Abstract
The blind quantum computation (BQC) protocol allows for privacy-preserving remote quantum computations. In this paper, we introduce a remote quantum error correction code preparation protocol for BQC using a cluster state and analyze its blindness in the measurement-based quantum computation model. Our protocol requires fewer quantum resources than previous methods, as it only needs weak coherent pulses, eliminating the need for quantum memory and limited quantum computing. The results of our theoretical analysis and simulations show that our protocol requires fewer quantum resources compared to non-coding methods with the same qubit error rate.
MSC:
81P73
1. Introduction
With the rapid development of quantum technology, quantum computing has attracted increasing attention from researchers because of its theoretically super-high computing power. In the classical field, it is very hard for conventional computers to deal with the non-deterministic polynomial (NP) problems. However, these tasks have the potential to be solved by a quantum computer in the future [1,2,3,4,5,6]. At present, a practical quantum computer requires large-scale quantum resources, expensive equipment, and low-temperature environment, etc., which ordinary clients cannot afford. A blind quantum computation (BQC) protocol as an optimal potential solution can address this problem at hand. By harnessing of the power of BQC, the client (Alice) can effectively delegate intricate computing tasks to a remote quantum server (Bob) while guaranteeing the privacy of Alice’s information [7,8,9]. The breakthrough of QBC is not only the low cost of overcoming Alice’s computing limitations but also protecting sensitive data well. In recent years, many extension BQC protocols have emerged [10,11,12,13,14,15,16]. The universal blind quantum computation (UBQC) proposed by Broadbent, Fitzsimons, and Kashefi [9] is very popular among these protocols, in which Alice only needs to prepare the single-photon states.
In UBQC, the preparation is a very important process [9] which directly determines the number of pulses to be sent and the state of the desired qubits and is the basis of the successful execution of subsequent quantum computing. In Alice’s preparation, she prepares the required single photon pulses for a desired computing and sends them to Bob through a quantum channel. However, the probability of the photon number satisfies the Poisson distribution, which results in a lower generated probability of single photons. It is also inevitable that two or multiple photon pulses are sent in the preparation, which will destroy the privacy of quantum states in Alice’s preparation. Hence, a remote blind qubit state preparation (RBSP) protocol is proposed by Dunjko et al. [10] to delegate Bob to prepare qubits, which only requires Alice to send weak coherent pulses to Bob. To prepare a desired qubit, the number of pulses is of the order , where represents the transmittance of the quantum channel. Xu and Lo then presented the one decoy state-based RBSP protocol to improve the preparation efficiency [11]. The number of pulses to prepare a desired qubit can be reduced from to almost . Obviously, the decoy state technique can be used to prepare more qubits in unit time. On this basis, the multi-decoy states technique in quantum key distribution [17] can also be applied to the UBQC protocol. Subsequently, Zhao and Li proposed a blind quantum state preparation protocol with two decoy states [12,13,14], which further improves the preparation efficiency. Their simulation experiments also show that the preparation protocol with two decoy states is more suitable for long-distance communication.
However, in the preparation of UBQC, the qubits disturbed by noise are prone to errors [16,18]. To avoid the accumulation and propagation of these errors in the subsequent computations, quantum error-correcting code [19] offers a viable solution to correct error qubits in the preparation process. Tan Xiaoqing et al. [20] proposed a fault-tolerant framework for blind quantum computing, which used 7-qubit CSS code to encode the logical GHZ states to overcome the collective-dephasing noise and the collective-rotating noise. However, the client was required to have the ability of single-qubit measurement on the third qubit of the logical GHZ state and share the remaining Bell state with the server. Morimae and Koshiba [21] have shown that it is impossible for the classical client to implement perfectly secure one-round delegated quantum computing. Therefore, the client at least requires access to the quantum channel or other quantum properties in a realistic situation. In order to reduce the client’s burden and dependence on quantum, we delegate quantum error-correcting code preparation to Bob for implementation. Since the delegated preparation is implemented in the measurement-based quantum computation (MBQC) framework [22,23], the encoding circuit is required to be converted into graph states to prepare the quantum error-correcting codes in the MBQC manner.
Combined with two-decoy-state RBSP, a remote quantum error-correcting code preparation protocol on cluster state is presented to correct errors in blind quantum computation. In our protocol, the cluster states are used as graph states to prepare quantum error-correcting codes that are unknown to Bob. Then, these codes can be considered as encoded logical qubits for subsequent fault-tolerant blind quantum computation. The security of the proposed protocol is proven theoretically to be -blind. Finally, the lower bound of quantum resource consumption is estimated, i.e., the number of required pulses. When the prepared quantum error-correcting codes have the same qubit error rate, our protocol can reduce the number of pulses, which will contribute to the practical application of UBQC in the future.
The remainder of the paper is structured as follows: In Section 2, we introduce the basic knowledge. In Section 3, we present a quantum error-correcting code preparation protocol on cluster state to correct qubit errors. Furthermore, we demonstrate that the protocol is -blind and estimate the quantum resource consumption. In Section 4, simulation results show the quantum resource consumption of coding and non-coding protocols in the case of the same qubit error rate. In Section 5, the necessary conclusions are drawn.
2. Technical Preliminaries
2.1. Qubit Error
Due to environmental noise, it is inevitable that errors occur in quantum computations. Therefore, we need to build a general error model to correct qubit errors. In quantum Hilbert space, a quantum state can be described as
where are the basis vectors in the Hilbert space, and .
After the noise has occurred, the evolution of the quantum state contains four cases: (1) no error, (2) the bit error , (3) the phase error , and (4) both bit and phase errors. Hence, an error operator can be considered a linear combination of identity operator I, bit flip operator X, phase flip operator Z, and bit-phase flip operator Y [24]. These Pauli operators are
To simplify the analysis, suppose the noise occurs on a single qubit, so the quantum state can be described as a superposition state of the four possible states , , , and [25]. If one measures the error quantum state , it collapses into one of four states. In order to correct the qubit error, we need to perform a diagnostic process to determine which error occurred in four possible cases and then utilize Pauli operators to act on the error qubit to correct it.
