Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity
Abstract
:1. Introduction
- RQ1: Can verifiable credentials be used in conjunction with IPFS to theoretically enforce authenticated identity and storage of underlying NFT digital assets?
- RP1: Verifiable credentials allow for increased privacy, security, and longevity of data.
- RQ2: Can social media (specifically Twitter) be used in conjunction with NFTs to practically reduce the likelihood of digital asset infringements and fraud?
- RP2: IF a smart contract can be coded to leverage Twitter’s social, non-human user verification process and connect that already established identity authenticity with NFTs, THEN a reduced likelihood of NFT fraud and infringements would occur.
- Design a theoretical architecture that converges NFTs, IPFS, and verifiable credentials with the aim of storing underlying digital assets in a decentralized manner;
- Design and develop a practical web-based application that has the functionality to link NFTs to an authenticated digital identity through the use of social media (i.e., Twitter).
2. Related Work and Background
- Verifiable Credentials
- Non-fungible Tokens
- ERC721 Smart Contract
- Social Media
2.1. Related Work
2.2. Verifiable Credentials
2.2.1. Elements
- Data claim—A piece of data representing a statement made about a subject. Example: “Bob graduated from the University of Pretoria”.
- Metadata—Attributes of the data claim such as the issuer, expiry date of the credential, an illustrative image representing the credential, and a public verifiable key.
- Proof—Information about the prover that allows other parties and users to verify the validity of the data claim held, that it has not been altered in any way, and that it has not been revoked by the issuer.
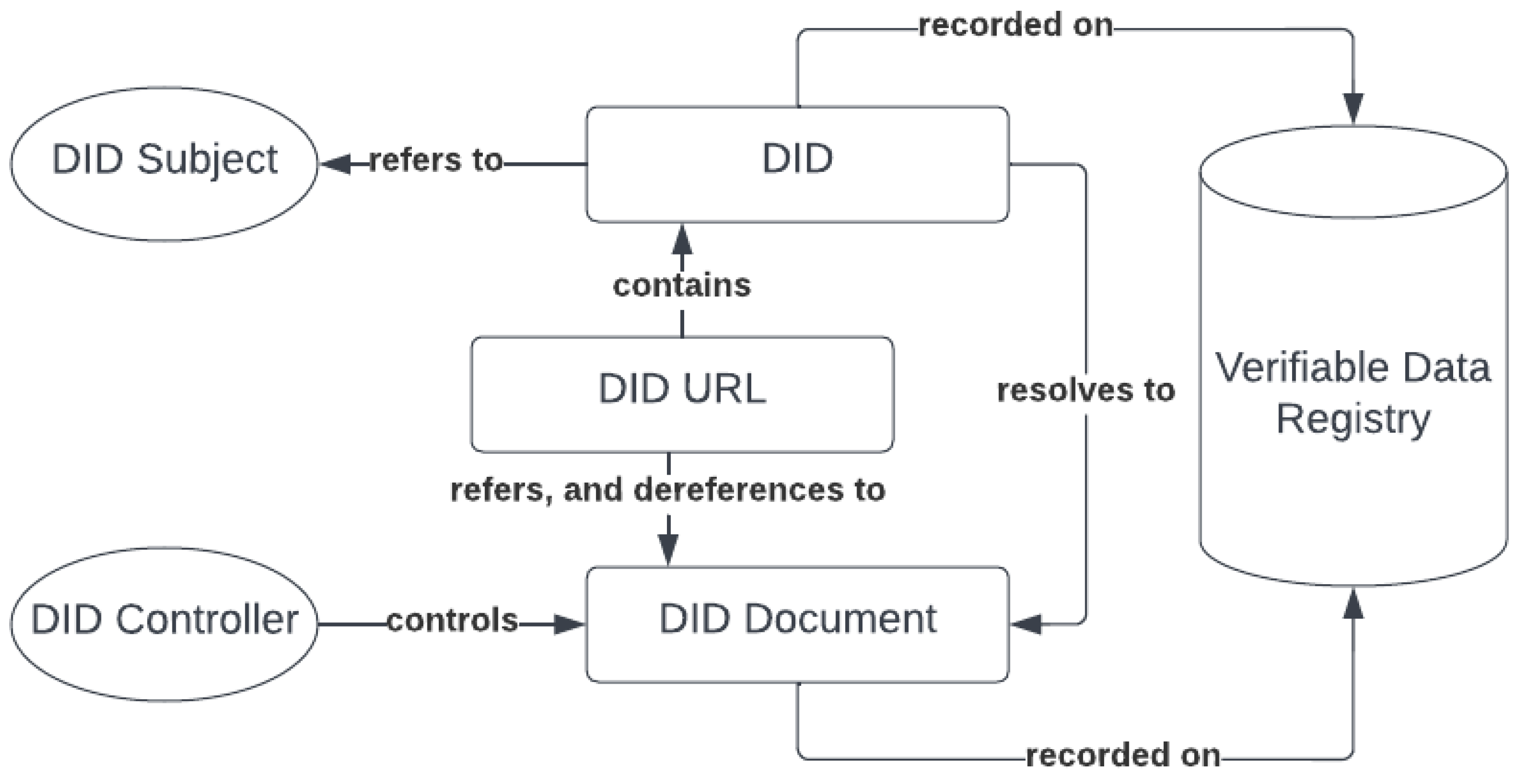
- DID—A DID, or decentralized identifier, is a type of uniform resource identifier (URI—a standard identifier format for all resources on the World Wide Web) and is composed of the scheme DID, method identifier, and a unique, method-specific identifier specified by the DID method. It should be noted that DIDs are resolvable to DID documents.
