A Hierarchical Authorization Reversible Data Hiding in Encrypted Image Based on Secret Sharing
Abstract
1. Introduction
- We propose a hierarchical authorization structure RDH-ED for secret sharing through difference preservation. This innovative approach involves classifying participants’ identities into different levels, employing diverse embedding methods, necessitating core users’ participation in secret reconstruction, and granting core users enhanced privileges. These enhancements effectively meet the hierarchical authorization demands of RDH-ED in distributed scenarios.
- A polynomial embedding algorithm is developed for embedding copyright information into polynomial coefficients during secret distribution by the image owner. This functionality enables the authentication of the carrier image, thereby bolstering security and traceability.
- We propose a hierarchical embedding algorithm that segregates participants into core users and ordinary users. Core users utilize adaptive difference reservation embedding, while ordinary users employ pixel bit replacement embedding. This strategy ensures that core users play a pivotal role in secret recovery during reconstruction, elevating their authorization levels.
- Compared with the existing superior RDH-ED, our scheme boasts a higher embedding rate, lower expansion rate, enhanced security, and superior reversibility, showing significant performance enhancements compared to current solutions.
2. Related Works
2.1. Shamir’s (k, n) Secret Sharing
2.2. SIS Based on Pixel Difference Preservation
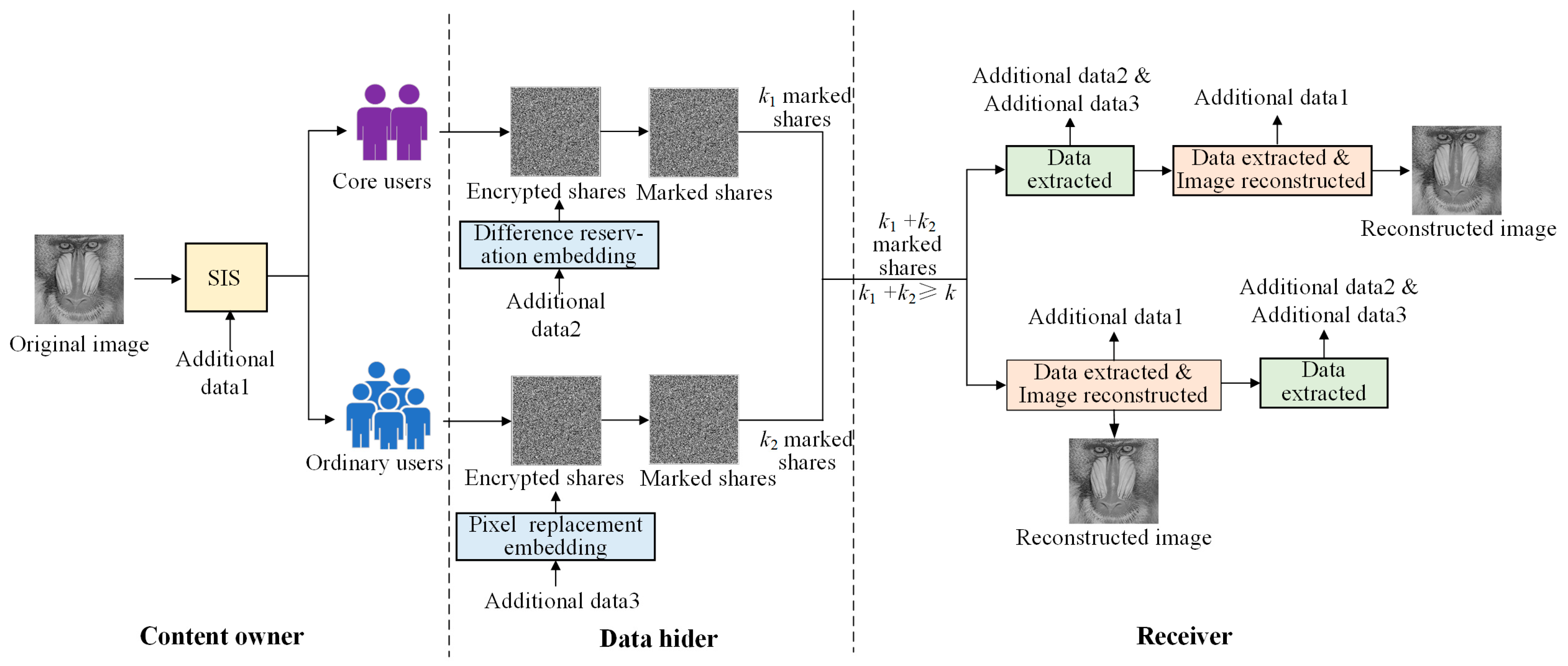
3. Proposed RDHEI-ED Scheme
3.1. The Procedures of Hierarchical Authorization Structure RDH-ED
| Algorithm 1: Secret sharing and data embedding |
