Numerical Method for a Risk Model with Two-Sided Jumps and Proportional Investment
Abstract
1. Introduction
- (1)
- How do the upward jumps and the proportional investment affect dividend payments?
- (2)
- How does the volatility rate of risky assets affect dividend payments?
- (3)
- If the explicit solution for the related actuarial quantity is difficult to obtain, does the numerical solution exist?
- (4)
- Can we find the admissible optimal strategy through numerical simulation?
2. Problem Formulation
3. Dynamic Programming
3.1. HJB Equation
- is strictly increasing.
- is strictly concave.
3.2. Verification of Optimality
4. Integro-Differential Equations
5. Sinc Asymptotic Numerical Analysis
5.1. Sinc Function Preliminaries
5.2. Numerical Approximate Solution
5.3. Error Analysis
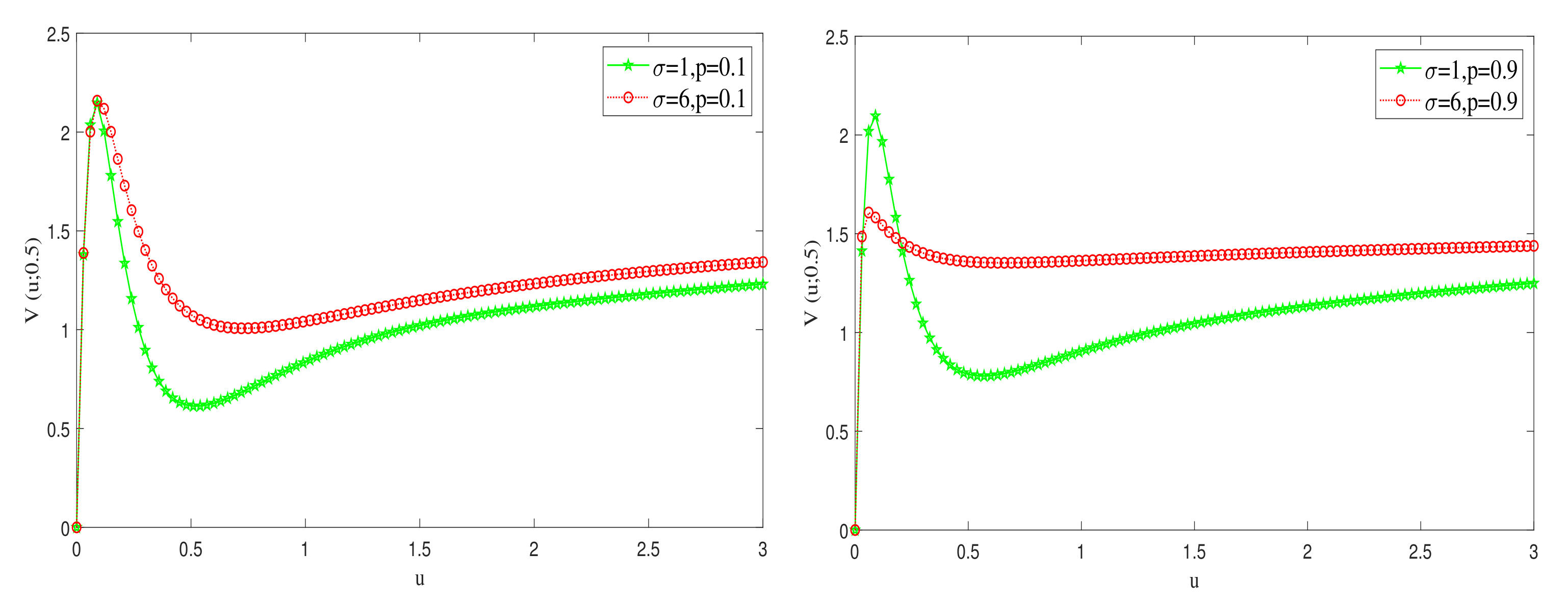
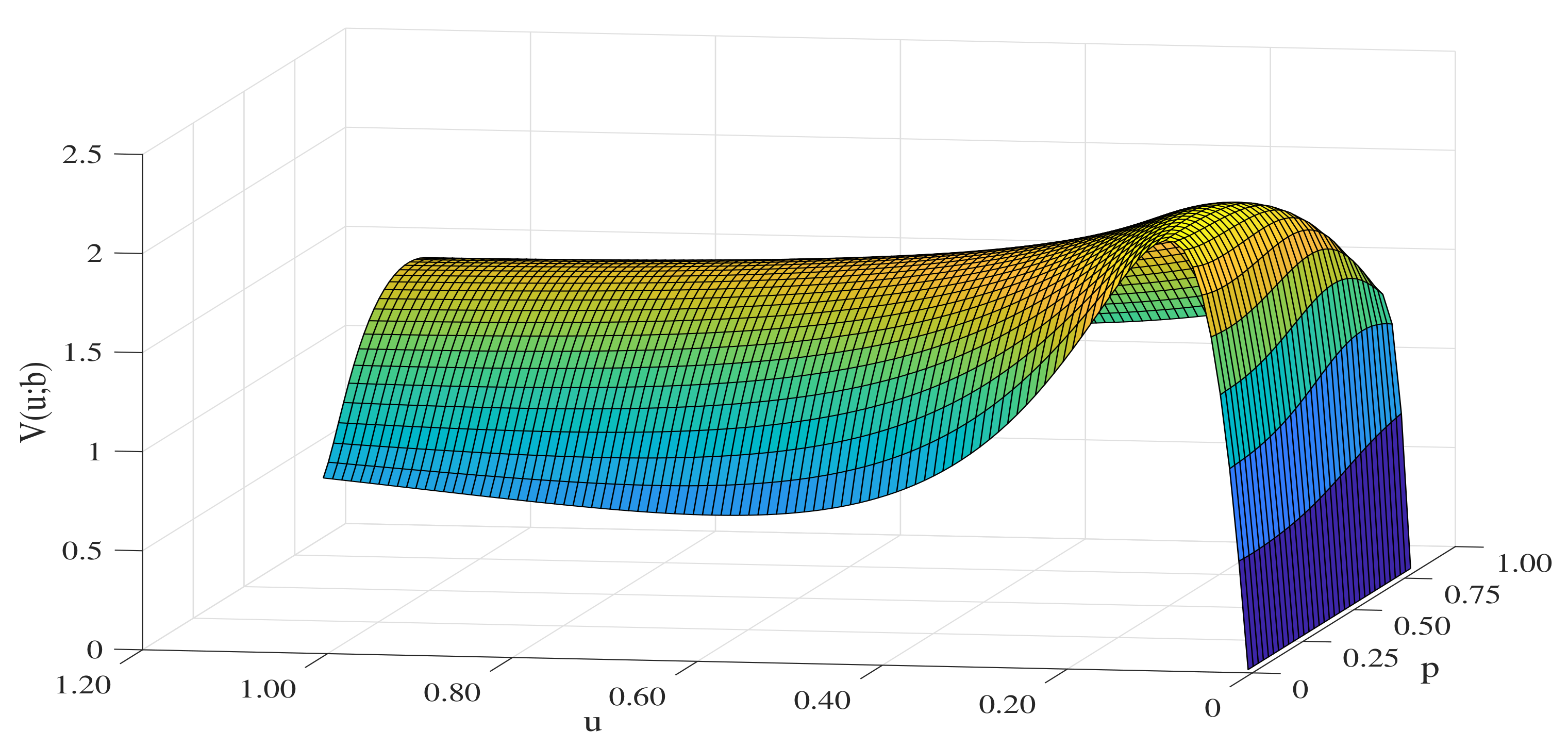
6. Numerical Illustrations
6.1. Error Analysis Example
6.2. Sensitivity Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Terziolu, M.K. Advances in Econometrics, Operational Research, Data Science and Actuarial Studies: Techniques and Theories; Springer: New York, NY, USA, 2021. [Google Scholar]
- Wüthrich, M.V.; Merz, M. Statistical Foundations of Actuarial Learning and its Applications; Springer: New York, NY, USA, 2023. [Google Scholar]
- Wüthrich, M.V.; Merz, M. Financial Modeling, Actuarial Valuation and Solvency in Insurance; Springer: New York, NY, USA, 2013. [Google Scholar]
- Gerber, H.U.; Shiu, E.S. On the time value of ruin. North Am. Actuar. J. 1998, 2, 48–72. [Google Scholar] [CrossRef]
- Albrecher, H.; Cheung, E.C.; Thonhauser, S. Randomized observation periods for the compound Poisson risk model: The discounted penalty function. Scand. Actuar. J. 2013, 2013, 424–452. [Google Scholar] [CrossRef]
- Cheung, E.C.; Liu, H. Joint moments of discounted claims and discounted perturbation until ruin in the compound Poisson risk model with diffusion. Probab. Eng. Inf. Sci. 2022, 1–31. [Google Scholar] [CrossRef]
- Zhu, J.; Li, S. Time-consistent investment and reinsurance strategies for mean-variance insurers under stochastic interest rate and stochastic volatility. Mathematics 2020, 8, 2183. [Google Scholar] [CrossRef]
- Pirozzi, E. On a fractional stochastic risk model with a random initial surplus and a multi-layer strategy. Mathematics 2022, 10, 570. [Google Scholar] [CrossRef]
