Factors of Risk Analysis for IoT Systems
Abstract
:1. Introduction
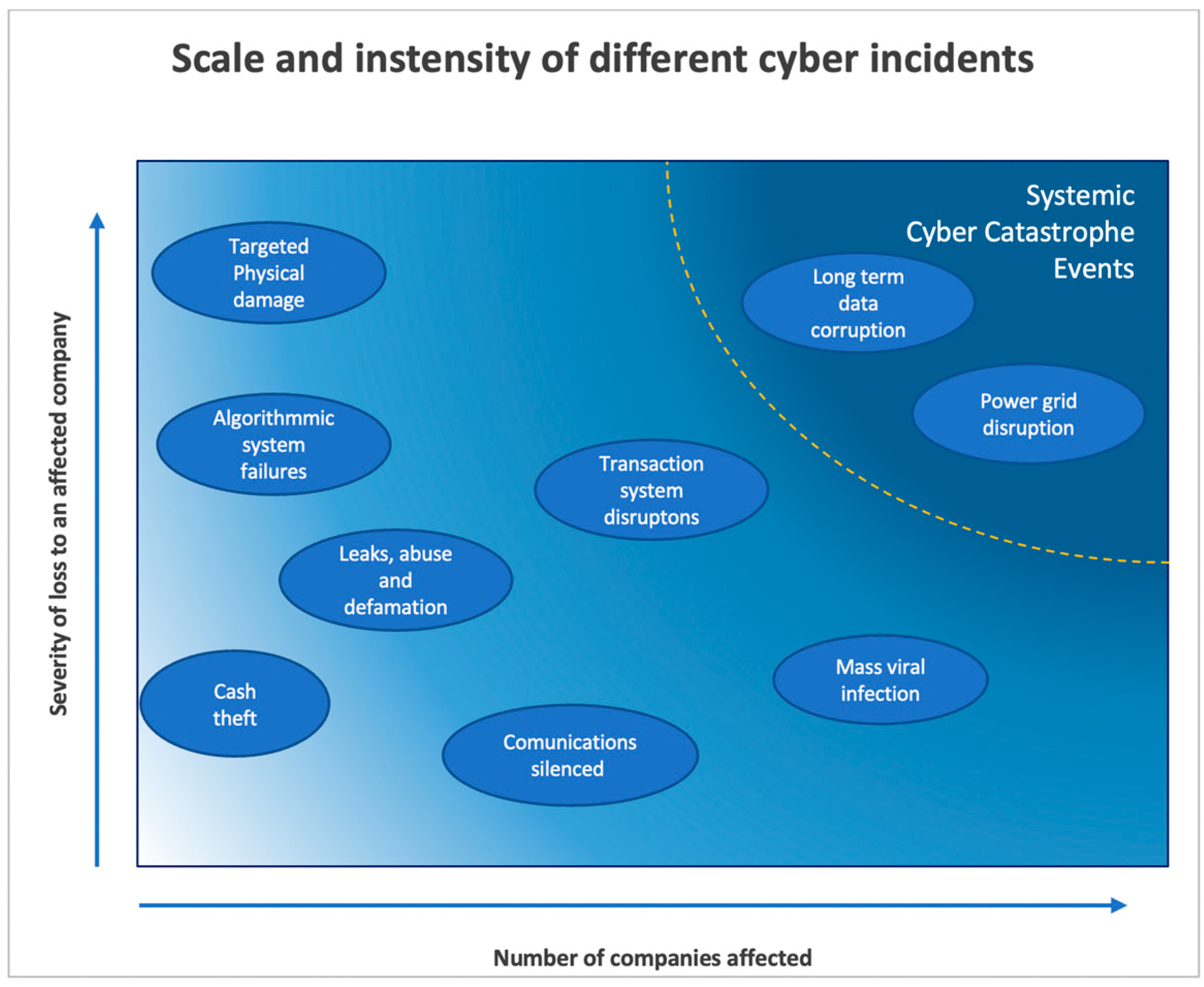
- Level 1: The pervasiveness of technology could penetrate a high number of organizations simultaneously;
- Level 2: Interdependencies between organizations are growing, and cybersecurity failure in one organization has the potential to cascade across its dependent organizations;
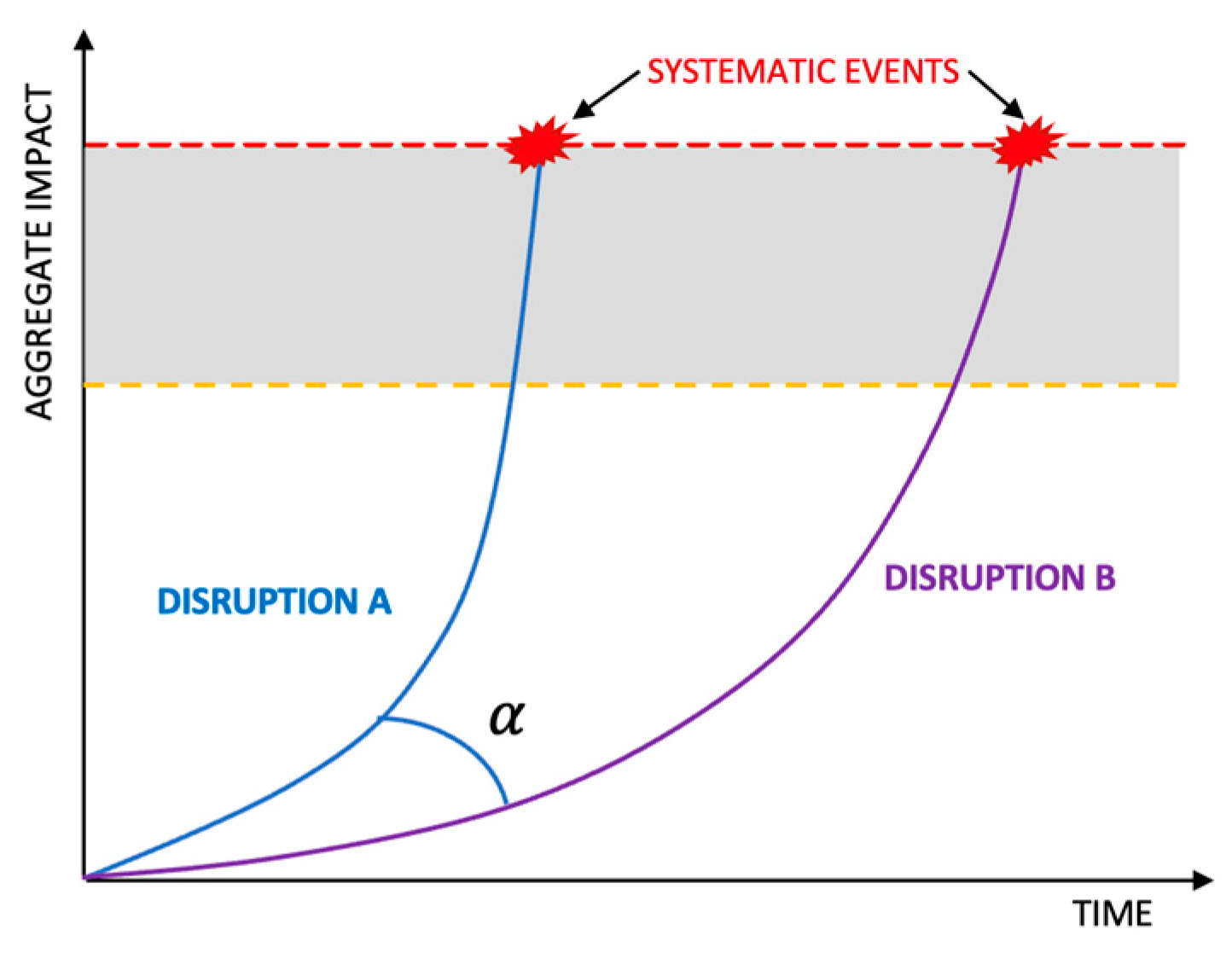
- Level 3: Cybersecurity failure could be systematically catastrophic to economies and societies, and multiple heterogeneous sectors could fail.
- Repeated attacks;
- Scattershot attacks;
- Pervasive attacks;
- Rolling attacks;
- Transitive attacks;
- Cascading attacks;
- Shared resource consumption attacks;
- Critical function attacks;
- Regional attacks;
- Service dependency attacks;
- Coordinated supply chain attacks.
- Risk concentration and lack of substitutability: Systemic risk arises from technical and IT systems, such as operating systems, program applications, cloud servers, and network equipment. These systems could be single points of failure, affecting the normal operations of organizations and generating financial/economic losses;
- Complex interdependency: Interconnections among systems increase the level of complexity, allowing cyber attacks to spread throughout a system. Impacts on one part of the system may affect another; for example, attacks on a central financial system are through indirect interconnections in remote areas. The accumulation of local volatility added to systemic risks is derived from the other networks;
