1. Introduction
Along with the widespread adoption of the Internet of Things (IoT), the application of IoT has been extended to infrastructure-lacking environments without continuous end-to-end connectivity, such as rural and post-disastrous areas. Disruption Tolerant Networking (DTN) bridges the gap between intermittently connected environments and helps the expansion of the IoT applications in these stressed and unstable environments. Mobile Social Network (MSN) is a special type of DTN that has become increasingly important due to the proliferation of portable devices with higher computing power at a lower cost. The social behaviors of humans have a significant impact on the overall network performance, especially in networks with disruptions and long delays. Furthermore, IoT applications require efficient and reliable multicast services to facilitate data dissemination to the group of participating nodes. The following subsections briefly describe the concept, background, and interrelation of IoT, DTN, MSN, and multicasting in DTN.
1.1. The Internet of Things
The Internet of Things is an emerging paradigm in communication networks, commonly known as the Third Wave. The IoT is the interconnection of uniquely identifiable physical things with embedded systems connected to the Internet [
1] that ideally interact with one another without any human intervention. The “things” in IoT refers to a wide variety of devices, such as smartphones, sensors, measurement devices, and laptops. As the concept of IoT slowly assimilates into our daily life, its application is similarly extended to remote environmental monitoring systems, such as agricultural sensing and Supervisory Control and Data Acquisition (SCADA) [
2,
3] data logging. IoT sensors, devices, and controllers are being deployed over large geographical areas that require continuous connection to the network to gather environmental sensing data. However, network connectivity may not always exist due to the lack of network infrastructure in remote regions. The end-to-end network link between data sources and destinations is not available or is available only periodically. Furthermore, IoT devices usually have limited storage and battery life, and they operate using low-power short-range wireless technologies. They are periodically scheduled to sleep until a network link is available to conserve energy, and buffer management can reduce storage consumption in IoT application deployment. A wide distribution of nodes with limited wireless radio range, storage resources, and battery life leads to a greater chance of limited network connectivity.
1.2. Disruption Tolerant Networking
Disruption Tolerant Networking (DTN) [
4] addresses the intermittent network issues in unstable and stressed scenarios and exchanges data opportunistically over an infrastructure-less network. DTN thus allows IoT devices to communicate in the presence of connectivity disruption. It employs a store-carry-forward message switching paradigm, as shown in
Figure 1, by introducing a new Bundle Protocol (BP) above the transport layer [
5]. The source node generates a message bundle and relays the bundle to nearby nodes within transmission range. The relay node stores the bundle and carries it while moving until it meets the destination node or another potential relay node. Finally, the relay node forwards the bundle to the destination node. DTN tackles the issues of intermittent connectivity, high delivery latency, asymmetric data rates, and high error rates in such partitioned networks. DTN can be considered as a Mobile Ad hoc Network (MANET) with intermittent connectivity or a sparse MANET. DTN and MANET are similar in node mobility. Both are infrastructure-less and resource-constrained, and both may frequently experience network partitions. Nevertheless, they are different in terms of communication protocols. MANET uses TCP/IP that requires an end-to-end path for best-effort delivery, whereas DTN uses the bundle layer protocol as mentioned above. Furthermore, while network partitions cause packet losses in MANET, they increase network coverage in DTN with trade-offs in higher delivery delay [
6].
1.3. Mobile Social Network
The Mobile Social Network (MSN), previously known as Pocket Switched Networks [
7,
8], is a special type of DTN and can be viewed as one type of socially aware DTN. MSN is of growing significance as mobile devices (e.g., smartphones, wearable devices, etc.) proliferate. MSN enables users to share and exchange data between themselves in an established network without the presence of network infrastructure. Data transfer occurs upon opportunistic contacts between mobile devices. The data contents are shared without the need to download the content through the infrastructure. Mobile devices in MSN are largely influenced by user decisions and social behavior. A detailed state-of-the-art MSN is presented in Reference [
9], along with the MSN design requirements and future developments. MSN has received increased attention in recent years due to the rapid growth in the use of handheld devices and growing interest in social-based routing strategies. Some recent solutions [
10,
11,
12] are proposed for MSN, but they are not multicast-oriented. Since MSN is human-centric and based on the interaction patterns of people and their social interests, it is one of the precursors in realizing the newly emerging Internet of People (IoP) paradigm. The IoP is a human and device-centric paradigm that views human and user devices as the key elements in the network. Conti et al. [
13] presented a comprehensive overview of IoP and outlined the open challenges in IoP realization.
1.4. Multicasting in DTN
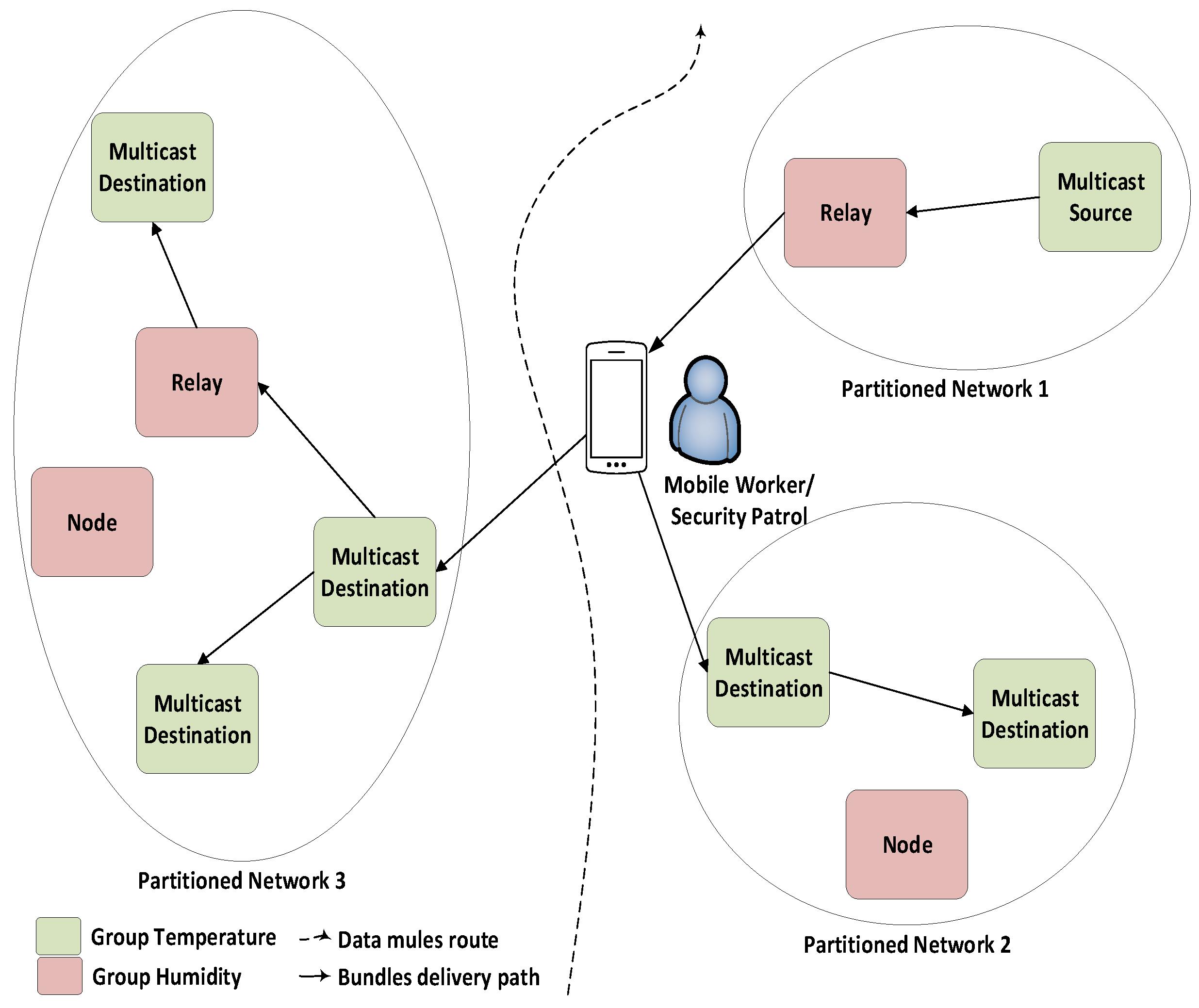
IoT devices can generate or collect data as usual and transmit them through DTN. The nodes store the message bundles in their buffer and carry bundles until a communication link is available. In the case of environmental sensing, end-to-end communication paths between nodes do not exist due to node sparsity in the networks. To overcome this shortcoming, data mules are used to bridge the gaps between partitioned networks. For example,
Figure 2 shows a scenario where workers with smartphones, known as data mules, traverse the monitored area according to schedule. The IoT devices establish a connection with the smartphone and forward the collected data. The smartphone distributes the data to neighboring devices if it is intended for multiple recipients. The smartphone can deliver configuration updates from the control center to different groups of participating devices using multicasting services in DTN.
Multicast is an efficient mechanism for data dissemination in IoT applications. It is required because it can save bandwidth, increase resource utilization, and reduce transmission costs compared to unicast routing. However, since multicast approaches are proposed for the Internet or a well-connected MANET and they always assume available end-to-end paths between data sources and destinations, they are not suitable for DTN environments that have sparse connectivity. For example, the Reliable Multicast Transport Protocol (RMTP) [
14] requires continuous network connectivity, and EraMobile [
15] works only in MANETs that require temporary network topology establishment. However, data collection in remote areas with limited coverage is error-prone, and node update verification is a tedious task. Reliable multicast capability in DTN would overcome these limitations and enable the support of data dissemination among a group of participating nodes in a DTN-based IoT network.
In this paper, we survey recent multicast approaches according to the design intention of their proposed algorithm and provide an overview of multicasting services and open issues in DTN for future research into the Reliable Multicast Disruption Tolerant Networking (RMDTN) protocol. A more up-to-date state-of-the-art study of DTN multicast protocols is presented and compared to the existing surveys. Key solutions and performance evaluation of each of the protocols are summarized. Furthermore, new insights and discussions are provided on the enabling of DTN multicasting in IoT applications, which is one of the key research trends in this field.
Nevertheless, unicast routing strategies in DTN are not covered in this paper, since they have been studied extensively and several related surveys have been published. For example, Zhang [
16] categorized unicast routing approaches based on the predictability of the mobility model into deterministic and stochastic schemes. Cao and Sun [
17] combined the works from References [
16,
18] with improvement by classifying the unicast approaches according to the availability of infrastructure assistance. They introduced a hybrid category combining naïve-replication and utility-forwarding-based routing with infrastructure assistance. Sobin et al. [
6] reviewed a large number of unicast approaches along with multicast and anycast routing according to how protocols make forwarding decisions to relay nodes. A reference architecture for DTN routing protocols is proposed in Reference [
19] with three basic components: Queue management, forwarding policies, and message replication. The authors classify relevant DTN unicast routing protocols in the literature into a single technique or combination of techniques, according to the components used.
