Blockchain-Based Data Breach Detection: Approaches, Challenges, and Future Directions
Abstract
:1. Introduction
- To explore existing types of data breach attacks.
- To give a complete assessment of research on this topic.
- To categorize blockchain-based breach detection techniques based on attack types.
- To tabulate the most scientific developments from all related articles to provide a quick overview of the field’s progress.
2. Review Methodology
(“Blockchain” OR “Digital Ledger” OR “Distributed Ledger” OR “BLC”) AND (“Data Leak” OR “Data Breach” OR “Information Leak”) AND (“Detection” OR “Technique” OR “Mitigation” OR “Algorithm” OR “Mechanism”)
- What are the various forms of breaches that might occur? Identify the different types of data breaches documented in the literature.
- How is blockchain used to detect data breaches? What proposals and techniques did the researchers make to address the problems and obstacles they encountered?
- What challenges occur when blockchain technology is used to identify data breaches?
3. Comprehensive Review
4. Breach Scenarios Arising from Technical Failures
- Guardtime—KSI Blockchain: Guardtime’s Keyless Signature Infrastructure (KSI) [87] blockchain verifies the integrity of the data. Real-time data integrity and log-tampering protection are also guaranteed by KSI. Data breaches have been successfully detected by using it in the security and healthcare industries.
- IBM Food Trust: Blockchain technology is used by the food supply chain IBM Food Trust [88] to enable traceability. Blockchain technology has also proven to be useful in quickly detecting and identifying compromised food goods throughout the supply chain.
- Walmart’s Blockchain for Pharmaceutical Traceability: Walmart [89] uses blockchain technology to monitor the pharmaceutical supply chain. In order to guarantee the legitimacy and security of goods, the system also enhances traceability and assists in identifying breaches in the pharmaceutical supply chain.
5. Challenges and Recommendations for Future Directions
6. Conclusions and Future Work
- To obtain additional scalability and fewer transaction fees, check into Layer 2 solutions or alternative blockchain platforms.
- Examine blockchain networks’ privacy-preserving techniques by paying particular attention to how they handle sensitive personal data. Develop and examine techniques like homomorphic encryption and zero-knowledge proof to preserve privacy and safeguard breach detection procedures.
- Examine the potential and benefits of hybrid blockchain technologies in order to achieve a balance between efficiency and transparency. Adopt hybrid solutions to provide a safe and adaptable environment for identifying data breaches. These solutions combine the advantages of public and private blockchains.
- Conduct extensive testing in many real-world scenarios to fully validate the system. To simulate sophisticated insider attacks, conduct more complex penetration testing or stress testing for high transaction volumes.
- Collect feedback and views from prospective end users and other stakeholders, such as data protection authorities. When making system enhancements, consider user feedback to ensure that it meets practical requirements and is compliant.
- Study the possibility of incorporating blockchain-based detection of data breaches seamlessly into the existing security systems in a typical organization. Develop solutions that would allow easy integration and compatibility between diverse security frameworks for large-scale adoption and effectiveness.
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Samanta, M.; Pal, P.; Mukherjee, A. Prevention of information leakage by modulating the trust uncertainty in Ego-Network. In Proceedings of the 2017 9th International Conference on Communication Systems and Networks (COMSNETS), Bengaluru, India, 4–8 January 2017; IEEE: New York, NY, USA, 2017; pp. 377–378.
- Kumar, J.; Singh, A.K. Dynamic resource scaling in cloud using neural network and black hole algorithm. In Proceedings of the 2016 Fifth International Conference on Eco-friendly Computing and Communication Systems (ICECCS), Bhopal, India, 8–9 December 2016; IEEE: New York, NY, USA, 2016; pp. 63–67. [Google Scholar]
- Homoliak, I.; Toffalini, F.; Guarnizo, J.; Elovici, Y.; Ochoa, M. Insight into insiders and it: A survey of insider threat taxonomies, analysis, modeling, and countermeasures. ACM Comput. Surv. 2019, 52, 1–40. [Google Scholar] [CrossRef]
- Insiders, Cybersecurity. Crowd Research Partners. Insider Threat 2017. 2018. Available online: https://crowdresearchpartners.com/wp-content/uploads/2017/07/Insider-Threat-Report-2018.pdf (accessed on 15 December 2023).
