Analysis and Control of Malware Mutation Model in Wireless Rechargeable Sensor Network with Charging Delay
Abstract
:1. Introduction
- 1.
- For existing mutation models, the WSN has an energy constraint. As a solution, charging needs to be completed within a certain period of time. To address this problem, the mutation model with charging delay is proposed to analyse the process of spreading malware. The effect of charging delay on mutation model is also analyzed.
- 2.
- Through the analysis of the mutation model with charging delay, two different basic reproductive numbers, and , are obtained. Then, the locally asymptotically stability is proven. Moreover, the bifurcation phenomenon and periodic oscillation of the mutation model are analyzed.
- 3.
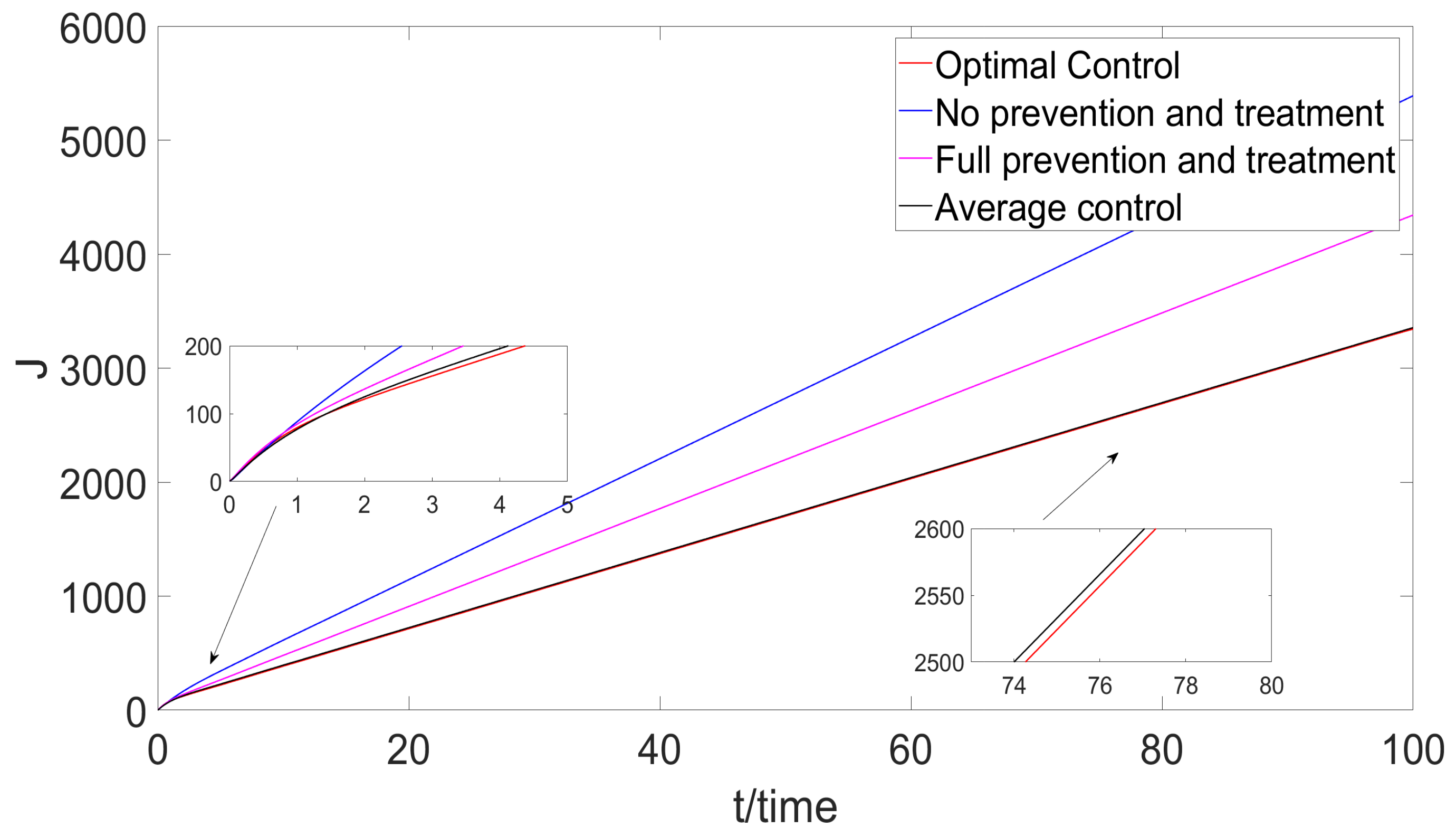
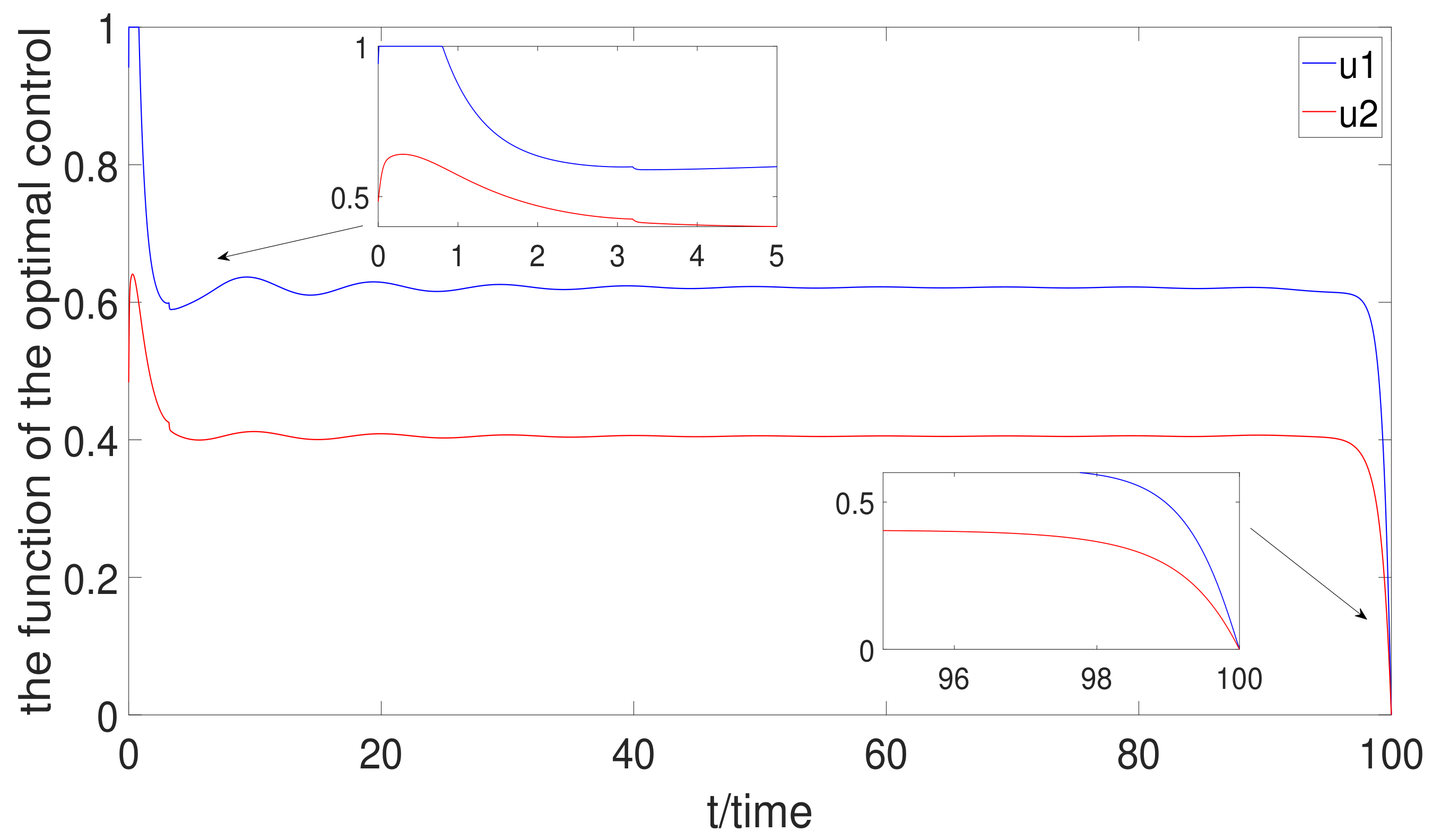
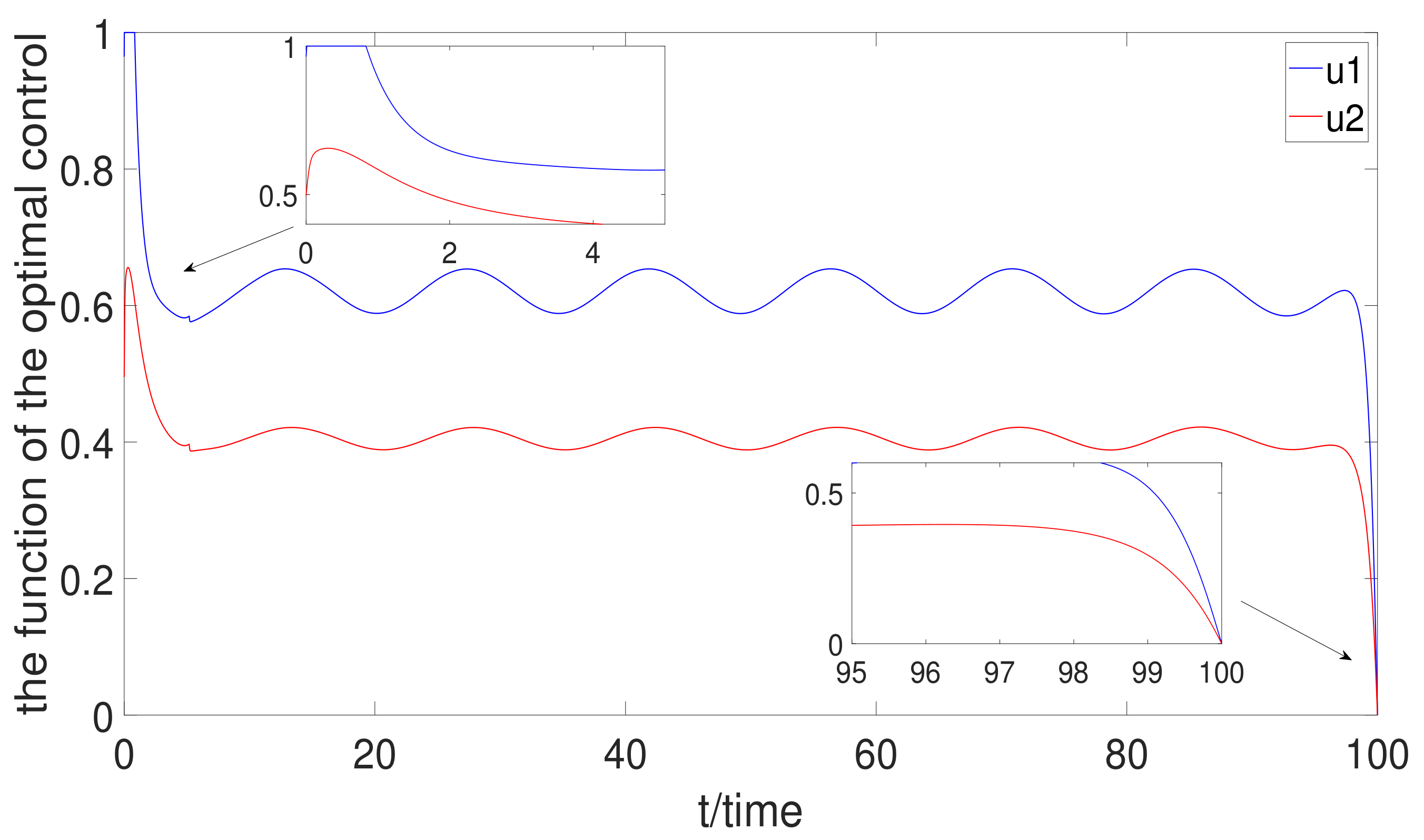
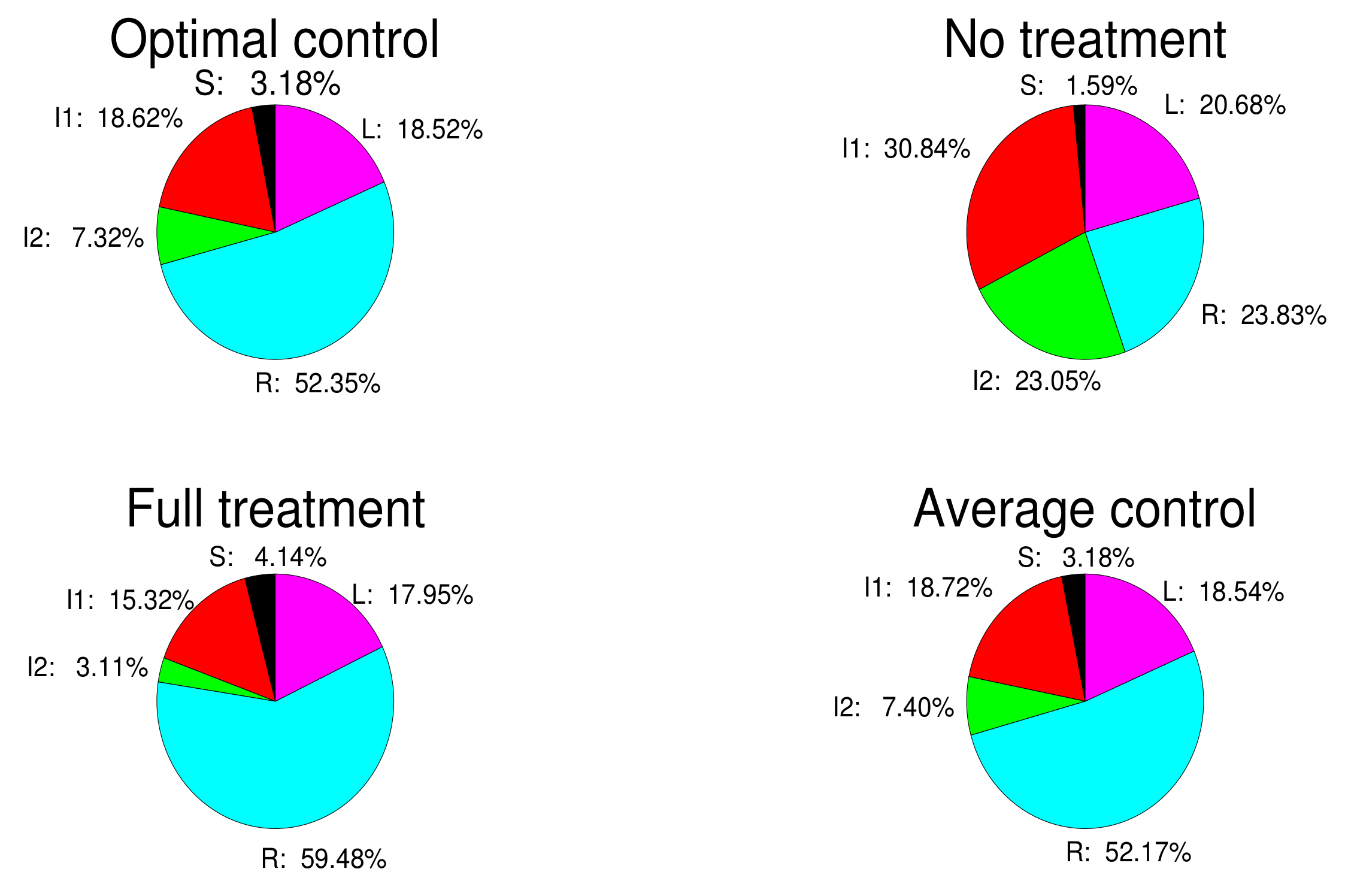
- Based on the mutation model with charging delay, the optimal charging delay control strategy is discussed. According to the Pontryagin’s Maximun Principle, the optimal variable can be derived. It is found that the charging delay has great influence on optimal control. Meanwhile, no treatment control, average control, and full treatment are also analyzed. By comparison with the three control methods, the optimal control is the best control method of them.
