A Joint Allocation Method of Multi-Jammer Cooperative Jamming Resources Based on Suppression Effectiveness
Abstract
:1. Introduction
- The radar detection performance change is regarded as an indicator to evaluate the jamming suppression effect, and the influence of different cooperative jamming methods on the radar detection probability are discussed. A calculation model for the detection probability of networked radars under cooperative jamming is proposed.
- A powerful variant of the ABC algorithm is proposed to improve the adaptability and performance of the algorithm. The IABC algorithm is proven to be effective by comparing it with different heuristics.
- The proposed IABC algorithm is improved by using crossover mutation operation, a mechanism for replacing the worst nectar, and random key encoding.
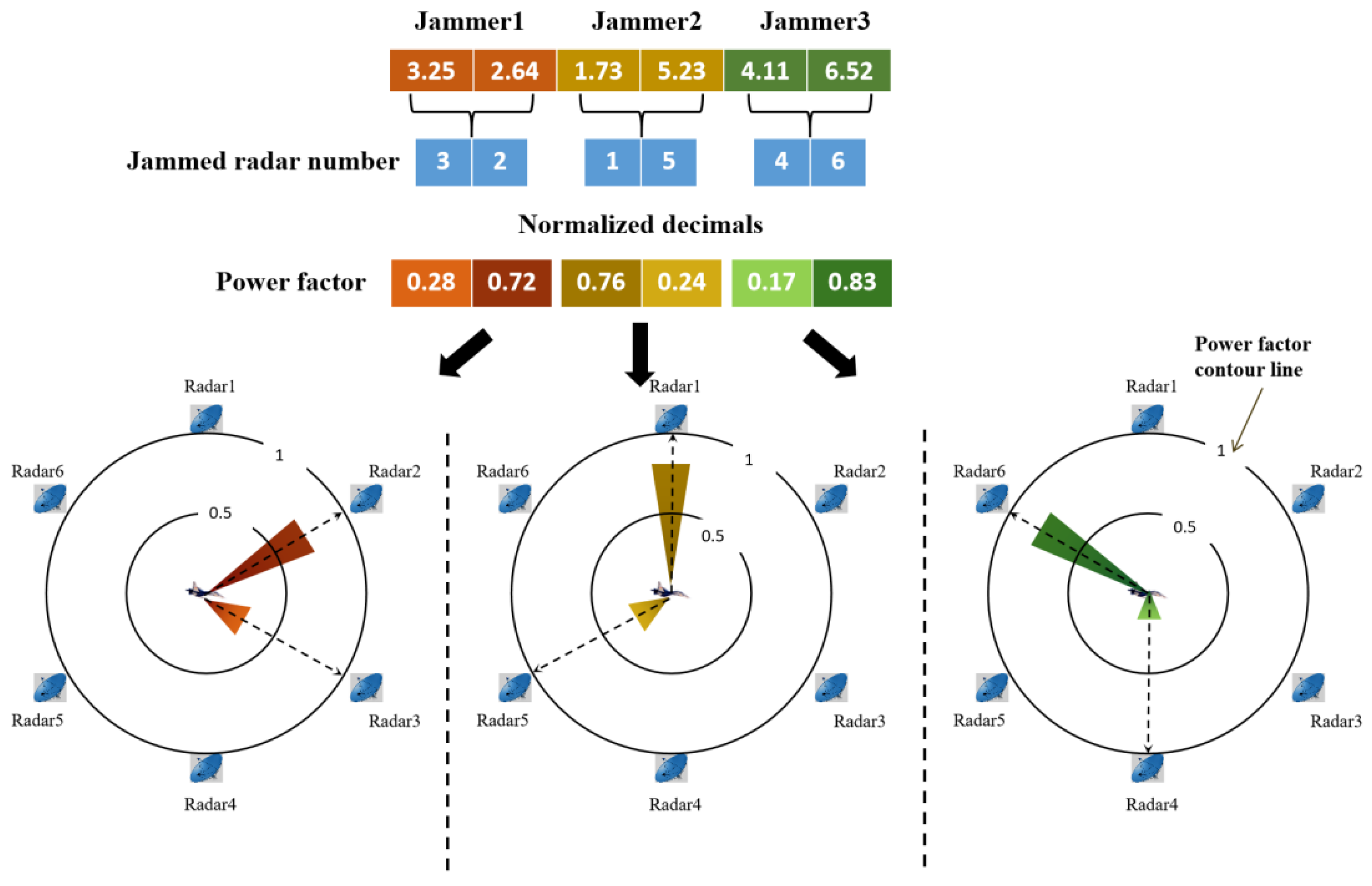
- This problem focuses on the dynamic allocation of two variables, including jamming beam and power. In order to compute the distribution scheme of multiple resources in parallel, we apply a random key encoding method. A random integral and a random deviation are mapped to jamming beam pointing and the proportion of power, respectively. In addition, a repair strategy for infeasible solutions is designed to ensure that all solutions in the iteration meet complex constraints.
2. Related Work
3. Multi-Jammer Cooperative Jamming Networked Radar Beam-Power Joint Allocation Model
