Abstract
The traditional SIRS virus propagation model is used to analyze the malware propagation behavior of wireless rechargeable sensor networks (WRSNs) by adding a new concept: the low-energy status nodes. The SIRS-L model has been developed in this article. Furthermore, the influence of time delay during the charging behavior of the low-energy status nodes needs to be considered. Hopf bifurcation is studied by discussing the time delay that is chosen as the bifurcation parameter. Finally, the properties of the Hopf bifurcation are explored by applying the normal form theory and the center manifold theorem.
1. Introduction
With the development and application of communication technology and sensor technology, wireless sensor networks (WSNs) have come into being. WSNs are widely used globally, such as in the military industry, agricultural production, ecological monitoring, disaster warning, and infrastructure status monitoring [1]. Due to the self-organized network of WSNs, sensor nodes are vulnerable to various attacks in the process of information transmission [2,3,4,5,6,7,8,9,10]. Thus, it is of practical significance to prevent and deal with malicious attacks in WSNs.
The characteristics of WSNs can be listed as follows: adapting wireless communication, the topology being able to be changed dynamically, the security mechanism being imperfect, and the energy of nodes being limited, etc. Thus, the security of wireless sensor networks is facing great challenges. The attacks against sensor network nodes can be roughly divided into the following types: network worms, bots, and Trojans, among others [11,12,13,14]. Most malware attacks in WSNs mainly aim at paralyzing them or losing their power. In order to overcome the defect of short life cycle of WSNs, wireless rechargeable sensor networks (WRSNs) have been developed and have caught more attention. Consequently, a relatively special attack has appeared to against the nodes’ power, namely, the denial of charge (DOC) [15]. The prevention and control of malware spread in WRSNs have become a hot issue.
The propagation mechanism of malware is similar to that of viruses in biological groups. Many scholars have made great contributions to malware propagation dynamics. In the beginning, the spread of malware mainly focuses on the traditional Internet. For example, Zou et al. put forward the worm propagation models represented by SI (susceptible–infected), SIS (susceptible–infected–susceptible), and SIR (susceptible–infected–recovered) [16,17,18,19]. These studies lay a foundation for the later studies on the propagation behavior of malware in WSNs. However, it is worth noting that there are some differences between WSNs and the traditional Internet: (1) Because of their topological structure, the communication range of WSNs has physical limitations. (2) The limited energy characteristics lead to uneven communication capabilities. (3) The link-layer access conflict and avoidance mechanism of WSNs sharing wireless channel also introduces space-time correlation for the propagation dynamics of WSNs. (4) WSNs have a high degree of self-organization. Therefore, it is of great significance to study the malware propagation model in WSNs, which has been proposed in recent years. For example, Tanachaiwiwat began to study the propagation behavior of network worms in 2009 [20]. Khayam et al. used signal processing technology to study the propagation model of worms in 2006 [21]. Furthermore, the SEIR (susceptible–exposed–infected–recovered) model is adapted to study the spread of malware [22], while the SEIRS-V (susceptible–exposed–infected–recovered–susceptible and vaccinated) model explores the application of Hopf bifurcation during the malware spreading [23,24]. With the development, the research on WRSNs was pushed forward recently [25,26,27,28,29,30,31], considering the new concept of L (low-energy status) nodes. It is worth noting that the transition from the low-energy status nodes to the normal status nodes is called charging. At present, there are many charging methods for WRSNs, such as unmanned aerial vehicle (UAV) charging [32].
The related techniques and modeling basis of this paper mainly refer to the papers in Table 1:

Table 1.
Related research on the modeling and analysis of this paper.
In order to promote the study of virus dynamics in WRSNs, the modeling in this paper is mainly based on the SIRS (susceptible–infected–recovered–susceptible) infectious disease model. Combined with the charging delay in WRSNs, the bifurcation in the process of charging needs to be considered. Therefore, the general contributions of this paper are as follows:
- Establishing the SIRS-L (susceptible–infected–recovered–susceptible–low-energy) model.
- The equilibrium solutions of the SIRS-L model are obtained, and the basic reproductive number R0 is defined through the regeneration matrix [34].
- Revealing of the stability of the SIRS-L model when the charging delay is ignored.
- The variation of the solutions of the characteristic equation are discussed if the charging delay is considered through the theory in [35], and the occurrence conditions of Hopf bifurcation are figured out.
- The properties of the Hopf bifurcation are explored by applying the normal form theory and the center manifold theorem [36].
The content of this paper is organized as follows: In Section 2, we establish the SIRS-L (susceptible–infected–recovered–susceptible–low-energy) model combined with the concept of low-energy nodes and the charging delay; in Section 3, the equilibrium points analysis and the corresponding Hopf bifurcation conditions are presented; the properties of the Hopf bifurcation are given in Section 4; the simulation analysis are revealed in Section 5; the conclusions are given in Section 6.
2. Modeling
On the basis of the classical SIRS model, we obtained the SIRS-L model as follows (1), with the parameters being explained in Table 2:

Table 2.
Interpretation of the model parameters.
The following formula is obtained through the injection rate and the deactivation rate: . Therefore, we can obtain if the total number of nodes is stable. In order to make the analysis more clearer, the system (1) is simplified as follows (2) with the meaning , where and . Thus, represents the proportion of nodes in the system (1).
3. Local Stability and Analysis of Hopf Bifurcation
The disease-free solution and endemic solution of the system (2) can be obtained as follows:
where .
The basic reproductive number R0 is obtained through the next generation matrix method [34].
Set:
and
Thus,
It can be found that if , the model (2) has the unique endemic solution . By linearization technique, the characteristic matrix of system (2) about can be obtained as follows.
where
The characteristic equation of the model (2) at is shown as:
The detailed representations of are given in Appendix A.
Firstly, we study the local stability of system (2) at when .
If , Equation (8) can be rebuilt as:
where
The following formulas can be obtained:
If hypothesis (H1) , , , , , and , in Equation (10) holds, and all the characteristic solutions of Equation (9) are negative. Thus, is locally asymptotically stable under the theory of the Hurwitz criterion.
Then, we begin to consider the change of the characteristic solutions of Equation (9) when the charging time delay is introduced.
If , multiplying on both sides of Equation (8), we can obtain the following equation:
Referring to the processing method of the paper [35], let = iω (ω > 0) be the root of Equation (11). After separating the imaginary and real parts, we obtain
where
Squaring and adding the two Equations in Equation (12), we obtain
Because of , the following two cases are discussed:
Case 1: If , Equation (13) could be represented as follows:
Equation (14) can be calculated as follows:
where
Let and the following equation can be obtained:
and
Set
where
The following solutions can be calculated:
where
Then, the expression of can be obtained as combined with Equation (13), we can obtain A function concerning ω can be obtained by
Thus, (H2) Equation (20) has finite positive roots (). The corresponding time delay can be obtained as follows:
Case 2: If , Equation (13) could be represented as follows:
Similar to Case 1, a function concerning ω can be obtained by
Thus, (H3) Equation (23) has finite positive roots (). The corresponding time delay can be obtained as follows:
Let
Then, if Equation (13) has a pair of purely imaginary roots Next, the conditions for bifurcation are obtained in the following analysis. From Equation (11), we obtain
with
Thus,
where
If the hypothesis (H4) holds, the following Theorem 1 can be obtained by the Hopf bifurcation theorem [36].
