the grayscale image of Fruit after encryption; and (d) the histogram of the encrypted grayscale image of Fruit.
6. Conclusions
In this study, a novel chaotic system is introduced, extending the Shimizu-Morioka system by incorporating additional parameters and a nonlinear component. By combining GYC partial region stability theory with adaptive backstepping synchronization, we significantly reduce the convergence time of the new chaotic system. The synchronization speeds for e1, e2, e3, and e4 are found to be approximately 3.42, 3.55, 5.89, and 9.23 times faster, respectively. The synchronization of this complex system is also successfully achieved. Furthermore, the FPGA-based synchronization of the new Shimizu–Morioka system is implemented, with identical results observed across the continuous-time, discrete-time, and FPGA systems. When compared with traditional adaptive backstepping control, the proposed method, using GYC partial region stability theory, outperforms it in performance as presented in Table 2, Table 3 and Table 4. Finally, an image encryption algorithm is developed using FPGA and digital signal processing. Experimental results indicate that the encryption’s key space is sufficiently large to withstand exhaustive key differential attack analysis. The proposed method has been shown to offer robust security, and its processing speed is highly suitable for image encryption tasks. Encryption through logic operations has been completed, and decryption using the slave system has also been successfully achieved, following the implementation of synchronization.
Author Contributions
Conceptualization, C.-H.Y., S.-Y.L., L.-M.T. and S.-C.C.; formal analysis, C.-H.Y., S.-Y.L. and J.-D.L.; funding acquisition, S.-Y.L. and S.-C.C.; investigation, C.-H.Y., S.-Y.L., L.-M.T. and S.-C.C.; methodology, C.-H.Y., S.-Y.L., L.-M.T., S.-C.C. and J.-D.L.; project administration, C.-H.Y., S.-Y.L., L.-M.T. and S.-C.C.; resources, C.-H.Y.; software, J.-D.L.; supervision, C.-H.Y., S.-Y.L., L.-M.T. and S.-C.C.; validation, C.-H.Y., J.-D.L., S.-Y.L., L.-M.T. and S.-C.C.; visualization, C.-H.Y., S.-Y.L., L.-M.T. and S.-C.C.; writing—original draft, J.-D.L.; writing—review and editing, J.-D.L., C.-H.Y. and S.-Y.L. All authors have read and agreed to the published version of the manuscript.
Funding
This paper was supported in part by National Science and Technology Council with grant no. NSTC 113-2221-E-027-055, NSTC 111-2221-E-019-068-MY3, the University System of Taipei Joint Research Program with grant no. USTP-NTUT-NTOU-113-03, and the Institute for the Development and Quality, Macau, Macao.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created in this paper. Data are contained within the article to this article as no datasets were generated or analyzed during the current study.
Acknowledgments
We also deeply appreciate significant support from the National Taipei University of Technology, Taiwan, National Taiwan Ocean University, Taiwan, and the Institute for Development and Quality, Macau, Macao.
Conflicts of Interest
The authors declare no conflicts of interest. Also, the funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
References
- CISCO. Available online: https://www.cisco.com/#tabs-35d568e0ff-item-194f491212-tab (accessed on 29 January 2025).