- Ko, L.L.; Divakaran, D.M.; Liau, Y.S.; Thing, V.L. Insider threat detection and its future directions. Int. J. Secur. Netw. 2017, 12, 168–187. [Google Scholar] [CrossRef]
- Ghosh, A.; Dhar, P.; Banerjee, A.; Sanyal, M. A Survey of Data Leakage Detection in Cloud Computing Platform. Int. J. Sci. Res. Eng. Manag. 2023, 7, 1–6. [Google Scholar]
- Rauf, U.; Mohsen, F.; Wei, Z. A Taxonomic Classification of Insider Threats: Existing Techniques, Future Directions & Recommendations. J. Cyber Secur. Mobil. 2023, 12, 221–252. [Google Scholar]
- Ebadinezhad, S. A Systematic Literature Review on Information Security Leakage: Evaluating Security Threat. In Proceedings of the Third International Conference on Sustainable Expert Systems: ICSES, Lalitpur, Nepal, 9–10 September 2022; Springer Nature: Singapore, 2023; pp. 993–1007. [Google Scholar]
- Hu, T.; Xin, B.; Liu, X.; Chen, T.; Ding, K.; Zhang, X. Tracking the Insider Attacker: A Blockchain Traceability System for Insider Threats. Sensors 2020, 20, 5297. [Google Scholar] [CrossRef] [PubMed]
- Srivastava, S.; Mohit; Kumar, A.; Jha, S.K.; Dixit, P.; Prakash, S. Event-driven data alteration detection using block-chain. Secur. Priv. 2021, 4, e146. [Google Scholar] [CrossRef]
- Tukur, Y.M.; Thakker, D.; Awan, I.U. Ethereum blockchain-based solution to insider threats on perception layer of IoT systems. In Proceedings of the 2019 IEEE Global Conference on Internet of Things (GCIoT), Dubai, United Arab Emirates, 4–7 December 2019; IEEE: New York, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Sahai, S.; Atre, M.; Sharma, S.; Gupta, R.; Shukla, S.K. Verity: Blockchain based framework to detect insider attacks in dbms. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; IEEE: New York, NY, USA, 2020; pp. 26–35. [Google Scholar]
- Tukur, Y.M.; Thakker, D.; Awan, I. Edge-based blockchain enabled anomaly detection for insider attack prevention in Internet of Things. Trans. Emerg. Telecommun. Technol. 2020, 32, e4158. [Google Scholar] [CrossRef]
- Gu, J.; Sun, B.; Du, X.; Wang, J.; Zhuang, Y.; Wang, Z. Consortium blockchain-based malware detection in mobile devices. IEEE Access 2018, 6, 12118–12128. [Google Scholar] [CrossRef]
- Delgado-Mohatar, O.; Sierra-Cámara, J.M.; Anguiano, E. Blockchain-based semi-autonomous ransomware. Future Gener. Comput. Syst. 2020, 112, 589–603. [Google Scholar] [CrossRef]
- Pletinckx, S.; Trap, C.; Doerr, C. Malware coordination using the blockchain: An analysis of the cerber ransomware. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; IEEE: New York, NY, USA, 2018; pp. 1–9. [Google Scholar]
- Kumar, R.; Wang, W.; Kumar, J.; Zakira; Yang, T.; Ali, W. Collective intelligence: Decentralized learning for Android malware detection in IoT with blockchain. arXiv 2021, arXiv:2102.13376. [Google Scholar]
- Raje, S.; Vaderia, S.; Wilson, N.; Panigrahi, R. Decentralised firewall for malware detection. In Proceedings of the 2017 International Conference on Advances in Computing, Communication and Control (ICAC3), Mumbai, India, 1–2 December 2017; IEEE: New York, NY, USA, 2017; pp. 1–5. [Google Scholar]
- Hu, J.-W.; Yeh, L.-Y.; Liao, S.-W.; Yang, C.-S. Autonomous and malware-proof blockchain-based firmware update platform with efficient batch verification for Internet of Things devices. Comput. Secur. 2019, 86, 238–252. [Google Scholar] [CrossRef]
- Fuji, R.; Usuzaki, S.; Aburada, K.; Yamaba, H.; Katayama, T.; Park, M.; Shiratori, N.; Okazaki, N. Investigation on sharing signatures of suspected malware files using blockchain technology. In Proceedings of the International Multi-Conference of Engineers and Computer Scientists (IMECS), Hong Kong, 13–15 March 2019; pp. 94–99. [Google Scholar]
- Rana, S.; Gudla, C.; Sung, A.H. Evaluating machine learning models on the Ethereum blockchain for Android malware detection. In Intelligent Computing; Proceedings of the Computing Conference; Springer: Cham, Switzerland, 2019; pp. 446–461. [Google Scholar]
- Homayoun, S.; Dehghantanha, A.; Parizi, R.M.; Choo, K.-K.R. A blockchain-based framework for detecting malicious mobile applications in app stores. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; IEEE: New York, NY, USA, 2019; pp. 1–4. [Google Scholar]
- Yuan, Q.; Huang, B.; Zhang, J.; Wu, J.; Zhang, H.; Zhang, X. Detecting phishing scams on ethereum based on transaction records. In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020; IEEE: New York, NY, USA, 2020; pp. 1–5. [Google Scholar]
- Chen, W.; Guo, X.; Chen, Z.; Zheng, Z.; Lu, Y. Phishing Scam Detection on Ethereum: Towards Financial Security for Blockchain Ecosystem. In Proceedings of the Twenty-Ninth International Joint Conference on Artificial Intelligence (IJCAI-20), Yokohama, Japan, 11–17 July 2020; pp. 4506–4512. [Google Scholar]