2. Modeling
3. Local Stability and Existence of Hopf Bifurcation
4. Direction and Stability of the Hopf Bifurcation
5. Optimal Strategy
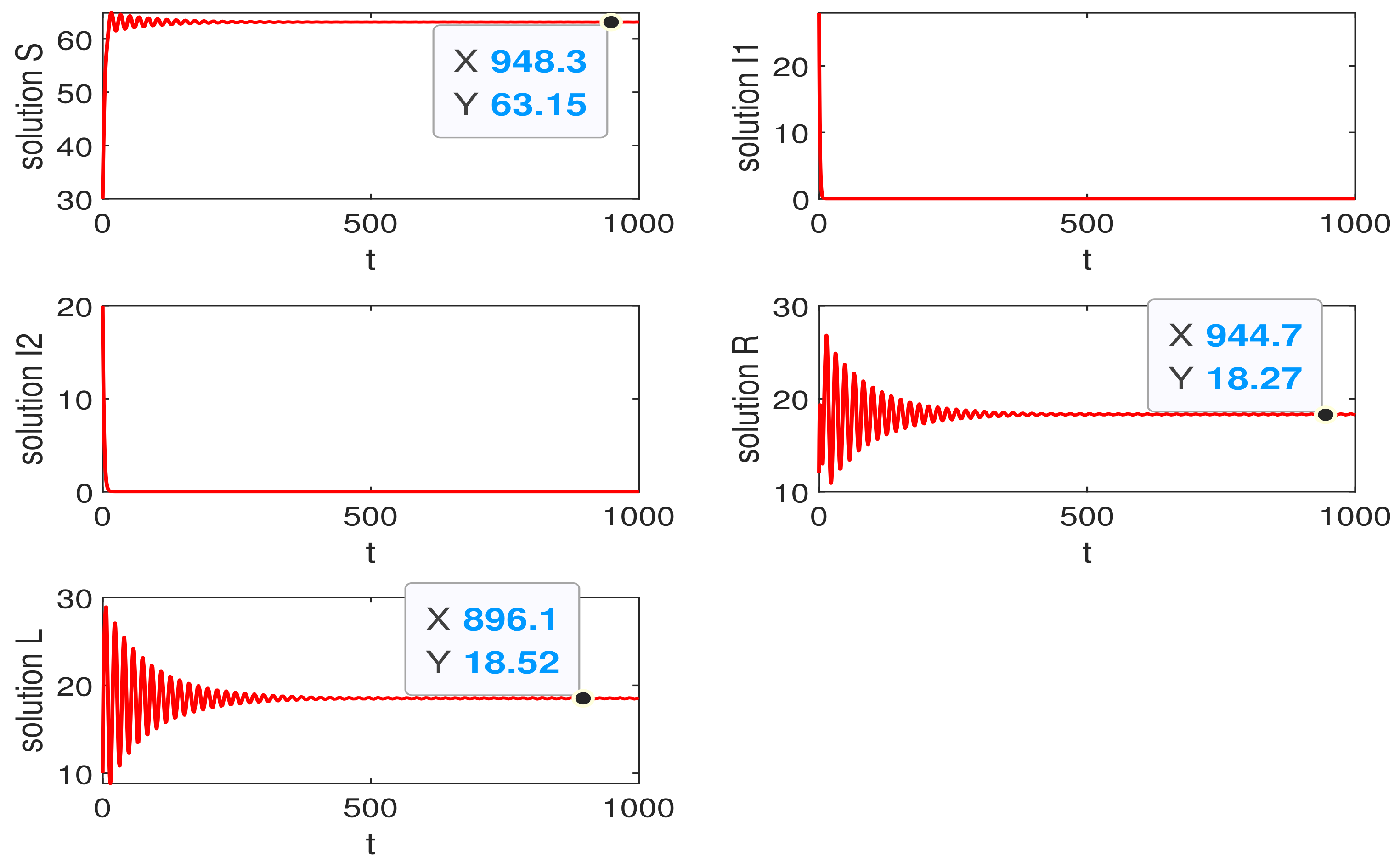
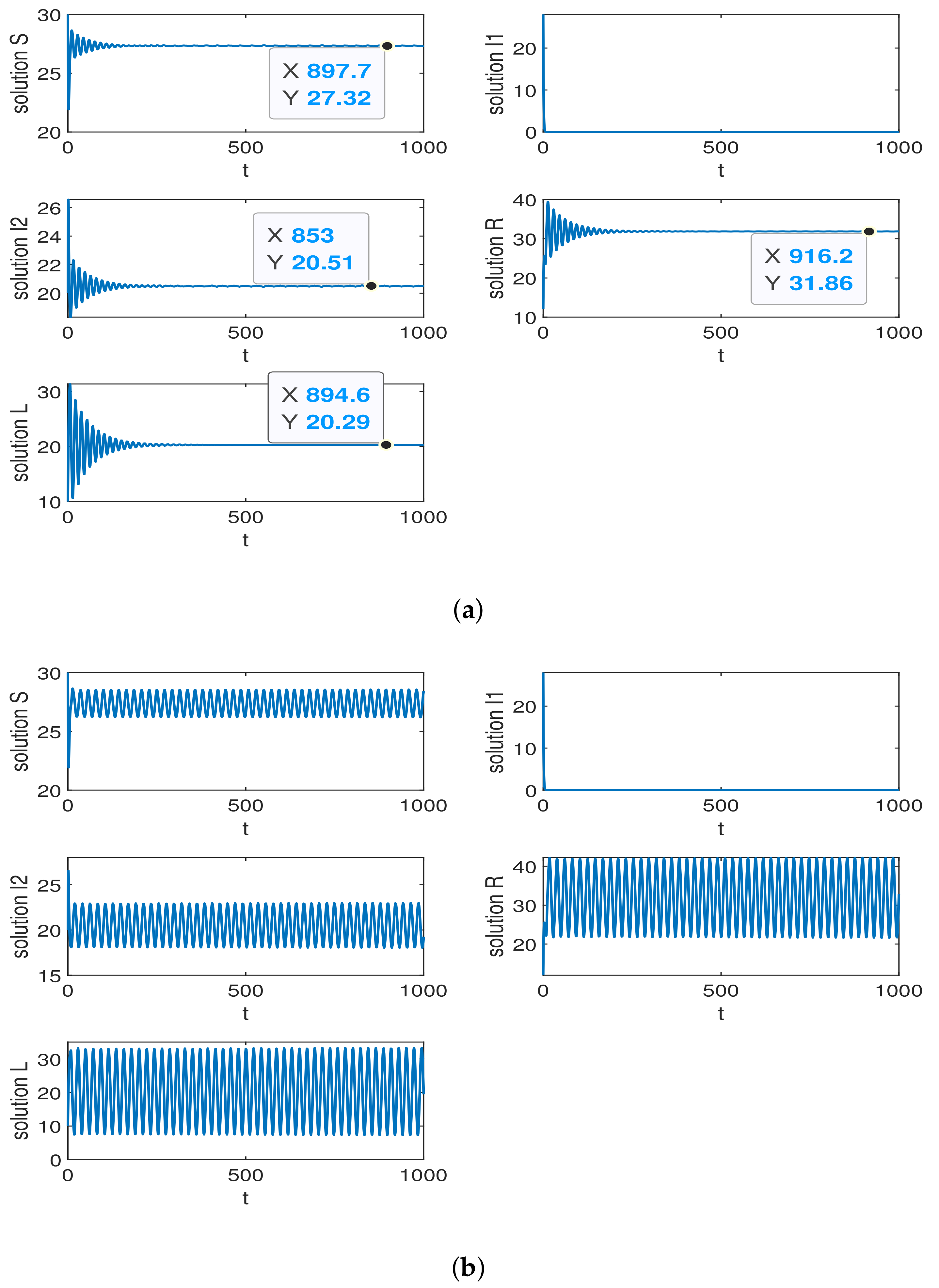
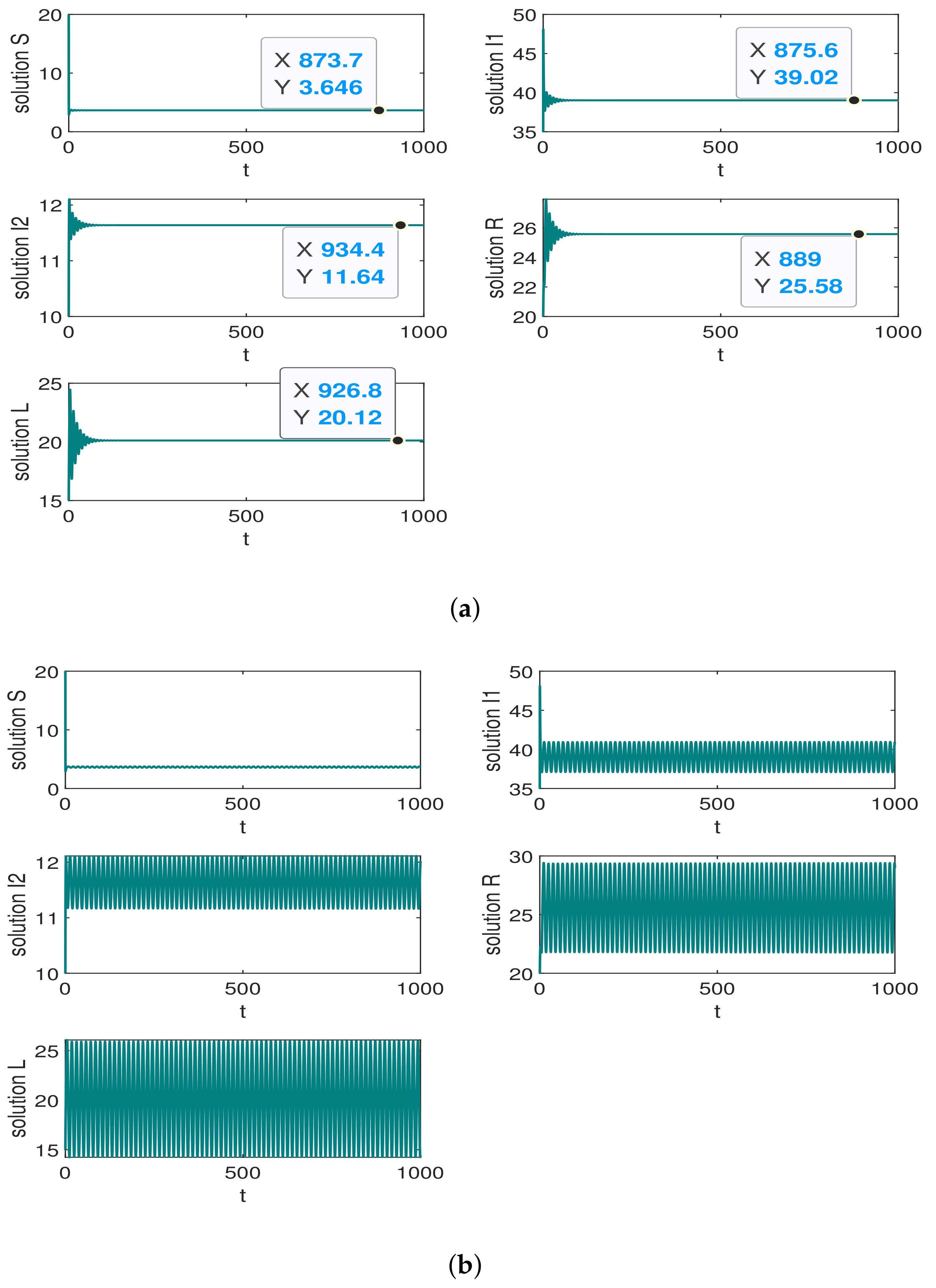
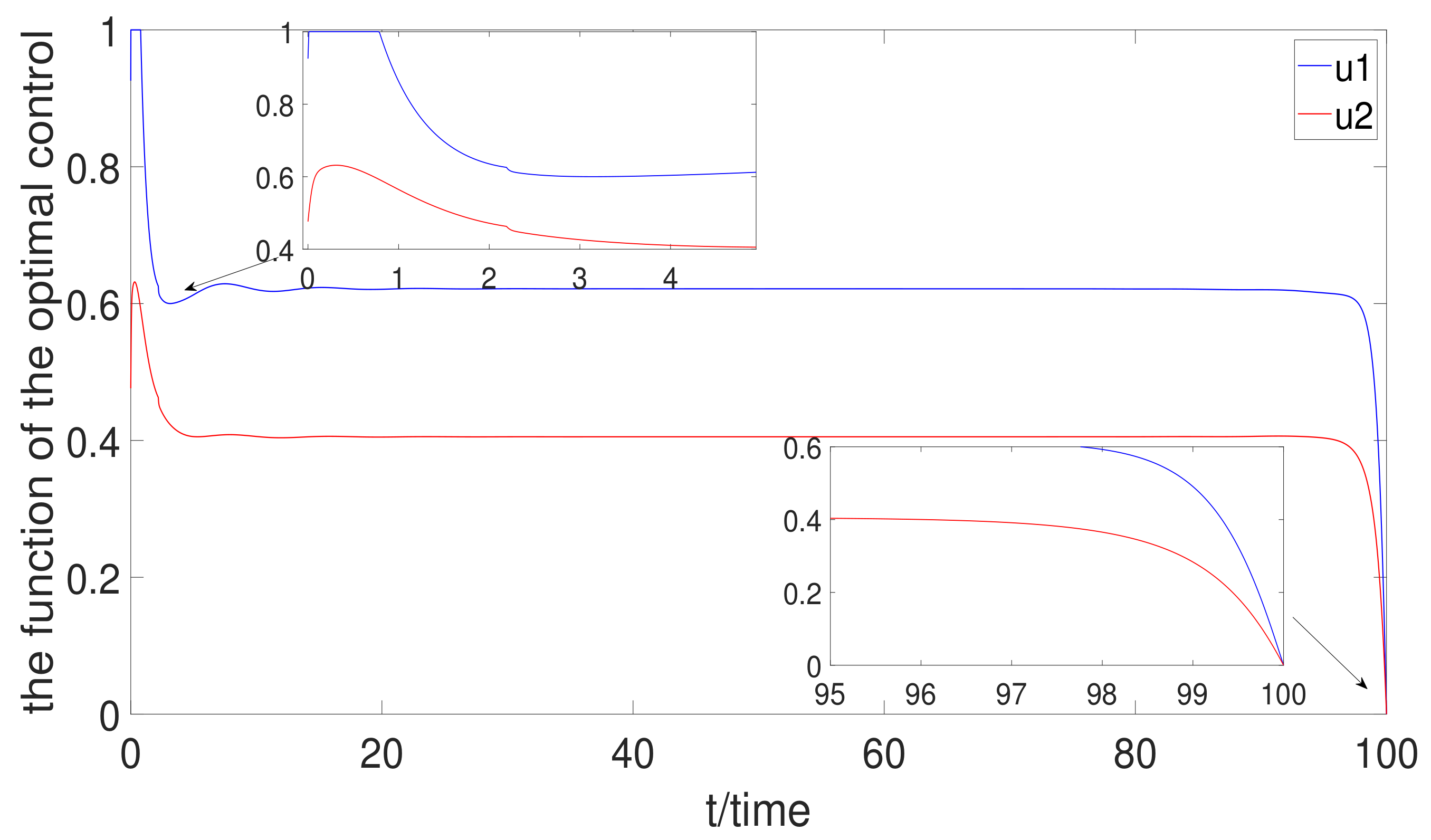
6. Simulation
6.1. Relationship between Parameters and Basic Reproductive Numbers
6.2. The Trend of the Quantity of State Nodes
6.3. Optimal Control Strategy Analysis
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, W.; Zhu, H. Research on Comprehensive Enterprise Network Security. In Proceedings of the 2021 IEEE 11th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 18 20 June 2021; pp. 1–6. [Google Scholar]
- Manshaei, M.H.; Zhu, Q.; Alpcan, T.; Bacşar, T.; Hubaux, J.P. Game theory meets network security and privacy. ACM Comput. Surv. (CSUR) 2013, 45, 1–39. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Sandra, S.H.; Natarajan, S.; Sakir, S. A survey of security in software defined networks. IEEE Commun. Surv. Tutorials 2015, 2015, 623–654. [Google Scholar]
- Kulkarni, R.V.; Förster, A.; Venayagamoorthy, G.K. Computational intelligence in wireless sensor networks: A survey. IEEE Commun. Surv. Tutorials 2010, 13, 68–96. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Butun, I.; Morgera, S.D.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutorials 2013, 16, 266–282. [Google Scholar] [CrossRef]
- Ren, Q.C.; Liang, Q.L. Energy and quality aware query processing in wireless sensor database systems. Inf. Sci. 2007, 177, 2188–2205. [Google Scholar] [CrossRef]
- Lenin, R.B.; Ramaswamy, S. Anosov flows with stable and unstable differentiable distributions. Ann. Oper. Res. 2015, 233, 237–261. [Google Scholar] [CrossRef]
- Kephart, J.O.; White, S.R. Directed-graph epidemiological models of computer viruses. In Computation: The Micro and the Macro View; World Scientific: Singapore, 1992; pp. 71–102. [Google Scholar]
- Kephart, J.O.; White, S.R. Measuring and modeling computer virus prevalence. In Proceedings of the 1993 IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 24–26 May 1993; pp. 2–15. [Google Scholar]
- Liu, W.P.; Liu, C.; Yang, Z.; Liu, X.Y.; Zheng, Y.H.; Wei, Z.X. Modeling the propagation of mobile malware on complex networks. Commun. Nonlinear Sci. Numer. Simul. 2016, 37, 249–264. [Google Scholar] [CrossRef]