Theorem 1.
If (H1)–(H4) hold, the endemic solution of the model (2) is locally asymptotically stable for, and the model (2) undergoes a Hopf bifurcation at the endemic solutionif.
4. Properties of the Hopf bifurcation
The properties of the Hopf bifurcation are explored in this section by applying the normal form theory and the center manifold theorem [36]. Let . The transformations are given as Thus, the model (2) can be written as:
where and
where
and
According to the application of Riesz representation theorem, there exists a 6 × 6 matrix function such as:
The following equation is chosen:
with is the Dirac delta function.
For the following equations are defined
and
The model (28) is equivalent to
is defined as
with a bilinear form
where
The eigenvector of is shown as and the eigenvector of is shown as . Then the following results can be obtained:
and
We obtain Equation (38) from Equation (35):
Equation (39) is chosen as:
with .
Following the computation introduced in [36], we obtain
with
and
where
Thus, the following values can be obtained:
Theorem 2 is given as:
Theorem 2.
For the model (2), if(), the Hopf bifurcation is supercritical (subcritical). If(), the bifurcating periodic solutions are stable (unstable). If(), the bifurcating periodic solutions increase (decrease).
5. Simulation
5.1. Parameter Dependence of
In this section, prevention methods are analyzed in system (2).
The basic reproduction number is generally used to describe the infectivity of virus. Therefore, it is also applicable to the spread of malware in WRSNs. On the assumption that the system is stable, if , malware will be cleared eventually. If , malware will always exist.
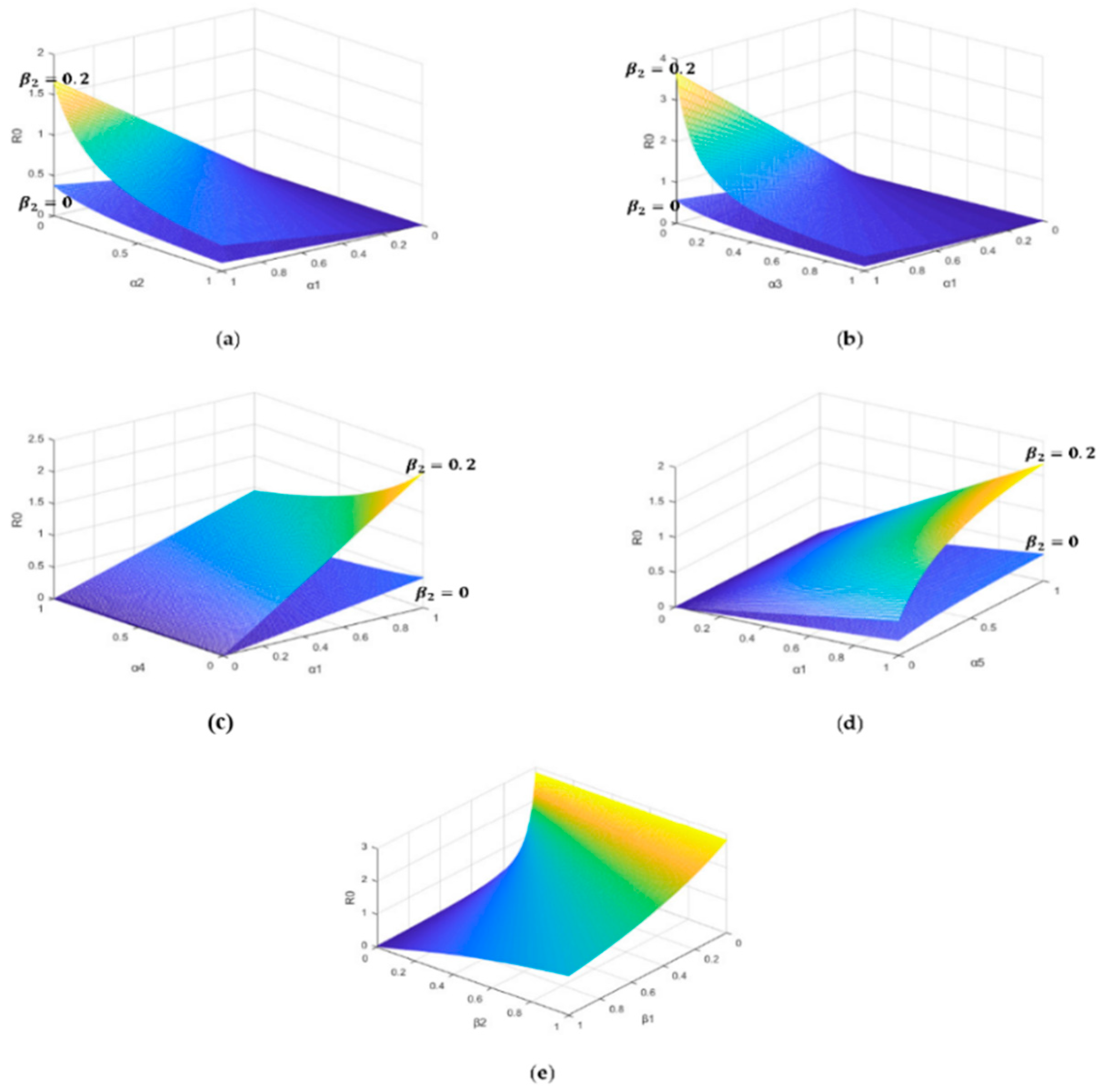
The size of is affected by different parameters. What is worth concerning about is the influence of the parameter () on the malware spread under different diffusion rates . Here, we first assume that only one parameter () and are changed while the other parameters are unchanged. We observe the spread of malware in the system.
- (1)
- The parameters are as follows in Figure 1a: Figure 1a shows that with the increase of the diffusion rate , the malware is more easier prevailing. However, the self-healing rate of the infected nodes has a inhibitory effect on the spread of malware. Figure 1a also shows that the charging behavior makes the spread of malware easier.
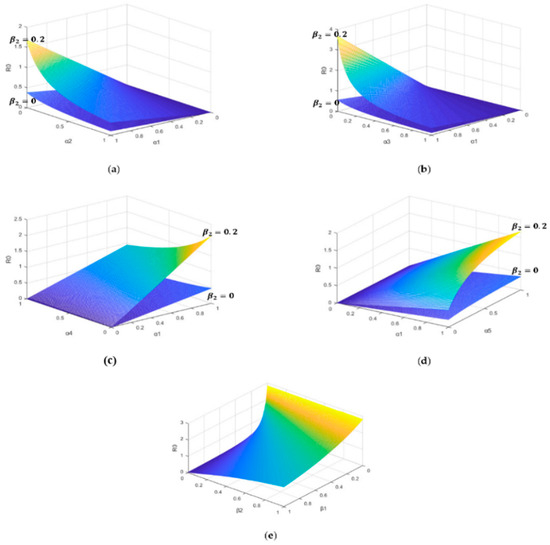 Figure 1. Mutual influence of parameters. (a) The relationships between and (b) The relationships between and . (c) The relationships between and . (d) The relationships between and . (e) The relationships between and .