- Ng, A.C. On a dual model with a dividend threshold. Insur. Math. Econ. 2009, 44, 315–324. [Google Scholar] [CrossRef]
- Bayraktar, E.; Egami, M. Optimizing venture capital investments in a jump diffusion model. Math. Methods Oper. Res. 2008, 67, 21–42. [Google Scholar] [CrossRef]
- Boucherie, R.J.; Boxma, O.J.; Sigman, K. A note on negative customers, GI/G/1 workload, and risk processes. Probab. Eng. Informational Sci. 1997, 11, 305–311. [Google Scholar] [CrossRef]
- Cheung, E.C.; Liu, H.; Willmot, G.E. Joint moments of the total discounted gains and losses in the renewal risk model with two-sided jumps. Appl. Math. Comput. 2018, 331, 358–377. [Google Scholar] [CrossRef]
- Martín-González, E.M.; Murillo-Salas, A.; Pantí, H. Gerber-Shiu function for a class of Markov-modulated Lévy risk processes with two-sided jumps. Methodol. Comput. Appl. Probab. 2022, 24, 2779–2800. [Google Scholar] [CrossRef]
- Rebello, J.J.; Thampi, K. Some ruin theory components of two sided jump problems under renewal risk process. Int. Math. Forum 2017, 12, 311–325. [Google Scholar] [CrossRef]
- Ivanovs, J. On scale functions for Lévy processes with negative phase-type jumps. Queueing Syst. 2021, 98, 3–19. [Google Scholar] [CrossRef]
- Zhang, L. The Erlang (n) risk model with two-sided jumps and a constant dividend barrier. Commun. Stat. Theory Methods 2021, 50, 5899–5917. [Google Scholar] [CrossRef]
- Zhuo, W.; Yang, H.; Chen, X. Expected discounted penalty function for a phase-type risk model with stochastic return on investment and random observation periods. Kybernetes 2018, 47, 1420–1434. [Google Scholar] [CrossRef]
- Oseni, B.M.; Jolayemi, E.T. Ruin probabilities in perturbed risk process with stochastic investment and force of interest. Kybernetes 2018, 13, 1593–1608. [Google Scholar] [CrossRef]
- Elghribi, M. Stochastic calculus in a risk model with stochastic return on investments. Stochastics Int. J. Probab. Stoch. Processes 2020, 93, 110–129. [Google Scholar] [CrossRef]
- Chen, S.; Li, Z.; Li, K. Optimal investment–reinsurance policy for an insurance company with VaR constraint. Insur. Math. Econ. 2010, 47, 144–153. [Google Scholar] [CrossRef]
- Zhang, Q.; Chen, P. Robust optimal proportional reinsurance and investment strategy for an insurer with defaultable risks and jumps. J. Comput. Appl. Math. 2019, 356, 46–66. [Google Scholar] [CrossRef]