- Brown, R.; Chua, L.O. Clarifying chaos: Examples and counterexamples. Int. J. Bifurc. Chaos 1996, 6, 219–249. [Google Scholar] [CrossRef]
- Dachselt, F.; Schwarz, W. Chaos and cryptography. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 1498–1509. [Google Scholar] [CrossRef]
- Jakimoski, G.; Kocarev, L. Chaos and cryptography: Block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 2001, 48, 163–169. [Google Scholar] [CrossRef]
- Schmitz, R. Use of chaotic dynamical systems in cryptography. J. Frankl. Inst. 2001, 338, 429–441. [Google Scholar] [CrossRef]
- Kocarev, L.; Jakimoski, G.; Stojanovski, T.; Parlitz, U. From chaotic maps to encryption schemes. In Proceedings of the 1998 IEEE International Symposium on Circuits and Systems (ISCAS), Monterey, CA, USA, 31 May–3 June 1998; pp. 514–517. [Google Scholar]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Sankpal, P.R.; Vijaya, P. Image encryption using chaotic maps: A survey. In Proceedings of the 2014 Fifth International Conference on Signal and Image Processing, Bangalore, India, 8–10 January 2014; pp. 102–107. [Google Scholar]
- Ephin, M.; Joy, J.A.; Vasanthi, N. Survey of Chaos based Image encryption and decryption techniques. In Proceedings of the Amrita International Conference of Women in Computing (AICWIC’13), Coimbatore, India, 9–11 January 2013; International Journal of Computer Applications (IJCA): Wilmington, NC, USA, 2013. [Google Scholar]
- Lorenz, E.N. Deterministic nonperiodic flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef]
- Hsu, W.-T.; Tsai, J.S.-H.; Guo, F.-C.; Guo, S.-M.; Shieh, L.-S. From fault-diagnosis and performance recovery of a controlled system to chaotic secure communication. Int. J. Bifurc. Chaos 2014, 24, 1450151. [Google Scholar] [CrossRef]
- Mittal, A.; Dwivedi, A.; Dwivedi, S. Parameter adaptation technique for rapid synchronization and secure communication. Eur. Phys. J. Spec. Top. 2014, 223, 1549–1560. [Google Scholar] [CrossRef]
- Hu, H.; Deng, Y.; Liu, L. Counteracting the dynamical degradation of digital chaos via hybrid control. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 1970–1984. [Google Scholar] [CrossRef]
- Liu, S.; Zhang, F. Complex function projective synchronization of complex chaotic system and its applications in secure communication. Nonlinear Dyn. 2014, 76, 1087–1097. [Google Scholar] [CrossRef]
- Padmanaban, E.; Boccaletti, S.; Dana, S. Emergent hybrid synchronization in coupled chaotic systems. Phys. Rev. E 2015, 91, 022920. [Google Scholar] [CrossRef]
- Mahmoud, G.M.; Mahmoud, E.E.; Arafa, A.A. Passive control of n-dimensional chaotic complex nonlinear systems. J. Vib. Control 2013, 19, 1061–1071. [Google Scholar] [CrossRef]
- Hung, M.-L.; Yau, H.-T. Circuit implementation and synchronization control of chaotic horizontal platform systems by wireless sensors. Math. Probl. Eng. 2013, 2013, 903584. [Google Scholar] [CrossRef]
- Eskov, V.; Gavrilenko, T.; Vokhmina, Y.V.; Zimin, M.; Filatov, M. Measurement of chaotic dynamics for two types of tapping as voluntary movements. Meas. Tech. 2014, 57, 720–724. [Google Scholar] [CrossRef]
- Ge, Z.-M.; Yu, J.-K.; Chen, H.-K. Three asymptotical stability theorems on partial region with applications. Jpn. J. Appl. Phys. 1998, 37, 2762. [Google Scholar] [CrossRef]
- El-Dessoky, M.; Yassen, M.; Aly, E. Bifurcation analysis and chaos control in Shimizu–Morioka chaotic system with delayed feedback. Appl. Math. Comput. 2014, 243, 283–297. [Google Scholar] [CrossRef]
- Tlelo-Cuautle, E.; Carbajal-Gomez, V.; Obeso-Rodelo, P.; Rangel-Magdaleno, J.; Nunez-Perez, J.C. FPGA realization of a chaotic communication system applied to image processing. Nonlinear Dyn. 2015, 82, 1879–1892. [Google Scholar] [CrossRef]
- Masmoudi, A.; Puech, W. Lossless chaos-based crypto-compression scheme for image protection. IET Image Process. 2014, 8, 671–686. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).