Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment
Abstract
:1. Introduction
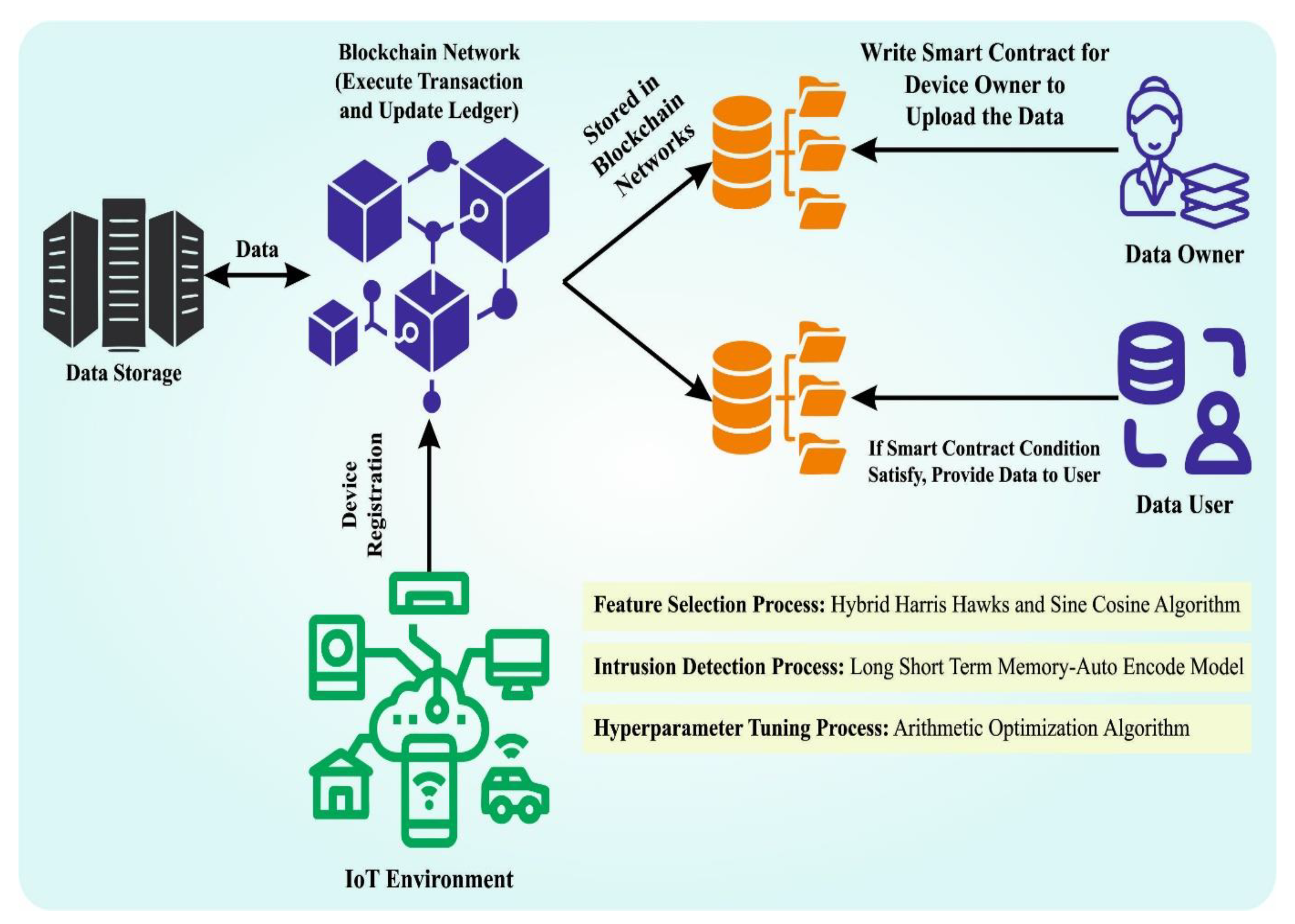
- A novel H3SC-DLIDS technique comprising H3SC-based feature selection, LSTM-AE-based classification and AOA-based hyperparameter tuning is presented in this study for DDoS attack detection in the IoT network. To the best of the researcher’s knowledge, no authors proposed this H3SC-DLIDS technique so far in the literature.
- A new H3SC technique has been developed by integrating the characteristics of the HHO algorithm and SCA for an optimal selection of the features.
- An AOA has been presented in this study with an LSTM-AE model for attack detection.
- Hyperparameter optimization of the LSTM-AE model using the AOA algorithm and cross-validation, helps in boosting the predictive outcome of the proposed model for unseen data.
2. Related Works
3. The Proposed Model
3.1. BC Technology
- Proof-of-importance (PoI): the node that can construct a block has the maximal amount of transactions.
- Proof-of-stake (PoS): the node with high wealth has a higher opportunity to contribute from the consensus, and constructs the block.
- Proof-of-work (PoW): a transaction can be approved once the node accepts its P2P network.