- DID subjects—The subject of a DID is the entity identified by the DID. This can be a person, organization, thing, or concept. The DID subject can also be the DID controller.
- DID controllers—The controller of a DID is the entity that has the ability, as defined by the DID method, to make changes to the DID document. This ability is controlled through the ownership of a set of cryptographic keys. It should be noted that a DID might have more than one controller.
- Verifiable data registries—In order to be resolvable to DID documents, DIDs have to be recorded on an underlying network. This can be any specific technology that supports the recording and returning of DID documents, such as decentralized file systems and ledgers, databases of any kind and peer to peer networks.
- DID documents—DID documents containing information relating to a DID.
- DID methods—DID methods are the mechanisms by which a DID and the associated DID document are created, resolved, updated, and deactivated.
- DID resolvers and DID resolution—The process of DID resolution entails a DID resolver using a DID as input and produces an associated DID document.
- DID URL dereferencing—The process of DID URL dereferencing entails taking a DID URL as input and produces a resource.
- Private wallets—In order to implement verifiable credentials, manage DIDs, and store private keys, digital “wallets” are used. They come in several formats, including mobile phone applications, software, cloud storage, and hardware. Aside from the type of digital wallet used, an imperative element maintained is that it is under the ownership and control of the end user.
2.2.2. Advantages
- Privacy—The concept of selective disclosure allows the prover the ability to only reveal certain attributes of a specific data claim they hold. Regarding an identity document, for example, the prover can choose to only reveal the year of birth. Furthermore, the prover can choose who they share data claims with and can revoke the sharing of data claims at any time. The prover therefore has full control over their data. Verifiable credentials are stored on an edge or cloud wallet under the control of the prover. Therefore, no personal identification data are stored externally, be it decentralized or centralized.
- Security—Security of data is enforced by cryptography via the blockchain. Furthermore, the verifiable credential resides in the cloud or edge wallet of the prover and not centrally in the location of the issuer. Only the public DID would reside on the blockchain.
- Longevity—Verifiable credentials will never be involuntarily removed from the network, even in the case where the issuer is not operating anymore. Once a verifiable credential is created, the DID linked to it will exist on the blockchain in a decentralized manner and not be linked to any centralized server or location that can be shut down.
2.3. Non-fungible Tokens
NFT Smart Contracts
2.4. ERC721 Smart Contract
2.4.1. ERC20-like Functions
- name—Defines the token name for other applications and smart contracts;
- symbol—Defines the token symbol;
- totalSupply—Defines the total number of tokens that exist on the blockchain;
- balanceOf—This function returns the number of NFTs owned by a specific wallet address.
2.4.2. Ownership Functions
- ownerOf—This function returns the owner of a specific NFT. Due to the ERC721 standard representing tokens that are unique and non-fungible, these are represented as an ID on the blockchain. Users and smart contracts on the network can use this to identify the owner of the token.
- approve—This function will approve the ability for the owner of the token to transfer it to another user or entity.
- takeOwnership—This optional function can be executed by an outside party to transfer tokens out of another user’s account. Therefore, this function can be used when a user has been approved to own a specific amount of tokens and wants to transfer these tokens from another user’s or entity’s balance.
- transfer—This is another transfer-based function similar to the approve function that allows an owner to transfer tokens to another user or entity, just like other digital tokens or coins.
- tokenOfOwnerByIndex—This optional function allows an owner to hold more than one NFT at a time. Due to each NFT being represented by a unique ID, the smart contract stores these IDs in an array and the function allows for the retrieval of these IDs from the array.
2.4.3. Metadata Functions
- tokenMetadata—This function is an interface that allows users to identify the link to the tokens metadata.
2.4.4. Events
- Transfer—This event is triggered when ownership of an NFT is changed from one user to another. It describes which account transferred and received the token and the token ID that was transferred.
- Approve—This event is triggered when the approve function is executed. It describes which account currently owns the token, which account is approved to take ownership in the future, and the token ID that is approved to have its ownership transferred.
2.5. Social Media
3. Proposed Solution: Digital Identity
- Authentication
- NFT Linkage
- NFT Lookup Functionality
- Limitations
- Express—A framework that runs within Node.js and allows developers to create and maintain servers;
- React—A JavaScript library used for building user interfaces;
- Node.js—An open-source, cross-platform JavaScript runtime environment;
- Passport.js—An authentication middleware for Node.js.