- Risk correlation: Idiosyncratic cyber shocks can cause a loss of confidence that generates market liquidity shocks, market risk, and solvency risk.
- Small or idiosyncratic cyber events that, due to linkages and dependencies among affected organizations, generate cascade effects;
- Timing affects the response to events that, due to the resources of the organization, allow the mitigation of financial losses and control the damage to reputation;
- Focus on critical functions, increasing the impact related to the loss or disruption.
2. Background
2.1. Risk Analysis in IoT
- Shortcomings of period assessment;
- Changing of system boundaries;
- Failure to consider assets as an attack platform;
- The challenge of understanding connections.
- “Risk assessment AND IoT”;
- “Risk Security AND IoT”;
- “Risk analysis AND IoT”.
- IoT core value assets (IoTCA) where digital assets are categorized as (1a) IoT digitized assets (IoTDA) and services are digitized from traditional services, or (1b), in which IoT assets are born digital, representing things and services that are intrinsically digital;
- IoT operational assets (IoTOA), representing assets that support the creation, consumption, and distribution of services.
2.2. Risk Modeling
- Identifying the association degree of risk factors with specific data;
- Understanding that risk factors change over time;
- Identifying the association of risk factors with single or multiple systems.
- The risk factors;
- The stress scenario which prescribes a range of scenarios related with the risk factors;
