A Matrix Coding-Oriented Reversible Data Hiding Scheme Using Dual Digital Images
Abstract
:1. Introduction
- The embedding capacity is significantly larger, which can be up to 786,432 bits.
- It is a suitable solution for applications requiring high embedding capacity but that can scarify the image quality to be visually acceptable.
- Both the process of embedding and the process of extraction are simple and have a satisfiable execution time. The shadow construction phase took 0.5242 s, while the secret message extraction and the image reconstruction phase took 0.9158 s.
2. Related Work
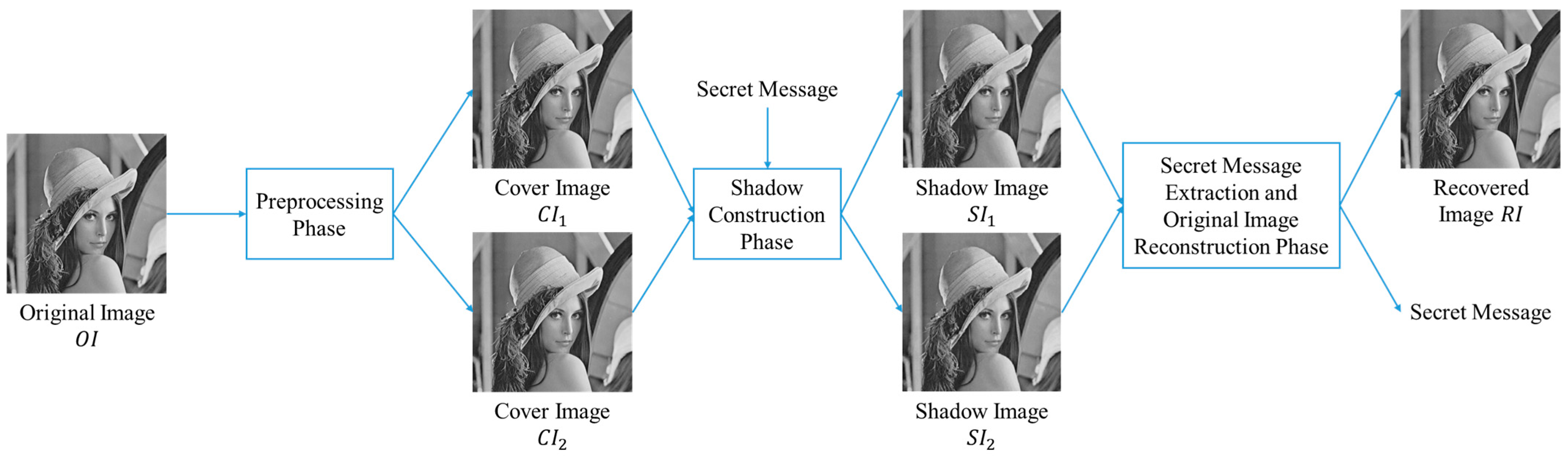
3. Proposed Scheme
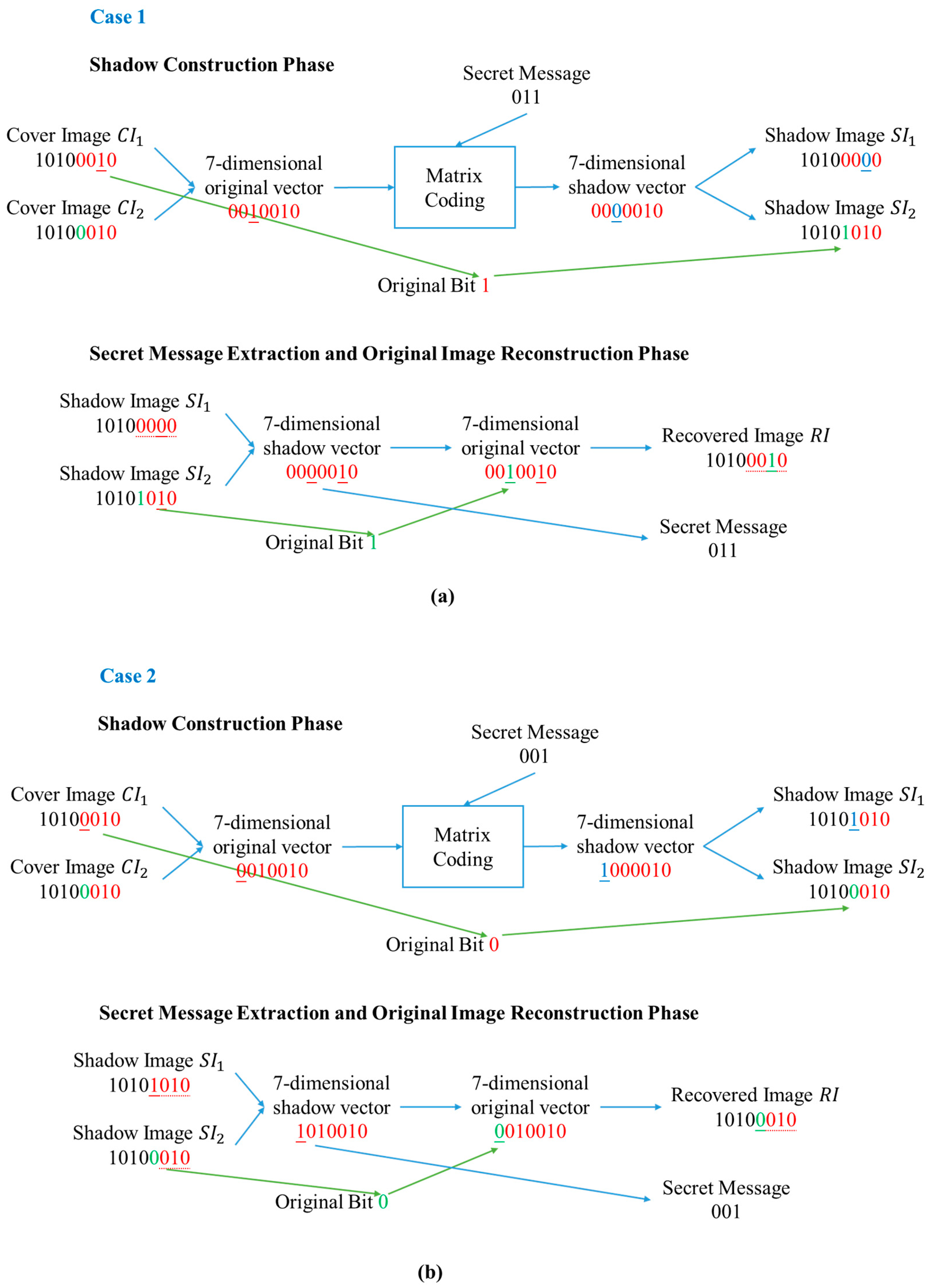
3.1. Shadow Construction Phase
| Algorithm 1. Shadow Construction | |
| Input | An original image and a secret message . |
| Output | Shadow images , . |
| Step 1 | Duplicate the original image and create two cover images , |
| Step 2 | Set the initial secret bit count |
| Step 3 | FOR each |
| Step 3a | Obtain three secret bits |
| Step 3b | Select current cover pixel pair = where pixel from the cover image and pixel from the cover image |
| Step 3c | Convert pixel values and to binary. |
| Step 3d | Construct the 7-dimensional cover vector using Equation (5). |
| Step 3e | Calculate the and obtain the shadow vector using Equations (2) and (3). |
| Step 3f | Let and |
| Step 3g | Set the recovery bit to store the original bit value for recovery as below, IF ELSE WHILE IF BREAK END END END |
| Step 3h | Set shadow pixel pair = where is the current pixel in shadow images and is the current pixel in shadow images according to IF is odd ( ( ELSE = ( = ( END |
| END | |
| Step 4 | Export shadow images , . |
3.2. Secret Message Extraction and Original Image Reconstruction Phase
| Algorithm 2. Secret Message Extraction and Original Image Reconstruction | |
| Input | Dual shadow images , . |
| Output | Recovered image , and recovered secret message . |
| Step 1 | Duplicate to . |
| Step 2 | Set the initial secret bit count . |
| Step 3 | FOR each |
| Set | |
| Step 3a | Set the current shadow pixel pair = where is the current pixel in the shadow image and is the current pixel in the shadow images . |
| Step 3b | Convert pixel values and to binary and let = and = . |
| Step 3c | Construct the shadow vector = using Equation (5) and use it as the coset leader. |
| Step 3d | Extract three secret bits based on the coset leader in Table 1 and append them to recovered secret message . |
| Step 3e | |
| Step 3f | Obtain the original bit value IF is odd ELSE END |
