Model-Based Systems Engineering Cybersecurity for Space Systems
Abstract
:1. Introduction
2. Materials and Methods
- Attacks on satellite control systems or mission packages to shut them down in orbit;
- Targeting ground infrastructure, such as data centers and control centers;
- Spoofing and hacking attacks on communication networks used by space segments;
- Terrestrial jamming of receivers in specific geographic regions or orbital jamming of a signal sent from a ground station to a satellite [10].
3. Results
3.1. Space Cybersecurity Standardization
3.1.1. United States Space Cybersecurity Standards
3.1.2. European Space Cybersecurity Standards
3.1.3. Industry Cybersecurity Standards
3.2. General Cybersecurity Standardization
3.2.1. NIST SP 800-160 Volume 2
- System focuses on mission functions and on the effects of a persistent threat;
- Assumption of a changing environment;
- Assumption that the adversary will compromise or breach the system or organization and maintain a presence [22].
3.2.2. NIST SP 800-160 Volume 1
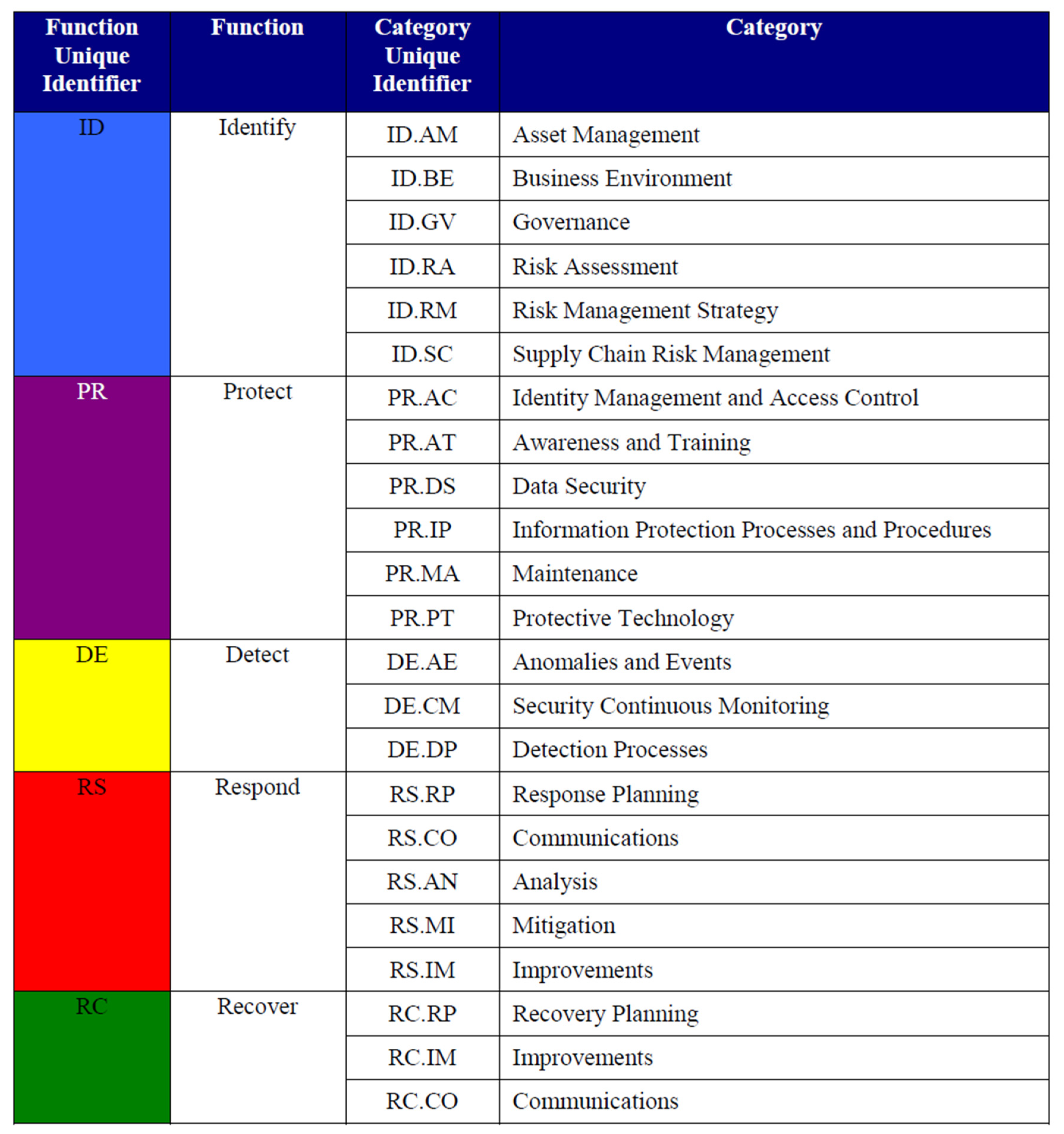
3.2.3. NIST Framework for Improving Critical Infrastructure Cybersecurity
3.2.4. NIST SP 800-161r1
3.3. Modeling Key Takeaways from Cyber Resiliency Standards
4. Discussion
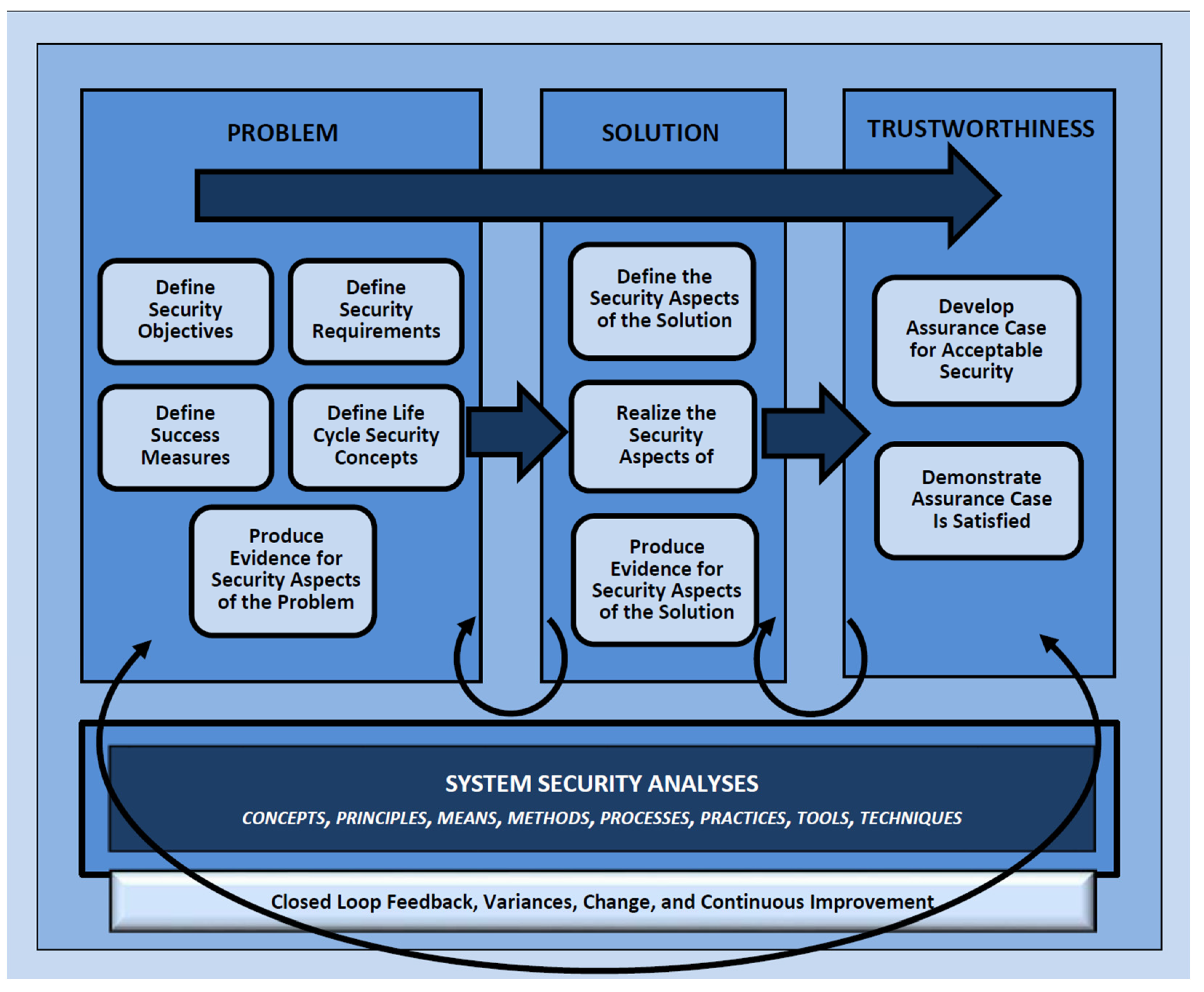
4.1. Integrating Cybersecurity Requirements into MBSE
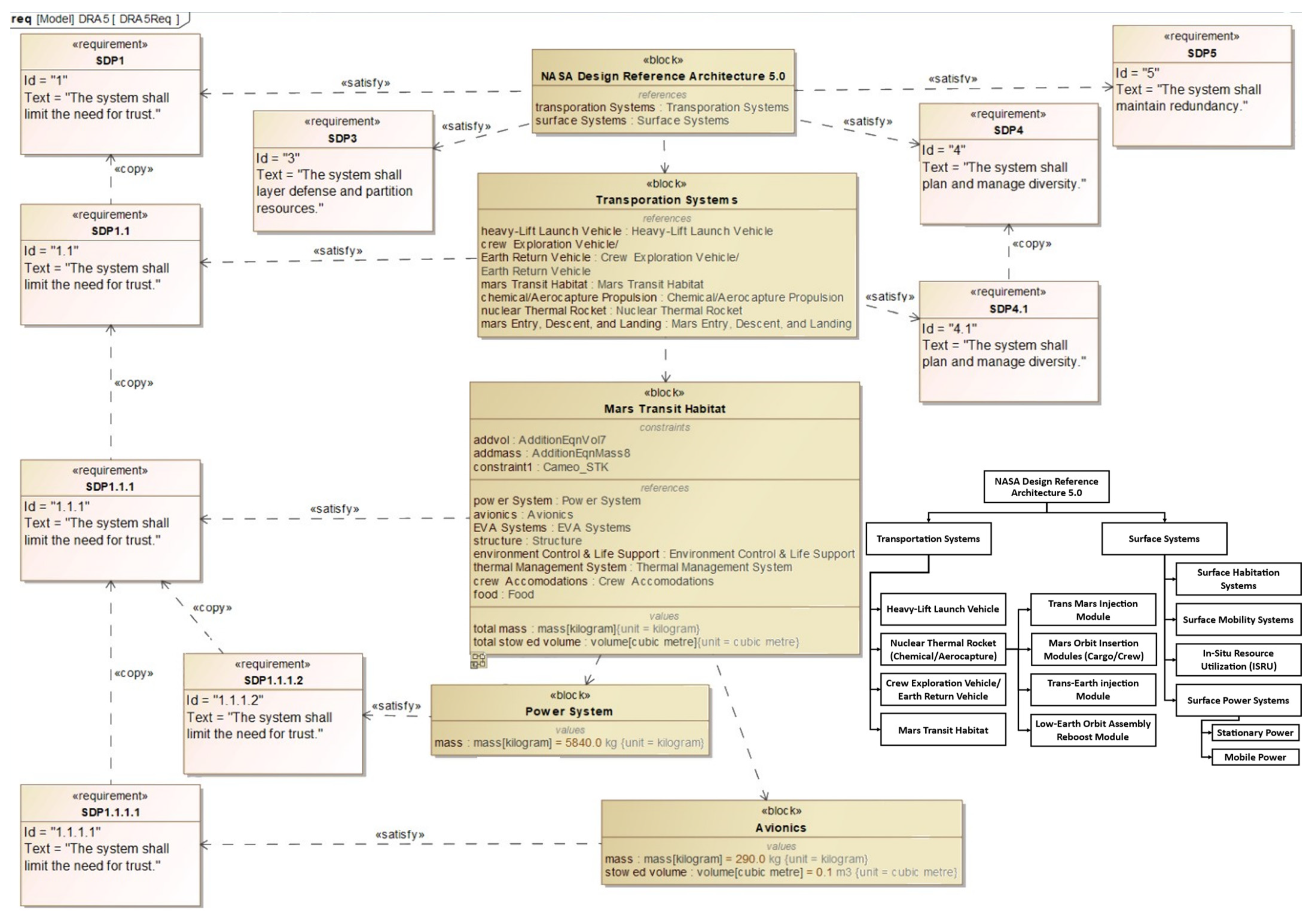
4.2. Use Case: Crewed Mars Mission Planning Cybersecurity
4.3. Quantifying MBSE Benefit Metrics for Cybersecure Space System Design and Development
5. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Henderson, K.; Salado, A. Value and benefits of model-based systems engineering (MBSE): Evidence from the literature. Syst. Eng. 2021, 24, 51–66. [Google Scholar] [CrossRef]
- Friedenthal, S.; Oster, C. Chapter 4: Applying SysML and a Model-Based Systems Engineering Approach to a Small Satellite Design. In Advances in Systems Engineering; American Institute of Aeronautics and Astronautics, Inc.: Reston, VA, USA, 2016; pp. 127–218. [Google Scholar] [CrossRef]
