A Hybrid Delay Aware Clustered Routing Approach Using Aquila Optimizer and Firefly Algorithm in Internet of Things
Abstract
:1. Introduction
- Recreating and emphasizing the AO algorithm’s distinctive features;
- Using the AO approach, we provide a solution to the IoT’s cluster-based routing problem;
- Highlighting the salient features of the FA algorithm and discussing them in detail;
- Multi-hop routing using the FA algorithm for improved power usage and throughput;
- Investigating how efficient clustered routing is.
2. Literature Review
3. The Proposed Mechanism
3.1. System Model
- The IoT devices are scattered around in a random pattern.
- Starting power is the same for all IoT nodes.
- BS is installed constantly in the core of the system.
- Endless battery life and storage space are two of the BS’s many perks.
- Each and every cluster has exactly one node in the CH.
- All connections have plenty of available bandwidth.
3.2. Problem Declaration
3.3. AO Algorithm
3.4. Clustering STEP
3.5. FA Algorithm
- ✓
- Fireflies are unisexual. This indicates that fireflies are interested in one another regardless of their sex [36].
- ✓
- Their luminosity determines the appeal of fireflies. It indicates that fewer brilliant fireflies are drawn to more brilliant fireflies. As the space among fireflies grows, so does their desirability. In the absence of a more brilliant firefly, the motion of fireflies is arbitrary.
- ✓
- A function for measuring the luminosity of fireflies is created.
3.6. Communication Step
4. Performance Review
4.1. Simulator
- ▪
- Its designs are more adaptable than those of rival software.
- ▪
- Making use of an extensive range of resources in a unified way.
- ▪
- As a result of its compatibility with other programming languages, it is simple to debug.
- ▪
- The ability to scale as well as flexibility for multiple layers is intrinsic [43].
4.2. Model Parameters
4.3. Evaluation Metrics
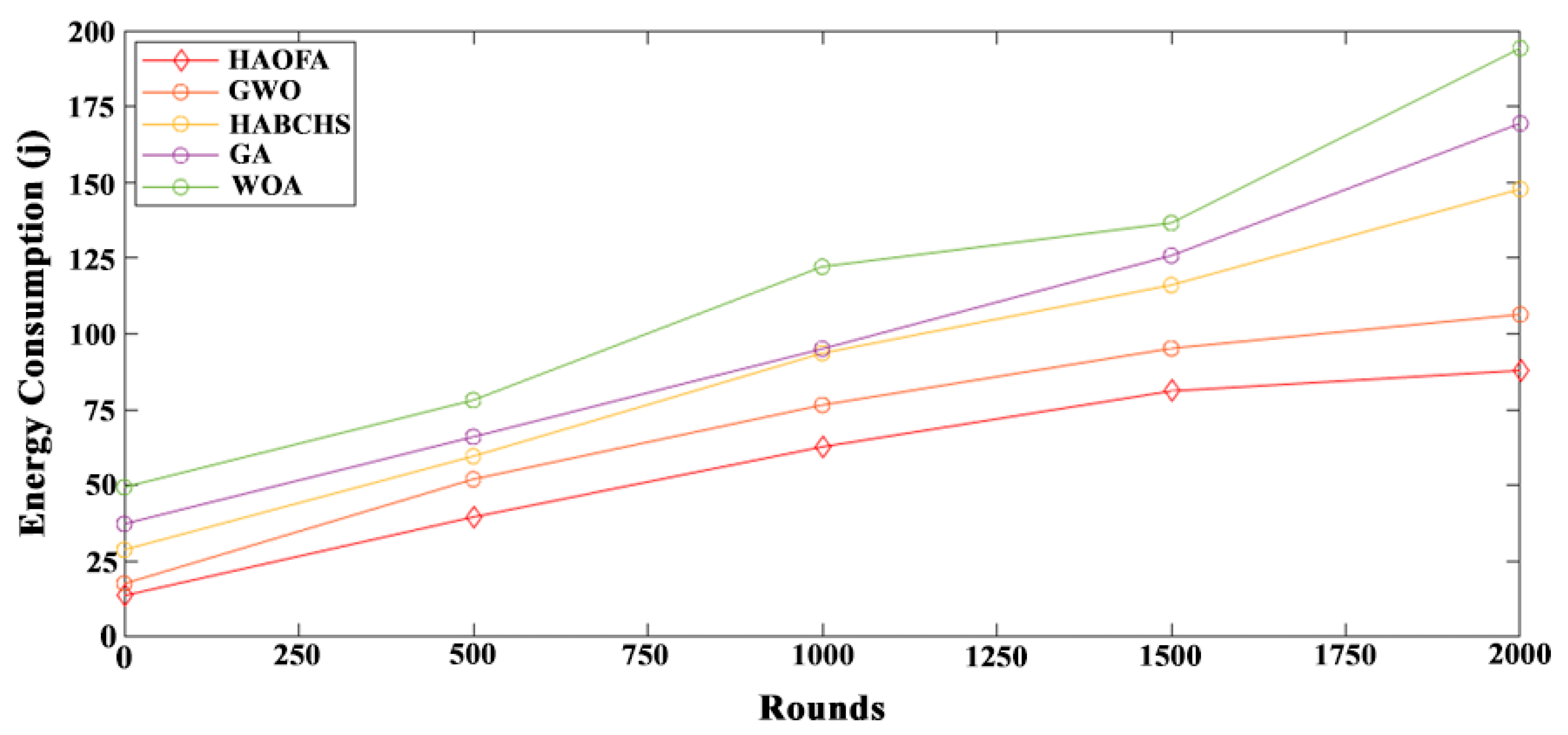