3.1. Authentication
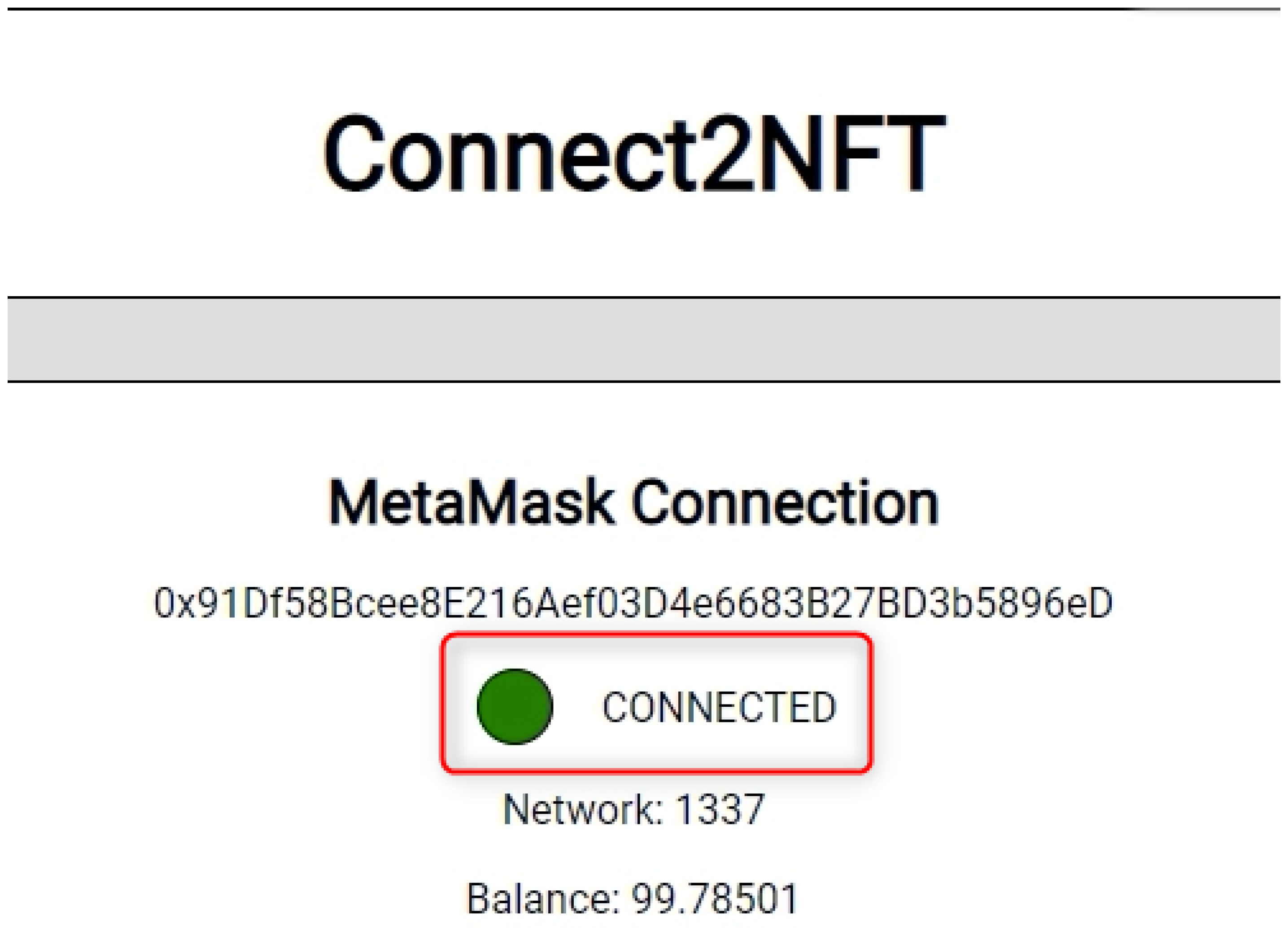
3.1.1. Connect to Digital Wallet
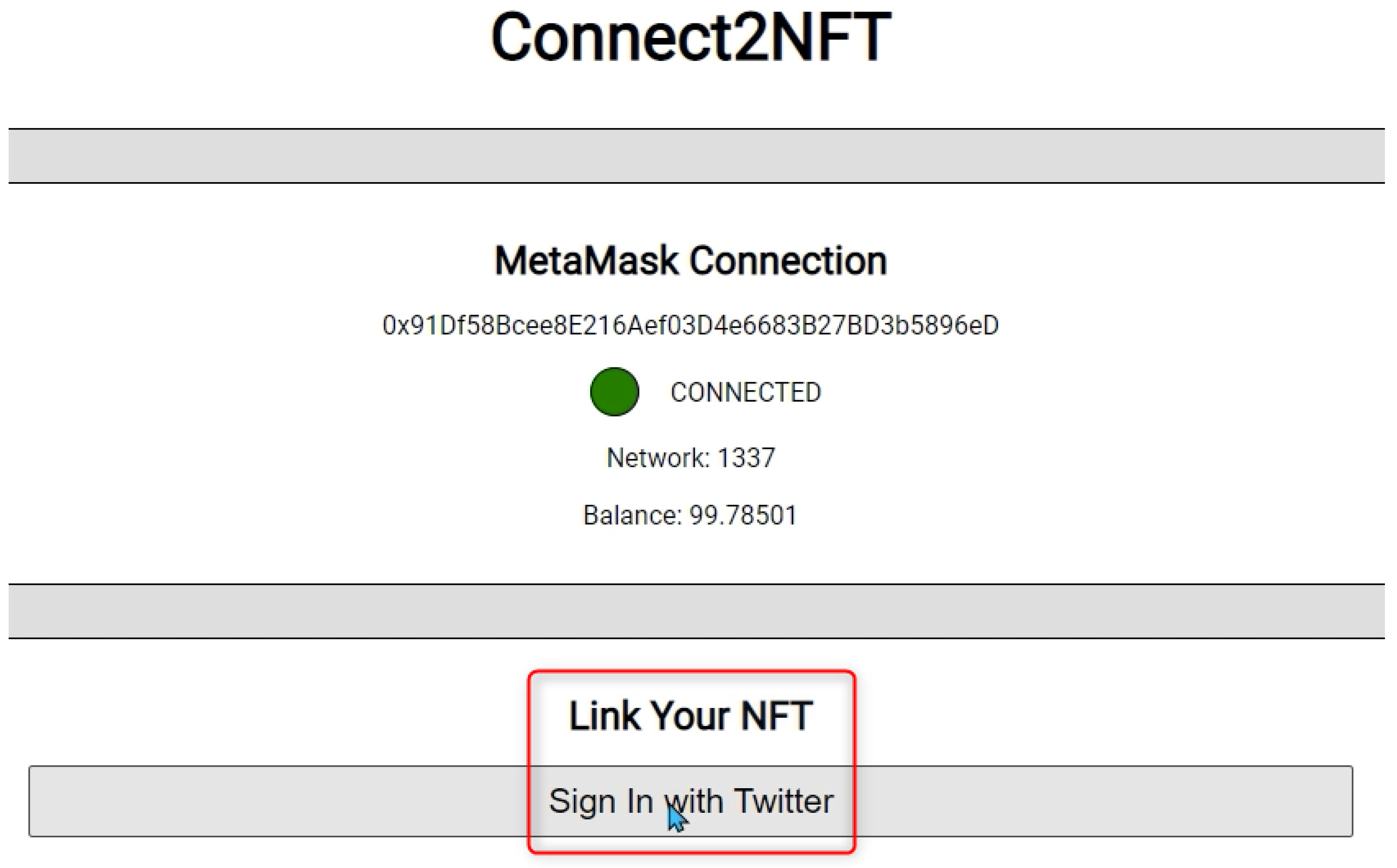
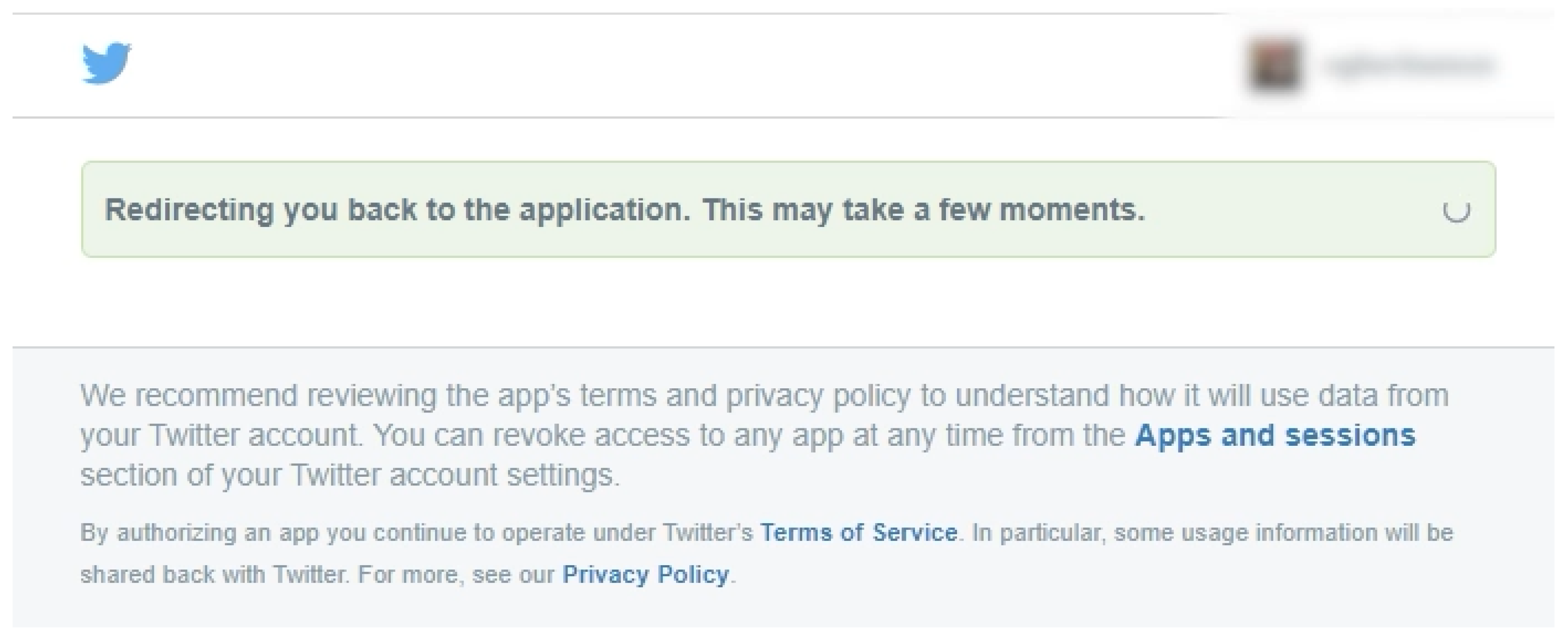
3.1.2. Login to Twitter
3.2. NFT Linkage
3.2.1. NFT Selection
3.2.2. NFT Connection
3.3. NFT Lookup Functionality
3.4. Limitations
3.5. Future Development
- MetaMask connection and authentication;
- Twitter connection and authentication;
- Display user NFTs;
- Link NFT smart contract;
- Link verification;
- Display badge if user is the NFT creator.
- NFT transfers;
- NFT explorer;
- Unlink functionality;
- Front-end design and implementation;
- Mobile responsiveness;
- Smart contract testing;
- Live deployment.