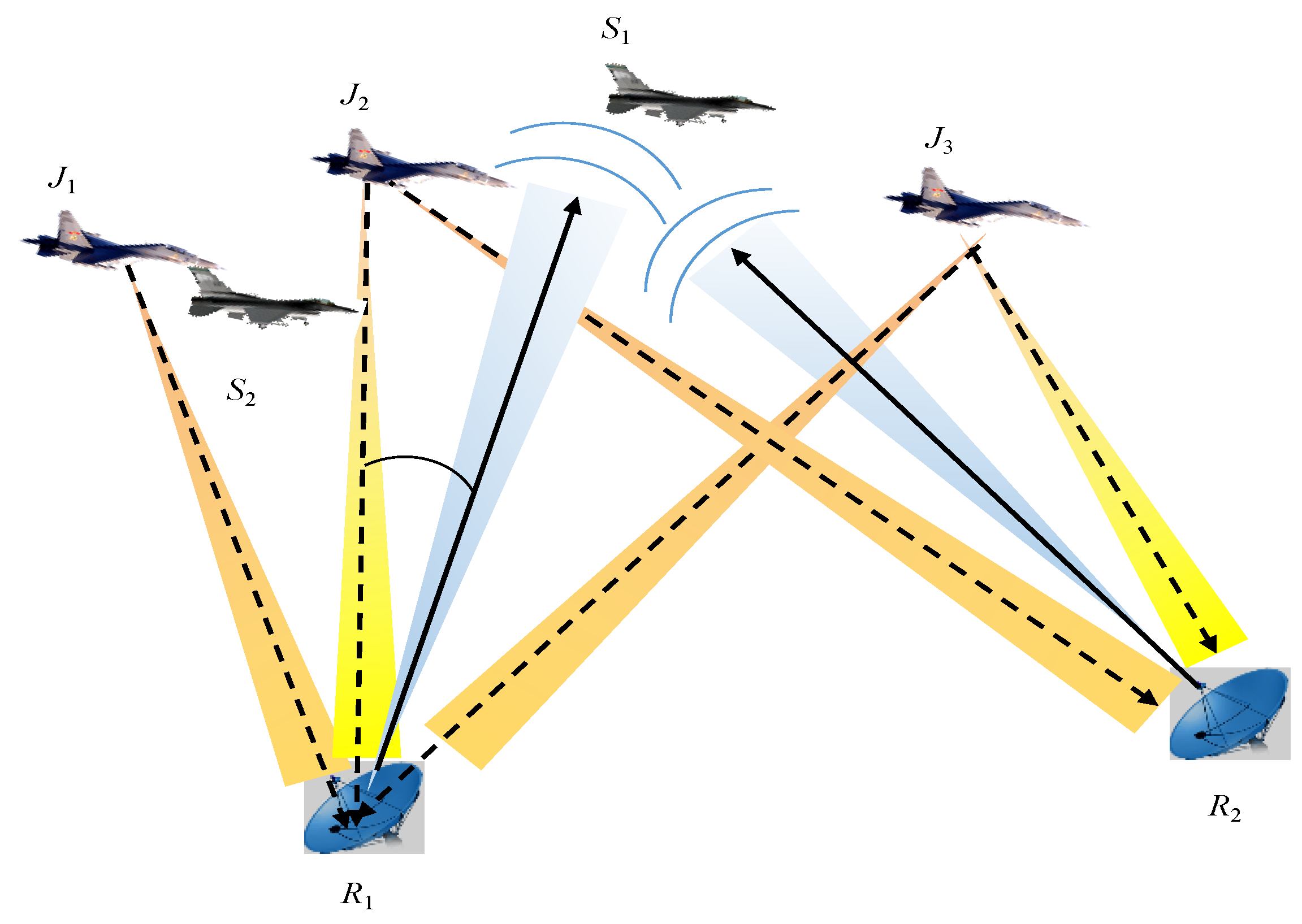
3.1. A Framework for Joint Allocation of Jamming Beam-Power
3.2. Jamming Beam-Power Allocation Constraint Model
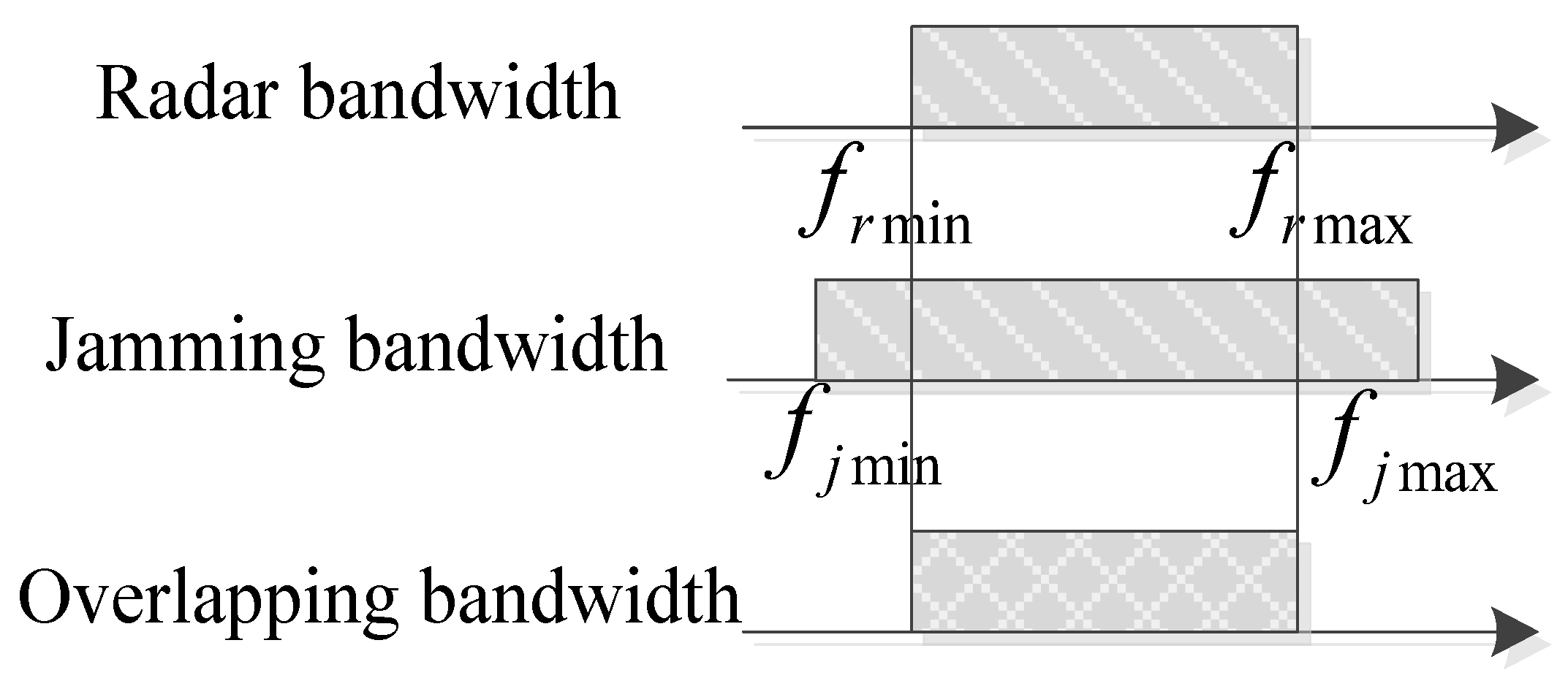
3.2.1. Beam Allocation Constraint Model
3.2.2. Power Allocation Constraint Model
- (1)
- Power factor constraints
3.3. Objective Function Model of Jamming Resource Allocation Based on Detection Probability
- (1)
- Radars are not jammed
- (2)
- Radars are jammed
4. A Beam-Power Joint Allocation Method for Multi-Jammers Cooperative Jamming Networked Radars
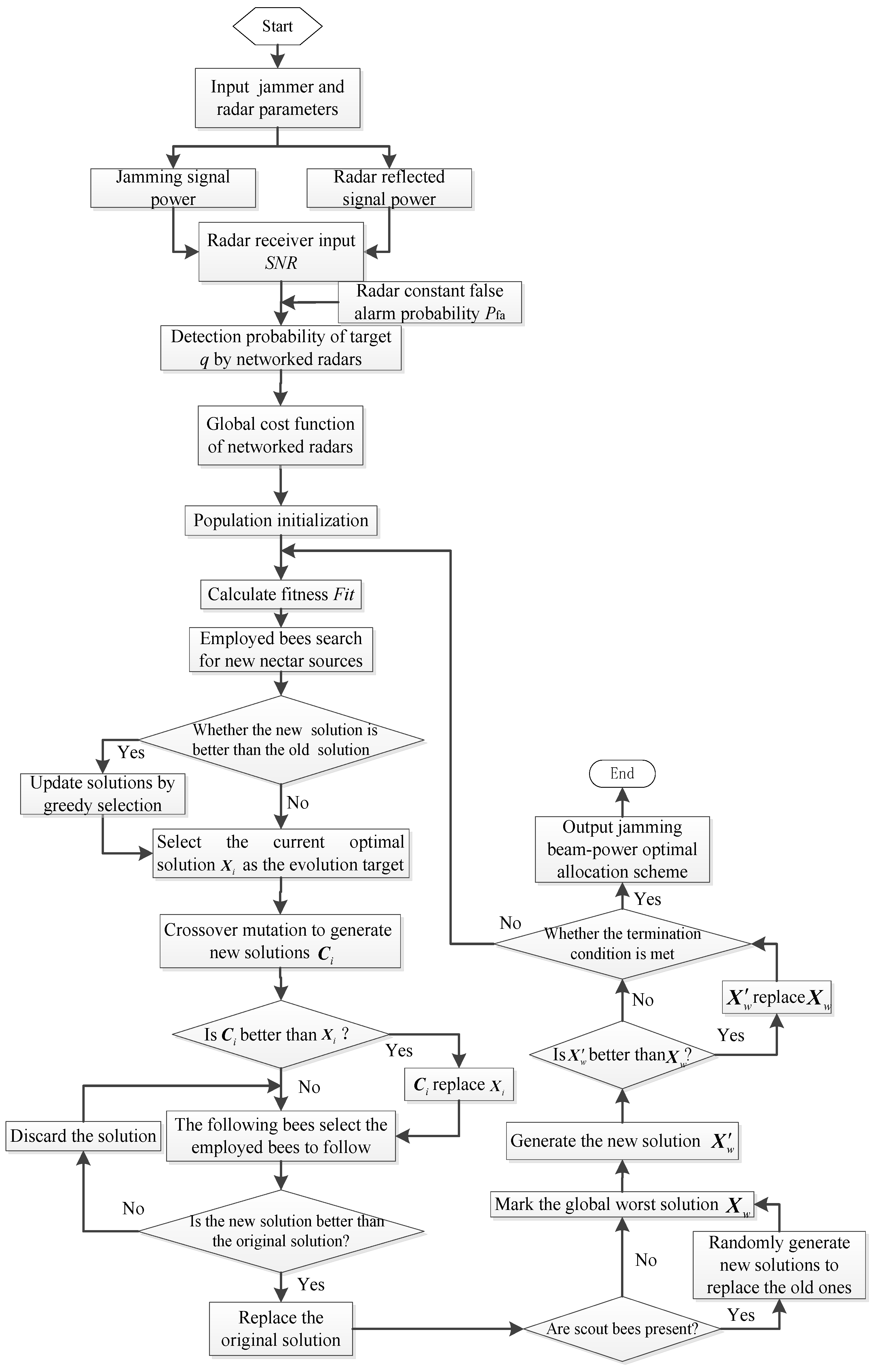
4.1. ABC Algorithm
- (1)
- Population initialization
- (2)
- Employed bee stage
- (3)
- Onlooker bee stage
- (4)
- Scout bee stage
4.2. Improvement of ABC Algorithm
4.2.1. Crossover Mutation Operation
4.2.2. The Worst Nectar Source Replacement Mechanism
4.2.3. A Random Key Based Encoding Method
| Algorithm 1 Adjustment process of infeasible solutions |
| Step 1 Determine the number of radars N and encoding length D. Initialize the population and limit the boundary conditions of the encoding. End End Step 2 Determine whether the updated solution satisfies the constraints. End |
4.2.4. The Flow of Cooperative Jamming Beam-Power Allocation Based on IABC Algorithm
| Algorithm 2 Pseudo-Code of cooperative jamming beam-power allocation based on IABC algorithm |
