Military Applications of Machine Learning: A Bibliometric Perspective
Abstract
:1. Introduction
2. Related Work
2.1. Previous Research on the Military Applications of ML
- Reviews on robotics and smart devices with military applications. We found several works on this subject, including on drones, sensors, computer vision, unmanned aerial vehicles, etc. These works have military applications, although they are not specifically developed for the military field;
- Reviews on generic ML and optimization techniques with military applications. In this category, we included several more or less generic review papers on ML and optimization techniques, but always including applications to the military field;
- Reviews on ML and optimization techniques focused on military applications. This category includes works specifically developed for the military field, and therefore can be considered as being more related to the proposals of this article.
- Military AI overview. The main AI projects and milestones carried out by the Defense Advanced Research Projects Agency (DARPA) are examined. In June 2016, the Alpha AI air combat simulation opponent pilot developed by the U.S. University of Cincinnati scored a victory over famed Air Force tactical instructor Colonel Gene Lee. As of 2018, the AI Next project included five directions: new AI capability; robust AI; anti-AI; high-performance AI and next-generation AI;
- Observation, orientation, decision and action approaches. The authors explore this approach based primarily on data and AI in the military field:
- ○
- Information fusion. In the military field, merging heterogeneous information from different sources is essential;
- ○
- Situation awareness. The perception of the existing elements in the volume of the time and space of an environment, understanding its meaning, intention with other agents and its future;
- ○
- Decision support system. Requires the participation of hybrid decision makers: humans and computers;
- ○
- Path planning. Used to avoid threats or obstacles to help commanders choose the appropriate path;
- ○
- Human–machine interface. Interrelating a mechanical element with an assistant in an ideal environment.
- Challenges and solutions of AI in a military context. The main ones found by the authors are as follows:
- ○
- Modeling of complex systems. A large amount of information is generated in a war environment. The level of intelligence can be verified and evaluated by means of a simulation system, which is quite reduced;
- ○
- Imperfect information environment. In a combat situation, the information obtained is always limited, and the authenticity of the information is not guaranteed. AI technology is not omnipotent; it must be combined with traditional technologies, such as knowledge reasoning and search and solution, in which the role of domain knowledge is indispensable.
2.2. Background of Data-Driven Architecture for Organizations
- ○
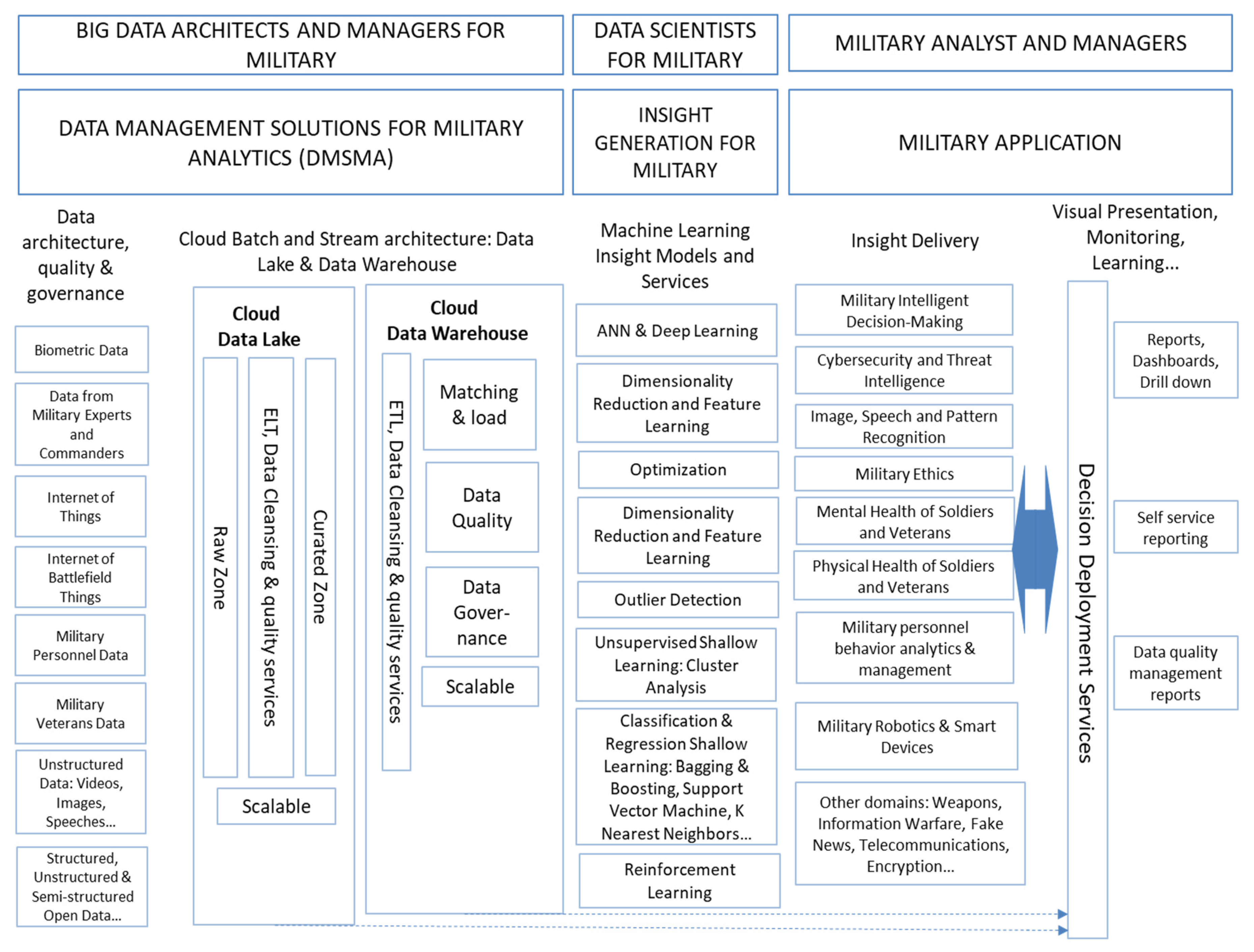