| Step 3g | Let = ( |
| Step 3h | Set the altered bit value back to its original value by the following: WHILE IF BREAK END END IF END |
| END | |
| Step 4 | Export recovered images and recovered secret message . |
3.3. Processing Flow Examples
4. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kumar, R.; Chand, S. A new image steganography technique based on similarity in secret message. In Proceedings of the Confluence 2013: The Next Generation Information Technology Summit (4th International Conference), Noida, India, 26–27 September 2013; IET: Stevenage, Hertfordshire, UK, 2013; pp. 376–379. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. An optimal information hiding approach based on pixel value differencing and modulus function. Wirel. Pers. Commun. 2019, 108, 159–174. [Google Scholar] [CrossRef]
- Bender, W.; Gruhl, D.; Morimoto, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Moulin, P.; O’Sullivan, J.A. Information-theoretic analysis of information hiding. IEEE Trans. Inf. Theory 2003, 49, 563–593. [Google Scholar] [CrossRef]
- Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E. Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 2005, 14, 253–266. [Google Scholar] [CrossRef] [PubMed]
- Zhang, W.; Hu, X.; Li, X.; Yu, N. Recursive histogram modification: Establishing equivalency between reversible data hiding and lossless data compression. IEEE Trans. Image Process. 2013, 22, 2775–2785. [Google Scholar] [CrossRef]
- Lin, C.C.; Liu, X.L.; Tai, W.L.; Yuan, S.M. A novel reversible data hiding scheme based on AMBTC compression technique. Multimed. Tools Appl. 2015, 74, 3823–3842. [Google Scholar] [CrossRef]
- Sun, W.; Lu, Z.M.; Wen, Y.C.; Yu, F.X.; Shen, R.J. High performance reversible data hiding for block truncation coding compressed images. Signal Image Video Process. 2013, 7, 297–306. [Google Scholar] [CrossRef]
- Chen, K.M. High capacity reversible data hiding based on the compression of pixel differences. Mathematics 2020, 8, 1435. [Google Scholar] [CrossRef]
- Rai, A.K.; Kumar, N.; Kumar, R.; Om, H.; Chand, S.; Jung, K.H. Intra-block correlation based reversible data hiding in encrypted images using parametric binary tree labeling. Symmetry 2021, 13, 1072. [Google Scholar] [CrossRef]
- Mittal, S.; Goyal, S.; Aggarwal, S.; Kumar, R. Interpolative AMBTC based reversible data hiding in encrypted images using rhombus mean. In Proceedings of the 2023 International Conference on Device Intelligence, Computing and Communication Technologies (DICCT), Dehradun, India, 17–18 March 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 451–456. [Google Scholar] [CrossRef]
