1. Introduction: The Use of Simple Graphs in the Description of the Fundamental Entities
Apriorics is an attempt to describe the fundamental building block of physical reality in terms of graph theory and information. The philosophical basis of apriorics was dealt with in [
1], in which apriorics was connected to structuralism, a philosophical approach denying inherent meaning to any notion, and interprets each and everything solely in terms of its connections to other things. Here, we are more concerned with the mathematical aspects of the theory and less with the philosophical aspects. Hence, we focus our attention on proofs and rigorous mathematical derivations.
To be sure, also the General Theory of Information, as a multidisciplinary framework, seeks to understand and quantify information in various contexts. Proposed by physicist Giancarlo Ruffo, it builds on the foundational work of Claude Shannon’s information theory. This theory goes beyond traditional concepts of information, extending to complex systems, thermodynamics, biology, and even the quantum realm. It explores the role of information in shaping the behavior and organization of systems, emphasizing the link between entropy, complexity, and information. By doing so, the General Theory of Information provides a comprehensive perspective on how information is a fundamental element in the fabric of our universe, impacting diverse scientific domains [
2,
3,
4,
5,
6,
7,
8,
9,
10,
11]. Notice, however, that the General Theory of Information cannot predict the correct number of fundamental fermions and fundamental gauge bosons and the three fundamental interactions in the way that apriorics does, as is described below.
Category theory is a branch of abstract mathematics that focuses on studying relationships and structures in a generalized way. It deals with objects and morphisms (arrows) between them, emphasizing their properties and how they interact, rather than specific elements. Categories provide a framework for understanding diverse mathematical and scientific concepts, including algebra, topology, and logic. By abstracting the commonalities between different mathematical structures, category theory promotes a deeper understanding of mathematical concepts and their universal principles. Its broad applicability extends beyond mathematics, finding use in computer science, physics, and other fields for modeling and reasoning about complex systems [
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31]. However, category theory does not predict the correct number of fundamental fermions and fundamental gauge bosons and the three fundamental interactions in the way that apriorics does.
Of course, graph theory has a much wider application domain with respect to apriorics. Graph theory, being a branch of mathematics, has numerous real-life applications across various fields. Here are some examples:
Social networks: Graph theory is extensively used in social network analysis to model relationships between individuals or entities. It helps analyze connectivity patterns, identify influential nodes (people), and understand information flow within networks like Facebook, Twitter, or LinkedIn.
Transportation networks: Graphs model transportation systems such as road networks, railway lines, and airline routes. Graph algorithms optimize routes, schedule public transportation, and analyze traffic flow, contributing to urban planning and logistics management.
Telecommunications: Graph theory aids in designing communication networks, including the internet, mobile networks, and satellite communication systems. It optimizes data routing, analyzes network robustness, and ensures efficient transmission of information.
Epidemiology: Graphs model disease spread within populations, with nodes representing individuals and edges representing contacts or interactions. Graph analysis helps track and predict disease outbreaks, assess vaccination strategies, and identify key factors influencing transmission.
Biology and genetics: Graph theory is used to model biological systems such as protein–protein interaction networks, metabolic pathways, and gene regulatory networks. It aids in understanding biological processes, identifying essential genes or proteins, and predicting drug targets.
Computer networks: Graphs represent computer networks, with nodes as devices (computers and routers) and edges as connections (links and cables). Graph algorithms optimize network routing, detect network intrusions, and ensure robustness and reliability of communication systems.
Recommendation systems: Graph theory underlies recommendation algorithms in e-commerce, streaming services, and social media platforms. It models user–item interactions and generates personalized recommendations based on similarities between users or items.
Operations research: Graph theory is applied in operations research to model complex systems; optimize resource allocation; and solve logistical problems such as the traveling salesman problem, network flow problems, and facility location problems.
Chemistry and molecular biology: Graph theory represents molecular structures and chemical compounds, aiding in drug discovery, molecular modeling, and understanding chemical reactions. It helps analyze molecular interactions, predict compound properties, and design novel drugs.
Image processing and computer vision: Graph-based techniques are used in image segmentation, object recognition, and pattern recognition. Graph algorithms extract features from images, analyze image similarity, and enhance image understanding in various applications, including medical imaging and surveillance systems.
These examples demonstrate the versatility and applicability of graph theory in addressing complex real-world problems across diverse domains.
Attack graphs are graphical representations used in cybersecurity to model and analyze potential threats and vulnerabilities in a computer network. Here is how one can model threats using attack graphs:
Identify assets and vulnerabilities:
- −
Begin by identifying the assets within the network that need to be protected, such as servers, databases, and sensitive data.