Figure 1. Mutual influence of parameters. (a) The relationships between and (b) The relationships between and . (c) The relationships between and . (d) The relationships between and . (e) The relationships between and . - (2)
- The parameters are as follows in Figure 1b: Figure 1b shows that with the increase of the recovery rate of the infected nodes , the spread of malware can be effectively suppressed, which will provide us with the reference value in the control of malware. Similarly, Figure 1b also shows that without the charging behavior (), the control of malware will become easier.
- (3)
- (4)
- Figure 1a–d together reflect that the charging behavior will encourage the spread of malware, which will provide us with the data reference for the control of the malware spread in the SIRS-L model.
Next, the influence on the malware spread under different low-energy-node conversion rate and charging success rate are also discussed.
- (5)
- The parameter settings are as follows in Figure 1e: . Figure 1e reflects the influence of the low-energy node conversion rate and the charging success rate on malware propagation. It is shown that if the low-energy node conversion rate is less than 0.2, the increase of the charging success rate can easily lead to the prevalence of malware. On the other side, if the low-energy node conversion rate is larger than 0.4, we can appropriately reduce the charging success rate to suppress the spread of malware.
5.2. Analysis and Display of Equilibrium Solutions
In this section, the distribution of nodes’ states under different parameters of and are discussed to verify the stability of the system and to discuss the bifurcation.
- (1)
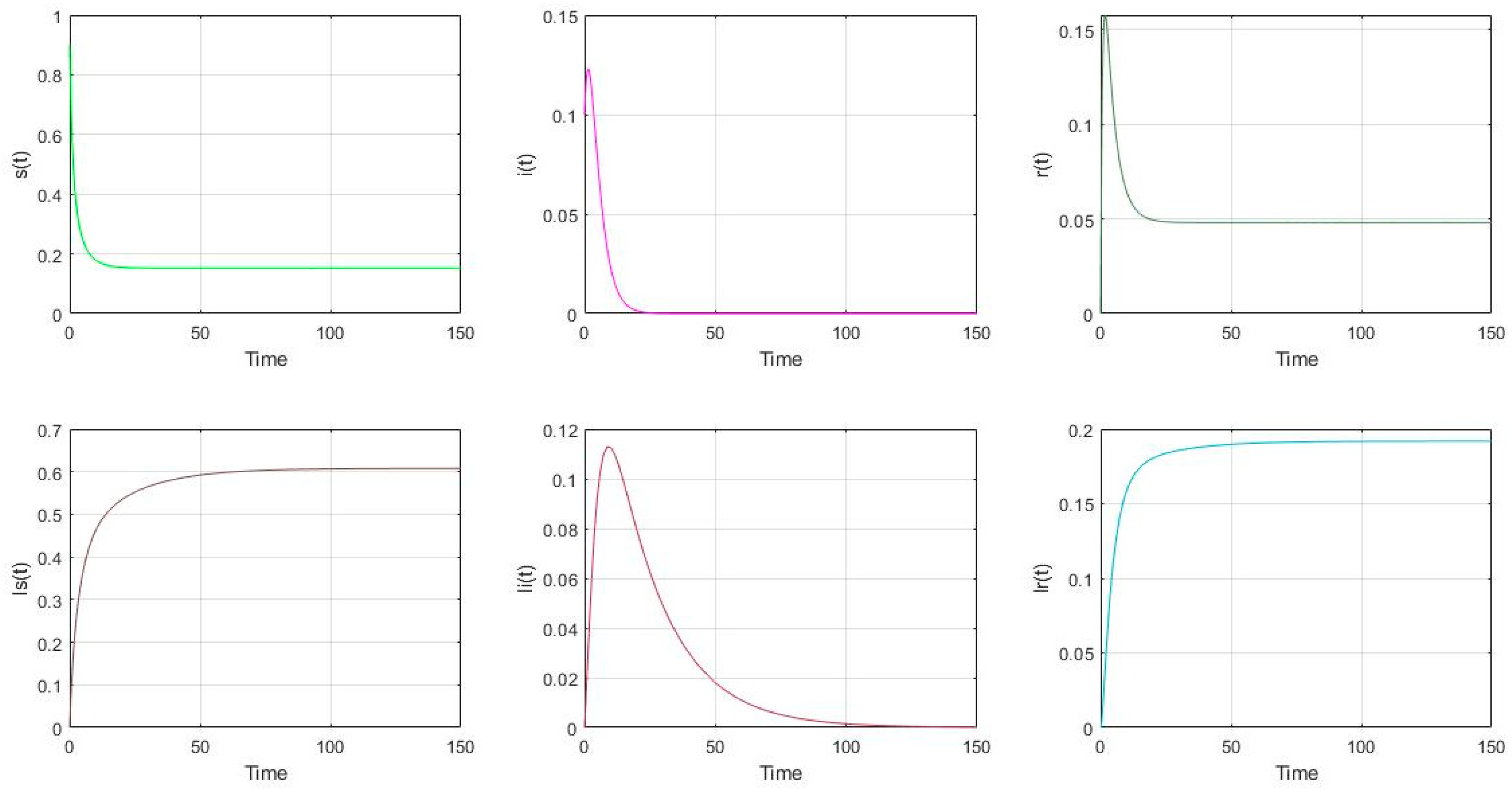
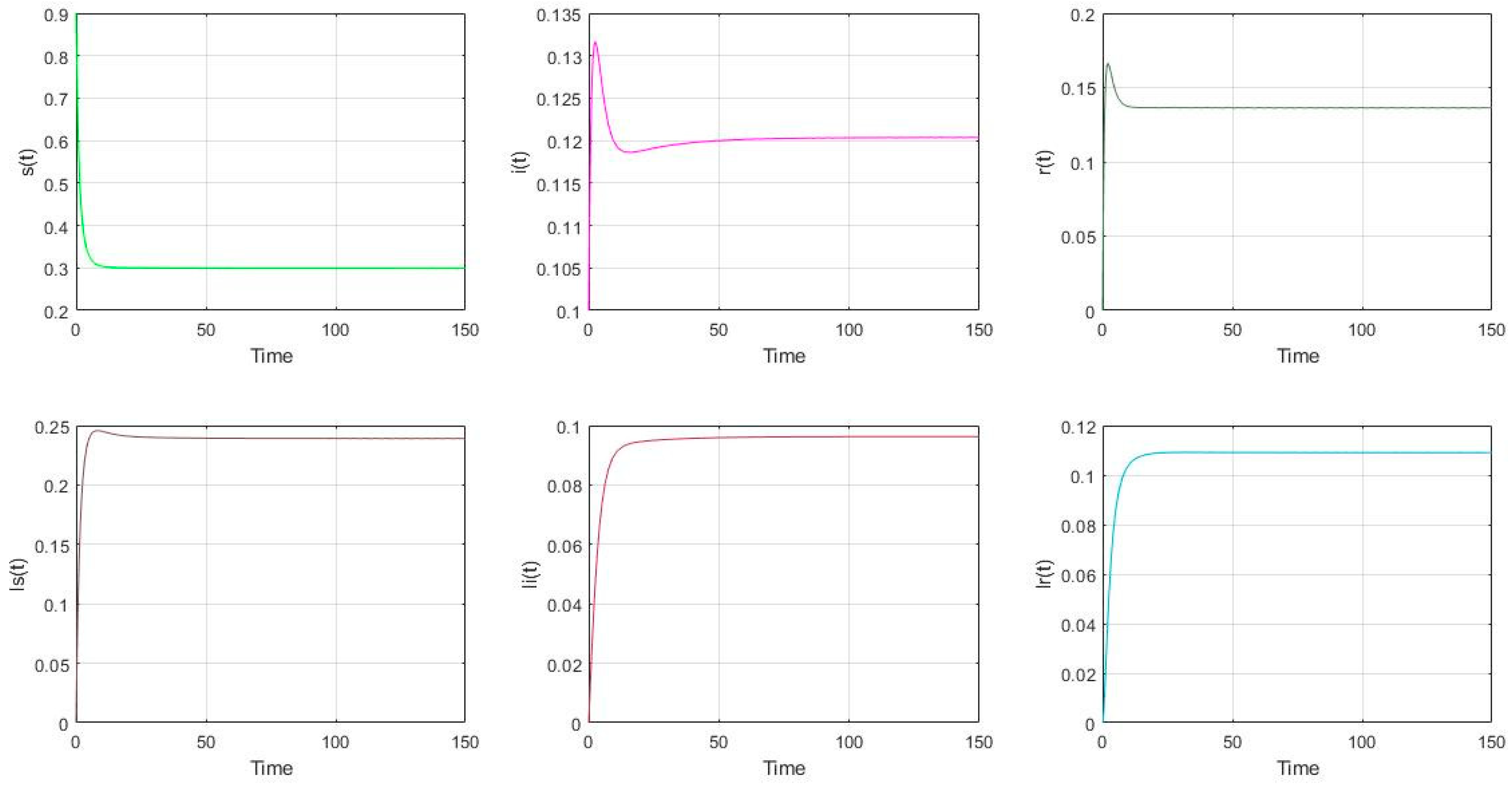
- The parameter settings are as follows in Figure 2: with the initial value of nodes’ scale: (s(0), i(0), r(0), ls(0), li(0), lr(0))= (0.9, 0.1, 0, 