- The monitored outcomes which represent subsequent actions and recommendations.
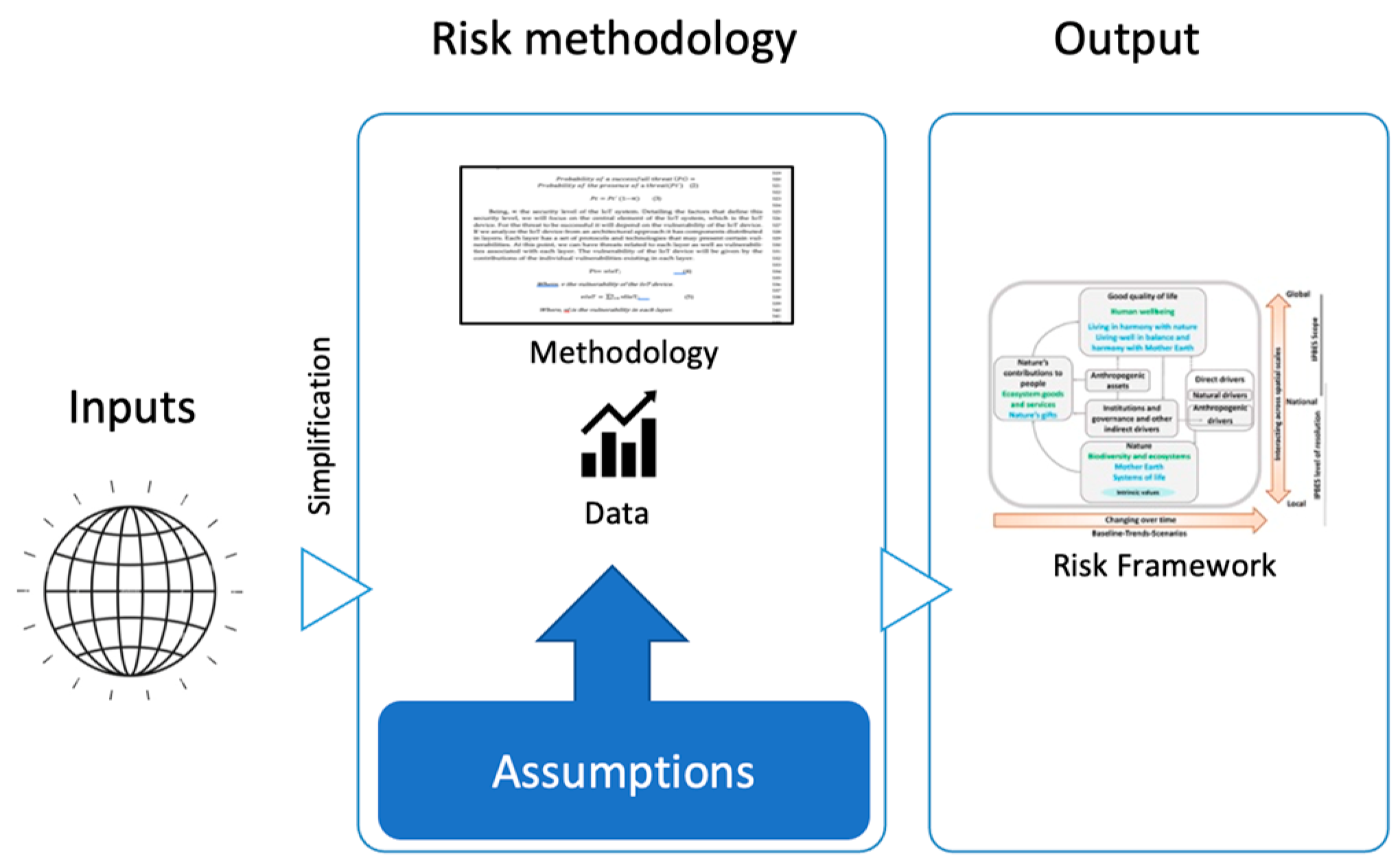
3. Risk Modeling in IoT Systems
- Define the method to quantify the risk. In this study this is performed in relation to probability and impact, which are generic factors used in multiple risk analysis methodologies and ISO 27,000 standards;
- Establish the input elements for the risk analysis in relation to the probability and impact. In this study, this is the macro categories (vulnerability, susceptibility, attack surface, interdependency);
- Establish the output elements for the risk analysis in relation to the probability and impact. In this study, this is the base of the economic impact, social impact, and environmental impact;
- Define the methodology to quantify the values in function of the interrelation between the macro categories. We establish a set of simulations to determine a distribution function in relationship to the inputs and outputs of the risk analysis;
- Based on the distribution function, we select a model to quantify the risk value from an economic perspective. We select an economic perspective in relation to the systematic risk possibility mentioned by the global economic forum and the contents of this study;
- We define a risk scale to determine the level of impact on the IoT attacks in relation to the possibility of a systematic risk event. The scale will monitor subsequent risk values.
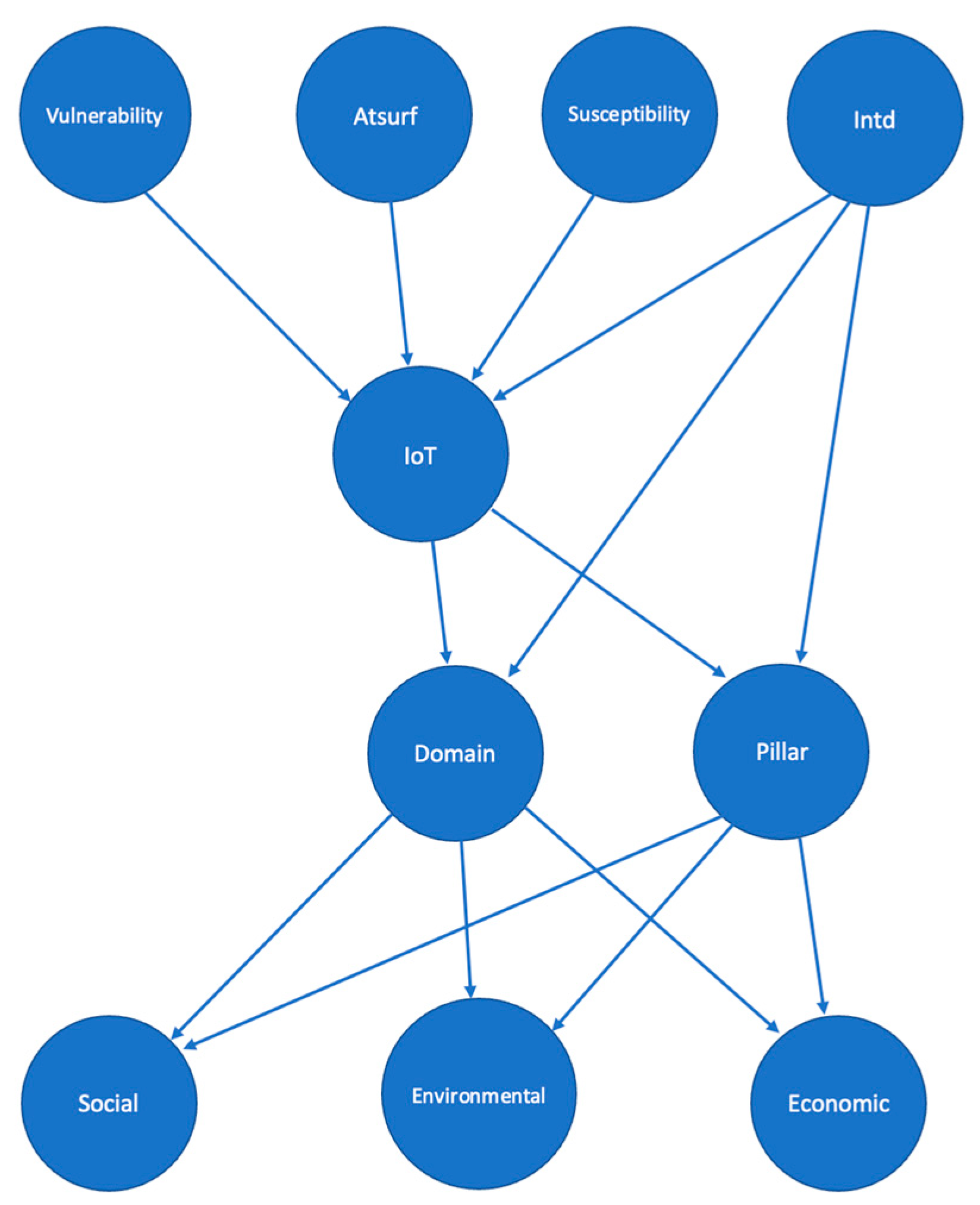
3.1. Input Elements