| Input: Population number NP, Initial nectar number SN, Maximum times of evaluations for fitness Gmax, Maximum search times in adjacent domains Limit = 100, Dimension of Vectors D, Lower bound and Upper bound . Output: The optimal individuals. 01: initialize population according to Algorithm 1 02: for i = 1 to SN 03: evaluate the nectar fitness 04: trial(i) = 0 04: end for; 05: while iter < Gmax 06: for each employed bee 07: obtain new solution Vi using Equation (10) 08: if Vi do not satisfy the constraints 09: Repair Vi according to Algorithm 1 10: end for 11: evaluate the fitness of Vi 12: if F(Xi) < F(Vi) 13: Xi = Vi 14: trial(i) = 0 15: end for 16: trial(i) = trial(i) + 1 17: obtain new solution Ci using Equations (13) and (14) 18: if Ci do not satisfy the constraints 19: Repair Ci according to Algorithm 1 20: end for 21: evaluate the fitness of Ci 22: if F(Xi) < F(Ci) 23: Xi = Ci 24: trial(i) = 0 25: end for 26: trial(i) = trial(i) + 1 27: iter = iter + 1 28: for each onlooker bee 29: select new solution by the roulette method 30: generate new solution Vi using Equation (10) 31: if Vi do not satisfy the constraints 32: Repair Vi according to Algorithm 1 33: end for 34: evaluate fitness value of new solution 35: if F(Xi) < F(Vi) 36: Xi = Vi 37:trial(i) = 0 38: end for 39:trial(i) = trial(i) + 1 40: iter = iter + 1 41: according to Equation (15) 42: if do not satisfy the constraints 43: Repair according to Algorithm 1 44: trial(i) = 0 45: end for 46: iter = iter + 1 47: for each scout bee 48: if trial(i)> Limit 49: generate new solution Xi according to Algorithm 1 50: iter = iter + 1 51: record the optimal solution so far 52: end while |