2.2. Quantum Error-Correcting Codes
In the error-correcting process, the error syndrome measurement is used to diagnose which qubit is in error. With the increasing number of qubits in code, it is more difficult to determine where the error occurred. As a result, we use seven qubits to encode one qubit, which can correct a qubit error in an encoded block, which is called the 7-qubit Steane code, . The encoded logical qubit base is shown as follows:
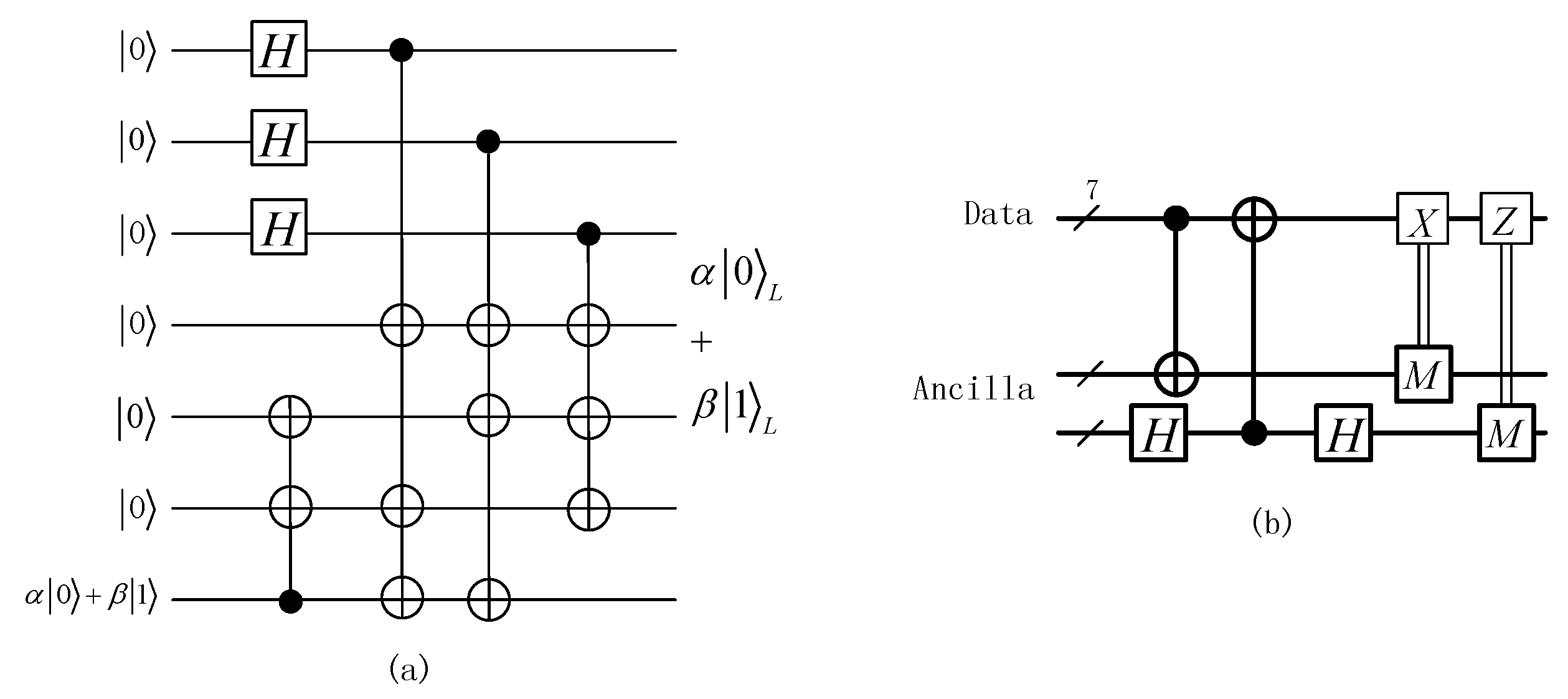
Based on the encoding principle of Steane code [24], we can design the encoding circuit of quantum error-correcting code, as shown in Figure 1a. The unknown data qubit and six ancilla qubits can be used to encode an encoded logical qubit. According to the error syndrome measurement circuit in Figure 1b, one uses two Steane ancilla states to diagnose the bit and phase error syndromes, respectively. Finally, the Pauli gates are used to act on the error qubits to correct them in each encoded block.

Figure 1.
The quantum encoded and syndrome measurement circuits of the Steane code [[7,1,3]]. (a) A 7-qubit encoded logical qubit is prepared by a data qubit and six ancilla qubits. (b) The bit and phase errors occurring in the encoded block can be diagnosed with two Steane ancilla states and recovered by Pauli gates.
2.3. Realization of Quantum Gates on Cluster State
For a quantum circuit, we can use the ordered quantum gates to describe the computational process. Any quantum gate can be transformed into a combination of quantum gates in the universal gate group, such as . Hence, only if we can realize every quantum gate in the universal logic gate group can we implement arbitrary quantum computing.
In the framework of MBQC [26], we know that quantum gates can be realized by multi-particle entangled graph states, such as cluster state and brickwork state [9,22]. Note that the encoded circuit consists of Hadamard gates and CNOT gates in Figure 1. Hence, we only need to realize these two types of quantum gates on graph states. Since quantum gates in brickwork state only act on the neighboring qubit, the CNOT gate acting on non-neighboring qubits needs many SWAP gates to be realized, which is very inefficient. Hence, we use the cluster state to realize these Hadamard and CNOT gates in the encoding circuit, as shown in Figure 2.