- Kumar, R.; Sharma, D.; Dua, A.; Jung, K.H. A review of different prediction methods for reversible data hiding. J. Inf. Secur. Appl. 2023, 78, 103572. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Yan, W.; Ding, W.; Dongxu, Q. Image sharing based on Chinese remainder theorem. J. North China Univ. Technol. 2000, 12, 6–9. [Google Scholar]
- Chang, C.C.; Kieu, T.D.; Chou, Y.C. Reversible data hiding scheme using two steganographic images. In Proceedings of the TENCON 2007—2007 IEEE Region 10 Conference, Taipei, Taiwan, 30 October–2 November 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 1–4. [Google Scholar] [CrossRef]
- Qin, C.; Chang, C.C.; Hsu, T.J. Reversible data hiding scheme based on exploiting modification direction with two steganographic images. Multimed. Tools Appl. 2015, 74, 5861–5872. [Google Scholar] [CrossRef]
- Lu, T.C.; Tseng, C.Y.; Wu, J.H. Dual imaging-based reversible hiding technique using LSB matching. Signal Process. 2015, 108, 77–89. [Google Scholar] [CrossRef]
- Huang, C.T.; Weng, C.Y.; Shongwe, N.S. Capacity-Raising Reversible Data Hiding Using Empirical Plus–Minus One in Dual Images. Mathematics 2023, 11, 1764. [Google Scholar] [CrossRef]
- Jana, B.; Giri, D.; Kumar Mondal, S. Dual image based reversible data hiding scheme using (7, 4) hamming code. Multimed. Tools Appl. 2018, 77, 763–785. [Google Scholar] [CrossRef]
- Kim, C.; Yang, C.N.; Zhou, Z.; Jung, K.H. Dual efficient reversible data hiding using Hamming code and OPAP. J. Inf. Secur. Appl. 2023, 76, 103544. [Google Scholar] [CrossRef]
- Chang, C.C.; Kieu, T.D.; Chou, Y.C. A high payload steganographic scheme based on (7, 4) hamming code for digital images. In Proceedings of the 2008 International Symposium on Electronic Commerce and Security, Guangzhou, China, 3–5 August 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 16–21. [Google Scholar] [CrossRef]



| Syndrome | 000 | 001 | 010 | 011 | 100 | 101 | 110 | 111 |
| Coset leader | 0000000 | 1000000 | 0100000 | 0010000 | 0001000 | 0000100 | 0000010 | 0000001 |
| Images | PSNR (dB) | SSIM | ||||
|---|---|---|---|---|---|---|
| Shadow 1 | Shadow 2 | Average | Shadow 1 | Shadow 2 | Average | |
| Airplane | 36.36 | 36.35 | 36.35 | 0.8990 | 0.8984 | 0.8987 |
| Baboon | 36.33 | 36.34 | 36.33 | 0.9645 | 0.9644 | 0.9645 |
| Barbara | 36.36 | 36.36 | 36.36 | 0.9313 | 0.9313 | 0.9313 |
| Boat | 36.30 | 36.27 | 36.28 | 0.9259 | 0.9255 | 0.9257 |
| Goldhill | 36.32 | 36.33 | 36.32 | 0.9274 | 0.9279 | 0.9277 |
| Lena | 36.41 | 36.37 | 36.39 | 0.9030 | 0.9026 | 0.9028 |