- Data management solutions for business analytics (DMSBA). Data are the essential raw materials for data-driven decision making. From them, ML algorithms will be able to find the desired knowledge in the form of patterns. In this way, we should have access to both internal and external data considered important for decision making. The format of these data can be structured (typically tables of relational databases that are manipulated with SQL), semi-structured (with structure but not tables, including NoSQL databases) or unstructured (without a defined format, such as natural language, images, video, etc.) [37,39]. A conventional organization is mainly characterized by structured internal data from its operational systems: ERP (enterprise resource planning) and CRM (customer relational management). Prior to their analysis, these data must be stored. For this purpose, there are two main types of systems: a data warehouse, mainly for structured data, and a data lake, for all other cases. Data provided by experts should also be considered in this layer, since this type of knowledge should be systematized in organizations [40];
- ○
- Insight generation for business. This is the task performed by data scientists with ML algorithms at its core. ML algorithms are classified into three main categories: supervised learning, unsupervised learning and reinforcement learning. Supervised ML uses labeled data in a certain target class, which must be learned by the algorithm. If this target variable is continuous, we would be in a case of regression, as would be the case if it is discrete in classification. Unsupervised ML works with unlabeled data by obtaining groupings of the data, association rules, dimensionality reduction, etc. Reinforcement ML considers the problem of a computational agent learning to make decisions by a trial-and-error method [39];
- ○
- Business Application. This is the task performed by data scientists with ML algorithms at its core. Using the knowledge extracted in the previous layer, the appropriate business decisions are made in this layer. Although there are many business applications, the most important ones have been identified in [38], as shown in Figure 1. A preliminary view is that many of these applications could be applicable in military fields, such as predictive analytics and intelligent decision making, cybersecurity and threat intelligence, healthcare, image, speech and pattern recognition, etc. In this layer there is a constant task of monitoring and permanent learning about the decisions taken, in order to contrast them with the business objectives.
3. Research Methodology
3.1. Set the Objectives of the Analysis
3.2. Data Extraction
3.3. Data Preprocessing
3.4. Multidimensional Analysis
- Co-authorship analysis: The relatedness of items is determined based on their number of co-authored documents;
- Citation analysis: The relatedness of items is determined based on the number of times they cite each other;
- Bibliographic coupling analysis: The relatedness of items is determined based on the number of references they share;
- Co-citation analysis: The relatedness of items is determined based on the number of times they are cited together;
- Co-occurrence analysis: The relatedness of keywords is determined on the number of documents in which they occur together. In this sense, the equivalence index is usually used [41]:
3.5. Network Extraction and Clustering
3.6. Building of the Strategy Diagram
3.7. Building of the Evolution and Overlapping Diagrams
3.8. Visualization and Interpretation of Results
3.9. Overall Results of the Analysis
4. Application of ML in the Military Context
4.1. Theme Analysis
4.2. Source Analysis
4.3. Country Analysis
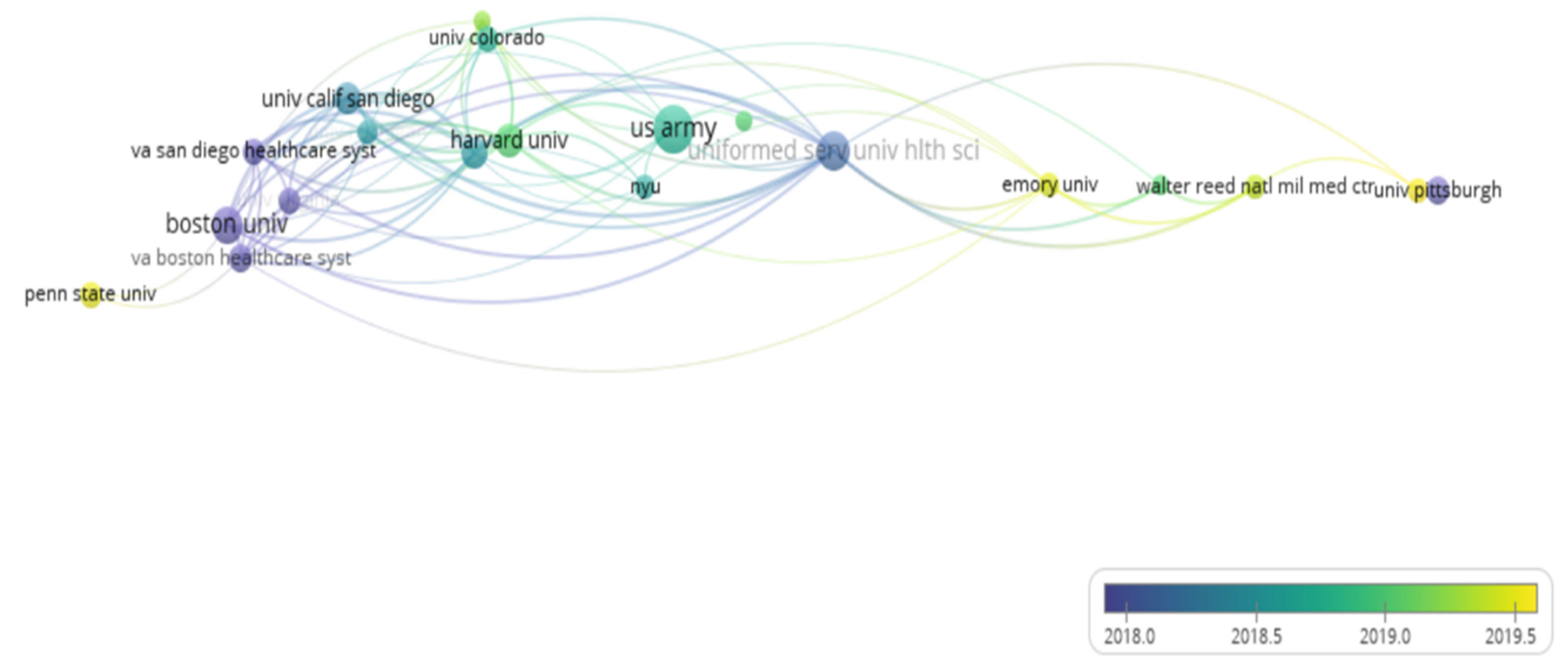
4.4. Organization Analysis
4.5. Author Analysis
4.6. Overall Results of the Analysis
- Psychological and behavioral disorders;
- Soldier analytics;
- ML and Opt techniques;
- AI, robotics and smart devices;
- Military medical studies.