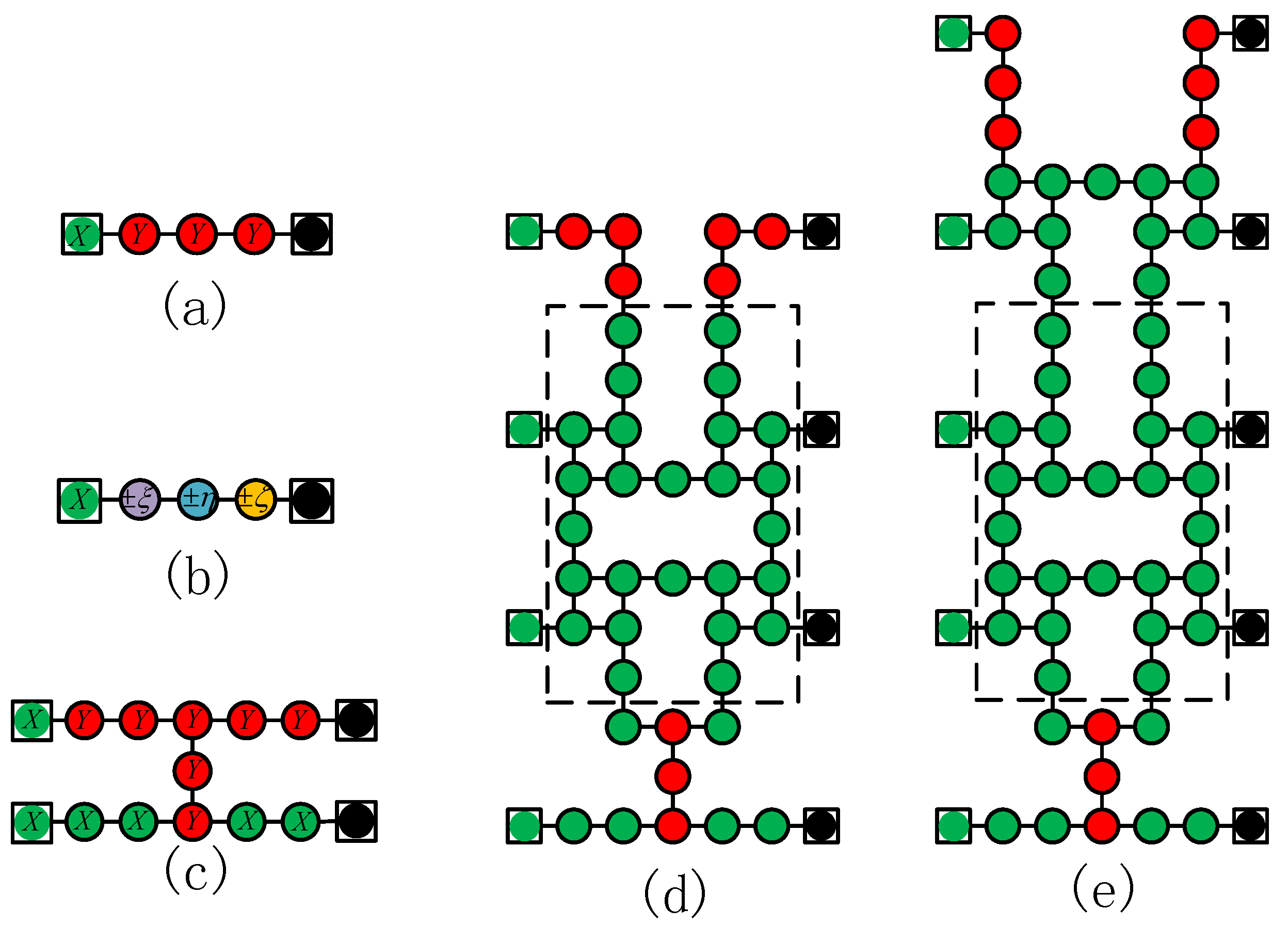
Figure 2.
Implementation of basic quantum gates on cluster state. Each circle represents a qubit, and the left-most squares represent the input qubits, the right-most squares denote the output qubits. Each green circle represents a cluster qubit measured in the eigenbasis of Pauli gate X, the red denotes I. The , , and represent the measurement angles of the measurement basis . (a) The Hadamard gate. (b) A general rotation gate. (c) The CNOT gate applied between adjacent logical qubits. (d) The CNOT gate applied between two logical qubits separated by an even number. (e) The CNOT gate applied between two logical qubits separated by an odd number.
In Figure 2, these diagrams are used to illustrate the realization of quantum gates on cluster states. (a) represents the pattern to realize the Hadamard gate. Each circle symbolizes a qubit, and the lines indicate entangling operators. Controlled-Z (CZ) gates are employed to interact between neighboring qubits, preparing the entangled state. The qubits are measured in a specifically selected basis, with the green (red) circle representing a measurement in the eigenstates of the X (Y) Pauli gate. The measurement basis is determined by the measurement angle . The eigenbasis of X (Y) corresponds to . The computational basis is the eigenbasis of Z. (b) illustrates a general one-qubit rotating quantum gate through one-qubit measurement in a cluster state, where the measurement basic angles depend on the measurement results of other qubits. (c), (d), and (e) show the CNOT gate applied between different distance logical qubits. One can repeat the rectangle parts enclosed by the black dashed line in (d) and (e) to deal with any separation. In quantum computing in a cluster state, the basis is used to eliminate the redundant qubits, and the adaptive basis is used to measure the remaining qubits to implement any quantum gate.
3. Quantum Error-Correcting Code Preparation on Cluster State
In the field of quantum computation, it is widely recognized that cluster states can be used to realize arbitrary quantum gates. Indeed, the essence of a quantum circuit resides in its meticulously ordered sequence of quantum gates, forming the fundamental backbone of quantum computing. Consequently, each quantum circuit can be efficiently performed in a cluster state [22]. By harnessing the power of cluster states, the quantum encoding circuit can also be feasible, enabling the generation of quantum error-correcting codes. These encoded qubits can then be utilized to construct novel brickwork states to facilitate the realization of fault-tolerant quantum computing.