- Liu, D.; Wang, W.; Wang, Y.; Tan, Y. Phishledger: A decentralized phishing data sharing mechanism. In Proceedings of the 2019 International Electronics Communication Conference, Okinawa, Japan, 7–9 July 2019; pp. 84–89. [Google Scholar]
- Edirimannage, S.; Nabeel, M.; Elvitigala, C.; Keppitiyagama, C. PhishChain: A Decentralized and Transparent System to Blacklist Phishing URLs. arXiv 2022, arXiv:2202.07882. [Google Scholar]
- Yuan, Z.; Yuan, Q.; Wu, J. Phishing detection on Ethereum via learning representation of transaction subgraphs. In Blockchain and Trustworthy Systems. BlockSys 2020. Communications in Computer and Information Science; Springer: Singapore, 2020; pp. 178–191. [Google Scholar]
- Qaisar, S.; Basit, A. DDoS botnet prevention using blockchain in software defined internet of things. In Proceedings of the 2019 16th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 8–12 January 2019; IEEE: New York, NY, USA, 2019; pp. 624–628. [Google Scholar]
- Singh, R.; Tanwar, S.; Sharma, T.P. Utilization of blockchain for mitigating the distributed denial of service attacks. Secur. Priv. 2020, 3, e96. [Google Scholar] [CrossRef]
- Javaid, U.; Siang, A.K.; Aman, M.N.; Sikdar, B. Mitigating loT device-based DDoS attacks using blockchain. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 71–76. [Google Scholar]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Trans. Emerg. Telecommun. Technol. 2020, 32, e4112. [Google Scholar] [CrossRef]
- Rodrigues, B.; Bocek, T.; Hausheer, D.; Lareida, A.; Sina, R.; Burkhard, S. Blockchain-Based Architecture for Collaborative DDoS Mitigation Using Smart Contracts; Springer: Berlin/Heidelberg, Germany, 2017; pp. 1–4. [Google Scholar]
- Spathoulas, G.; Giachoudis, N.; Damiris, G.-P.; Theodoridis, G. Collaborative blockchain-based detection of distributed denial of service attacks based on internet of things botnets. Future Internet 2019, 11, 226. [Google Scholar] [CrossRef]
- Chen, M.; Tang, X.; Cheng, J.; Xiong, N.; Li, J.; Fan, D. A DDoS attack defense method based on blockchain for IoTs devices. In Artificial Intelligence and Security. ICAIS 2020. Communications in Computer and Information Science; Springer: Singapore, 2020; pp. 685–694. [Google Scholar]
- Silowash, G.J.; Spooner, D.L.; Costa, D.L.; Albrethsen, M.J. Low-Cost Technical Solutions to Jump Start an Insider Threat Program; Carnegie-Mellon University: Pittsburgh, PA, USA, 2016. [Google Scholar]
- Al-Mhiqani, M.N.; Ahmad, R.; Abidin, Z.Z.; Abdulkareem, K.H.; Mohammed, M.A.; Gupta, D.; Shankar, K. A new intelligent multilayer framework for insider threat detection. Comput. Electr. Eng. 2021, 97, 107597. [Google Scholar] [CrossRef]
- Hong, W.; Yin, J.; You, M.; Wang, H.; Cao, J.; Li, J.; Liu, M. Graph intelligence enhanced bi-channel insider threat detection. In Proceedings of the International Conference on Network and System Security, Denarau Island, Fiji, 9–12 December 2022; Springer Nature: Cham, Switzerland, 2022; pp. 86–102. [Google Scholar]
- Haq, M.A.; Khan, M.A.R.; Alshehri, M. Insider Threat Detection Based on NLP Word Embedding and Machine Learning. Intell. Autom. Soft Comput. 2022, 33, 619–635. [Google Scholar]
- Lee, J.; Alghamdi, A.; Zaidi, A.K. Creating a digital twin of an insider threat detection enterprise using model-based systems engineering. In Proceedings of the 2022 IEEE International Systems Conference (SysCon), virtual conference, 25–28 April 2022; IEEE: New York, NY, USA; pp. 1–7. [Google Scholar]
- Georgiadou, A.; Mouzakitis, S.; Askounis, D. Detecting Insider Threat via a Cyber-Security Culture Framework. J. Comput. Inf. Syst. 2021, 62, 706–716. [Google Scholar] [CrossRef]
- Ye, X.; Han, M.-M. An improved feature extraction algorithm for insider threat using hidden Markov model on user behavior detection. Inf. Comput. Secur. 2020, 30, 19–36. [Google Scholar] [CrossRef]
- Al-Harrasi, A.; Shaikh, A.K.; Al-Badi, A. Towards protecting organisations’ data by preventing data theft by malicious insiders. Int. J. Organ. Anal. 2021, 31, 875–888. [Google Scholar] [CrossRef]
- Pal, P.; Chattopadhyay, P.; Swarnkar, M. Temporal feature aggregation with attention for insider threat detection from activity logs. Expert Syst. Appl. 2023, 224, 119925. [Google Scholar] [CrossRef]
- AlSlaiman, M.; Salman, M.I.; Saleh, M.M.; Wang, B. Enhancing false negative and positive rates for efficient insider threat detection. Comput. Secur. 2023, 126, 103066. [Google Scholar] [CrossRef]