4.3.1. Energy Consumption
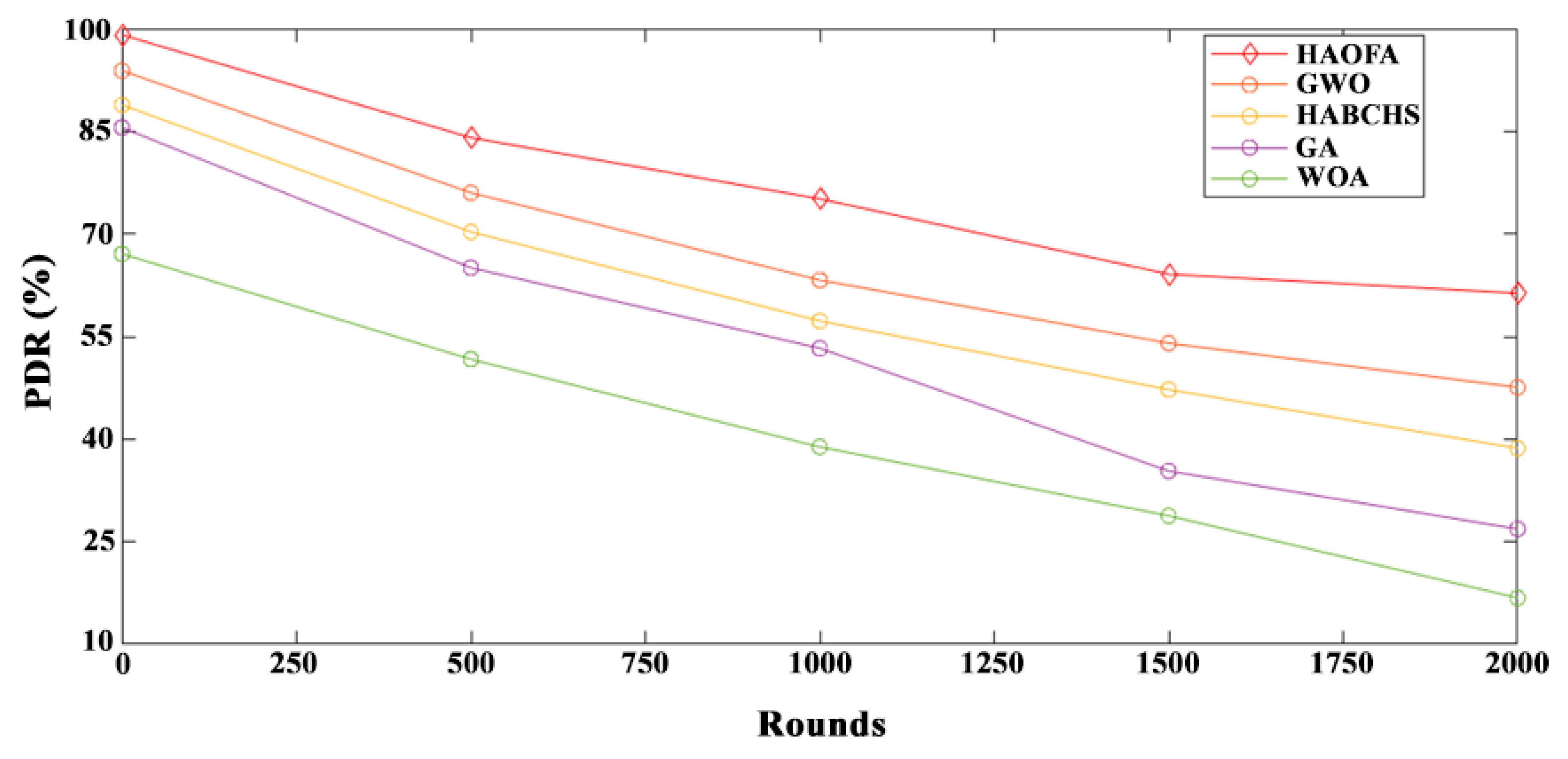
4.3.2. PDR
4.3.3. E2E Delay
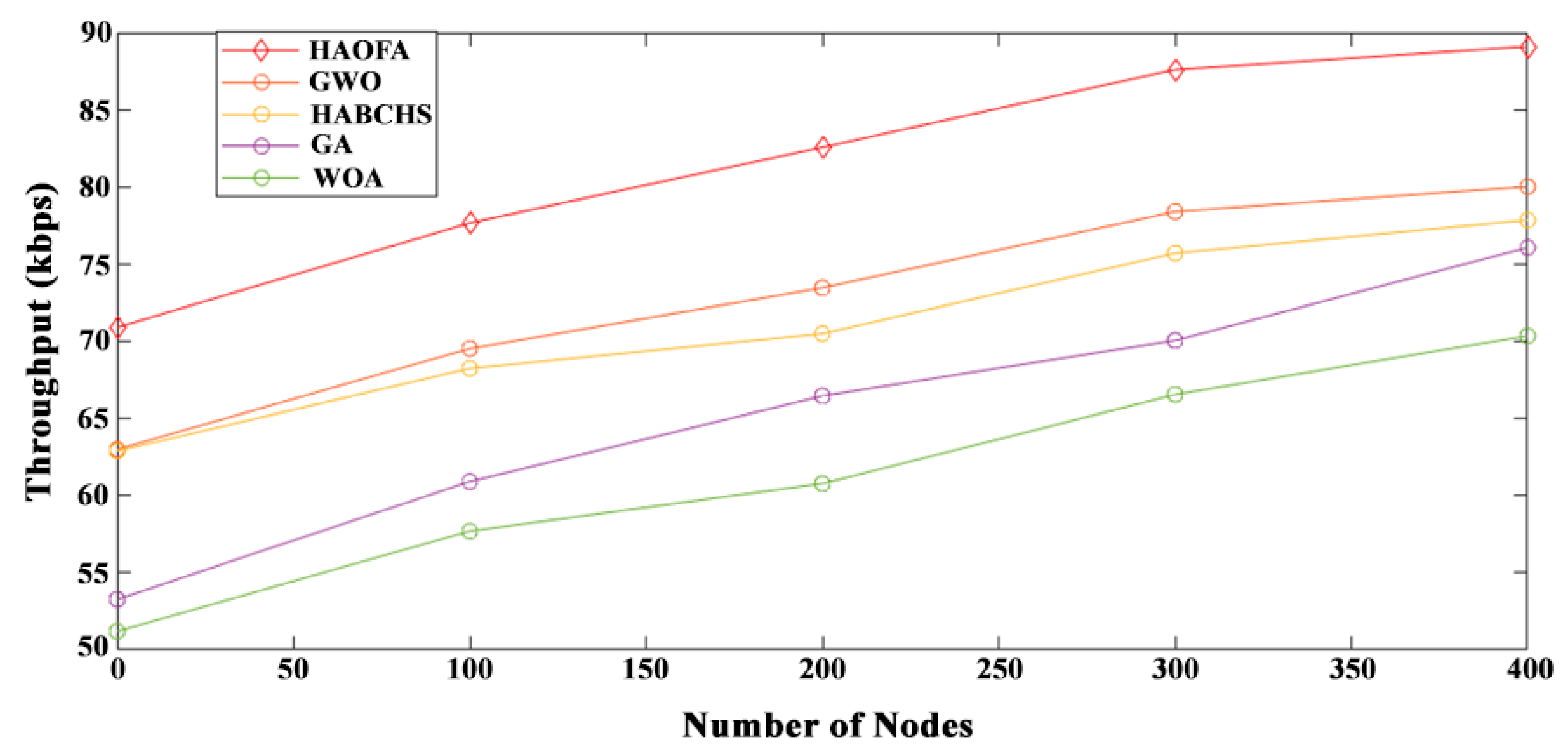
4.3.4. Throughput
5. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lansky, J.; Sadrishojaei, M.; Rahmani, A.M.; Malik, M.H.; Kazemian, F.; Hosseinzadeh, M. Development of a Lightweight Centralized Authentication Mechanism for the Internet of Things Driven by Fog. Mathematics 2022, 10, 4166. [Google Scholar] [CrossRef]
- Sadrishojaei, M.; Navimipour, N.J.; Reshadi, M.; Hosseinzadeh, M. An Energy-Aware IoT Routing Approach Based on a Swarm Optimization Algorithm and a Clustering Technique. Wirel. Pers. Commun. 2022, 1–17. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Naqvi, R.A.; Malik, M.H.; Malik, T.S.; Sadrishojaei, M.; Hosseinzadeh, M.; Al-Musawi, A. E-Learning Development Based on Internet of Things and Blockchain Technology during COVID-19 Pandemic. Mathematics 2021, 9, 3151. [Google Scholar] [CrossRef]
- Tamizhselvan, C.; Vijayalakshmi, V. SDN-MCHO: Software Define network based Multi-criterion Hysteresis Optimization based for reliable device routing in Internet of Things for the smart surveillance application. Comput. Commun. 2020, 153, 632–640. [Google Scholar]
- Sadrishojaei, M.; Navimipour, N.J.; Reshadi, M.; Hosseinzadeh, M. A new preventive routing method based on clustering and location prediction in the mobile internet of things. IEEE Internet Things J. 2021, 8, 10652–10664. [Google Scholar] [CrossRef]
- Shang, X.; Che, X. Optimization of fitness data monitoring system based on Internet of Things and cloud computing. Comput. Commun. 2021, 177, 125–132. [Google Scholar] [CrossRef]
- Ghosh, A.; Chakraborty, N. Cascaded cuckoo search optimization of router placement in signal attenuation minimization for a wireless sensor network in an indoor environment. Eng. Optim. 2019, 51, 2127–2146. [Google Scholar] [CrossRef]