The remainder of this paper is structured as follows.
Section 2 lists some of the related survey studies in DTN multicast routing approaches.
Section 3 describes the motivation of this survey and some applications of multicast routing in the IoT context.
Section 4 discusses existing work on DTN multicast routing protocols based on their routing characteristics, while
Section 5 summarizes some open issues in DTN and discusses them in terms of multicast.
Section 6 concludes the paper.
2. Related Work
Sobin et al. [
6] classified existing DTN routing protocols according to relay selection strategies in forwarding messages to the destinations. The protocols are grouped into social-based routing and pure opportunistic routing categories and are discussed in terms of source injection (i.e., single-copy or multi-copies schemes) and communication strategies based on the number of receivers (e.g., unicast, multicast, or anycast). Only a few multicast routing protocols, up until 2014, are listed in their paper.
Patra et al. [
20], however, presented a more comprehensive survey on multicast routing for DTN. The following four categories of multicast routing protocols are discussed: Flooding, tree-based, probabilistic, and intelligent protocols. Multicast messages can be flooded in the network or forwarded along a multicast tree to reach the destinations. Probabilistic approaches select the best relays based on the encounter history. Intelligent approaches combine flooding and forwarding techniques for better use of the available resources. A brief performance comparison between different multicast routing approaches is also provided in the survey.
Wang and Wu [
21] discussed the following three models related to multicast DTNs: The single-node model, the multiple-copies model, and the single-copy model. In the first, a ferry node that moves around holds message bundles intended for all destinations and delivers them to the destinations upon contact. The multiple copies model replicates the destination set when it encounters a node that satisfies certain conditions. In the single-copy model, a single copy of each destination is maintained, in which destinations can be scattered at different nodes. Here, the copy is forwarded to the encountered nodes whenever there is a higher delivery probability.
Zhao et al. [
22] provided an overview of multicast models for DTNs. They divided multicast in DTNs into the following four categories: Unicast-based, broadcast-based, tree-based, and group-based multicast. Juyal et al. [
23] presented a general overview of multicast routing schemes in DTN, but the performance evaluation is done using an old algorithm. Lastly, in our previous work [
24], a taxonomy of DTN multicast routing strategies is introduced, and we discussed some of the common protocols briefly.
3. Motivation and IoT Applications
The emerging IoT paradigm tries to connect almost every device to the Internet. However, this is not always possible when the challenging environment results in connectivity disruption, especially in remote areas with limited network connectivity. Although wireless sensor networks (WSN) are one of the key enablers in IoT applications, the lack of continuous electrical supply and imperfect telecommunication infrastructures hamper information exchange. For example, battery-operated sensors are often deployed in outskirt areas to collect environmental data, but the collected data are unable to reach the sink without proper communication. Therefore, DTN is designed to help bridge the gap between intermittently connected WSNs and extend wireless connectivity over opportunistic environments. For example, drones can be deployed in plantations to collect and store temperature and soil humidity data, as shown in
Figure 3, and can forward the data to the control center. DTN-enabled IoT devices enable better communications among devices despite connectivity disruptions. The following section discusses some DTN-enabled IoT applications.
The Internet of Bikes-DTN (IoB-DTN) [
25] protocol exploits a bike sharing system to collect urban data with data aggregation mechanisms by combining multiple data from the same source or different sources into a single DTN bundle. Low cost and low power operated IoT devices (i.e., integrated sensors and communication devices) are installed on the bike to generate data and store the data as a bundle. The bundle is either relayed to encountered bikes or forwarded to the sinks. Auzias et al. [
26] proposed BoAP, an implementation of the Constrained Application Protocol (CoAP) [
27] over BP that replaces UDP with BP in the transport layer to allow CoAP communication in DTN, hence enabling a delay tolerant IoT. With this IoT-over-DTN architecture, the IoT application encapsulates the BoAP message into a BP bundle and the IBR-DTN [
28] BP daemon stores the bundle and forwards it to other BP daemons in the DTN. The authors listed multicast as one of the possible optimizations to realize a more efficient BoAP implementation. They suggested that the non-singleton Endpoint Identifier (EID) properties of the BP can replace the IP multicast group address in CoAP and proposed combining multiple payloads addressed to the same destination (i.e., group EID) into a single BP bundle.
NanoDTN [
29] is a super-lightweight BP implementation for resource-constrained IoT devices, such as sensors. It only retains a few basic functionalities and interoperability with µDTN [
30] due to the memory constraint of a sensor. However, nanoDTN does not fit into the scenario or application with the reliability requirement since the authors only use one MAC layer without carrier sensing, which does not ensure reliable delivery. IoT-cum-DTN [
31] is an Internet of Hybrid Opportunistic Things architecture framework to interoperate existing DTN and IoT standards with an MQTT Convergence Layer Adapter (CLA). IoT-cum-DTN outperformed References [
26,
29] in IoT publish/subscribe semantics using MQTT-SN and IBR-DTN. The IoT-cum-DTN node communicates with normal DTN nodes and IoT publisher/subscriber nodes as peers by encapsulating IoT messages as DTN bundles. A comprehensive survey on using DTN solutions in IoT applications has been presented in Reference [
32], and the authors discussed the adoption of DTN approaches in the IoT context.
IoT applications require multicasting support for efficient routing and better resource utilization. Although there are some prominent works in the literature addressing multicasting support in DTN, such as Reference [
22,
33], and others to be discussed in the following section, none of them discusses DTN multicast routing in the IoT context. Multicast routing in delay tolerant IoT application imposes more stringent requirements due to the resource-constrained nature of IoT devices. In this survey, we study the current state of multicast routing protocols proposed for DTN and the future endeavor of RMDTN.
4. Multicast Routing Approaches in DTN
In this paper, we classify some of the recently proposed DTN multicast routing protocols based on the purpose of the routing algorithm suggested in the present study. The implementation of multicast routing protocols in DTN is challenging due to the intermittent nature of DTN as well as the limitations of IoT devices. Multicast in DTN requires efficient data transmission to a group of intended receivers without neglecting the overall performance of the networks. Given the wide variety of DTN applications in different fields, there is no single DTN multicast solution capable of addressing all the multi-faceted limitations of DTN in different situations. Each proposed solution is focused on addressing particular aspects of a given scenario or addresses specific issues in an application. Different multicast routing approaches are studied to understand the design aspect of multicast algorithms. We discuss some of the significant multicast approaches in DTN that have been proposed recently in this section.
Figure 4 shows the classification of DTN routing approaches. In this taxonomy, the surveyed multicast DTN routing approaches are grouped into four main concepts: Social-aware, buffer-efficient, energy-aware, and geographical routing strategies under multicast DTN routing approaches. The Unicast DTN routing approaches are outside the scope of this paper but are significant within the comprehensive literature under the DTN umbrella.
4.1. Social-Aware Multicast Routing in DTN
Social-based multicast routing approaches exploit social behaviors of DTN nodes to select relays for forwarding messages. Social characteristics between mobile users in the DTN are stable due to their long-term social relationships and behaviors. Whereas positive social characteristics (e.g., centrality and community) facilitate the routing process, negative characteristics (e.g., selfishness) usually degrades routing performance. We further classify the surveyed social-aware multicast routing protocols regarding contact probability (based on encounter history) and profile-based interests.
4.1.1. Contact Probability
Single-Data Multicast: Gao et al. [
34] presented an analytical model to select forwarding nodes with single-data and multiple-data items based on the social network concept, namely node centrality and social community. Forwarding nodes are chosen based on their capabilities, measured by social-based metrics, to forward message bundles to destinations. In Single-Data Multicast (SDM), a minimum number of relays is selected based on Cumulative Contact Probability (CCP), the average probability that a node encounters a random node within a time constraint.
Figure 5 shows the SDM data forwarding process. The multicast source S selects K forwarding nodes (i.e., the minimum number of forwarding nodes to guarantee the required delivery ratio within the specified time constraint). Each forwarding node (Rj, i) forwards the message bundle to only encountered nodes (Rj+1, i) with higher centrality metrics than itself and removes its own local copy to ensure that K number of forwarding nodes remain in the network.
Multiple-Data Multicast: In Multiple-Data Multicast (MDM) [
34], the nodes maintain their destination-awareness about other nodes to select relays from their neighbors. Data will be forwarded to the gateway node if the intended receivers are in other communities.
Figure 6 shows the MDM data forwarding process. The multicast source S needs to deliver data items d1 and d2 to destination sets {D1, D2, D3} and {D2, D4}, respectively. S selects R1 to forward data items to D1 and D2 in the same community. R2 is selected by S to forward d1 to D3 in community C. The gateway node G1 in community B acts as the source after receiving the data item from R2. G1 selects forwarding nodes to relay d1 to the next gateway node G2. Finally, G2 acts as the source and selects relays to forward d1 to D3. Overhead is reduced largely with the proposed SDM and MDM mechanism.
Cloud-Based Multicast: Wang et al. [
35] presented a cloud-based multicast scheme to address the problem of relay selection for efficient multicasting in MSNs. It is a cost-effective scheme that offers multicasting services in this variant of DTN with a feedback control mechanism. The destination cloud consists of the destinations and the nodes that are frequently in contact with destinations of similar characteristics. The scheme works in the following two phases: Pre-cloud and inside-cloud, as shown in
Figure 7. The source makes the forwarding decision based on the forwarding metric when it meets a node during the pre-cloud phase. The forwarding metric is obtained from the feedback control mechanism after capturing the shortest multicast time for a node to forward data to the destinations during the previous multicast process. In the inside-cloud phase, any node that holds the message only forwards the message when it meets the destination. Cloud-based multicasting with a feedback control mechanism disseminates the data rapidly using the local information exchanging scheme only. Although the performance of the cloud-based multicast scheme is unfavorable in the beginning, the feedback mechanism improves the performance and stabilizes after a few rounds.
Two-Level Multicast Routing: Two-Level Multicast Routing (TLMR) is a single-copy multicast routing approach that bundles multiple multicast recipients into a single copy of the data packet. Le et al. [
36] intended to reduce transmission costs and achieve an optimal delivery rate and efficient computing resource usage at the same time. This approach switches between one-hop delivery probability and multi-hop delivery probability when selecting the forwarding nodes. In the first level, the message relay selects the relay based on the social-tie strength of the encountered node with multicast destinations. The decision in the second level is made based on the multi-hop delivery probability computed over the most possible route to the destinations. Though the second level can make a more accurate relay selection, it results in higher computing overhead compared to the first level. TLMR maintains a balance between the computing overhead and the transmission rate.