- Zhu, L.H.; Zhou, X.; Li, Y.M. Global dynamics analysis and control of a rumor spreading model in online social networks. Phys. A Stat. Mech. Its Appl. 2019, 526, 120903. [Google Scholar] [CrossRef]
- Li, J.X.; Ning, R.; Zhen, J. An SICR rumor spreading model in heterogeneous networks. Discret. Contin. Dyn.-Syst.-B 2020, 25, 1497. [Google Scholar] [CrossRef] [Green Version]
- Choi, S.H.; Seo, H.; Yoo, M. A multi-stage SIR model for rumor spreading. Discret. Contin. Dyn. Syst.-B. 2020, 25, 2351. [Google Scholar] [CrossRef] [Green Version]
- Huang, Y.A.; Tang, M.; Zou, Y.; Zhou, J. Hybrid phase transitions of spreading dynamics in multiplex networks. Chin. J. Phys. 2018, 56, 1166–1172. [Google Scholar] [CrossRef]
- Khayam, S.A.; Radha, H. Using signal processing techniques to model worm propagation over wireless sensor networks. IEEE Signal Process. Mag. 2006, 23, 164–169. [Google Scholar] [CrossRef]
- Feng, L.P.; Song, L.P.; Zhao, Q.S.; Wang, H.B. Modeling and stability analysis of worm propagation in wireless sensor network. Math. Probl. Eng. 2015, 2015, 129598. [Google Scholar] [CrossRef] [Green Version]
- Singh, A.; Awasthi, A.K.; Singh, K.; Srivastava, P.K. Modeling and analysis of worm propagation in wireless sensor networks. Wirel. Pers. Commun. 2018, 98, 2535–2551. [Google Scholar] [CrossRef]
- Ojha, R.P.; Srivastava, P.K.; Sanyal, G.; Gupta, N.S. Improved model for the stability analysis of wireless sensor network against malware attacks. Wireless Personal Commun. 2021, 116, 2525–2548. [Google Scholar] [CrossRef]
- Muthukrishnan, S.; Muthukumar, S.; Chinnadurai, V. Optimal control of malware spreading model with tracing and patching in wireless sensor networks. Wirel. Pers. Commun. 2021, 117, 2061–2083. [Google Scholar] [CrossRef]
- Ye, X.T.; Xie, S.S.; Shen, S.G. SIR1R2:Characterizing Malware Propagation in WSNs With Second Immunization. IEEE Access 2021, 9, 82083–82093. [Google Scholar] [CrossRef]
- Gharaei, N.; Al-Otaibi, Y.D.; Rahim, S.; Alyamani, H.J.; Khani, N.A.K.K.; Malebary, S.J. Broker-Based Nodes Recharging Scheme for Surveillance Wireless Rechargeable Sensor Networks. IEEE Sens. J. 2021, 21, 9242–9249. [Google Scholar] [CrossRef]