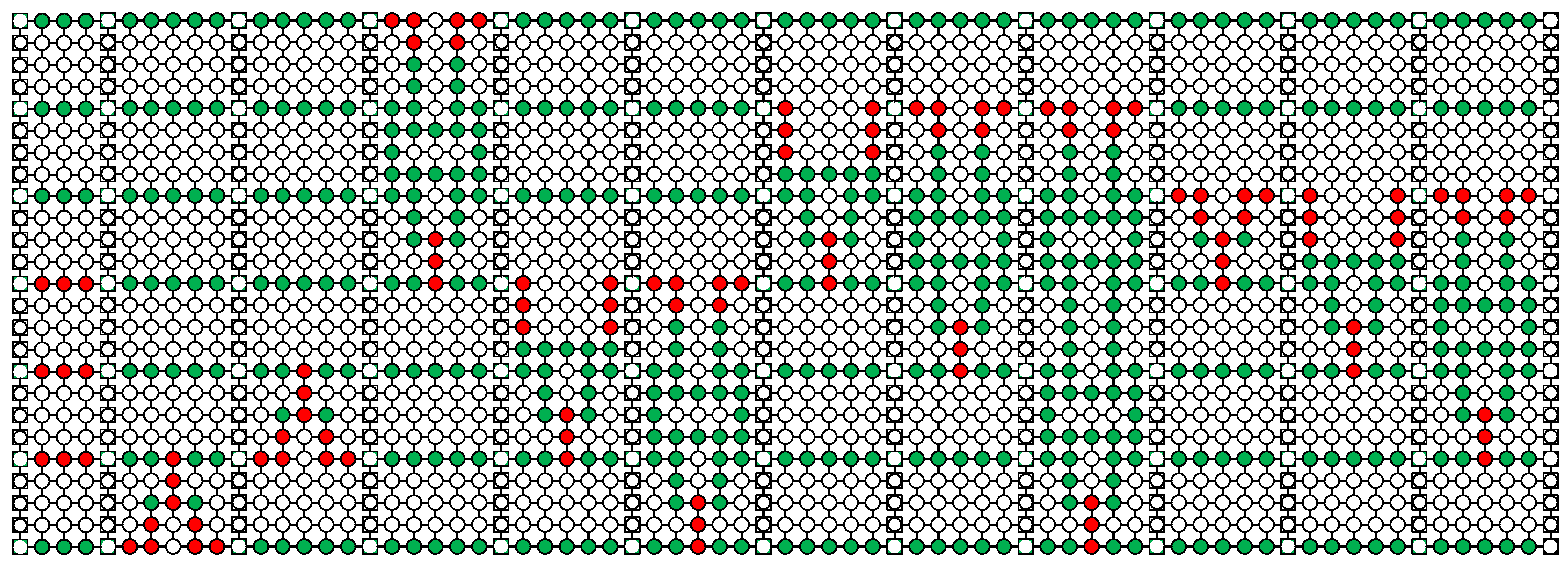
According to the implementation of quantum gates on cluster state in the preliminaries, the encoding circuit of [[7,1,3]] code needs to be transformed into MBQC on cluster state, then the quantum error-correcting code preparation can be realized through measuring each qubit on cluster state, as shown in Figure 3. In the preparation process, Bob initiates the construction of the initial cluster state, followed by the judicious utilization of the computational basis to eliminate the redundant qubits based on the precise positional information provided by Alice. In accordance with Alice’s designated measurement bases , the remaining qubits of the cluster state serve as a platform for preparing quantum error-correcting codes. These bases are meticulously designed to be orthogonally projected onto the states , where designates the measurement angle. Note that the specific values of such as or corresponds to the X or Y Pauli measurement, respectively. It is important to emphasize that these measurements are inherently destructive. Obviously, the measurement is understood as a destructive measurement. The measurement outcome of qubit i is denoted by . Our convention dictates that when the state collapses to as a result of the measurement, and when it collapses to .

Figure 3.
The implementation of the [[7,1,3]] encoding circuit on cluster state. The measured cluster qubits are denoted by the green, red, and white circles, representing the measurements in the eigenbases of X, Y, and Z, respectively.
During the process of removing redundant qubits, an inherent challenge arises concerning the potential leakage of quantum gates used, which could inadvertently disclose the underlying structural information of the cluster state to Bob. However, Alice’s primary concern lies in ensuring the security of the encoded logical qubit during the preparation, while the quantum gates employed in the encoded circuit can be made public to Bob. To accomplish preparation, three distinct measurement bases are employed, including , and corresponding to the eigenbases of the Pauli gates , respectively. These measurement bases exhibit a notable characteristic: their independence from the polarization angle . As a result, the information pertaining to remains entirely secure and undisclosed to Bob throughout the process. These findings shed light on the potential of cluster states for secure and efficient quantum information processing in quantum error-correcting code preparation.
In UBQC, the delegated preparation process contains Alice’s preparation, Bob’s preparation, and the interaction measurement. In Alice’s preparation, Alice sends N data pulses to Bob, which comprise signal states and two decoy states, and their polarization is , where is chosen randomly from . In addition, Alice needs to send a series of ancilla pulses to Bob, and their polarization is , which is allowed to be public. In Bob’s preparation, the required qubit can be generated based on non-coding RBSP [13]. Among the generated qubit and a series of ancilla qubits, Bob utilizes CZ gates to entangle them to build an initial cluster state. During the interaction measurement, Bob follows Alice’s instructions and eliminates the redundant qubits from the initial cluster state in the computational basis, as shown in the white circles in Figure 3. According to Alice’s measurement basis , the remaining qubits on cluster state are measured sequentially until the final outcome is obtained. Finally, Bob can achieve the required quantum error-correcting codes. As depicted in Algorithm 1, we propose an innovative protocol for remote quantum error-correcting code preparation on cluster state, which lays the groundwork for subsequent fault-tolerant blind quantum computing.
| Algorithm 1: A remote quantum error-correcting code preparation on cluster state |
 |
The [[7,1,3]] encoding circuit is designed based on the generator matrix, and its correctness had been proven by Preskill [24]. Since the preparation on cluster state is equivalent to the encoding circuit model, our protocol can generate the correct quantum error-correcting codes. In order to ensure Alice’s information privacy, the encoding logical qubits (quantum error-correcting codes) are required to be unknown to Bob in UBQC. In other words, the polarization angle is always unknown to Bob in the preparation process of the encoding logical qubits .
In UBQC, the client and server share a joint state that describes the evolution of the entire system. The ideal state is symbolized as that effectively guarantees the client’s information against potential malicious attacks. During the preparation, the ideal state evolves into a set of states, which can be conveniently represented by . To ensure robust security against any server actions, it is imperative that all states with this set remain equally blind. To assess the security level achievable in practical implementation, we explore scenarios where the client transmits a realistic state to replace a perfect state . In the following, we introduce the concept of almost blindness by quantifying the proximity between the realistic joint state and the ideal joint state, i.e., -blind [10].
Definition 1.