5. Discussion
- –
- Data management solutions for military analytics (DMSMA). In general terms, it can be said that the data that predominate in the military context are more complex to process than those in a conventional organization. In the study we have carried out, the main sources found are biometric data, e.g., from electroencephalograms [70]; data from military experts and commanders (e.g., field assessments and weaponry needed in that particular field), which should be used in conjunction with the other data to build decision systems [35]; the Internet of things, smart and connected devices widely used by the military, generating large volumes of information over time [71], e.g., those provided by radars [72]; the Internet of battlefield things, which connects soldiers with smart technology in weapons and other objects to give troops “extra sensory powers” [73]; military personnel data, e.g., those obtained in screening interviews [74]; military veterans’ data obtained, e.g., from their administrative personal files [75]; and other data, both internal and open in any format (including videos, images and speeches), e.g., those coming from unmanned aerial vehicles [76], videos for facial recognition [77,78], data from the Internet, etc.;
- –
- Insight generation for military. The predominant ML algorithms in this layer are the so-called deep ML algorithms, since these algorithms give better results with a large volume of data and/or unstructured data [69]. These algorithms are based on neural networks [79]. If the number of layers of such a network is high, they are called deep learning, e.g., these algorithms are applied to military subjects in [72,80,81]. Deep adversarial algorithms are often used to attack other ML models and cause their failure, e.g., [82]. Another deep variant is the long short-term memory (LSTM) algorithms, which are specialized in the treatment of large-scale time series, e.g., [83]. Another type of deep network is the convolutional neural networks (CNNs) that are often used for object detection [82]. In contrast to deep algorithms, there are shallow algorithms [83]; application examples can be found in [84]. We can also find examples of clustering [85], the detection of outliers [86], optimization [87], reinforcement learning [88], etc.;
- –
- Military application. Several of these applications have already been discussed in Section 4.1. The following is a list of the most important ones: cybersecurity and threat intelligence [88]; image, speech and pattern recognition [89]; the mental health of soldiers and veterans [74]; military ethics [90]; military personnel behavior analytics and management [91,92]; military robotics and smart devices [63]; and the physical health of soldiers and veterans, etc. It is remarkable that several of these ML applications in the military field have not been identified in previous works [36].
6. Conclusions and Future Work
- The wars in Afghanistan and Iraq are coming under intense scrutiny for their mental effects on military personnel;
- Soldier analytics could become an area in its own right, as it has a lot of specificity compared to today’s people analytics;
- The area of deep learning is growing in military applications;
- There are interesting emerging topics related to AI, such as intrusion detection, brain interfaces, self-driving vehicles, false information processing, cybersecurity, etc.;
- Underlying this is an intrinsic importance in medical research that is likely to have fewer strategic constraints from governments.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, Y.; Dai, Z.; Zhang, L.; Wang, Z.; Chen, L.; Zhou, Y. Application of Artificial Intelligence in Military: From Projects View. In Proceedings of the 2020 6th International Conference on Big Data and Information Analytics (BigDIA), Shenzhen, China, 4–6 December 2020; pp. 113–116. [Google Scholar] [CrossRef]
- Pan, J.; Yi, K.; Fang, H.; Zhao, Y.; Du, K.; Liu, W. Analysis of Military Information Construction under the Background of Artificial Intelligence. E3S Web Conf. 2021, 235, 03046. [Google Scholar] [CrossRef]
- Cho, S.; Shin, W.; Kim, N.; Jeong, J.; In, H.P. Priority Determination to Apply Artificial Intelligence Technology in Military Intelligence Areas. Electronics 2020, 9, 2187. [Google Scholar] [CrossRef]
- Ajakwe, S.O.; Nwakanma, C.I.; Lee, J.M.; Kim, D.S. Machine Learning Algorithm for Intelligent Prediction for Military Logistics and Planning. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 21–23 October 2020; pp. 417–419. [Google Scholar] [CrossRef]
- Cobo, M.J.; López-Herrera, A.G.; Herrera-Viedma, E.; Herrera, F. SciMAT: A new science mapping analysis software tool. J. Am. Soc. Inf. Sci. Technol. 2012, 63, 1609–1630. [Google Scholar] [CrossRef]