- Li, X.; Li, X.; Jia, J.; Li, L.; Yuan, J.; Gao, Y.; Yu, S. A High Accuracy and Adaptive Anomaly Detection Model with Dual-Domain Graph Convolutional Network for Insider Threat Detection. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1638–1652. [Google Scholar] [CrossRef]
- Singh, M.; Mehtre, B.M.; Sangeetha, S.; Govindaraju, V. User Behaviour based Insider Threat Detection using a Hybrid Learning Approach. J. Ambient Intell. Humaniz. Comput. 2023, 14, 4573–4593. [Google Scholar] [CrossRef]
- Al-Shehari, T.; Alsowail, R.A. Random resampling algorithms for addressing the imbalanced dataset classes in insider threat detection. Int. J. Inf. Secur. 2022, 22, 611–629. [Google Scholar] [CrossRef]
- Randive, K.; Mohan, R.; Sivakrishna, A.M. An efficient pattern-based approach for insider threat classification using the image-based feature representation. J. Inf. Secur. Appl. 2023, 73, 103434. [Google Scholar] [CrossRef]
- Sivakrishna, A.M.; Mohan, R.; Randive, K. AUBIT: An Adaptive User Behaviour Based Insider Threat Detection Technique Using LSTM-Autoencoder. In Recent Trends in Computational Intelligence and Its Application: Proceedings of the 1st International Conference on Recent Trends in Information Technology and its Application (ICRTITA, 22); CRC Press: Boca Raton, FL, USA, 2023; p. 267. [Google Scholar]
- Zhu, D.; Sun, H.; Li, N.; Mi, B.; Huang, X. SPYRAPTOR: A Stream-based Smart Query System for Real-Time Threat Hunting within Enterprise. In Proceedings of the 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Rio de Janeiro, Brazil, 24–26 May 2023; IEEE: New York, NY, USA, 2023; pp. 1055–1062. [Google Scholar]
- Wen, T.; Xiao, Y.; Wang, A.; Wang, H. A novel hybrid feature fusion model for detecting phishing scam on Ethereum using deep neural network. Expert Syst. Appl. 2023, 211, 118463. [Google Scholar] [CrossRef]
- Wang, L.; Xu, M.; Cheng, H. Phishing scams detection via temporal graph attention network in Ethereum. Inf. Process. Manag. 2023, 60, 103412. [Google Scholar] [CrossRef]
- Xiong, A.; Tong, Y.; Jiang, C.; Guo, S.; Shao, S.; Huang, J.; Wang, W.; Qi, B. Ethereum phishing detection based on graph neural networks. IET Blockchain, 2023; early view. [Google Scholar]
- Pitre, V.; Joshi, A.; Das, S. Blockchain and Machine Learning Based Approach to Prevent Phishing Attacks. In Proceedings of the 2023 3rd Asian Conference on Innovation in Technology (ASIANCON), Ravet, India, 25–27 August 2023; IEEE: New York, NY, USA, 2023; pp. 1–6. [Google Scholar]
- Kim, J.; Lee, S.; Kim, Y.; Ahn, S.; Cho, S. Graph Learning-Based Blockchain Phishing Account Detection with a Heterogeneous Transaction Graph. Sensors 2023, 23, 463. [Google Scholar] [CrossRef]
- Sharma, A.; Rani, S.; Shah, S.H.; Sharma, R.; Yu, F.; Hassan, M.M. An Efficient Hybrid Deep Learning Model for Denial of Service Detection in Cyber Physical Systems. IEEE Trans. Netw. Sci. Eng. 2023, 10, 2419–2428. [Google Scholar] [CrossRef]
- Quincozes, S.E.; Kazienko, J.F.; Quincozes, V.E. An extended evaluation on machine learning techniques for Denial-of-Service detection in Wireless Sensor Networks. Internet Things 2023, 22, 100684. [Google Scholar] [CrossRef]
- Samaan, S.S.; Jeiad, H.A. Feature-based real-time distributed denial of service detection in SDN using machine learning and Spark. Bull. Electr. Eng. Inform. 2023, 12, 2302–2312. [Google Scholar] [CrossRef]
- Yaseen, H.S.; Al-Saadi, A. Q-learning based distributed denial of service detection. Int. J. Electr. Comput. Eng. 2023, 13, 972. [Google Scholar] [CrossRef]
- Seyam, A.; Nassif, A.B.; Nasir, Q.; AlShabi, M.A. Denial of service detection on industrial control system using BLSTM. In Artificial Intelligence and Machine Learning for Multi-Domain Operations Applications V; SPIE: Bellingham, WA, USA, 2023; Volume 12538, pp. 525–532. [Google Scholar]
- Aldhyani, T.H.H.; Alkahtani, H. Cyber Security for Detecting Distributed Denial of Service Attacks in Agriculture 4.0: Deep Learning Model. Mathematics 2023, 11, 233. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V. A novel deep learning-based approach for malware detection. Eng. Appl. Artif. Intell. 2023, 122, 106030. [Google Scholar] [CrossRef]
- Alomari, E.S.; Nuiaa, R.R.; Alyasseri, Z.A.A.; Mohammed, H.J.; Sani, N.S.; Esa, M.I.; Musawi, B.A. Malware Detection Using Deep Learning and Correlation-Based Feature Selection. Symmetry 2023, 15, 123. [Google Scholar] [CrossRef]
- De Oliveira, A.S.; Sassi, R.J. Behavioral malware detection using deep graph convolutional neural networks. TechRxiv 2023. [Google Scholar] [CrossRef]