- −
Identify potential vulnerabilities in the network, including software vulnerabilities, misconfigurations, weak passwords, and insecure network protocols.
Construct the attack graph:
- −
Represent the network as a graph, where nodes represent network components (e.g., hosts, routers, and switches) and edges represent possible attack paths between them.
- −
Start with an initial node representing the attacker’s entry point into the network.
- −
Add nodes and edges to the graph to represent the attacker’s progression through the network, exploiting vulnerabilities and gaining access to different components.
- −
Each node in the graph represents a state of compromise (e.g., gaining unauthorized access to a server), and each edge represents a specific attack path or exploitation technique.
Assign attack costs and probabilities:
- −
Assign costs or probabilities to edges in the graph to represent the difficulty or likelihood of a successful attack along that path.
- −
Factors influencing costs or probabilities may include the complexity of the attack, the strength of security measures in place, and the attacker’s skill level.
Analyze attack paths:
- −
Analyze the attack graph to identify critical paths that attackers could take to compromise sensitive assets.
- −
Identify common attack patterns and techniques used by adversaries to exploit vulnerabilities and move laterally within the network.
Mitigation and remediation:
- −
Use the attack graph analysis to prioritize security measures and allocate resources for mitigating vulnerabilities and reducing the risk of successful attacks.
- −
Implement security controls, such as firewalls, intrusion detection systems, and access controls, to disrupt or block potential attack paths identified in the graph.
- −
Continuously monitor and update the attack graph as new vulnerabilities are discovered or as the network configuration changes.
By modeling threats using attack graphs, organizations can gain insights into potential attack scenarios, prioritize security efforts, and enhance the resilience of their networks against cyber threats.
The computational complexity of using graphs in real-life applications can vary widely depending on the specific problem being addressed, the size and complexity of the graph, and the algorithms and techniques employed. Here are some considerations:
Graph representation: The complexity of representing a graph in memory depends on the number of vertices (nodes) and edges, as well as the data structures used. For sparse graphs, where the number of edges is relatively low compared to the number of vertices, adjacency lists may be more efficient than adjacency matrices.
Graph traversal: Algorithms for traversing graphs, such as depth-first search (DFS) or breadth-first search (BFS), have time complexities of O(V + E), where V is the number of vertices, and E is the number of edges. Traversal can become computationally expensive for large graphs or graphs with dense connectivity.
Shortest paths: Finding the shortest path between two vertices in a graph, using algorithms like Dijkstra’s algorithm or the Bellman–Ford algorithm, typically has a time complexity of O((V + E)logV) or O(VE), depending on the algorithm used and whether negative edge weights are allowed.
Graph connectivity: Determining graph connectivity, such as whether the graph is strongly connected or whether there exists a path between every pair of vertices, can be computationally intensive. Algorithms like Tarjan’s strongly connected components algorithm have a time complexity of O(V + E).
Graph coloring: Problems such as graph coloring, where vertices must be assigned colors such that no adjacent vertices share the same color, are known to be NP-hard. Finding an optimal coloring for an arbitrary graph can be computationally intractable, and heuristic approaches are often used in practice.
Maximum flow: Computing maximum flow in a graph, such as in network flow problems, can be solved efficiently using algorithms like the Ford–Fulkerson algorithm or the Edmonds–Karp algorithm, with a time complexity of O(V E2).
Graph clustering and community detection: Identifying clusters or communities within a graph involves partitioning the vertices into groups based on their connectivity patterns. Various algorithms exist for this task, such as the Louvain method or spectral clustering, with varying computational complexities depending on the approach.
In summary, the computational complexity of using graphs in real-life applications can range from linear time complexity for simple traversal algorithms to exponential or NP-hard complexity for more complex problems such as graph coloring or finding optimal solutions. Efficient algorithms, careful problem formulation, and leveraging problem-specific properties of the graph are essential for managing computational complexity in practical applications.
In previous works [
1,
32,
33,
34,
35,
36], a theory for the description of the fundamental entities, named apriorics, was suggested and elaborated. The predictions of this theory were compatible with experimental findings in elementary particle physics. In this theory, the fundamental entities (FEs) are the vertices in a simple undirected graph [
37,
38,
39,
40] called an ontological structure (OS), and they can be described by their internal connections defining the graph, without any needed reference to anything else. These nodes must satisfy the following five axioms (which are explained and justified in [
32,
33]):
- (a)
Every node (vertex) must be connected to one other vertex (at least).