Social Differences Multicast Routing: Different from typical social-based routing, Social Differences Multicast Routing (SDMR) [
37] forwards multicast bundles to nodes with larger social differences. SDMR relay selection is based on the following two social difference metrics: Similarity difference and centrality difference. The former refers to the difference between the two encountered nodes to the bundle destination, and the latter refers to the difference between nodes to all the nodes in the network. A greater similarity difference increases the ratio of the bundle delivery, while a higher centrality difference expands the data coverage. In the SDMR scheme, data are transmitted with minimum cost, without compromising the delivery ratio and round-trip time. Such an efficient scheme, according to Deng and Chang [
37], is well suited for DTNs with limited energy and buffer capacity.
4.1.2. Interest Profile
Q-learning-based Gain-aware Routing: The Q-learning-based Gain-aware Routing (QGR) protocol [
38] is designed to maximize the commercial gain of the content provider through a composite routing index, combining revenue from delivery and the forwarding cost when disseminating commercial contents (e.g., coupons). Any node that runs this protocol can identify the encountered node as a content destination or as a relay, based on the interest level on the content and interaction patterns. The state-action functions of Q-learning enable the nodes to learn a set of forwarding actions to identify the right path with maximized gain.
Figure 8 shows the interaction and routing scenario in the QGR protocol. Each N-i node is indicated with the redemption probability (i.e., interest level). Higher total gain can be achieved when N-0 chooses N-1 as a relay, even though N-2 can also contribute to higher revenue but lower dissemination potential. QGR is applicable and beneficial to marketing applications because it can maximize commercial gain. However, it has no mechanism to detect and handle node selfishness in terms of social context for D2D content dissemination.
Multicast Polymorphic Epidemic Routing: Galluccio et al. [
39] proposed a multicast polymorphic epidemic routing scheme that utilizes the interest similarity of nodes to aid multicast data dissemination in DTN. Each node stores its interests into an interest profile using a Z-dimensional array, where Z is the total number of interests in the network. A similar structure is stored in each packet header as a packet relevance profile. This scheme computes a cosine similarity metric based on the interest profile of two nodes during each contact. A packet will be relayed if the cosine similarity value is high, which indicates both nodes belongs to the same group. In the case of different group node contact, the cosine similarity metric will be computed from the packet relevance profile and interest profile of the contacted node. The authors introduce adaptive recovery schemes along with this scheme to facilitate multicast routing.
Community and Social Feature-Based Multicast: Community and social feature-based multicast [
40] is a compare-split scheme based on community detection that includes two algorithms: Multi-CSDO involves destination nodes only in community detection, and Multi-CSDR involves both the destination nodes and the relay candidates in community detection. In this scheme, each message contains a set of destinations. When the message holder encounters a destination node, it will forward the message to the encountered node. The destination set in the message holder will undergo hierarchical clustering and will be divided into two communities. The nodes that have higher social similarity to each of the community will carry the message for that community. Social similarity is based on dynamic social features that make up an interest profile in each node.
4.1.3. Discussion
Mobile devices, such as smartphones, carried by individuals possess specific social characteristics due to the behavior and interest of their owners. Those who share similar interests can comprise Social Wireless Networks (SWNs), where the interaction patterns can be leveraged to achieve efficient data delivery. For example, the smartphone carried by an individual collects traffic data along the way when driving from home to work and shares the information with other road users who have similar interests. Positive social characteristics are common metrics exploited by researchers to design a social-driven solution to increase message delivery in DTN.
Table 1 shows the performance comparison of social-aware multicast routing in DTN. Most of the schemes are compared with one of the common benchmark algorithms, which are epidemic routing in terms of delivery ratio, cost, and latency. The epidemic protocol usually stands out from others in terms of delivery ratio due to its flooding-based nature which can achieve a high rate in delivery.
SDM, MDM [
34], Cloud-based Multicasting [
35], and TLMR [
36] focus on social centrality and community to select the most suitable forwarding node based on the contact probability of a node. SDM and MDM are cost-effective because a minimum number of relays in multicast data forwarding are utilized, and hence they have a lower delivery cost. The performance of the cloud-based multicast scheme is highly dependent on the size of the destination cloud. Its delivery delay is lower when cloud size is small, with a tradeoff of higher delivery cost due to the increased number of forwarding nodes. However, the First In First Out (FIFO) message dropping policy might cause some multicast messages to be discarded before they reach the destination cloud. Reference [
36] has a higher delivery cost due to the longer forwarding path that involves more relays, but the chosen route has lower latency. The routing performance is not promising if the individual has low social centrality and community characteristics. The SDMR [
37] introduces two social metrics to compute the differences between nodes instead of social similarity, which is beneficial in terms of expanding forwarding coverage and relieving high centrality nodes from exhaustion. The latency for SDMR is high due to the extension of the coverage area, and a moving node will carry the message for a longer period.
For the social-aware schemes that are based on interest profile, QGR [
38] considers the interest level of a user on specific content to implement a coupon dissemination mechanism using multicast routing strategies. QGR sacrifices latency to minimize the forwarding cost. Polymorphic epidemic multicast routing [
39], Multi-CSDO, and Reference [
40] only consider offline social features in constructing the user interest profile. Furthermore, all the social-aware multicast routing schemes did not take energy metric into account in the relay selection, which is a significant element in social-based networks that are comprised of highly mobile nodes.
Multiple social characteristic metrics can be considered jointly when designing a multicast routing algorithm to improve the predictability of mobility patterns, since human behaviors are not dependent solely on contact opportunities. Furthermore, the combination of social metrics and opportunistic metrics may improve the routing performance, but inappropriate combinations could result in the degradation of overall network performance, and the complexity of the routing strategies increases proportionally with the number of metrics taken into consideration. Some nodes are selfish in nature and they are reluctant to participate in message relaying. The authors in Reference [
41] proposed a Congestion Aware and Selfishness Aware Social Routing protocol (CASASR) that considers energy level as the reason for a node to behave selfishly. Li et al. [
42] studied the impact of node selfishness in a DTN multicast context and how the multicast group size affects the performance of the multicast routing performance.
4.2. Buffer-Efficient Multicast Routing in DTN
Resource-constrained IoT devices usually have limited storage capabilities, and they need to store message bundles until opportunistic contact with others to forward data. Enabling multicast communication in DTN causes severe buffer overhead due to the repeated replication of messages to increase delivery rate, especially in multi-copy-based routing. Without proper buffer management, obsolete messages will be removed from the message buffer when the storage is full. However, it is difficult to guarantee that all the intended recipients will receive a message if the messages are removed too early. Improper buffer management thus results in a low delivery ratio, particularly when many nodes initiate multicast sessions together. Buffer-efficient multicast routing strategies increase the overall network performance and are beneficial in terms of message delivery reliability. Buffer-efficient multicast strategies can be modeled by either using a buffer management scheme or reducing the number of message replicas in the network.
4.2.1. Buffer Management
Sociality-based Buffer Management for Multicast Routing: Sociality-based Buffer Management for Multicast Routing (SBMR) [
43] includes a buffer management strategy to assist social centrality-based distributed multicast routing. Nodes with a higher social centrality score are selected as forwarding nodes. This method results in a heavier transmission workload on the selected nodes, which now must drop messages more often when the storage is full. When there is an incoming message upon encountering some node, the node will first check if its available buffer is enough to accommodate the message. When the buffer is sufficient, it will accept the message and store it into the buffer. On the contrary, SBMR drops messages with the most copies (i.e., highest replication number) in the network whenever the storage is fully loaded. Consequently, storage space is saved for messages with fewer numbers of copies, and the messages are not well-distributed in the network.
Sociality-based Comprehensive Buffer Management for Multicast Routing: A new metric, message Time-To-Live (TTL), is introduced in their extended work on Sociality-based Comprehensive Buffer Management for Multicast Routing (SCBMR) [
44] to remove messages with more replicas and with shorter TTL in the network. For example, when node i encounters node j and node i wants to forward message t
m node j after the social centrality comparison between two nodes, node j will proceed to check if it has enough buffer to accommodate message t
m, as shown in Algorithm 1. The
MNTm value is computed from the replication number and the
TTL value of the message as follows:
where
MNim is the replication number of message
m for multicast and
TTLm is the
TTL value for message
m. The values of
a and
b are the tunable parameters to decide the weight of the replication number and
TTL value. Both schemes improve the message delivery ratio without compromising the transmission cost and delivery latency.
| Algorithm 1 Buffer management algorithm in SCBMR [44]. |
| 1: Require: Node i forwards message tm to node j |
| 2: if (Node j’s free buffer size < tm size) then |
| 3: Msg = message with maximum MNTm value in Node j’s buffer; |
| 4: Node j removes message Msg from its buffer; |
| 5: end if |
| 6: Node j caches incoming message in its buffer; |
Quota-Based Multicast Routing: Quota-Based Multicast Routing (QBMR) [
45] exploits contact behavior in selecting relay nodes to multicast messages in DTNs. This scheme is extended from Dynamic Quota-Based Routing (DQBR) [
46], which considers only DTN unicast routing. QBMR adopts a quota replication scheme to dynamically generate a different number of message replicas based on the present condition of the network. QBMR reduces the redundant message replicas in the network and results in a higher delivery rate and lower latency. The authors further added a probability-based method to QBMR to remove obsolete messages. Each node maintains an i-list table to record the number of receivers for a multicast message based on the responses from multicast destinations. They will compute the average multicast group size from the table as the threshold to remove multicast messages from the buffer. When the number of receivers for a multicast message exceeds the average group size, this message has a higher probability to be removed if the buffer is full. It will be marked as a frozen message and moved to the temporal region of the buffer. This is to ensure any multicast receiver who join later is able to receive a multicast message from a high contact probability node after a long period. Any incoming message is stored in the normal region and the oldest message will be moved to the temporal region as a frozen message by the drop policy if the normal region is full. It calculates a rank value to decide the sequence to delete messages after looping through the buffer. The advantage of QBMR is that it does not require any overhead cost to maintain group membership information. The node will exchange and merge the i-list tables on each encounter. During the merging process, the entries with the same multicasting EID (M_EID) are grouped together to look for the maximum value of the number of receipts for a multicast message. This maximum value donates the current size of a multicast group and the average multicast group size can be estimated.