0, 0, 0). It is shown that (s(∞), i(∞), r(∞), ls(∞), li(∞), lr(∞)) = (0.1520, 0, 0.0480, 0.6079, 0, 0.1920). It is shown that if the malware appears in the model (2), it will gradually disappear if . It also can be shown that if , the total proportion of the low-energy nodes (ls, li, lr) is larger than that of the general nodes (s, i, r).
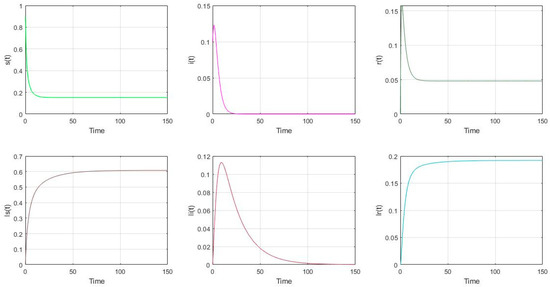 Figure 2. The distribution of nodes if and .
Figure 2. The distribution of nodes if and . - (2)
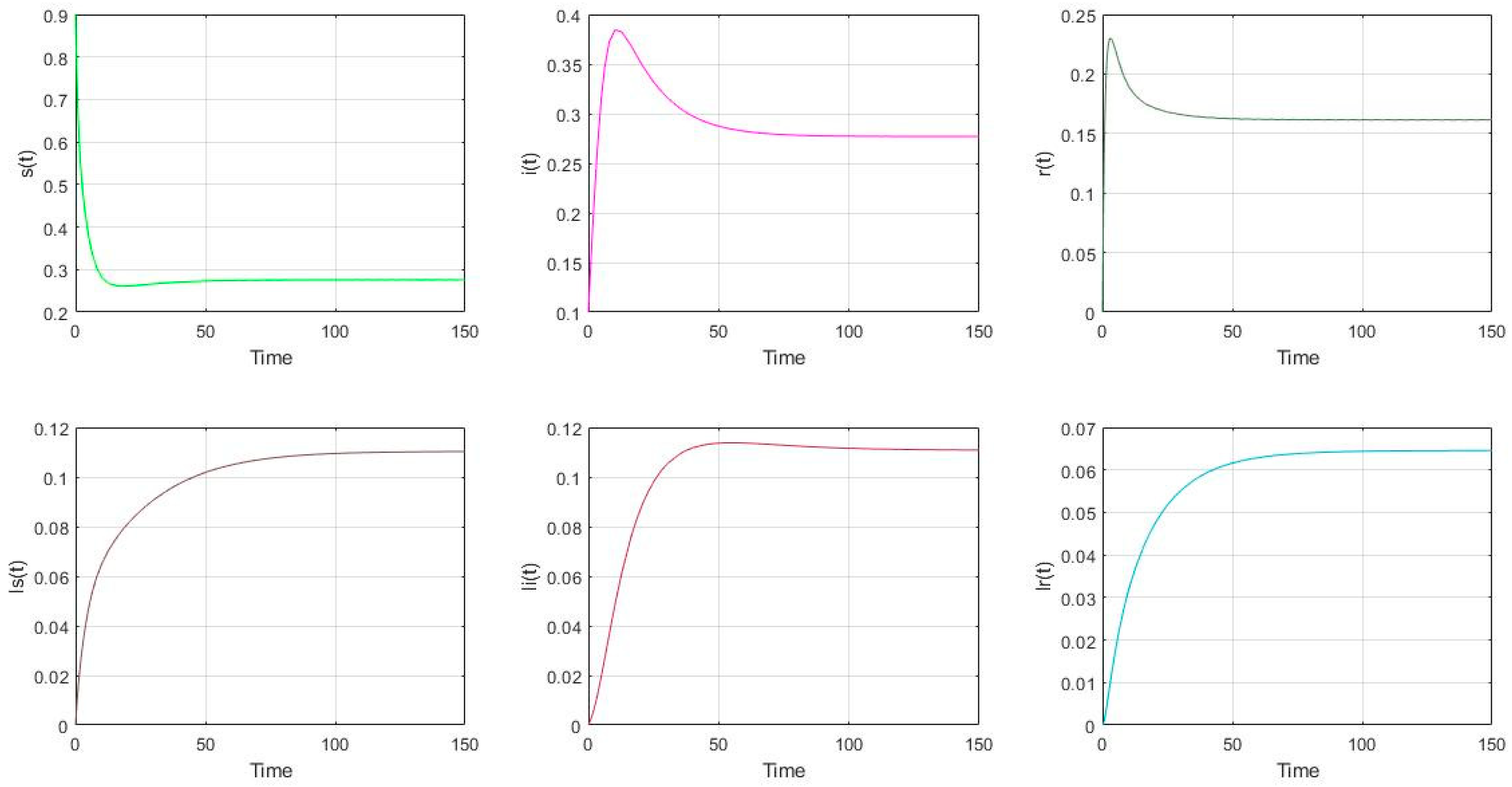
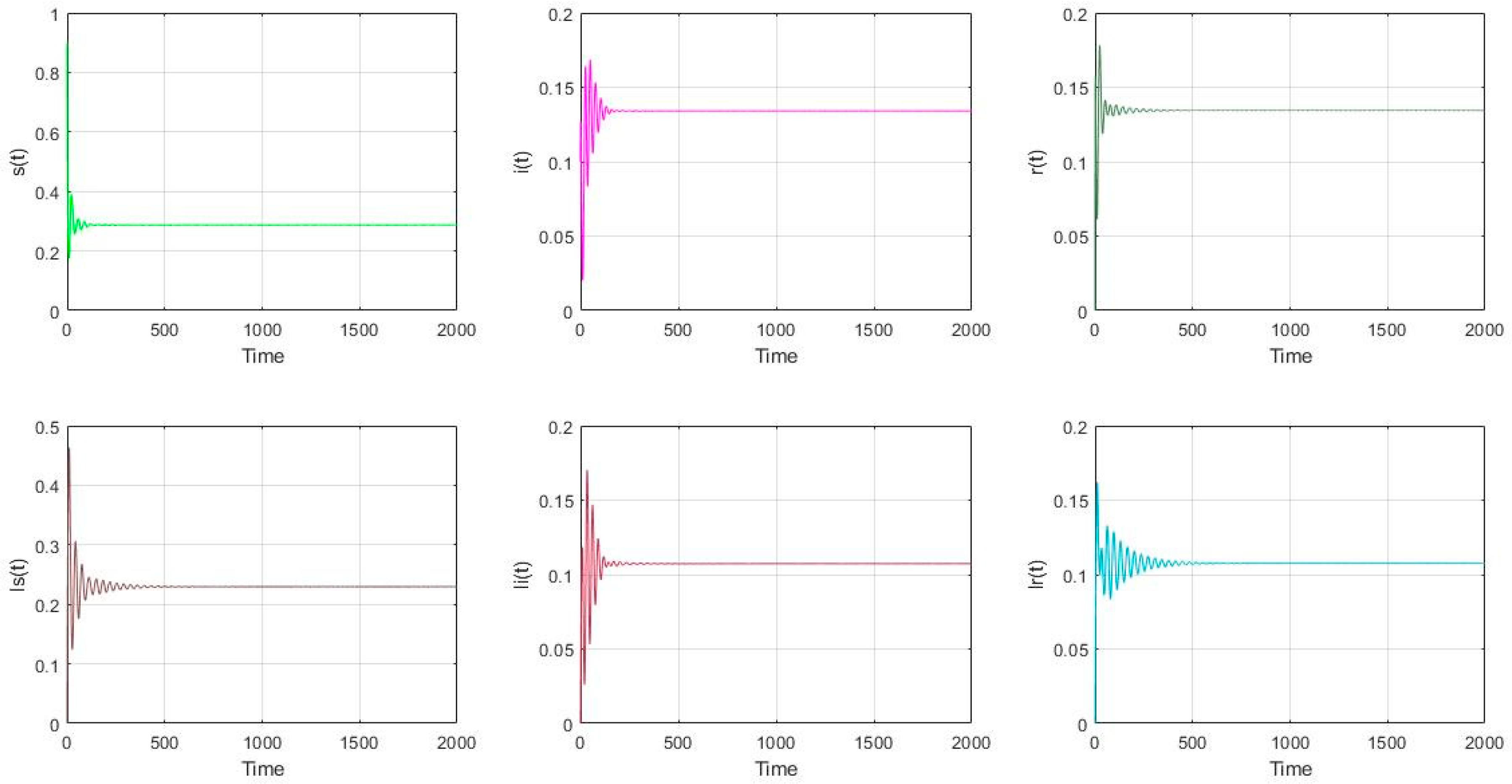
- The parameter settings are as follows in Figure 3: , with the initial value of nodes’ scale: (s(0), i(0), r(0), ls(0), li(0), lr(0))= (0.9, 0.1, 0, 0, 0, 0). It is shown that (s(∞), i(∞), r(∞), ls(∞), li(∞), lr(∞)) = (0.2756, 0.2770, 0.1616, 0.1103, 0.1109, 0.0646). It shows that the malware will prevail if .
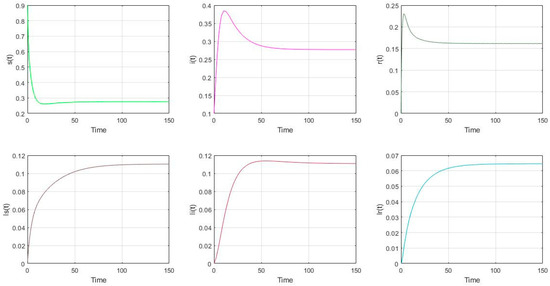 Figure 3. The distribution of nodes if and .