- Azar, A.T.; Koubaa, A.; Mohamed, N.A.; Ibrahim, H.A.; Ibrahim, Z.F.; Kazim, M.; Ammar, A.; Benjdira, B.; Khamis, A.M.; Hameed, I.A.; et al. Drone Deep Reinforcement Learning: A Review. Electronics 2021, 10, 999. [Google Scholar] [CrossRef]
- Pundir, M.; Sandhu, J.K. A Systematic Review of Quality of Service in Wireless Sensor Networks using Machine Learning: Recent Trend and Future Vision. J. Netw. Comput. Appl. 2021, 188, 103084. [Google Scholar] [CrossRef]
- Liu, H.; Meng, G.; Deng, Z.; Li, M.; Chang, J.; Dai, T.; Fang, X. Progress in Research on VOC Molecule Recognition by Semiconductor Sensors. Acta Physico-Chim. Sin. 2020, 38, 2008018. [Google Scholar] [CrossRef]
- Mellit, A.; Kalogirou, S.A. MPPT-based artificial intelligence techniques for photovoltaic systems and its implementation into field programmable gate array chips: Review of current status and future perspectives. Energy 2014, 70, 1–21. [Google Scholar] [CrossRef]
- Wilson, A.N.; Kumar, A.; Jha, A.; Cenkeramaddi, L.R. Embedded Sensors, Communication Technologies, Computing Platforms and Machine Learning for UAVs: A Review. IEEE Sens. J. 2021, 22, 1807–1826. [Google Scholar] [CrossRef]
- Al-Kaff, A.; Martín, D.; García, F.; de la Escalera, A.; Armingol, J.M. Survey of computer vision algorithms and applications for unmanned aerial vehicles. Expert Syst. Appl. 2018, 92, 447–463. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, H.; Xue, X.; Jiang, Y.; Shen, Q. Deep learning for remote sensing image classification: A survey. WIREs Data Min. Knowl. Discov. 2018, 8, 1264. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Xin, J. Survivable Deployments of Optical Sensor Networks against Multiple Failures and Disasters: A Survey. Sensors 2019, 19, 4790. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Convertino, V.A.; Schauer, S.G.; Weitzel, E.K.; Cardin, S.; Stackle, M.E.; Talley, M.J.; Sawka, M.N.; Inan, O.T. Wearable Sensors Incorporating Compensatory Reserve Measurement for Advancing Physiological Monitoring in Critically Injured Trauma Patients. Sensors 2020, 20, 6413. [Google Scholar] [CrossRef] [PubMed]
- Martins, O.; Adekunle, A.A.; Adejuyigbe, S.B.; Adeyemi, H.O. Quantitative Performance Review of Wheeled Mobile Robot Path Planning Algorithms. GAZI Univ. J. Sci. 2021, 34, 765–784. [Google Scholar] [CrossRef]
- Banerjee, A.; Maity, S.; Mastrangelo, C.H. Nanostructures for Biosensing, with a Brief Overview on Cancer Detection, IoT, and the Role of Machine Learning in Smart Biosensors. Sensors 2021, 21, 1253. [Google Scholar] [CrossRef]
- Tian, Y.; Lan, L.; Guo, H. A review on the wavelet methods for sonar image segmentation. Int. J. Adv. Robot. Syst. 2020, 17, 1729881420936091. [Google Scholar] [CrossRef]
- Aziz, L.; Salam, M.S.B.H.; Sheikh, U.U.; Ayub, S. Exploring Deep Learning-Based Architecture, Strategies, Applications and Current Trends in Generic Object Detection: A Comprehensive Review. IEEE Access 2020, 8, 170461–170495. [Google Scholar] [CrossRef]
- Nampoothiri, M.G.; Vinayakumar, B.; Sunny, Y.; Antony, R. Recent developments in terrain identification, classification, parameter estimation for the navigation of autonomous robots. SN Appl. Sci. 2021, 3, 480. [Google Scholar] [CrossRef]
- Zhang, H.; Xin, B.; Dou, L.-H.; Chen, J.; Hirota, K. A review of cooperative path planning of an unmanned aerial vehicle group. Front. Inf. Technol. Electron. Eng. 2020, 21, 1671–1694. [Google Scholar] [CrossRef]
- Hu, W.-D.; Li, Q.; Chen, X.-S.; Lu, W. Recent progress on advanced infrared photodetectors. Acta Phys. Sin. 2019, 68, 20190281. [Google Scholar] [CrossRef]
- Degenstein, L.M.; Sameoto, D.; Hogan, J.D.; Asad, A.; Dolez, P.I. Smart Textiles for Visible and IR Camouflage Application: State-of-the-Art and Microfabrication Path Forward. Micromachines 2021, 12, 773. [Google Scholar] [CrossRef]
- de Neufville, R.; Baum, S.D. Collective action on artificial intelligence: A primer and review. Technol. Soc. 2021, 66, 101649. [Google Scholar] [CrossRef]
- Amalina, F.; Hashem, I.A.T.; Azizul, Z.H.; Fong, A.T.; Firdaus, A.; Imran, M.; Anuar, N.B. Blending Big Data Analytics: Review on Challenges and a Recent Study. IEEE Access 2019, 8, 3629–3645. [Google Scholar] [CrossRef]
- Evangelista, J.R.G.; Sassi, R.J.; Romero, M.; Napolitano, D. Systematic Literature Review to Investigate the Application of Open Source Intelligence (OSINT) with Artificial Intelligence. J. Appl. Secur. Res. 2021, 16, 345–369. [Google Scholar] [CrossRef]
- De las Heras-Rosas, C.D.L.; Herrera, J. Innovation and Competitive Intelligence in Business. A Bibliometric Analysis. Int. J. Financ. Stud. 2021, 9, 31. [Google Scholar] [CrossRef]