| Input: original image, k1, k, n 1: Split the image into blocks of size 2 × 2; 2: Scramble image blocks using scrambled key; 3: Generate session key using users’ identity numbers and pseudorandom number generator; 4: Scan the image blocks to obtain the size M; 5: l←1; 6: while l < M do 7: Scan image block to obtain pixels a, b, c, d; 8: Encrypt extra secrets using AES; 9: Construct the polynomial f(x); 10: Calculate f(x) by substituting session key as x to generate then distribute shares to participant P; 11: if P == core users 12: Implementing difference preserving embedding; 13: else 14: Implementing pixel bit replacement embedding; 15: end if 16: l←l + 1; 17: end while Output: Share images with extra secrets embedded |
3.2. Image Preprocessing
3.3. Session Key Generation
3.4. Encrypted Image Generation
3.4.1. Polynomial Construction
3.4.2. Secret Share Generation
3.5. Marked Image Generation after Data Embedding
3.5.1. Difference Reservation Embedding
3.5.2. Pixel Bit Replacement Embedding
3.6. Data Extraction and Image Recovery
| Algorithm 2: Secret extraction and image reconstruction |
| Input: Share images with extra secrets embedded, k1, k, n 1: l←1; 2: while l < M do 3: if P == core users 4: Obtain the first pixel and the three differences; 5: Extract the extra secret; 6: else 7: Obtain the first pixel; 8: Extract the extra secret; 9: Recovering the first original pixel using the first share pixel by Theorem 1; 10: Use the three differences and the first original pixel to obtain the original three pixels. 11: end if 12: l←l + 1; 13: end while Output: Extra secret, reconstructed image |
3.7. Instance of the Proposed Scheme
4. Experimental Results and Comparisons
4.1. Security Analysis
4.1.1. Keyspace
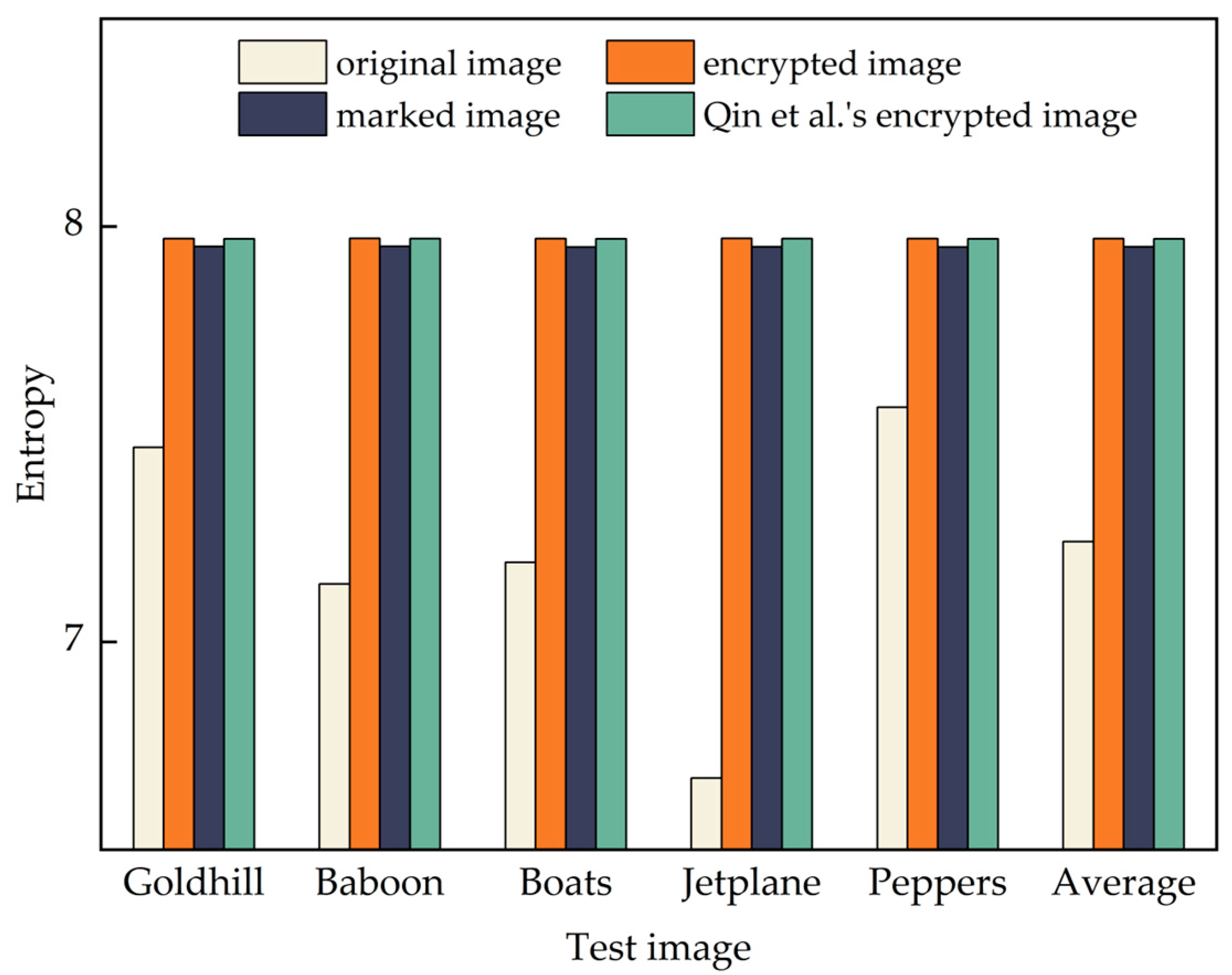