- (b)
The connection between two nodes (vertices) is non-reflective (a node cannot connect to itself) and commutative (if node F1 is connected to node F2, it necessarily follows that F2 is connected to F1), but not necessarily transitive (if F1 is connected to F2 and F2 is connected to F3, it does not mean that F1 and F3 are connected).
- (c)
Two nodes (vertices) can be connected by not more than one connection.
- (d)
If two nodes (vertices), F1 and F2, are connected, then there must exist an additional third node (vertex), F3, connected to F1 and F2. F3 will be denoted the “mediator” between the nodes F1 and F2.
- (e)
It is required that every two nodes (vertices) are different (the meaning of the word “different” is to be explained below) in terms of their connections to the other nodes (vertices).
In this paper, we show through mathematical proof that there is no ontological structure with less than seven nodes. We also show through construction that there are at least two distinct ontological structures with seven nodes. In addition, we show how the connections (edges) of those graphs can be mapped into the elementary particles (basic fermions and bosons) and how the properties of those connections (elementary particles) can be derived.
Thus, the information contained in the above set of axioms is equivalent to the information of the required particles (fundamental fermions and gauge bosons) in the standard model of elementary particles, as we show below.
The fifth axiom (axiom e) requires criteria to distinguish between two nodes (vertices) in the ontological structure (OS) graph by their connections to other nodes (vertices). The valency (number of connections) alone cannot serve to uniquely distinguish between two nodes (vertices) because, according to the equivalence theorem, every simple graph has at least two vertices of the same valency, so that axiom e will not be satisfied. An additional criterion, which might serve the purpose of distinction between two nodes (vertices), is given below:
Definition 1.
The significance set (SS) of vertex P is the set of all the valences of the nodes connected to P.
Figure 1 is given as an example. Let us look at SS(P
1) =2,3,3,5, since P
1 is connected to P
2, P
4, P
5, and P
6; and the valences of these nodes (vertices), which are given in parentheses in the figure, are, respectively, 3, 3, 2, and 5. By the same method, we derive SS (P
5) = 4,5.
Definition 2.
The vertices P1 and P2 are considered equal; P1 = P2 if, and only if, they have the same valency and SS (P1) = SS (P2).
For example, in
Figure 1, P
3 ≠ P
2. Both vertices have the same number of connections, 3, but they have different significance sets. SS (P
2) = 3,4,5; and SS (P
3) = 3,3,5.
Definition 3.
A simple, undirected graph respecting all five axioms, a to e, is to be named ontological structure (OS).
In the OS graph, every node corresponds to an FE, and every node connection (edge) corresponds to a binary combination of FEs which will be mapped to an elementary particle. The order of an OS is the number of nodes in the graph. Since each node corresponds to an FE, it is expected that the simplest description of physical reality will correspond to the OS with the lowest number of nodes.
3. Characteristics of OS Graphs
An interesting problem is the construction of the graphs of all possible OSs of a given order, n. The goal of obtaining a general solution to this problem has not been achieved yet, and we hope that experts in the enumeration of graphs satisfying specified conditions [
15] will be able to help in this endeavor. We believe that the following concepts and theorems have some potential in resolving this problem.
In the subsequent theorems and proofs, we use the following notations:
V(P) denotes the valency of the vertex P.
O(n)—OS graph of order n satisfying axioms a to e.
The multiplicity of k, mk, is the number of vertices having valency k. (See Definition 4).
The index I of O(n) is the number of vertices in the OS having different valency. (See Definition 5).
Theorem 1.
Let the vertices of O(n) be P1, P2, …, Pn. Let Ki = V(Pi) (1 ≤ i ≤ n). If max(Ki) < n − 1, then it is possible to enlarge the O(n) to O(n + 1) by adding the vertex Pn+1* and by connecting it to all the n vertices of O(n).
Proof.
Let us denote by P1*, P2*, …, Pn* the vertices P1, …, Pn when they are connected to Pn+1*. It is clear that V(Pi*) =V(Pi) + 1 for 1 ≤ i ≤ n. We have to show that the set of the vertices P1*, P2*, …Pn+1* satisfies the basic axioms, a to e. The proof of the validity of axioms a to c is trivial. Since Pn+1* is connected to all the n vertices, axiom d is satisfied for Pn+1*. The fact that the set P1, …., Pn is an OS guarantees that axiom d is satisfied also for the vertices P1*, …, Pn*. Now, let us turn to axiom e. It is clear that V(Pn+1*) ≠ V(Pi*) for every i ≤ n. Since we assumed that max{ V(Pi) } < n − 1, then max{ V(Pi*) } < n. It is easy to show that, for every two vertices, Pi* and Pj* in O(n + 1) (1 ≤ i ≠ j ≤ n) Pi*≠Pj* (because Pi ≠ Pj in O(n).), so that axiom e is satisfied for all the vertices of O(n + 1). □
As a result of Theorem 1, we obtain the following theorem:
Theorem 2.