Reliable Multicast over Delay tolerant mobile Ad hoc networks: Reliable Multicast over Delay tolerant mobile Ad hoc networks (RMDA) is a flooding-based multicast scheme with a group management module and a transmission management module. It forwards the message bundle to a computed average amount of group members to ensure reliability but induces a higher buffer resource consumption [
47]. RMDA achieves a higher delivery ratio by keeping track of the total number of group members. Begerow et al. [
48] proposed an extended version of RMDA with a buffer management strategy, as depicted in
Figure 9. It checks whether the available buffer can accommodate incoming messages. The oldest unicast message is deleted first, followed by the multicast message with a delivery ratio closest to the RMDA value whenever the free buffer is not enough to accommodate new messages. They further introduced a configurable delivery ratio to prioritize multicast messages and reserve a certain amount of buffer space for multicast messages only [
49]. The scheme removes buffered messages based on an estimated number of group members, the number of ACKs, and the configured delivery ratio level. The simulation results show that the ratio of message delivery increases even in a larger group size. However, the flooding-based nature of these protocols forwards the message bundles to any encountered node without authentication.
Precede Global Knowledge-Based Scheduling and Drop Policy: The precede Global knowledge-Based Scheduling and Drop policy (GBSD) [
50] is known as an optimal-based strategy dedicated to unicasting in DTNs. GBSD schedules and drops messages by estimating the delivery probability of each message upon contact. Hsu and Hu [
51] extended GBSD to formulate the delivery probability to multiple endpoints to support the multicasting service in DTN, and they implemented a new E-GBSD algorithm to schedule and to remove messages. E-GBSD prioritizes source messages in the buffer and stores them until the local buffer is full of source messages to ensure their availability, which is done by the utility function to maximize the value of the change in message delivery rate (MDR). E-GBSD performs better than FIFO and GBSD and achieves the highest MDR among the three of them.
4.2.2. Reduce Replication
Non-Replication Multicasting Scheme: Wang and Wu [
52] proposed a compare-split scheme to construct a dynamic multicast tree for single-copy message forwarding. The goal of the scheme is to minimize the number of forwarders to reach multicast destinations. The compare-split is performed during contact with potential relays. The scheme makes a comparison during the encounter of a node without any destination subset and decides whether the split will occur based on the contact rate level. Ratio-based-Split (RS) is used to divide the destination subset according to the activity levels of two encountered nodes until only one destination remains in the destination set. The scheme will either wait until it meets the destination or forward the message to a node with a higher encounter rate level with the destination. This scheme exploits the contact state information to construct a dynamic non-replication tree for multicast with a small number of relay nodes, thus reducing buffer resource consumption.
Space Minimizing Tree-Based Routing: Anshuman Tripathi [
53] proposed a generic tree computation algorithm to compute multicast paths with a lower number of relay nodes. The algorithm leads to the reduction of the number of message copies spawned in the network. Space Minimizing Tree-Based Routing (SMTBR) selects relays based on the importance metric. The importance of a node refers to the likelihood that the node will be selected in a multicast path. As shown in
Figure 10, a thin multicast tree structure that has fewer participating nodes can be obtained from SMTBR using a generic tree computation algorithm. The solid circles represent the relays that utilize the discovered path to forward a single-copy of the message until they reach the branch points where the message is replicated as needed for delivery to the destinations (represented by hollow circles in
Figure 10). Two specifications of the algorithm have been discussed. The first updates the importance of a node for every iteration. The node with higher importance is most likely to be selected as a relay. In the second specification, the algorithm updates only once to distinguish important nodes from unimportant nodes. There is a trade-off between message copy reduction and message delivery latency. The delay in message delivery increases for both specifications.
4.2.3. Discussion
Table 2 shows the performance comparison of buffer-efficient multicast routing in DTN. All the schemes with buffer management mechanisms achieve a considerably high delivery ratio. The flooding mechanism always incurs a high delivery cost. Some proposed solutions addressed the buffer issues by adopting a buffer management mechanism in their multicast routing approaches. They used local information, such as the type of message, message TTL, hop counts, and received time-to drop messages in storage. For example, the buffer management scheme in RMDA [
47] prioritizes multicast messages and dropped unicast messages more frequently to free the buffer. Otherwise, network information, such as the number of message copies and the number of received ACKs, can be used as metrics to control the number of messages remaining in the network. There is also the combination of local and network-based information as metrics to remove messages in case of a full buffer to accommodate any new incoming messages. For example, SCBMR [
44] combines the number of replicas with message TTL information to preserve node storage for messages that are not well-distributed in the network. A delay-tolerant IoT network often consists of resource-constrained IoT devices with limited buffer space. The nodes’ buffers will be easily overwhelmed with multicast messages, but they still need to guarantee that intended receivers receive a DTN multicast message. Any routing scheme cannot just drop the oldest message without ensuring the message’s coverage in the network.
Another category of buffer-efficient multicast in DTN exploits dynamic multicast tree generation to reduce the number of message replication or the number of message relays. The single-copy multicasting approach ensures that only a single copy of each multicast message is maintained in the network when the message is forwarded along each tree branch. For example, the Non-Replication Multicasting Scheme [
54] and SMTBR [
53] exploit contact information to build a multicast tree to achieve a minimum number of message replicas in the network. However, tree-based multicast routing approaches are not flexible and require global knowledge to construct the multicast tree.
Ezife et al. [
55] presented a survey on buffer management strategies in DTN and classified them based on protocol dependency and type of drop policy. The authors summarized that major strategies use a dynamic dropping policy due to the mobility characteristics of DTN, which are non-protocol specific, that enable customization and optimization across protocols. However, this survey did not focus on buffer management strategies in DTN multicasting. Provisioning multicast routing approaches with an efficient buffer management scheme improve the overall network performance. Limited storage capacity is always the major constraint of the devices in WSN. Söderman et al. [
56] proposed a buffer management algorithm for a delay-tolerant WSN in the IoT environment, namely SmartGap. SmartGap drops the low priority messages with minimal impact on the overall performance. Buffer-efficient multicast routing strategies are applicable to delay tolerant WSN to accommodate data dissemination IoT application, which involves a large number of wireless sensor nodes
4.3. Energy-Aware Multicast Routing in DTN
Energy is a significant metric in DTN performance since IoT devices are usually limited in battery capacity. They are expected to operate continuously without the need for frequent recharging. Nodes with low residual energy impact the performance of the network, and they do not perform data forwarding efficiently. Multicast induces more transmission overhead, which results in high energy consumption. The residual energy of the nodes can be considered as a metric to design a DTN multicast routing protocol.
Multicast Routing Protocol using Transfer AIM-listed Probability And Energy: The Multicast Routing Protocol using Transfer AIM-listed Probability And Energy (MRPTPAE) [
57] selects the next forwarding node based on the weighted average of the Energy Probability (EP), which is computed from the residual energy and transmission probability of a node. Transmission probability is based on the delivery probability of the Probabilistic Routing Protocol using History of Encounters and Transitivity (PRoPHET) [
58], and when combined with EP, the optimal next hop can be determined. The source node will transfer the message to the chosen next hop if the EP of the next hop is greater than the source node. MRPTPAE also introduced a congestion control strategy to compare message forwarding factors during network congestion and drop messages with the lowest forwarding factors. MRPTPAE helps to control the number of messages in the network and leads to lower overall network energy consumption.
Energy-Aware Single-Data Multicast: Energy-Aware Single-Data Multicast (EASDM) is a socially-aware multicast routing scheme with energy consumption optimization features. This scheme is extended from the Single-Data Multicast (SDM) that was proposed by Gao et al. [
33]. SDM is a social-based multicast routing approach that exploits the social centrality metric for relay selection. SDM is extended to provision energy awareness in multiple multicast sessions in Reference [
59]. Participating nodes monitor their residual energy and exchange this information with any encountered node. Relay nodes are selected based on the centrality metric and the remaining energy of the node.
As shown in
Figure 11, the multicast source groups the nodes with Pi values less than 0.5 into the high-centrality set and gathers the rest into a low-centrality set. Node C will be selected as relay first because it has the highest residual energy, followed by node A with the second highest residual energy. EASDM selects a subset of nodes as forwarding nodes from the high-centrality node set and reserves the remaining nodes for future use. Node E is further chosen as relay due to the highest residual energy in the low-centrality set. It will select relays from the low-centrality node set if the constraint is not satisfied. This scheme supports multiple multicast sessions while maintaining the expected delivery rate. The author claimed that EASDM can sustain the network for a longer time by relieving some of the high centrality nodes. However, this scheme does not integrate awareness of the relay interest in the message.
Energy-Aware Multiple-Data Multicast: Roy et al. proposed the Energy-Aware Multiple-Data Multicast (EAMDM) along with EASDM in Reference [
60]. The EAMDM is based on the MDM [
33] that select relays based on social community characteristics. The differences between EASDM and EAMDM are that the latter includes the available buffer sizes of the potential relays and a priority metric based on the delivery time constraints of data items to make forwarding decisions. In a set of data items with the same delivery ratio, each data item has different size and delivery time constraint. A data item with a shorter delivery time constraint will have a higher priority to be relayed first. Potential relays will be selected from the encountered neighbors with enough buffer to accommodate this data item and high delivery probability to the destinations. A node with the highest residual energy will be selected as the relay. This process continues until all the performance constraint is satisfied before proceeding to the next data item with lower priority.
Group Encounter Based PRoPHET: The authors proposed the Decentralized Post-Disaster Resource Management [
61] (DPDRM) scheme to manage and exchange information on resources, such as medicines and food of each camp site. DPDRM utilizes smart phones carried by volunteers to provide inventory sharing and resource discovery functionalities. The inventory sharing module shares the resource inventories periodically to a specific group of nodes and the latter enables a query on a specific resource to be disseminated to get a quick response from any node holding resource inventories. Both modules employed Group Encounter Based PRoPHET (Ge-PRoPHET) routing protocol to facilitate sharing of resource inventories and query dissemination. Ge-PRoPHET is adapted from PRoPHET to provision group-based multicasting (groupcasting) for post-disaster communication based on group delivery predictability (GDP), and replicates messages only if the encountered nodes have a better chance of meeting any member node of a destination group. This scheme achieves a reduction in average energy consumption due to transmission by minimizing unintended replication of resource inventories and queries.
Discussion
Energy efficient routing in DTN receives much attention from the research community. Energy deficiency in DTN nodes is always an indisputable challenge that many researchers intend to resolve. Node mobility, frequent contact, and multicast message routing consume much energy which depletes the node’s battery power more quickly. Depleted batteries increase the network disruption and impact on the delivery ratio.