- Sadrishojaei, M.; Navimipour, N.J.; Reshadi, M.; Hosseinzadeh, M. A new clustering-based routing method in the mobile internet of things using a krill herd algorithm. Clust. Comput. 2022, 25, 351–361. [Google Scholar] [CrossRef]
- Chen, Z.; Long, X.; Chen, L.; Wu, Y.; Wu, J.; Liu, S. Intra-cluster aggregation aware routing for distributed training in wireless sensor networks. Concurr. Comput. Pract. Exp. 2021, e6795. [Google Scholar] [CrossRef]
- Sadrishojaei, M.; Navimipour, N.J.; Reshadi, M.; Hosseinzadeh, M. Clustered Routing Method in the Internet of Things Using a Moth-Flame Optimization Algorithm. Int. J. Commun. Syst. 2021, 34, e4964. [Google Scholar] [CrossRef]
- Devassy, D.; Johnraja, J.I.; Paulraj, G.J.L. NBA: Novel bio-inspired algorithm for energy optimization in WSN for IoT applications. J. Supercomput. 2022 Apr 30, 1–18. [CrossRef]
- Rana, N.; Latiff, M.S.A.; Abdulhamid, S.M.; Misra, S. A hybrid whale optimization algorithm with differential evolution optimization for multi-objective virtual machine scheduling in cloud computing. Eng. Optim. 2021, 54, 1999–2016. [Google Scholar] [CrossRef]
- Rani, S.; Ahmed, S.H.; Rastogi, R. Dynamic clustering approach based on wireless sensor networks genetic algorithm for IoT applications. Wirel. Netw. 2020, 26, 2307–2316. [Google Scholar] [CrossRef]
- Dwivedi, B.; Patro, B.D.K.; Srivastava, V.; Jadon, S.S. LBR-GWO: Layered based routing approach using grey wolf optimization algorithm in wireless sensor networks. Concurr. Comput. Pract. Exp. 2022, 34, e6603. [Google Scholar] [CrossRef]
- Yousefi, S.; Derakhshan, F.; Aghdasi, H.S.; Karimipour, H. An energy-efficient artificial bee colony-based clustering in the internet of things. Comput. Electr. Eng. 2020, 86, 106733. [Google Scholar] [CrossRef]
- Singh, S.; Kumar, P. MH-CACA: Multi-objective harmony search-based coverage aware clustering algorithm in WSNs. Enterp. Inf. Syst. 2020, 14, 1325–1353. [Google Scholar] [CrossRef]