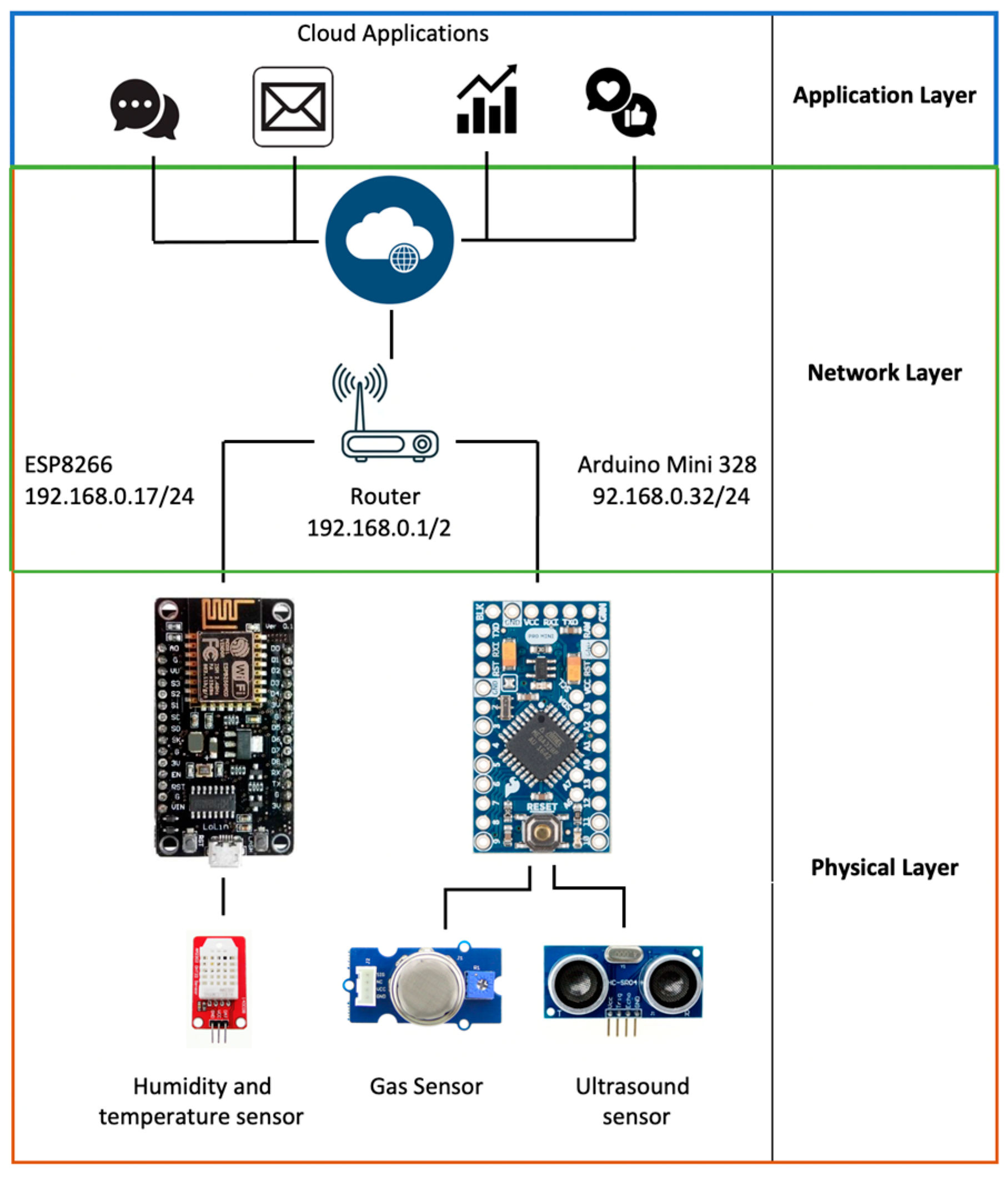
- Organization: The application domain for which the IoT system has been developed has certain inherent characteristics due to its functionality. Among the domains we have health, agriculture, education, and energy, among others. If we approach the analysis of an IoT solution applied for traffic management, its location will be in an external public area, which could imply an exposure to physical attacks, in contrast to an IoT solution used in smart homes. This is an aspect to be considered in security risk assessment processes. Additionally, in the organization we have the pillar related to technological infrastructure, economic infrastructure, social infrastructure, and governance, which may vary between organizations. Two factors related to organizations from a security perspective are:
- a.
- Vulnerability: The weakness in each layer of an IoT architecture, which is the possibility of suffering attacks;
- b.
- Susceptibility: IoT systems are made up of a set of protocols, technologies, and devices, so depending on this set, it is possible that one device is more susceptible to an attack than another.
- Attack surface: The greater number of interconnected devices and systems increases the surface to be exploited by a given threat that is likely to generate an attack.
- Interdependence: Interdependence between IoT, OT and IT systems can increase risk exposure as there is the possibility of an attack from external systems. How security attacks interact with more IoT elements can also modify the level of risk.