A UBQC protocol with imperfect preparation is ϵ-blind if the trace distance between the ideal joint state and realistic joint state is less than . Finally, we have:
Theorem 1.
Our preparation Algorithm 1 is ϵ-blind to Bob.
Proof.

In our protocol, the measurement-based quantum computation is used to realize quantum error-correcting code preparation on cluster state. The prepared data qubit and a series of ancilla qubits can be considered as quantum resources to build the cluster state. Based on the RBSP protocol [10,13], the generated data qubit is -blind. In order to demonstrate the -blindness of the encoded logical qubit , we only need to prove that the encoding circuit on cluster state is -blind. In other words, the angle of polarization of in the preparation process is unknown to Bob.
To be more precise, it is necessary to illustrate that the measurements on cluster state do not reveal any information about polarization angle . The cluster state is built by multiple entanglement qubits. For the purpose of simplicity, it suffices to prove that the polarization angle is -blind to Bob during the measurements on the minimum cluster state. Further, we analyze three kinds of measurements on cluster state according to the [[7,1,3]] encoding circuit. The eigenstates of are used to measure the qubits on the minimum cluster state, respectively. We explore whether there is information leakage of the polarization angle during the measurements.
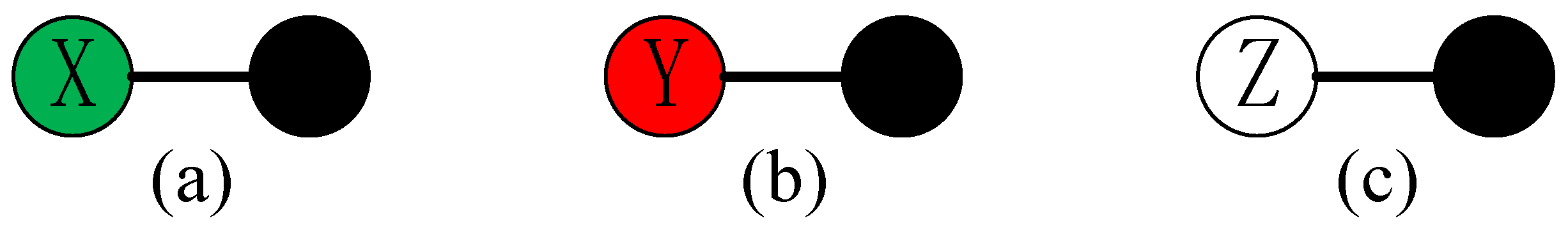
The first qubit and the second qubit are used to build the minimum cluster state using CZ gate, as shown in Figure 4. If the first qubit is measured in the eigenstates of X gate, as shown in Figure 4a, the quantum state is or with an equal probability. The second qubit is evolved into , where k represents the measurement result of the first qubit, as shown in Equation (5). If the eigenstates of Y gate are used to measure the first qubit, as shown in Figure 4b, the polarization state of the second qubit is evolved into , k is also determined by measurement result of the first qubit, as shown in Equation (5). It can be seen that the information of the first qubit is transmitted to the second qubit through MBQC without loss of information. If the first qubit and the second qubit are entangled into the minimum using CZ gate, as shown in Figure 4c, and the eigenstates of Z gate are used to measure the first qubit, the second qubit is still , as shown in Equation (6). Obviously, the remaining qubits are unchanged when the redundant qubits are eliminated by Z.

Figure 4.
The cluster state with two qubits. The green, red, and white represent the measurements of X, Y, and Z gates. (a) The first qubit of the cluster state is measured in the eigenbasis of X. (b) The first qubit is measured in Y. (c) The first qubit is measured in Z.
Thus, the polarization angle is irrelevant to the eigenstates of , and Z. During the measurements on cluster state, Bob can not obtain any information about the angle of polarization . Hence, the generated encoded logical qubit is -blind in our Algorithm 1 if the input data qubit is -blind. □
In our protocol, these pulses sent by Alice consist of two parts, data and ancilla. Based on non-coding RBSP, note that data pulses are employed to generate the required data qubits . Each data qubit is then transformed into its corresponding logical qubit as required. Consequently, the number of data pulses used aligns with that of the non-coding RBSP, denoted as [14]. The number of ancilla pulses depends on the cluster state used to prepare encoded states, as shown in Figure 3. It is important to highlight that the number of ancilla qubits is a constant if one encoded qubit is prepared, denoted as C. The transmittance of the quantum channel between client and server directly affects the probability of the pulses being received, denoted as T, and the scale of quantum computation is denoted as S, the number of required ancilla pulses . Hence, we can derive the lower bound of the total number of pulses in Algorithm 1.
where represents the secure parameter. , are the average photon number of signal states and two decoy states, respectively. represents the proportion of single-photon states in the signal states, and the lower bound is denoted as [13]. The probabilities of signal pulses chosen by the client are defined as . S is the computational scale, and T represents the transmittance of the quantum channel.
We assume that the qubit errors are independent. We can repeatedly use ancilla qubits in the correction, so we do not consider the ancilla qubit consumption in the correction process, as shown in Figure 1b. In the code, we note that each encoded block can correct one error. Therefore, before encoding, the error probability of each qubit is e (), and after encoding, it changes to . In a quantum computation with computation scale S, the error rate of each generated qubit based on non-coding RBSP [13] is e. If an error qubit occurs in all generated qubits, the preparation process fails. Since the error rate of each encoded qubit is in the preparation of Algorithm 1, the successful probability of encoded preparation is derived as . We consider the non-coding RBSP protocol as a repeated Bernoulli experiment, then the success probability of preparation is . By repeating the process k times, the success probability can be calculated as . In the scenario where the success probabilities are equal for both coded and non-coded cases, specifically indicated by , the number of repetitions, denoted as k, can be determined using the following derivation:
Hence, when the generated qubit error rate in the coding case is , the non-coding RBSP needs to repeatedly send pulses to achieve the same generated qubit error rate.
In UBQC, we assume that Alice has a laser transmitter with frequency f, and Bob has a full-fledged quantum computer. By deriving the preparation efficiency of UBQC, which represents the rate at which qubits are generated per second, we can gain valuable insights into the system’s performance. According to Equation (7), the upper bound of the efficiency for the concatenation code can be estimated as
In summary, our Algorithm 1 can prepare -blind quantum error-correcting codes to correct qubit errors. Under the condition of the same generated qubit error rate, our approach can reduce the number of weak coherent pulses and improve preparation efficiency compared with the non-coding RBSP protocol.
