Color Image Encryption Algorithm Based on Cross-Spiral Transformation and Zone Diffusion
Abstract
1. Introduction
2. Theoretical Principles
2.1. Color Image Encryption Algorithm
- (1)
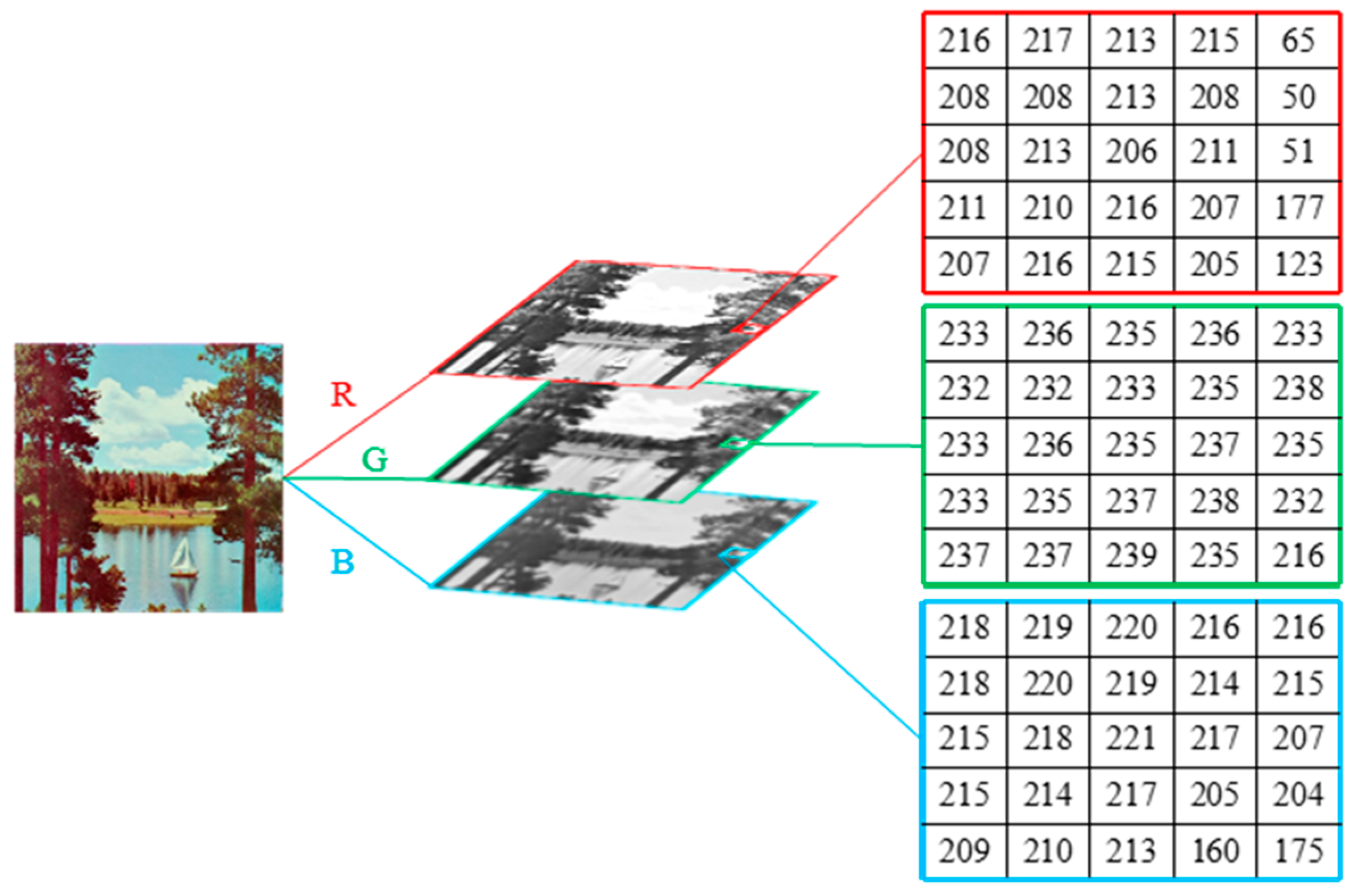
- The three channels are encrypted independently. Firstly, the three components, R, G, and B, of the color image are decomposed, as shown in Figure 2. Secondly, the same algorithm is used for the three channels and encrypted separately in the form of grayscale images. Finally, the grayscale ciphertext images of the three components are combined in their original order to form the final color ciphertext image. This line of thinking does not take into account the high correlation between the R, G, and B components, resulting in color images being slightly less defensive against attacks.