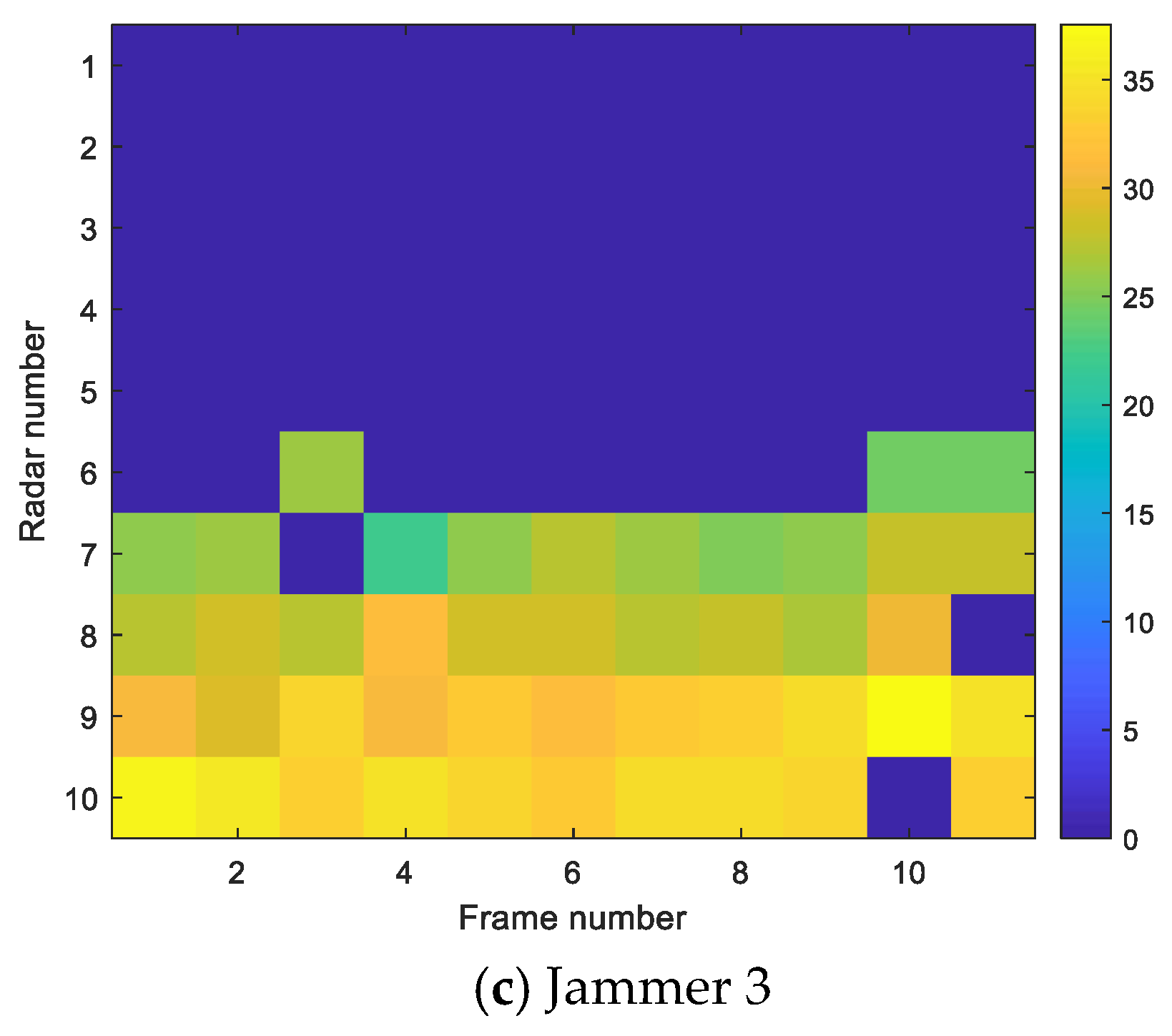
5. Numerical Simulation and Analysis
5.1. Scenario Setting and Experimental Results
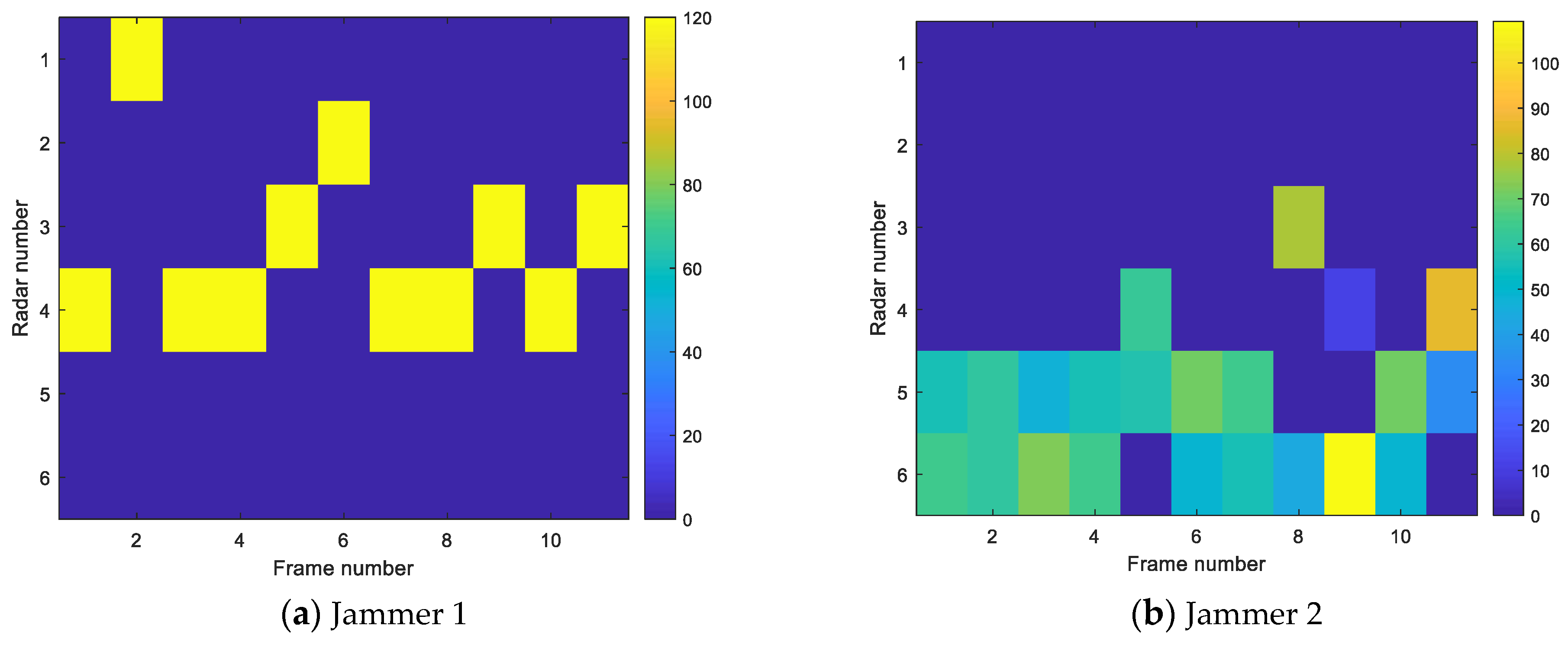
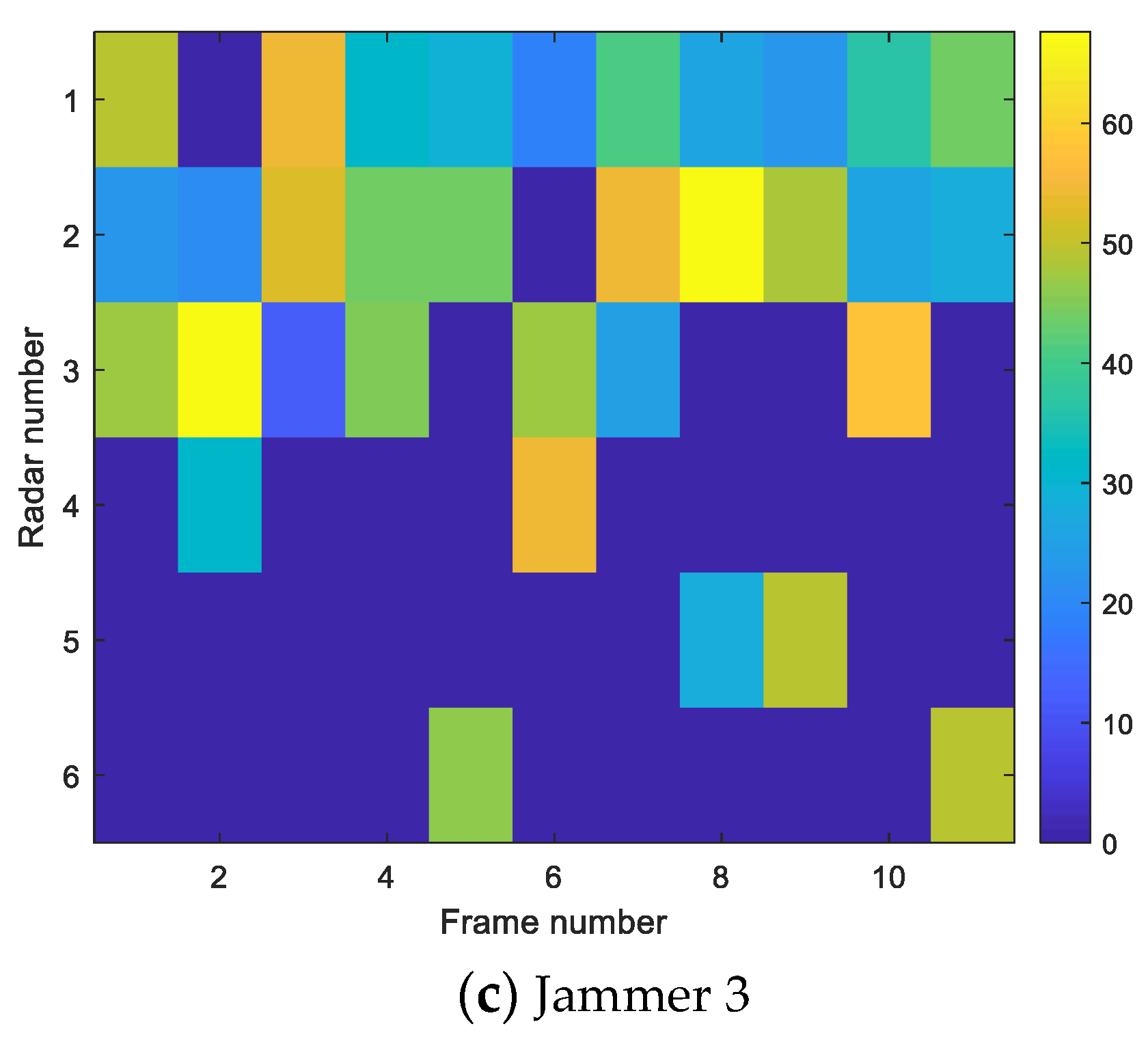
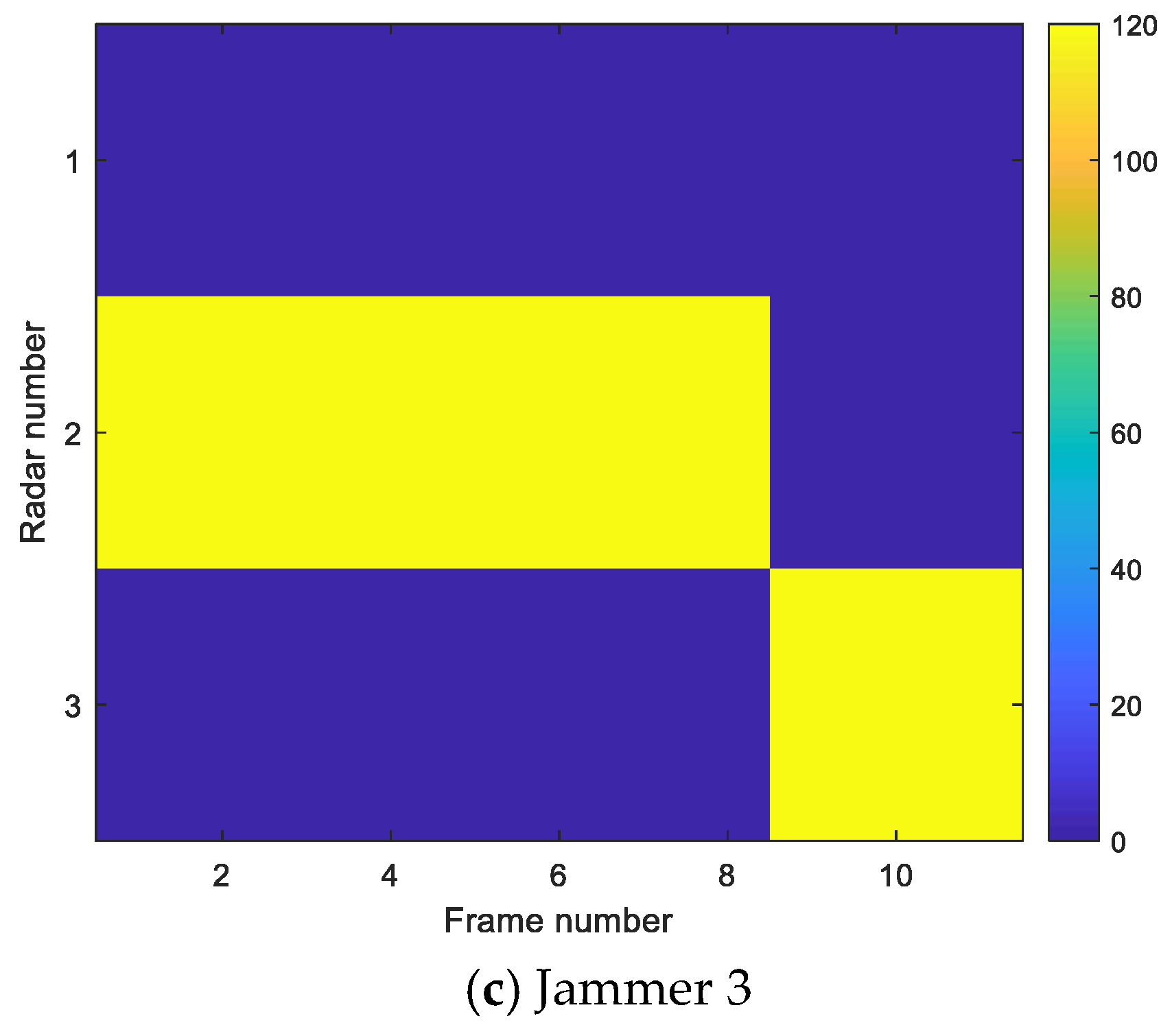
5.2. Comparative Analysis of Cooperative Jamming Simulation in Different Scenarios
- (1)
- Comparison experiment of jamming resource allocation between the multi-beam system and single-beam system
- (2)
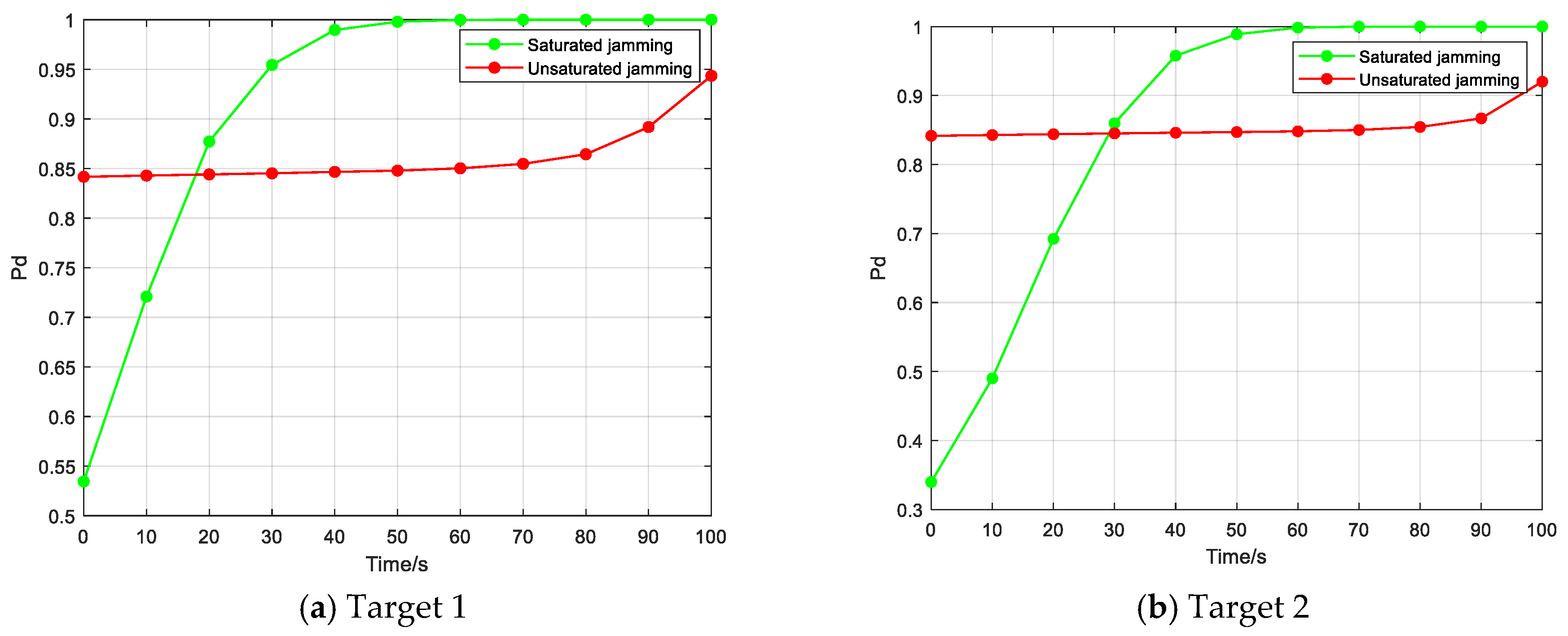
- Comparison experiment of resource allocation between saturated jamming and unsaturated jamming
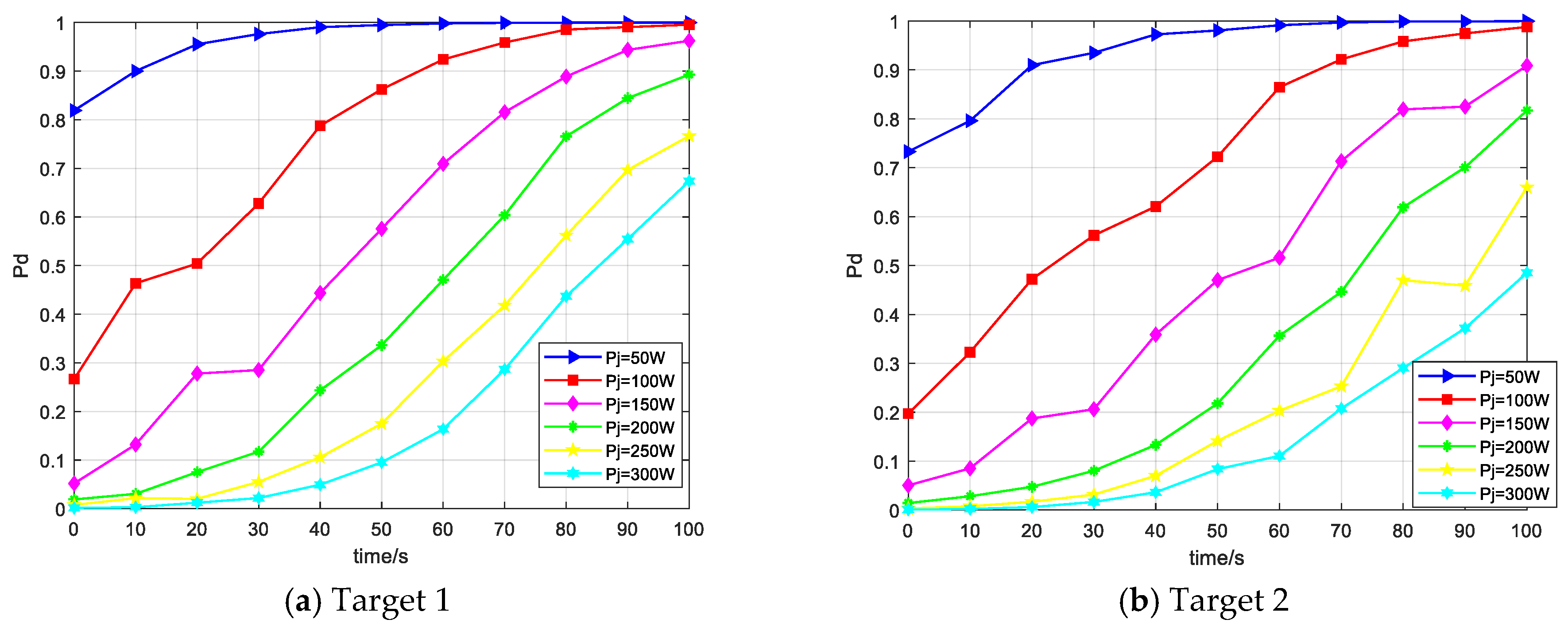
5.3. Influence of Jamming Parameters on Detection Probability
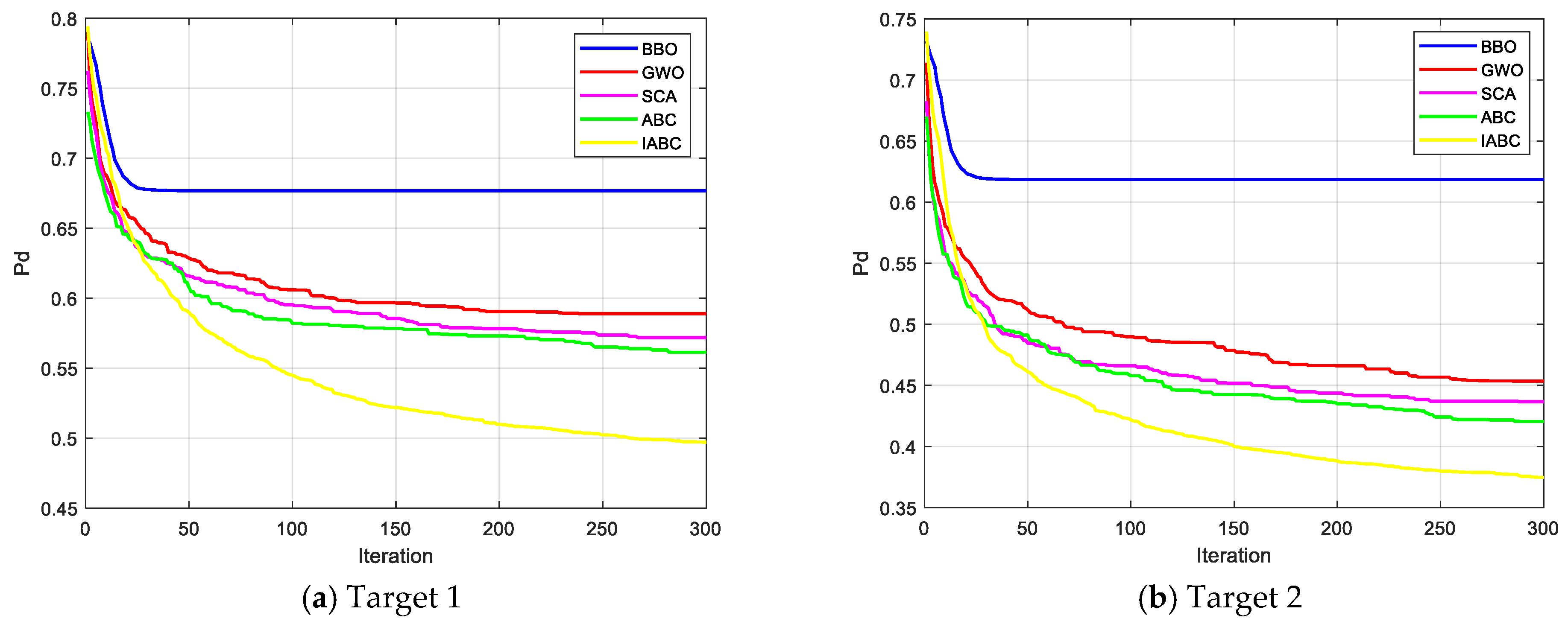
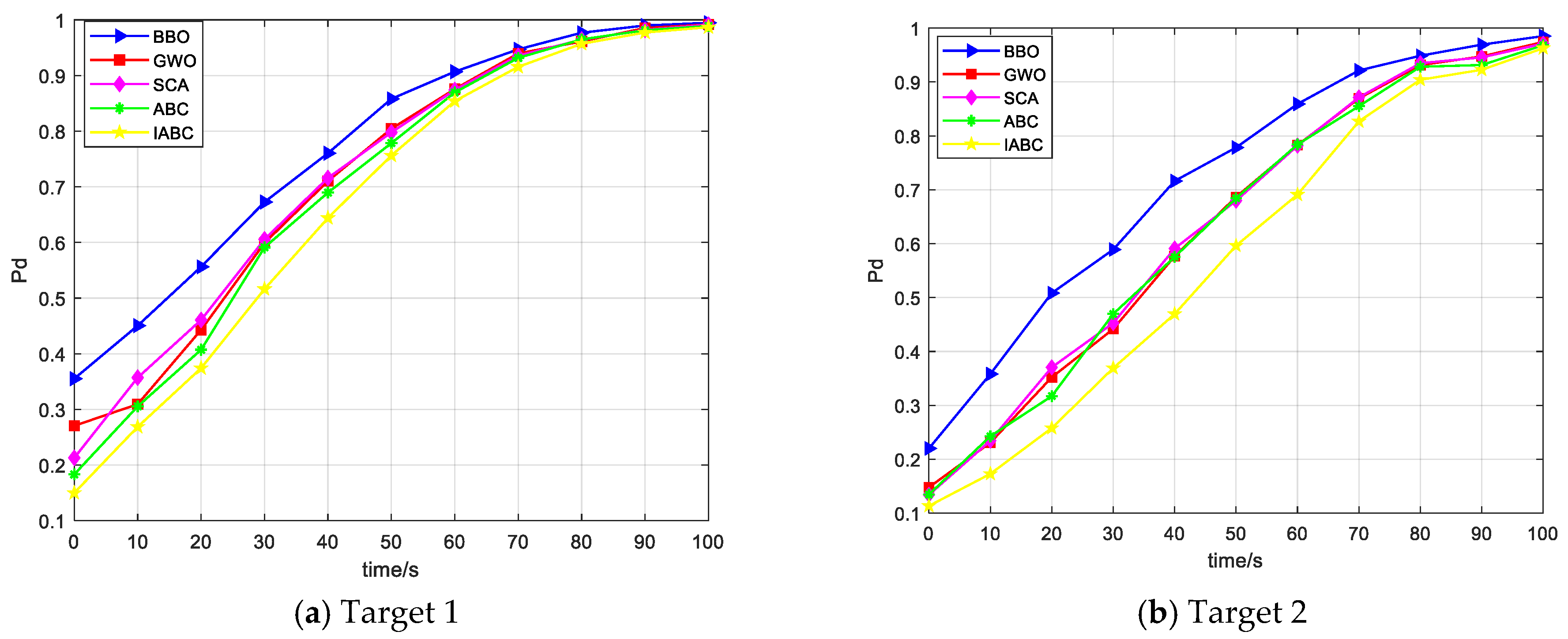
5.4. Experiment Analysis and Algorithm Performance Comparison
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Radar Reflected Signal Power Model
Appendix A.2. Jamming Signal Model
References
- Fu, X.Y. Study on Cooperative Jamming Policy and Jamming Methods of Radar; University of Electronic Science and Technology of China: Chengdu, China, 2020. [Google Scholar]
- Xiang, C.W.; Jiang, Q.S.; Qu, Z. Modeling and algorithm of dynamic resource assignment for ESJ electronic warfare aircraft. Command. Control. Simul. 2017, 39, 85–89. [Google Scholar]