- Modeling to Mars: A NASA Model Based Systems Engineering Pathfinder Effort | AIAA SPACE Forum. Available online: https://arc.aiaa.org/doi/abs/10.2514/6.2017-5235 (accessed on 24 February 2021).
- Pavalkis, S. MBSE in Real-Life Space Exploration Projects. Modeling Community Blog, 15 July 2015. Available online: https://blog.nomagic.com/mbse-real-life-space-exploration-projects/ (accessed on 4 November 2020).
- Wang, L.; Izygon, M.; Okon, S.; Wagner, H.; Garner, L. Effort to Accelerate MBSE Adoption and Usage at JSC. In Proceedings of the AIAA SPACE 2016, Long Beach, CA, USA, 13–16 September 2016. [Google Scholar] [CrossRef] [Green Version]
- Klesh, A.T.; Cutler, J.W.; Atkins, E.M. Cyber-Physical Challenges for Space Systems. In Proceedings of the 2012 IEEE/ACM Third International Conference on Cyber-Physical Systems, Beijing, China, 17–19 April 2012; pp. 45–52. [Google Scholar] [CrossRef] [Green Version]
- Falco, G. The Vacuum of Space Cyber Security. In Proceedings of the 2018 AIAA SPACE and Astronautics Forum and Exposition, Orlando, FL, USA, 17–19 September 2018. [Google Scholar] [CrossRef]
- Suloway, T.; Visner, S.S.; Kordella, S. A Cyber Attack-Centric View of Commercial Space Vehicles and the Steps Needed to Mitigate, November 2020. Available online: https://www.mitre.org/publications/technical-papers/a-cyber-attack-centric-view-of-commercial-space-vehicles (accessed on 8 June 2021).
- Manulis, M.; Bridges, C.P.; Harrison, R.; Sekar, V.; Davis, A. Cyber security in New Space. Int. J. Inf. Secur. 2021, 20, 287–311. [Google Scholar] [CrossRef]
- Space, the Final Frontier for Cybersecurity? Chatham House—International Affairs Think Tank, 22 September 2016. Available online: https://www.chathamhouse.org/2016/09/space-final-frontier-cybersecurity (accessed on 1 November 2021).
- Job One for Space Force: Space Asset Cybersecurity. Belfer Center for Science and International Affairs. Available online: https://www.belfercenter.org/publication/job-one-space-force-space-asset-cybersecurity (accessed on 1 November 2021).