- (2)
- The three channels are encrypted in the form of grayscale images as a whole. Firstly, the three channels, R, G, and B, of the color image are decomposed, as shown in Figure 3. Secondly, the three channels are first stitched into a large grayscale image. Finally, the whole is encrypted in the form of a grayscale image to obtain a ciphertext image. This line of thinking would ignore the characteristics of color images.
2.2. Traditional Spiral Transformation
2.3. Cross Spiral Transformation
2.4. Chen’s Chaotic System
2.5. Piecewise Linear Chaotic Map
2.6. Zone Segmentation
3. Algorithm Description
3.1. Key Generation
3.2. Encryption Process
- (1)
- If the value of the index matrix X1, X2, and X3 is 1, it means that the pixel of the R component is selected;
- (2)
- If the value of the index matrix X1, X2, and X3 is 2, it means that the pixel of the G component is selected;
- (3)
- If the value of the index matrix X1, X2, and X3 is 3, it means that the pixel of the B component is selected.
- (1)
- Z1 zone diffusion:
- (2)
- Z2 zone diffusion:where i = dpx + 1, dpx + 2, …, m, and z = 1, 2, …, 24.
- (3)
- Z3 zone diffusion:where i = 1, 2, …, dpx, y = dpy +1, and dpy + 2, …, n.
- (4)
- Z4 zone diffusion:where i = 1, 2, …, dpx and z = 1, 2, …, 24.
| Algorithm 1: Encryption process. |
| Input: Plain color image I, h1, h2, h3, h4, h5 and h6 Output: Encryption image C 1: 2: 3: 4: 5: 6: 7: L1, L2, L3= Chen (x0, y0, z0, 1000 + 1: 1000 + m × n) 8: for t = 1 to mn do: 9: 10: 11: 12: 13: 14: 15: end for 16: X1 = reshape (A1, m, n) 17: X2 = reshape (A2, m, n) 18: X3 = reshape (A3, m, n) 19: when X1 = 1, X2 = 1, X3 = 1, R component is selected 20: when X1 = 2, X2 = 2, X3 = 2, G component is selected 21: when X1 = 3, X2 = 3, X3 = 3, B component is selected 22: for t = 1 to 3 do: 23: Pt= Cross spiral transform (I(:, :, t)) 24 : Qt = dec2bin(Pt) 25 : C( :, :, t) = Zone diffusion Qt 26 : Et = C( :, :, t) 27 : end for |
3.3. Decryption Process
4. Simulation Experiments and Results
5. Algorithm Analyses
5.1. Key Space Analysis
5.2. Key Sensitivity Analysis
5.3. Information Entropy Analysis
5.4. Histogram Analysis
5.5. Differential Attack Analysis
5.6. Correlation of Adjacent Pixels
5.7. Occlusion Attack Analysis
5.8. Chosen-Plaintext Attack
5.9. Randomness Test
5.10. Encryption Time and Computational Complexity Analysis
6. Conclusions and Outlooks
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, C.; Wang, X.; Xia, Z.; Ma, B.; Shi, Y.Q. Image description with polar harmonic fourier moments. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 40–52. [Google Scholar] [CrossRef]
- Asgari, C.M. A novel image encryption algorithm based on polynomial combination of chaotic maps and dynamic function generation. Signal Process. 2019, 157, 1–13. [Google Scholar] [CrossRef]
- Xiong, L.; Han, X. Robust reversible watermarking in encrypted image with secure multi-party based on lightweight cryptography. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 75–91. [Google Scholar] [CrossRef]
- Demirtas, M. A novel multiple grayscale image encryption method based on 3D bit-scrambling and diffusion. Optik 2022, 266, 169624. [Google Scholar] [CrossRef]
- Tong, L.; Zhou, N.; Huang, Z.; Xie, X.-W.; Liang, Y.-R. Nonlinear multi-image encryption scheme with the reality-preserving discrete fractional angular transform and DNA sequences. Secur. Commun. Netw. 2021, 20, 6650515. [Google Scholar] [CrossRef]