- Zhu, H.-J.; Gu, W.; Wang, L.-M.; Xu, Z.-C.; Sheng, V.S. Android malware detection based on multi-head squeeze-and-excitation residual network. Expert Syst. Appl. 2023, 212, 118705. [Google Scholar] [CrossRef]
- Al-Andoli, M.N.; Sim, K.S.; Tan, S.C.; Goh, P.Y.; Lim, C.P. An Ensemble-Based Parallel Deep Learning Classifier with PSO-BP Optimization for Malware Detection. IEEE Access 2023, 11, 76330–76346. [Google Scholar] [CrossRef]
- Fascí, L.S.; Fisichella, M.; Lax, G.; Qian, C. Disarming visualization-based approaches in malware detection systems. Comput. Secur. 2023, 126, 103062. [Google Scholar] [CrossRef]
- Bhat, P.; Behal, S.; Dutta, K. A system call-based android malware detection approach with homogeneous & heterogeneous ensemble machine learning. Comput. Secur. 2023, 130, 103277. [Google Scholar]
- Zhu, H.; Wei, H.; Wang, L.; Xu, Z.; Sheng, V.S. An effective end-to-end android malware detection method. Expert Syst. Appl. 2023, 218, 119593. [Google Scholar] [CrossRef]
- Herrera-Silva, J.A.; Hernández-Álvarez, M. Dynamic Feature Dataset for Ransomware Detection Using Machine Learning Algorithms. Sensors 2023, 23, 1053. [Google Scholar] [CrossRef] [PubMed]
- Liu, C.; Lu, J.; Feng, W.; Du, E.; Di, L.; Song, Z. MOBIPCR: Efficient, accurate, and strict ML-based mobile malware detection. Future Gener. Comput. Syst. 2023, 144, 140–150. [Google Scholar] [CrossRef]
- Singh, J.; Sharma, K.; Wazid, M.; Das, A.K. SINN-RD: Spline interpolation-envisioned neural network-based ransomware detection scheme. Comput. Electr. Eng. 2023, 106, 108601. [Google Scholar] [CrossRef]
- Wu, Y.; Li, M.; Zeng, Q.; Yang, T.; Wang, J.; Fang, Z.; Cheng, L. DroidRL: Feature selection for android malware detection with reinforcement learning. Comput. Secur. 2023, 128, 103126. [Google Scholar] [CrossRef]
- Wu, Y.; Shi, J.; Wang, P.; Zeng, D.; Sun, C. DeepCatra: Learning flow-and graph-based behaviours for Android malware detection. IET Inf. Secur. 2022, 17, 118–130. [Google Scholar] [CrossRef]
- Sharma, A.; Kaur, P. Tamper-proof multitenant data storage using blockchain. Peer-to-Peer Netw. Appl. 2022, 16, 431–449. [Google Scholar] [CrossRef]
- Kang, Y.; Li, Q.; Liu, Y. Trusted Data Analysis and Consensus Mechanism of Product Traceability Based on Blockchain. Comput. Intell. Neurosci. 2022, 2022, 3035231. [Google Scholar] [CrossRef]
- Azbeg, K.; Ouchetto, O.; Andaloussi, S.J. Access Control and Privacy-Preserving Blockchain-Based System for Diseases Management. IEEE Trans. Comput. Soc. Syst. 2022, 10, 1515–1527. [Google Scholar] [CrossRef]
- Pelekoudas-Oikonomou, F.; Zachos, G.; Papaioannou, M.; de Ree, M.; Ribeiro, J.C.; Mantas, G.; Rodriguez, J. Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems. Sensors 2022, 22, 2449. [Google Scholar] [CrossRef] [PubMed]
- Chatziamanetoglou, D.; Rantos, K. Blockchain-Based Cyber Threat Intelligence Sharing Using Proof-of-Quality Consensus. Secur. Commun. Networks 2023, 2023, 3303122. [Google Scholar] [CrossRef]
- Parlak, M. Blockchain-based Immutable Evidence and Decentralized Loss Adjustment for Autonomous Vehicle Accidents in Insurance. arXiv 2023, arXiv:2303.18130. [Google Scholar]
- Azbeg, K.; Ouchetto, O.; Andaloussi, S.J. BlockMedCare: A healthcare system based on IoT, Blockchain and IPFS for data management security. Egypt. Inform. J. 2022, 23, 329–343. [Google Scholar] [CrossRef]
- Asif, M.; Aziz, Z.; Bin Ahmad, M.; Khalid, A.; Waris, H.A.; Gilani, A. Blockchain-based authentication and trust management mechanism for smart cities. Sensors 2022, 22, 2604. [Google Scholar] [CrossRef]
- Namane, S.; Ben Dhaou, I. Blockchain-Based Access Control Techniques for IoT Applications. Electronics 2022, 11, 2225. [Google Scholar] [CrossRef]
- Aslam, T.; Maqbool, A.; Akhtar, M.; Mirza, A.; Khan, M.A.; Khan, W.Z.; Alam, S. Blockchain Based Enhanced ERP Transaction Integrity Architecture and PoET Consensus. Comput. Mater. Contin. 2022, 70, 1089–1109. [Google Scholar] [CrossRef]
- Yu, D.; Xu, H.; Zhang, L.; Cao, B.; Imran, M.A. Security analysis of sharding in the blockchain system. In Proceedings of the 2021 IEEE 32nd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Virtual Conference, 13–16 September 2021; IEEE: New York, NY, USA; pp. 1030–1035. [Google Scholar]
- Zhang, L.; Xu, H.; Onireti, O.; Imran, M.A.; Cao, B. How Much Communication Resource is Needed to Run a Wireless Blockchain Network? IEEE Netw. 2021, 36, 128–135. [Google Scholar] [CrossRef]
- Mylrea, M.E.; Gourisetti, S.N.G.; Tatireddy, V.; Kaur, K.J.; Allwardt, C.H.; Singh, R.; Plummer, J.; Bishop, R.; Hahn, A.L. Keyless Infrastructure Security Solution (KISS): VOLTTRON™ KSI® Blockchain Design and Specification; No. PNNL-28310; Pacific Northwest National Lab. (PNNL): Richland, WA, USA, 2018.