| Lake | 36.34 | 36.36 | 36.35 | 0.9253 | 0.9256 | 0.9255 |
| Peppers | 36.36 | 36.36 | 36.36 | 0.9053 | 0.9053 | 0.9053 |
| Average | 36.35 | 36.34 | 36.34 | 0.9227 | 0.9226 | 0.9227 |
| Scheme | Indicator | Barbara | Goldhill | Lena | Peppers |
|---|---|---|---|---|---|
| proposed scheme | EC | 786,432 | 786,432 | 786,432 | 786,432 |
| bpp | 1.50 | 1.50 | 1.50 | 1.50 | |
| PSNR1 | 36.36 | 36.32 | 36.41 | 36.36 | |
| PSNR2 | 36.36 | 36.33 | 36.37 | 36.36 | |
| PSNRAVG | 36.36 | 36.32 | 36.39 | 36.36 | |
| Qin et al. [16] | EC | 557,339 | 557,194 | 557,052 | 557,245 |
| bpp | 1.06 | 1.06 | 1.06 | 1.06 | |
| PSNR1 | 52.12 | 52.12 | 52.11 | 51.25 | |
| PSNR2 | 41.58 | 41.58 | 41.58 | 41.52 | |
| PSNRAVG | 46.85 | 46.85 | 46.85 | 46.39 | |
| Lu et al. [17] | EC | 524,288 | 524,288 | 524,288 | 524,192 |
| bpp | 1.00 | 1.00 | 1.00 | 1.00 | |
| PSNR1 | 49.14 | 49.17 | 49.13 | 49.11 | |
| PSNR2 | 49.11 | 49.09 | 49.12 | 49.08 | |
| PSNRAVG | 49.13 | 49.13 | 49.13 | 49.10 | |
| Jana et al. [19] | EC | 74,752 | 74,752 | 75,752 | 73,728 |
| bpp | 0.14 | 0.14 | 0.14 | 0.14 | |
| PSNR1 | 51.86 | 51.86 | 51.85 | 51.84 | |
| PSNR2 | 51.96 | 51.97 | 51.56 | 51.94 | |
| PSNRAVG | 51.91 | 51.92 | 51.71 | 51.89 | |
| Kim et al. [20] | EC | 524,288 | 524,288 | 524,288 | 524,288 |
| bpp | 1.00 | 1.00 | 1.00 | 1.00 | |
| PSNR1 | 54.12 | 54.16 | 54.14 | 54.15 | |
| PSNR2 | 48.14 | 48.11 | 48.13 | 48.12 | |
| PSNRAVG | 51.13 | 51.14 | 51.14 | 51.14 |
| Phase | Execution Time (s) |
|---|---|
| Shadow Construction Phase | 0.5242 |
| Secret Message Extraction and Original Image Reconstruction Phase | 0.9158 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, J.-C.; Chang, C.-C.; Lin, Y.; Chang, C.-C.; Horng, J.-H. A Matrix Coding-Oriented Reversible Data Hiding Scheme Using Dual Digital Images. Mathematics 2024, 12, 86. https://doi.org/10.3390/math12010086
Liu J-C, Chang C-C, Lin Y, Chang C-C, Horng J-H. A Matrix Coding-Oriented Reversible Data Hiding Scheme Using Dual Digital Images. Mathematics. 2024; 12(1):86. https://doi.org/10.3390/math12010086
Chicago/Turabian StyleLiu, Jui-Chuan, Ching-Chun Chang, Yijie Lin, Chin-Chen Chang, and Ji-Hwei Horng. 2024. "A Matrix Coding-Oriented Reversible Data Hiding Scheme Using Dual Digital Images" Mathematics 12, no. 1: 86. https://doi.org/10.3390/math12010086
APA StyleLiu, J.-C., Chang, C.-C., Lin, Y., Chang, C.-C., & Horng, J.-H. (2024). A Matrix Coding-Oriented Reversible Data Hiding Scheme Using Dual Digital Images. Mathematics, 12(1), 86. https://doi.org/10.3390/math12010086