4. Proposed Solution: Data Storage
4.1. Verifiable Credentials
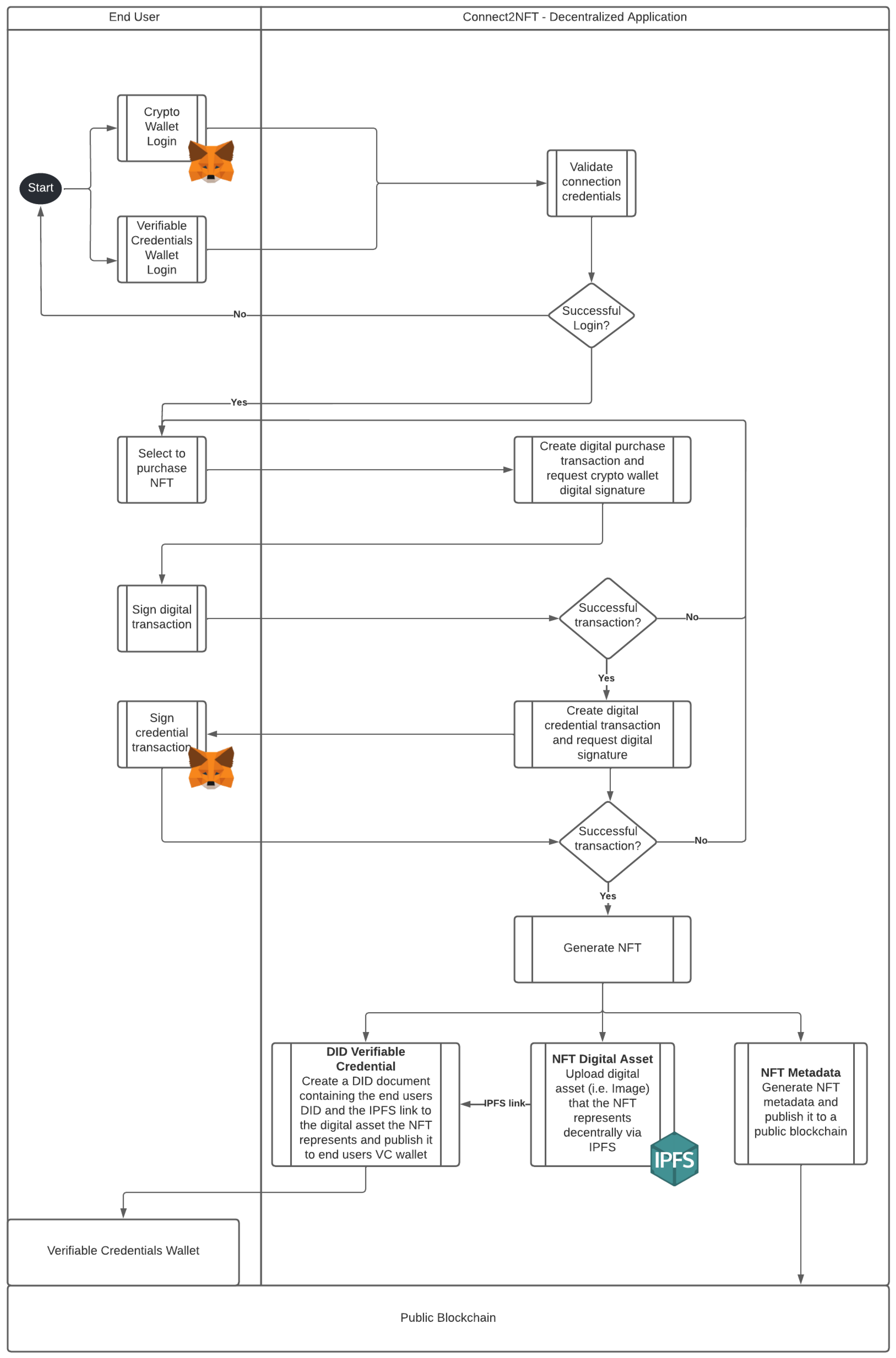
- An end user will gain access to the decentralized application (DApp) through a mandatory dual login. The first login will require the end user to connect to their cryptocurrency wallet of choice. MetaMask has been used for this example. The DApp will authenticate and validate the user’s credentials using the digital provider’s (in this case, MetaMask) cryptographically secured login flow. The second mandatory login path requires the end user to connect to their decentralized identifier’s (DID) managing platform for verifiable credentials issuing, management, and verification. The DApp will authenticate and validate the user’s credentials using the digital provider’s secured login flow.
- Once a successful login is obtained, the end user can choose to purchase an NFT from the DApps NFT offerings.
- Once an NFT has been selected, two digital transactions will take place that require the digital signature of both parties involved. The first transaction is the transfer of the NFT from the seller and current holder (DApp) to the buyer and future holder (end user). This transaction entails deducting the listed price of the NFT from the end user’s MetaMask wallet balance. The second transaction is the creation of a digital credential transaction that will be issued by DApp, creating a verifiable credential for the end user.
- If the above two transactions are successfully processed, the NFT will then be minted on the DApp platform. This entails executing an underlying NFT smart contract and thus creating a JSON file containing the mandatory metadata, such as the NFT name, description, and the URL to the location of the digital asset that the NFT represents. However, instead of including a general URL as is usually the case, the digital asset will be automatically uploaded in a decentralized manner via IPFS, and the content identifier or CID will be added to the DID document created. A DID URL is then generated and added to the metadata of the NFT on-chain. A DID URL is a network location identifier for specific resources, such as DID subjects or DID documents.
- Once the NFT has been issued, the end user will now have two artifacts in their possession. The first is the NFT metadata that reside on-chain, including the DID URL linking to the credential issued in relation to the NFT, which is stored in the end user’s verifiable credentials wallet. The second artifact is the digital asset the NFT represents, which will be stored off-chain via IPFS.
- If an NFT is transferred to another user, the underlying smart contract contained within the NFT will revoke the verifiable credential connected the NFT that is held by the seller and re-issue it to the verifiable credential wallet of the buyer.