- Proof-of-authority (PoA): certain nodes are allowed to produce novel blocks and protect the BC. It is to be noted that the aforementioned process features potential benefits and probable disadvantages, too, primarily based on the basic network architecture.
3.2. Design of H3SC-Based Feature Selection
3.3. Optimal LSTM-AE-Based DDoS Attack Detection
4. Results and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Saveetha, D.; Maragatham, G. Design of Blockchain enabled intrusion detection model for detecting security attacks using deep learning. Pattern Recognit. Lett. 2022, 153, 24–28. [Google Scholar] [CrossRef]
- Hamouda, D.; Ferrag, M.A.; Benhamida, N.; Seridi, H. PPSS: A privacy-preserving secure framework using blockchain-enabled federated deep learning for Industrial IoTs. Pervasive Mob. Comput. 2022, 88, 101738. [Google Scholar] [CrossRef]
- Shah, H.; Shah, D.; Jadav, N.K.; Gupta, R.; Tanwar, S.; Alfarraj, O.; Tolba, A.; Raboaca, M.S.; Marina, V. Deep Learning-Based Malicious Smart Contract and Intrusion Detection System for IoT Environment. Mathematics 2023, 11, 418. [Google Scholar] [CrossRef]
- Wang, Z.; Jiang, D.; Lv, Z.; Song, H. A Deep Reinforcement Learning based Intrusion Detection Strategy for Smart Vehicular Networks. In Proceedings of the IEEE INFOCOM 2022-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Virtual, 2–5 May 2022; pp. 1–6. [Google Scholar]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Kumar, N.; Hassan, M.M. A privacy-preserving-based secure framework using blockchain-enabled deep-learning in the cooperative intelligent transport system. IEEE Trans. Intell. Transp. Syst. 2021, 23, 16492–16503. [Google Scholar] [CrossRef]
- Ragab, M.; Sabir, M.F.S. Outlier detection with optimal hybrid deep learning enabled intrusion detection system for ubiquitous and smart environment. Sustain. Energy Technol. Assess. 2022, 52, 102311. [Google Scholar] [CrossRef]
- Medhane, D.V.; Sangaiah, A.K.; Hossain, M.S.; Muhammad, G.; Wang, J. Blockchain-enabled distributed security framework for next-generation IoT: An edge cloud and software-defined network-integrated approach. IEEE Internet Things J. 2020, 7, 6143–6149. [Google Scholar] [CrossRef]
- Al-Shammari, N.K.; Syed, T.H.; Syed, M.B. An Edge–IoT framework and prototype based on blockchain for smart healthcare applications. Eng. Technol. Appl. Sci. Res. 2021, 11, 7326–7331. [Google Scholar] [CrossRef]
- Alghamdi, A.; Zhu, J.; Yin, G.; Shorfuzzaman, M.; Alsufyani, N.; Alyami, S.; Biswas, S. Blockchain Empowered Federated Learning Ecosystem for Securing Consumer IoT Features Analysis. Sensors 2022, 22, 6786. [Google Scholar] [CrossRef]
- Biswas, S.; Sharif, K.; Li, F.; Nour, B.; Wang, Y. A scalable blockchain framework for secure transactions in IoT. IEEE Internet Things J. 2018, 6, 4650–4659. [Google Scholar] [CrossRef]
- Heidari, A.; Navimipour, N.J.; Unal, M. A Secure Intrusion Detection Platform Using Blockchain and Radial Basis Function Neural Networks for Internet of Drones. IEEE Internet Things J. 2023; in press. [Google Scholar] [CrossRef]
- Sharma, B.; Sharma, L.; Lal, C.; Roy, S. Anomaly based network intrusion detection for IoT attacks using deep learning technique. Comput. Electr. Eng. 2023, 107, 108626. [Google Scholar] [CrossRef]
- Mansour, R.F. Artificial intelligence based optimization with deep learning model for blockchain enabled intrusion detection in CPS environment. Sci. Rep. 2022, 12, 12937. [Google Scholar] [CrossRef] [PubMed]
- Ashraf, E.; Areed, N.F.; Salem, H.; Abdelhay, E.H.; Farouk, A. Fidchain: Federated intrusion detection system for blockchain-enabled iot healthcare applications. Healthcare 2022, 10, 1110. [Google Scholar] [CrossRef]
- Sarhan, M.; Lo, W.W.; Layeghy, S.; Portmann, M. HBFL: A hierarchical blockchain-based federated learning framework for collaborative IoT intrusion detection. Comput. Electr. Eng. 2022, 103, 108379. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B.; Choo, K.K.R. A deep blockchain framework-enabled collaborative intrusion detection for protecting IoT and cloud networks. IEEE Internet Things J. 2020, 8, 9463–9472. [Google Scholar] [CrossRef]