In O(n), if max{V(Pi)} = n − 1, (1 ≤ i ≤ n), then by adding the vertex Pn+1* and by connecting it to all the other vertices, we do not obtain an OS.
Proof.
Suppose that V(Pk) = n − 1; then, V(Pk*) = n = V(Pn+1*). Also, since Pk* and Pn+1* are connected to all the other vertices, they have the same SS, so that Pk* = Pn+1*, and axiom e is not satisfied. □
A magnitude of some use in the analysis of OS is the multiplicity of a valency, V, defined as follows.
Definition 4.
In O(n), the vertices having the same valency shall be called equivalent vertices. The number of vertices, mk, having V = k shall be called the multiplicity of k.
Example 1.
The multiplicities of the vertices of the OS O1(7) and O2(7) discussed in the previous section are given in Table 6. Definition 5.
The index of O(n), I, is the number of vertices in the OS with a different valency.
Example 2.
In 01(7), I = 4 since there are 4 different equivalent subsets corresponding to the valencies 2, 3, 4, and 5. In O2(7), I = 5.
One direction towards the solution of the problem formulated above is to find analytical expressions of mk as a function of k and n. Let us turn now to a few theorems concerning this issue.
Theorem 3.
(a) Σimi = n. (b) 1/2·Σ i mi·i = N. Here, N is the number of edges in the OS considered.
The proof of this theorem emerges directly from Definitions 4 and 5.
Example 3.
For O1(7), 1/2·∑imi·i = 1/2·(2·2 + 2·3 + 1·4 + 2·5 + 0·6) = 12. For O2(7), 1/2·∑imi·i = 1/2·(2·2 + 1·3 + 2·4 + 1·5 + 1·6) = 13 (see Table 1 and Table 2). Theorem 4.
In O(n), mn−1 ≤ 1.
Proof.
The theorem states that, in the OS of order n, the maximum number of vertices having n − 1 connections (i.e., connected to all the other vertices) is 1. Suppose that for the two vertices, Pk and Pi, we have V(Pk) = V(Pi) = n − 1. Then, since both Pk and Pi are connected to all the other vertices, they have the same SS, such that Pk = Pi, in contradiction to axiom e. □
Theorem 5.
In O(n), if V(Pk) = V(Pi) = n − 2, then Pk must be connected to Pi.
Proof.
If Pk is not connected to Pi, then it must be connected to all the other n − 2 vertices. The same goes for the vertex Pi. (Since Pk and Pi have valency equal to n − 2.) So, both SS(Pk) = SS(Pi) and Pk = Pi are in contradiction to axiom e. □
Theorem 6.
In O(n) mn−2 ≤ n/2.
Proof.
Let us divide the set of the n vertices P1, …, Pn into two subsets: (a) the set containing all the mn−2 interconnected vertices having valency equal to n − 2 and (b) the set of all the other n − mn−2 vertices. Each vertex of set (a) has to be connected to n − 2 − (mn−2 − 1) =n − mn−2 − 1 vertices of set (b) (since it is connected to the mn−2 − 1 valency equal to n − 2, according to Theorem 5). Hence, each vertex of set (a) has to be connected to all the n − mn−2 vertices of set (b), except one (the “unpaired” one). In order that all the vertices of set (a) will have different SSs (otherwise, part of them would be equal, in contradiction to axiom e), they must be different in the vertex to which they are not connected (the “unpaired”). Hence, the number of different vertices in set (a) cannot be greater than the number of possible “unpaired” vertices, n − mn−2. We then have mn−2 ≤ n − mn−2 or mn−2 ≤ n/2. □
Example 4.
In O1(7) and in O2(7), n = 7, so that m5 ≤ 3.
Theorem 7.
In O(n), if mn−1 = 1, then mn−2 ≤ (n − 1)/2.
Proof.
According to Theorem 6, every vertex of set (a) (defined in the proof of the previous theorem) has to be connected to the other mn−2 − 1 vertices of this set, and, since mn−1 = 1, it also has to be connected to the vertex having V = n − 1. Hence, every vertex of set (a) is connected to those mn−2 vertices. Since its V = n − 2, it has to be connected to n − 2-mn−2 vertices having a valency different from n − 2 or n − 1. The number of vertices of set (b) is n − 1 − mn−2. Therefore, every vertex of set (a) has to be connected to all the n − mn−2 − 1 vertices of set (b), except one (the “unpaired” one). In order that all the vertices of set (a) will be different (according to axiom e), they must be different in the vertex to which they are not connected (the “unpaired”). Hence, the number of different vertices in set (a) cannot be greater than the number of possible “unpaired” vertices, n − mn−2 − 1. We then have mn−2 ≤ n − mn−2 − 1 or mn−2 ≤ (n − 1)/2. □
Theorem 8.