- Wang, X.; Fei, Z.; Huang, J.; Zhang, J.A.; Yuan, J. Joint resource allocation and power control for radar interference mitigation in multi-UAV networks. Sci. China Inf. Sci. 2021, 64, 182307. [Google Scholar] [CrossRef]
- Liu, X. Study on Cooperative Jamming Techniques against Radar Network; National University of Defense Technology: Changsha, China, 2019. [Google Scholar]
- Pan, Y.H.; Gao, Y.L.; Zhang, L.; Liu, W. Resource allocation optimization techniques for multi-jammer cooperative noise jamming. J. Air Force Early Warn. Acad. 2017, 31, 346–350. [Google Scholar]
- Cui, Z.M.; Peng, S.R.; Ren, M.Q.; Long, S.M. Research on multi-beam interference resource scheduling based on beam quantity control. J. Air Force Early Warn. Acad. 2020, 34, 274–278. [Google Scholar]
- Song, H.F.; Wu, H.; Cheng, S.Y.; Chen, Y. Integrated management algorithm of jamming resources in multi-beam jamming systems. Acta Armamentarh 2013, 34, 332–338. [Google Scholar]
- Gao, X.G.; Hu, M.; Zheng, J.S. Jamming strategy for single plane to multi-target in task of penetration. Syst. Eng. Electron. 2010, 32, 1239–1243. [Google Scholar]
- Wan, K.F.; Gao, X.G.; Liu, Y. Optimal power partitioning for cooperative electronic jamming based on Lanchester with variable efficiency factors. Syst. Eng. Electron. 2011, 33, 1544–1547. [Google Scholar]
- Liu, Q.; Wang, X.H.; Wang, X.; Cheng, S.Y. A study on methods of active barrage jamming power assignment based on multi-targets. Fire Control. Command. Control. 2012, 37, 164–166. [Google Scholar]