4.1.2. Histogram
4.1.3. Relevant Parameters
- Shannon Entropy
- 2.
- PSNR and SSIM
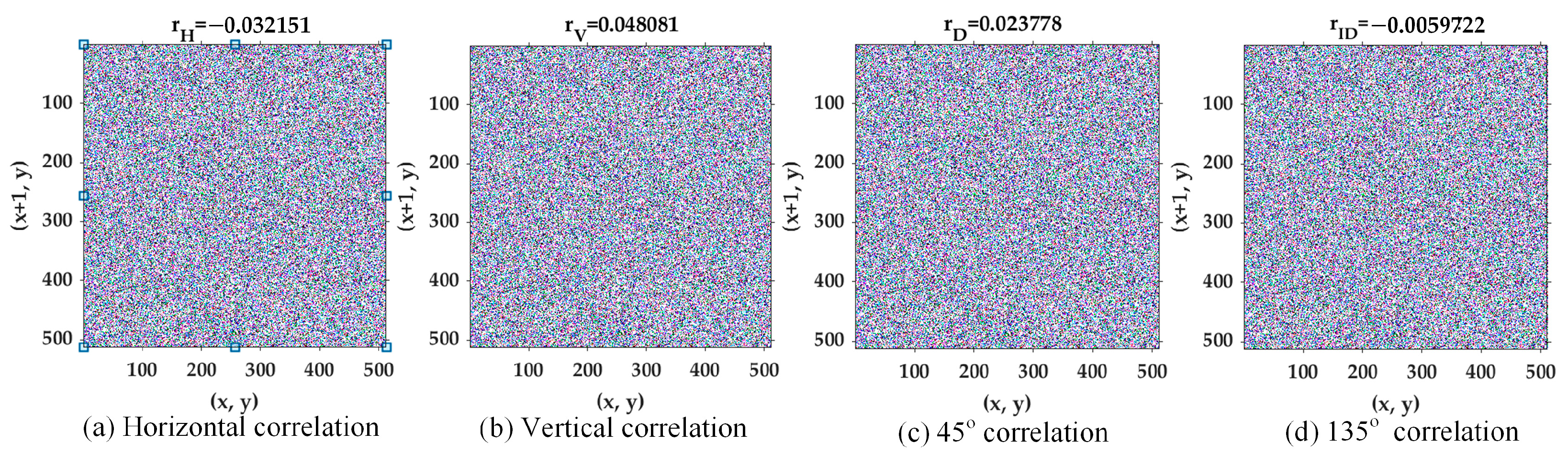
4.1.4. Pixel Correlation
4.2. Embedding Rate
4.3. Reversibility
4.3.1. Relevant Parameters
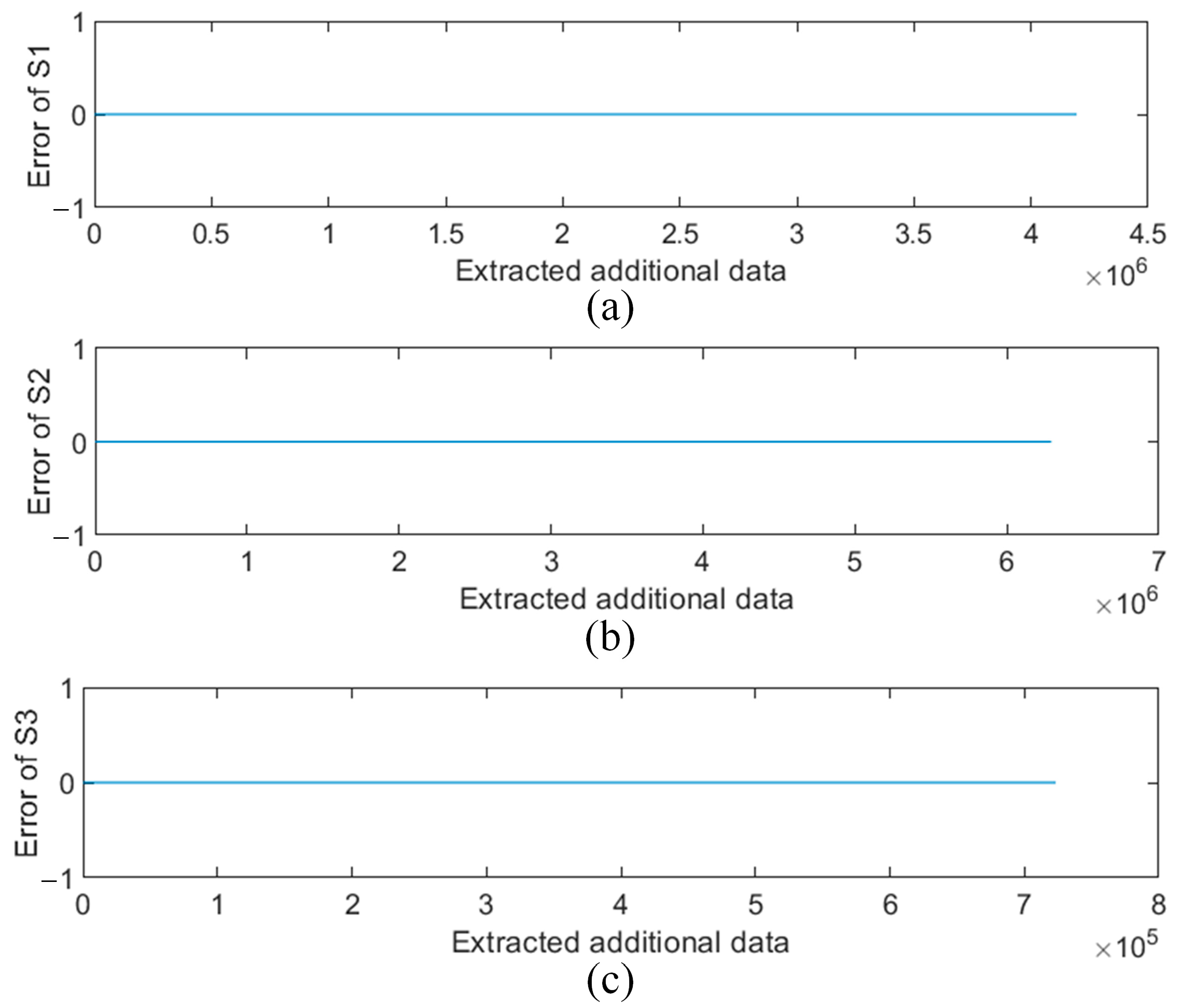
4.3.2. Error Map for Secret Extraction
4.4. Data Extension
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Puech, W.; Chaumont, M.; Strauss, O. A reversible data hiding method for encrypted images. In Proceedings of the SPIE—The International Society for Optical Engineering, San Jose, CA, USA, 18 March 2008; Volume 6819. [Google Scholar] [CrossRef]
- Zhang, X.P. Reversible Data hiding in encrypted image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Zhou, J.T.; Sun, W.W.; Dong, L.; Liu, X.M.; Au, O.C.; Tang, Y.Y. Secure reversible image data hiding over encrypted domain via key modulation. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 441–452. [Google Scholar] [CrossRef]
- Wu, X.T.; Weng, J.; Yang, W.Q. Adopting secret sharing for reversible data hiding in encrypted images. Signal Process. Off. Publ. Eur. Assoc. Signal Process. 2018, 143, 269–281. [Google Scholar] [CrossRef]
- Wang, Y.; Yan, S.; Yang, W.; Cai, Y. Covert communications with constrained age of information. IEEE Wirel. Commun. Lett. 2021, 10, 368–372. [Google Scholar] [CrossRef]
- Ansari, M.R.R.; Allwinnaldo; Alief, R.N.; Igboanusi, I.S.; Lee, J.M.; Kim, D.S. HADES: Hash-Based audio copy detection system for copyright protection in decentralized music sharing. IEEE Trans. Netw. Serv. Manag. 2023, 20, 2845–2853. [Google Scholar] [CrossRef]
- Qian, Z.; Zhang, X.; Wang, S. Reversible data hiding in encrypted JPEG bitstream. IEEE Trans. Multimed. 2014, 16, 1486–1491. [Google Scholar] [CrossRef]