Table 3 shows the performance comparison of energy-aware multicast routing in DTN. We notice that the energy consumption for mobile nodes in energy-aware schemes is very low compared to other schemes. MRPTPAE [
57], EASDM, and EAMDM [
60] take into account node residual energy to make relay selections, and this causes the computation overhead to be higher.
There are limited studies in the literature addressing provisioning energy-aware routing mechanisms in DTN multicasting services. Nonetheless, energy efficient algorithms can be incorporated into multicast routing schemes, since they are generic. Hence, we discuss some of the proposed energy-related algorithms for unicast and broadcast in DTNs. Eshghi et al. [
62] studied epidemic routing in an energy-constrained DTN and implemented an optimal energy-aware relay selection based on the node’s remaining energy and message’s age. Meanwhile, the nodes in the Energy Efficient Routing Protocol based on Fuzzy Ant colonies (EERPFAnt) [
63] are able to estimate the remaining energy levels of each potential relay at the time when they meet with their destination. In Reference [
64], the Distance-based Energy-Efficient Opportunistic Forwarding (DEEOF) framework estimates the node distance, tolerant delay, and the number of forwarders to broadcast messages in DTN. The nearer the forwarders are or the earlier the time of delivery is, the less energy is consumed for message delivery. EASDM [
59] is one of the few protocols that consider energy level in the design of multicast routing algorithm.
Many IoT applications have an energy constraint requirement to ensure overall network availability, such as in post-disaster communication scenarios. Conventional energy saving schemes schedule nodes to sleep, reducing contact probabilities and further degrading the overall performance. Routing algorithms that solely replicate an unnecessary number of messages to increase delivery ratios are inefficient, and they cause high overheads due to redundant message replication, transmission, and reception. It is a significant energy waste, especially in delay tolerant and resource-constrained networks. These algorithms are not feasible in resource-constrained IoT environments, since energy is a vital resource to ensure network availability. Kang and Chung [
65] devised an energy-aware routing protocol based on PRoPHET in delay-tolerant WSNs. They considered a disaster-related scenario consisting of pedestrians, cars, and trams as mobile nodes to store-carry-forward emergency messages and self-generated sensor data to a static sink node. The combination of the node’s residual energy, delivery probability, and the node’s category decides the message forwarding on each encounter. All the IoT sensor data in the delay tolerant WSN are gathered and delivered to the cloud for further analysis. Stamatakis et al. [
66] proposed an energy efficient packet transmission policy that selects energy efficient wireless networks to reduce energy consumption in the disruption-tolerant IoT network with heterogeneous resources. We believe that energy efficiency algorithms not only enhance multicasting services and delivery success rate but also provide more reliable transmission.
4.4. Geographical Multicast Routing in DTN
Geographic routing exploits geographic position information to make message forwarding decisions. The source is either aware of the destinations’ location or selects appropriate relays based on their geographic position. The ferry or data mule move from one region to another region to forward messages. For example, patrols and workers carry handheld devices around a deployed area according to a scheduled route to provide periodic network connectivity. Ferry-based routing approaches are hence scenario-specific, since the route must be defined before implementation. Location-based routing approaches are based on node location to forward data and require minimal network information. The nodes are equipped with navigation systems to collect information about the location of destinations and neighbors during multicast sessions.
4.4.1. Ferry/MULE-Based
Ferry-Based Interdomain Multicast Routing: Interdomain multicast refers to the delivery of multicast messages between multiple domains. Yang and Chuah [
67] introduced the Ferry-Based Interdomain Multicast Routing (FBIMR) scheme to support multicast routing for data forwarding across multiple domains. FBIMR deploys one or more ferries to deliver multicast traffic from one domain to another. A source forwards multicast messages to the domain leader for delivery. A ferry helps in transferring the interdomain traffic from its own local group to outside groups by contacting the domain leaders. FBIMR works efficiently when coupled with the Encounter-Based Multicast Routing with redundancy (EBMR2) scheme for intradomain multicast delivery within local groups.
Figure 12 depicts the multicast message delivery process of the FBIMR scheme. Initially, the source forwards multicast messages to the group leader. The Message Ferry (MF) travels from Group 1 to visit the Group Leader (GL) of another group. The GL uses the EBMR2 scheme to deliver multicast messages to the destinations within its own domain after receiving the messages from MF. FBIMR constructs a hierarchical multicast to lower the management overhead.
New Vehicular Delay-Tolerant Networks: Palma et al. [
68] proposed a multicast routing protocol in vehicular DTN, namely New Vehicular Delay-Tolerant Networks (NewVDTN), which is a combination of some geographic-based routing features [
69], PROPHET [
58], and spray-and-wait [
70] protocols. A dense scenario with high vehicle density is differentiated from a sparse scenario with low vehicle density according to an estimation of the number of nodes encountered. In dense scenarios, the scheme selects MULE (Mobile Ubiquitous LAN Extensions) nodes carefully by considering their movement directions and the network general storage level estimation, and the scheme then assigns a TTL to the source message to reduce congestion. Messages are scheduled according to their priority and general buffer occupancy estimation. In sparse scenarios, the scheme will forward messages to as many MULEs as possible to achieve a better ratio of delivery to the destinations. The list of encountered nodes is always sorted based on the estimated vehicle density. It is possible to forward messages to the nodes with higher contact probabilities.
Social Dynamic Features Aware: The authors in Reference [
71] examined the social dynamic features of vehicles in macroscopic and microscopic views. The former indicates that messages can be propagated between two areas easily when there is high traffic flow of taxis between them. The latter indicates the movement pattern of individual taxis with transition probability to reach one of the areas in the map based on past trajectory. Combining both macro and micro dynamic features of vehicles, the authors proposed GEOgraphic multicast routing based on the Social Dynamic Features Aware (GeoSDFA) scheme. GeoSDFA is a mobility-aware geocast scheme that calculates a likelihood value for each message, which is the probability of vehicles to forward a message towards a specific area. A node compares its messages’ likelihood value with its encountered node and forwards the messages if it finds that the likelihood value of the encountered node is higher. However, there might be chances that a vehicle visits the destination areas frequently, even when the likelihood value is low. If the likelihood value of an encountered node for a message is lower, a node will further compare its contact strength to destination areas with the encountered node. Different from existing geocast schemes, GeoSDFA is not solely based on vehicle probability, but also takes into consideration the realistic scenario that some vehicles with lower probabilities are able to reach some areas.
4.4.2. Location-Based
Collaborative Time-Stamp based Multicast Routing: Collaborative Time-Stamp based Multicast Routing (CTMR) [
72] is a probabilistic routing protocol based on historical encounters and implements a time-stamp to limit recently communicated nodes from further communication attempts within a predefined time-stamp threshold. The authors make the assumption that recently communicated nodes are not likely to have new bundles for forwarding, and thus energy in the nodes is preserved from unnecessary communication overhead. CTMR employs a customized bundle format, which includes the GPS coordinates of nodes when it creates the bundle. This location information is stored as one bundle for the metadata for every bundle in each node. For any encounter of two nodes after the time-stamp limit, they first exchange the metadata of the bundles and calculate the location differences of the same type of bundles from both nodes using the Haversine formula. The sender only forwards bundles when the location difference is greater than the predefined location difference threshold to minimize redundancy.
4.4.3. Discussion
Ferry/mule-based routing is a type of routing with infrastructure assistance that adopts additional mobile nodes to bridge the communication between disconnected networks. The Message Ferrying (MF) concept is adopted in Reference [
73] for sparse MANETs to relay messages using ferries to reach a specific region. Ferries travel around the specific region to forward and collect data. The authors in Reference [
73] extended their work for DTN communications using multiple ferries and different route designs [
74] via four approaches: Single Route Algorithm (SIRA), Multi-Route Algorithm (MURA), Node Relaying Algorithm (NRA), and Ferry Relaying Algorithm (FRA) approaches. Another work in Reference [
75] categorizes ferries into two types: Regional ferries belonging to the source region, and independent ferries, which do not stick to any region. However, none of the proposals address multicast routing in DTN except FBIMR [
67] and NewVDTN [
68]. FBIMR forwards multicast messages between different domains with the help of message ferries to achieve inter-domain multicasting. NewVDTN selects the data mule based on the congestion level of the network for multicast message delivery.
Table 4 shows the performance comparison of geographical multicast routing in DTN. In FBIMR, the increased number of ferries improves the overall performance more than increasing the speed of the ferry in a single ferry deployment. NewVDTN is well suited for sparse networks, but its performance decreases when the network density is higher. The deployment of data MULEs requires careful consideration of the network density and the number of MULEs; even the trajectory of the MULE plays an important role. For location-based schemes, CTMR [
72] limits the communication attempts by the implementation of a time contrast to better conserve energy and results in higher delivery delay.
The ferry/mule-based approach is a promising approach to improve the performance of DTN multicasting. Unmanned Aerial Vehicles (UAVs) or drones are being used as ferries for data dissemination and collection. For example, the authors in [
76] used a drone in DTN to lower the cost of implementing smart cities monitoring. In Geographic Spray and Wait (GeoSaW) [
77], the current location and scheduled path information of UAVs are utilized to determine the most suitable UAV to relay messages to the destination. The reliability of message delivery can be further enhanced by location-aware algorithms using geographical information gathered from GPS equipment or localization techniques.
5. Open Issues in DTN Multicasting
The DTN paradigm successfully addresses some of the problems related to intermittent connectivity in the opportunistic network. However, there are indeed some prominent open issues worthy of researchers’ attention. The redefinition of multicast routing in DTN also gives rise to new issues in different aspects, such as security, node behavior, and the performance of DTN. This section intends to give some insight into open issues in DTN and to further discuss them in terms of multicast routing.
5.1. Node Integrity
From the perspective of DTN nodes, they are vulnerable to attacks (e.g., Denial of Services (DoS) and spoofing) and might behave maliciously. Security mechanisms are a necessity in DTN, especially in MSN when the distribution of personal or classified information is involved. However, traditional security models designed for standard Internet Protocol are not suitable for DTN due to the sparse and intermittent nature of classified information. Since DTN is a resource-constrained network, in which bandwidth, energy, storage, and processing power are limited, a good security mechanism with minimal resource overhead shall be implemented. Due to this limitation, most of the proposed routing schemes do not consider the security aspects in DTN, where the security mechanism involves forwarding nodes (e.g., routers and gateways) in the authentication process. Forwarding nodes authenticate sender information to prevent unauthorized traffic at the earliest time and to conserve network resources. Some nodes might maliciously drop or tamper with messages forwarded to them, and we have to avoid relaying messages to such kinds of nodes. The trust level of each node can be calculated, and messages are relayed only to trustworthy nodes. There are available trust management schemes to detect and filter out malicious nodes in DTNs based on the forwarding pattern and the energy level of the node, such as in Reference [
78]. Besides that, faulty node detection mechanisms are also important to detect and isolate faulty nodes that might produce erroneous data [
79].