- Abualigah, L.; Yousri, D.; Elaziz, M.A.; Ewees, A.A.; Al-Qaness, M.A.; Gandomi, A.H. Aquila optimizer: A novel meta-heuristic optimization algorithm. Comput. Ind. Eng. 2021, 157, 107250. [Google Scholar] [CrossRef]
- Natesan, G.; Konda, S.; de Prado, R.P.; Wozniak, M. A Hybrid Mayfly-Aquila Optimization Algorithm Based Energy-Efficient Clustering Routing Protocol for Wireless Sensor Networks. Sensors 2022, 22, 6405. [Google Scholar] [CrossRef]
- Pakdel, H.; Fotohi, R. A firefly algorithm for power management in wireless sensor networks (WSNs). J. Supercomput. 2021, 77, 9411–9432. [Google Scholar] [CrossRef]
- Xia, B.; Zhang, L. Firefly Optimization-Based Cooperative Localization Algorithm for Intelligent IoT. Discret. Dyn. Nat. Soc. 2022, 2022, 3398071. [Google Scholar]
- Sennan, S.; Somula, R.; Luhach, A.K.; Deverajan, G.G.; Alnumay, W.; Jhanjhi, N.Z. Energy efficient optimal parent selection based routing protocol for Internet of Things using firefly optimization algorithm. Trans. Emerg. Telecommun. Technol. 2021, 32, e4171. [Google Scholar] [CrossRef]
- Ilyas, M.; Ullah, Z.; Alam Khan, F.; Chaudary, M.H.; Malik, M.S.A.; Zaheer, Z.; Durrani, H.U.R. Trust-based energy-efficient routing protocol for Internet of things–based sensor networks. Int. J. Distrib. Sens. Netw. 2020, 16, 1550147720964358. [Google Scholar] [CrossRef]
- Behera, T.M.; Mohapatra, S.K. A novel scheme for mitigation of energy hole problem in wireless sensor network for military application. Int. J. Commun. Syst. 2021, 34, e4886. [Google Scholar] [CrossRef]
- Sadrishojaei, M.; Navimipour, N.J.; Reshadi, M.; Hosseinzadeh, M.; Unal, M. An energy-aware clustering method in the IoT using a swarm-based algorithm. Wirel. Netw. 2022, 28, 125–136. [Google Scholar] [CrossRef]
- Hriez, S.; Almajali, S.; Elgala, H.; Ayyash, M.; Salameh, H.B. A Novel Trust-Aware and Energy-Aware Clustering Method That Uses Stochastic Fractal Search in IoT-Enabled Wireless Sensor Networks. IEEE Syst. J. 2021, 16, 2693–2704. [Google Scholar] [CrossRef]