3.2. Output Elements
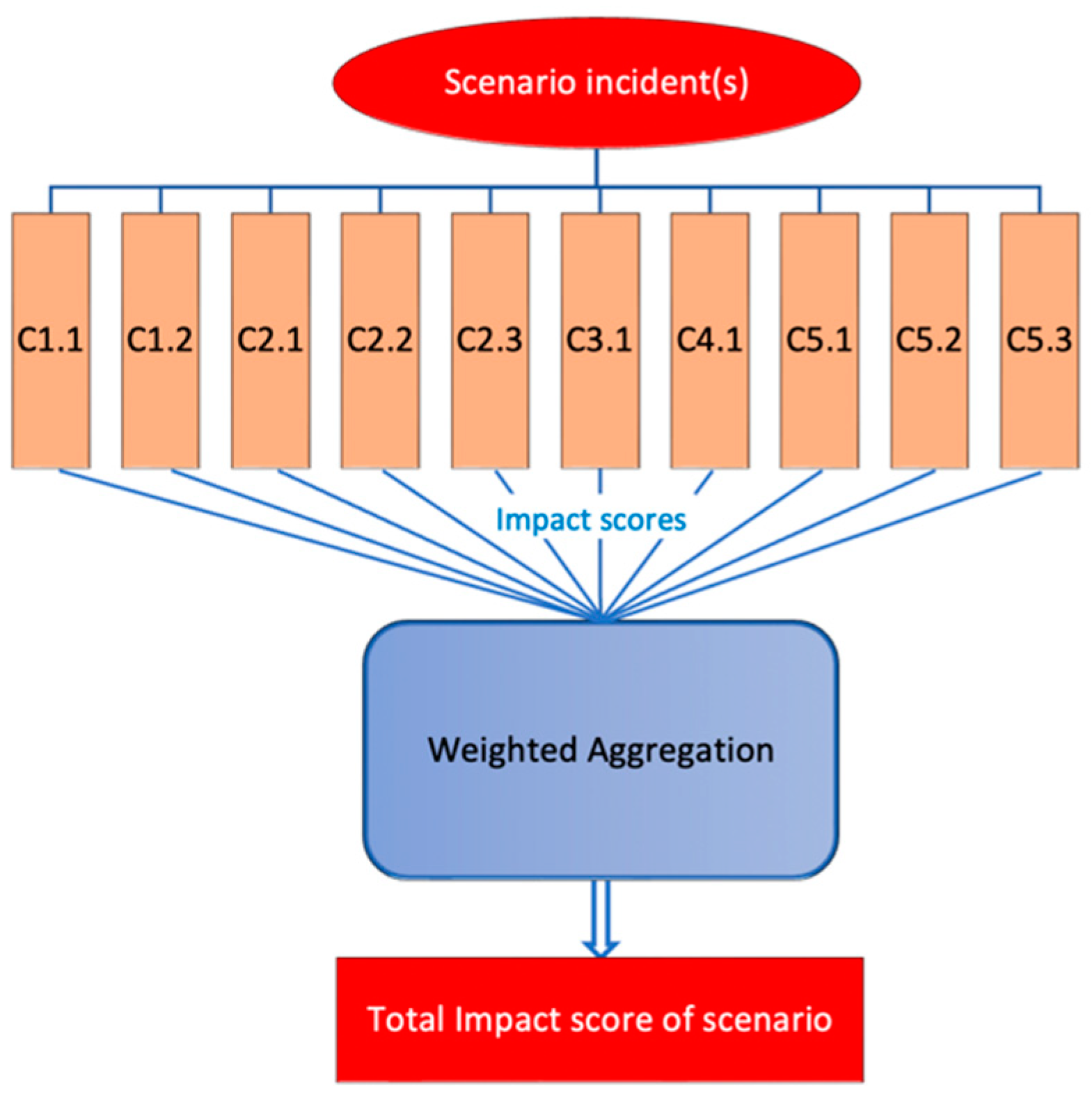
3.3. Methodology
4. Monitoring of Outputs
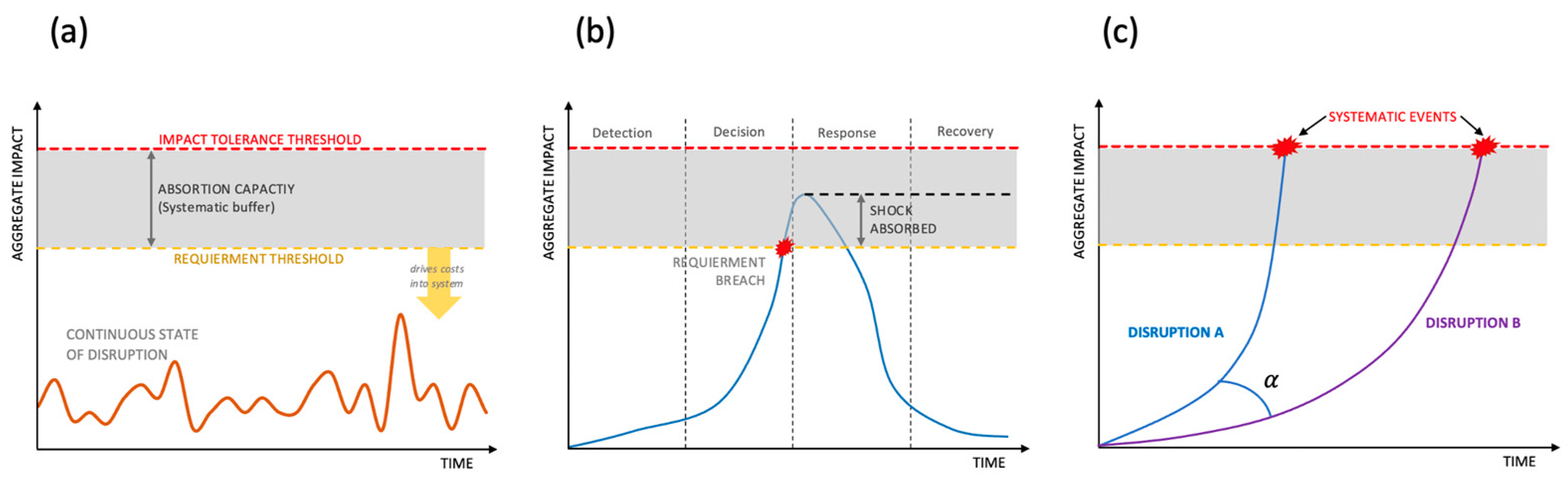
- Context: We define the following assumption. A DoS attack on a parking IoT system is presented. We define our capacity of absorption of losses as USD 25,000;
- Shock: The attack could generate economic, social, and environmental losses. In Table 10, we describe the possible loss for economic, social, and environmental aspects;
- Amplification: The attack not only affects the parking lot with losses, but the owners as well. The social event in this case has the same value as the economic impact;
- Systemic Event: In this case, there is no systemic event that could affect the local or global economy.
5. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Al-Sarawi, Shadi, Mohammed Anbar, Rosni Abdullah, and Ahmad B. Al Hawari. 2020. Internet of Things Market Analysis Forecasts, 2020–2030. Paper presented at 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, July 27–28; pp. 449–53. [Google Scholar] [CrossRef]
- Andrade, Roberto O., Sang G. Yoo, Iván Ortiz-Garces, and Jhonattan Barriga. 2022. Security Risk Analysis in IoT Systems through Factor Identification over IoT Devices. Applied Sciences 12: 2976. [Google Scholar] [CrossRef]
- Andrade, Roberto Omar, Sang Guun Yoo, Luis Tello-Oquendo, and Iván Ortiz-Garcés. 2020. A Comprehensive Study of the IoT Cybersecurity in Smart Cities. IEEE Access 8: 228922–41. [Google Scholar] [CrossRef]
- Bank of England. 2022. Model Risk Management Principles for Stress Testing. Available online: https://www.bankofengland.co.uk/prudential-regulation/publication/2018/model-risk-management-principles-for-stress-testing-ss (accessed on 18 April 2022).
- BBC. 2022. BitMart: Crypto-Exchange Losses $150m to Hackers. Available online: https://www.bbc.com/news/technology-59549606 (accessed on 18 April 2022).
- Cazares, María, Roberto O. Andrade, Julio Proaño, and Iván Ortiz. 2021. Study of Technological Solutions in the Analysis of Behavioral Factors for Sustainability Strategies. In Sustainable Intelligent Systems. Advances in Sustainability Science and Technology. Edited by Amit Joshi, Atulya K. Nagar and Gabriela Marín-Raventós. Singapore: Springer. [Google Scholar] [CrossRef]
- Echeverría, Aarón, Cristhian Cevallos, Ivan Ortiz-Garces, and Roberto O. Andrade. 2021. Cybersecurity Model Based on Hardening for Secure Internet of Things Implementation. Applied Sciences 11: 3260. [Google Scholar] [CrossRef]
- European Systemic Risk Board. 2022. Mitigating Systemic Cyber Risk. Available online: https://www.esrb.europa.eu/news/schedule/2021/html/20210701_conf_systemic_risk_analytics.en.html (accessed on 15 January 2022).
- García, Fresia Yanina Holguín, and Lohana Mariella Lema Moreta. 2018. Maturity Model for the Risk Analysis of Information Assets based on Methodologies MAGERIT, OCTAVE y MEHARI; focused on Shipping Companies. Paper presented at 2018 7th International Conference on Software Process Improvement (CIMPS), Guadalajara, Mexico, October 17–19; pp. 29–39. [Google Scholar] [CrossRef]
- Huang, Yu-Lun, and Wen-Lin Sun. 2018. An AHP-Based Risk Assessment for an Industrial IoT Cloud. Paper presented at 2018 IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C), Lisbon, Portugal, July 16–20. [Google Scholar]
- International Monetary Fund. 2022. Understanding Financial Interconnectedness. Available online: https://www.elibrary.imf.org/view/journals/007/2010/023/article-A001-en.xml (accessed on 2 February 2022).
- Kaffenberger, Lincoln, and Emanuel Kopp. 2022. Cyber Risk Scenarios, the Financial System, and Systemic Risk Assessment. Available online: https://carnegieendowment.org/2019/09/30/cyber-risk-scenarios-financial-system-and-systemic-risk-assessment-pub-79911 (accessed on 18 April 2022).
- Kieras, Timothy, Junaid Farooq, and Quanyan Zhu. 2021. I-SCRAM: A Framework for IoT Supply Chain Risk Analysis and Mitigation Decisions. IEEE Access 9: 29827–40. [Google Scholar] [CrossRef]
- Lee, In. 2020. Internet of Things (IoT) Cybersecurity: Literature Review and IoT Cyber Risk Management. Future Internet 12: 157. [Google Scholar] [CrossRef]
- Matheu-García, Sara N., José L. Hernández-Ramos, Antonio F. Skarmeta, and Gianmarco Baldini. 2019. Risk-based automated assessment and testing for the cybersecurity certification and labelling of IoT devices. Computer Standards & Interfaces 62: 64–83. [Google Scholar] [CrossRef]
- McKinsey. 2022. Meeting the Future: Dynamic Risk Management for Uncertain Times. Available online: https://www.mckinsey.com/business-functions/risk-and-resilience/our-insights/meeting-the-future-dynamic-risk-management-for-uncertain-times (accessed on 18 April 2022).
- NetDiligence. 2022. Sixth Annual Cyber Claims Study | NetDiligence. Available online: https://netdiligence.com/press-releases/netdiligence-releases-latest-study-on-cyber-claim-costs/ (accessed on 18 April 2022).
- New York Times. 2022. Pipeline Attack Yields Urgent Lessons About U.S. Cybersecurity. Available online: https://www.nytimes.com/2021/05/14/us/politics/pipeline-hack.html (accessed on 18 April 2022).
- Nurse, Jason R. C., Sadie Creese, and David De Roure. 2017. Security Risk Assessment in Internet of Things Systems. IT Professional 19: 20–26. [Google Scholar] [CrossRef] [Green Version]
- Park, Mookyu, Haengrok Oh, and Kyungho Lee. 2019. Security Risk Measurement for Information Leakage in IoT-Based Smart Homes from a Situational Awareness Perspective. Sensors 19: 2148. [Google Scholar] [CrossRef] [Green Version]
- Pereira, Carlos, Diana Guimarães, João Mesquita, Frederico Santos, Luis Almeida, and Ana Aguiar. 2018. Feasibility of Gateway-Less IoT E-Health Applications. Paper presented at 2018 European Conference on Networks and Communications (EuCNC), Ljubljana, Slovenia, June 18–21; pp. 324–28. [Google Scholar] [CrossRef]
- Rak, Massimiliano, Valentina Casola, Alessandra De Benedictis, and Umberto Villano. 2018. Automated Risk Analysis for IoT Systems. In Lecture Notes on Data Engineering and Communications Technologies. Berlin: Springer, pp. 265–75. [Google Scholar] [CrossRef]
- Randaliev, Petar, Dave De Roure, Stacy Cannady, Rafael Mantilla Montalvo, Razvan Nicolescu, and Michael Huth. 2018. Economic impact of IoT cyber risk—Analysing past and present to predict the future developments in IoT risk analysis and IoT cyber insurance. Paper presented at Living in the Internet of Things: Cybersecurity of the IoT—2018, London, UK, March 28–29. [Google Scholar]
- Thibaud, Montbel, Huihui Chi, Wei Zhou, and Selwyn Piramuthu. 2018. Internet of Things (IoT) in high-risk Environment, Health and Safety (EHS) industries: A comprehensive review. Decision Support Systems 108: 79–95. [Google Scholar] [CrossRef]
- World Economic Forum. 2016. Understanding-Systemic-Cyber-Risk. Available online: https://www.weforum.org/whitepapers/understanding-systemic-cyber-risk (accessed on 18 April 2022).