- Zhu, S.; Deng, X.; Zhang, W.; Zhu, C. Image encryption scheme based on newly designed chaotic map and parallel DNA coding. Mathematics 2023, 11, 231. [Google Scholar] [CrossRef]
- Huang, L.; Chai, B.; Xiang, J.; Zhang, Z.; Liu, J. Chaotic image encryption based on spiral traversal and finite field bidirectional diffusion. Phys. Scr. 2023, 98, 035217. [Google Scholar] [CrossRef]
- Zhou, S.; Qiu, Y.; Wang, X.; Zhang, Y. Novel image cryptosystem based on new 2D hyperchaotic map and dynamical chaotic S-box. Nonlinear Dyn. 2023, 111, 9571–9589. [Google Scholar] [CrossRef]
- Man, X.; Song, Y. Encryption of Color Images with an evolutionary framework controlled by chaotic systems. Entropy 2023, 25, 631. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1245–1257. [Google Scholar] [CrossRef]
- Wang, X.; Guan, N.; Yang, J. Image encryption algorithm with random scrambling based on one-dimensional logistic self-embedding chaotic map. Chaos Solitons Fractals 2021, 150, 111–129. [Google Scholar] [CrossRef]
- Naskar, P.K.; Bhattacharyya, S.; Mahatab, K.C.; Dhal, K.G.; Chaudhuri, A. An efficient block-level image encryption scheme based on multi-chaotic maps with DNA encoding. Nonlinear Dyn. 2021, 105, 3673–3698. [Google Scholar] [CrossRef]
- Chen, S.; Lü, J. Parameters identification and synchronization of chaotic systems based upon adaptive control. Phys. Lett. A 2002, 299, 353–358. [Google Scholar] [CrossRef]
- Rehman, A.U.; Liao, X. Selective encryption for gray images based on chaos and DNA complementary rules. Multimed. Tools Appl. 2015, 74, 4655–4677. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Yan, X.; Li, Q.; Wang, X. Image encryption based on chaotic sub-block scrambling and chaotic digit Selection diffusion. Opt. Lasers Eng. 2020, 134, 106202. [Google Scholar] [CrossRef]
- Li, S.; Zhao, L.; Yang, N. Medical image encryption based on 2D Zigzag confusion and dynamic diffusion. Secur. Commun. Netw. 2021, 2021, 6624809. [Google Scholar] [CrossRef]
- Lone, M.A.; Qureshi, S. RGB image encryption based on symmetric keys using Arnold transform, 3D chaotic map and affine hill cipher. Optik 2022, 260, 168880. [Google Scholar] [CrossRef]
- Zhao, Y.; Meng, R.; Zhang, Y.; Yang, Q. Image encryption algorithm based on a new chaotic system with Rubik’s cube transform and Brownian motion model. Optik 2023, 273, 170342. [Google Scholar] [CrossRef]
- Shen, H.; Shan, X.; Xu, M.; Tian, Z. A new chaotic image encryption algorithm based on transversals in a latin square. Entropy 2022, 24, 1574. [Google Scholar] [CrossRef]
- Tang, Z.; Yang, Y.; Xu, S.; Yu, C.; Zhang, X. Image encryption with double spiral scans and chaotic maps. Secur. Commun. Netw. 2019, 2019, 8694678. [Google Scholar] [CrossRef]
- Yuan, H.; Jiang, L. Image scrambling based on spiral filling of bits. Int. J. Signal Process. Image Process. Pattern Recognit. 2015, 8, 225–234. [Google Scholar] [CrossRef]
- Wang, Q.; Zhang, X.; Zhao, X. Color image encryption algorithm based on bidirectional spiral transformation and DNA coding. Phys. Scr. 2023, 98, 25211. [Google Scholar] [CrossRef]
- Dhiveyaswathi, T.; Balamurugan, G. An enhanced image encryption approach using four dimension hyperchaotic chen map. In Proceedings of the 2021 5th International Conference on Computer, Communication and Signal Processing, Chennai, India, 24–25 May 2021; pp. 89–93. [Google Scholar]