- Qin, C.; Sun, Y.H.; Zhang, Y.H.; Ai, M.T. A novel path planning of mobile charger in wireless rechargeable sensor networks. In Proceedings of the 2017 29th Chinese Control And Decision Conference (CCDC), Chongqing, China, 28–30 May 2017; pp. 2063–2067. [Google Scholar]
- Lin, C.; Shang, Z.; Du, W.; Ren, J.K.; Wang, L.; Wu, G.W. CoDoC: A novel attack for wireless rechargeable sensor networks through denial of charge. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 856–864. [Google Scholar]
- Li, P.D.; Yang, L.X.; Yang, X.F.; Zhong, X.; Wen, J.H.; Xiong, Q.Y. Energy-efficient patching strategy for wireless sensor networks. Sensors 2019, 19, 262. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, G.Y.; Huang, Z.Y.; Wu, X.L.; Liang, Z.W.; Hong, F.H.; Su, X.K. Modelling and Analysis of the Epidemic Model under Pulse Charging in Wireless Rechargeable Sensor Networks. Entropy 2021, 23, 927. [Google Scholar] [CrossRef] [PubMed]
- Liu, G.Y.; Su, X.K.; Hong, F.H.; Zhong, X.J.; Liang, Z.W.; Wu, X.L.; Huang, Z.Y. A Novel Epidemic Model Base on Pulse Charging in Wireless Rechargeable Sensor Networks. Entropy 2022, 24, 302. [Google Scholar] [CrossRef] [PubMed]
- Keshri, N.; Mishra, B.K. Two time-delay dynamic model on the transmission of malicious signals in wireless sensor network. Chaos Solitons Fractals 2014, 56, 151–158. [Google Scholar] [CrossRef]
- Zhang, Z.Z.; Zou, J.C.; Upadhyay, R.K.; ur Rahman, G. An epidemic model with multiple delays for the propagation of worms in wireless sensor networks. Results Phys. 2000, 19, 103424. [Google Scholar] [CrossRef]
- Song, Y.L.; Wei, J.J. Local Hopf bifurcation and global periodic solutions in a delayed predator–prey system. J. Math. Anal. Appl. 2005, 301, 1–21. [Google Scholar] [CrossRef] [Green Version]
- Xu, J.; Lu, Q.S. Hopf bifurcation of time-delay Lienard equation. Int. J. Bifurc. Chaos 1999, 9, 939–951. [Google Scholar] [CrossRef]
- Wulf, V.; Ford, N.J. Numerical Hopf bifurcation for a class of delay differential equations. J. Comput. Appl. Math. 2000, 115, 601–616. [Google Scholar] [CrossRef] [Green Version]
- Liu, G.Y.; Peng, B.H.; Zhong, X.J. A novel epidemic model for wireless rechargeable sensor network security. Sensors 2020, 21, 123. [Google Scholar] [CrossRef]
- Nurtay, A.; Hennessy, M.G.; Sardanyés, J.; Alsedà, L.; Elena, S.F. Theoretical conditions for the coexistence of viral strains with differences in phenotypic traits: A bifurcation analysis. R. Soc. Open Sci. 2019, 6, 181179. [Google Scholar] [CrossRef] [Green Version]