In terms of multicast security, the present security architecture does not provide security measures to restrict any node to register with a specific multicast group Endpoint Identifier (EID). EIDs are used to identify the sender and receiver of a message bundle. Any node can register itself into a multicast group and receive traffic dedicated to that group. When a node receives a message in flooding-based routing, it will forward the message to every encountered node, including unintended recipients. For example, temperature nodes in environmental monitoring should receive a minimum number of messages intended for other groups of nodes to prevent high bandwidth consumption and long delays in message delivery. Furthermore, security mechanisms also prevent unintended receivers from performing malicious activities. Security mechanisms are essential in DTN multicasting to protect the integrity of the node [
80].
Many security aspects related to node integrity in DTN are unexplored, such as encryption of multicast data, multicast routing protocol security, and trust management in DTN multicast. These issues still remain open for further research.
5.2. Group Authentication
From the perspective of DTN group membership, multicast group key management is one of the critical components for multicast group authentication to secure communication and protect data. However, conventional group key management schemes are not applicable in DTN due to its frequent disruption and long propagation delays. For example, the stateful Logical Key Hierarchy (LKH) [
81] scheme requires re-keying from the key management center when a user joins or leaves the network, and it is not practical in DTNs with no reliable end-to-end network links. A Chinese Remainder Group Key (CRGK) scheme [
82] for DTN environments is proposed, which omits the broadcast of key update messages when a new user joins the network by letting each member derive a new group key using a forward hash function. CRGK only broadcasts the key update message when a user leaves the group, and the complexity depends on the number of users in the group. Gupta [
83] extended CRGK into the Modified Chinese Remainder Group Key (MCRGK) scheme that does not need to broadcast any key update messages when a user joins or leaves the group. Both CRGK and MCRGK are only able to accommodate small to medium-sized DTN groups. Menesidou, Katos, and Kambourakis [
84] surveyed these key establishment methods for group communication as part of their proposed taxonomy and discussed them in details with DTN’s security requirements.
Xu, Chen, and Du [
82] discussed three requirements for group key management schemes in DTN. Firstly, the scheme needs to minimize the number and size of the key update messages to avoid communication overheads. Secondly, an efficient group key management scheme for DTN should be stateless, and re-keying can be done through the latest key update message. Lastly, adding a key lifetime to the scheme is necessary to protect forward security after a user leaves the group. Nevertheless, the scalability of group key management schemes remains one of the most prominent issues. The computational complexity of the key server and length of key update messages grows with the size of the group. The implementation of key management schemes in the DTN multicast protocol will increase the resource overheads, especially for IoT devices, and this is an interesting open issue to be resolved.
5.3. Selfish Behavior of Nodes
Most DTN routing approaches expect nodes to assist with message forwarding in a cooperative way. However, this is not necessarily true in the real-world environment due to the selfish behavior of the nodes, which are classified into individual and social selfishness [
85]. The former refers to the reluctance of a node to relay messages to conserve resources, and the latter points to its willingness to forward messages to nodes in the same community. Several incentive mechanisms [
11,
79,
86] are proposed for DTN routing approaches to motivate selfish nodes to cooperate and help in improving system-wide performance.
Multicast in DTN is intended to provide efficient message delivery to a group of users with less resource overhead. However, it is also similarly affected by the selfish behaviors of nodes. Li et al. [
42] and Li et al. [
87] studied the impact of this selfish behavior on two-hop relay and epidemic routing schemes in terms of average latency and transmission cost. They demonstrated that individual selfishness increases both the message transmission delay and the cost, whereas social selfishness increases only the message transmission delay and reduces the transmission cost. Therefore, individually selfish and socially selfish nodes impact network performance differently. A sophisticated multicast routing algorithm is thus required to detect and handle the two types of selfish nodes differently according to the context information to improve performance.
5.4. Performance due to Protocol Complexity
There are a few common performance metrics that are used to evaluate the effectiveness and efficiency of DTN routing algorithms, including the following: Delivery ratio, delivery latency, transmission cost, and energy consumption. Since IoT devices deployed in a DTN environment are usually limited in storage and operate in low power mode for message forwarding, a routing algorithm shall achieve enough delivery ratios within a specific delivery latency and low overhead in terms of delivery cost and energy consumption. Data efficiency and overall efficiency are two other performance metrics that are specific to the multicast communication paradigm and are based on the ratio of delivered multicast packets to the traffic generated (data or control packets) in the network [
6].
Multicast in DTN requires group membership maintenance due to the mobility of nodes. The fact that nodes may join or leave a group anytime contributes to the dynamic topologies in the network. Membership might change during message propagation, which might be longer due to intermittent connectivity, so there is no general framework to define the intended receivers of multicast traffic. Such a dynamic membership generates extra transmission overheads that affects the overall performance. On the other hand, the security mechanism in DTN also incurs extra transmission and computation costs. Encoding or use of a cryptography algorithm increases the bandwidth utilization, while computation costs depend on the security algorithm used to encrypt the messages.
Furthermore, buffer management schemes also increase the complexity of routing protocols and affect network performance with higher computational cost. The goal of a sophisticated multicast routing protocol aims to achieve a maximum delivery ratio with shorter delays and make the best use of resources to improve overall network performance.
Besides the discussed open issues, we also should pay attention to the incorporation of artificial intelligence (AI) in DTN to improve routing efficiency and network performance. For example, AI can help to minimize the number of replications using fuzzy logic and ant colony optimization [
63], or can compute and learn the trust level to select the best candidate to relay messages [
88]. Furthermore, there are potential new applications for DTN in future internet architectures, such as the Information Centric Network (ICN) [
89], or for use in new technologies, such as fog computing [
90].
6. Conclusions
Some applications for IoT require disruption-tolerant communication, especially in sparse and intermittent networks where there is no continuous end-to-end communication between the data source and its destinations. The design of DTN multicast routing protocols in such contexts becomes more complex due to the reliability constraints in ensuring that intended receivers receive messages without compromising the overall performance. The current state of multicast routing approaches in DTN was outlined and classified based on their design concepts: social-awareness, buffer-efficient, energy-awareness, and geography. Although the surveyed protocols are classified into specific categories, some of them exhibit the characteristics of another category due to the hybrid approach incorporating multiple design concepts.
The usage of buffer management schemes is highest among the discussed schemes due to their non-protocol dependent nature. The rest of the described protocols are rather scenario-specific, as the authors intend to solve some specific problems using DTN multicast services. The social-aware multicast routing protocols have evolved from merely using the encounter history to including the dynamic social features of the users. MSN continues to evolve due to the inseparable relationship between humans and devices. Socially-aided protocols will deserve more attention than ever in the future of DTN research. However, we should not neglect the importance of energy-aware protocols, since IoT devices are usually resource-constrained, and energy conservation is essential for maintaining longer network lifetimes. The exploitation of social patterns to minimize delivery costs in combination with efficient buffer management schemes will definitely help in providing energy-efficient protocols in the future.
Open issues in DTN were also discussed both in general and in terms of multicast limitations. Node integrity and group authentication in DTN have always been major concerns, especially with the increasing involvement of humans and their devices. It is critical to adopt security measures and trust management mechanisms. However, the increase in computation costs and maintenance overhead is unavoidable, and efficient mechanisms need to be devised to improve the overall performance of security mechanisms. The focus of our future work is to address some of the performance-related issues in designing a reliable multicast for DTN to support IoT applications.
Author Contributions
The contributions of authors are as follows: Conceptualization, K-S.W. and T-C.W.; formal analysis, K-S.W.; investigation, K-S.W.; resources: K-S.W.; supervision, T-C.W.; validation: T-C.W.; writing—original draft: K.S.W.; writing—review and editing, K-S.W. and T-C.W.
Funding
This work is supported in part by Universiti Sains Malaysia through RUI Grant No. 1001/PKOMP/811336.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Holler, J.; Tsiatsis, V.; Mulligan, C.; Karnouskos, S.; Avesand, S.; Boyle, D. From Machine-to-Machine to the Internet of Things: Introduction to a New Age of Intelligence, 1st ed.; Academic Press: Cambridge, MA, USA, 2014; ISBN 978-0-12-407684-6. [Google Scholar]
- Boyer, S.A. SCADA: Supervisory Control and Data Acquisition, 3rd ed.; International Society of Automation: Durham, NC, USA, 2004; ISBN 978-1-93-600709-7. [Google Scholar]
- Stouffer, K.; Falco, J.; Kent, K. Guide to Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2006.