- Xiao, Y.; Chen, Y.; Long, C.; Shi, J.; Ma, J.; He, J. A novel hybrid secure method based on DNA encoding encryption and spiral scrambling in chaotic OFDM-PON. IEEE Photonics J. 2020, 12, 1–15. [Google Scholar] [CrossRef]
- Wang, X.; Chen, S. Chaotic image encryption algorithm based on dynamic spiral scrambling transform and Deoxyribonucleic Acid encoding operation. Mathematics 2020, 8, 160897–160914. [Google Scholar] [CrossRef]
- Liu, Y.; Shen, X.; Liu, J.; Peng, K. Optical asymmetric JTC cryptosystem based on multiplication-division operation and RSA algorithm. Opt. Laser Technol. 2023, 160, 109042. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Wang, X.; Li, Q.; Yan, X. Spiral-transform-based fractal sorting matrix for chaotic image encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2022, 69, 3320–3327. [Google Scholar] [CrossRef]
- Xu, J.; Zhao, B. Designing an image encryption algorithm based on hyperchaotic system and DCT. Int. J. Bifurc. Chaos 2023, 32, 2350021. [Google Scholar] [CrossRef]
- Wang, X.; Wang, X.; Teng, L.; Jiang, D.H.; Xian, Y. Lossless embedding: A visually meaningful image encryption algorithm based on hyperchaos and compressive sensing. Chin. Phys. B 2023, 32, 20503. [Google Scholar] [CrossRef]
- Huang, H.; Yang, S. Color image encryption based on logistic mapping and double random-phase encoding. IET Image Process 2017, 11, 211–216. [Google Scholar] [CrossRef]
- Zhu, H.; Dai, L.; Liu, Y.; Wu, L. A three-dimensional bit-level image encryption algorithm with Rubik’s cube method. Math. Comput. Simul. 2021, 185, 754–770. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, Z.; Yang, X. Fast image encryption algorithm based on 2D-FCSM and pseudo-wavelet transform. Nonlinear Dyn. 2023, 111, 6839–6853. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A novel bit-level image encryption algorithm based on chaotic maps. Opt. Lasers Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
- Wang, M.; Liu, H.; Zhao, M. Bit-level image encryption algorithm based on random-time S-Box substitution. Eur. Phys. J. Spec. Top. 2022, 231, 3225–3237. [Google Scholar] [CrossRef]
- Wang, M.; Wang, X.; Zhang, Y.; Zhou, S.; Zhao, T.; Yao, N. A novel chaotic system and its application in a color image cryptosystem. Opt. Lasers Eng. 2019, 121, 479–494. [Google Scholar] [CrossRef]
- Zhang, Q.; Han, J. A novel color image encryption algorithm based on image hashing, 6D hyperchaotic and DNA coding. Multimed. Tools Appl. 2021, 80, 13841–13864. [Google Scholar] [CrossRef]
- Liu, H.; Jin, C. A color image encryption scheme based on arnold scrambling and quantum chaotic. Int. J. Netw. Secur. 2017, 19, 347–357. [Google Scholar]
- Hu, C.; Xie, X.; Zhou, N. Colour image encryption scheme based on the real-valued discrete Gabor transform. J. Mod. Opt. 2022, 69, 511–522. [Google Scholar] [CrossRef]
- Gan, Z.; Chai, X.; Han, D.; Chen, Y.-R. A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput. Appl. 2019, 31, 7111–7130. [Google Scholar] [CrossRef]
- Lu, J.; Chen, G. A new chaotic attractor coined. Int. J. Bifurc. Chaos 2002, 12, 659–661. [Google Scholar] [CrossRef]
- Tian, J.; Lu, Y.; Zuo, X.; Liu, Y.; Qiao, B.; Fan, M.; Ge, Q.; Fan, S. A novel image encryption algorithm using PWLCM map-based CML chaotic system and dynamic DNA encryption. Multimed. Tools Appl. 2021, 80, 32841–32861. [Google Scholar] [CrossRef]
- The University of Southern California SIPI Image Database. Available online: http://sipi.usc.edu/database (accessed on 5 April 2023).