- Amutha, S.; Kannan, B.; Kanagaraj, M. Energy-efficient cluster manager-based cluster head selection technique for communication networks. Int. J. Commun. Syst. 2020, 34, e4741. [Google Scholar] [CrossRef]
- Saxena, S.; Mehta, D. An Adaptive Fuzzy-Based Clustering and Bio-Inspired Energy Efficient Hierarchical Routing Protocol for Wireless Sensor Networks. Wirel. Pers. Commun. 2021, 120, 2887–2906. [Google Scholar] [CrossRef]
- Ahmad, M.; Ikram, A.A.; Wahid, I.; Ullah, F.; Ahmad, A.; Alam Khan, F. Optimized clustering in vehicular ad hoc networks based on honey bee and genetic algorithm for internet of things. Peer Peer Netw. Appl. 2020, 13, 532–547. [Google Scholar] [CrossRef]
- Xiuwu, Y.; Ying, L.; Yong, L.; Hao, Y. WSN Clustering Routing Algorithm Based on Hybrid Genetic Tabu Search. Wirel. Pers. Commun. 2022, 124, 3485–3506. [Google Scholar] [CrossRef]
- Poluru, R.K.; R, L.K. An improved fruit fly optimization (IFFOA) based cluster head selection algorithm for internet of things. Int. J. Comput. Appl. 2021, 43, 623–631. [Google Scholar] [CrossRef]
- Jayalakshmi, P.; Sridevi, S.; Janakiraman, S. A hybrid artificial bee colony and harmony search algorithm-based metahueristic approach for efficient routing in WSNs. Wirel. Pers. Commun. 2021, 121, 3263–3279. [Google Scholar] [CrossRef]
- Agrawal, D.; Pandey, S. Optimization of the selection of cluster-head using fuzzy logic and harmony search in wireless sensor networks. Int. J. Commun. Syst. 2021, 34, e4391. [Google Scholar] [CrossRef]
- Abualigah, L.; Elaziz, M.A.; Khodadadi, N.; Forestiero, A.; Jia, H.; Gandomi, A.H. Aquila Optimizer Based PSO Swarm Intelligence for IoT Task Scheduling Application in Cloud Computing. In Integrating Meta-Heuristics and Machine Learning for Real-World Optimization Problems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 481–497. [Google Scholar]
- Perumalla, S.; Chatterjee, S.; Kumar, A.S. Modelling of oppositional Aquila Optimizer with machine learning enabled secure access control in Internet of drones environment. Theor. Comput. Sci. 2022. [Google Scholar] [CrossRef]