- Huang, F.; Huang, J.; Shi, Y.Q. New framework for reversible data hiding in encrypted domain. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2777–2789. [Google Scholar] [CrossRef]
- Xiang, S.; Luo, X. Reversible data hiding in homomorphic encrypted domain by mirroring ciphertext group. IEEE Trans. Circuits Syst. Video Technol. 2018, 28, 3099–3110. [Google Scholar] [CrossRef]
- Wang, X.; Chang, C.C.; Lin, C.C. Reversible data hiding in encrypted images with block-based adaptive MSB encoding. Inf. Sci. 2021, 567, 375–394. [Google Scholar] [CrossRef]
- Yang, Y.; He, H.; Chen, F.; Yuan, Y.; Mao, N. Reversible data hiding in encrypted images based on time-Varying huffman coding table. IEEE Trans. Multimed. 2023, 25, 8607–8619. [Google Scholar] [CrossRef]
- Chen, K.M.; Chang, C.C. High-capacity reversible data hiding in encrypted images based on extended run-length coding and block-based MSB plane rearrangement. J. Vis. Commun. Image Represent. 2019, 58, 334–344. [Google Scholar] [CrossRef]
- Yin, Z.X.; Xiang, Y.Z.; Zhang, X.P. Reversible data hiding in encrypted images based on multi-MSB prediction and huffman Coding. IEEE Trans. Multimed. 2020, 22, 874–884. [Google Scholar] [CrossRef]
- Puteaux, P.; Puech, W. A Recursive Reversible data hiding in encrypted images method with a very high payload. IEEE Trans. Multimed. 2021, 23, 636–650. [Google Scholar] [CrossRef]
- Gao, G.; Zhang, L.; Lin, Y.; Tong, S.; Yuan, C. High-performance reversible data hiding in encrypted images with adaptive Huffman code. Digit. Signal Process. 2023, 133, 103870. [Google Scholar] [CrossRef]