- Erwin, S. Space Force Rolls out Cybersecurity Standards for Commercial Providers of Satellite Services. SpaceNews, 26 May 2022. Available online: https://spacenews.com/space-force-rolls-out-cybersecurity-standards-for-commercial-providers-of-satellite-services/ (accessed on 18 September 2022).
- United States Space Force. USSF Commercial SATCOM Office Announces Development of New Security Program. Available online: https://www.spaceforce.mil/News/Article/2230831/ussf-commercial-satcom-office-announces-development-of-new-security-program/https%3A%2F%2Fwww.spaceforce.mil%2FNews%2FArticle%2F2230831%2Fussf-commercial-satcom-office-announces-development-of-new-security-program%2F (accessed on 18 September 2022).
- Federal Office for Information Security. Cyber Security for Air and Space Applications. Available online: https://www.bsi.bund.de/EN/Themen/Unternehmen-und-Organisationen/Informationen-und-Empfehlungen/IT-Sicherheit-in-Luft-und-Raumfahrt/it-sicherheit-in-luft-und-raumfahrt.html?nn=916896 (accessed on 30 November 2022).
- ESA ESEC. Available online: https://www.esa.int/About_Us/Corporate_news/ESA_ESEC (accessed on 30 November 2022).
- ESA Practices Cybersecurity. Available online: https://www.esa.int/Space_Safety/ESA_practices_cybersecurity (accessed on 30 November 2022).
- Space19+—Road to ESA’s Council at Ministerial Level. Available online: https://blogs.esa.int/space19plus/ (accessed on 30 November 2022).
- UNODA. Report of the Secretary-General on Reducing Space Threats through Norms, Rules and Principles of Responsible Behaviors. 2021. Available online: https://www.un.org/disarmament/topics/outerspace-sg-report-outer-space-2021/ (accessed on 30 November 2022).
- Indico. Open-Ended Working Group on Reducing Space Threats through Norms, Rules and Principles of Responsible Behaviours, Second Session. Available online: https://indico.un.org/event/1001999/ (accessed on 30 November 2022).
- Aerospace Corporation. SSI: Cybersecurity Implementation | The Aerospace Corporation. Available online: https://aerospace.org/ssi-cybersecurity-implementation (accessed on 30 November 2022).
- Space ISAC. About Us. Available online: https://s-isac.org/about-us/ (accessed on 30 November 2022).
- Ross, R.; Pillitteri, V.; Graubart, R.; Bodeau, D.; McQuaid, R. Developing Cyber-Resilient Systems: A Systems Security Engineering Approach. SP 800-160 Vol. 2 Rev. 1. Available online: https://csrc.nist.gov/publications/detail/sp/800-160/vol-2-rev-1/final (accessed on 18 September 2022).
- Ross, R.; McEvilley, M.; Oren, J. Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems; NIST Special Publication (SP) 800-160; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018; Volume 1. [Google Scholar] [CrossRef]
- Barrett, M.P. Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. NIST, April 2018. Available online: https://www.nist.gov/publications/framework-improving-critical-infrastructure-cybersecurity-version-11 (accessed on 18 September 2022).
- Critical Infrastructure Sectors | CISA. Available online: https://www.cisa.gov/critical-infrastructure-sectors (accessed on 4 November 2020).
- Boyens, J.; Smith, A.; Bartol, N.; Winkler, K.; Holbrook, A.; Fallon, M. Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations; NIST Special Publication (SP) 800-161 Rev. 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2022. [Google Scholar] [CrossRef]
- Mažeika, D.; Butleris, R. Integrating security requirements engineering into MBSE: Profile and guidelines. Secur. Commun. Netw. 2020, 2020, 5137625. [Google Scholar] [CrossRef] [Green Version]
- Kirshner, M.; Valerdi, R. Integrating Model-Based Systems and Digital Engineering for Crewed Mars Mission Planning. J. Aerosp. Inf. Syst. 2022, 19, 668–676. Available online: https://arc.aiaa.org/doi/10.2514/1.I010986 (accessed on 3 October 2021). [CrossRef]
- Friedenthal, S.; Moore, A.; Steiner, R. A Practical Guide to SysML: The Systems Modeling Language, 3rd ed.; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 2014. [Google Scholar]
- Biria, A. Analytical Approach to the Design of Optimal Satellite Constellations for Space-Based Space Situational Awareness Applications. Ph.D. Thesis, University of Texas at Austin, Austin, TX, USA.