- Ahmad, P.K.; Ahmad, H.N.; Massoud, B.A.; Mirnia, M. A novel multi-image cryptosystem based on weighted plain images and using combined chaotic maps. Multimed. Syst. 2021, 27, 907–925. [Google Scholar]
- Ashish, G.; Vijay, K. A RGB image encryption technique using Lorenz and Rossler chaotic system on DNA sequences. Multimed. Tools Appl. 2018, 77, 27017–27039. [Google Scholar]
- Li, T.; Shi, J.; Zhang, D. Color image encryption based on joint permutation and diffusion. J. Electron. Imaging 2021, 30, 13008. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Yang, F.; Xian, Y. Color image encryption based on cross 2D hyperchaotic map using combined cycle shift scrambling and selecting diffusion. Nonlinear Dyn. 2021, 105, 1859–1876. [Google Scholar] [CrossRef]
- Su, Q.; Zhang, X.; Wang, H. A blind color image watermarking algorithm combined spatial domain and SVD. Int. J. Intell. Syst. 2021, 37, 4747–4771. [Google Scholar] [CrossRef]
- Muhammad, A.; Tabasam, R.; Sohail, Z. An image encryption scheme proposed by modifying chaotic tent map using fuzzy numbers. Multimed. Tools Appl. 2022, 10, 16861–16879. [Google Scholar]
- Zhang, X.; Gao, T. Multiple-image encryption algorithm based on the bit plane and superpixel. Multimed. Tools Appl. 2022, 12, 19969–19991. [Google Scholar] [CrossRef]
- Zhang, X.; Gong, Z. Color image encryption algorithm based on 3D Zigzag transformation and view planes. Multimed. Tools Appl. 2022, 81, 31753–31785. [Google Scholar] [CrossRef]
- Zhang, Y.; Xie, H.; Sun, J.; Zhang, H. An efficient multi-level encryption scheme for stereoscopic medical images based on coupled chaotic system and Otsu threshold segmentation. Comput. Biol. Med. 2022, 14, 105542. [Google Scholar] [CrossRef]
- Ahmad, L.M.; Shaima, Q. Encryption scheme for RGB images using chaos and affine hill cipher technique. Nonlinear Dyn. 2023, 111, 5919–5939. [Google Scholar]
- Erkan, U.; Toktas, A.; Toktas, F.; Alenezi, F. 2D eπ-map for image encryption. Inf. Sci. 2022, 589, 770–789. [Google Scholar] [CrossRef]
- Wen, J.; Xu, X.; Sun, K.; Jiang, Z.; Wang, X. Triple-image bit-level encryption algorithm based on double cross 2D hyperchaotic map. Nonlinear Dyn. 2023, 111, 6813–6838. [Google Scholar] [CrossRef]
- Zhang, X.; Hu, Y. Multiple-image encryption algorithm based on the 3D scrambling model and dynamic DNA coding. Opt. Laser Technol. 2021, 141, 107073. [Google Scholar] [CrossRef]
- Zhou, S.; Wang, X.; Zhang, Y. Novel image encryption scheme based on chaotic signals with finite-precision error. Inf. Sci. 2023, 62, 782–798. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, M.; Tian, J.; Gong, Z. Color image encryption algorithm based on dynamic block Zigzag transformation and six-sided star model. Electronics 2022, 11, 2512. [Google Scholar] [CrossRef]
- Yu, F.; Xu, S.; Xiao, X.; Yao, W.; Huang, Y.; Cai, S.; Yin, B.; Li, Y. Dynamics analysis, FPGA realization and image encryption application of a 5D memristive exponential hyperchaotic system. Integration 2023, 90, 58–70. [Google Scholar] [CrossRef]
- Doubla, I.S.; Njitacke, Z.T.; Ekonde, S.; Tsafack, N.; Nkapkop, J.D.D.; Kengne, J. Multistability and circuit implementation of tabu learning two-neuron model: Application to secure biomedical images in IoMT. Neural Comput. Appl. 2021, 33, 14945–14973. [Google Scholar] [CrossRef]





