- Nandy, S.; Adhikari, M.; Khan, M.A.; Menon, V.G.; Verma, S. An intrusion detection mechanism for secured IoMT framework based on swarm-neural network. IEEE J. Biomed. Health Inform. 2021, 26, 1969–1976. [Google Scholar] [CrossRef] [PubMed]
- Ragab, M.; Altalbe, A. A Blockchain-based architecture for enabling cybersecurity in the internet-of-critical infrastructures. CMC-Comput. Mater. Contin. 2022, 72, 1579–1592. [Google Scholar] [CrossRef]
- Abdulrab, H.Q.; Hussin, F.A.; Ismail, I.; Assaad, M.; Awang, A.; Shutari, H.; Devan, P.A.M. Hybrid Harris Hawks with Sine Cosine for Optimal Node Placement and Congestion Reduction in an Industrial Wireless Mesh Network. IEEE Access 2023, 11, 2500–2523. [Google Scholar] [CrossRef]
- Mafarja, M.; Thaher, T.; Al-Betar, M.A.; Too, J.; Awadallah, M.A.; Abu Doush, I.; Turabieh, H. Classification framework for faulty-software using enhanced exploratory whale optimizer-based feature selection scheme and random forest ensemble learning. Appl. Intell. 2023, 53, 1–43. [Google Scholar] [CrossRef]
- Spandonidis, C.; Theodoropoulos, P.; Giannopoulos, F. A Combined Semi-Supervised Deep Learning Method for Oil Leak Detection in Pipelines Using IIoT at the Edge. Sensors 2022, 22, 4105. [Google Scholar] [CrossRef]
- Elkasem, A.H.; Kamel, S.; Hassan, M.H.; Khamies, M.; Ahmed, E.M. An Eagle Strategy Arithmetic Optimization Algorithm for Frequency Stability Enhancement Considering High Renewable Power Penetration and Time-Varying Load. Mathematics 2022, 10, 854. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-iot dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Garg, S.; Hassan, M.M. A distributed intrusion detection system to detect DDoS attacks in blockchain-enabled IoT network. J. Parallel Distrib. Comput. 2022, 164, 55–68. [Google Scholar] [CrossRef]
- Liu, T.; Sabrina, F.; Jang-Jaccard, J.; Xu, W.; Wei, Y. Artificial Intelligence-Enabled DDoS Detection for Blockchain-Based Smart Transport Systems. Sensors 2022, 22, 32. [Google Scholar] [CrossRef] [PubMed]











| BoT-IoT Binary Dataset | |
|---|---|
| Class | No. of Instances |
| Attack | 1579 |
| Normal | 477 |
| Total Number of Samples | 2056 |
| BoT-IoT Multiclass Dataset | |
|---|---|
| Class | No. of Instances |
| DDoS | 500 |
| DoS | 500 |
| Recon | 500 |
| Theft | 79 |
| Normal | 477 |
| Total Number of Instances | 2056 |
| Class | |||||
|---|---|---|---|---|---|
| Attack | 98.48% | 98.73% | 98.48% | 98.60% | 97.14% |
| Normal | 95.81% | 95.01% | 95.81% | 95.41% | 97.14% |
| Average | 97.14% | 96.87% | 97.14% | 97.01% | 97.14% |
| Class | |||||
|---|---|---|---|---|---|
| DDoS | 98.98% | 97.80% | 98.00% | 97.90% | 98.65% |
| DoS | 99.12% | 97.82% | 98.60% | 98.21% | 98.95% |
| Recon | 98.88% | 97.42% | 98.00% | 97.71% | 98.58% |
| Theft | 99.17% | 91.89% | 86.08% | 88.89% | 92.89% |
| Normal | 99.08% | 98.31% | 97.69% | 98.00% | 98.59% |
| Average | 99.05% | 96.65% | 95.67% | 96.14% | 97.53% |
| Methods | ||||
|---|---|---|---|---|
| H3SC-DLIDS | 99.05% | 96.65% | 95.67% | 96.14% |
| AE-MLP Model | 98.19% | 95.91% | 93.31% | 95.13% |
| IDS-IoT Model | 97.40% | 95.80% | 94.90% | 95.53% |
| XGBoost Model | 97.09% | 94.28% | 92.13% | 95.05% |
| RF Model | 97.00% | 94.98% | 93.69% | 94.57% |
| DT Model | 95.21% | 92.43% | 92.51% | 93.26% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Katib, I.; Ragab, M. Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment. Mathematics 2023, 11, 1887. https://doi.org/10.3390/math11081887
Katib I, Ragab M. Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment. Mathematics. 2023; 11(8):1887. https://doi.org/10.3390/math11081887
Chicago/Turabian StyleKatib, Iyad, and Mahmoud Ragab. 2023. "Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment" Mathematics 11, no. 8: 1887. https://doi.org/10.3390/math11081887
APA StyleKatib, I., & Ragab, M. (2023). Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment. Mathematics, 11(8), 1887. https://doi.org/10.3390/math11081887