- Nguyen, H.; Do, L. The Adoption of Blockchain in Food Retail Supply Chain: Case: IBM Food Trust Blockchain and the Food Retail Supply Chain in Malta. 2018. Available online: https://www.theseus.fi/handle/10024/158615 (accessed on 15 December 2023).
- Pham, H. The Impact of Blockchain Technology on the Improvement of Food Supply Chain Management: Transparency and Traceability: A Case Study of Walmart and Atria. Available online: https://www.theseus.fi/handle/10024/157299 (accessed on 15 December 2023).

| Features | [6] | [7] | [8] | This Survey |
|---|---|---|---|---|
| Consensus protocols for data breaches are presented. | X | X | X | ✓ |
| Enabling technologies were discussed in order to offer defenses against various aspects of the problem of data leaking. | ✓ | X | X | ✓ |
| Explores the application of blockchain in the domain of data breaches and how it might be improved. | X | X | ✓ | ✓ |
| Identifies potential future directions for creating more reliable leakage prevention systems that can improve on some of the shortcomings of the present ones. | X | ✓ | X | ✓ |
| Provides a more comprehensive and recent analysis of how the blockchain is being used to address data breach issues. | X | X | X | ✓ |
| The advantages and drawbacks of blockchain technology for detecting data breaches. | X | X | X | ✓ |
| Provides bibliographic information used in the review. | X | X | ✓ | ✓ |
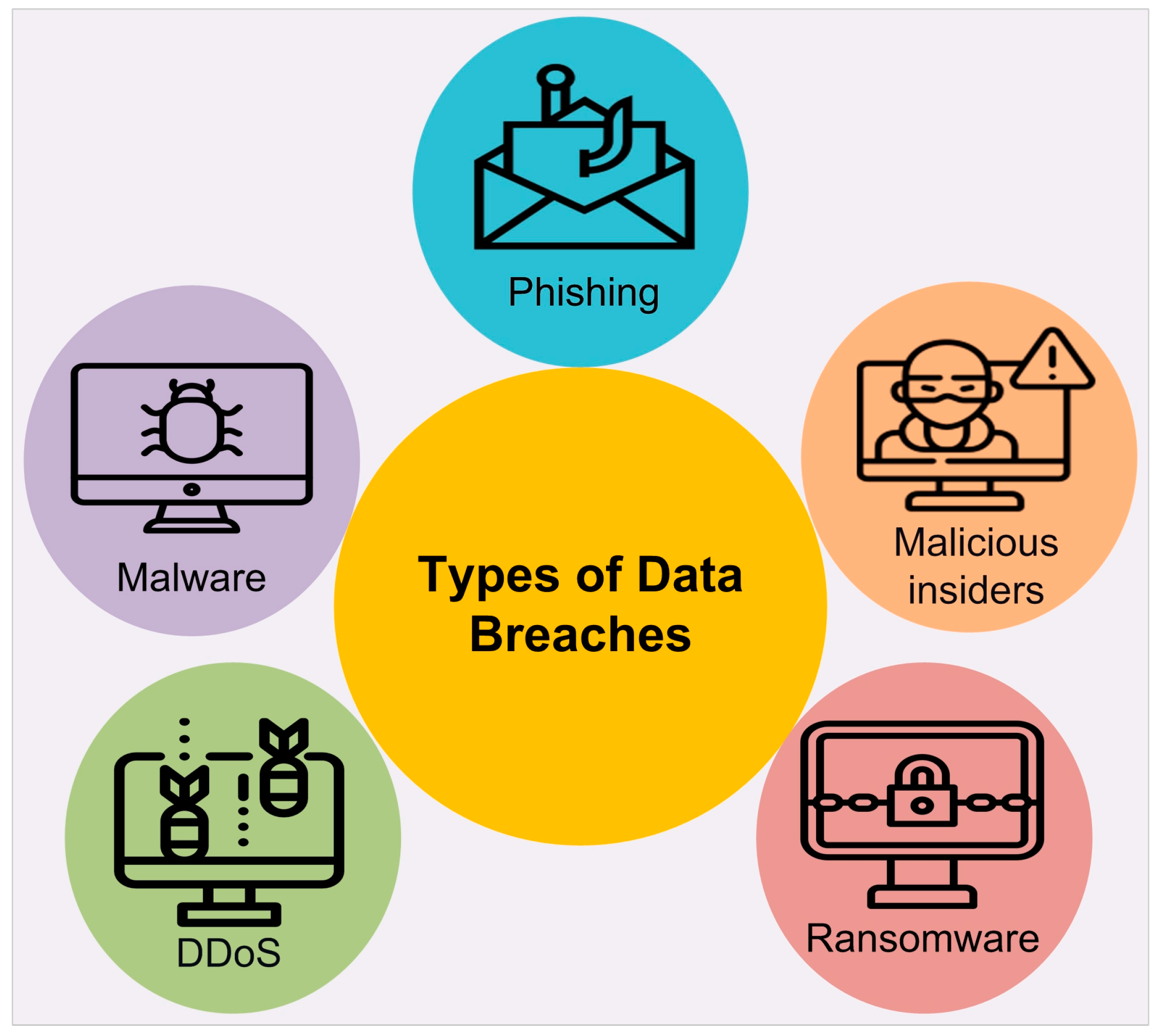
| A taxonomy of current data breach types is presented. | ✓ | ✓ | ✓ | ✓ |
| Highlights current and future issues and genuine concerns in the data breach field. | X | ✓ | X | ✓ |
| Compares existing blockchain-based data breach detection solutions based on type, platform, smart contracts, and consensus algorithm. | X | X | X | ✓ |
| Inclusion Criteria | Exclusion Criteria |
|---|---|
| The paper must be related to data breaches and blockchain in some way. | Articles that are written in a language other than English. |
| Publications in the field of information leakage breaches or data breaches. | Duplicate articles that replicate research that has already been published. |
| Papers that emphasize how blockchain was utilized to prevent data breaches. | Papers that emphasize non-blockchain-based techniques to prevent data breaches. |
| Papers that focus on how blockchain may be used to address important challenges of breach detection. | Articles in which a survey or review is presented. |
| From 2017 to 2023, all research on this topic was covered. | Articles that are not part of the broader data breach and blockchain domain. |
| Ref. | Blockchain Platform | Consensus Algorithm | Breach Type | Smart Contract | Domain | Implementation | GDPR | Language/Tool Used | Evaluation Metrics |
|---|---|---|---|---|---|---|---|---|---|
| [9] | Not specified | Delegated proof of stake | Insider threat | No | Not specified | Yes | No | Not specified | Response time with respect to node number and test time |
| [10] | Not specified | Not specified | Insider threat | No | Not specified | Yes | No | Not specified | Not specified |
| [11] | Ethereum | Proof of work | Insider threat | Yes | IoT | Yes | No | Marvin v.19.9, LoRaWAN v.1.0.4 | Time |
| [12] | Hyperledger Fabric | Not specified | Insider threat | No | Education | Yes | No | Python v.3.8, Hyperledger Fabric v1.4, SQLite v3.11.0 | CRUD query runtime |
