1. Introduction
Number theory is the branch of mathematics that focuses on the appealing qualities of integers. Number theory is known as the Queen of Mathematics because of many unanswered problems it contains. With the advancement of supercomputers, number theory is now used in various engineering domains, particularly in cryptography. Everybody relies on online exchanges in the current advanced period, where security plays an enormous role. To ensure online safety, cryptographic algorithms that are developed using number theoretic ideas play a significant task. Cryptography is typically defined as the study of mathematical approaches for achieving various information security goals such as secrecy, authenticity, integrity, non-repudiation, and so on. The term refers to a subset of strategies rather than the mechanism of delivering data security. In most cryptographic algorithms, the generation of large prime numbers is required to encrypt and decrypt the messages passed through the online channel.
The reasoning of Diophantine equations and their applications is a growing field in number theory. The Diophantine equation is a multivariate polynomial equation with integer coefficients which seeks only integral solutions. Subsequently, the Diophantine problem is notable to be a difficult problem and is relied upon to be utilized in cryptography applications. In general, Diophantine equations have been solved by considering the ring of integers,
Z. But, because of its arising applications, presently the specialists are begun to think about the problem over arbitrary rings. The linear Diophantine equation
is the simplest form of the Diophantine equation, where
are integers and
are unknown integers. Another important class of Diophantine equation is the Pell’s equation. The Indian mathematicians Brahmagupta and Bhaskara were the first to explore the Pell’s equation. Since ancient times, Pell’s Equation, which pertains to the cyclic group and has several solutions, has been used in the domain of number theory for a wide range of applications. Numerous disciplines are now addressing the binary quadratic Diophantine equations, both homogeneous and non-homogeneous. Since various Diophantine problems are evolving day by day, various mathematicians across the globe study these problems. Many cryptography methods have been developed based on these characteristics [
1,
2,
3,
4,
5,
6,
7,
8]. Thirumala et al. [
9] recently devised an efficient technique based on Pell’s equation that provides good reliability in opposition to side-channel exploits such as timing attacks. RSA (Rivest–Shamir–Adleman) is a widely used public key cryptographic method in security systems. Raghunandan et al. [
10] used the generalized Pell’s equation for compelling the safety of RSA.
A trapdoor function is one that is computationally simple in one direction but hard to determine in the reverse directions (identifying its inverse) without particular information. In cryptography, trapdoor functions are usually applied. Mathematically, if
f is a trapdoor function, then there exists a secret information
t, such that given
and
t, it is straightforward to compute
x. Making trapdoors is regarded as the core of the process of developing public key cryptosystems. Bijective trapdoor functions are universally recognized as adequate for public key cryptography [
11,
12]. The recent developments in the theory of trapdoor functions can be seen in [
13,
14]. An authentication protocol is a kind of protocol that is intended to secure the exchange of authentication data between two or more clients. The factors to be taken into account in the authentication process are
A protocol must constitute at least two clients, and everyone associated must be aware of the protocol ahead of time.
The protocol must be followed by all the concerned clients.
The steps involved in the protocol must be well defined.
A protocol must be comprehensive, containing instructions for every possible scenario.
“Smart” devices and technologies have enabled substantial advancements in industry revenue and safety in recent decades. Hernández-Álvarez et al. [
15] developed a new device to avail estimates of the temperature of diabetic foot where cryptographic protocols are present to ensure data security. Bullón Pérez et al. [
16] performed another interesting research on Blockchain systems in the retail sector. In 2017, Rey and Dios [
17] carried out a critical review on cryptographic protocols on wireless sensor networks concentrating on secret key cryptosystems. Malware has now emerged as a possible threat to the IoT, and hence to Wireless Sensor Networks. Batista et al. [
18] presented an Agent-Based design for assessing trojan transmission on these networks. Recently, Martinez et al. [
19] performed a critical review on the cryptographic techniques associated with block chain and bitcoin. Okumura [
20] developed a new public key cryptosystem based on Diophantine equations of degree increasing type. He used those type of Diophantine equations to recover the plaintext. Murthy and Swamy [
21] derived a new authentication protocol as well as a new encryption-decryption algorithm based on the Pell’s equation. Later, Alvarez et al. [
22] and Youssef [
23] modified the algorithm developed by [
21]. Recently, Alecci and Dutto [
24] studied the use of Pell hyperbolas in cryptosystems with security based on the discrete logarithm problem.
In the present work, the authors aim to develop a new authentication protocol based on the geometric properties of solutions of the second degree Diophantine equation and also analysed the initial cost and effort required to develop a new software for this protocol using the basic constructive cost models (COCOMO).
2. Mathematical Properties of the Equation
This section deals with the study on mathematical properties of the equation .