- Dodge, J.; Khanna, R.; Irvine, J.; Lam, K.-H.; Mai, T.; Lin, Z.; Kiddle, N.; Newman, E.; Anderson, A.; Raja, S.; et al. After-Action Review for AI (AAR/AI). ACM Trans. Interact. Intell. Syst. 2021, 11, 1–35. [Google Scholar] [CrossRef]
- Samarasinghe, D.; Barlow, M.; Lakshika, E.; Lynar, T.; Moustafa, N.; Townsend, T.; Turnbull, B. A Data Driven Review of Board Game Design and Interactions of Their Mechanics. IEEE Access 2021, 9, 114051–114069. [Google Scholar] [CrossRef]
- Khan, M.J.; Khan, H.S.; Yousaf, A.; Khurshid, K.; Abbas, A. Modern Trends in Hyperspectral Image Analysis: A Review. IEEE Access 2018, 6, 14118–14129. [Google Scholar] [CrossRef]
- Small, S.G.; Medsker, L. Review of information extraction technologies and applications. Neural Comput. Appl. 2014, 25, 533–548. [Google Scholar] [CrossRef]
- López-Robles, J.R.; Otegi-Olaso, J.R.; Gómez, I.P.; Cobo, M.J. 30 years of intelligence models in management and business: A bibliometric review. Int. J. Inf. Manag. 2019, 48, 22–38. [Google Scholar] [CrossRef]
- Miller, D.J.; Xiang, Z.; Kesidis, G. Adversarial Learning Targeting Deep Neural Network Classification: A Comprehensive Review of Defenses Against Attacks. Proc. IEEE 2020, 108, 402–433. [Google Scholar] [CrossRef]
- Gomes, G.F.; Mendéz, Y.A.D.; Alexandrino, P.D.S.L.; da Cunha, S.S., Jr.; Ancelotti, A.C., Jr. The use of intelligent computational tools for damage detection and identification with an emphasis on composites–A review. Compos. Struct. 2018, 196, 44–54. [Google Scholar] [CrossRef]
- Rempel, M.; Cai, J. A review of approximate dynamic programming applications within military operations research. Oper. Res. Perspect. 2021, 8, 100204. [Google Scholar] [CrossRef]
- Wang, W.; Liu, H.; Lin, W.; Chen, Y.; Yang, J.-A. Investigation on Works and Military Applications of Artificial Intelligence. IEEE Access 2020, 8, 131614–131625. [Google Scholar] [CrossRef]
- Svenmarck, P.; Luotsinen, L.; Nilsson, M.; Schubert, J. Possibilities and challenges for artificial intelligence in military applications. In Proceedings of the NATO Big Data and Artificial Intelligence for Military Decision Making Specialists’ Meeting, Bordeaux, France, 30 May–1 June 2018; pp. 1–16. [Google Scholar]
- Moreno, C.; Carrasco, R.A.; Herrera-Viedma, E. Data and Artificial Intelligence Strategy: A Conceptual Enterprise Big Data Cloud Architecture to Enable Market-Oriented Organisations. Int. J. Interact. Multimed. Artif. Intell. 2019, 5, 6. [Google Scholar] [CrossRef]
- Xu, Y.; Zhou, Y.; Sekula, P.; Ding, L. Machine learning in construction: From shallow to deep learning. Dev. Built Environ. 2021, 6, 100045. [Google Scholar] [CrossRef]
- Sarker, I.H. Machine Learning: Algorithms, Real-World Applications and Research Directions. SN Comput. Sci. 2021, 2, 160. [Google Scholar] [CrossRef] [PubMed]
- Cid-López, A.; Hornos, M.J.; Carrasco, R.A.; Herrera-Viedma, E. A hybrid model for decision-making in the Information and Communications Technology sector. Technol. Econ. Dev. Econ. 2015, 21, 720–737. [Google Scholar] [CrossRef]
- Cobo, M.J.; Jürgens, B.; Herrero-Solana, V.; Martínez, M.A.; Herrera-Viedma, E. Industry 4.0: A perspective based on bibliometric analysis. Procedia Comput. Sci. 2018, 139, 364–371. [Google Scholar] [CrossRef]
- Huang, W.-Q.; Ding, C.; Wang, S.-Y.; Hu, S. An Efficient Clustering Mining Algorithm for Indoor Moving Target Trajectory Based on the Improved AGNES. IEEE 2015, 1, 1318–1323. [Google Scholar] [CrossRef]
- Cámara, N.; Tuesta, D. Measuring financial inclusion: A muldimensional index. BBVA Res. Pap. 2014, 14, 26. [Google Scholar] [CrossRef] [Green Version]
- Verma, V.; Aggarwal, R.K. A comparative analysis of similarity measures akin to the Jaccard index in collaborative recommendations: Empirical and theoretical perspective. Soc. Netw. Anal. Min. 2020, 10, 1–16. [Google Scholar] [CrossRef]
- Kehle-Forbes, S.M.; Campbell, E.H.; Taylor, B.C.; Scholten, J.; Sayer, N. Does Co-Occurring Traumatic Brain Injury Affect VHA Outpatient Health Service Utilization and Associated Costs Among Veterans with Posttraumatic Stress Disorder? An Examination Based on VHA Administrative Data. J. Head Trauma Rehabil. 2017, 32, E16–E23. [Google Scholar] [CrossRef] [PubMed]
- Adamowski, T.; Kiejna, A. Mental Disorders Between Military Conflict’s Veterans. Adv. Clin. Exp. Med. 2006, 15, 355–360. [Google Scholar]
- Kang, B.; Karel, M.J.; Corazzini, K.N.; McConnell, E.S. A mixed methods study on the manifestations of behavioural symptoms of dementia among veterans with and without posttraumatic stress disorder. J. Adv. Nurs. 2021, 77, 3176–3188. [Google Scholar] [CrossRef] [PubMed]