- De Finetti, B. Su un’impostazione alternativa della teoria collettiva del rischio. In Transactions of the XVth International Congress of Actuaries; Actuarial Society of America: New York, NY, USA, 1957; Volume 2, pp. 433–443. [Google Scholar]
- Vierkötter, M.; Schmidli, H. On optimal dividends with exponential and linear penalty payments. Insur. Math. Econ. 2017, 72, 265–270. [Google Scholar] [CrossRef]
- Albrecher, H.; Azcue, P.; Muler, N. Optimal dividend strategies for two collaborating insurance companies. Adv. Appl. Probab. 2017, 49, 515–548. [Google Scholar] [CrossRef]
- Chen, X.; Ou, H. A compound Poisson risk model with proportional investment. J. Comput. Appl. Math. 2013, 242, 248–260. [Google Scholar] [CrossRef]
- Albrecher, H.; Azcue, P.; Muler, N. Optimal ratcheting of dividends in insurance. SIAM J. Control Optim. 2020, 58, 1822–1845. [Google Scholar] [CrossRef]
- Dong, H.; Yin, C.; Dai, H. Spectrally negative Lévy risk model under Erlangized barrier strategy. J. Comput. Appl. Math. 2019, 351, 101–116. [Google Scholar] [CrossRef]
- Chen, Y.; Bian, B. Optimal investment and dividend policy in an insurance company: A varied bound for dividend rates. Discret. Contin. Dyn. Syst. 2019, 24, 5083–5105. [Google Scholar] [CrossRef]
- Bo, L.; Song, R.; Tang, D.; Wang, Y.; Yang, X. Lévy risk model with two-sided jumps and a barrier dividend strategy. Insur. Math. Econ. 2012, 50, 280–291. [Google Scholar] [CrossRef]
- Palmowski, Z.; Vatamidou, E. Phase-type approximations perturbed by a heavy-tailed component for the Gerber-Shiu function of risk processes with two-sided jumps. Stoch. Model. 2020, 36, 337–363. [Google Scholar] [CrossRef]
- Chen, X.; Xiao, T.; Yang, X.q. A Markov-modulated jump-diffusion risk model with randomized observation periods and threshold dividend strategy. Insur. Math. Econ. 2014, 54, 76–83. [Google Scholar] [CrossRef]
- Gerber, H.U.; Shiu, E.S. On optimal dividend strategies in the compound Poisson model. North Am. Actuar. J. 2006, 10, 76–93. [Google Scholar] [CrossRef]
- Schmidli, H. On minimizing the ruin probability by investment and reinsurance. Ann. Appl. Probab. 2002, 12, 890–907. [Google Scholar] [CrossRef]
- Jgaard, B.H.; Taksar, M. Controlling risk exposure and dividends payout schemes: Insurance company example. Math. Financ. 1999, 9, 153–182. [Google Scholar] [CrossRef]