Theorem 1. The positive integral solutions of the Diophantine equation do not lie on a straight line with slope .
Proof. The Diophantine equation
can be written as
Let
which is the slope of the straight line joining
and
. It follows that the relationship (4) gives
. It is not true due to positive integral solutions of the Diophantine equation. Hence the positive integral solutions do not lie on a straight line when
. Also, (4) does not hold when
or
.
Note 1. In general, a slope of the straight line joining and is . The relationship (4) does not hold when or . If , consider the case when . Then implies that . Also from (4), it is clear that when . Hence, we obtain the solution of as which is considered as the equivalent solution but not distinct.
Theorem 2. Let one pair of the Diophantine equation be known. Then the distance δ between the constructed points and satisfies the condition where provided .
Proof. Given one pair , finding out another pair satisfying is a challenge. Let be the distance between the constructed points and , where and are unknown. Then . This implies . Since , . So . Given , becomes a constant and let it be k. Then , provided . This implies that .
Theorem 3. If one pair is known, then the other point of the Diophantine equation satisfies or .
Proof. Consider . This can be written as which implies . Since all s and ’s are positive, . Thus . For the given , is a constant. Let us assume that . Then which implies . Similarly, if , then which implies .
Theorem 4. If is known and is chosen as and then the upper bound for the distance d between the points and which satisfies the relation is given by where .
Proof. Let
d be the distance between
and
. Then, we have
. Since
,
Since
,
and
. Thus
. Since
we have
or
, where
. Hence
follows.
Note 2. Let one positive integral pair of the Diophantine equation be known. Then we are finding out the relationship between δ and d (from Theorems 2 and 4) given as Example 1. Let and . Given . Then . It follows as . Now which implies . But , where . Let us choose . Then and . Hence .
Example 2. Let and . Then . Thus, . Now, . But, , where . By taking , we get and . Hence .
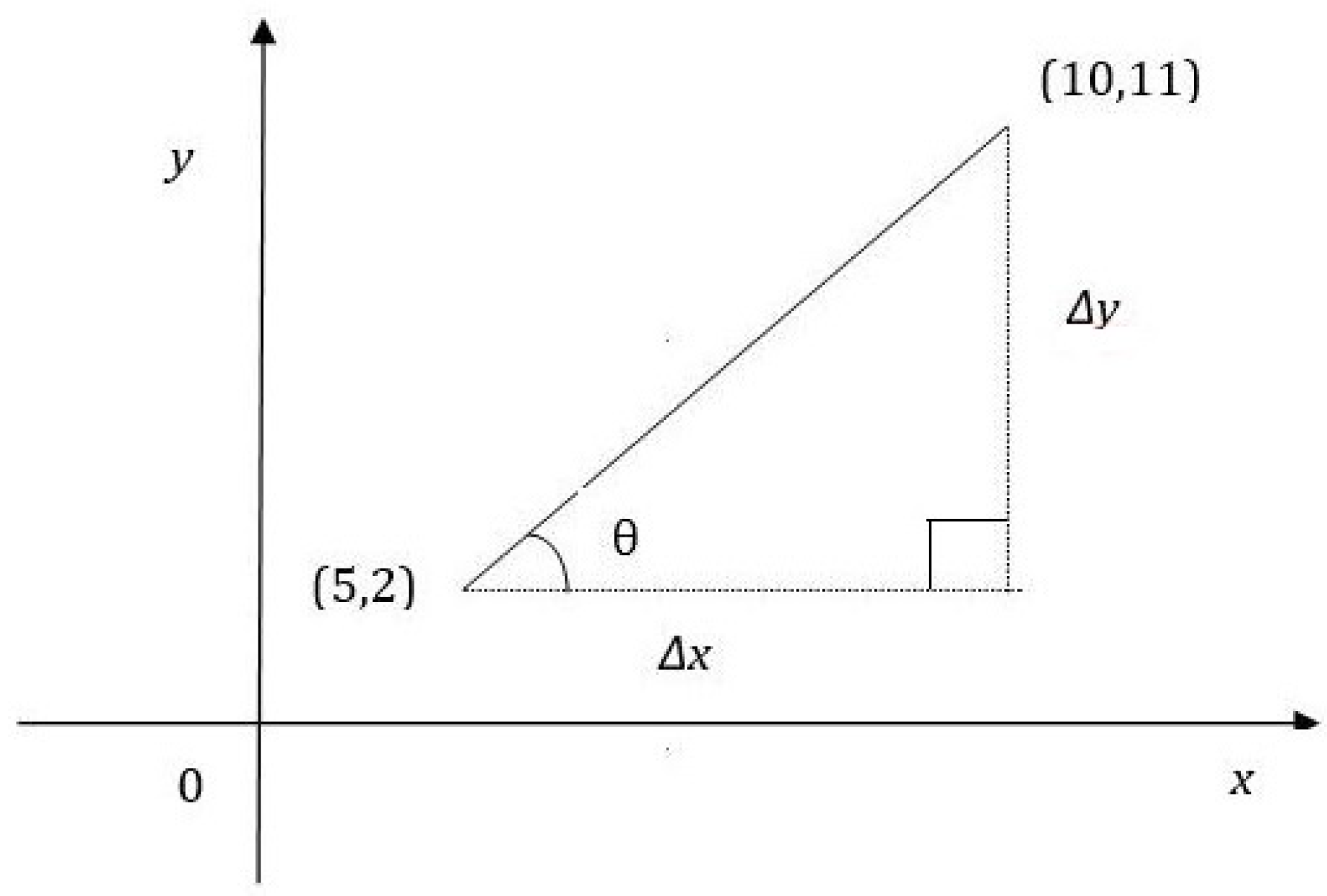
Example 3. Let us have and satisfying the Diophantine equation where and . The slope of the line between and is . Let θ be the angle of inclination. Then . Further, distance units. Therefore, the equation of the line is . Now we can construct a right-angled triangle with vertices , and as in Figure 1. Example 4. Let us have and satisfying the Diophantine equation where and . The slope of the line between and is . Let θ be the angle of inclination. Then . Further, distance units. Therefore the equation of the line is . Now we can construct another right angled triangle with vertices , and as in Figure 2. Theorem 5. If the two points and are the solutions of the quadratic Diophantine equation where and , then the four points , , and constitute a rectangle where and .
Proof. Given that
and
. Let the given points
,
,
and
be the four vertices of a four-sided polygon. By two-dimensional geometry, either
and
denote the length and width of the polygon
or
and
be the width and length
. The distance
d between the points
and
acts as a diagonal of the polygon as in
Figure 3.