Figure 3. The distribution of nodes if and . - (3)
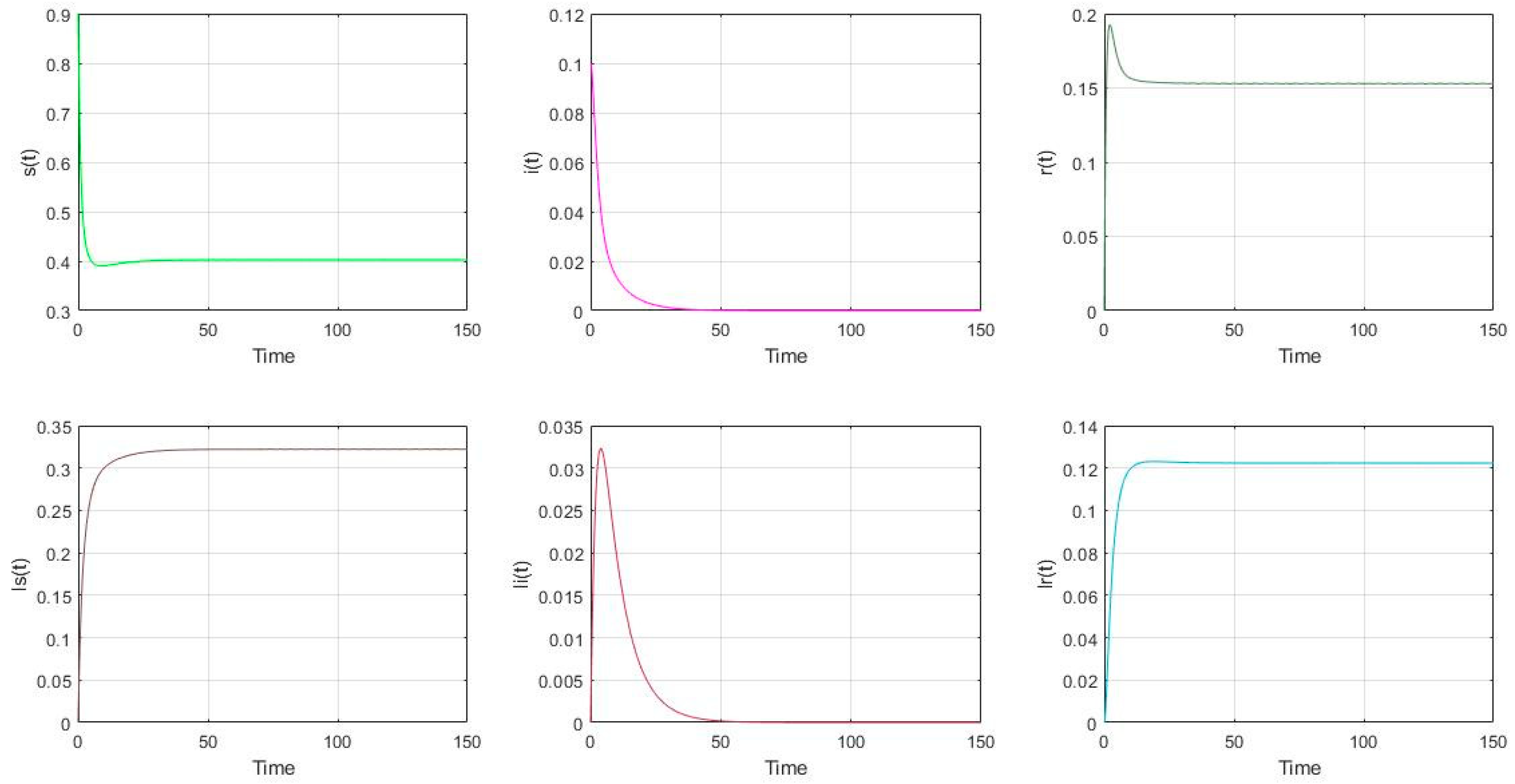
- The parameter settings are as follows in Figure 4: , with the initial value of nodes’ scale: (s(0), i(0), r(0), ls(0), li(0), lr(0))= (0.9, 0.1, 0, 0, 0, 0). It is shown that (s(∞), i(∞), r(∞), ls(∞), li(∞), lr(∞)) = (0.4027, 0, 0.1529, 0.3221, 0, 0.1223). It shows that if the malware appears in the model (2), it will gradually disappear if . It also can be shown that if , the total proportion of the low-energy nodes (ls, li, lr) is smaller than the proportion of the low-energy nodes in Figure 2 if the charging operation is not performed .
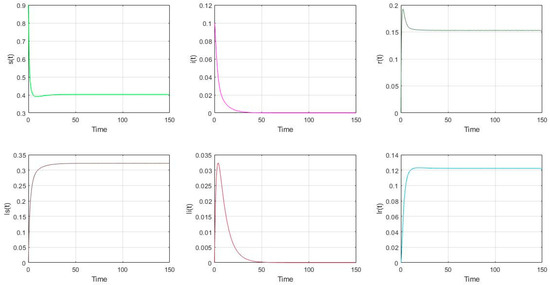 Figure 4. The distribution of nodes if and .
Figure 4. The distribution of nodes if and . - (4)
- The parameter settings are as follows in Figure 5: , with the initial value of nodes’ scale: (s(0), i(0), r(0), ls(0), li(0), lr(0)) = (0.9, 0.1, 0, 0, 0, 0). It is shown that (s(∞), i(∞), r(∞), ls(∞), li(∞), lr(∞)) = (0.2988, 0.1204, 0.1364, 0.2391, 0.0963, 0.1091). It shows that the malware will prevail if . Similarly, it also can be shown that if , the total proportion of the low-energy nodes (ls, li, lr) is smaller than the proportion of the low-energy nodes in Figure 2 if the charging operation is not performed . The total proportion of the low-energy nodes is similar to the corresponding proportion in Figure 4, which represents the proportion of low-energy nodes is only related to and .
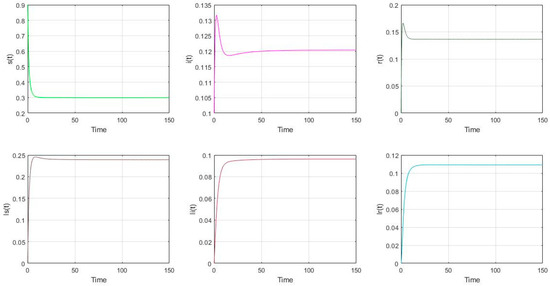 Figure 5. The distribution of nodes if and .
Figure 5. The distribution of nodes if and .
The above results (1)–(4) can be summarized as follows: the system is locally stable on the premise that the parameters meet the hypothesis (H1). In addition, if , the malicious software will persist in the system, while if , the malicious software will be finally cleared. Next, we verify the bifurcation of the system.