- Faheem, M.; Butt, R.A.; Raza, B.; Alquhayz, H.; Ashraf, M.W.; Raza, S.; Bin Ngadi, A. FFRP: Dynamic firefly mating optimization inspired energy efficient routing protocol for internet of underwater wireless sensor networks. IEEE Access 2020, 8, 39587–39604. [Google Scholar] [CrossRef]
- Zier, A.; Abouaissa, A.; Lorenz, P. FIRP: Firefly Inspired Routing Protocol for Future Internet of Things. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 2948–2953. [Google Scholar]
- Meena, N.; Singh, B. Firefly optimization based hierarchical clustering algorithm in wireless sensor network. J. Discret. Math. Sci. Cryptogr. 2021, 24, 1717–1725. [Google Scholar] [CrossRef]
- Idrees, A.K.; Couturier, R. Energy-saving distributed monitoring-based firefly algorithm in wireless sensors networks. J. Supercomput. 2022, 78, 2072–2097. [Google Scholar] [CrossRef]
- Ali, S.; Kumar, R. Hybrid energy efficient network using firefly algorithm, PR-PEGASIS and ADC-ANN in WSN. Sens. Int. 2022, 3, 100154. [Google Scholar] [CrossRef]
- Reddy, M.P.K.; Babu, M.R. Implementing self adaptiveness in whale optimization for cluster head section in Internet of Things. Clust. Comput. 2019, 22, 1361–1372. [Google Scholar] [CrossRef]
- Jaiswal, K.; Anand, V. A grey-wolf based optimized clustering approach to improve qos in wireless sensor networks for iot applications. Peer Peer Netw. Appl. 2021, 14, 1943–1962. [Google Scholar] [CrossRef]
- Riley, G.F.; Henderson, T.R. The ns-3 network simulator. In Modeling and Tools for Network Simulation; Springer: Berlin/Heidelberg, Germany, 2010; pp. 15–34. [Google Scholar]
- Carneiro, G. NS-3: Network Simulator 3. UTM Lab Meeting April. 2010, Volume 20, pp. 4–5. Available online: https://www.researchgate.net/file.PostFileLoader.html?id=57847c9ccbd5c2b8361a0599&assetKey=AS%3A382893969952770%401468300444552 (accessed on 15 August 2022).