- Zou, H.; Chen, G.H. Reversible data hiding in encrypted image with local-correlation-based classification and adaptive encoding strategy. Signal Process. 2023, 205, 1108847. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.Q.; Liu, J. A multilevel reversible data hiding scheme in encrypted domain based on R-LWE. Comput. Res. Dev. 2016, 53, 2307–2322. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.Q.; Liu, J.; Su, T.T.; Yang, X.Y. Fully homomorphic encryption encapsulated difference expansion for reversible data hiding in encrypted domain. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 2353–2365. [Google Scholar] [CrossRef]
- Chinnasamy, P.; Deepalakshmi, P.; Dutta, A.K.; You, J.; Joshi, G.P. Ciphertext-Policy Attribute-Based Encryption for Cloud Storage: Toward Data Privacy and Authentication in AI-Enabled IoT System. Mathematics 2022, 10, 68. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Priyanka, S.; Raman, B. Reversible data hiding based on Shamir’s secret sharing for color images over cloud. Inf. Sci. 2018, 422, 77–97. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.Q.; Zhang, X.P.; Liu, J.; Su, T.T.; Yang, X.Y. A reversible data hiding scheme in encrypted domain for secret image sharing based on Chinese Remainder Theorem. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 2469–2481. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Wang, Y.; Yi, S.; Zhou, Y.; Jia, X. Reversible data hiding in encrypted images using cipher-feedback secret sharing. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 4968–4982. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Wang, Y.; Yi, S.; Zheng, Y.F.; Liu, X.Y.; Chen, Y.Y.; Zhang, X.P. Matrix-based secret sharing for reversible data hiding in encrypted images. IEEE Trans. Dependable Secur. Comput. 2023, 20, 3669–3686. [Google Scholar] [CrossRef]