In O(n), if V(Pk) = V(Pi) = 2, then Pk cannot be connected to Pi.
Proof.
If Pk is connected to Pi, then, according to axiom d, there exists a mediator vertex, Pm, connected to both Pk and Pi. Let V(Pm) = x; then, SS(Pk) = 2,x. SS(Pi) = 2,x., so that Pk = Pi, in contradiction to axiom e. □
Theorem 9.
If mn−1 = 1, then m2 ≤ min{(n − 1)/2, I − 2}.
Proof.
Let set (a) be the set of all the m2 vertices having V = 2 and (b) be the set of all the other n- m2 vertices. Every vertex of (a) has to be connected to 2 vertices of (b) according to Theorem 8. Now, if mn−1 = 1, then every vertex of (a) must be connected to the vertex Pn−1, having V = n − 1, so that the number of possibilities of choosing the second vertex of the pair is n − m2 − 1, and so that m2 ≤ n − m2 − 1 or m2≤ (n − 1)/2. Also, every vertex of set (a) must be connected to a vertex with different valency of set (b) (since it is already connected to the vertex having valency equal to n − 1). The number of such subsets of vertices with different valency, excluding Pn−1, which is a subset of its own and the subset of vertices having V = 2, is I − 2, so that m2 ≤ I − 2. Hence, m2 ≤ min{(n − 1)/2, I − 2}. □
Theorem 10.
In O(n), if V(P) = 3 and P is connected to the vertices P1, P2, and P3, then one of these vertices, say P2, has to be connected to the other two and satisfy the condition v(P2) > 3.
Proof.
According to axiom d, if P1 is connected to P, then there must be another vertex connected to P and P1. Let this vertex be P2. The same goes for P3, which must be connected either to P1 or to P2. Hence, there is a vertex (from P1, P2, and P3) connected to the other two. Now, if this vertex is P2 and V(P2) = 3, then SS(P) = SS(P2) = 3,x,y, where x = V(P1) and y = V(P3), and P = P2. So, there exists at least one other vertex connected to P2; hence, V(P2) > 3. □
Theorem 11.
In O(n), if V(P) = 3, then P cannot be connected to more than one vertex having V = 2.
Proof.
Suppose that P is connected to P1, P2, and P3 and let V(P1) = V(P3) = 2 and V(P2) = x > 3 (according to the previous theorem). According to Theorem 10, the only possible connection of P to P1, P2, and P3 satisfies SS(P1) = SS(P3) = 3,x. So, P1 = P3, in contradiction to axiom e. □
Theorem 12.
If V(P) = 2, then P cannot be connected to more than one vertex having V = 3.
Proof.
Let P be connected to P1 and P2, and V(P1) = V(P2) = 3. According to axiom d, P1 and P2 have to be connected to each other, since if P and P1 are connected, there must be a vertex connected to both, but since V(P) = 2, this third vertex must be P2. According to Theorem 10, P1 has to be connected to P3, having V = x > 3. However, since P1 and P3 are connected, then according to axiom d, there must be a third vertex connected to both. Now, since P1 already has three connections (P, P2, and P3), no additional vertex can be connected to P1; hence, this mediator can be either P or P2. However, P has two connections already and can have no more. Thus, P3 must be connected to P2 so that SS(P1) = SS(P2) = 2,3,x, in contradiction to axiom e. □
Theorem 13.
There cannot exist an OS of the order n = 3.
Proof.
According to axioms a and d every vertex has to be connected to at least two other vertices so that all the three vertices in the graph have to be connected to each other. Hence the three vertices have the same valency = 2, and the same SS = 2,2. Thus, they are equal in contradiction to axiom e. □
Theorem 14.
There cannot exist an OS of order n = 4.
Proof.
In this case, the valency of the vertices can be 2 or 3. According to Theorem 10, the existence of a vertex having V = 3 is impossible since it necessitates the existence of a vertex having V greater than 3. Hence, all vertices must have V = 2. But according to Theorem 8, the connections between these vertices cannot be realized. □
Theorem 15.
There cannot exist an OS of order n = 5.
Proof.