| Mechanism | Approach | Advantage | Weakness |
|---|---|---|---|
| Hriez, Almajali [25] | Trust-based technique for clustering that can identify compromised nodes. |
|
|
| Amutha, Kannan [26] | Electing the CH node depending on the cluster manager |
|
|
| Saxena and Mehta [27] | Multi-criteria decision-making with fuzzy logic |
|
|
| Ahmad, Ikram [28] | Hybrid optimization method using GA and honey bee approach |
|
|
| Xiuwu, Ying [29] | Clustering mechanism using a hybrid form of genetic tabu search |
|
|
| Poluru and Kumar R [30] | Fruit fly optimization method for picking CH nodes |
|
|
| Jayalakshmi, Sridevi [31] | Combining the HS technique with the ABC strategy for clustering |
|
|
| Agrawal and Pandey [32] | Algorithm for clustering based on fuzzy logic and HS |
|
|
| Parameter Title | Value |
|---|---|
| Radius | 500 m |
| Count of all Nodes | 400 |
| Placement of BS | (250, 250) |
| Size of Data packet | 1024 byte |
| Primary Nodes Power | 0.5 J |
| 50 nJ/bit | |
| 10 pJ/bit/m2 | |
| 0.0013 pJ/bit/m4 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hosseinzadeh, M.; Ionescu-Feleaga, L.; Ionescu, B.-Ș.; Sadrishojaei, M.; Kazemian, F.; Rahmani, A.M.; Khan, F. A Hybrid Delay Aware Clustered Routing Approach Using Aquila Optimizer and Firefly Algorithm in Internet of Things. Mathematics 2022, 10, 4331. https://doi.org/10.3390/math10224331
Hosseinzadeh M, Ionescu-Feleaga L, Ionescu B-Ș, Sadrishojaei M, Kazemian F, Rahmani AM, Khan F. A Hybrid Delay Aware Clustered Routing Approach Using Aquila Optimizer and Firefly Algorithm in Internet of Things. Mathematics. 2022; 10(22):4331. https://doi.org/10.3390/math10224331
Chicago/Turabian StyleHosseinzadeh, Mehdi, Liliana Ionescu-Feleaga, Bogdan-Ștefan Ionescu, Mahyar Sadrishojaei, Faeze Kazemian, Amir Masoud Rahmani, and Faheem Khan. 2022. "A Hybrid Delay Aware Clustered Routing Approach Using Aquila Optimizer and Firefly Algorithm in Internet of Things" Mathematics 10, no. 22: 4331. https://doi.org/10.3390/math10224331
APA StyleHosseinzadeh, M., Ionescu-Feleaga, L., Ionescu, B.-Ș., Sadrishojaei, M., Kazemian, F., Rahmani, A. M., & Khan, F. (2022). A Hybrid Delay Aware Clustered Routing Approach Using Aquila Optimizer and Firefly Algorithm in Internet of Things. Mathematics, 10(22), 4331. https://doi.org/10.3390/math10224331