- Fall, K. A Delay-tolerant Network Architecture for Challenged Internets. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM’03), Karlsruhe, Germany, 25–29 August 2003; ACM: New York, NY, USA, 2003; pp. 27–34. [Google Scholar]
- Cerf, V.; Burleigh, S.; Hooke, A.; Torgerson, L.; Durst, R.; Scott, K.; Fall, K.; Weiss, H. Delay-Tolerant Networking Architecture. Request for Comments (RFC) 4838. Internet Engneering Task Force, April 2007. Available online: https://www.rfc-editor.org/info/rfc4838 (accessed on 2 January 2019).[Green Version]
- Sobin, C.C.; Raychoudhury, V.; Marfia, G.; Singla, A. A Survey of Routing and Data Dissemination in Delay Tolerant Networks. J. Netw. Comput. Appl. 2015, 67, 128–146. [Google Scholar] [CrossRef]
- Hui, P.; Chaintreau, A.; Scott, J.; Gass, R.; Crowcroft, J.; Diot, C. Pocket Switched Networks and Human Mobility in Conference Environments. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking (WDTN’05), Philadelphia, PA, USA, 22–26 August 2005; ACM: New York, NY, USA, 2005; pp. 244–251. [Google Scholar]
- Hui, P.; Crowcroft, J.; Yoneki, E. Bubble Rap: Social-based Forwarding in Delay Tolerant Networks. IEEE Trans. Mob. Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Mao, Z.; Jiang, Y.; Min, G.; Leng, S.; Jin, X.; Yang, K. Mobile social networks: Design requirements, architecture, and state-of-the-art technology. Comput. Commun. 2017, 100, 1–19. [Google Scholar] [CrossRef] [Green Version]
- Yan, Y.; Chen, Z.; Wu, J.; Wang, L. An Effective Data Transmission Algorithm Based on Social Relationships in Opportunistic Mobile Social Networks. Algorithms 2018, 11, 125. [Google Scholar] [CrossRef]
- Jedari, B.; Liu, L.; Qiu, T.; Rahim, A.; Xia, F. A game-theoretic incentive scheme for social-aware routing in selfish mobile social networks. Future Gener. Comput. Syst. 2017, 70, 178–190. [Google Scholar] [CrossRef]
- Tsai, T.C.; Liu, T.S.; Han, C.C. Waterchat: A group chat application based on opportunistic mobile social networks. J. Commun. 2017, 12, 405–411. [Google Scholar] [CrossRef]
- Conti, M.; Passarella, A.; Das, S.K. The Internet of People (IoP): A new wave in pervasive mobile computing. Pervasive Mob. Comput. 2017, 41, 1–27. [Google Scholar] [CrossRef]
- Paul, S.; Sabnani, K.K.; Lin, J.C.H.; Bhattacharyya, S. Reliable multicast transport protocol (RMTP). IEEE J. Sel. Areas Commun. 1997, 15, 407–421. [Google Scholar] [CrossRef] [Green Version]
- Genç, Z.; Özkasap, Ö. EraMobile: Epidemic-based reliable and adaptive multicast for MANETs. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC 2007), Kowloon, China, 11–15 March 2007; pp. 4398–4403. [Google Scholar]
- Zhang, Z. Routing in intermittently connected mobile ad hoc networks and delay tolerant networks: Overview and challenges. IEEE Commun. Surv. Tutor. 2006, 8, 24–37. [Google Scholar] [CrossRef]
- Cao, Y.; Sun, Z. Routing in delay/disruption tolerant networks: A taxonomy, survey and challenges. IEEE Commun. Surv. Tutor. 2013, 15, 654–677. [Google Scholar] [CrossRef]
- Pelusi, L.; Passarella, A.; Conti, M. Opportunistic networking: Data forwarding in disconnected mobile ad hoc networks. IEEE Commun. Mag. 2006, 44, 134–141. [Google Scholar] [CrossRef]
- Massri, K.; Vitaletti, A.; Vernata, A.; Chatzigiannakis, I. Routing Protocols for Delay Tolerant Networks: A Reference Architecture and a Thorough Quantitative Evaluation. J. Sens. Actuator Netw. 2016, 5, 6. [Google Scholar] [CrossRef]
- Patra, S.; Saha, S.; Shah, V.; Sengupta, S.; Singh, K.G.; Nandi, S. A Qualitative Survey on Multicast Routing in Delay Tolerant Networks. In Recent Trends in Wireless and Mobile Networks, Proceedings of the Third International Conferences, WiMo 2011 and CoNeCo 2011, Ankara, Turkey, 26–28 June 2011; Özcan, A., Zizka, J., Nagamalai, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 197–206. ISBN 978-3-642-21937-5. [Google Scholar]
- Wu, J.; Wang, Y. Opportunistic Mobile Social Networks, 1st ed.; CRC Press: Boca Raton, FL, USA, 2014; ISBN 978-1-4665-9494-4. [Google Scholar]
- Zhao, W.; Ammar, M.; Zegura, E. Multicasting in delay tolerant networks: Semantic models and routing algorithms. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking (WDTN’05), Philadelphia, PA, USA, 22–26 August 2005; ACM: New York, NY, USA, 2005; pp. 268–275. [Google Scholar]
- Juyal, V.; Pandey, N. Performance comparison of DTN multicasting routing algorithms- opportunities and challenges. In Proceedings of the International Conference on Intelligent Sustainable Systems (ICISS 2017), Palladam, India, 7–8 December 2017; pp. 53–57. [Google Scholar]
- Wong, K.S.; Wan, T.C.; Ang, W.C. A survey on current status of Disruption Tolerant Network support for Multicast. In Proceedings of the 2016 3rd International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 15–17 August 2016; pp. 276–281. [Google Scholar]
- Zguira, Y.; Rivano, H.; Meddeb, A. Internet of bikes: A DTN protocol with data aggregation for urban data collection. Sensors 2018, 18, 2819. [Google Scholar] [CrossRef] [PubMed]
- Auzias, M.; Maheo, Y.; Raimbault, F. CoAP over BP for a Delay-Tolerant Internet of Things. In Proceedings of the 2015 3rd International Conference on Future Internet of Things and Cloud (FiCloud 2015), Rome, Italy, 24–26 August 2015; pp. 118–123. [Google Scholar]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP), RFC 7252. June 2014. Available online: https://www.rfc-editor.org/info/rfc7252 (accessed on 2 January 2019).
- Doering, M.; Lahde, S.; Morgenroth, J.; Wolf, L. IBR-DTN: An efficient implementation for embedded systems. In Proceedings of the Third ACM workshop on Challenged networks (CHANTS’08), San Francisco, CA, USA, 15 September 2008; pp. 117–119. [Google Scholar]
- Raveneau, P.; Rivano, H. Tests Scenario on DTN for IOT III Urbanet Collaboration. [Technical Report] RT-0465, Inria—Research Centre Grenoble—Rhône-Alpes. INRIA, 2015. Available online: https://hal.inria.fr/hal-01187114 (accessed on 2 January 2019).
- von Zengen, G.; Büsching, F.; Pöttner, W.B.; Wolf, L. An overview of µDTN: Unifying DTNs and WSNs. In Proceedings of the 11th GI/ITG KuVS Fachgespräch Drahtlose Sensornetze (FGSN), Darmstadt, Germany, 13–14 September 2012. [Google Scholar]
- Xu, Y.; Mahendran, V.; Radhakrishnan, S. Internet of Hybrid Opportunistic Things: A novel framework for interconnecting IoTs and DTNs. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 1067–1068. [Google Scholar]
- Benhamida, F.Z.; Bouabdellah, A.; Challal, Y. Using delay tolerant network for the Internet of Things: Opportunities and challenges. In Proceedings of the 8th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 4–6 April 2017; pp. 252–257. [Google Scholar]
- Gao, W.; Li, Q.; Zhao, B.; Cao, G. Multicasting in delay tolerant networks: A social network perspective. In Proceedings of the Tenth ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc’09), New Orleans, LA, USA, 18–21 May 2009; pp. 299–308. [Google Scholar]
- Gao, W.; Li, Q.; Zhao, B.; Cao, G. Social-aware multicast in disruption-tolerant networks. IEEE/ACM Trans. Netw. 2012, 20, 1553–1566. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, J.; Yang, W.S. Cloud-based multicasting with feedback in mobile social networks. IEEE Trans. Wirel. Commun. 2013, 12, 6043–6053. [Google Scholar] [CrossRef]
- Le, T.; Kalantarian, H.; Gerla, M. A two-level multicast routing strategy for delay tolerant networks. In Proceedings of the 14th Annual Mediterranean Ad Hoc Networking Workshop (MED-HOC-NET 2015), Vilamoura, Portugal, 17–18 June 2015; pp. 1–7. [Google Scholar]
- Deng, X.; Chang, L. A Multicast Routing Scheme Based on Social Differences in Delay-Tolerant Networks. In Proceedings of the Fourth International Conference on Emerging Intelligent Data and Web Technologies, Xi’an, China, 9–11 September 2013; pp. 501–507. [Google Scholar]
- Hajiaghajani, F.; Biswas, S. Learning based gain-aware content dissemination in delay tolerant networks. In Proceedings of the 9th International Conference on Communication Systems and Networks (COMSNETS 2017), Bangalore, India, 4–8 January 2017; pp. 198–205. [Google Scholar]
- Galluccio, L.; Lorenzo, B.; Glisic, S. Sociality-aided new adaptive infection recovery schemes for multicast DTNs. IEEE Trans. Veh. Technol. 2016, 65, 3360–3376. [Google Scholar] [CrossRef]
- Chen, X.; Shang, C.; Wong, B.; Li, W.; Oh, S. Efficient multicast algorithms in opportunistic mobile social networks using community and social features. Comput. Netw. 2016, 111, 71–81. [Google Scholar] [CrossRef]
- Keykhaie, S.; Rostaei, M. Congestion- and selfishness-aware social routing in delay tolerant networks. In Proceedings of the 7th International Conference on Computer and Knowledge Engineering (ICCKE 2017), Mashhad, Iran, 26–27 October 2017; pp. 439–444. [Google Scholar]
- Li, Y.; Su, G.; Wu, D.O.; Jin, D.; Su, L.; Zeng, L. The impact of node selfishness on multicasting in delay tolerant networks. IEEE Trans. Veh. Technol. 2011, 60, 2224–2238. [Google Scholar] [CrossRef]
- Deng, X.; Chang, L. Sociality-based buffer management for multicast in DTNs. In Proceedings of the Fourth International Conference on Emerging Intelligent Data and Web Technologies (EIDWT 2013), Xi’an, China, 9–11 September 2013; pp. 508–514. [Google Scholar]
- Deng, X.; Wang, J.; Chang, L. Sociality–based comprehensive buffer management for multicast in DTNs. Int. J. Inf. Commun. Technol. 2013, 7, 263–277. [Google Scholar] [CrossRef]
- Lo, S.C.; Luo, N.W.; Gao, J.S.; Tseng, C.C. Quota-based multicast routing in delay-tolerant networks. Wirel. Pers. Commun. 2014, 74, 1329–1344. [Google Scholar] [CrossRef]
- Lo, S.C.; Liou, W.R. Dynamic quota-based routing in delay-tolerant networks. In Proceedings of the IEEE 75th Vehicular Technology Conference (VTC Spring 2012), Yokohama, Japan, 6–9 May 2012; pp. 1–5. [Google Scholar]
- Begerow, P.; Schellenberg, S.; Seitz, J.; Finke, T.; Schroeder, J. Reliable Multicast in Heterogeneous Mobile Ad-hoc Networks. Electron. Commun. EASST 2013, 56, 1–11. [Google Scholar] [CrossRef]