- Li, X.M.; Dong, T.L.; Huang, G.M. A efficient Distribution method of jamming power to distributed MIMO radar. Fire Control. Command. Control. 2017, 42, 26–31. [Google Scholar]
- He, J.; Huang, C.; Han, G.X. Jamming blanketed zone computing model of multiple radar jammers against airborne targeting radar. Oper. Res. Manag. Sci. 2016, 25, 39–43. [Google Scholar]
- Zhang, D.L.; Yi, W.; Kong, L.J. Optimal joint allocation of multijammer resources for jamming netted radar system. J. Or Radar 2021, 10, 595–606. [Google Scholar]
- Cheng, Y.J.; Ma, H.; Xu, Z. Influence of distributed jamming of UAV to detecting capability of the air-defence radar. Command. Control. Simul. 2014, 36, 9–12+22. [Google Scholar]
- Zhu, Y.; Wang, P.G.; Jiang, Z.B. Modeling and Analysis of Radar Detection Range in Jamming. Mod. Radar 2006, 28, 12–14. [Google Scholar]
- Hou, D.Q.; Qi, F.; Yang, Z. Models for Radar Detection Probability Based on Operation Simulation. Electron. Inf. Warf. Technol. 2016, 31, 61–64. [Google Scholar]
- Shi, R.; Liu, J. Application of Intelligent Optimization Methods in Jamming Resource Allocation: A Review. Electron. Opt. Control. 2019, 26, 54–61. [Google Scholar]
- Luo, R.H.; Li, S.M. Optimization of Firepower Allocation Based on Improved BBO Algorithm. J. Nanjing Univ. Aeronaut. Astronaut. 2020, 52, 897–902. [Google Scholar] [CrossRef]