Case 1: m4 = 0. According to the Theorem 6, m3 ≤ 2. Also, m2 ≤ 1 because the only available connections for a vertex having V = 2 are to two vertices having V = 3 (see Theorem 8). So, m2 + m3 + m4 ≤ 3 is in contradiction to Theorem 3a, claiming that this sum should be equal to n = 5. □
Case 2: m4 = 1. According to the Theorem 7, m3 ≤ 2. According to Theorem 9, m2 ≤ I − 2 = 1. (In this case I = 3 since there are three equivalent sets of vertices having V = 2,3,4.) Hence, m2 + m3 + m4 ≤ 1 + 2 + 1 = 4 < 5, in contradiction to Theorem 3(a). □
Theorem 16.
There cannot exist an OS of the order n = 6.
Proof.
According to Theorem 4, m5 = 0,1. Let us examine these two possibilities.
According to Theorems 8 and 12, the only possible SS for the vertices having V = 2 are 3,4 and 4,4, so that m2 ≤ 2.
Let us show now that m4 ≠ 0. If m4 = 0, then m2 = 0 because none of the two possibilities discussed above for the vertices having V = 2 can exist. Hence, according to 3(a), m3 = 6. However, this is impossible due to Theorem 10, which prevents m3 vertices from being connected among themselves. Therefore, m4 ≠ 0.
Let us show now that m4 ≠ 1. If m4 = 1, then there is one possible SS for the vertices having V = 2, namely SS = 3,4, so that m2 = 1. According to Theorem 3(a), we obtain m3 = 6 − 1 − 1 = 4. This result is impossible since, according to Theorems 10 to 12, there are only two possible SSs for the vertices having V = 3: 2,3,4 and 3,3,4, so that m3 must be equal to 2 and not to 4. Hence, m4 ≠ 1.
Since m4 ≤ 3 (Theorem 6), let us consider the case in which m4 = 3. According to Theorem 5, the only possible SS for the vertices having V = 4 are 4,4,2,2; 4,4,3,2; and 4,4,3,3. However, these three possibilities cannot be realized since, in this case, the OS will include seven vertices (having valences equal to 2, 2, 3, 3, 4, 4, and 4) instead of 6. Therefore, m4 ≤ 2. Since we proved that m4 ≠ 0,1, there is only one possible value to m4, namely m4 = 2.
Let us show now that m2 ≠ 0. If m2 = 0, since m4 =2, then m3 = 4 (Theorem 3(a)). But this is impossible since, according to Theorem 10, there are only three possible SSs for the vertices having V = 3: 4,4,4; 3,4,4; and 3,3,4. Therefore, since m2 ≤ 2, we obtain m2 = 1,2.
We now show that m2 ≠ 1, so that m2 = 2
If m
2 = 1, then (since we found that m
4 = 2) m
3 = 6 − 2 − 1 = 3. The handshaking lemma is a consequence of the degree sum formula, according to which the sum of the degrees (the numbers of times each vertex is touched) equals twice the number of edges N in the graph. Specifically, this means that, in the apriorics n = 6 case, we have the following (Theorem 3(b)):
Since according to axiom d, m
1 = 0 and according to axiom a, m
0 = 0 this implies the following:
Now, this is in clear contradiction to ; thus, this case cannot occur.
So that m2 ≠ 1. Since we found that m2 ≤ 2 and m2 ≠ 0 we obtain m2 = 2.
We have then to find an OS of order 6 having the following multiplicities: m
5 = 0, m
4 = 2, m
2 = 2 and m
3 = 6 – 2 − 2 = 2. Let the vertices of this OS be denoted as follows: P
1(4), P
2(4), P
3(3), P
4(3), P
5(2), and P
6(2)—see
Figure 3-1c. According to Theorem 5 P
1(4) is connected to P
2(4). The possible SS values for these 2 vertices are, respectively: SS = 2,2,3,4, and SS = 2,3,3,4. Hence P
1(4) is connected to the 3 vertices—P
3(3), P
5(2) and P
6(2). And P
2(4) is connected to three vertices say P
6(2) and P
3(3), P
4(3).