4.2. Centralized Storage
4.3. IPFS
4.4. Decentralized Storage
5. Smart Contract Testing
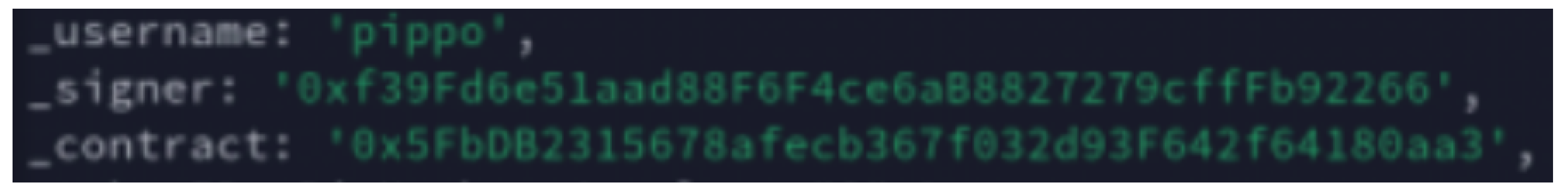
- Twitter user name: “username”;
- NFT holders digital address: “signer”;
- NFT token address: “contract”.
6. Comparison and Discussion
- Acquire the data—Thorough research was conducted to determine which existing solutions and a developed proposed solution could potentially address the research question presented.
- Establish criteria for comparison—The following categories have been determined as the main analysis factors in determining if the solution supports the detailed hypotheses. These criteria aspects were determined through an iterative walkthrough comparison of each existing and proposed solution as part of the case study.
- Analyze the data—A walkthrough study was performed of each existing solution and of the proposed solution that was designed and/or developed.
- Conclusion—A conclusion is drawn in Section 6 for the case study comparison. Furthermore, future research points are detailed.
6.1. Proposed Solution: Digital Identity
6.1.1. Control
6.1.2. Provability
6.1.3. Transparency
6.1.4. Range
6.1.5. Security
6.1.6. Tamper-Proofness
6.1.7. Privacy
6.1.8. Scalability
6.1.9. Cost
6.2. Proposed Solution: Data Storage
6.2.1. Longevity, Control
6.2.2. Provability
6.2.3. Transparency, Portability, Tamper-Proofness
6.2.4. Scalability
6.2.5. Cost
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| NFT | Non-fungible Token |
| VC | Verifiable Credentials |
| IoT | Internet of Things |
| DID | Decentralized Identifier |
| IPFS | InterPlanetary File System |
| USD | United States Dollar |
| RQ | Research Question |
| RP | Research Proposition |
| H | Hypothesis |
References
- Verifiable Credentials Data Model v1.1. Available online: https://www.w3.org/TR/vc-data-model/ (accessed on 3 March 2022).
- Wang, Q.; Li, R.; Wang, Q.; Chen, S. Non-fungible token (NFT): Overview, evaluation, opportunities and challenges. arXiv 2021, arXiv:2105.07447. [Google Scholar]
- IBM. Why New Off-Chain Storage Is Required for Blockchains Document, version 1.0; IBM: Armonk, NY, USA, 2018. [Google Scholar]
- NFTs Have a Huge Persistence Problem. Available online: https://futurism.com/nfts-have-huge-persistence-problem (accessed on 3 March 2022).
- Kumar, R.; Marchang, N.; Tripathi, R. Distributed Off-Chain Storage of Patient Diagnostic Reports in Healthcare System Using IPFS and Blockchain. In Proceedings of the 2020 International Conference on COMmunication Systems NETworkS (COMSNETS), Bangalore, India, 7 January 2020. [Google Scholar]
- Kumar, S.; Bharti, A.K.; Amin, R. Decentralized Secure Storage of Medical Records Using Blockchain and IPFS: A Comparative Analysis with Future Directions. 2021. Available online: https://onlinelibrary.wiley.com/doi/abs/10.1002/spy2.162 (accessed on 3 March 2022).
- Sangaiah, A.K.; Javadpour, A.; Ja’fari, F.; Pinto, P.; Zhang, W. A hybrid heuristics artificial intelligence feature selection for intrusion detection classifiers in cloud of things. Clust. Comput. 2022. [Google Scholar] [CrossRef]
- Arenas, R.; Fernandez, P. CredenceLedger: A Permissioned Blockchain for Verifiable Academic Credentials. In Proceedings of the 2018 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, 17 June 2018. [Google Scholar]
- LaGuardia, A.M. NFT—Friend or Foe of Today’s Art Market? 2021. Available online: https://digitalcommons.sia.edu/stu_theses/104/ (accessed on 4 April 2022).
- Yin, J.; Xiao, Y.; Pei, Q.; Ju, Y.; Liu, L.; Xiao, M.; Wu, C. SmartDID: A Novel Privacy-preserving Identity based on Blockchain for IoT. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Shekar, M.C.; Gururaj, H.L.; Flammini, F. Securing personal identity using blockchain. Int. J. Crit. Comput.-Based Syst. 2022, 10, 248–267. [Google Scholar] [CrossRef]
- Chiacchio, F.; D’Urso, D.; Oliveri, L.M.; Spitaleri, A.; Spampinato, C.; Giordano, D. A Non-Fungible Token Solution for the Track and Trace of Pharmaceutical Supply Chain. Appl. Sci. 2022, 12, 4019. [Google Scholar] [CrossRef]
- Twitter Users Can Now Add Verified NFTs as Profile Photos. Available online: https://www.bloomberg.com/news/articles/2022-01-20/twitter-users-can-now-add-verified-nfts-as-profile-photos (accessed on 4 April 2022).