- Maurandy, J.; Helm, A.; Gill, E.; Stalford, R. 11.5.3 Cost-Benefit Analysis of SysML Modelling for the Atomic Clock Ensemble in Space (ACES) Simulator. INCOSE Int. Symp. 2012, 22, 1726–1745. [Google Scholar] [CrossRef]
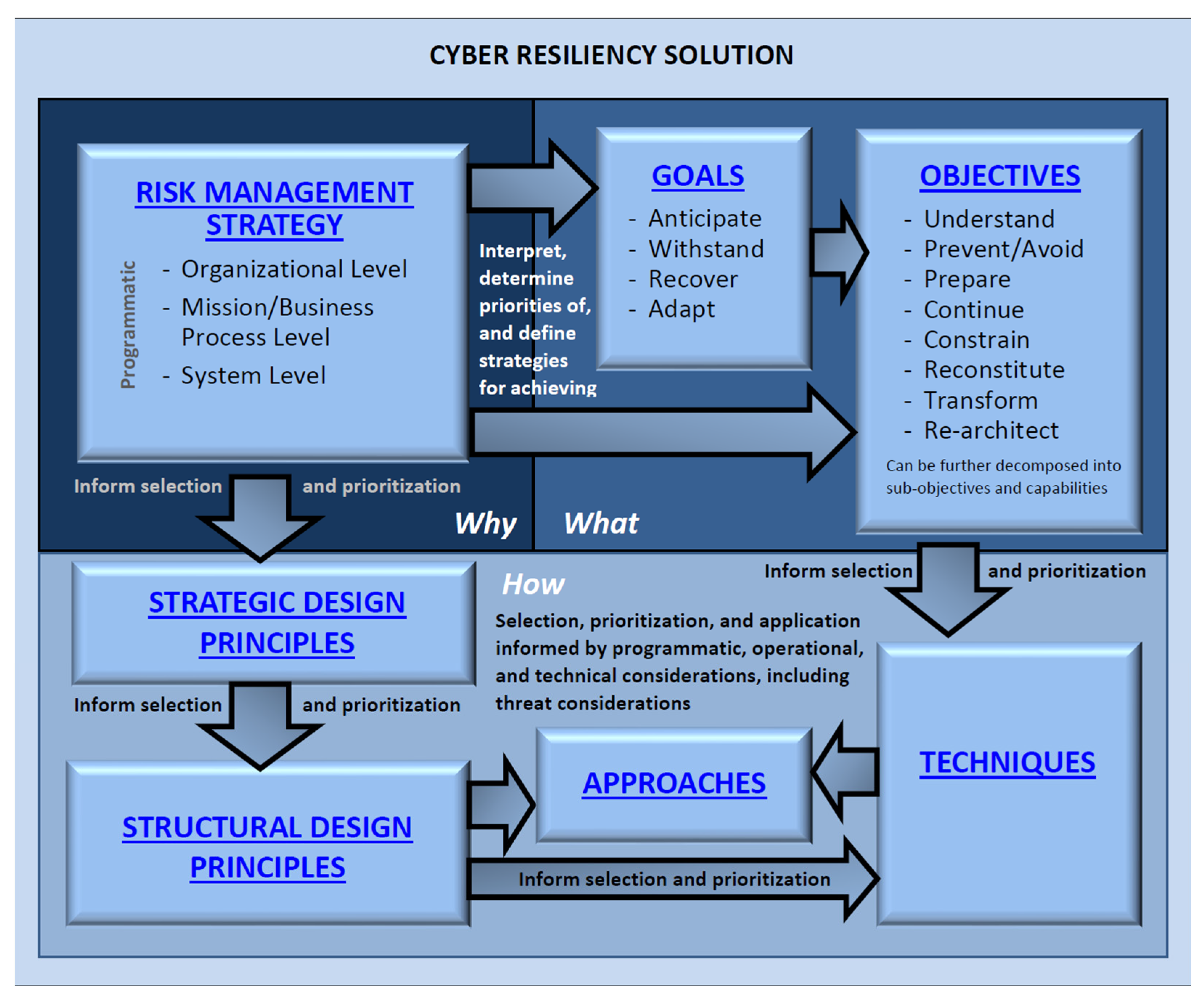
| Goals Traced to Objectives | Anticipate | Withstand | Recover | Adapt |
|---|---|---|---|---|
| Prevent/Avoid | X | X | ||
| Prepare | X | X | X | X |
| Continue | X | X | ||
| Constrain | X | X | ||
| Reconstitute | X | |||
| Understand | X | X | X | X |
| Transform | X | X | ||
| Rearchitect | X | X |
| Strategic Design Principles Traced to Objectives | Focus on Common Critical Assets | Support Agility and Architect for Adaptability | Reduce Attack Surfaces | Assume Compromised Resources | Expect Adversaries to Evolve |
|---|---|---|---|---|---|
| Prevent/Avoid | X | X | |||
| Prepare | X | X | X | ||
| Continue | X | X | X | ||
| Constrain | X | X | |||
| Reconstitute | X | X | X | ||
| Understand | X | X | X | X | |
| Transform | X | X | X | X | |
| Rearchitect | X | X | X | X | X |
| Objectives Traced to Techniques/Approaches | Prevent/Avoid | Prepare | Continue | Constrain | Reconstitute | Understand | Transform | Rearchitect |
|---|---|---|---|---|---|---|---|---|
| ADAPTIVE RESPONSE | X | X | X | X | X | X | ||
| Dynamic Reconfiguration | X | X | X | X | X | |||
| Dynamic Resource Allocation | X | X | X | X | ||||
| Adaptive Management | X | X | X | X | X | X | ||
| ANALYTIC MONITORING | X | X | X | X | ||||
| Monitoring and Damage Assessment | X | X | X | X | ||||
| Sensor Fusion and Analysis | X | |||||||
| Forensic and Behavioral Analysis | X | |||||||
| CONTEXTUAL AWARENESS | X | X | X | X | ||||
| Dynamic Resource Awareness | X | X | ||||||
| Dynamic Threat Awareness | X | |||||||
| Mission Dependency and Status Visualization | X | X | X | X | ||||
| COORDINATED PROTECTION | X | X | X | X | X | X | X | |
| Calibrated Defense-in-Depth | X | X | X | |||||
| Consistency Analysis | X | X | X | X | X | X | ||
| Orchestration | X | X | X | X | X | X | X | |
| Self-Challenge | X | X | ||||||
| DECEPTION | X | X | ||||||
| Obfuscation | X | |||||||
| Disinformation | X | |||||||
| Misdirection | X | X | ||||||
| Tainting | X | |||||||
| DIVERSITY | X | X | X | X | X | |||