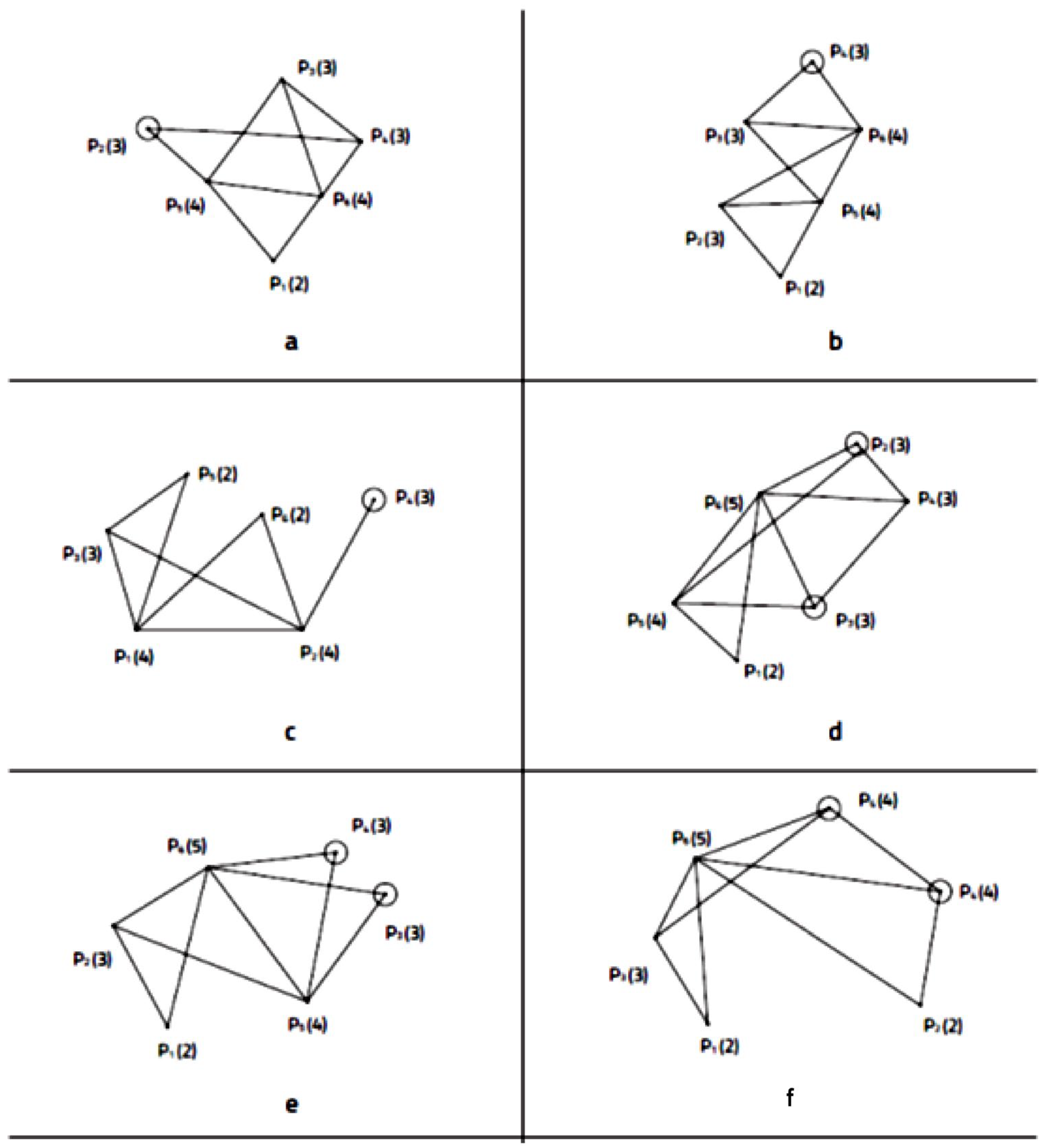
Now P5(2) and P6(2) cannot be connected according to theorem 8. Hence according to axiom d at least one of the vertices having V = 2, say P5(2), must be connected to P3(3) (The mediator between P5(2) and P1(4) must be one of the vertices already connected to P1(4) as all its connections are already allocated. It cannot be P6(2) due to Theorem 8 and it cannot be P2(4) which has only one V = 2 vertex in its SS structure and this is P6(2)). Since P2(4) is connected to P4(3) (circled in the figure), then according to axiom d they both have to be connected to their mediator, but this is impossible since the structure includes already six vertices and all the other vertices, except P4(3), are fully connected in accordance with their valence.
We see then that the attempt to design an OS satisfying the above-mentioned conditions (m2 = m3 = m4 = 2) results in contradiction.
In this case, m4 ≤ 2 (Theorem 7). Also, m2 ≤ 2 because the only possible SSs for the vertex having V = 2 are 5,4 and 5,3 (since these vertices must be connected to the vertex having V = 5, and according to Theorem 8, they cannot be connected to each other). Hence, if m4 = 0, then m2 = 1, and according to Theorem 3, m3 = 4. But this result is impossible since, according to Theorems 10 and 12, there are only two possible SSs for the vertices having V = 3; SS = 5,3,3; and SS = 5,3,2. Hence, m4 ≠ 0, so that m4 = 1,2.