- Albrecher, H.; Thonhauser, S. Optimal dividend strategies for a risk process under force of interest. Insur. Math. Econ. 2008, 43, 134–149. [Google Scholar] [CrossRef]
- Wan, N. Dividend payments with a threshold strategy in the compound Poisson risk model perturbed by diffusion. Insur. Math. Econ. 2007, 40, 509–523. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, X. Linearized and rational approximation method for solving non-linear Burgers’ equation. Int. J. Numer. Methods Fluids 2004, 45, 509–525. [Google Scholar] [CrossRef]
- Stenger, F. Numerical Methods Based on Sinc and Analytic Functions; Springer: New York, NY, USA, 1993. [Google Scholar]
- Stenger, F. Handbook of Sinc Numerical Methods; CRC Press: Boca Raton, FL, USA, 2011. [Google Scholar]
- Liu, Y.; Chen, X.; Zhuo, W. Dividends under threshold dividend strategy with randomized observation periods and capital-exchange agreement. J. Comput. Appl. Math. 2020, 366, 112426. [Google Scholar] [CrossRef]
- Wang, C.; Deng, N.; Shen, S. Numerical method for a perturbed risk model with proportional investment. Mathematics 2023, 11, 43. [Google Scholar] [CrossRef]
- Lund, J.; Bowers, K.L. Sinc Methods for Quadrature and Differential Equations; SIAM: Philadelphia, PA, USA, 1992. [Google Scholar]
- Stenger, F. Summary of Sinc numerical methods. J. Comput. Appl. Math. 2000, 13, 379–420. [Google Scholar] [CrossRef]
- Zhi, H.; Pu, J. On a dual risk model perturbed by diffusion with dividend threshold. Chin. Ann. Math. Ser. B 2016, 37, 777–792. [Google Scholar] [CrossRef]
- Zhang, Z.; Yang, H.; Li, S. The perturbed compound Poisson risk model with two-sided jumps. J. Comput. Appl. Math. 2010, 233, 1773–1784. [Google Scholar] [CrossRef]
- Cheung, E.C. On a class of stochastic models with two-sided jumps. Queueing Syst. 2011, 69, 1–28. [Google Scholar] [CrossRef]
- Labbé, C.; Sendov, H.S.; Sendova, K.P. The Gerber–Shiu function and the generalized Cramér–Lundberg model. Appl. Math. Comput. 2011, 218, 3035–3056. [Google Scholar] [CrossRef]
- Dong, H.; Liu, Z. The ruin problem in a renewal risk model with two-sided jumps. Math. Comput. Model. 2013, 57, 800–811. [Google Scholar] [CrossRef]


| Literature | Risk Model | Sinc | Error Analysis | ||
|---|---|---|---|---|---|
| Two-Sided Jumps | Investment | Dividend | |||
| Dong et al. [27] | ✔ | ||||
| Cheung et al. [12] | ✔ | ||||
| Martín-González et al. [13] | ✔ | ||||