| Architectural Diversity | X | X | X | |||||
| Design Diversity | X | X | X | |||||
| Synthetic Diversity | X | X | X | X | ||||
| Information Diversity | X | X | X | |||||
| Path Diversity | X | X | X | |||||
| Supply Chain Diversity | X | X | X | |||||
| DYNAMIC POSITIONING | X | X | X | X | X | |||
| Functional Relocation of Sensors | X | X | ||||||
| Functional Relocation of Cyber Resources | X | X | X | |||||
| Asset Mobility | X | X | X | |||||
| Fragmentation | X | X | ||||||
| Distributed Functionality | X | X | ||||||
| NONPERSISTENCE | X | X | X | X | ||||
| Nonpersistent Information | X | X | X | X | ||||
| Nonpersistent Services | X | X | X | X | ||||
| Nonpersistent Connectivity | X | X | X | X | ||||
| PRIVILEGE RESTRICTION | X | X | X | |||||
| Trust-Based Privilege Management | X | X | ||||||
| Attribute-Based Usage Restriction | X | X | ||||||
| Dynamic Privileges | X | X | X | |||||
| REALIGNMENT | X | X | X | |||||
| Purposing | X | X | ||||||
| Offloading | X | X | ||||||
| Restriction | X | X | ||||||
| Replacement | X | X | ||||||
| Specialization | X | X | ||||||
| Evolvability | X | X | ||||||
| REDUNDANCY | X | X | X | X | X | X | ||
| Protected Backup and Restore | X | X | X | |||||
| Surplus Capacity | X | X | ||||||
| Replication | X | X | X | X | X | |||
| SEGMENTATION | X | X | X | X | ||||
| Predefined Segmentation | X | X | X | X | ||||
| Dynamic Segmentation and Isolation | X | X | X | |||||
| SUBSTANTIATED INTEGRITY | X | X | X | X | ||||
| Integrity Checks | X | X | X | X | ||||
| Provenance Tracking | X | X | X | |||||
| Behavior Validation | X | X | X | X | ||||
| UNPREDICTABILITY | X | X | ||||||
| Temporal Unpredictability | X | X | ||||||
| Contextual Unpredictability | X | X | ||||||
| Integrity Checks | X | X | X | X |
| Structural Design Principle | Associated Technique |
|---|---|
| Limit the Need for Trust | Coordinated Protection, Privilege Restriction, Realignment, Substantiated Integrity |
| Control Visibility and Use | Deception, Nonpersistence, Privilege Restriction, Segmentation |
| Layer Defense and Partition Resources | Analytic Monitoring, Coordinated Protection, Diversity, Dynamic Positioning, Redundancy, Segmentation |
| Plan and Manage Diversity | Coordinated Protection, Diversity, Redundancy |