- Xing, H.X.; Wu, H.; Chen, Y.; Zhang, X. Multi-efficiency optimization method of jamming resource based on multi-objective grey wolf optimizer. J. Beijing Univ. Aeronaut. Astronaut. 2020, 46, 1990–1998. [Google Scholar]
- Yong, L.Q.; Li, Y.H.; Jia, W. Literature Survey on Research and Application of Sine Cosine Algorithm. Comput. Eng. Appl. 2020, 56, 26–34. [Google Scholar]
- Li, C. Radar Jamming Decision Making Technology Based on Swarm Intelligence Algorithm; Xidian University: Xi’an, China, 2021. [Google Scholar]
- Wang, B.Y. Research on the Online Effectiveness Evaluation of Radar Countermeasure; Xidian University: Xi’an, China, 2018. [Google Scholar]
- Zorarpacı, E.; Ayşe, Ö.S. Privacy preserving rule-based classifier using modified artificial bee colony algorithm. Expert Syst. Appl. 2021, 183, 115437. [Google Scholar] [CrossRef]
- Brajević, I. A shuffle-based artificial bee colony algorithm for solving integer programming and minimax problems. Mathematics 2021, 9, 1211. [Google Scholar] [CrossRef]
- Yildizdan, G.; Baykan, Ö.K. A New Hybrid BA_ABC Algorithm for Global Optimization Problems. Mathematics 2020, 8, 1749. [Google Scholar] [CrossRef]
- Sun, N.; Lu, Y. A self-adaptive genetic algorithm with improved mutation mode based on measurement of population diversity. Neural Comput. Appl. 2019, 31, 1435–1443. [Google Scholar] [CrossRef]
- Zhou, Y.Y. Principles and Technologies of Electronic Warfare System; Publishing House of Electronics Industry: Beijing, China, 2014; pp. 130–133. [Google Scholar]