- Begerow, P.; Krug, S.; Schellenberg, S.; Seitz, J. Buffer Management for Reliable Multicast over Delay Tolerant Networks. In Proceedings of the 10th International Conference on Mobile Ad-hoc and Sensor Networks (MSN 2014), Maui, HI, USA, 19–21 December 2014; pp. 171–178. [Google Scholar]
- Begerow, P.; Krug, S.; Schellenberg, S.; Seitz, J. Robust reliability-aware buffer management for DTN multicast in disaster scenarios. In Proceedings of the 7th International Workshop on Reliable Networks Design and Modeling (RNDM 2015), Munich, Germany, 5–7 October 2015; pp. 274–280. [Google Scholar]
- Krifa, A.; Barakat, C.; Spyropoulos, T. Message Drop and Scheduling in DTNs: Theory and Practice. IEEE Trans. Mob. Comput. 2012, 11, 1470–1483. [Google Scholar] [CrossRef] [Green Version]
- Hsu, Y.F.; Hu, C.L. Enhanced Buffer Management for Data Delivery to Multiple Destinations in Delay Tolerant Networks. IEEE Trans. Veh. Technol. 2016, 65, 8735–8739. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, J. A dynamic multicast tree based routing scheme without replication in delay tolerant networks. J. Parallel Distrib. Comput. 2012, 72, 424–436. [Google Scholar] [CrossRef]
- Tripathi, A. Space Optimized Multicast in Delay Tolerant Networks. Int. J. Comput. Netw. Technol. 2013, 1, 139–149. [Google Scholar] [CrossRef]
- Wu, J.; Wang, Y. A non-replication multicasting scheme in delay tolerant networks. In Proceedings of the 7th IEEE International Conference on Mobile Ad-hoc and Sensor Systems (IEEE MASS 2010), San Francisco, CA, USA, 8–12 November 2010; pp. 89–98. [Google Scholar]
- Ezife, F.; Li, W.; Yang, S. A Survey of Buffer Management Strategies in Delay Tolerant Networks. In Proceedings of the IEEE 14th International Conference on Mobile Ad Hoc and Sensor Systems (MASS 2017), Orlando, FL, USA, 22–25 October 2017; pp. 599–603. [Google Scholar]
- Söderman, P.; Grinnemo, K.J.; Hidell, M.; Sjödin, P. Mind the smartgap: A buffer management algorithm for delay tolerant wireless sensor networks. In Proceedings of the 12th European Conference on Wireless Sensor Networks (EWSN 2015), Porto, Portugal, 9–11 Febuary 2015; pp. 104–119. [Google Scholar]
- Bardi, M.; Guo, W.; Xie, P. Research on multicast routing for deep space networks based on DTN. In Proceedings of the International Conference on Cyberspace Technology (CCT 2014), Beijing, China, 8–10 November 2014; pp. 1–5. [Google Scholar]
- Lindgren, A.; Doria, A.; Schelén, O. Probabilistic routing in intermittently connected networks. In Service Assurance with Partial and Intermittent Resources, Proceedings of the First International Workshop on SAPIR 2004, Fortaleza, Brazil, 1–6 August 2004; Dini, P., Lorenz, P., de Souza, J.N., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 239–254. ISBN 978-3-540-22567-6. [Google Scholar]
- Roy, A.; Acharya, T.; Dasbit, S. Energy-aware social-based multicast in delay-tolerant networks. In Proceedings of the IEEE 81st Vehicular Technology Conference (VTC Spring 2015), Glasgow, UK, 11–14 May 2015; pp. 1–5. [Google Scholar]
- Roy, A.; Bose, S.; Acharya, T.; DasBit, S. Social-based energy-aware multicasting in delay tolerant networks. J. Netw. Comput. Appl. 2017, 87, 169–184. [Google Scholar] [CrossRef]
- Bhattacharjee, S.; Roy, S.; DasBit, S. DPDRM: A decentralized post-disaster resource management scheme using energy efficient smart phone based DTN. J. Netw. Comput. Appl. 2018, 111, 1–16. [Google Scholar] [CrossRef]
- Eshghi, S.; Khouzani, M.H.R.; Sarkar, S.; Shroff, N.B.; Venkatesh, S.S. Optimal energy-aware epidemic routing in DTNs. IEEE Trans. Autom. Control 2015, 60, 1554–1569. [Google Scholar] [CrossRef]
- Ababou, M.; Bellafkih, M.; El kouch, R. Energy Efficient Routing Protocol for Delay Tolerant Network Based on Fuzzy Logic and Ant Colony. Int. J. Intell. Syst. Appl. 2018, 10, 69–77. [Google Scholar] [CrossRef] [Green Version]
- Lu, Y.; Wang, W.; Chen, L.; Zhang, Z.; Huang, A. Distance-based energy-efficient opportunistic broadcast forwarding in mobile delay-tolerant networks. IEEE Trans. Veh. Technol. 2016, 65, 5512–5524. [Google Scholar] [CrossRef]
- Kang, M.W.; Chung, Y.W. A novel energy-aware routing protocol in intermittently connected delay-tolerant wireless sensor networks. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Stamatakis, G.; Tragos, E.Z.; Traganitis, A. Energy efficient policies for data transmission in disruption tolerant heterogeneous IoT networks. Sensors 2018, 18, 2891. [Google Scholar] [CrossRef] [PubMed]
- Yang, P.; Chuah, M. Efficient interdomain multicast delivery in disruption tolerant networks. In Proceedings of the 4th International Conference on Mobile Ad-hoc and Sensor Networks (MSN 2008), Wuhan, China, 10–12 December 2008; pp. 81–88. [Google Scholar]
- Palma, A.; Pereira, P.R.; Casaca, A. Multicast routing protocol for vehicular delay-tolerant networks. In Proceedings of the IEEE 8th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob 2012), Barcelona, Spain, 8–10 October 2012; pp. 753–760. [Google Scholar]
- Stojmenović, I. Position-based routing in ad hoc networks. IEEE Commun. Mag. 2002, 40, 128–134. [Google Scholar] [CrossRef] [Green Version]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and Wait: An Efficient Routing Scheme for Intermittently Connected Mobile Networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-tolerant Networking (WDTN’05), Philadelphia, PA, USA, 26 August 2005; ACM: New York, NY, USA, 2005; pp. 252–259. [Google Scholar]
- Liao, Q.; Zhang, J. Geographic Routing Based on Social Dynamic Features Aware in Vehicle Social Network. In Proceedings of the 15th International Symposium on Wireless Communication Systems (ISWCS 2018), Lisbon, Portugal, 28–31 August 2018; pp. 1–6. [Google Scholar]
- Gupta, A.K.; Mandal, J.K.; Bhattacharya, I.; Mondal, T.; Shaw, S.S. CTMR-collaborative time-stamp based multicast routing for delay tolerant networks in post disaster scenario. Peer-to-Peer Netw. Appl. 2016, 11, 162–180. [Google Scholar] [CrossRef]
- Zhao, W.; Ammar, M.; Zegura, E. A message ferrying approach for data delivery in sparse mobile ad hoc networks. In Proceedings of the 5th ACM international symposium on Mobile ad hoc networking and computing (MobiHoc’04), Tokyo, Japan, 24–26 May 2004; pp. 187–198. [Google Scholar]
- Zhao, W.; Ammar, M.; Zegura, E. Controlling the mobility of multiple data transport ferries in a delay tolerant network. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; pp. 1407–1418. [Google Scholar]
- Harras, K.A.; Almeroth, K.C. Inter-regional messenger scheduling in delay tolerant mobile networks. In Proceedings of the International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM’06), Buffalo-Niagara Falls, NY, USA, 26–29 June 2006; pp. 93–102. [Google Scholar]
- Giannini, C.; Shaaban, A.A.; Buratti, C.; Verdone, R. Delay Tolerant Networking for smart city through drones. In Proceedings of the International Symposium on Wireless Communication Systems (ISWCS 2016), Poznan, Poland, 20–23 September 2016; pp. 603–607. [Google Scholar]
- Bujari, A.; Calafate, C.T.; Cano, J.C.; Manzoni, P.; Palazzi, C.E.; Ronzani, D. A Location-Aware Waypoint-Based Routing Protocol for Airborne DTNs in Search and Rescue Scenarios. Sensors 2018, 18, 3758. [Google Scholar] [CrossRef] [PubMed]
- Asuquo, P.; Cruickshank, H.; Ogah, C.P.A.; Lei, A.; Sun, Z. A Distributed Trust Management Scheme for Data Forwarding in Satellite DTN Emergency Communications. IEEE J. Sel. Areas Commun. 2018, 36, 246–256. [Google Scholar] [CrossRef] [Green Version]
- Mao, Y.; Zhu, P. A game theoretical model for energy-aware DTN routing in MANETs with nodes’ selfishness. Mob. Netw. Appl. 2015, 20, 593–603. [Google Scholar] [CrossRef]
- Bindra, H.S.; Sangal, A.L. Considerations and Open Issues in Delay Tolerant Network’S (DTNs) Security. Wirel. Sens. Netw. 2010, 2, 645–648. [Google Scholar] [CrossRef]
- Harney, H.; Harder, E. Logical Key Hierarchy Protocol. Internet-Draft Draft-Harney-Sparta-Lkhp-Sec-00. Internet Engineering Task Force, March 1999. Available online: https://tools.ietf.org/html/draft-harney-sparta-lkhp-sec-00 (accessed on 2 January 2019).
- Xu, G.; Chen, X.; Du, X. Chinese remainder theorem based DTN group key management. In Proceedings of the IEEE 14th International Conference on Communication Technology, Chengdu, China, 9–11 November 2012; pp. 779–783. [Google Scholar]
- Gupta, M. Group Key Exchange Management in Delay Tolerant Network. Int. J. Comput. Appl. 2016, 144, 16–19. [Google Scholar] [CrossRef]
- Menesidou, S.A.; Katos, V.; Kambourakis, G. Cryptographic key management in delay tolerant networks: A survey. Future Internet 2017, 9, 26. [Google Scholar] [CrossRef]
- Li, Q.; Zhu, S.; Cao, G. Routing in Socially Selfish Delay Tolerant Networks. In Proceedings of the 30th IEEE International Conference on Computer Communications (INFOCOM 2010), San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Wu, G.; Wang, J.; Yao, L.; Lin, C. A Secure Social-Aware Incentive Scheme for Delay Tolerant Networks. In Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 813–820. [Google Scholar]
- Li, Y.; Jin, D.; Su, L.; Zeng, L. Performance evaluation of routing schemes for the energy-constrained DTN with selfish nodes. IEICE Trans. Commun. 2011, E94-B, 1442–1446. [Google Scholar] [CrossRef]
- Singh, A.V.; Juyal, V.; Saggar, R. Trust based Intelligent Routing Algorithm for Delay Tolerant Network using Artificial Neural Network. Wirel. Netw. 2017, 23, 693–702. [Google Scholar] [CrossRef]
- Monticelli, E.; Arumaithurai, M.; Psaras, I.; Fu, X.; Ramakrishnan, K.K. Combining Opportunistic and Information Centric Networks in Real World Applications. Available online: https://pdfs.semanticscholar.org/4b92/b74326d06c089438802ed0e56624a798dc54.pdf (accessed on 2 January 2019).
- Gao, L.; Luan, T.H.; Yu, S.; Zhou, W.; Liu, B. FogRoute: DTN-Based Data Dissemination Model in Fog Computing. IEEE Internet Things J. 2017, 4, 225–235. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).