| Algorithm | Proposed | Ref. [44] | Ref. [45] | Ref. [46] | Ref. [47] |
|---|---|---|---|---|---|
| Key space | 10161 | 10135 | 1056 | 10128 | 1090 |
| Figure | Decrypted Key | Pixel Difference Ratios |
|---|---|---|
| Figure 13a | the correct key | 0.0% |
| Figure 13b | δ1 + 10−14 | 99.7421% |
| Figure 13c | δ3 + 10−14 | 99.6357% |
| Figure 13d | δ5 + 10−14 | 99.2297% |
| Algorithm | Images | Entropy of Plain Images | Entropy of Encrypted Images | ||||
|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | ||
| Proposed | Baboon | 7.7066 | 7.4752 | 7.7522 | 7.9993 | 7.9991 | 7.9993 |
| House | 7.4156 | 7.2294 | 7.4353 | 7.9993 | 7.9992 | 7.9993 | |
| Sailboat | 7.1927 | 7.5641 | 7.3057 | 7.9741 | 7.9746 | 7.9745 | |
| Splash | 6.3093 | 6.9206 | 5.9263 | 7.9990 | 7.9990 | 7.9988 | |
| Average | 7.1560 | 7.2973 | 7.1048 | 7.9929 | 7.9929 | 7.9929 | |
| Ref. [22] | Baboon | 7.7066 | 7.4752 | 7.7522 | 7.9970 | 7.9974 | 7.9975 |
| Ref. [44] | Baboon | 7.7066 | 7.4752 | 7.7522 | 7.9970 | 7.9973 | 7.9973 |
| Ref. [45] | Baboon | 7.7066 | 7.4752 | 7.7522 | 7.9992 | 7.9994 | 7.9992 |
| Ref. [46] | Baboon | 7.7066 | 7.4752 | 7.7522 | 7.9972 | 7.9973 | 7.9974 |
| Color Encrypted Images | Components | Local Information Entropy | Pass/File | |
|---|---|---|---|---|
| Test Values | Average Values | |||
| Baboon | R | 7.9020 | 7.9021 | Passed |
| G | 7.9023 | Passed | ||
| B | 7.9021 | Passed | ||
| House | R | 7.9026 | 7.8026 | Passed |
| G | 7.9028 | Passed | ||
| B | 7.9024 | Passed | ||
| Sailboat | R | 7.9026 | 7.9028 | Passed |
| G | 7.9030 | Passed | ||
| B | 7.9028 | Passed | ||
| Splash | R | 7.9025 | 7.9022 | Passed |
| G | 7.9021 | Passed | ||
| B | 7.9022 | Passed | ||
| Algorithms | Images | NPCR (%) | UACI (%) | ||||
|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | ||
| Proposed | Baboon | 99.61 | 99.61 | 99.60 | 33.42 | 33.41 | 33.43 |
| House | 99.59 | 99.61 | 99.61 | 33.41 | 33.42 | 33.44 | |
| Sailboat | 99.64 | 99.60 | 99.60 | 33.47 | 33.51 | 33.50 | |
| Splash | 99.62 | 99.62 | 99.60 | 33.50 | 33.64 | 33.51 | |
| Ref. [22] | Baboon | 99.62 | 99.62 | 99.63 | 33.57 | 33.37 | 33.63 |
| Ref. [44] | Baboon | 99.61 | 99.55 | 99.60 | 33.45 | 33.41 | 33.28 |
| Ref. [45] | Sailboat | 99.59 | 99.62 | 99.60 | 33.47 | 33.46 | 33.48 |
| Ref. [46] | Baboon | 99.65 | 99.64 | 99.62 | 33.26 | 33.64 | 33.33 |
| Images | Channel | Plain Images | Encrypted Images | ||||
|---|---|---|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | Horizontal | Vertical | Diagonal | ||
| Baboon | R | 0.9227 | 0.8597 | 0.8476 | 0.0004 | −0.0003 | 0.00272 |
| G | 0.8656 | 0.7578 | 0.7260 | 0.0038 | 0.0009 | 0.0042 | |
| B | 0.9070 | 0.8776 | 0.8357 | −0.0010 | 0.0001 | −0.0013 | |
| House | R | 0.9543 | 0.9532 | 0.9184 | −0.0025 | −0.0013 | −0.0006 |
| G | 0.9339 | 0.9279 | 0.8771 | 0.0028 | −0.0015 | 0.0019 | |
| B | 0.9751 | 0.9591 | 0.9356 | 0.0021 | 0.001 | −0.0010 | |
| Sailboat | R | 0.9415 | 0.9365 | 0.9203 | 0.0100 | 0.0359 | 0.0407 |
| G | 0.9678 | 0.9664 | 0.9523 | 0.0162 | 0.0484 | 0.0510 | |