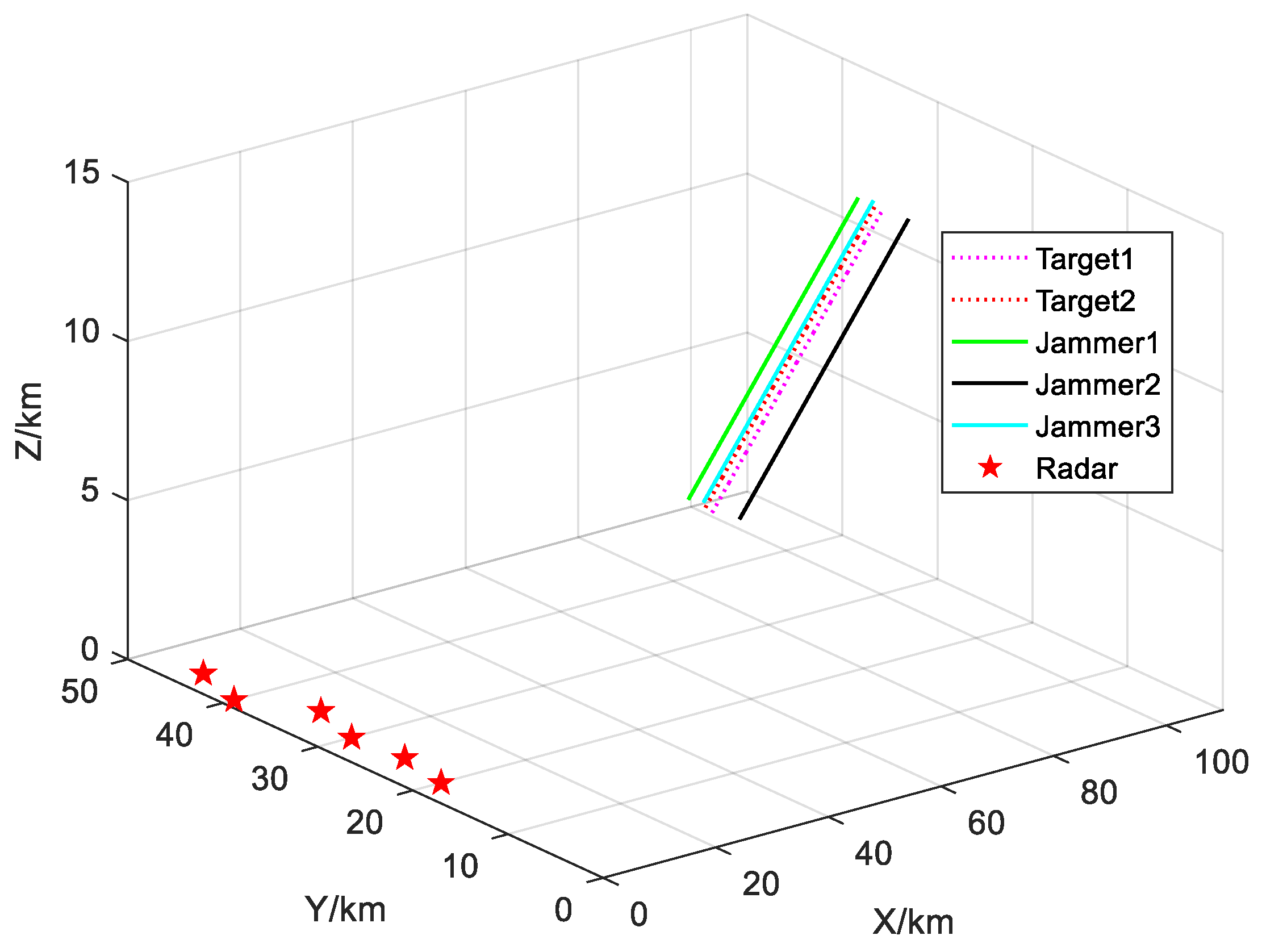








| Coordinate/km | |
|---|---|
| Target 1 | [100, 30, 12] |
| Target 2 | [100.5, 31, 12] |
| Jammer 1 | [101, 33, 12] |
| Jammer 2 | [101.5, 28, 12] |
| Jammer 3 | [102, 32, 12] |
| Coordinate/km | |
|---|---|
| Radar 1 | [5, 20, 0] |
| Radar 2 | [7, 25, 0] |
| Radar 3 | [6, 30, 0] |
| Radar 4 | [9, 35, 0] |
| Radar 5 | [2, 40, 0] |
| Radar 6 | [5, 45, 0] |
| Index | Value | Index | Value |
|---|---|---|---|
| 120 W | 0.1 m | ||
| 10 dB | 3° | ||
| 10 MHz | 6 dB | ||
| 0.5 | [−3000, 0, −80] m/s |
| Index | Value | Index | Value |
|---|---|---|---|
| 200 MW | 3 dB | ||
| 40 dB | 10−6 | ||
| 10 MHz | 0.1 m | ||
| 6 dB | 1 m2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xing, H.; Xing, Q.; Wang, K. A Joint Allocation Method of Multi-Jammer Cooperative Jamming Resources Based on Suppression Effectiveness. Mathematics 2023, 11, 826. https://doi.org/10.3390/math11040826
Xing H, Xing Q, Wang K. A Joint Allocation Method of Multi-Jammer Cooperative Jamming Resources Based on Suppression Effectiveness. Mathematics. 2023; 11(4):826. https://doi.org/10.3390/math11040826
Chicago/Turabian StyleXing, Huaixi, Qinghua Xing, and Kun Wang. 2023. "A Joint Allocation Method of Multi-Jammer Cooperative Jamming Resources Based on Suppression Effectiveness" Mathematics 11, no. 4: 826. https://doi.org/10.3390/math11040826