4. Simulation Results
An Intel(R) Core(TM) i7-6700HQ CPU, 12.0GB RAM, and Win 10 pro OS were utilized to implement the simulations through MATLAB software. The transmittance T contains the outside fiber, the inside fiber, and the detection efficiency between Alice and Bob, which can be calculated as follows:
where represents the loss coefficient in decibels per kilometer (dB/km), L represents the length of the fiber optic cable in kilometers (km), stands for the internal transmittance of Bob’s optical components, and represents the detector efficiency. The average photon number of signal states is denoted as , and two decoy states are represented as . The signal state is chosen with probability , and two decoy states are chosen with . The scale of quantum computation is S. The secure parameter is symbolized as . The error rate per qubit is denoted as e. According to Figure 1 and Figure 3, the required number of ancilla qubits can be determined, i.e., . The repetition frequency of the laser transmitter is MHZ. The relative parameters setting in our simulation are shown in Table 1 (refer to the data in [11,17]).

Table 1.
The simulation parameters for our protocol.
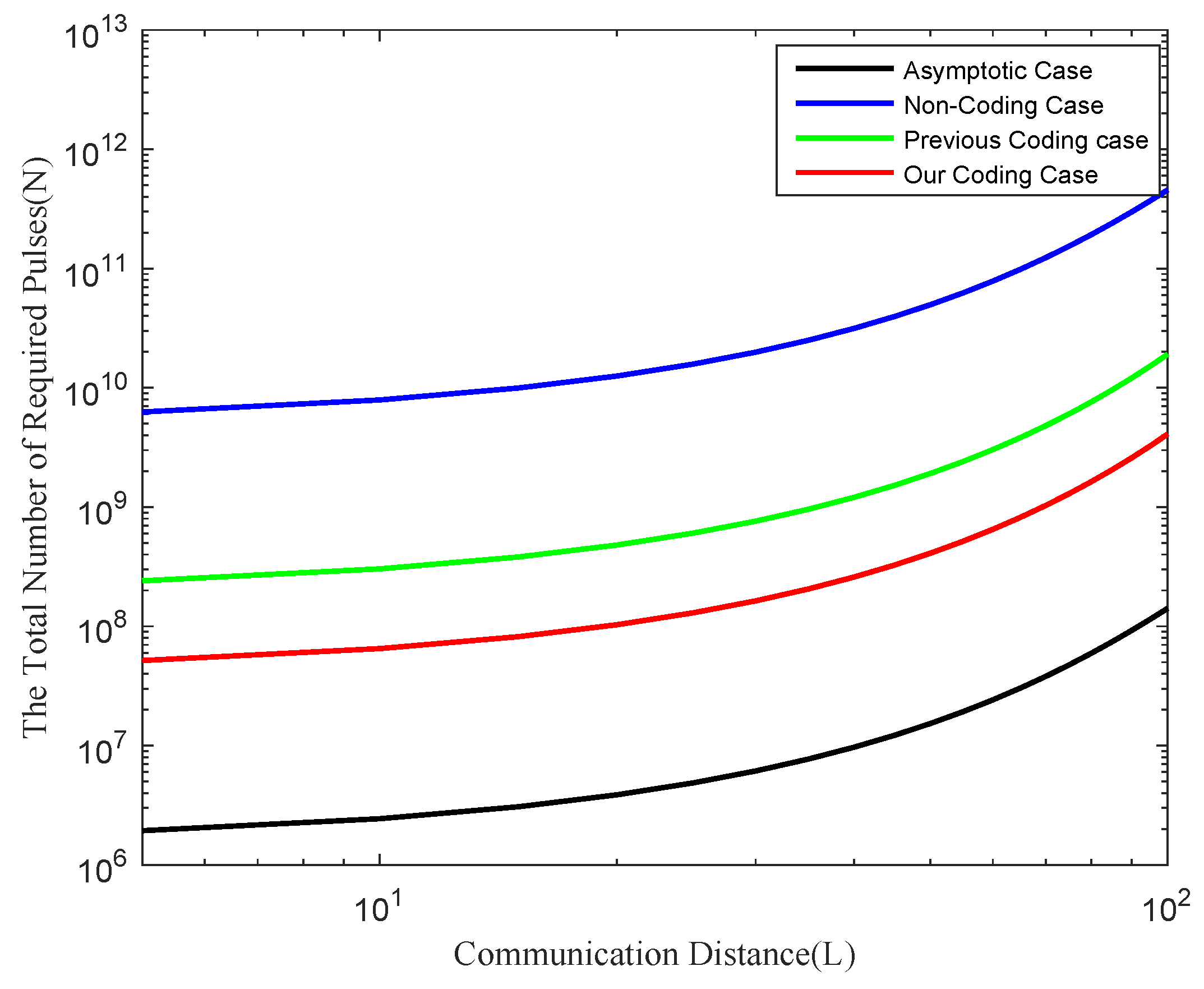
In Figure 5, note that the number of pulses in the coding case is comparatively lower than that in the non-coding RBSP [13] with the same qubit error rate and is closer to the asymptotic scenario (with infinite data-size and no qubit error [13,17]). The error rate of the generated qubits using Algorithm 1 is significantly lower than that of the non-coding RBSP. In order to obtain the same error rate, the non-coding case is required to repeat k times. Under the encoding condition of the same qubit error rate, the number of pulses required in our Algorithm 1 is lower than that of the previous coding case [14]. On the one hand, since our approach uses the cluster state instead of the brickwork state to realize remote delegated preparation, it can reduce many SWAP gates when utilizing CONT gates between non-adjacent qubits. On the other hand, our approach requires the CNOT gates with a high execution probability to avoid using too many ancilla qubits in the preparation to realize the operations of the fault-tolerant CNOT gates. Both aspects can greatly reduce the consumption of ancilla qubits; thereby, our proposed Algorithm 1 can reduce the number of pulses required.

Figure 5.