- Goderez, B.I. The survivor syndrome. Massive psychic trauma and posttraumatic stress disorder. Bull. Menn. Clin. 1987, 51, 96. [Google Scholar]
- Karstoft, K.-I.; Statnikov, A.; Andersen, S.B.; Madsen, T.; Galatzer-Levy, I.R. Early identification of posttraumatic stress following military deployment: Application of machine learning methods to a prospective study of Danish soldiers. J. Affect. Disord. 2015, 184, 170–175. [Google Scholar] [CrossRef]
- Pietrzak, R.H.; Tsai, J.; Harpaz-Rotem, I.; Whealin, J.M.; Southwick, S.M. Support for a novel five-factor model of posttraumatic stress symptoms in three independent samples of Iraq/Afghanistan veterans: A confirmatory factor analytic study. J. Psychiatr. Res. 2012, 46, 317–322. [Google Scholar] [CrossRef]
- Lammers, D.; Marenco, C.; Morte, K.; Conner, J.; Williams, J.; Bax, T.; Martin, M.; Eckert, M.; Bingham, J. Machine Learning for Military Trauma: Novel Massive Transfusion Predictive Models in Combat Zones. J. Surg. Res. 2022, 270, 369–375. [Google Scholar] [CrossRef]
- Bickel, K.E.; Kennedy, R.; Levy, C.; Burgio, K.L.; Bailey, F.A. The Relationship of Post-traumatic Stress Disorder to End-of-life Care Received by Dying Veterans: A Secondary Data Analysis. J. Gen. Intern. Med. 2020, 35, 505–513. [Google Scholar] [CrossRef]
- Lance, B.J.; Larkin, G.B.; Touryan, J.O.; Rexwinkle, J.T.; Gutstein, S.M.; Gordon, S.M.; Toulson, O.; Choi, J.; Mahdi, A.; Hung, C.P.; et al. Minimizing data requirements for soldier-interactive AI/ML applications through opportunistic sensing. Artificial Intelligence and Machine Learning for Multi-Domain Operations Applications II. Int. Soc. Opt. Photonics 2020, 11413, 1141306. [Google Scholar] [CrossRef]
- Zuromski, K.L.; Bernecker, S.L.; Gutierrez, P.M.; Joiner, T.E.; King, A.J.; Liu, H.; Naifeh, J.A.; Nock, M.K.; Sampson, N.A.; Zaslavsky, A.M.; et al. Assessment of a Risk Index for Suicide Attempts Among US Army Soldiers with Suicide Ideation: Analysis of Data From the Army Study to Assess Risk and Resilience in Servicemembers (Army STARRS). JAMA Netw. Open 2019, 2, e190766. [Google Scholar] [CrossRef] [PubMed]
- Bekesiene, S.; Smaliukiene, R.; Vaicaitiene, R. Using Artificial Neural Networks in Predicting the Level of Stress among Military Conscripts. Mathmatics 2021, 9, 626. [Google Scholar] [CrossRef]
- Aouto, A.; Huynh-The, T.; Lee, J.-M.; Kim, D.-S. Pose-Based Identification Using Deep Learning for Military Surveillance Systems. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 16–18 October 2019; pp. 626–629. [Google Scholar]
- Duddu, V. A survey of adversarial machine learning in cyber warfare. Def. Sci. J. 2018, 68, 356. [Google Scholar] [CrossRef] [Green Version]
- Fazekas, F. AI and Military Operations’ Planning. In Artificial Intelligence and Its Contexts; Springer: Berlin/Heidelberg, Germany, 2021; pp. 79–91. [Google Scholar]
- Restituyo, R.; Hayajneh, T. Vulnerabilities and Attacks Analysis for Military and Commercial IoT Drones. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 26–32. [Google Scholar]
- Ploumis, M. AI weapon systems in future war operations; strategy, operations and tactics. Comp. Strat. 2022, 41, 1–18. [Google Scholar] [CrossRef]
- Srinath, R.; Gayathri, R. Detection and classification of electroencephalogram signals for epilepsy disease using machine learning methods. Int. J. Imaging Syst. Technol. 2021, 31, 729–740. [Google Scholar] [CrossRef]
- Chukhnov, A.P.; Ivanov, Y.S. Algorithms for Detecting and Preventing Attacks on Machine Learning Models in Cyber-Security Problems. J. Phys. Conf. Ser. 2021, 2096, 012099. [Google Scholar] [CrossRef]
- Kang, J.J. A Military Human Performance Management System Design using Machine Learning Algorithms. In Proceedings of the 2021 31st International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 24–26 November 2021; pp. 13–18. [Google Scholar] [CrossRef]
- Escobar-Flores, J.G.; Sandoval, S.; Gámiz-Romero, E. Unmanned aerial vehicle images in the machine learning for agave detection. Environ. Sci. Pollut. Res. 2022, 1–12. [Google Scholar] [CrossRef]
- Berry, D. Application of big data in healthcare: Examination of the military experience. Health Technol. 2021, 11, 251–256. [Google Scholar] [CrossRef]
- Ren, L.; Chen, Y. Research on the Application of Data Mining Technology in Military Audit. In Proceedings of the 2021 International Conference on Education, Information Management and Service Science (EIMSS), Xi’an, China, 16–18 July 2021; pp. 277–283. [Google Scholar]
- Walker, P.B.; Norris, J.N.; Tschiffely, A.E.; Mehalick, M.L.; Cunningham, C.A.; Davidson, I.N.; Tshiffiley, A.E. Applications of Transductive Spectral Clustering Methods in a Military Medical Concussion Database. IEEE/ACM Trans. Comput. Biol. Bioinform. 2016, 14, 534–544. [Google Scholar] [CrossRef]