| [13] | Ethereum | Proof of stake | Insider threat | Yes | IoT | Yes | No | Arduino IDE v.1.8, LoRaWAN, Marvin device | Time with respect to temperature |
| [14] | Not specified | Not specified | Malware | No | Mobile devices | Yes | No | FlowDroid v.2.7 | Time, cost, accuracy, and recall rate |
| [15] | Ethereum | Proof of work | Ransomware | Yes | Not specified | Yes | No | Not specified | Storage and execution costs |
| [16] | Not specified | Not specified | Ransomware | No | Cerber | Yes | No | Not specified | Average time to mitigation |
| [17] | Ethereum | Delegated proof of stake | Malware | Yes | IoT | Yes | Yes | Solidity v.0.5.0 | TPR, FPR, Accuracy, and running time |
| [18] | Ethereum | Proof of work | Malware | Yes | Cybersecurity | Yes | No | Not specified | Accuracy, TPR |
| [19] | Ethereum | Proof of stake | Malware | Yes | IoT | Yes | No | Node.js, Web3 library, solidity v.0.5.0 | Number of requests per second |
| [20] | Ethereum | Proof of work | Malware | Yes | Not specified | Yes | No | Geth v1.13.1 and Python v.3.8 | False-negative rate and false-positive rate |
| [21] | Ethereum | Proof of stake | Malware | Yes | Android | Yes | No | Not specified | Accuracy, precision, recall, and f-measure |
| [22] | Not specified | Not specified | Malware | No | Mobile app store | No | No | Not specified | Not specified |
| [23] | Ethereum | Proof of stake | Phishing | No | Not specified | Yes | No | Not specified | Precision, recall, and F-score |
| [24] | Ethereum | Proof of stake | Phishing | Yes | Not specified | Yes | No | Not specified | Precision, recall, F1, and AUC |
| [25] | Hyperledger Fabric | Dpos and BFT | Phishing | No | Alibaba, PayPal, Chase, and Facebook | Yes | No | Hyperledger Fabric 1.1 | Performance throughput |
| [26] | Quorum | Byzantine Fault Tolerance | Phishing | Yes | URLs and crowdsourcing | Yes | No | Solidity v.0.5.0 | Ac, pre, rec |
| [27] | Ethereum | Proof of stake | Phishing | No | Not specified | Yes | No | Not specified | Precision, recall, and f-measure |
| [28] | Hyperledger | Not specified | DDoS | No | IoT | Yes | No | Python v.3.8, Stacheldraht v.1.666 | Not specified |
| [29] | Ethereum | Proof of stake | DDoS | Yes | IoT | No, only proof of concept | No | Ethereum Go client nodes v1.13.6, solidity v.0.5.0 | Not specified |
| [30] | Ethereum | Proof of stake | DDoS | Yes | IoT | No, only proof of concept | No | Ethereum Go client v1.13.6 (geth) | Not specified |
| [31] | Ethereum | Proof of stake | DDoS | Yes | IoT/Fog Computing | Yes | No | Python v.3.8 | Accuracy, detection rate, and false alarm |
| [32] | Ethereum | Proof of stake | DDoS | Yes | Not specified | Yes | No | Ethereum Virtual Machine v1.13.8, solidity v.0.5.0 | Gas cost |
| [33] | Ethereum | Not specified | DDoS | Yes | IoT | Yes | No | Not specified | Number of packets with respect to time |
| [34] | Not specified | Not specified | DDoS | Yes | IoT | No | No | Not specified | Not specified |
| Features | References | Employed | Domain |
|---|---|---|---|
| Distributed and tamper-proof ledger | Sharma et al. [75] | For transparent data storage system | Multitenant data storage |
| Authentication process | Kang et al. [76] | For controlling and monitoring data access | Product traceability |
| Smart contracts for access control | Azbeg et al. [77] | To enforce access control policies | Disease management |
| Monitoring and alerting mechanisms | Pelekoudas et al. [78] | For real-time monitoring and alerting | Healthcare monitoring system |