- (5)
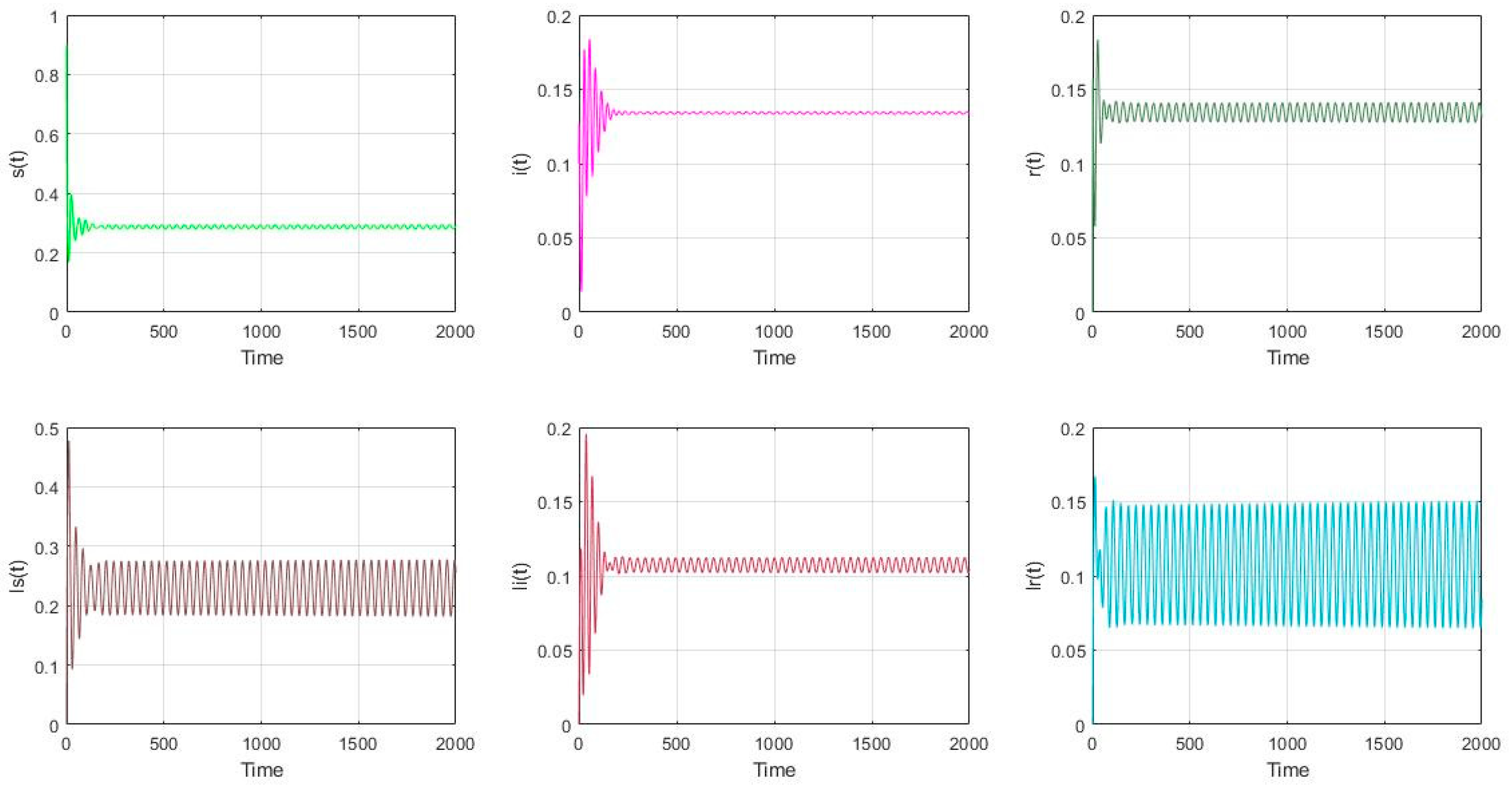
- The parameter settings are as follows in Figure 6 and Figure 7: , with the initial value of nodes’ scale: (s(0), i(0), r(0), ls(0), li(0), lr(0)) = (0.9, 0.1, 0, 0, 0, 0). It can be calculated that and . In Figure 6, it can be seen that the model (2) is asymptotically stable if . What’s more, in Figure 7, the model (2) undergoes a Hopf bifurcation if . According to Equation (41) and Theorem 2, the following parameters can be obtained: The result can be concluded that the Hopf bifurcation is supercritical, the bifurcating periodic solutions are stable and the period of the periodic solutions decreases.
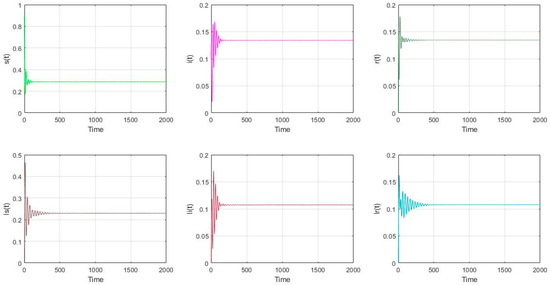 Figure 6. The distribution of nodes if and .
Figure 6. The distribution of nodes if and .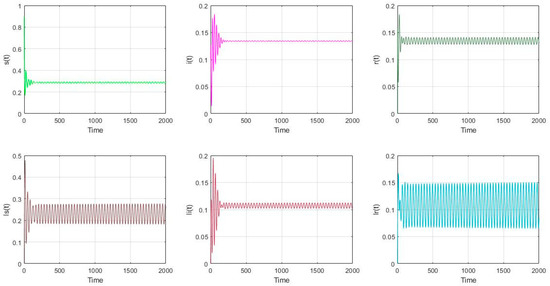 Figure 7. The distribution of nodes if and .
Figure 7. The distribution of nodes if and .
6. Conclusions
This article puts forward a novel SISR-L model that considers the low-energy status nodes. Combined with the reality, the charging delay is introduced in the model to study the bifurcation. We have proved that the system is locally stable under certain conditions. In addition, the influence of different parameters on the spread of malware is displayed in the simulation. It is worth noting that in the SISR-L system, the charging behavior will make it more difficult to control the spread of malware. On the analysis of bifurcation, we reveal that the SISR-L model is locally asymptotically stable if the charging delay is less than , and the model undergoes a Hopf bifurcation at the endemic solution if the charging delay is larger than . Finally, the properties of Hopf bifurcation were explored through applying the normal form method and the center manifold theorem. All the analyses can provide theoretical reference for the control of malware propagation in the SISR-L model.
Author Contributions
Conceptualization, G.L., J.L. and Z.P.; methodology, G.L. and J.L.; software, G.L. and J.L.; validation, G.L. and J.L.; formal analysis, G.L. and J.L.; investigation, G.L., J.L. and Z.L.; writing—original draft preparation, J.L.; writing—review and editing, G.L., J.L. and Z.L. All authors have read and agreed to the published version of the manuscript.
Funding
The authors acknowledge funding received from the following science foundations: the National Natural Science Foundation of China (61403089, 51975136, 52075109); the 2020 Department of Education of Guangdong Province Innovative and Strong School Project (Natural Sciences)—Young Innovators Project (Natural Sciences) under grant 2020KQNCX054; the National Key Research and Development Program of China (2018YFB2000501); the Science and Technology Innovative Research Team Program in Higher Educational Universities of Guangdong Province (2017KCXTD025); the Innovative Academic Team Project of Guangzhou Education System (1201610013); the Special Research Projects in the Key Fields of Guangdong Higher Educational Universities (2019KZDZX1009); the Science and Technology Research Project of Guangdong Province (2017A010102014, 2016A010102022); and the Science and Technology Research Project of Guangzhou (201707010293). They are all appreciated for supporting this work.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
No conflict of interest.