Let us show now that m2 ≠ 0. Suppose that m2 = 0, since m4 ≤ 2 (Theorem 7) and m3 + m4 + 1 = 6 (Theorem 3) -> m3 = 5 − m4; then, m3 ≥3. The only possible SSs for the vertex having V = 3 are 5,3,3; 5,4,3; and 5,4,4. But the case where SS = 5,3,3 is impossible. To show this, let us try to form an OS satisfying this condition. Let V(P1) = 3 and SS(P1) = 5,3,3. Let P1 be connected to P2, P3, and P4, where V(P2) = 3, V(P3) = 3, and V(P4) = 5. P2 and P3 have to be connected to P4 (having V = 5). Since V(P2) = 3, and it is connected only to two vertices (P1 and P4), it has to be connected to an additional vertex, P5 (not to P3 because, in this case, SS(P3) = 5,3,3, the same as SS(P1)), and P5 has to be connected to P4. By the same token, P3 and P4 have to be connected to P6. Now, the only possible values of the V of P5 and P6 is 4 (since m2 = 0, and there are already three vertices having V = 3 and one vertex having V = 5). Therefore, SS(P2) = SS(P3) = 3,4,5. Hence, P2 = P3, in contradiction to axiom e.
We are left then with the following four possibilities: m
2 = 1,2 and m
4 = 1,2. For each of these cases, m
3 = 5 − m
2 − m
4, as
It follows for
that
Thus,
. The remaining cases are given in
Table 7.
We subsequently show that the attempt to design an OS satisfying the conditions of each row in this table always results in the contradiction of one of the axioms, a to e. Pay attention to the fact that, in all the cases discussed below, all the vertices have to be connected to P6(5).
Let us begin with the first row of
Table 7, in which m
2 = 1, m
3 = 3, m
4 = 1, and m
5 = 1. Let us denote the vertices of the possible OS by P
1(2), P
2(3), P
3(3), P
4(3), P
5(4), and P
6(5). (The numbers in parentheses are the valences of the vertices). The possible SSs of P
1(2) can be either SS = 4,5 or SS = 3,5. Let us discuss each of these cases separately.
In this case (see
Figure 5d), P
1(2) is connected to P
5(4) and P
6(5). Then, P
5(4) is connected to P
2(3), P
3(3), and P
6(5). Now, P
2(3) and P
3(3) have two connections (to P
5(4) and P
6(5)) instead of three, and the only available connection is to a vertex having V = 3. But such connections will yield that the SS of these vertices (circled in the figure) will be SS = 3,4,5, so that these two vertices will be equal, in contradiction to axiom e.
In this case (see
Figure 5e), P
1(2) is connected to P
2(3) and P
6(5). Then, P
5(4) is connected to P
2(3), P
3(3), P
4(3), and P
6(5). (As noted earlier, all the vertices have to be connected to P
6(5).) As a result, all the vertices are fully connected in accordance with their V, except the vertices having V = 3. P
3(3) and P
4(3) are circled in the figure. They each have only two connections instead of three. Trying to form a connection between these vertices will result in making them equal (they will both have SS = 3,4,5), in contradiction to axiom e.
The analysis of these two cases shows that it is impossible to design an OS satisfying the conditions of the first row of
Table 7.
Let us examine now the second row in which m
2 = 2, m
3 = 1, m
4 = 2, and m
5 = 1. Let us denote the vertices of the possible OS by P
1(2), P
2(2), P
3(3), P
4(4), P
5(4), and P
6(5)—see
Figure 5f. The possible SSs of P
1(2) and P
2(2) are, respectively, SS = 3,5, and SS = 4,5 since, as was indicated previously, they cannot be connected to each other. Hence, P
1(2) has to be connected to P
3(3) and P
6(5), and P
2(2) has to be connected to P
4(4) and P
6(5). At this stage, P
5(4) has only two connections (to P
6(5) and to P
4(4)), and it cannot be connected to P
1(2) and P
2(2), which do not have any more available connections. Therefore, only P
3(3) is available for connection. Hence, P
5(4) and P
4(4) (circled in the figure) each have only three connections instead of four. Hence, it is impossible to design an OS satisfying the conditions of the fourth row. □
Remark 1.
We described two OSs of order 7 in Section 2—O1(7) and O2(7)—satisfying the axioms of apriorics. There may be other OSs of order 7. The enumeration of all the OSs of order 7 and of higher orders is still an open problem in apriorics.