| Decentralized threat intelligence sharing | Chatziamanetoglou et al. [79] | To securely share information | Cyber threat intelligence |
| Immutable forensic records | Parlak et al. [80] | To create immutable forensic records | Vehicle accidents in insurance |
| Reference | Components/Aspects | Blockchain Replaces |
|---|---|---|
| Azbeg et al. [81] | Data Storage Level | Centralized databases with distributed ledgers, ensuring redundancy. It augments storage with cryptographic hashing, ensuring security. |
| Asif et al. [82] | Authentication Process | Traditional authentication with decentralized identity management, enhancing security through cryptographic techniques and user-controlled cryptographic keys. |
| Namane et al. [83] | Access Control | Centralized access control with smart contracts for decentralized and automated authorization, augmenting access control with transparent access logs. |
| Pelekoudas et al. [78] | Monitoring and Alerting Mechanisms | Centralized monitoring with decentralized mechanisms for real-time visibility and augments it with tamper-proof audit trails for enhanced breach detection. |
| Aslam et al. [84] | Transaction Verification and Consensus | Centralized transaction verification with decentralized consensus, reducing fraud risk. Augmentation enhances verification integrity for robust data breach detection. |
| Challenge | Problem |
|---|---|
| Public blockchain networks have scalability issues when they handle a large number of transactions in parallel. | When handling data breach detection situations, the network might get congested, resulting in slower transaction processing times and increased costs. |
| Reaching agreement in blockchain networks is a time-consuming process, and, therefore, the speed of transaction is affected. | Responses must be timely in data breach detection. As a result, slow transaction processing can hamper timely detection and response. |
| Blockchain technology may not fit into legacy systems. | For organizations with existing infrastructure, integration of blockchain into the data breach detection systems can be hard and may require a lot of modification. |
| For instance, many common blockchain consensus mechanisms use PoW, which is quite costly in terms of energy. | Environmental concerns and high operational costs are due to the high energy consumption. |
| The development of blockchain technology may be much faster than regulatory frameworks. | Regulation adherence is necessary for data breach detection systems, and noncompliance with current laws may serve as grounds for legal action. |
| Interoperability of different blockchain platforms. | Detecting data breaches requires smooth communication between different systems. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ansar, K.; Ahmed, M.; Helfert, M.; Kim, J. Blockchain-Based Data Breach Detection: Approaches, Challenges, and Future Directions. Mathematics 2024, 12, 107. https://doi.org/10.3390/math12010107
Ansar K, Ahmed M, Helfert M, Kim J. Blockchain-Based Data Breach Detection: Approaches, Challenges, and Future Directions. Mathematics. 2024; 12(1):107. https://doi.org/10.3390/math12010107
Chicago/Turabian StyleAnsar, Kainat, Mansoor Ahmed, Markus Helfert, and Jungsuk Kim. 2024. "Blockchain-Based Data Breach Detection: Approaches, Challenges, and Future Directions" Mathematics 12, no. 1: 107. https://doi.org/10.3390/math12010107