- World Economic Forum. 2022. Global Risks Report 2022. Available online: https://www.weforum.org/reports/global-risks-report-2022 (accessed on 18 April 2022).

| Category | Mean | Medium | Max |
|---|---|---|---|
| Wire transfer found | 180 | 105 | 1400 |
| Wrongful data collection | 86 | 86 | 86 |
| System glitch | 1900 | 79 | 17,500 |
| Hacker | 337 | 74 | 7400 |
| Malware/virus | 308 | 70 | 9000 |
| Focus on | Based on | Contrasted with | Economic Impact Evaluated by | Reference |
|---|---|---|---|---|
| Gateway, Network, IoT device, Service | The ISO 31000, ISO 29119, STRIDE | NIST Security Control Framework | Does not apply | Sara |
| IoT digital assets | Business Impact Analysis | Does not apply | MicroMort y VaR | Randaliev |
| IoT assets | CKC framework | Center for Internet Security (CIS) | Expected financial loss | Thibaud |
| IoT nodes | LINDDUN | Does not consider | Cumulative business impact | Shivraj |
| IoT devices | AHP-based | %CPU y traffic-rate | Does not apply | Huang |
| IoT devices | Product threat, vulnerability, impact | CVSS | Does not apply | Park |
| IoT devices | Security graph | Security attributes, dependencies, security logical functions and security risk. | Does not apply | Kieras |
| Asset Threat Identification | ISO, STRIDE | NIST Security Control Framework | Does not apply | Rak |
| Layer | Attacks |
|---|---|
| Application | Social Engineering |
| Virus | |
| Trojan Injection Unauthorized access | |
| Exhaustion Collision Malware | |
| Network | Man-in-the-middle |
| Wormhole | |
| Unfairness | |
| De-synchronization | |
| Flooding | |
| Physical | Selective forwarding |
| Spoofing | |
| Eavesdropping | |
| Tampering | |
| Sybil | |
| Jamming |
| Compliance Classes | Description | Confidentiality | Integrity | Availability |
|---|---|---|---|---|
| Class 0 | Impact could happen in the IoT system | Low | Low | Low |
| Class 1 | Limited impact could occur in the IoT system. | Low | Medium | Medium |
| Class 2 | Significative impact to the availability of IoT system | Medium | Medium | High |
| Class 3 | Impact to sensitive data of IoT system | High | Medium | High |
| Class 4 | Loss control and critical impact of the IoT system. | High | High | High |
| Vertical Domain | Physical Vulnerability | Network Vulnerability | Application Vulnerability | Beta |
|---|---|---|---|---|
| Smart home | Within the boundaries of a house or building. Generally, few meters of geographic area. | Network topology generally is of star type. Network topology is small. Few devices in the network. | Applications on mobile devices, especially smartphones. | Low |
| Smart health | Within the boundaries of a building or medical campus. Coverage of geographic area of meters or kilometers. | Network topology could be extended-star type. The size of the network is medium. Network could contain hundreds of devices. | Applications on mobile devices (smartphones and tablets). | Medium |
| Smart traffic | Within the boundaries of a city. Geographic coverage in kilometers. | Mesh-type network topology. Large network. | Applications on computer devices (information systems). | High |
| Vertical/Domain | Economic | Social | Environmental |
|---|---|---|---|
| Smart city | Potential loss of high economic revenues due to non-operation of city services. | Loss of credibility of public services. | Possibility of certain attacks affecting services related to waste management that could affect the environment. |