| B | 0.9691 | 0.9702 | 0.9511 | 0.0485 | 0.0810 | 0.1786 | |
| Splash | R | 0.9883 | 0.9942 | 0.9862 | 0.0031 | −0.0027 | −0.0023 |
| G | 0.9883 | 0.9877 | 0.9804 | −0.0052 | −0.0008 | 0.0019 | |
| B | 0.9864 | 0.9842 | 0.9753 | 0.0037 | 0.0021 | −0.0008 | |
| Images | Algorithms | Channel | Directions | ||
|---|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | |||
| Encrypted images of the Baboon | Proposed | R | 0.0004 | −0.0003 | 0.0027 |
| G | 0.0038 | 0.0009 | 0.0042 | ||
| B | −0.0010 | 0.0001 | −0.0013 | ||
| Ref. [22] | R | −0.0017 | −0.0007 | 0.0015 | |
| G | 0.0028 | 0.0039 | 0.0015 | ||
| B | 0.0041 | 0.0061 | 0.0025 | ||
| Ref. [44] | R | 0.0033 | −0.0013 | −0.0009 | |
| G | 0.0001 | 0.0020 | −0.0012 | ||
| B | 0.0000 | 0.0000 | 0.0004 | ||
| Ref. [45] | R | −0.0023 | 0.0014 | 0.0155 | |
| G | −0.0115 | −0.0178 | 0.0044 | ||
| B | 0.0066 | −0.0089 | −0.0132 | ||
| Ref. [46] | R | −0.0036 | −0.0109 | −0.0052 | |
| G | −0.0008 | 0.0070 | 0.0095 | ||
| B | −0.0009 | 0.0082 | −0.0113 | ||
| Test | p-Values | Pass/File |
|---|---|---|
| Random excursions variant test | 0.9921 | Passed |
| Frequency test | 0.7652 | Passed |
| Frequency test within a block | 0.0975 | Passed |
| Runs test | 0.8743 | Passed |
| Test for the longest run of the ones in a block | 0.0871 | Passed |
| Binary matrix rank test | 0.4563 | Passed |
| Discrete Fourier transform test | 0.7611 | Passed |
| Non-overlapping template matching test | 0.2187 | Passed |
| Overlapping template matching test | 0.3125 | Passed |
| Maurer’s “Universal Statistical” test | 0.5692 | Passed |
| Linear complexity test | 0.1143 | Passed |
| Serial test | 0.3217 | Passed |
| Approximate entropy test | 0.5689 | Passed |
| Cumulative sums test | 0.4303 | Passed |
| Random excursions test | 0.7615 | Passed |
| Algorithms | Size | Resolution | Time | Simulation Software |
|---|---|---|---|---|
| Proposed | 256 × 256 × 3 | 256 × 256 | 0.5 s | MATLAB |
| 512 × 512 × 3 | 512 × 512 | 1.7 s | ||
| 1024 × 1024 × 3 | 1024 × 1024 | 3.1 s | ||
| Ref. [22] | 256 × 256 × 3 | 256 × 256 | 1.1 s | MATLAB |
| Ref. [44] | 512 × 512 × 3 | 512 × 512 | 2.5 s | MATLAB |
| Ref. [45] | 512 × 512 × 3 | 512 × 512 | 2.1 s | MATLAB |
| Ref. [46] | 512 × 512 × 3 | 512 × 512 | 1.7 s | MATLAB |
| Ref. [58] | 512 × 512 | 512 × 512 | 5.78 s | FPGA |
| Ref. [59] | 512 × 512 × 3 | 512 × 512 | 5.18 s | FPGA |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Liu, M.; Yang, X. Color Image Encryption Algorithm Based on Cross-Spiral Transformation and Zone Diffusion. Mathematics 2023, 11, 3228. https://doi.org/10.3390/math11143228
Zhang X, Liu M, Yang X. Color Image Encryption Algorithm Based on Cross-Spiral Transformation and Zone Diffusion. Mathematics. 2023; 11(14):3228. https://doi.org/10.3390/math11143228
Chicago/Turabian StyleZhang, Xiaoqiang, Mi Liu, and Xiaochang Yang. 2023. "Color Image Encryption Algorithm Based on Cross-Spiral Transformation and Zone Diffusion" Mathematics 11, no. 14: 3228. https://doi.org/10.3390/math11143228
APA StyleZhang, X., Liu, M., & Yang, X. (2023). Color Image Encryption Algorithm Based on Cross-Spiral Transformation and Zone Diffusion. Mathematics, 11(14), 3228. https://doi.org/10.3390/math11143228