- Avllazagaj, E.; Zhu, Z.Y.; Bilge, L.; Balzarotti, D.; Dumitras, T. When Malware Changed Its Mind: An Empirical Study of Variable Program Behaviors in the Real World. In Proceedings of the 30th USENIX Security Symposium, online, 11–13 August 2021; pp. 3487–3504. [Google Scholar]
- Li, D.M.; Li, C.C.; Xu, Y.J. The Stability of a Class of SEIR Epidemic Model with Virus Mutate. J. Harbin Univ. Sci. Technol. 2014, 19, 105–109. [Google Scholar]
- Li, D.M.; Fu, Y.L.; Gao, T.Q.; Li, C.C. Stability analysis of a class of SIR epidemic model with delayed spontaneous variation of vrius. J. Harbin Univ. Sci. Technol. 2020, 25, 2. [Google Scholar]
- Hao, R.J. Epidemic Spreading Model with Virus Variation and Its Stability; Nanjing University of Posts and Telecommunications: Nanjing, China, 2016. [Google Scholar]
- Xu, D.G.; Xu, X.Y.; Su, Z.F. Novel SIVR epidemic spreading model with virus variation in complex networks. In Proceedings of the 27th Chinese Control and Decision Conference (2015 CCDC), Qingdao, China, 23–25 May 2015; pp. 5164–5169. [Google Scholar]
- Cao, Y.L.; Wang, X.M.; He, Z.B. Optimal security strategy for malware propagation in mobile wireless sensor networks. Acta Electonica Sin. 2016, 44, 1851. [Google Scholar]
- Zhang, L.; Liu, M.X.; Xie, B.L. Optimal control of an SIQRS epidemic model with three measures on networks. Nonlinear Dyn. 2021, 103, 2097–2107. [Google Scholar] [CrossRef]
- Zhu, L.H.; Guan, G.; Li, Y.M. Nonlinear dynamical analysis and control strategies of a network-based SIS epidemic model with time delay. Appl. Math. Model. 2019, 70, 512–531. [Google Scholar] [CrossRef]
- Chen, L.J.; Hattaf, K.; Sun, J. Optimal control of a delayed SLBS computer virus model. Phys. A Stat. Mech. Its Appl. 2015, 427, 244–250. [Google Scholar] [CrossRef]
- Pei, Y.Z.; Chen, M.M.; Liang, X.Y.; Xia, Z.M.; Lv, Y.F.; Li, C.G. Optimal control problem in an epidemic disease SIS model with stages and delays. Int. J. Biomath. 2016, 9, 1650072. [Google Scholar] [CrossRef]
- Li, L.L.; Sun, C.X.; Jia, J.W. Optimal control of a delayed SIRC epidemic model with saturated incidence rate. Optim. Control Appl. Methods 2019, 40, 367–374. [Google Scholar] [CrossRef]