Appendix A
References
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Oliviero, F.; Romano, S.P. A reputation-based metric for secure routing in wireless mesh networks. In Proceedings of the IEEE GLOBECOM 2008–2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar]
- Rehman, A.U.; Rehman, S.U.; Raheem, H. Sinkhole attacks in wireless sensor networks: A survey. Wirel. Pers. Commun. 2019, 106, 2291–2313. [Google Scholar] [CrossRef]
- Alajmi, N. Wireless sensor networks attacks and solutions. arXiv 2014, arXiv:1407.6290. [Google Scholar]
- Ngai, E.C.; Liu, J.; Lyu, M.R. On the intruder detection for sinkhole attack in wireless sensor networks. In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; Volume 8, pp. 3383–3389. [Google Scholar]
- Hu, Y.C.; Perrig, A.; Johnson, D.B. Packet leashes: A defense against wormhole attacks in wireless networks. In Proceedings of the IEEE INFOCOM 2003. Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No. 03CH37428), San Francisco, CA, USA, 30 March–3 April 2003; Volume 3, pp. 1976–1986. [Google Scholar]
- Yu, B.; Xiao, B. Detecting selective forwarding attacks in wireless sensor networks. In Proceedings of the 20th IEEE International Parallel & Distributed Processing Symposium, Rhodes Island, Greece, 25–29 April 2006; p. 8. [Google Scholar]
- Salehi, S.A.; Razzaque, M.A.; Naraei, P.; Farrokhtala, A. Detection of sinkhole attack in wireless sensor networks. In Proceedings of the 2013 IEEE International Conference on Space Science and Communication (IconSpace), Melaka, Malaysia, 1–3 July 2013; pp. 361–365. [Google Scholar]
- Sundararajan, R.K.; Arumugam, U. Intrusion detection algorithm for mitigating sinkhole attack on LEACH protocol in wireless sensor networks. J. Sens. 2015, 2015. [Google Scholar] [CrossRef]
- Chen, C.; Song, M.; Hsieh, G. Intrusion detection of sinkhole attacks in large-scale wireless sensor networks. In Proceedings of the 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, Beijing, China, 25–27 June 2010; pp. 711–716. [Google Scholar]
- Liang, C.J.M.; Musăloiu-e, R.; Terzis, A. Typhoon: A Reliable Data Dissemination Protocol for Wireless Sensor Networks. In European Conference on Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2008; pp. 268–285. [Google Scholar]
- Song, Y.; Jiang, G.P. Model and Dynamic Behavior of Malware Propagation over Wireless Sensor Networks. In International Conference on Complex Sciences; Springer: Berlin/Heidelberg, Germany, 2009; pp. 487–502. [Google Scholar]
- Yetgin, H.; Cheung, K.T.K.; El-Hajjar, M.; Hanzo, L.H. A Survey of Network Lifetime Maximization Techniques in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2017, 19, 828–854. [Google Scholar] [CrossRef]
- Rasheed, A.; Mahapatra, R.N. The Three-Tier Security Scheme in Wireless Sensor Networks with Mobile Sinks. IEEE Trans. Parallel Distrib. Syst. 2010, 23, 958–965. [Google Scholar] [CrossRef]
- Lin, C.; Shang, Z.; Du, W.; Ren, J.K.; Wang, L.; Wu, G.W. CoDoC: A Novel Attack for Wireless Rechargeable Sensor Networks through Denial of Charge. In Proceedings of the IEEE INFOCOM, Paris, France, 29 April–2 May 2019. [Google Scholar]
- Desmedt, Y.; Frankel, Y. Shared generation of authenticators and signatures. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1991; pp. 457–469. [Google Scholar]
- Weidong, C.; Dengguo, F. A group of threshold group-signature schemes with privilege subsets. In Progress on Cryptography; Springer: Boston, MA, USA, 2004; pp. 81–88. [Google Scholar]
- Yi, S.; Dengguo, F. The Design and analysis of a new group of (tj, t, n) threshold group signature scheme. China Crypto. 2000. Available online: https://en.cnki.com.cn/Article_en/CJFDTotal-ZKYB200102002.htm (accessed on 20 July 2021).
- Wang, X.; Dong, Y. Threshold group signature scheme with privilege subjects based on ECC. In Proceedings of the 2010 International Conference on Communications and Intelligence Information Security, Nanning, China, 13–14 October 2010; pp. 84–87. [Google Scholar]
- Tanachaiwiwat, S.; Helmy, A. Encounter-based worms: Analysis and defense. Ad Hoc Netw. 2009, 7, 1414–1430. [Google Scholar] [CrossRef]
- Khayam, S.A.; Radha, H. Using signal processing techniques to model worm propagation over wireless sensor networks. IEEE Signal Process. Mag. 2006, 23, 164–169. [Google Scholar] [CrossRef]
- Batista, F.K.; Martin del Rey, A.; Queiruga-Dios, A. A new individual-based model to simulate malware propagation in wireless sensor networks. Mathematics 2020, 8, 410. [Google Scholar] [CrossRef]
- Zhang, Z.; Si, F. Dynamics of a delayed SEIRS-V model on the transmission of worms in a wireless sensor network. Adv. Differ. Equ. 2014, 2014, 1–15. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, Y. Bifurcation Analysis for an SEIRS-V Model with Delays on the Transmission of Worms in a Wireless Sensor Network. Math. Probl. Eng. 2017, 2017. [Google Scholar] [CrossRef]
- Liu, G.; Peng, B.; Zhong, X. A Novel Epidemic Model for Wireless Rechargeable Sensor Network Security. Sensors 2021, 21, 123. [Google Scholar] [CrossRef]
- Liu, G.; Peng, B.; Zhong, X. Epidemic Analysis of Wireless Rechargeable Sensor Networks Based on an Attack–Defense Game Model. Sensors 2021, 21, 594. [Google Scholar] [CrossRef]
- Liu, G.; Peng, B.; Zhong, X.; Cheng, L.; Li, Z. Attack-Defense Game between Malicious Programs and Energy-Harvesting Wireless Sensor Networks Based on Epidemic Modeling. Complexity 2020, 2020, 1–19. [Google Scholar] [CrossRef]
- Liu, G.; Peng, B.; Zhong, X.; Lan, X. Differential Games of Rechargeable Wireless Sensor Networks against Malicious Programs Based on SILRD Propagation Model. Complexity 2020, 2020, 13. [Google Scholar] [CrossRef]
- Liu, G.; Li, J.; Liang, Z.; Peng, Z. Analysis of Time-Delay Epidemic Model in Rechargeable Wireless Sensor Networks. Mathematics 2021, 9, 978. [Google Scholar] [CrossRef]
- Liu, G.; Peng, Z.; Liang, Z.; Li, J.; Cheng, L. Dynamics Analysis of a Wireless Rechargeable Sensor Network for Virus Mutation Spreading. Entropy 2021, 23, 572. [Google Scholar] [CrossRef]
- Liu, G.; Huang, Z.; Wu, X.; Liang, Z.; Hong, F.; Su, X. Modelling and Analysis of the Epidemic Model under Pulse Charging in Wireless Rechargeable Sensor Networks. Entropy 2021, 23, 927. [Google Scholar] [CrossRef]
- Liu, G.; Shu, C.; Liang, Z.; Peng, B.; Cheng, L. A Modified Sparrow Search Algorithm with Application in 3d Route Planning for UAV. Sensors 2021, 21, 1224. [Google Scholar] [CrossRef]
- Zhu, L.; Guan, G. Dynamical Analysis of a Rumor Spreading Model with Self-Discrimination and Time Delay in Complex Networks. Phys. A Stat. Mech. Appl. 2019, 533, 121953. [Google Scholar] [CrossRef]
- Diekmann, O.; Heesterbeek, H.; Britton, T. Mathematical Tools for Understanding Infectious Disease Dynamics; Princeton University Press: Princeton, NJ, USA, 2012; Volume 7. [Google Scholar]
- Cooke, K.L.; Van Den Driessche, P. On zeroes of some transcendental equations. Funkc. Ekvacioj 1986, 29, 77–90. [Google Scholar]
- Hassard, B.D.; Kazarinoff, N.D.; Wan, Y.H.; Wan, Y.W. Theory and Applications of Hopf Bifurcation; CUP Archive: Cambridge, UK, 1981; Volume 41. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).