- Zheng, Y.; Li, W.; Dong, X.; Zhou, M.; Xu, L. Application Research on Big Data of Military Training in Military Academy Teaching. In Proceedings of the 2020 International Conference on Modern Education and Information Management (ICMEIM), Dalian, China, 25–27 September 2020; pp. 357–361. [Google Scholar]
- Talbot, L.A.; Haffner, W.H.J.; Rice, C.L.; Rothwell, S.W. COVID-19 Pandemic: A Collection of Relevant Publications from Military Medicine. Mil. Med. 2020, 185, e1364–e1365. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, P.; Li, P.; Duan, K.; Wen, Y.; Yang, Q.; Zhang, T.; Yao, D. Noise-assisted multivariate empirical mode decomposition for multichannel EMG signals. Biomed. Eng. Online 2017, 16, 107. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hanson, P.; Truax, L.; Saranchak, D.D. IOT honeynet for military deception and indications and warnings. In Autonomous Systems: Sensors, Vehicles, Security, and the Internet of Everything. Int. Soc. Opt. Photonics 2018, 10643, 106431A. [Google Scholar] [CrossRef]
- Soldin, R.J. SAR Target Recognition with Deep Learning. In Proceedings of the 2018 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), Washington, DC, USA, 9–11 October 2018; pp. 1–8. [Google Scholar]
- Shahid, H.; Shah, M.A.; Almogren, A.; Khattak, H.A.; Din, I.U.; Kumar, N.; Maple, C. Machine Learning-based Mist Computing Enabled Internet of Battlefield Things. ACM Trans. Internet Technol. 2021, 21, 1–26. [Google Scholar] [CrossRef]
- Rosellini, A.J.; Stein, M.B.; Benedek, D.M.; Bliese, P.; Chiu, W.T.; Hwang, I.; Monahan, J.; Nock, M.K.; Sampson, N.A.; Street, A.E.; et al. Predeployment predictors of psychiatric disorder-symptoms and interpersonal violence during combat deployment. Depress. Anxiety 2018, 35, 1073–1080. [Google Scholar] [CrossRef]
- Rosellini, A.J.; Monahan, J.; Street, A.E.; Heeringa, S.G.; Hill, E.D.; Petukhova, M.; Reis, B.Y.; Sampson, N.A.; Bliese, P.; Schoenbaum, M.; et al. Predicting non-familial major physical violent crime perpetration in the US Army from administrative data. Psychol. Med. 2016, 46, 303–316. [Google Scholar] [CrossRef] [Green Version]
- Oh, D.; Han, J. Fisheye-Based Smart Control System for Autonomous UAV Operation. Sensors 2020, 20, 7321. [Google Scholar] [CrossRef]
- Sharma, S.; Bhatt, M.; Sharma, P. Face recognition system using machine learning algorithm. In Proceedings of the 2020 5th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 10–12 June 2020; pp. 1162–1168. [Google Scholar]
- Privett, G.J.; Harvey, P.R.W.; Booth, D.M.; Kent, P.J.; Redding, N.J.; Evans, D.; Jones, K.L. Software tools for assisting the multisource imagery analyst. In Proceedings of the Applications of Digital Image Processing XXVI, San Diego, CA, USA, 5–8 August 2003; Volume 5203, pp. 163–176. [Google Scholar] [CrossRef]
- Martinez, J.; MacAllister, A.; Dominguez, E.; Mahlmann, C.; Quinlan, G.; McKee, M. Applying Neural Networks to the F-35 Seam Validation Process. In Proceedings of the 2021 IEEE Aerospace Conference (50100), Big Sky, MT, USA, 6–13 March 2021; Volume 50100, pp. 1–11. [Google Scholar]
- Jahromi, A.N.; Hashemi, S.; Dehghantanha, A.; Parizi, R.M.; Choo, K.-K.R. An Enhanced Stacked LSTM Method with No Random Initialization for Malware Threat Hunting in Safety and Time-Critical Systems. IEEE Trans. Emerg. Top. Comput. Intell. 2020, 4, 630–640. [Google Scholar] [CrossRef]
- Wang, X.; Cheng, P.; Liu, X.; Uzochukwu, B. Fast and Accurate, Convolutional Neural Network Based Approach for Object Detection from UAV. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 3171–3175. [Google Scholar]
- Alfandi, O.; Khanji, S.; Ahmad, L.; Khattak, A. A survey on boosting IoT security and privacy through blockchain. Clust. Comput. 2021, 24, 37–55. [Google Scholar] [CrossRef]
- Zhong, G.; Ling, X.; Wang, L. From shallow feature learning to deep learning: Benefits from the width and depth of deep architectures. WIREs Data Min. Knowl. Discov. 2018, 9, 1255. [Google Scholar] [CrossRef] [Green Version]
- Graham, K.; Dipnall, J.; Van Hooff, M.; Lawrence-Wood, E.; Searle, A.; Ao, A.M. Identifying clusters of health symptoms in deployed military personnel and their relationship with probable PTSD. J. Psychosom. Res. 2019, 127, 109838. [Google Scholar] [CrossRef]
- Dwivedi, R.K.; Pandey, S.; Kumar, R. A Study on Machine Learning Approaches for Outlier Detection in Wireless Sensor Network. In Proceedings of the 2018 8th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 11–12 January 2018; pp. 189–192. [Google Scholar]