| Smart health | Possible high economic losses due to possible legal claims. | Possibility of the loss of lives. | Possibility of certain attacks affecting waste management. |
| Smart home | Possible low economic losses. | Low impact. | Low impact. |
| Smart grid | Potential high economic losses due to lack of energy for the organization’s operations. | Possibility of generating a feeling of chaos, insecurity, or stress in people due to the lack of electric power. | Possibility of certain attacks affecting waste management or environmental control processes in organizations due to lack of energy. |
| Smart traffic | Possible low-to-medium economic losses due to delays in people getting to their jobs. | Possibility of generating anxiety and exhaustion in drivers. | Possibility of increased pollution due to vehicular congestion. |
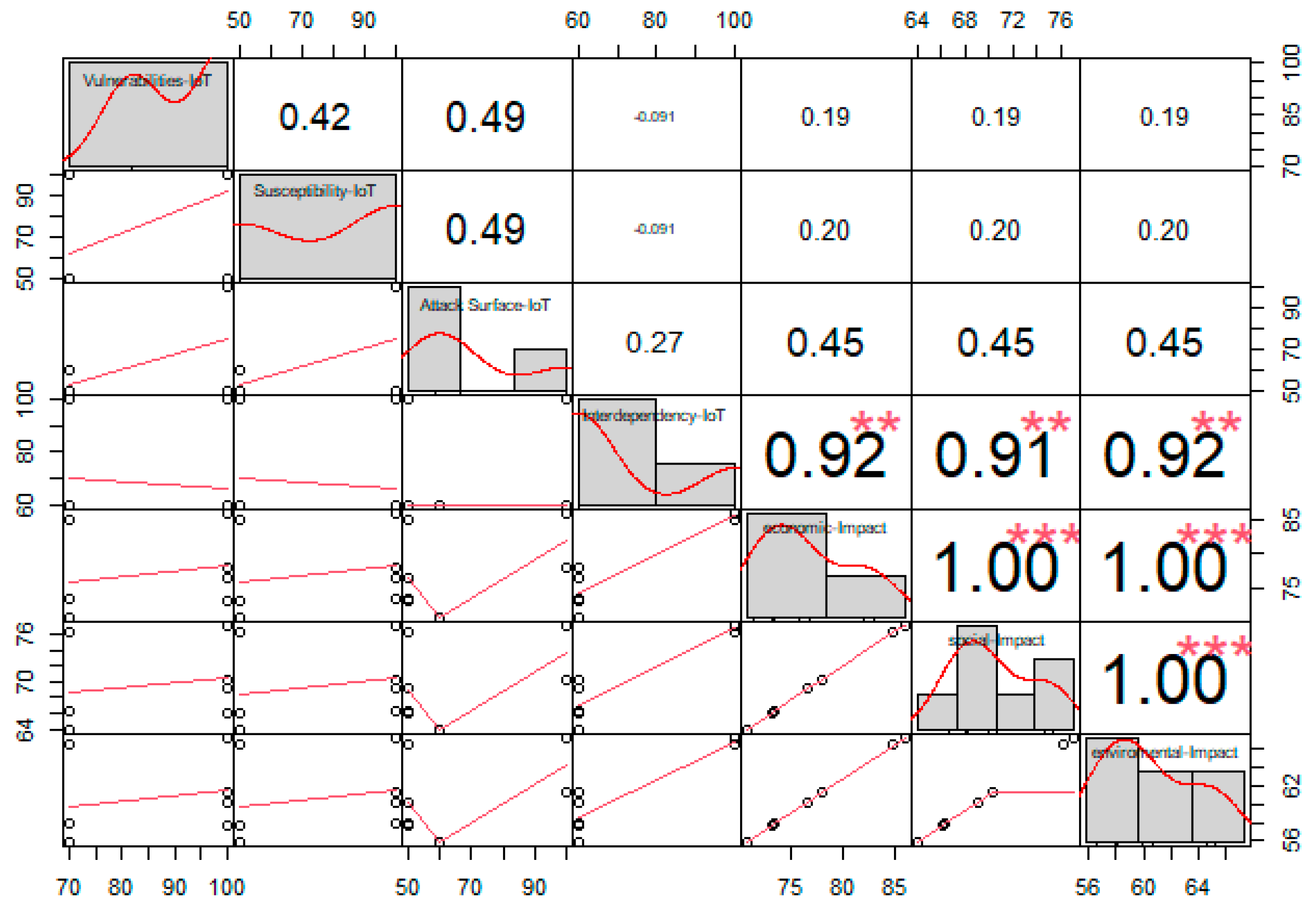
| Vulnerabilities–IoT | Susceptibility–IoT | Attack Surface–IoT | Interdependency–IoT | Economic Impact | Social Impact | Environmental Impact |
|---|---|---|---|---|---|---|
| 70.00% | 50.00% | 60.00% | 60.00% | 70.77% | 63.98% | 55.90% |
| 100.00% | 50.00% | 50.00% | 60.00% | 73.12% | 66.04% | 57.66% |
| 100.00% | 100.00% | 50.00% | 60.00% | 76.56% | 69.08% | 60.26% |
| 100.00% | 100.00% | 100.00% | 60.00% | 77.91% | 70.25% | 61.26% |
| 100.00% | 100.00% | 100.00% | 100.00% | 86.05% | 77.15% | 67.28% |
| 70.00% | 100.00% | 50.00% | 60.00% | 73.40% | 66.30% | 57.88% |
| 70.00% | 50.00% | 50.00 | 100.00% | 84.86% | 76.2% | 66.43% |
| Economic Impact | Risk Level |
|---|---|
| 70.77 | 7 |
| 73.12 | 7 |
| 76.56 | 7 |
| 77.91 | 7 |
| 86.05 | 8 |
| 73.40 | 7 |
| 84.86 | 8 |
| Attack | Lower | Upper |
|---|---|---|
| DoS | 15,000 | 45,000 |
| Eavesdropping | 2000 | 7500 |
| Privilege Escalation Attack | 10,000 | 80,000 |
| Indicator for Estimating Cost of Economic Security |
|---|
| Damage to smart infrastructure |
| A DoS attack can affect the IoT infrastructure related to vehicle detection devices, generating 10 h of inoperability to the parking lot. |
| Economic Loss |
| There are financial losses due to an estimated parking flow of 100 cars per hour. Since the inoperability is set to 10 h with a parking price at USD 10, the final loss cost is approximately USD 10,000. |
| Social damage |
| A social impact is inevitable due to the unavailability of parking lots, this generates stress and latency in people’s lives. In this case, we estimate that at least half (500) of the owners had an hour delay; if they were to be paid USD 20 an hour, the total loss would be USD 10,000. |
| Environmental damage |
| The inoperability of parking lots implies that cars will have to circulate throughout the zone generating more contamination to the atmosphere than usual. For simplicity, let us suppose that the environmental damage is of USD 5000. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Andrade, R.; Ortiz-Garcés, I.; Tintin, X.; Llumiquinga, G. Factors of Risk Analysis for IoT Systems. Risks 2022, 10, 162. https://doi.org/10.3390/risks10080162
Andrade R, Ortiz-Garcés I, Tintin X, Llumiquinga G. Factors of Risk Analysis for IoT Systems. Risks. 2022; 10(8):162. https://doi.org/10.3390/risks10080162
Chicago/Turabian StyleAndrade, Roberto, Iván Ortiz-Garcés, Xavier Tintin, and Gabriel Llumiquinga. 2022. "Factors of Risk Analysis for IoT Systems" Risks 10, no. 8: 162. https://doi.org/10.3390/risks10080162
APA StyleAndrade, R., Ortiz-Garcés, I., Tintin, X., & Llumiquinga, G. (2022). Factors of Risk Analysis for IoT Systems. Risks, 10(8), 162. https://doi.org/10.3390/risks10080162