| Bo et al. [29] | ✔ | ✔ | |||
| Zhuo et al. [17] | ✔ | ✔ | |||
| Chen and Ou [25] | ✔ | ✔ | ✔ | ||
| Elghribi [19] | ✔ | ||||
| Palmowski and Vatamidou [30] | ✔ | ||||
| Zhang [16] | ✔ | ✔ | |||
| Chen et al. [20] | ✔ | ✔ | |||
| Zhang and Chen [21] | ✔ | ||||
| Chen and Bian [28] | ✔ | ✔ | |||
| Chen et al. [31] | ✔ | ✔ | |||
| Vierkötter and Schmidli [23] | ✔ | ||||
| Albrecher et al. [26] | ✔ | ||||
| Our work | ✔ | ✔ | ✔ | ✔ | ✔ |
| SA | 1.5781 | 1.5799 | 1.5815 | 1.5830 | 1.5844 | 1.5856 | 1.5869 |
| ES | 1.5842 | 1.5799 | 1.5755 | 1.5708 | 1.5659 | 1.5607 | 1.5553 |
| RE (%) | −0.38 | 0.00 | 0.38 | 0.78 | 1.12 | 1.60 | 2.03 |
| u | ||||||||
|---|---|---|---|---|---|---|---|---|
| 1.9361 | 2.0904 | 2.1049 | 2.0473 | 2.0275 | 1.8774 | 1.6303 | 1.3118 | |
| 1.0918 | 1.6053 | 1.7960 | 1.8300 | 1.8225 | 1.7152 | 1.4964 | 1.2038 | |
| 0.8657 | 1.4111 | 1.6660 | 1.7408 | 1.7391 | 1.6550 | 1.4576 | 1.1877 | |
| 0.8621 | 1.3516 | 1.6177 | 1.7042 | 1.7045 | 1.6314 | 1.4493 | 1.1968 | |
| 0.9173 | 1.3420 | 1.6015 | 1.6899 | 1.6908 | 1.6234 | 1.4516 | 1.2115 |
| u | ||||||||
|---|---|---|---|---|---|---|---|---|
| 1.1381 | 1.4167 | 1.5262 | 1.5219 | 1.5088 | 1.3768 | 1.1310 | 0.9422 | |
| 0.7524 | 1.2371 | 1.4502 | 1.5001 | 1.4940 | 1.3859 | 1.1565 | 0.9781 | |
| 0.6953 | 1.1879 | 1.4371 | 1.5102 | 1.5073 | 1.4114 | 1.1948 | 1.0256 | |
| 0.7558 | 1.2043 | 1.4562 | 1.5330 | 1.5306 | 1.4387 | 1.2313 | 1.0693 | |
| 0.8407 | 1.2395 | 1.4829 | 1.5572 | 1.5546 | 1.4641 | 1.2631 | 1.1065 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, J.; Wang, C.; Deng, N.; Wang, S. Numerical Method for a Risk Model with Two-Sided Jumps and Proportional Investment. Mathematics 2023, 11, 1584. https://doi.org/10.3390/math11071584
Xu J, Wang C, Deng N, Wang S. Numerical Method for a Risk Model with Two-Sided Jumps and Proportional Investment. Mathematics. 2023; 11(7):1584. https://doi.org/10.3390/math11071584
Chicago/Turabian StyleXu, Jiaen, Chunwei Wang, Naidan Deng, and Shujing Wang. 2023. "Numerical Method for a Risk Model with Two-Sided Jumps and Proportional Investment" Mathematics 11, no. 7: 1584. https://doi.org/10.3390/math11071584
APA StyleXu, J., Wang, C., Deng, N., & Wang, S. (2023). Numerical Method for a Risk Model with Two-Sided Jumps and Proportional Investment. Mathematics, 11(7), 1584. https://doi.org/10.3390/math11071584