- Arnous, F.I.; Narayanan, R.M.; Li, B. Artificial intelligence implementation for multi-domain sensor suite optimization. In Proceedings of the Radar Sensor Technology XXIV International Society for Optics and Photonics, Bellingham, WA, USA, 27 April–8 May 2020; Volume 11408, p. 1140818. [Google Scholar] [CrossRef]
- Zuluaga, J.G.C.; Leidig, J.P.; Trefftz, C.; Wolffe, G. Deep Reinforcement Learning for Autonomous Search and Rescue. In Proceedings of the NAECON 2018—IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 23–26 July 2018; pp. 521–524. [Google Scholar]
- Shin, G.; Yooun, H.; Shin, D.; Shin, D. Incremental learning method for cyber intelligence, surveillance, and reconnaissance in closed military network using converged IT techniques. Soft Comput. 2018, 22, 6835–6844. [Google Scholar] [CrossRef]
- Zheng, Y.; Song, Q.; Liu, J.; Song, Q.; Yue, Q. Research on motion pattern recognition of exoskeleton robot based on multimodal machine learning model. Neural Comput. Appl. 2020, 32, 1869–1877. [Google Scholar] [CrossRef]
- Iftimie, I.A.; Wilson, R.L. The Use of Signals Intelligence in Offensive Cyberspace Operations: An Anticipatory Ethical Analysis. In Proceedings of the International Conference on Cyber Warfare and Security, Norfolk, VA, USA, 12–13 March 2020; p. 262-XVIII. [Google Scholar] [CrossRef]
- Zuromski, K.L.; Bernecker, S.L.; Chu, C.; Wilks, C.R.; Gutierrez, P.M.; Joiner, T.E.; Liu, H.; Naifeh, J.A.; Nock, M.K.; Sampson, N.A.; et al. Pre-deployment predictors of suicide attempt during and after combat deployment: Results from the Army Study to Assess Risk and Resilience in Servicemembers. J. Psychiatr. Res. 2020, 121, 214–221. [Google Scholar] [CrossRef] [PubMed]
- Morse, S.; Talty, K.; Kuiper, P.; Scioletti, M.; Heymsfield, S.B.; Atkinson, R.L.; Thomas, D.M. Machine learning prediction of combat basic training injury from 3D body shape images. PLoS ONE 2020, 15, e0235017. [Google Scholar] [CrossRef]
- Tursunbayeva, A.; Di Lauro, S.; Pagliari, C. People analytics—A scoping review of conceptual boundaries and value propositions. Int. J. Inf. Manag. 2018, 43, 224–247. [Google Scholar] [CrossRef]





















| Category of the Review Work | Refs. |
|---|---|
| Robotics and smart devices with military applications | [6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22] |
| Generic ML and optimization techniques with military applications | [23,24,25,26,27,28,29,30,31,32,33] |
| ML and optimization techniques focused on military applications | [34,35,36] |
| Dimension | Meaning | Type of Analysis Available |
|---|---|---|
| Sources | Journals, proceedings… | Citation, Bibliographic coupling, Co-citation |
| Authors | Author and co-authors | Co-authorship, Citation, Bibliographic coupling, Co-citation |
| Organizations | Authors’ institutions | Co-authorship, Citation, Bibliographic coupling |
| Countries | Authors’ countries | Co-authorship, Citation, Bibliographic coupling |
| Themes | Keywords, terms, topics… | Co-occurrence |
| Web of Science Categories | Record Count | % of 525 |
|---|---|---|
| Engineering Electrical Electronic | 161 | 30.667 |
| Computer Science Artificial Intelligence | 119 | 22.667 |
| Computer Science Information Systems | 92 | 17.524 |
| Computer Science Theory Methods | 77 | 14.667 |
| Telecommunications | 77 | 14.667 |
| Optics | 63 | 12.000 |
| Computer Science Interdisciplinary Applications | 34 | 6.476 |
| Automation Control Systems | 24 | 4.571 |
| Remote Sensing | 23 | 4.381 |
| Instruments Instrumentation | 21 | 4.000 |
| Imaging Science Photographic Technology | 20 | 3.810 |
| Engineering Multidisciplinary | 19 | 3.619 |
| Psychiatry | 19 | 3.619 |
| Computer Science Software Engineering | 18 | 3.429 |
| Physics Applied | 17 | 3.238 |
| Chemistry Analytical | 16 | 3.048 |
| Computer Science Cybernetics | 16 | 3.048 |
| Computer Science Hardware Architecture | 16 | 3.048 |
| Engineering Aerospace | 15 | 2.857 |
| Operations Research Management Science | 13 | 2.476 |
| Robotics | 13 | 2.476 |
| Environmental Sciences | 12 | 2.286 |
| Materials Science Multidisciplinary | 11 | 2.095 |
| Neurosciences | 11 | 2.095 |
| Surgery | 11 | 2.095 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Galán, J.J.; Carrasco, R.A.; LaTorre, A. Military Applications of Machine Learning: A Bibliometric Perspective. Mathematics 2022, 10, 1397. https://doi.org/10.3390/math10091397
Galán JJ, Carrasco RA, LaTorre A. Military Applications of Machine Learning: A Bibliometric Perspective. Mathematics. 2022; 10(9):1397. https://doi.org/10.3390/math10091397
Chicago/Turabian StyleGalán, José Javier, Ramón Alberto Carrasco, and Antonio LaTorre. 2022. "Military Applications of Machine Learning: A Bibliometric Perspective" Mathematics 10, no. 9: 1397. https://doi.org/10.3390/math10091397