The relationship between the total number of pulses N case and the communication distance L with the same qubit error rate. The red line represents the quantum resource consumption of Algorithm 1 with coding, the green line represents the simulation results of the previous coding case [14], and the blue line depicts the results in the non-coding case [13]. The simulation results depicted by the black line show the outcomes in the asymptotic scenario, characterized by an infinitely large data size and near-perfect preparation of qubits.
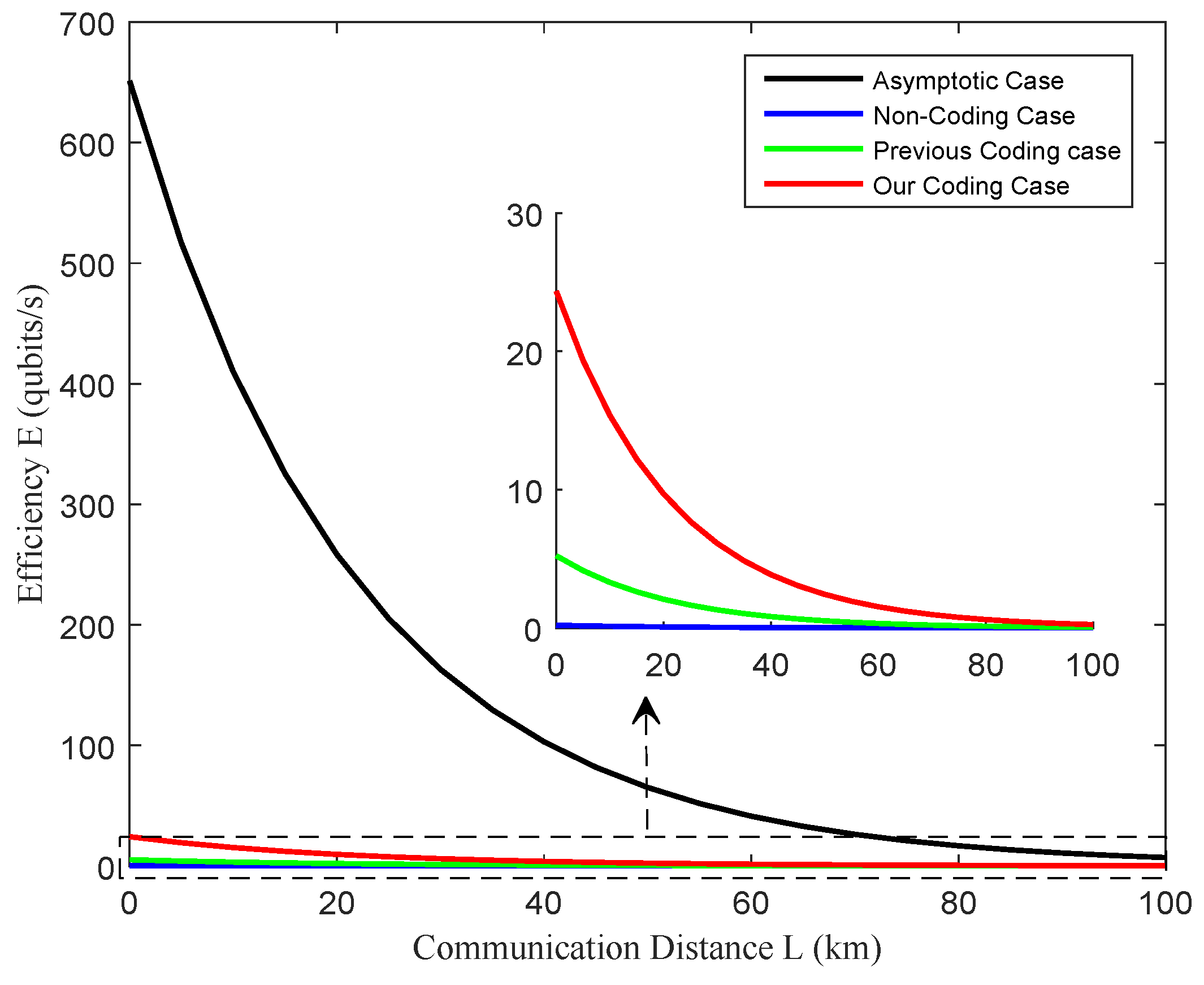
In Figure 6, the preparation efficiency E in the coding case is less than the non-coding RBSP with the same qubit error rate and is closer to the asymptotic case. Especially, the efficiency of our proposed Algorithm 1 is better than the previous protocols [13,14] with the same qubit error rate. This reason is that our approach can reduce the consumption of SWAP gates and ancilla qubits. With the increasing distance, the value of efficiency E grows rapidly, implying the significant impact of channel loss and corresponding qubit error rate. For long-distance communication, our protocol surpasses the non-coding case, primarily due to the fact that the value of E is closer to the asymptotic scenario (with an infinitely large data size and no qubit error [13,17]). These advantages underscore the enhanced performance and efficacy of our protocol, making it a favorable choice for long-distance blind quantum computing.

Figure 6.
The relationship between preparation efficiency E and the communication distance L with the same qubit error rate. The red line represents the preparation efficiency of Algorithm 1 with coding, the green line represents the simulation results of the previous coding case [14], and the blue line depicts the results in the non-coding case [13]. The simulation results represented by the black line illustrate the outcomes in the asymptotic scenario, characterized by an infinitely large data size and near-perfect preparation of qubits.
Therefore, our protocol holds the potential to enhance not only the preparation efficiency but also the conservation of quantum resources. Furthermore, the quantum error-correcting codes can be used as logical qubits to facilitate subsequent fault-tolerant blind quantum computation. The capability of our protocol ensures an optimized utilization of quantum resources while maintaining the integrity and reliability of the preparation in UBQC.