| Maintain Redundancy | Coordinated Protection, Diversity, Realignment, Redundancy |
| Make Resources Location Versatile | Adaptive Response, Diversity, Dynamic Positioning, Nonpersistence, Redundancy, Unpredictability |
| Leverage Health and Status Data | Analytic Monitoring, Contextual Awareness, Substantiated Integrity |
| Maintain Situational Awareness | Analytic Monitoring, Contextual Awareness |
| Manage Resources (Risk) Adaptively | Adaptive Response, Coordinated Protection, Deception, Dynamic Positioning, Nonpersistence, Privilege Restriction, Realignment, Redundancy, Segmentation, Unpredictability |
| Maximize Transience | Analytic Monitoring, Dynamic Positioning, Nonpersistence, Substantiated Integrity, Unpredictability |
| Determine Ongoing Trustworthiness | Coordinated Protection, Substantiated Integrity |
| Change or Disrupt the Attack Surface | Adaptive Response, Deception, Diversity, Dynamic Positioning, Nonpersistence, Unpredictability |
| Make the Effects of Deception and Unpredictability User-Transparent | Adaptive Response, Coordinated Protection, Deception, Unpredictability |
| Structural Design Principle | Related Technique |
| Limit the Need for Trust | Coordinated Protection, Privilege Restriction, Realignment, Substantiated Integrity |
| Control Visibility and Use | Deception, Nonpersistence, Privilege Restriction, Segmentation |
| Layer Defense and Partition Resources | Analytic Monitoring, Coordinated Protection, Diversity, Dynamic Positioning, Redundancy, Segmentation |
| Plan and Manage Diversity | Coordinated Protection, Diversity, Redundancy |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kirshner, M. Model-Based Systems Engineering Cybersecurity for Space Systems. Aerospace 2023, 10, 116. https://doi.org/10.3390/aerospace10020116
Kirshner M. Model-Based Systems Engineering Cybersecurity for Space Systems. Aerospace. 2023; 10(2):116. https://doi.org/10.3390/aerospace10020116
Chicago/Turabian StyleKirshner, Mitchell. 2023. "Model-Based Systems Engineering Cybersecurity for Space Systems" Aerospace 10, no. 2: 116. https://doi.org/10.3390/aerospace10020116
APA StyleKirshner, M. (2023). Model-Based Systems Engineering Cybersecurity for Space Systems. Aerospace, 10(2), 116. https://doi.org/10.3390/aerospace10020116