- Bamakan, S.M.H.; Nezhadsistani, N.; Bodaghi, O.; Qu, Q. A Decentralized Framework for Patents and Intellectual Property as NFT in Blockchain Networks. Res. Sq. 2021. [Google Scholar] [CrossRef]
- Link Twitter to your Domain! Available online: https://unstoppabledomains.com/chainlink (accessed on 17 April 2022).
- Posavec, A.B.; Aleksić-Maslać, K.; Tominac, M. Non-Fungible Tokens: Might Learning About Them Be Necessary? In Proceedings of the 2022 45th Jubilee International Convention on Information, Communication and Electronic Technology (MIPRO), Opatija, Croatia, 23–27 May 2022. [Google Scholar]
- Understanding the Verifiable Credentials (VCs). Available online: https://hackernoon.com/understanding-the-verifiable-credentials-vcs-it1535e9 (accessed on 5 August 2022).
- Chirtoaca, D.; Ellul, J.; Azzopardi, G. A framework for creating deployable smart contracts for non-fungible tokens on the Ethereum blockchain. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3 August 2020. [Google Scholar]
- ERC-721 Non-Fungible Token Standard. Available online: https://ethereum.org/en/developers/docs/standards/tokens/erc-721 (accessed on 27 May 2022).
- What Is Social Media. Available online: https://www.antonymayfield.com/2006/09/27/social-media-ebook/ (accessed on 10 April 2022).
- Social Media—Statistics & Facts. Available online: https://www.statista.com/topics/1164/social-networks (accessed on 10 April 2022).
- Social Media’s Growing Impact on Our Lives. Available online: https://www.apa.org/members/content/social-media-research (accessed on 10 April 2022).
- Uğur, G. The Effect of Social Media on Identity Construction. Mediterr. J. Soc. Sci. 2017, 8, 85. [Google Scholar]
- Cheesman, M. Self-Sovereignty for Refugees? The Contested Horizons of Digital Identity. Geopolitics 2022, 27, 134–159. [Google Scholar] [CrossRef]
- Barsaiyan, S.; Sijoria, C. Twitter Blue Tick—A Study of its Impact on Society. Indian J. Mark. 2021, 51, 38–52. [Google Scholar] [CrossRef]
- Kirabo, L.; Namara, M.; Mcneese, N. The Power of the Blue Tick (): Ugandans’ experiences and engagement on Twitter at the onset of the COVID-19 pandemic. In Proceedings of the 3rd African Human-Computer Interaction Conference: Inclusiveness and Empowerment, Maputo, Mozambique, 8–12 March 2021; pp. 84–93. [Google Scholar]
- The Storage Method of NFT Artworks That You Can’t Ignore. Available online: https://www.fio.one/2021/10/25/the-storage-method-of-nft-artworks-that-you-cant-ignore/ (accessed on 27 May 2022).
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656. [Google Scholar] [CrossRef]
- Arweave Wiki. Available online: https://arwiki.wiki/#/en/main (accessed on 29 April 2022).
- Mocha. Available online: https://mochajs.org/ (accessed on 2 October 2022).
- Brereton, P.; Kitchenham, B.A.; Budgen, D. Using a protocol template for case study planning. In Proceedings of the 12th International Conference on Evaluation and Assessment in Software Engineering, Bari, Italy, 26–27 June 2008. [Google Scholar]
- How to Buy LINK Directly from Your Wallet. Available online: https://unstoppabledomains.freshdesk.com/support/solutions/articles/48001199959-how-to-buy-link-directly-from-your-wallet (accessed on 27 May 2022).
- Introducing Twitter Blue—Twitter’s First-Ever Subscription Offering. Available online: https://help.twitter.com/en/using-twitter/twitter-blue (accessed on 2 June 2022).
- IPFS Gateway. Available online: https://docs.ipfs.io/concepts/ipfs-gateway/#overview (accessed on 17 April 2022).
- IPFS + Arweave. Available online: https://ipfs2arweave.com/ (accessed on 29 April 2022).
- What’s the Real Cost of IPFS? Available online: https://medium.com/pinata/whats-the-real-cost-of-ipfs-3623f274cfaa (accessed on 15 May 2022).
- Google One Plans. Available online: https://one.google.com/about/plans (accessed on 15 May 2022).
- Dropbox Plan Comparison. Available online: https://www.dropbox.com/individual/plans-comparison (accessed on 15 May 2022).
- Understanding Decentralized IDs (DIDs). Available online: https://medium.com/@adam-14796/understanding-decentralized-ids-dids-839798b91809 (accessed on 15 May 2022).