- Yu, C.; Zhang, X.; Qin, C.; Tang, Z. Reversible Data Hiding in Encrypted Images with Secret Sharing and Hybrid Coding. IEEE Trans. Circuits Syst. Video Technol. 2023, 33, 6443–6458. [Google Scholar] [CrossRef]
- Qin, C.; Jiang, C.Y.; Mo, Q.; Yao, H.; Chang, C.C. Reversible data hiding in encrypted image via secret sharing based on GF(p) and GF(2⁸). IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 1928–1941. [Google Scholar] [CrossRef]
- Chen, B.; Lu, W.; Huang, J.W.; Weng, J.; Zhou, Y.C. Secret sharing based reversible data hiding in encrypted images with multiple data-hiders. IEEE Trans. Dependable Secur. Comput. 2020, 19, 978–991. [Google Scholar] [CrossRef]
- Chen, Y.C.; Hung, T.; Hsieh, S.; Shiu, C. A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic schemes. IEEE Trans. Data Forensics Secur. 2019, 14, 3332–3343. [Google Scholar] [CrossRef]

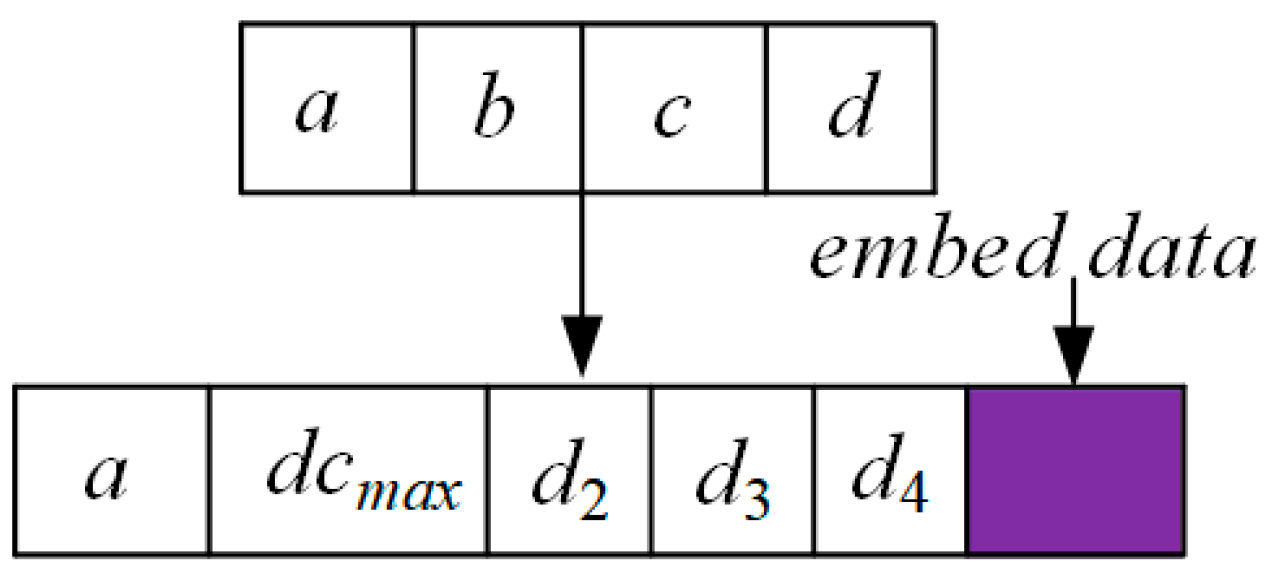





| |d|max | dcmax | |d| Coding Bits | Data Hiding Bits |
|---|---|---|---|
| [0, 1] | 000 | 1 | 15 |
| [2, 3] | 001 | 2 | 12 |
| [4, 7] | 010 | 3 | 9 |
| [8, 15] | 011 | 4 | 6 |
| [16, 31] | 100 | 5 | 3 |
| [32, 63] | 101 | 6 | 0 |
| Maximum Embedding Rate (bpp) | k = 2 | k = 3 | k = 4 | |||
|---|---|---|---|---|---|---|
| n = 2 | n = 3 | n = 3 | n = 4 | n = 4 | n = 5 | |
| Goldhill | 4.2532 | 2.9202 | 5.5865 | 4.2534 | 6.2531 | 5.0532 |
| Baboon | 4.1226 | 2.7897 | 5.4561 | 4.1228 | 6.1227 | 4.9227 |
| Boats | 4.1956 | 2.8664 | 5.5288 | 4.1954 | 6.1954 | 4.9951 |
| Airplane | 4.3332 | 3.0003 | 5.6666 | 4.3331 | 6.3334 | 5.1334 |
| Peppers | 4.3450 | 3.0121 | 5.6783 | 4.3450 | 6.3448 | 5.1450 |
| Jetplane | 4.3329 | 2.9996 | 5.6664 | 4.3331 | 6.3331 | 5.1330 |
| Test Image | Scheme [4] | Scheme [24] | Scheme [26] | Scheme [27] |
|---|---|---|---|---|
| Goldhill | 140% | 74% | 186% | 144% |