- Wan, C.; Li, T.; Zhang, W.; Dong, J. Dynamics of epidemic spreading model with drug-resistant variation on scale-free networks. Phys. A Stat. Mech. Its Appl. 2018, 493, 17–28. [Google Scholar] [CrossRef]
- Liu, G.Y.; Peng, Z.M.; Liang, Z.W.; Li, J.Q.; Cheng, L.F. Dynamics Analysis of a Wireless Rechargeable Sensor Network for Virus Mutation Spreading. Entropy 2021, 23, 572. [Google Scholar] [CrossRef]
- Liu, G.Y.; Chen, J.Y.; Liang, Z.W.; Peng, Z.M.; Li, J.Q. Dynamical Analysis and Optimal Control for a SEIR Model Based on Virus Mutation in WSNs. Mathematics 2021, 9, 929. [Google Scholar] [CrossRef]
- Liu, Y.; Chu, D.H.; Zou, Y.X.; Su, H. Stabilization of stochastic complex networks with switching jump diffusions based on adaptive aperiodically intermittent control. Nonlinear Dyn. 2021, 104, 3737–3751. [Google Scholar] [CrossRef]
- Achar, S.J.; Baishya, C.; Kaabar, K.A. Dynamics of the worm transmission in wireless sensor network in the framework of fractional derivatives. Math. Methods Appl. Sci. 2022, 45, 4278–4294. [Google Scholar] [CrossRef]



| N | The number of all nodes in the WSN |
|---|---|
| The proportion of birth and death sensor nodes | |
| The proportion of susceptible nodes becoming infected nodes | |
| The proportion of susceptible nodes becoming recovered nodes | |
| The proportion of infected nodes becoming recovered nodes | |
| The proportion of recovered nodes becoming susceptible nodes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, G.; Peng, Z.; Liang, Z.; Zhong, X.; Xia, X. Analysis and Control of Malware Mutation Model in Wireless Rechargeable Sensor Network with Charging Delay. Mathematics 2022, 10, 2376. https://doi.org/10.3390/math10142376
Liu G, Peng Z, Liang Z, Zhong X, Xia X. Analysis and Control of Malware Mutation Model in Wireless Rechargeable Sensor Network with Charging Delay. Mathematics. 2022; 10(14):2376. https://doi.org/10.3390/math10142376
Chicago/Turabian StyleLiu, Guiyun, Zhimin Peng, Zhongwei Liang, Xiaojing Zhong, and Xinhai Xia. 2022. "Analysis and Control of Malware Mutation Model in Wireless Rechargeable Sensor Network with Charging Delay" Mathematics 10, no. 14: 2376. https://doi.org/10.3390/math10142376
APA StyleLiu, G., Peng, Z., Liang, Z., Zhong, X., & Xia, X. (2022). Analysis and Control of Malware Mutation Model in Wireless Rechargeable Sensor Network with Charging Delay. Mathematics, 10(14), 2376. https://doi.org/10.3390/math10142376