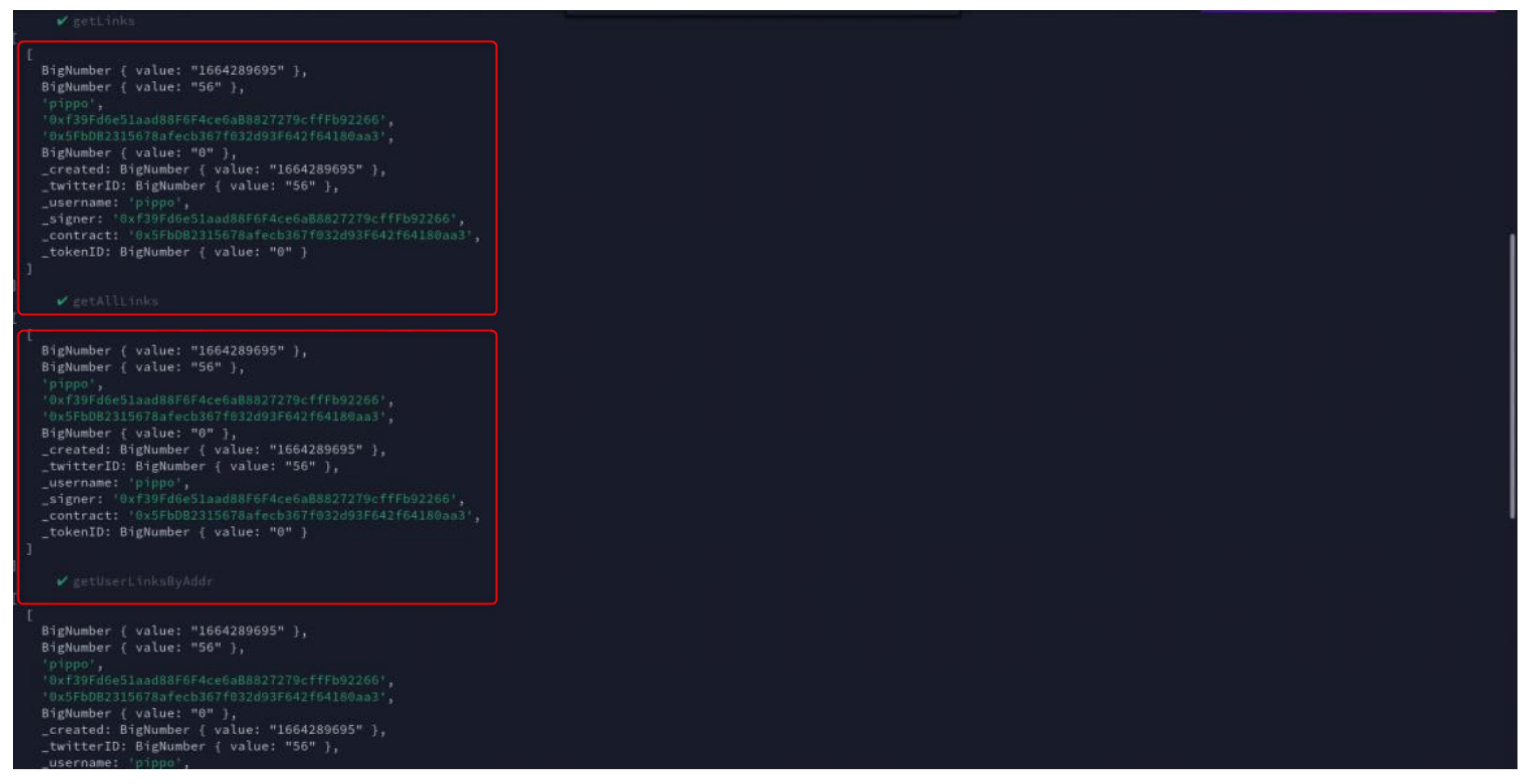


| Array | Pass or Fail |
|---|---|
| getLink | Pass |
| getLinks | Pass |
| getAllLinks | Pass |
| getUserLinksByAddr | Pass |
| getUserLinksByID | Pass |
| Remove | Fail |
| Characteristic | Proposed Solution | Unstoppable Domains/Chainlink NFT Tool | Twitter NFT Tool |
|---|---|---|---|
| Control | Y | Y | Y |
| Provability | Y | Y | N |
| Transparency | Y | N | N |
| Range | Y | N | Y |
| Security | Y | Y | Y |
| Tamper-proofness | Y | Y | Y |
| Privacy | Y | Y | Y |
| Scalability | Y | Y | Y |
| Cost | 0.0138 Ethereum (USD 40) | 3.17 Chainlink (USD 50) | USD 2.99 per month |
| Characteristic | Proposed Solution | Central | IPFS |
|---|---|---|---|
| Control | End User | Issuer | Network |
| Longevity | Y | N | Y |
| Provability | Y | N | N |
| Transparency | Y | Y | Y |
| Portability | Y | Y | Y |
| Tamper-proofness | Y | Y | Y |
| Scalability | Y | Y | Y |
| Cost | Minimal gas fees and USD 0.15 per GB | USD 9.99 per month per Terabyte | USD 0.15 per GB |
| Characteristic | Proposed Solution | Decentralized Storage (i.e., Arweave) |
|---|---|---|
| Control | End User | Network |
| Longevity | Y | Y |
| Provability | Y | N |
| Transparency | Y | Y |
| Portability | Y | Y |
| Tamper-proofness | Y | Y |
| Scalability | Y | Y |
| Cost | Minimal gas fees and USD 0.15 per GB | USD 0.05 per MB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bellagarda, J.; Abu-Mahfouz, A.M. Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity. Mathematics 2022, 10, 3934. https://doi.org/10.3390/math10213934
Bellagarda J, Abu-Mahfouz AM. Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity. Mathematics. 2022; 10(21):3934. https://doi.org/10.3390/math10213934
Chicago/Turabian StyleBellagarda, Jagger, and Adnan M. Abu-Mahfouz. 2022. "Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity" Mathematics 10, no. 21: 3934. https://doi.org/10.3390/math10213934
APA StyleBellagarda, J., & Abu-Mahfouz, A. M. (2022). Connect2NFT: A Web-Based, Blockchain Enabled NFT Application with the Aim of Reducing Fraud and Ensuring Authenticated Social, Non-Human Verified Digital Identity. Mathematics, 10(21), 3934. https://doi.org/10.3390/math10213934