5. Conclusions
In this study, we propose an innovative protocol for remote quantum error-correcting code preparation on cluster states, which can be used to correct error qubits in the preparation of UBQC. Based on the blindness of the original RBSP protocol, we demonstrate that Algorithm 1 is also -blind. Alice only needs to send weak coherent pulses, without quantum memory or extensive quantum computing capabilities. By incorporating quantum error-correcting codes, our protocol can reduce the number of pulses when preparing the quantum error-correcting codes with the same qubit error rate. Furthermore, these quantum error-correcting codes prepared by our protocol are unknown logical qubits to Bob, which can be used to build a new encoded brickwork state to realize the fault-tolerant blind quantum computation. Our proposed preparation protocol provides a theoretical basis for the practical application of blind quantum computation in the future. In our approach, when CNOT gates are executed, they need to run with a high probability. This will limit the generalized application of blind quantum computation. Hence, we will continue to research the surface codes and the concatenated codes with high fault tolerance to better balance the quantum resource consumption and the qubit error rate, so as to generalize the preparation protocol of quantum error-correcting codes.
Author Contributions
Writing—original draft preparation, Q.Z.; writing—review and editing, Q.Z., H.M., Y.Q., Q.L. and A.A.A.E.-L.; funding acquisition, Q.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by the National Natural Science Foundation of China (grant Number: 62071151). Also, Ahmed A. Abd El-Latif acknowledges the Talented Young Scientist Program (TYSP) and its support.
Institutional Review Board Statement
This research is not applicable to studies involving humans or animals.
Informed Consent Statement
This research is not applicable to studies involving humans.
Data Availability Statement
In our work, no new real data were created, and all the data were simulated data generated by the parameters in the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelpgia, PA, USA, 22–24 May 1996; ACM: New York, NY, USA, 1996; pp. 212–219. [Google Scholar]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Tanaka, S.; Tamura, R.; Chakrabarti, B.K. Quantum Spin Glasses, Annealing and Computation; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Albash, T.; Lidar, D.A. Adiabatic quantum computation. Rev. Mod. Phys. 2018, 90, 015002. [Google Scholar] [CrossRef]
- Alsubai, S.; Alqahtani, A.; Binbusayyis, A.; Sha, M.; Gumaei, A.; Wang, S. Quantum Computing Meets Deep Learning: A Promising Approach for Diabetic Retinopathy Classification. Mathematics 2023, 11, 2008. [Google Scholar] [CrossRef]
- Lee, X.; Xie, N.; Cai, D.; Saito, Y.; Asai, N. A Depth-Progressive Initialization Strategy for Quantum Approximate Optimization Algorithm. Mathematics 2023, 11, 2176. [Google Scholar] [CrossRef]
- Childs, A.M. Secure assisted quantum computation. Quantum Inf. Comput. 2005, 5, 456–466. [Google Scholar] [CrossRef]
- Arrighi, P.; Salvail, L. Blind quantum computation. Int. J. Quantum Inf. 2006, 4, 883–898. [Google Scholar] [CrossRef]
- Broadbent, A.; Fitzsimons, J.; Kashefi, E. Universal blind quantum computation. In Proceedings of the Foundations of Computer Science, 2009, FOCS’09, 50th Annual IEEE Symposium, Atlanta, GA, USA, 25–27 October 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 517–526. [Google Scholar]
- Dunjko, V.; Kashefi, E.; Leverrier, A. Blind quantum computing with weak coherent pulses. Phys. Rev. Lett. 2012, 108, 200502. [Google Scholar] [CrossRef] [PubMed]
- Xu, K.; Lo, H.K. Blind Quantum Computing with Decoy States. arXiv 2015, arXiv:1508.07910. [Google Scholar]
- Zhao, Q.; Li, Q. Blind Quantum Computation with Two Decoy States; Springer International Publishing: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Zhao, Q.; Li, Q. Finite-data-size study on practical universal blind quantum computation. Quantum Inf. Process. 2018, 17, 171. [Google Scholar] [CrossRef]
- Zhao, Q.; Li, Q.; Mao, H.; Wen, X.; Han, Q.; Li, M. Fault-tolerant quantum error correction code preparation in UBQC. Quantum Inf. Process. 2020, 19, 236. [Google Scholar] [CrossRef]
- Cojocaru, A.; Colisson, L.; Kashefi, E.; Wallden, P. On the possibility of classical client blind quantum computing. Cryptography 2021, 5, 3. [Google Scholar] [CrossRef]
- Shan, R.T.; Chen, X.; Yuan, K.G. Multi-party blind quantum computation protocol with mutual authentication in network. Sci. China Inf. Sci. 2021, 64, 1–14. [Google Scholar] [CrossRef]
- Ma, X.; Qi, B.; Zhao, Y.; Lo, H.K. Practical decoy state for quantum key distribution. Phys. Rev. A 2005, 72, 012326. [Google Scholar] [CrossRef]
- Chien, C.H.; Van Meter, R.; Kuo, S.Y. Fault-tolerant operations for universal blind quantum computation. ACM J. Emerg. Technol. Comput. Syst. 2015, 12, 9. [Google Scholar] [CrossRef]
- Fujii, K. Quantum Computation with Topological Codes: From Qubit to Topological Fault-Tolerance; Springer: Berlin/Heidelberg, Germany, 2015; Volume 8. [Google Scholar]
- Tan, X.; Tao, H.; Zhang, X.; Zeng, X.; Xu, Q. Fault-tolerant blind quantum computing using GHZ states over depolarization channel. Quantum Inf. Process. 2021, 20, 1–14. [Google Scholar] [CrossRef]
- Morimae, T.; Koshiba, T. Impossibility of perfectly-secure one-round delegated quantum computing for classical client. Quantum Inf. Comput. 2019, 19, 214–221. [Google Scholar] [CrossRef]
- Raussendorf, R.; Browne, D.E.; Briegel, H.J. Measurement-based quantum computation on cluster states. Phys. Rev. A 2003, 68, 022312. [Google Scholar] [CrossRef]
- Broadbent, A.; Fitzsimons, J.; Kashefi, E. Measurement-based and universal blind quantum computation. In Proceedings of the International School on Formal Methods for the Design of Computer, Communication and Software Systems, Bertinoro, Italy, 21 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 43–86. [Google Scholar]
- Preskill, J. Fault-tolerant quantum computation. In Introduction to Quantum Computation and Information; World Scientific: Singapore, 1998; pp. 213–269. [Google Scholar]
- Nielsen, M.A.; Chuang, I. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2002. [Google Scholar]
- Raussendorf, R.; Briegel, H.J. A one-way quantum computer. Phys. Rev. Lett. 2001, 86, 5188. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).