| Baboon | 162% | 312% | 667% | 136% |
| Boats | 129% | 57% | 185% | 140% |
| Airplane | 75% | 20% | 86% | 148% |
| Jetplane | 109% | 38% | 190% | 148% |
| Peppers | 138% | 73% | 175% | 149% |
| Test Image | MSE | PSNR | SSIM |
|---|---|---|---|
| Goldhill | 0 | +∞ | 1 |
| Baboon | 0 | +∞ | 1 |
| Boats | 0 | +∞ | 1 |
| Airplane | 0 | +∞ | 1 |
| Peppers | 0 | +∞ | 1 |
| Jetplane | 0 | +∞ | 1 |
| Scheme | Type | Encryption | Relative Expansion Rate | Total Expansion Rate |
|---|---|---|---|---|
| Ke et al. [22] | VRIE | Homomorphic encryption | 256 | 256 |
| Hua et al. [23] | VRAE | Secret sharing | 1/(r − 1) | n/(r − 1) |
| Qin et al. [26] | VRAE | Secret sharing | 1 | n |
| Chen et al. [28] | VRBE | Multi-secret sharing | 1 | 1 |
| Proposed | VRIE + VRAE | Secret sharing | 1 | n |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, C.; Zhang, M.; Kong, Y.; Jiang, Z.; Di, F. A Hierarchical Authorization Reversible Data Hiding in Encrypted Image Based on Secret Sharing. Mathematics 2024, 12, 2262. https://doi.org/10.3390/math12142262
Jiang C, Zhang M, Kong Y, Jiang Z, Di F. A Hierarchical Authorization Reversible Data Hiding in Encrypted Image Based on Secret Sharing. Mathematics. 2024; 12(14):2262. https://doi.org/10.3390/math12142262
Chicago/Turabian StyleJiang, Chao, Minqing Zhang, Yongjun Kong, Zongbao Jiang, and Fuqiang Di. 2024. "A Hierarchical Authorization Reversible Data Hiding in Encrypted Image Based on Secret Sharing" Mathematics 12, no. 14: 2262. https://doi.org/10.3390/math12142262
APA StyleJiang, C., Zhang, M., Kong, Y., Jiang, Z., & Di, F. (2024). A Hierarchical Authorization Reversible Data Hiding in Encrypted Image Based on Secret Sharing. Mathematics, 12(14), 2262. https://doi.org/10.3390/math12142262