Thus, we obtain two right-angled triangle, say and having the same hypotenuse d. Similarly, the right-angled triangles and have the hypotenuse as . Note that . Thus, the two diagonals of the polygon ABCD are equal and with the choice of it is clear that ABCD is a rectangle.
3. Existence of Trapdoor Function in Diophantine Cryptography
Everybody depends on the secret key to guarantee the security of data. So, it must be assured that the secret key is extremely difficult to crack. Note that cryptanalysis is the field of attacking cryptosystems. One method of cryptanalysis involves the attacker possessing both the message’s plaintext and ciphertext and attempting to decipher the key that converts the plaintext to the ciphertext. Using a brute-force attack, or checking all potential keys, is one way they can achieve this. The key space, or range of potential keys, should be very large in order to protect against a brute-force attack. A secret key shared by two users is used in symmetric-key cryptography. Party A can encrypt data with the secret key and transfer the output to Party B, who can decrypt and interpret data with the same key. Key management, or the secure exchange of secret keys between users, is the secure framework for symmetric cryptography. The drawback of the symmetric key cryptography is Key distribution and management is a serious problem—for
N users
keys are needed. In this section, we have invented a secure authentication communication protocol between client and server using Diophantine equation
as in
Figure 4.
In the step 1, Server sends a trapdoor information (message) to Client. The server keeps a distinct pair of -bit session key to each client. During every transaction, the server generates a trapdoor information in accordance with session key to each client. Each client receives a distinct trapdoor information computed by server. In the step 2, the client computes and . Then the client sends Hash() to server which verifies the result. Then the authentication mechanism has been established between both parties. In this protocol, when and are hacked by an attacker, it is computationally challenge to retrieve the values and due to Diophantine equation. It is observed that the client uses the as one time password (OTP)/E-token for any network transactions. Similar to the above protocol, we can send instead of Hash() to server as a plaintext. It is termed as transparent (naked) Diophantine authentication protocol. Along with big data tools, the proposed protocol helps to generate, distribute, store and revoke a large volume of E-tokens and keeps an eye on cryptographic attacks.
The ElGamal cryptosystem, a subset of public key cryptography, is based on the Discrete Logarithm Problem (DLP). It is vulnerable to the man-in-the-middle attack, chosen-plaintext attacks and not useful for one way communication. The computational complexity of DLP has come around O() where n is the amount of resources or operations required to execute the discrete logarithm. In the present study, the authors described Diophantine cryptography that could be solved in O(). It is useful to one-way communication system. Due to high computational complexity to crack or identify an exact integral solution to a given Diophantine equation, it is a real challenge to perform rudimentary cryptographic attacks.
Given a point
, estimating another point
satisfying
is computationally difficult for higher integral values. But for smaller integral values this process is not so hard. For the given point
, an attacker can try to form a rectangle in which a right angled triangle with angles
where
. The attacker requires to vary
and
and verify the Diophantine relationship. It needs
computations. Subsequently, the attacker tries to make two right angled triangles comprised into a rectangle which inscribed in a circle must have its diagonal as the diameter of the circle. The attacker computes the perimeter of the rectangle and verifies whether perimeter is equal to
. Gradually, the attacker increases the perimeter of the rectangle and the corresponding area of the circle in order to find a suitable point
. This ensures the existence of trapdoor function in Diophantine and very hard to crack this challenge. Algorithm 1 describes the pseudocode for the authentication protocol based on the equation
.
| Algorithm 1 Pseudocode for the authentication protocol |
| Input: B, the trapdoor message in a binary form. |
| Input: . |
| Output: decimal , base |
| while
do |
| remainder = B% 10 |
| decimal = decimal + remainder * base |
| B = B / 10 |
| base = base * 2 |
| end while |
| Output: n = decimal |
| ; |
| ; |
| ; |
| ; |
| if
then |
| Trapdoor is possible using Diophantine equation; |
| else |
| No solution |
| end if |
It is to be noted that the 128/256-bit session key and the trapdoor message act as the secret keys and it should be known to the server as well as clients to do the authentication. As a result, any safe key exchange mechanism should be used to exchange the keys. The symmetric cryptography is exposed in two ways: the requirement to communicate the key raises the risk of it being intercepted in transit, and quantum computers can employ Grover’s algorithm to enhance the accuracy of a brute-force attack. Since quantum algorithms do not completely break Hash-based digital signatures, the newly discovered authentication systems enable a secure digital data transmission.
In the symmetric key cryptography, a private key of a specific size is developed using a source of randomness. There is no mathematical proof (or analysis) to crack a private key because of the random creation process and the non-availability of patterns. Eventhough, brute-force attacks are included in cryptanalysis, a brute-force attack entails attempting to decipher the ciphertext and retrieve the plaintext using every feasible key. In order to find the correct key, an attacker would have to test 50% of all possible keys. As a result, a secret (or private key) with suitable entropy and length could adequately safeguard encrypted data. Grover’s approach, on the other hand, can leverage qubit superposition to expedite the brute-force attack by a quadratic factor. Also, when a cryptographic algorithm permits to use, doubling the symmetric key sizes keeps this type of encryption safe. However, doubling the key size is not a simple operation. When a cryptographic algorithm is deployed by a software under the environment of Cloud setup, it is quite simple since an update may provide for an efficient key-size change.
4. Cost and Effort Evaluation Using COCOMO Equations
One of the most widely used software prediction models is the constructive cost model (COCOMO). The two key factors that determine the integrity of any software development project are effort and schedule, both of which are consequences of COCOMO. One can choose a model of COCOMO based on the requirements on accuracy and correctness. There are three COCOMO models: Basic, Intermediate and Complex. Basic COCOMOs are developed for a rapid and fuzzy analysis of software estimation. Intermediate models consider cost drivers into account, while complex models take the influence of individual project phases. All these models can be used for various software developments under the Cloud based on the characteristics of the different system types: organic, semi-detached, and embedded.
This section explains how to create software utilising organic COCOMO equations to implement the new authentication protocol that is discussed in
Section 3. For organic model software projects, the fundamental COCOMO equations are
where
X is the effort applied in persons-months,
R is the build-up time in chronological months,
l is the calculated number of lines of code for the project (expressed in thousands) and
P is the number of persons.
Table 1 represents the values of the coefficients and exponents in COCOMO equations for different project types as in [
25].
The COCOMO parameter is used to quantify the workload of software and runtime after
l has been evaluated. The COCOMO equation shows that as
l increases, the workload and duration increase as well.
Table 2 represent the estimated work, time, and labor involved in creating each line of code in the program using basic COCOMO equations.
The number of lines of code for C++ program developed for the protocol is 42. Thus for authentication protocol, the effort persons-months, time months and the manpower persons. Hence, using the basic COCOMO equations, the initial cost, effort and manpower can be derived for developing a new software in order to implement the authentication protocol.
5. Conclusions
In the present work, some geometric properties of quadratic Diophantine equations are derived and explained their uses in the communication protocols. Also, a new secure authentication mechanism based on the positive integral solutions of the quadratic Diophantine is presented which can be employed in the generation of one-time passwords or E-tokens for cryptography applications. Further, the existence of trapdoor functions in Diophantine equation is well analysed. It is noted that the proposed authentication protocol is secure either performing Hashing method or without Hashing. Also, the initial cost and effort of a new software library under the environment of Cloud are determined for implementing the authentication protocols using basic COCOMO equations.